Malicious NuGet Packages Caught Distributing SeroXen RAT Malware

CATEGORIE : Virus |
DATE: 31.10.23 |
| WEB : The Hacker News |
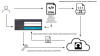
Cybersecurity researchers have uncovered a new set of malicious packages published to the NuGet package manager using a lesser-known method for malware deployment.
Software supply chain security firm ReversingLabs described the campaign as coordinated and ongoing since August 1, 2023, while linking it to a host of rogue NuGet packages that were observed delivering a remote access trojan called SeroXen RAT.