Hackers Can Exploit Windows Container Isolation Framework to Bypass Endpoint Security

CATEGORIE : Exploit |
DATE: 31.8.23 |
| WEB : The Hacker News |
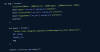
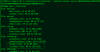
New findings show that malicious actors could leverage a sneaky malware detection evasion technique and bypass endpoint security solutions by manipulating the Windows Container Isolation Framework.
The findings were presented by Deep Instinct security researcher Daniel Avinoam at the DEF CON security conference held earlier this month.
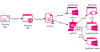
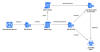
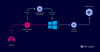
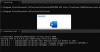
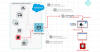
Microsoft's container architecture (and by extension, Windows Sandbox) uses what's called a dynamically generated image to separate the file system from each container to the host and at the same time avoid duplication of system files.