Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks

CATEGORIE : Cryptocurrency |
DATE: 31.12.23 |
| WEB : The Hacker News |
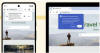
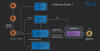
Cybersecurity researchers are warning about an increase in phishing attacks that are capable of draining cryptocurrency wallets.
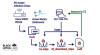
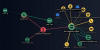
"These threats are unique in their approach, targeting a wide range of blockchain networks, from Ethereum and Binance Smart Chain to Polygon, Avalanche, and almost 20 other networks by using a crypto wallet-draining technique," Check Point researchers Oded Vanunu, Dikla Barda, and Roman Zaikin said.